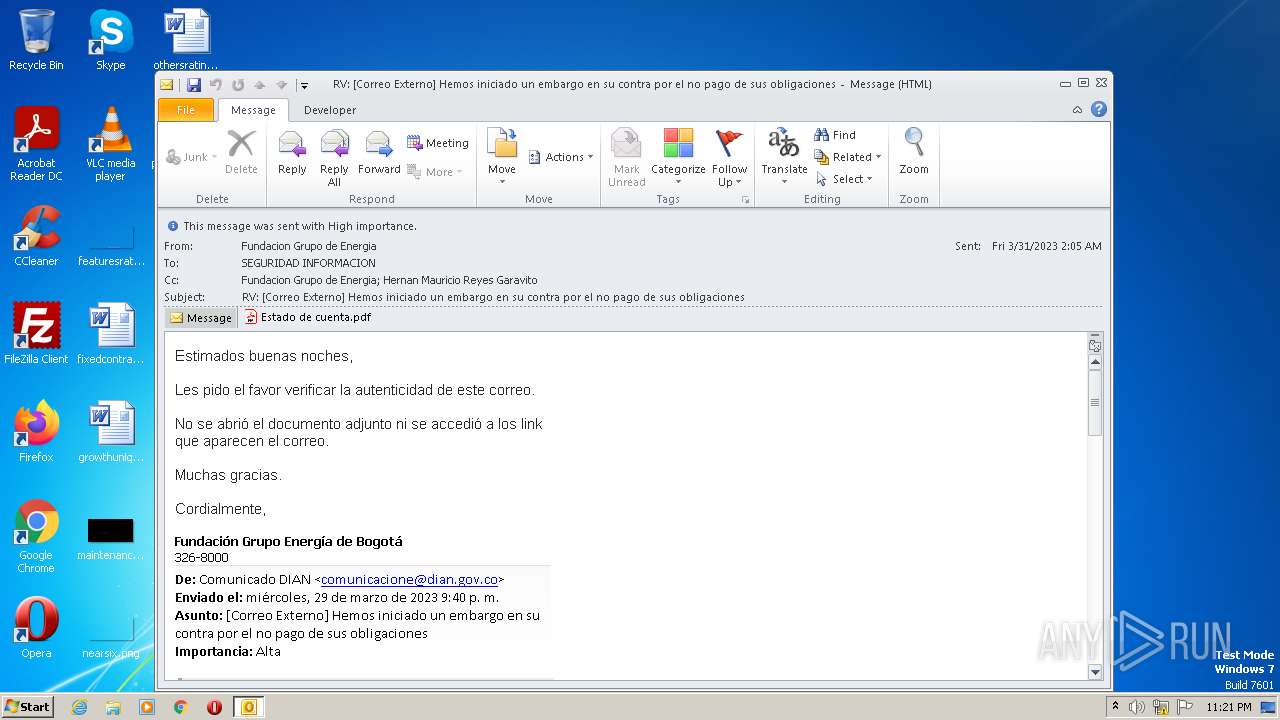
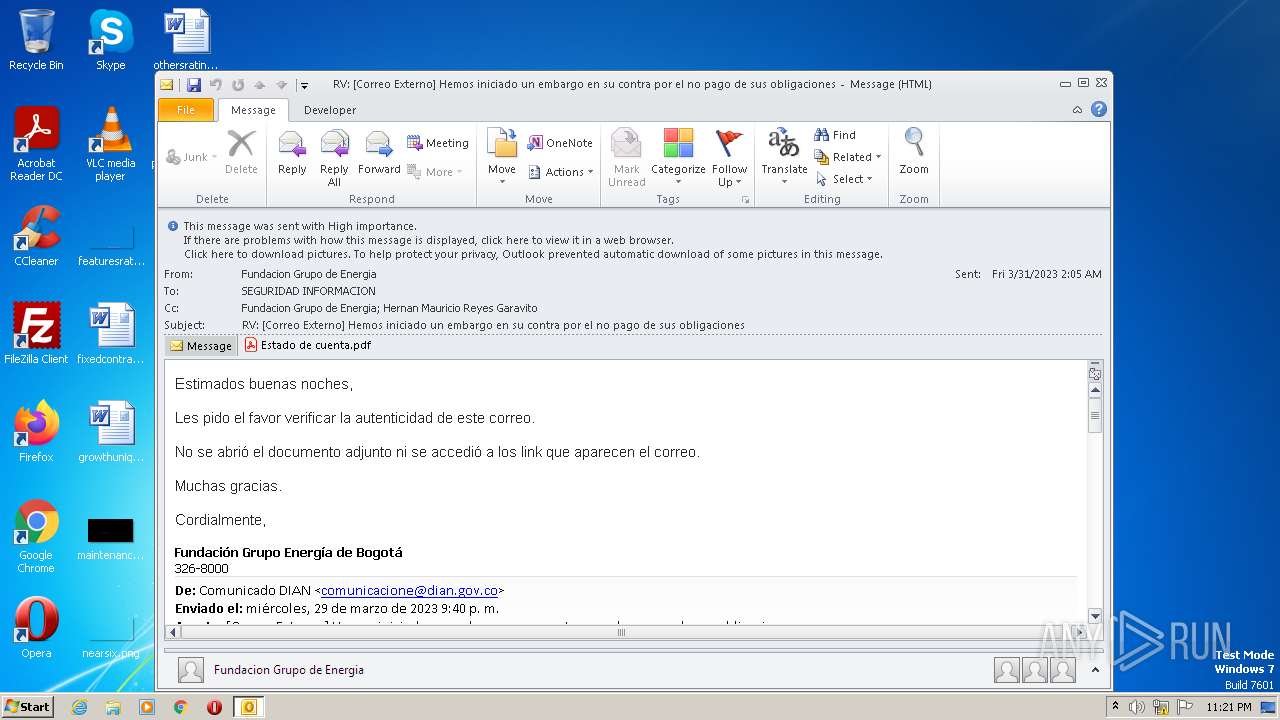
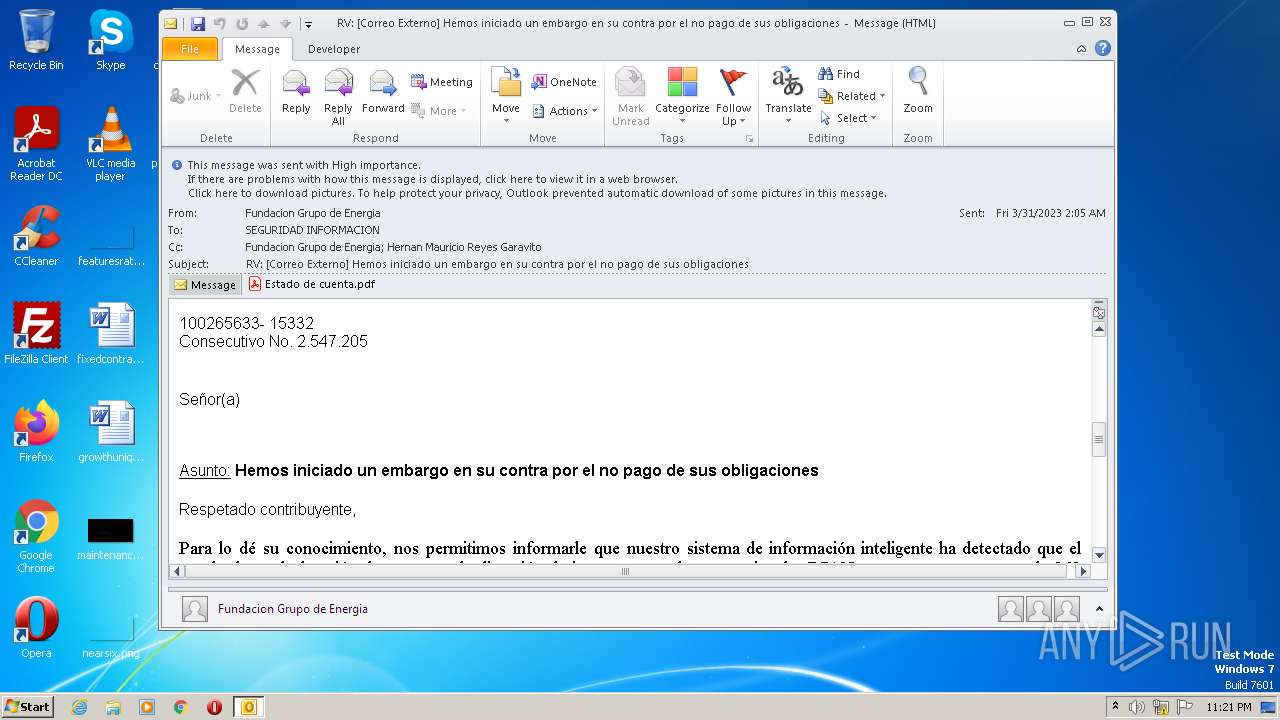
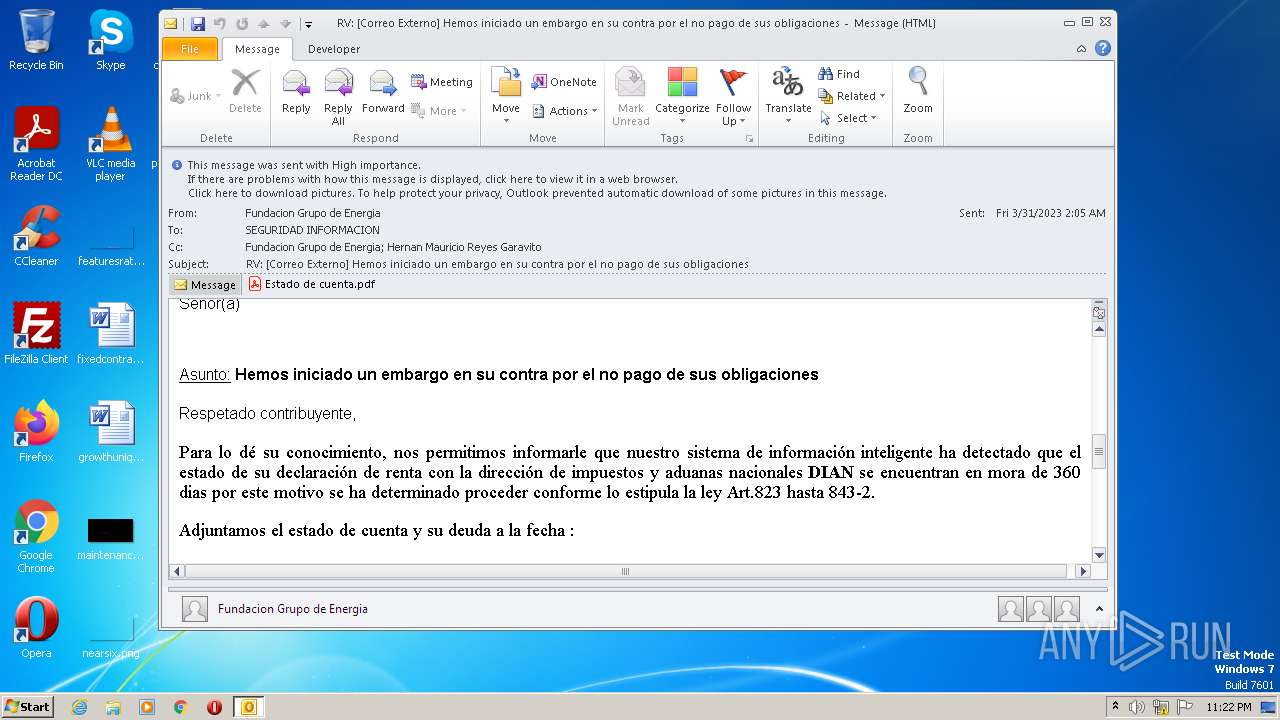
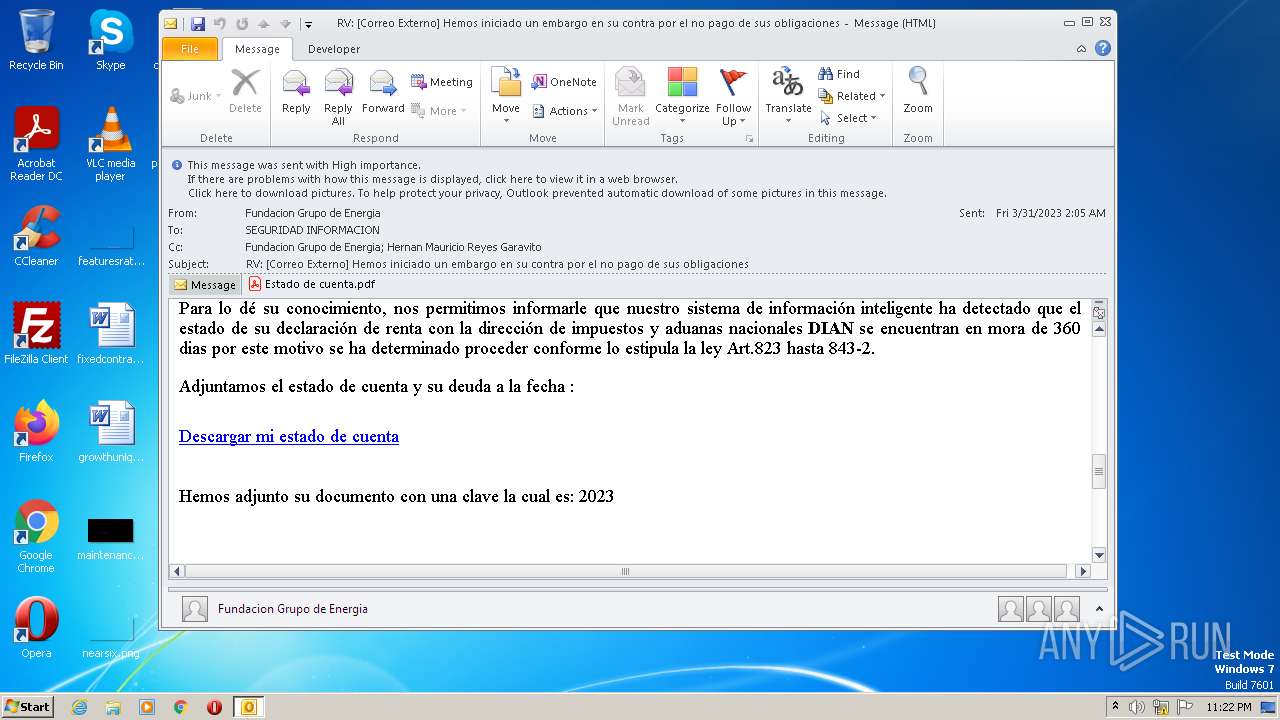
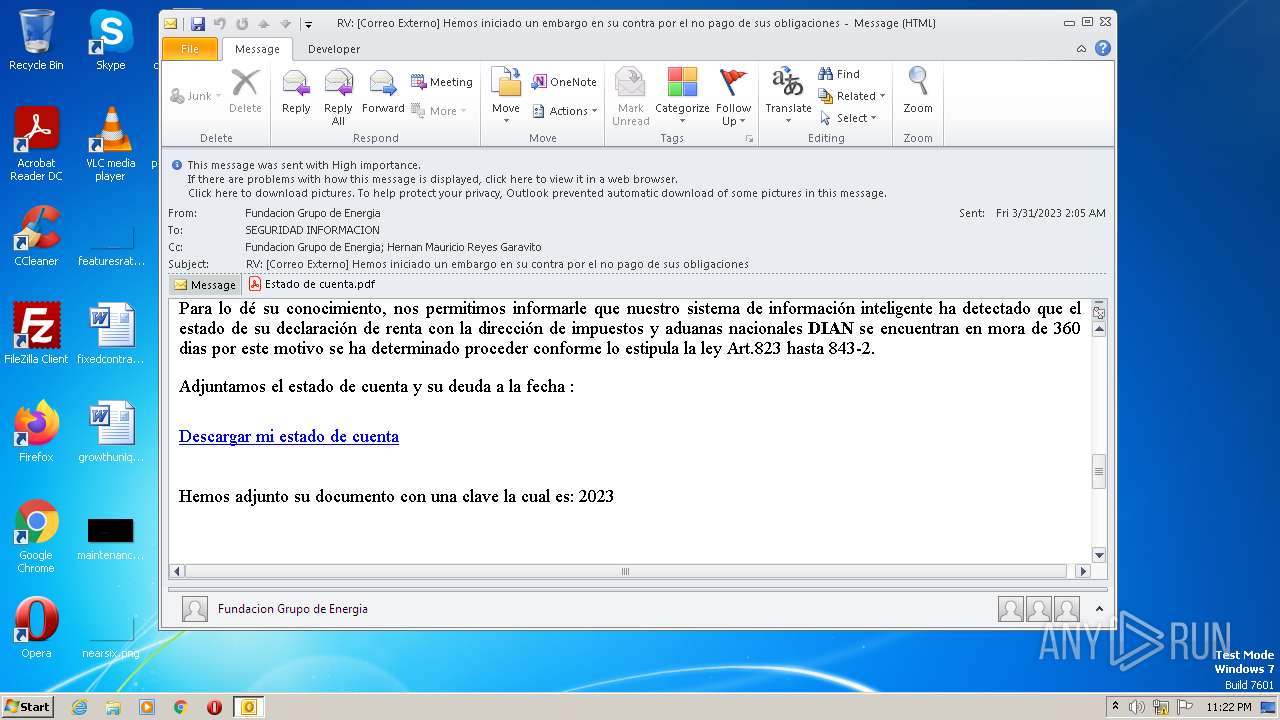
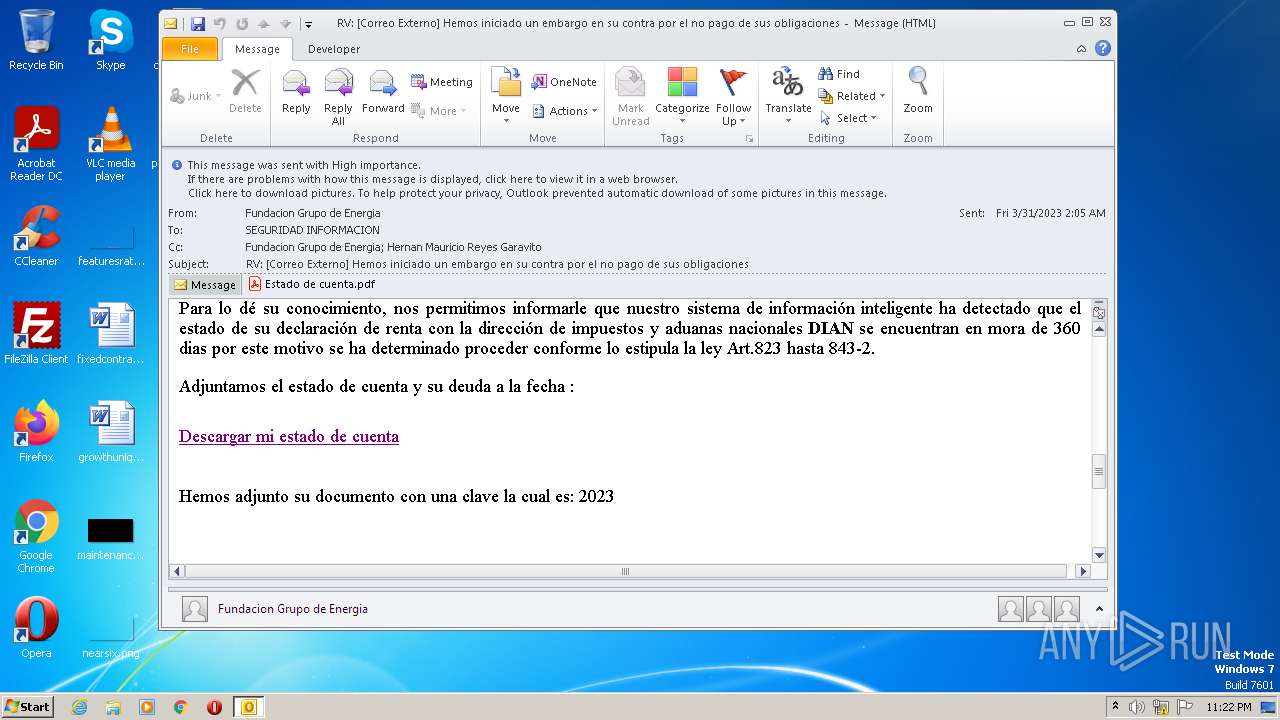
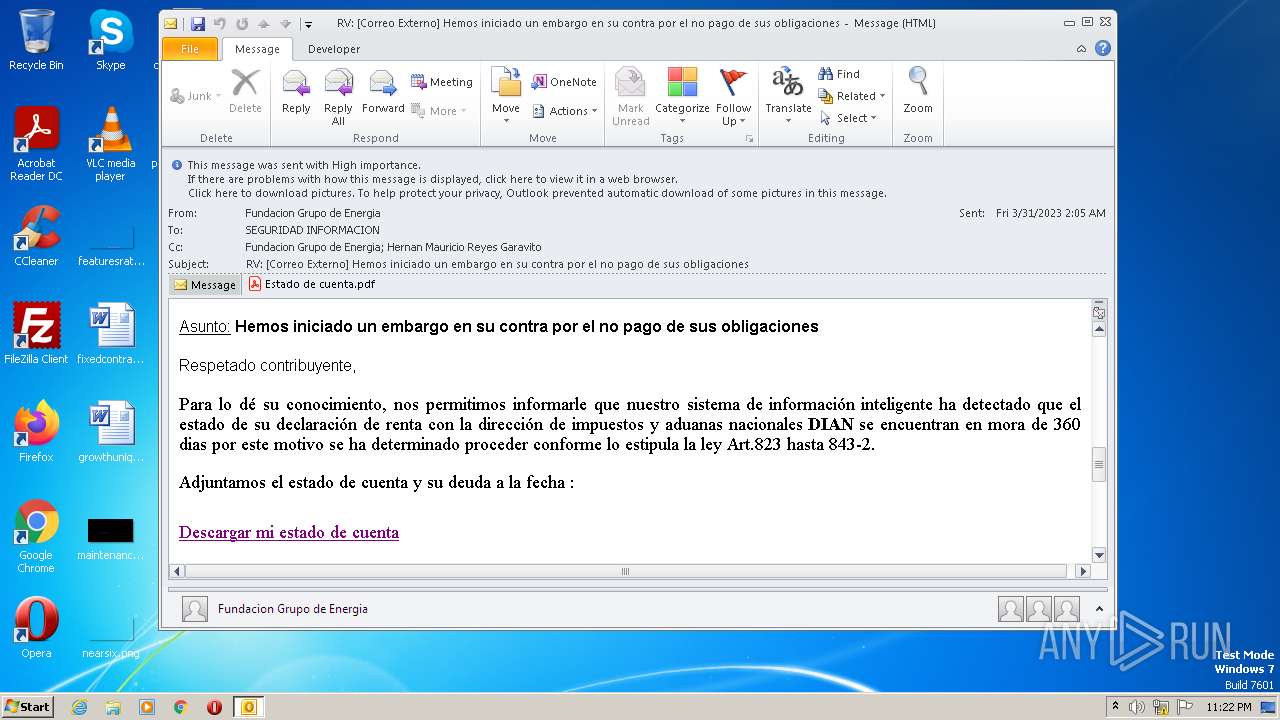
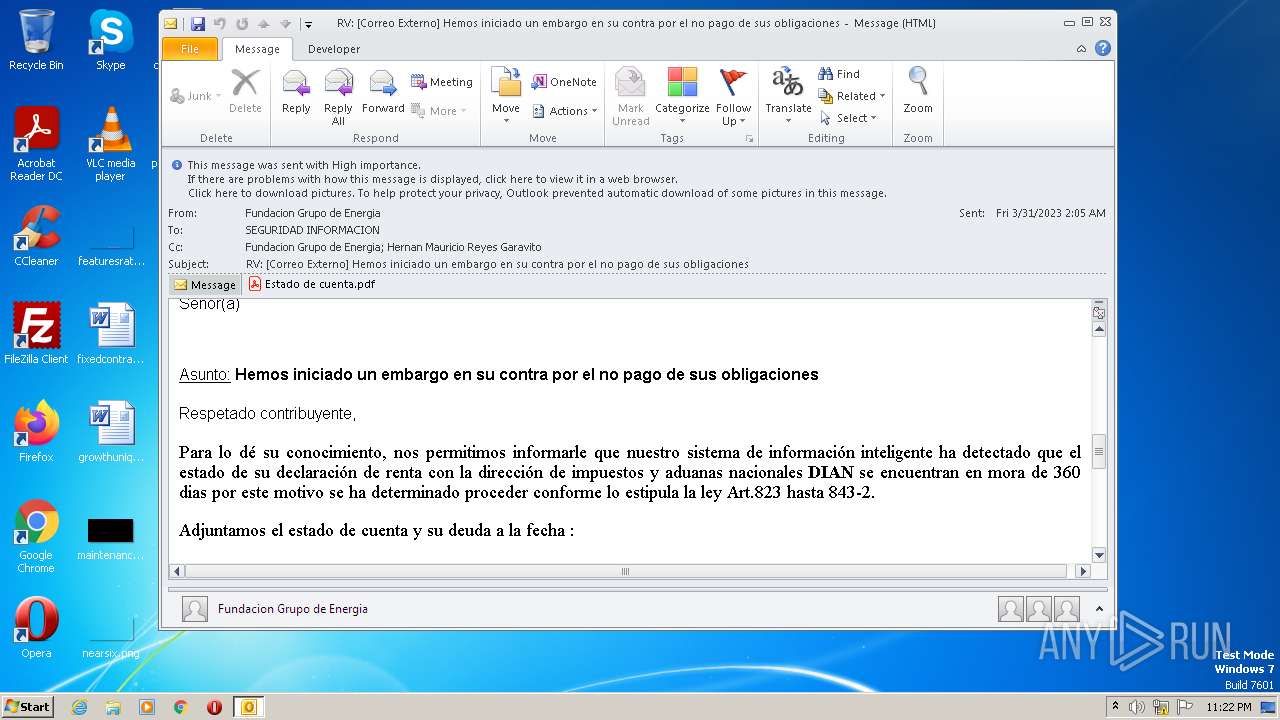
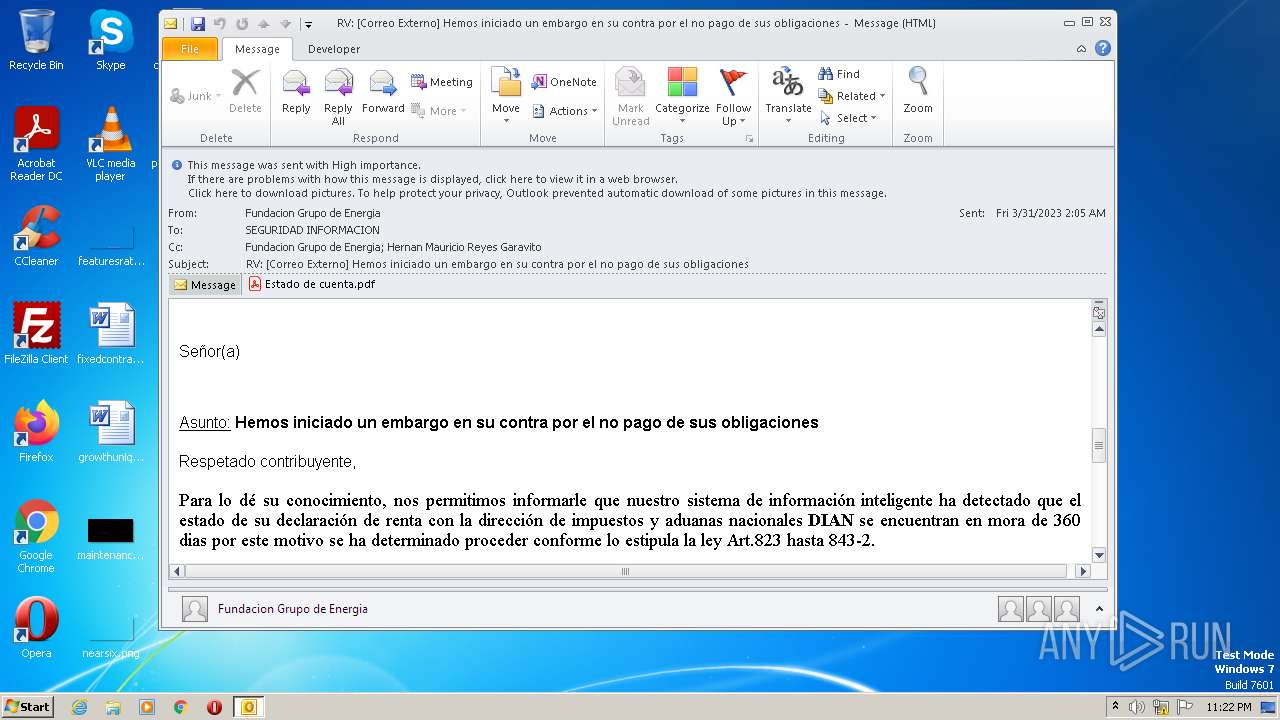
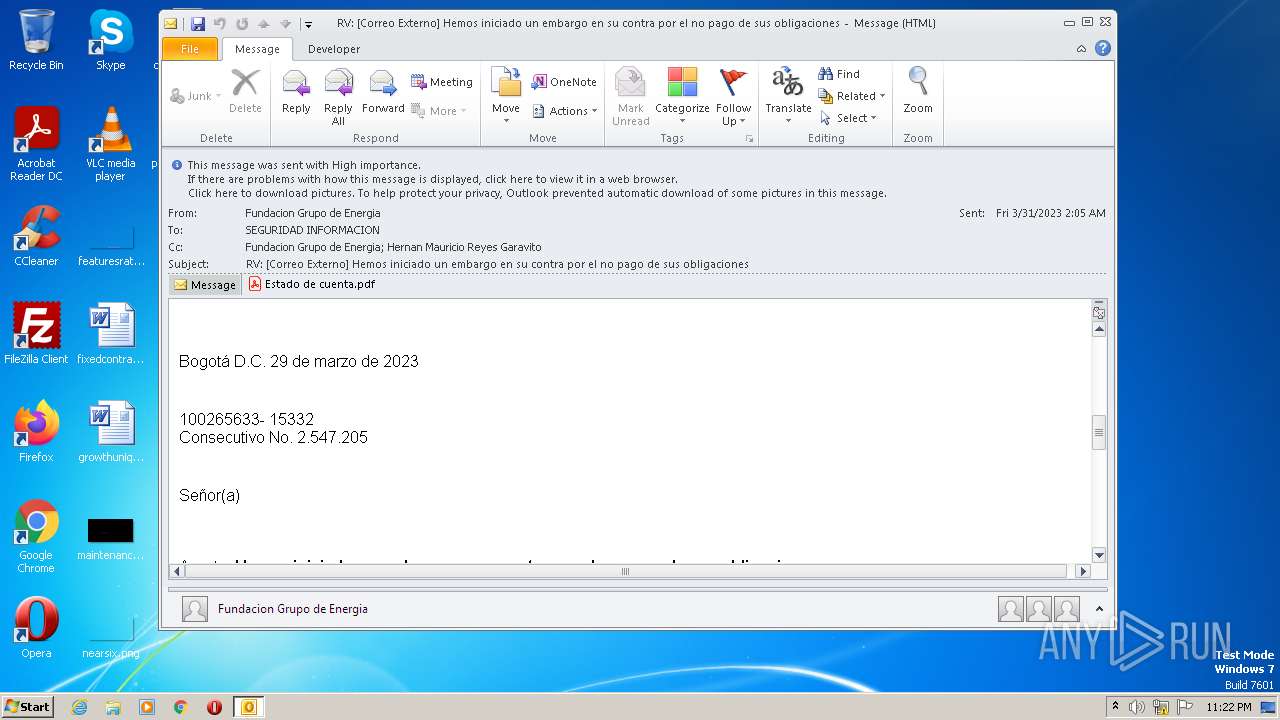
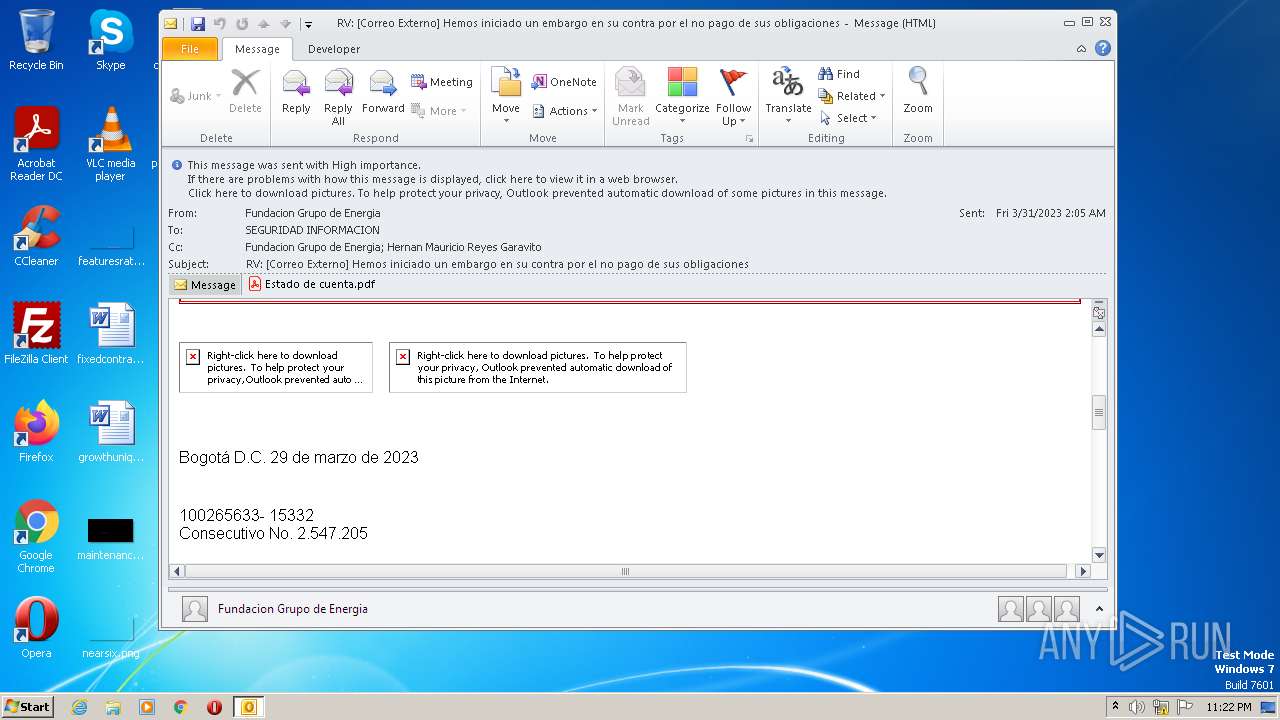
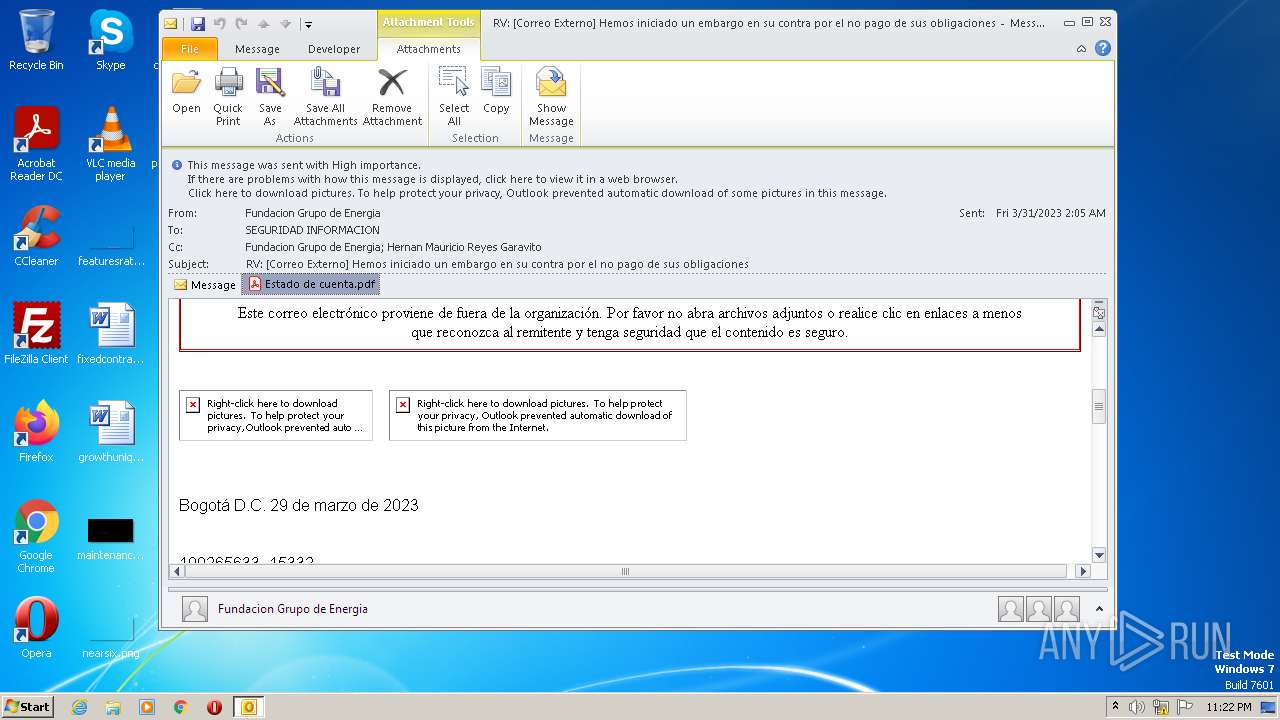
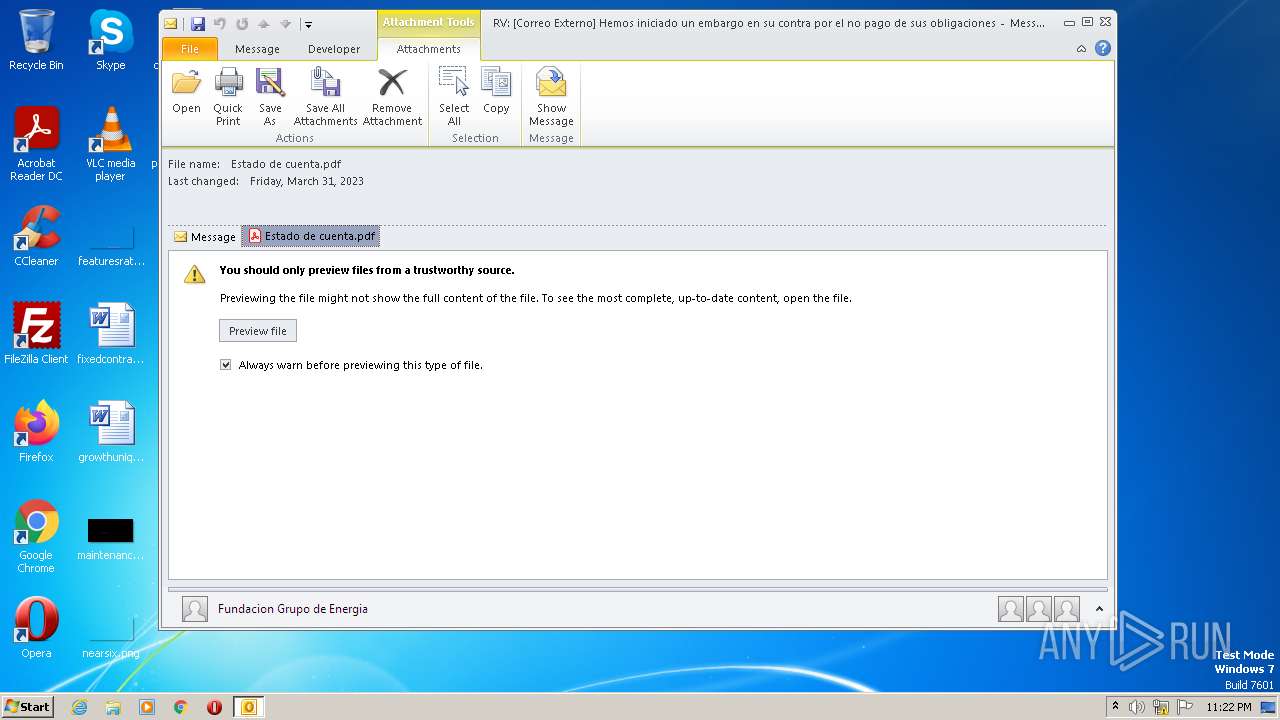
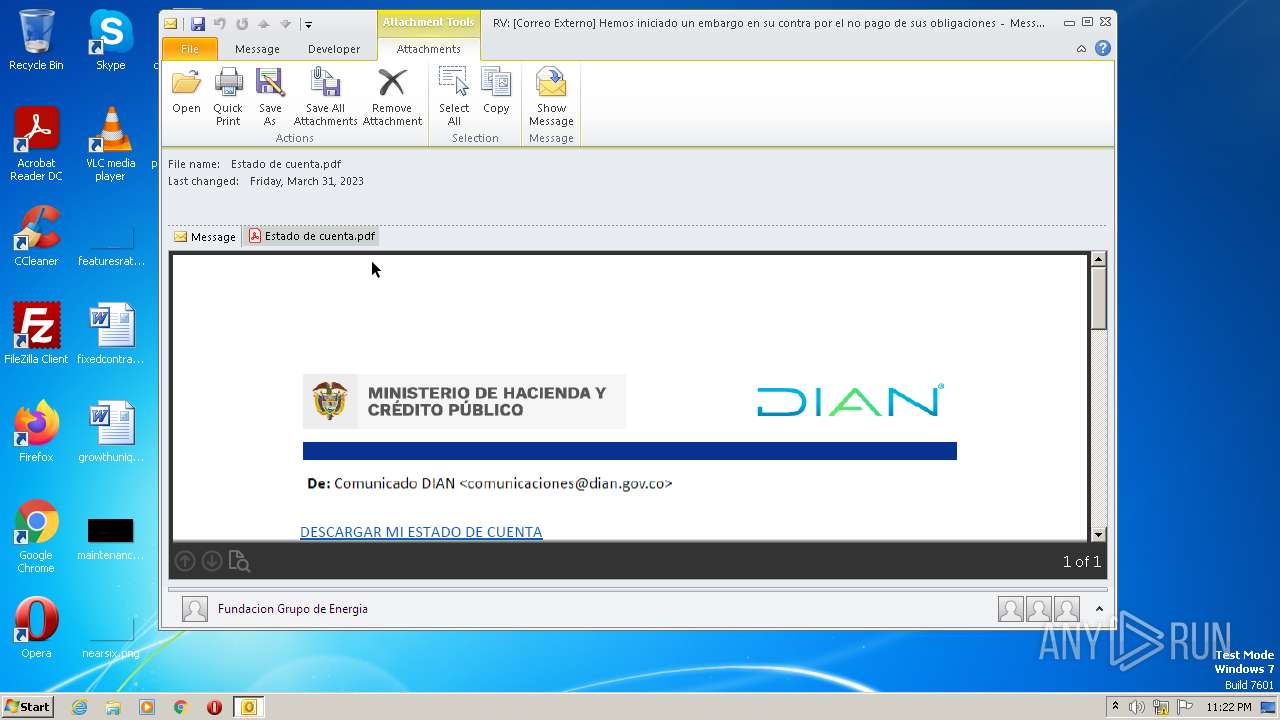
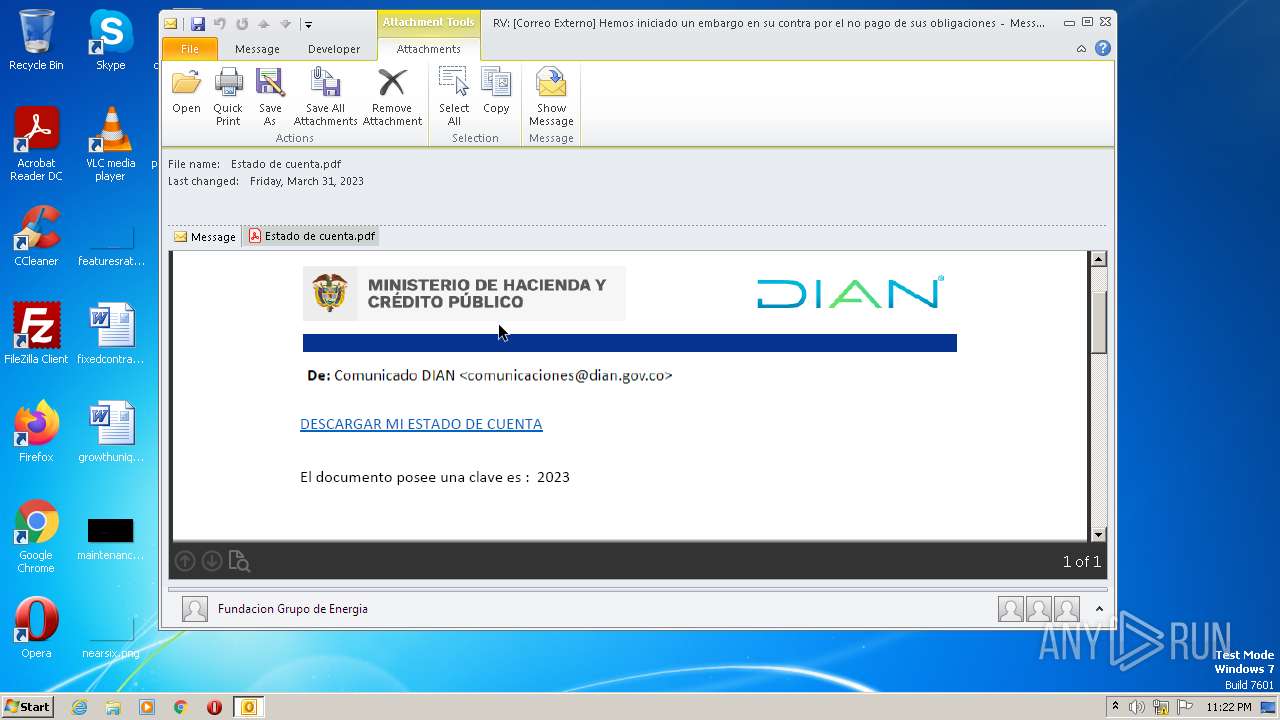
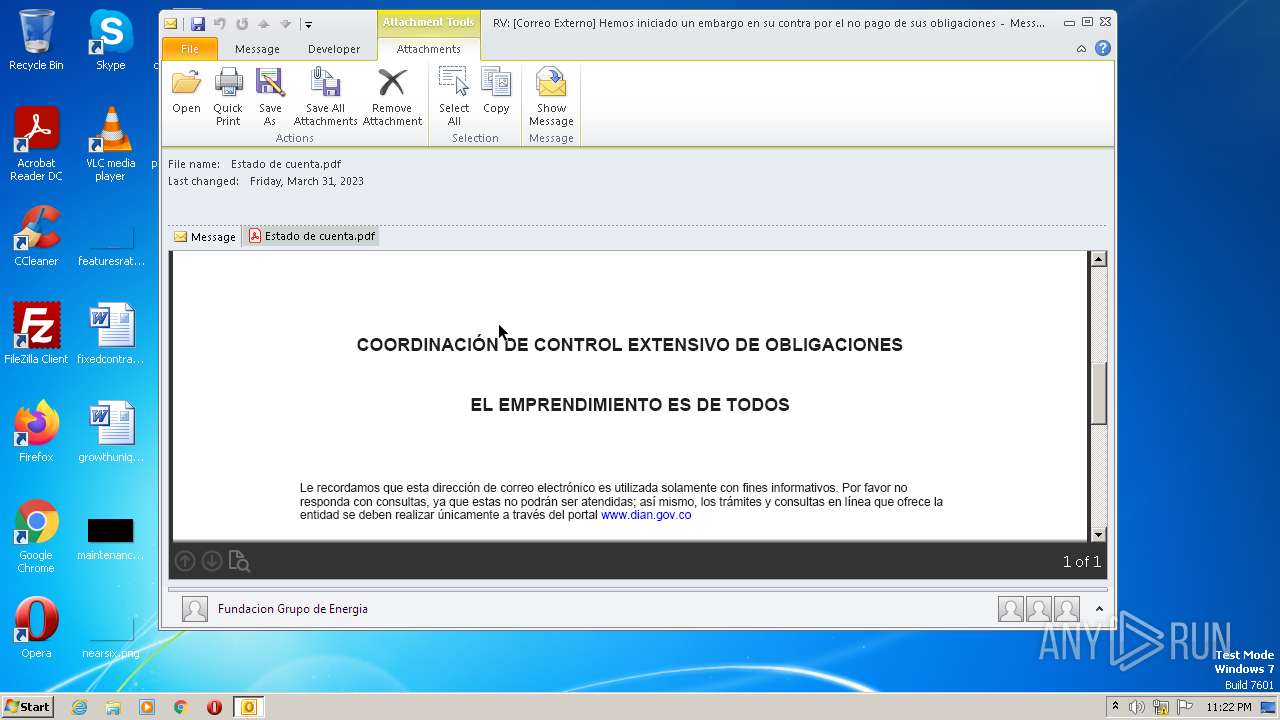
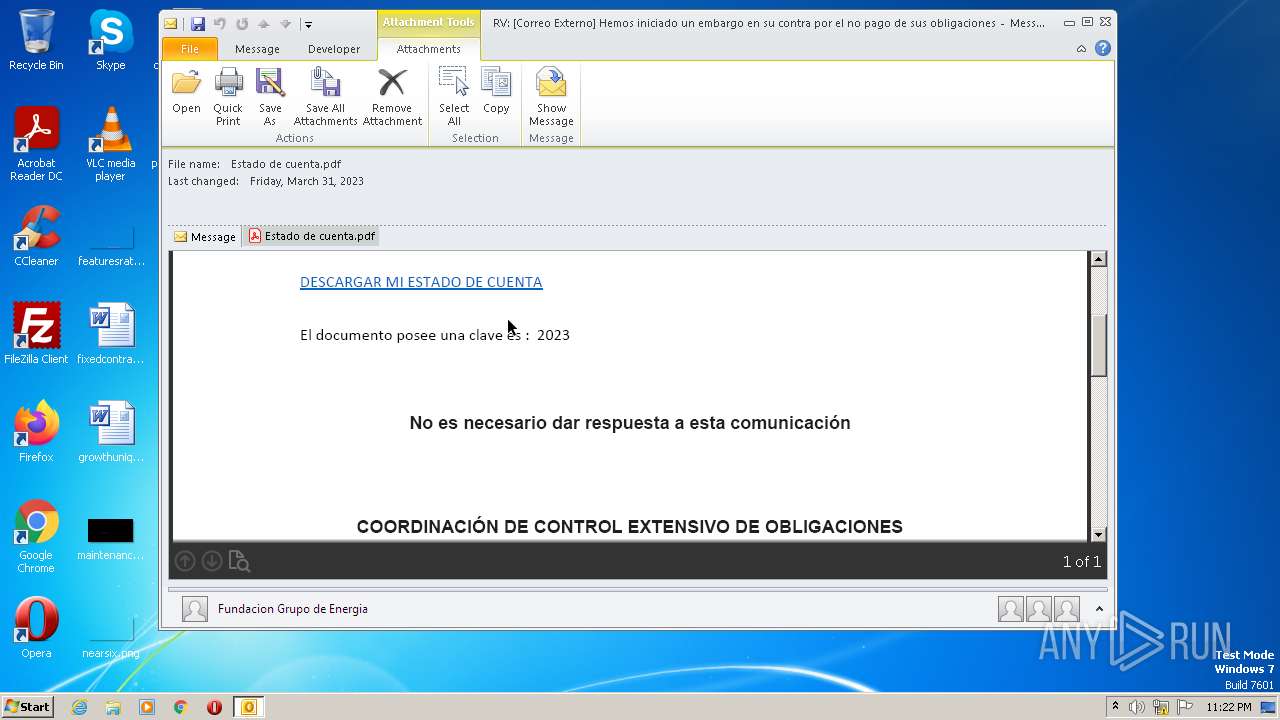
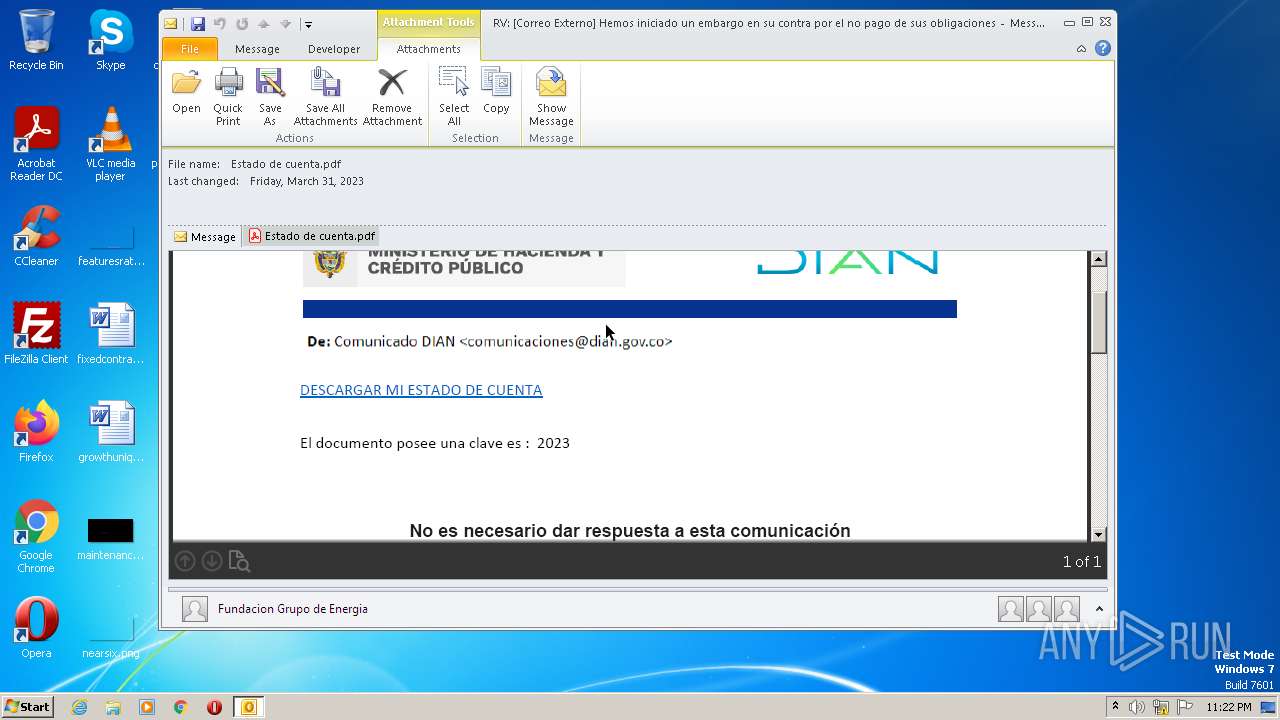
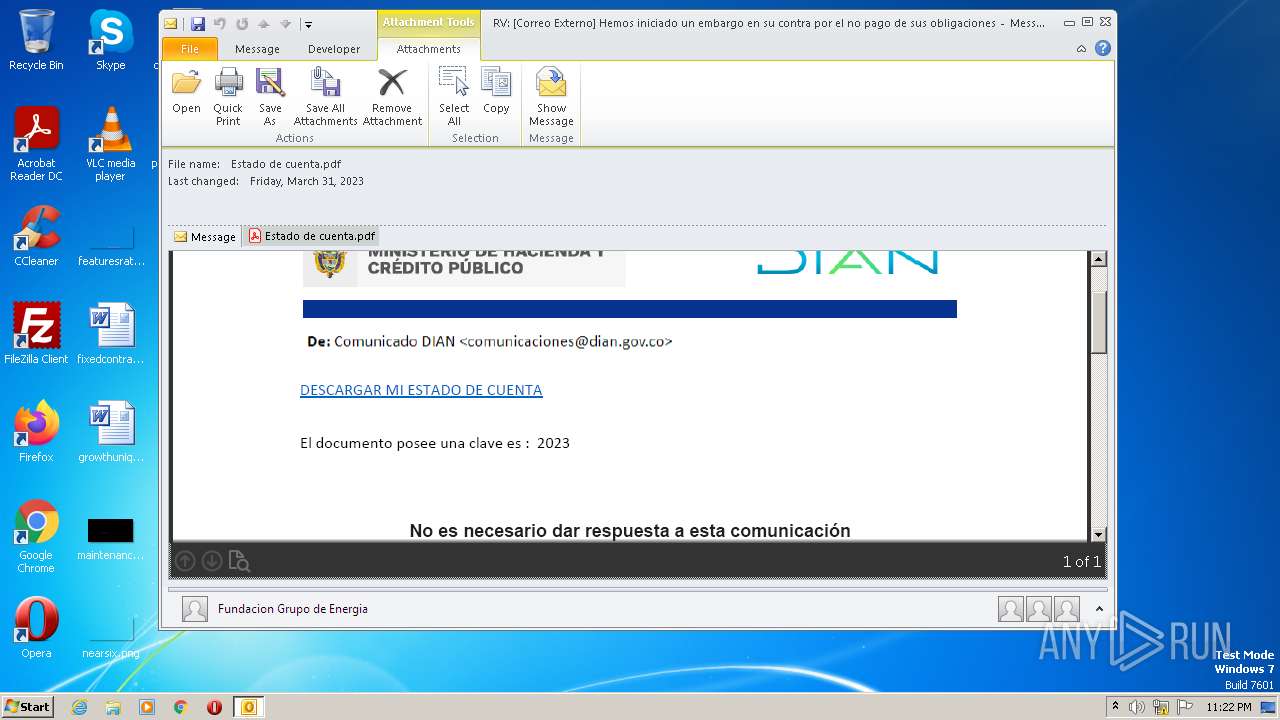
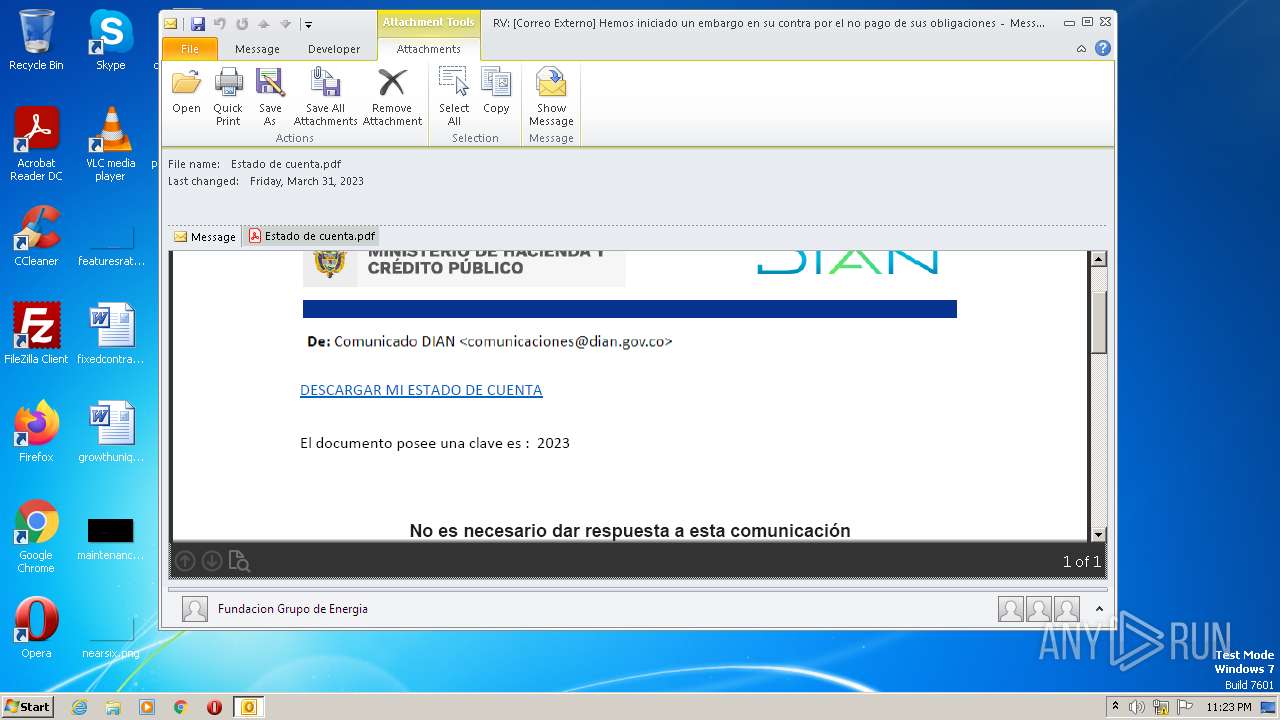
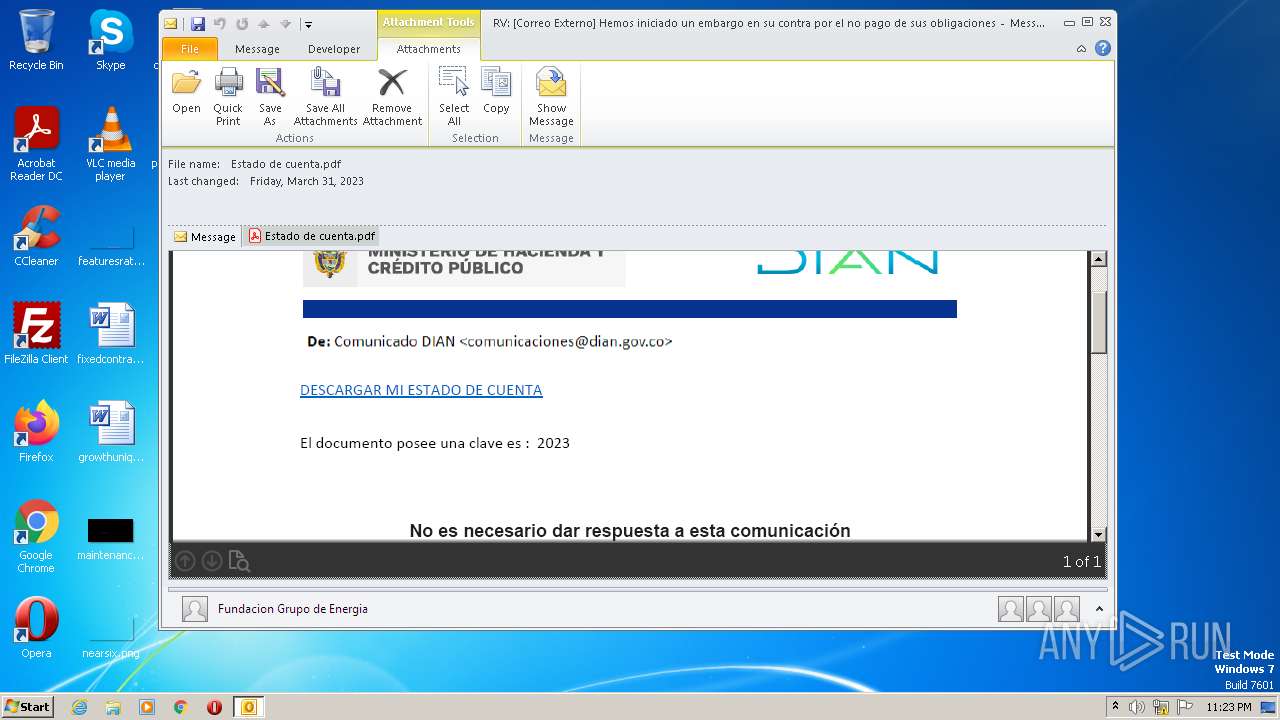
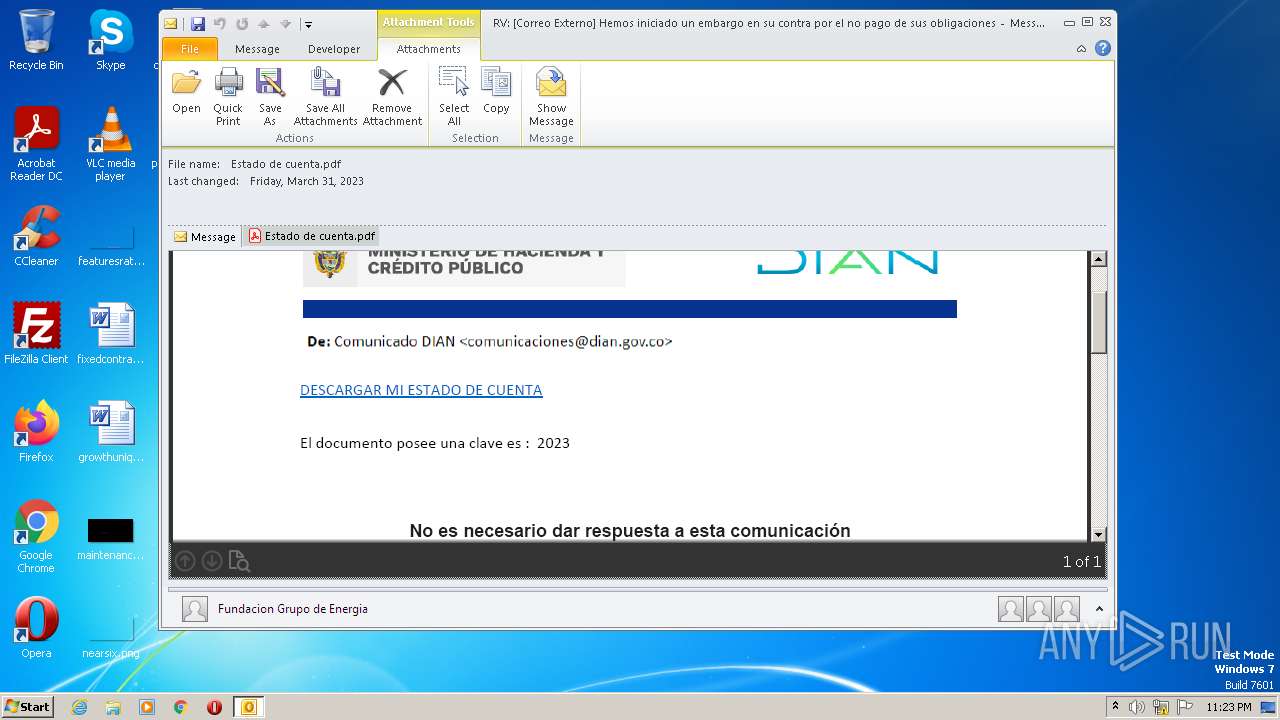
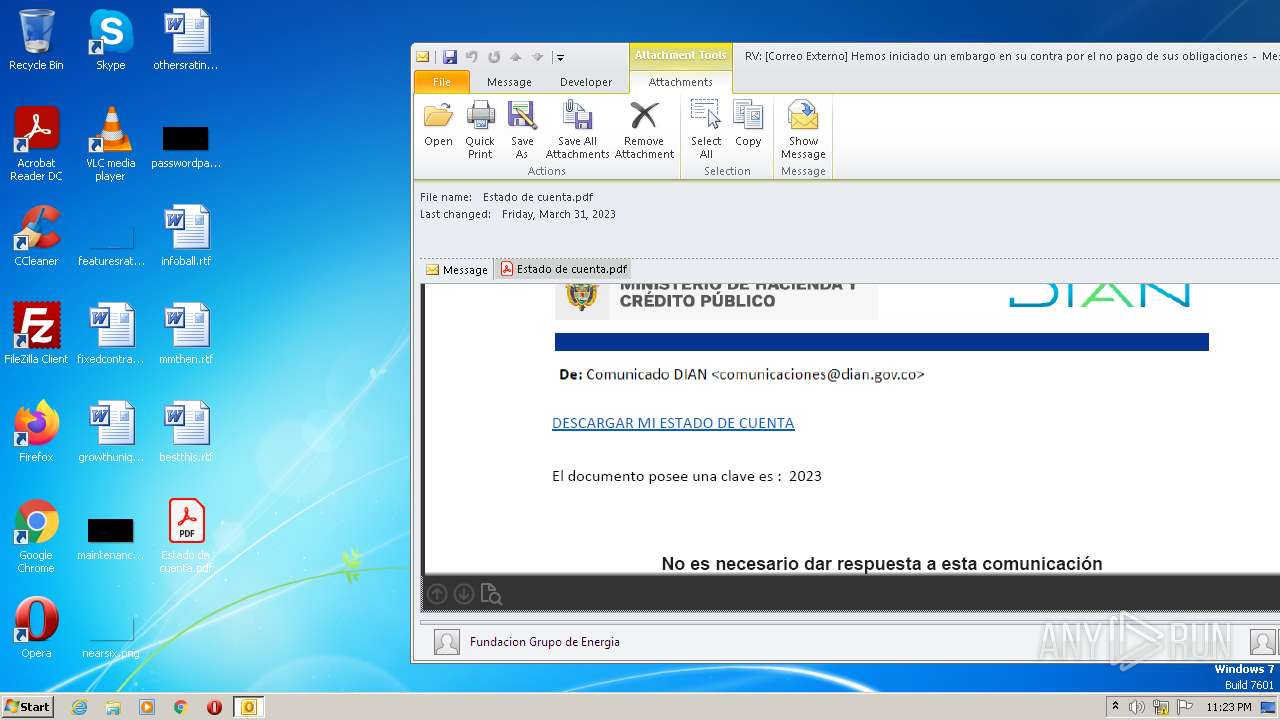
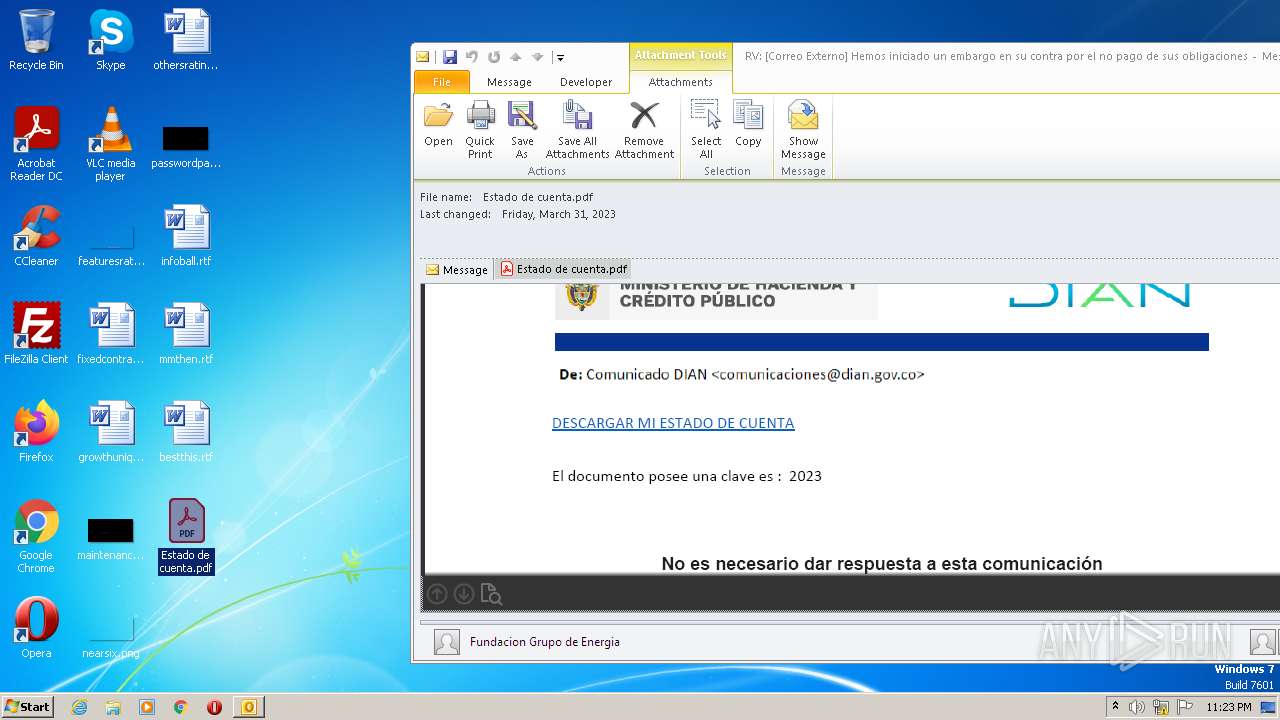
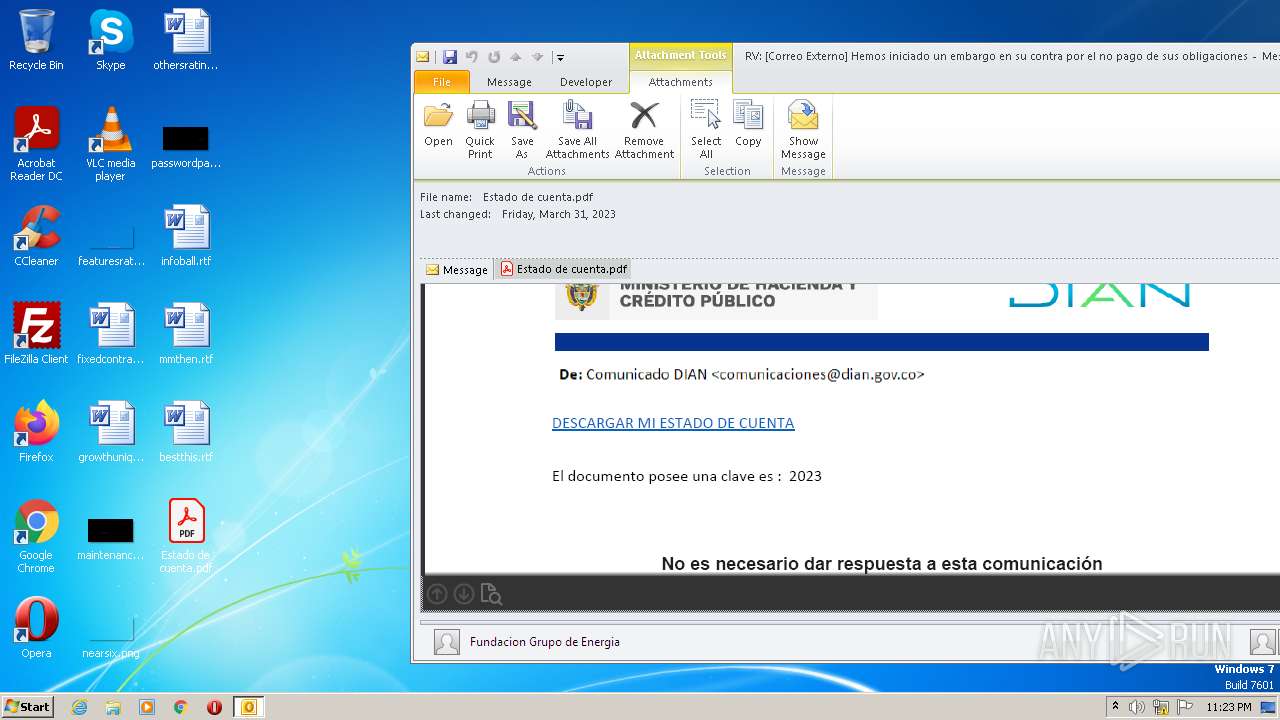
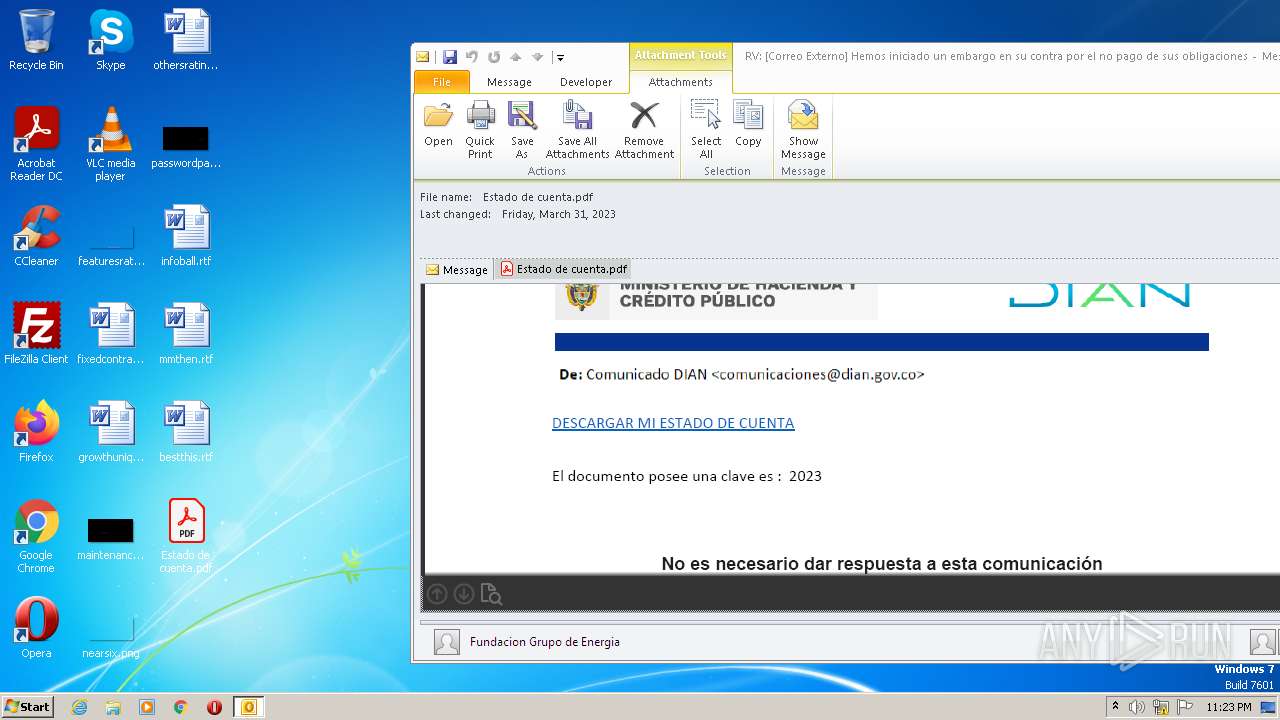
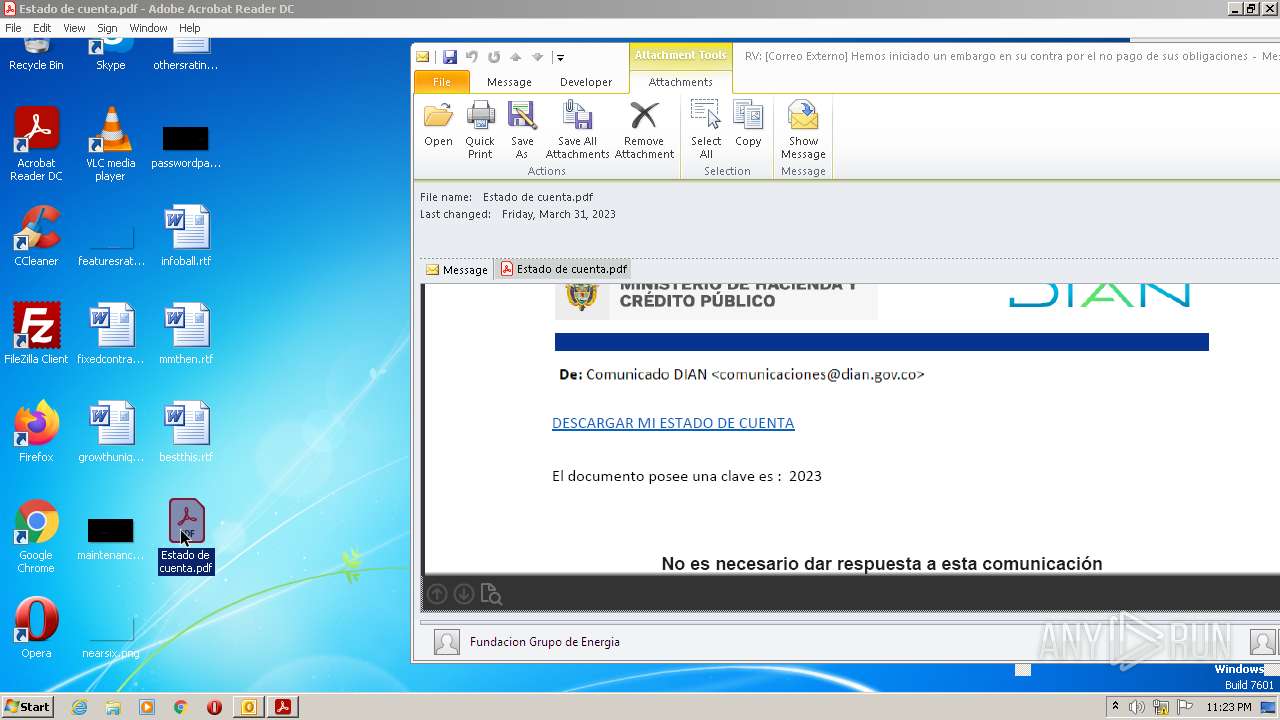
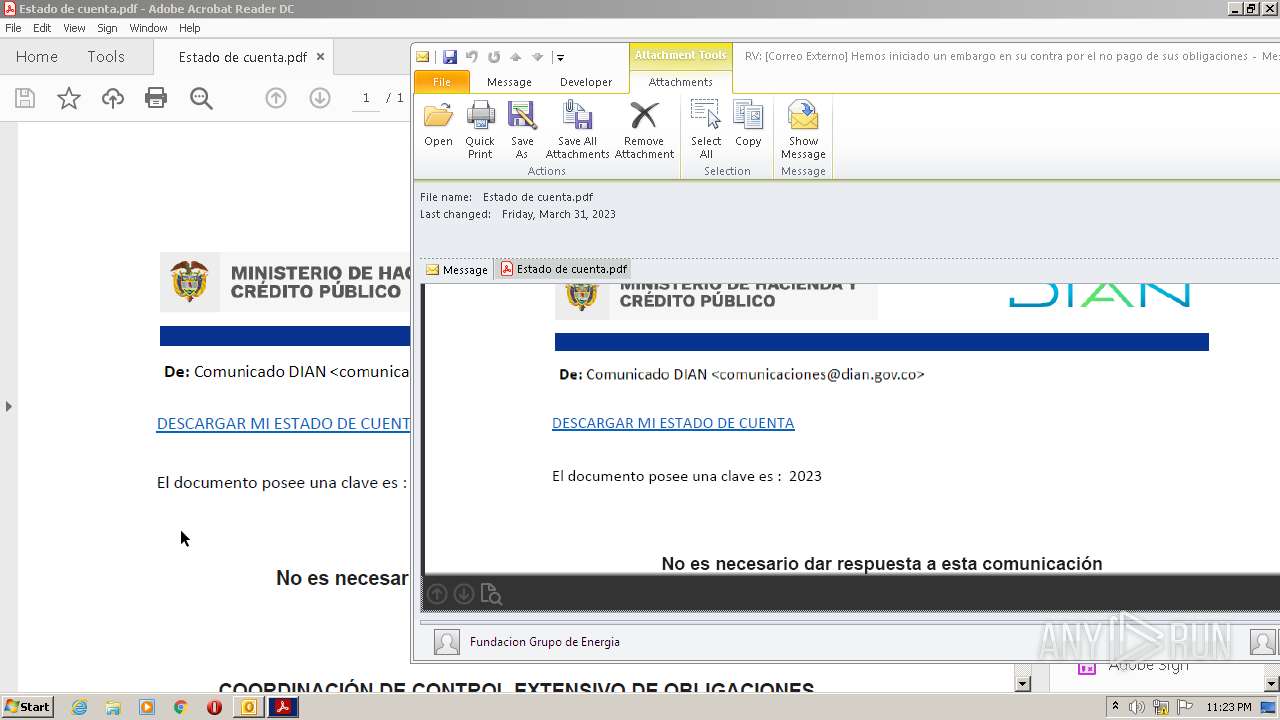
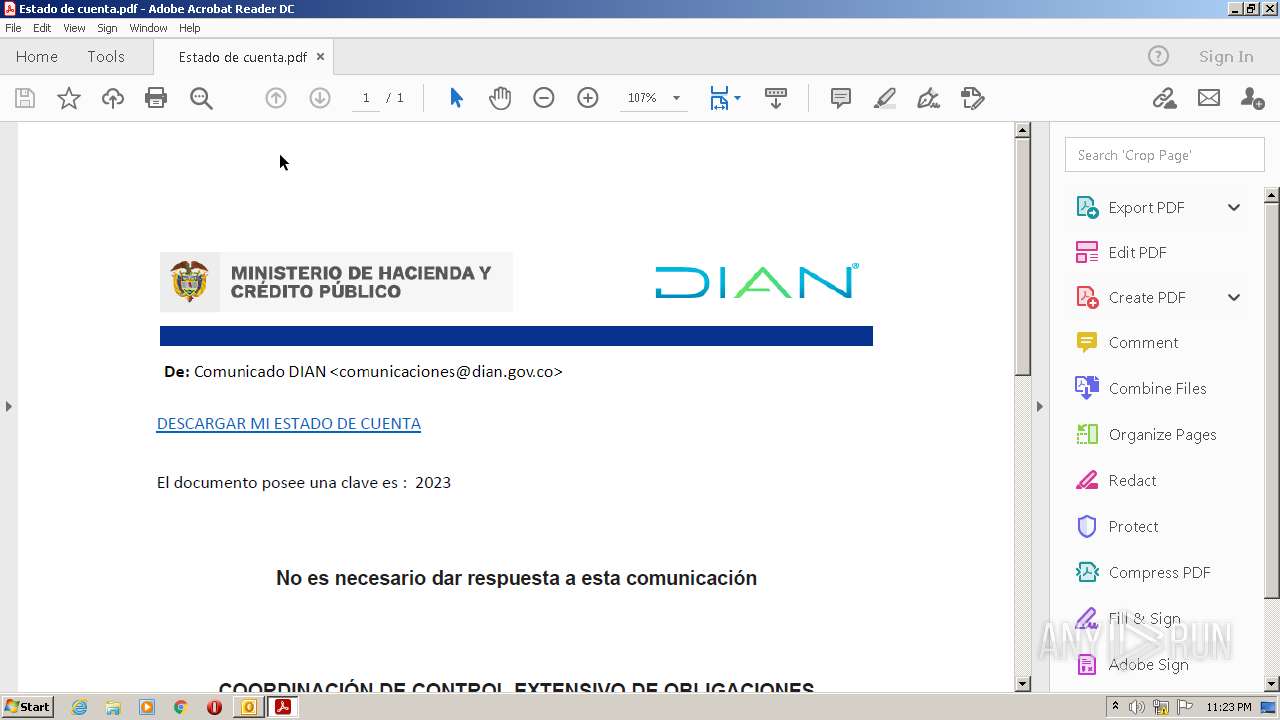
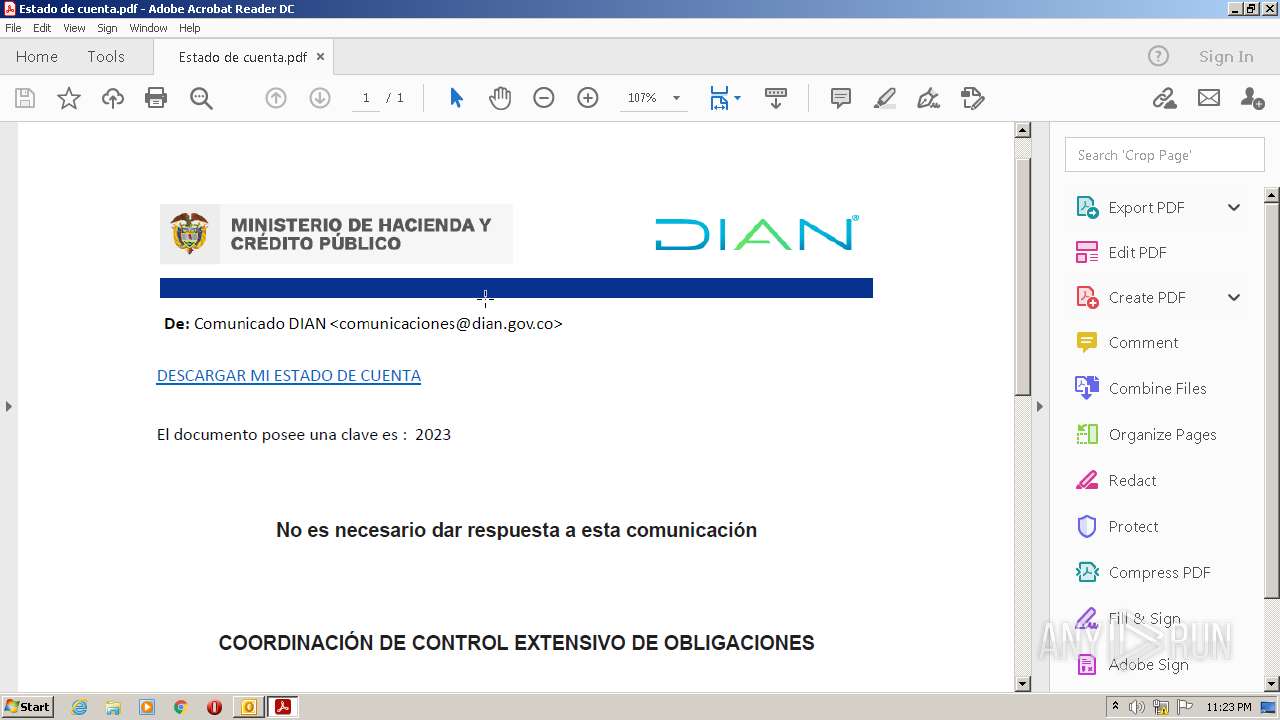
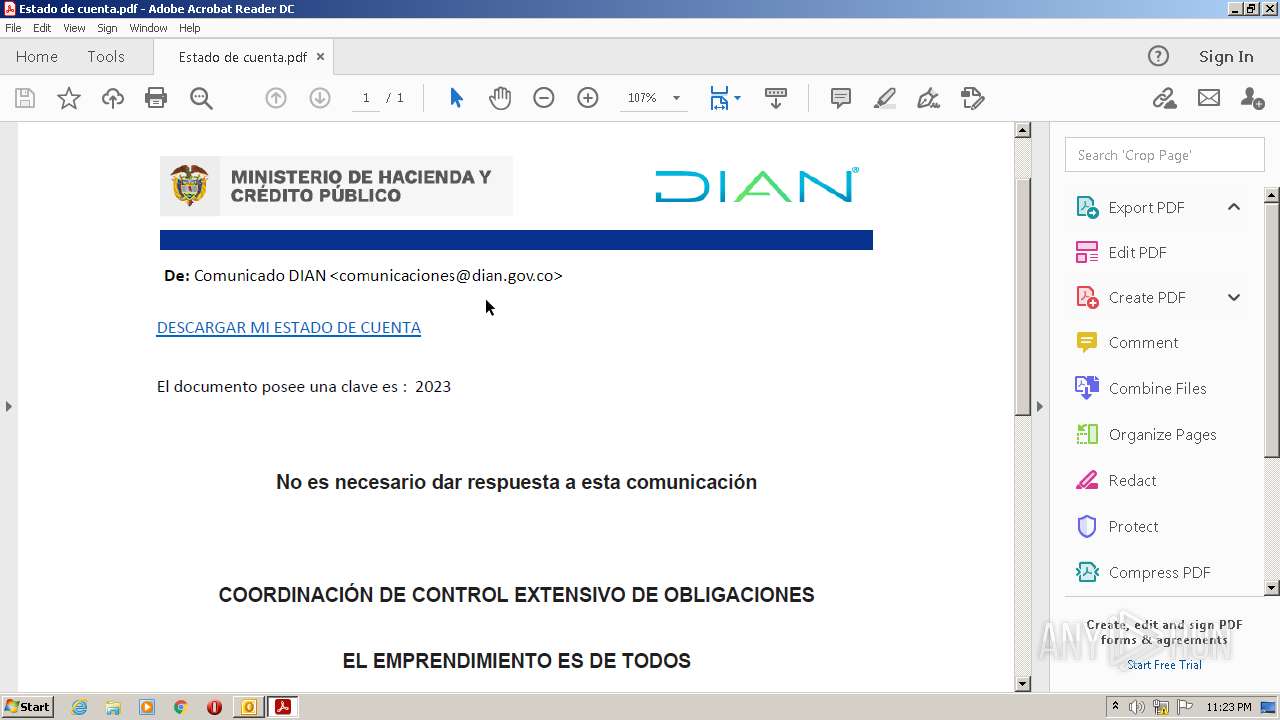
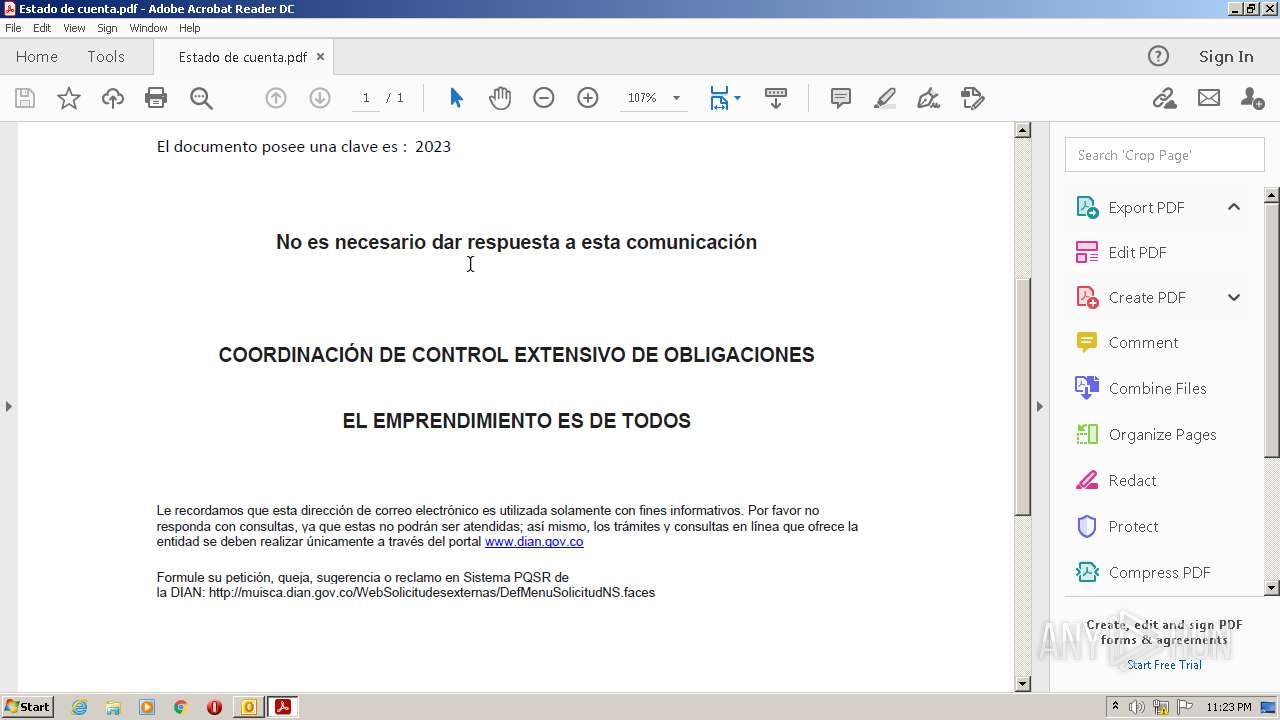
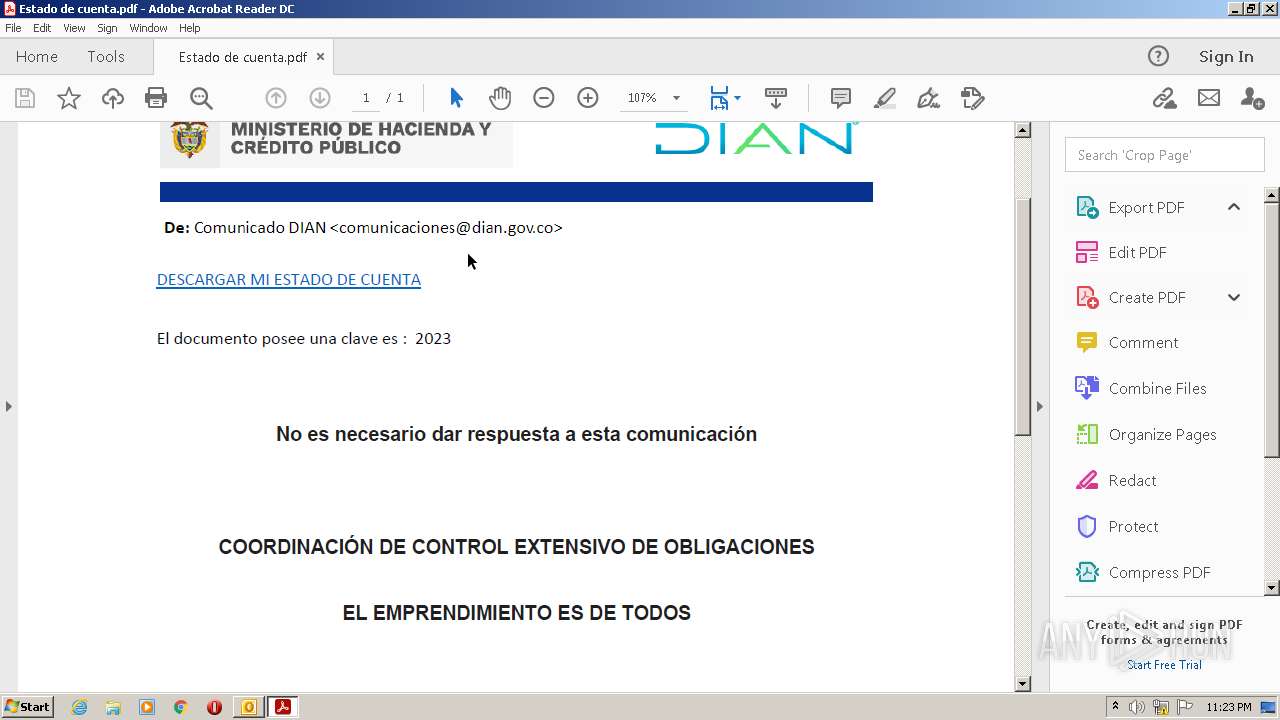
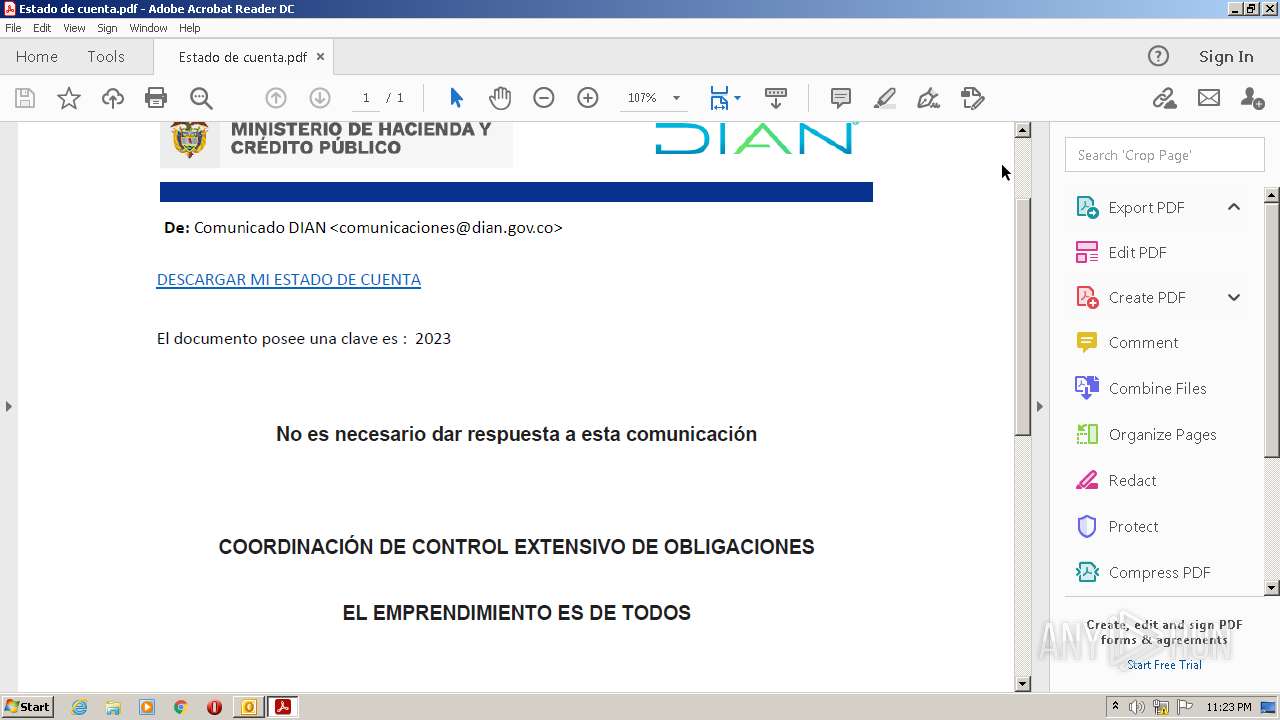
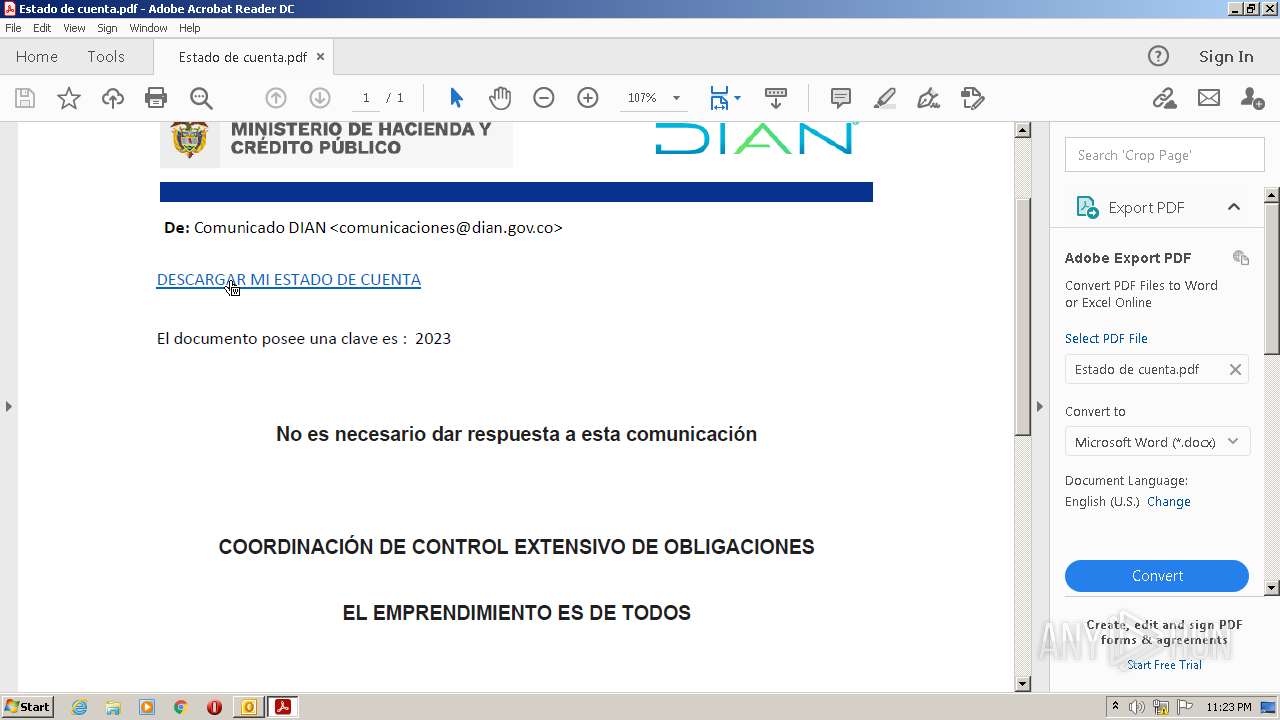
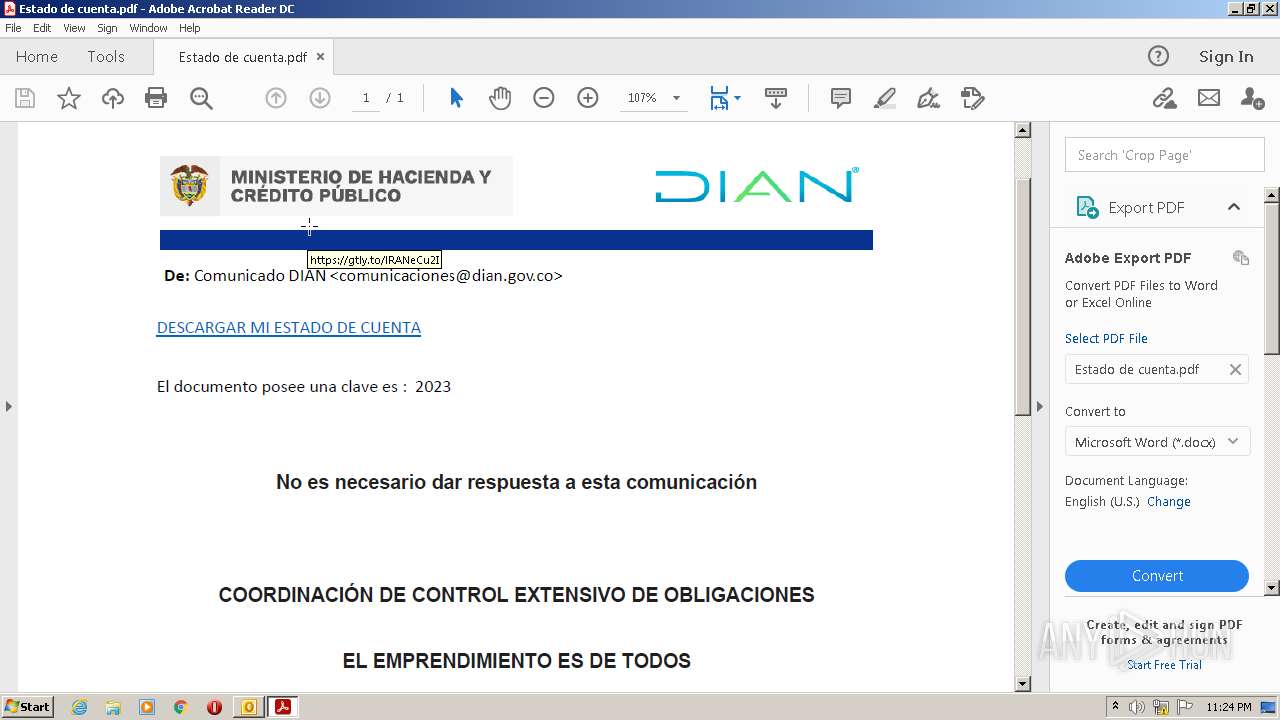
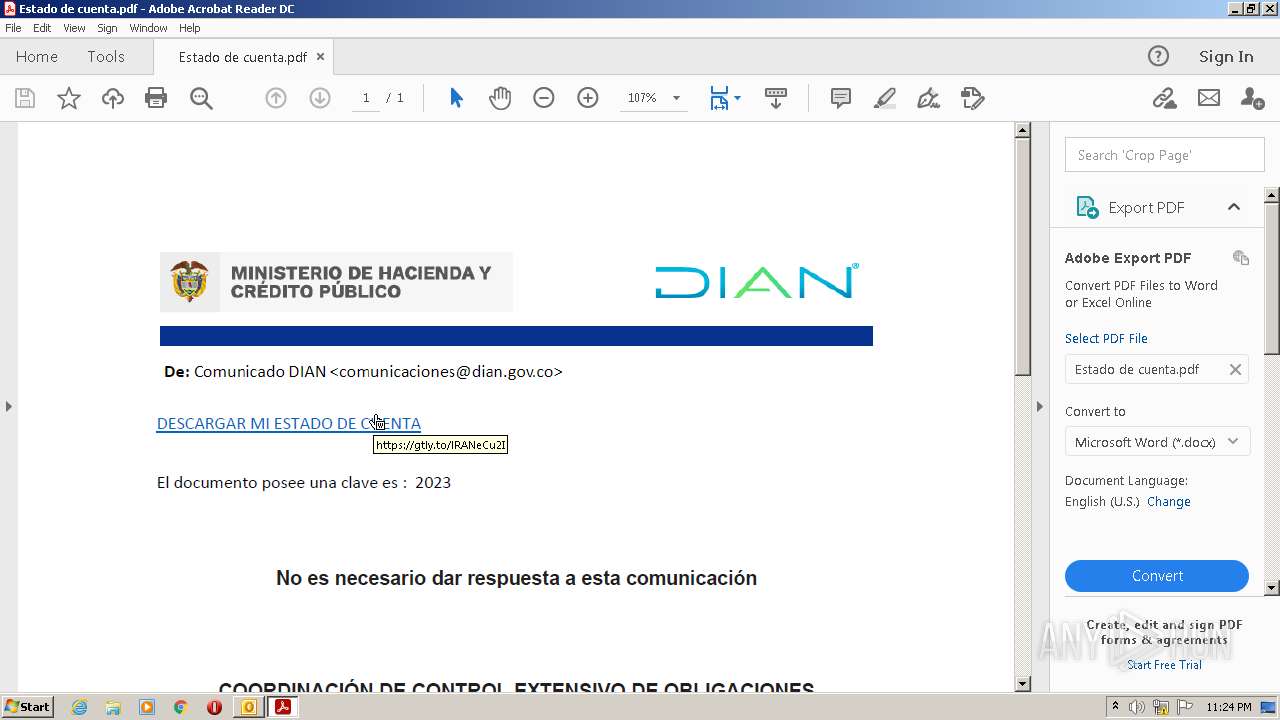
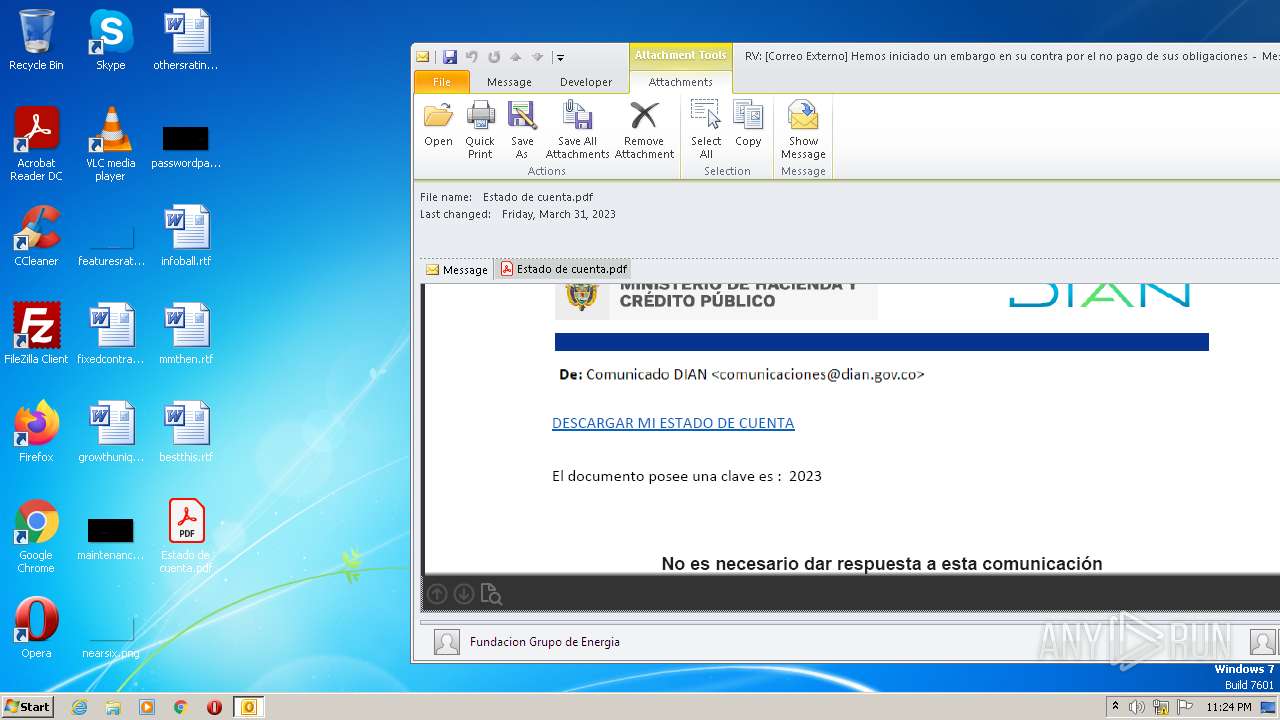
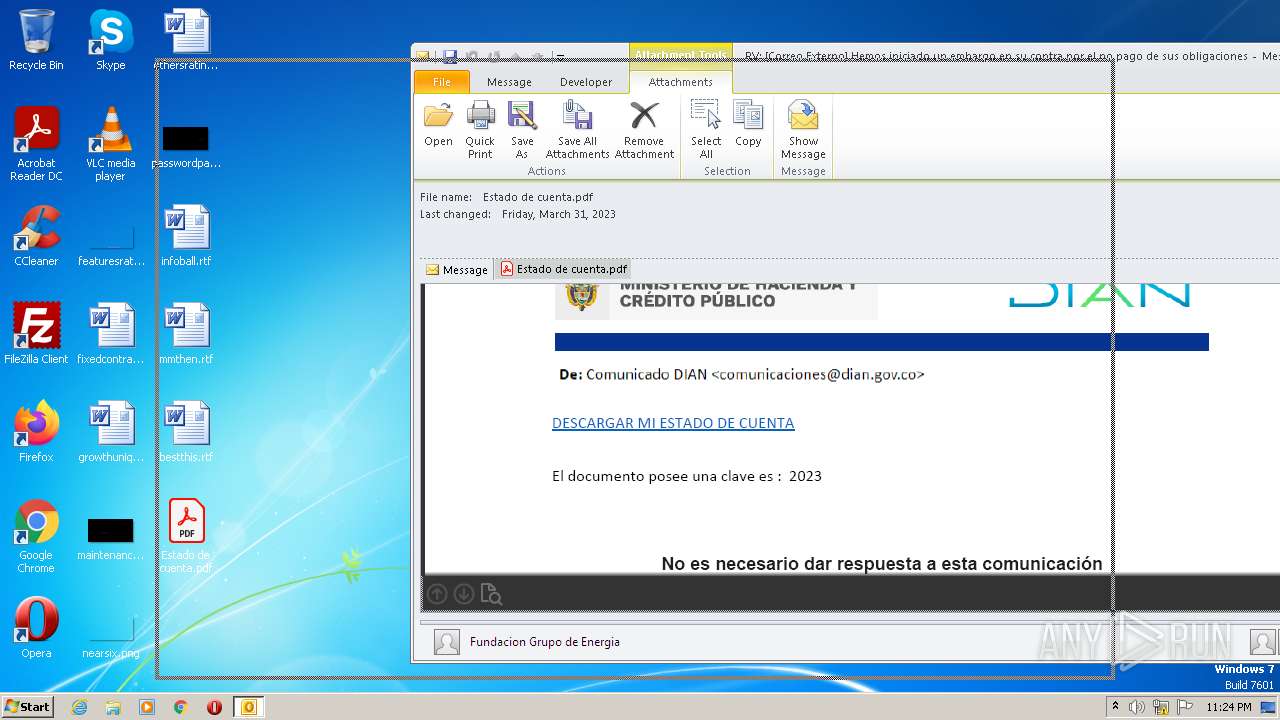
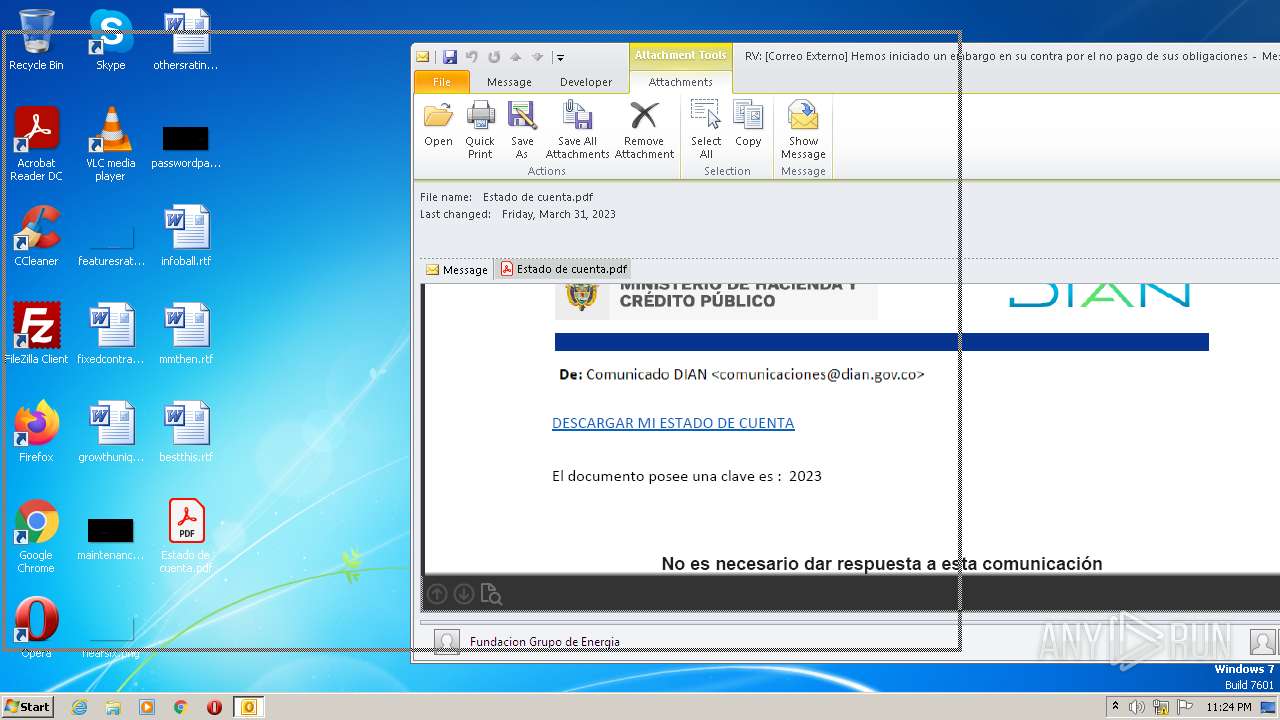
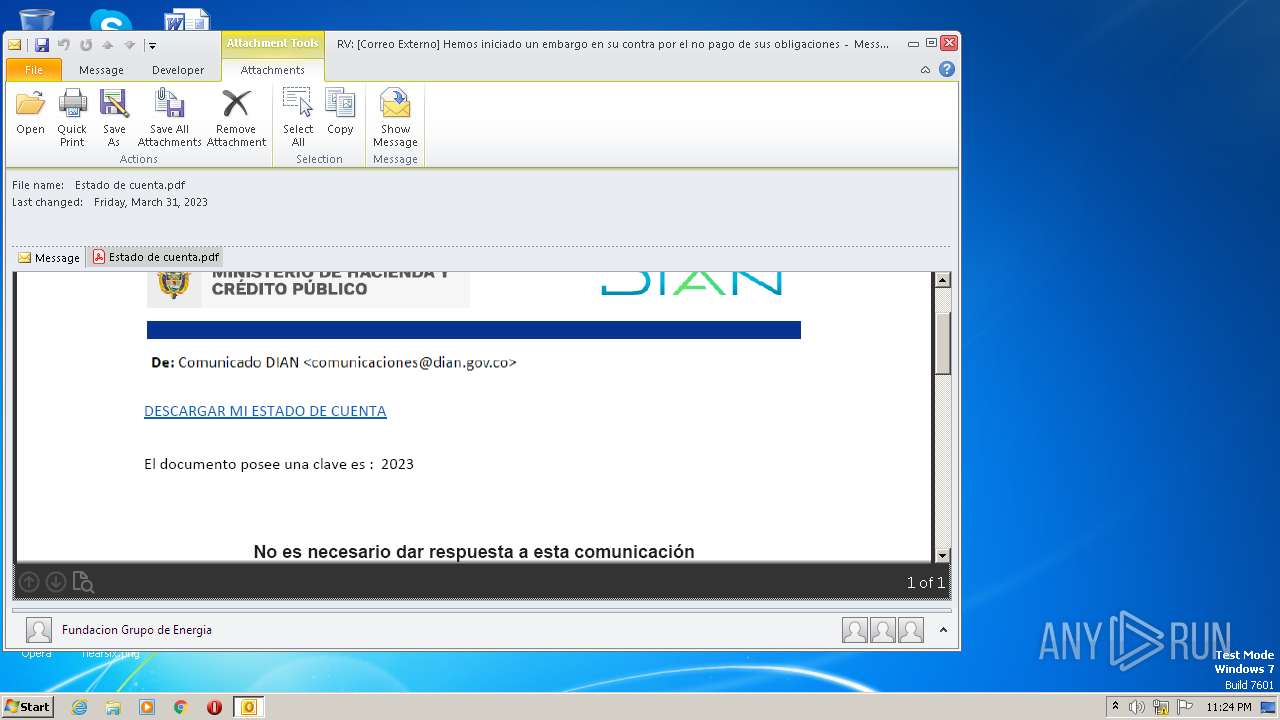
| File name: | RV Correo Externo Hemos iniciado un embargo en su contra por el no pago de sus obligaciones.msg |
| Full analysis: | https://app.any.run/tasks/94611556-1746-4693-931c-fb0d0077603a |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2023, 22:21:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 78196B3475D0BACAFFA8FC7423F98AF6 |
| SHA1: | 28B2397A216BB0098EF51F12D2A91E9A0DB7CD60 |
| SHA256: | 811108D02172325604DBD5140C100357031751F1CFDE2EFE64D6790747693822 |
| SSDEEP: | 3072:9iYJkNXiXkuxsweuxsERVN5JxRGANg/6hHBxzEJwFordR0eRbeRM:61iUuxsduxs4VNHxEr6hYJw/M |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
The process uses the downloaded file
- OUTLOOK.EXE (PID: 1900)
The process checks LSA protection
- prevhost.exe (PID: 3816)
Application launched itself
- iexplore.exe (PID: 3276)
- AcroRd32.exe (PID: 2168)
- RdrCEF.exe (PID: 2376)
- AcroRd32.exe (PID: 2652)
- iexplore.exe (PID: 3952)
Create files in a temporary directory
- iexplore.exe (PID: 3276)
- iexplore.exe (PID: 3952)
Reads Microsoft Office registry keys
- AcroRd32.exe (PID: 3692)
Manual execution by a user
- AcroRd32.exe (PID: 2652)
Checks supported languages
- Reader_sl.exe (PID: 2104)
Executable content was dropped or overwritten
- AdobeARM.exe (PID: 2012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
65
Monitored processes
20
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 692 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer /b /id 3816_1674420249 /if pdfshell_prev87965de6-e819-47e4-ad05-d102b0b6e78e | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1628 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1156,887723094690653642,1335540573606189655,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=13991860037180705761 --mojo-platform-channel-handle=1228 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1900 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\RV Correo Externo Hemos iniciado un embargo en su contra por el no pago de sus obligaciones.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2012 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:20.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Inc. Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.39.9311 Modules
| |||||||||||||||
| 2104 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 20.12.20041.394260 Modules
| |||||||||||||||
| 2112 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1156,887723094690653642,1335540573606189655,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=3520258849291178575 --mojo-platform-channel-handle=1232 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2168 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" /b /id 3816_1674420249 /if pdfshell_prev87965de6-e819-47e4-ad05-d102b0b6e78e | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | prevhost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2376 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 3221225547 Version: 20.13.20064.405839 Modules
| |||||||||||||||
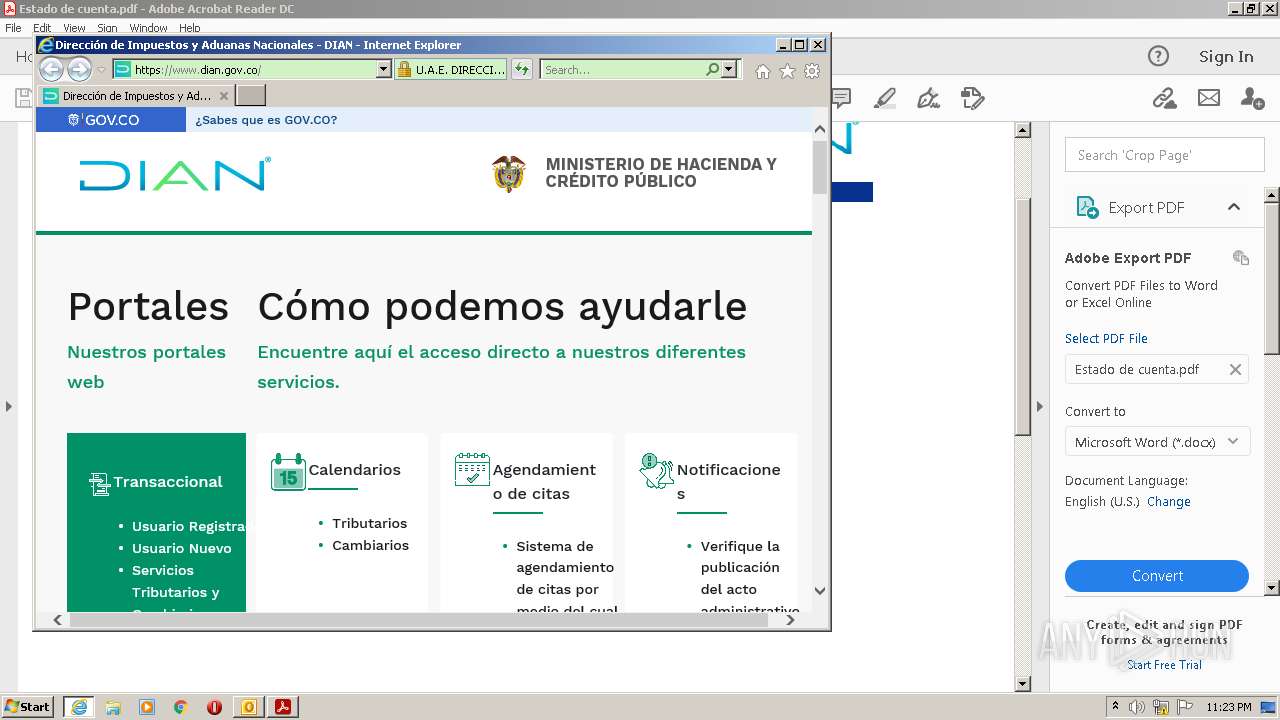
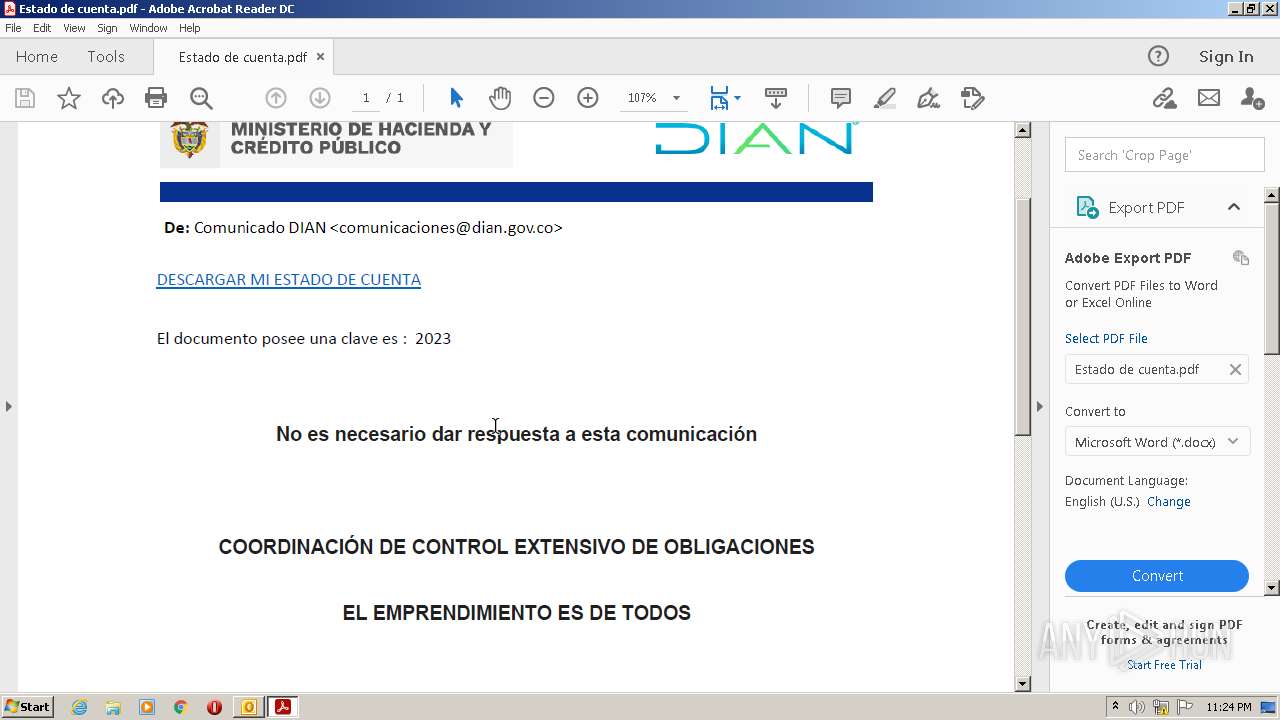
| 2652 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\Desktop\Estado de cuenta.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 3064 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3276 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
95 438
Read events
93 964
Write events
1 408
Delete events
66
Modification events
| (PID) Process: | (1900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (1900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (1900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (1900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (1900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (1900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (1900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (1900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (1900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (1900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
2
Suspicious files
376
Text files
156
Unknown types
72
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1900 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRF628.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1900 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 1900 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 3064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\2F23D0F5E4D72862517E1CB26A329742_F6FACC49395CFA949BCE851E73323C49 | der | |
MD5:— | SHA256:— | |||
| 1900 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2F23D0F5E4D72862517E1CB26A329742_F6FACC49395CFA949BCE851E73323C49 | binary | |
MD5:— | SHA256:— | |||
| 3064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:— | SHA256:— | |||
| 3064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:— | SHA256:— | |||
| 3064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\69FA0D4189D46E6E0AB54D22F26BC8CB_8D9C529D1950102E68D22D6905CDB050 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
66
DNS requests
35
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1900 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
3064 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://status.geotrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTIyCPRUzvKHRw7iRE1lF%2BfcLu%2FjgQUypJnUmHervy6Iit%2FHIdMJftvmVgCEA9u391J5f%2BCd3cvSR%2Fwk4I%3D | US | der | 471 b | whitelisted |
3064 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAGewca9P1l7sgwzOOVR2Hc%3D | US | der | 471 b | whitelisted |
3064 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/s/gts1d4/r4lZfIcNCVI/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSMBFDqU0NJQdZdEGU3bkhj0FoRrQQUJeIYDrJXkZQq5dRdhpCD3lOzuJICECDHFgbtVu2JEH4p6l8%2FWWs%3D | US | der | 471 b | whitelisted |
3064 | iexplore.exe | GET | 200 | 8.241.11.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ed69952bc2d0a33e | US | compressed | 4.70 Kb | whitelisted |
3276 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
3064 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQD%2FB2zZ7cy1JAocIdUzcD8Q | US | der | 472 b | whitelisted |
3064 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGpqxJbBk7c3CvIUCwl%2FKLk%3D | US | der | 471 b | whitelisted |
3064 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCXh%2B17FzWzVgrisikgAGpW | US | der | 472 b | whitelisted |
3064 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCFF8LsnHpqFgoBiSwjCX0g | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3064 | iexplore.exe | 142.250.186.168:443 | www.googletagmanager.com | GOOGLE | US | suspicious |
3276 | iexplore.exe | 204.79.197.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3064 | iexplore.exe | 142.250.186.131:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
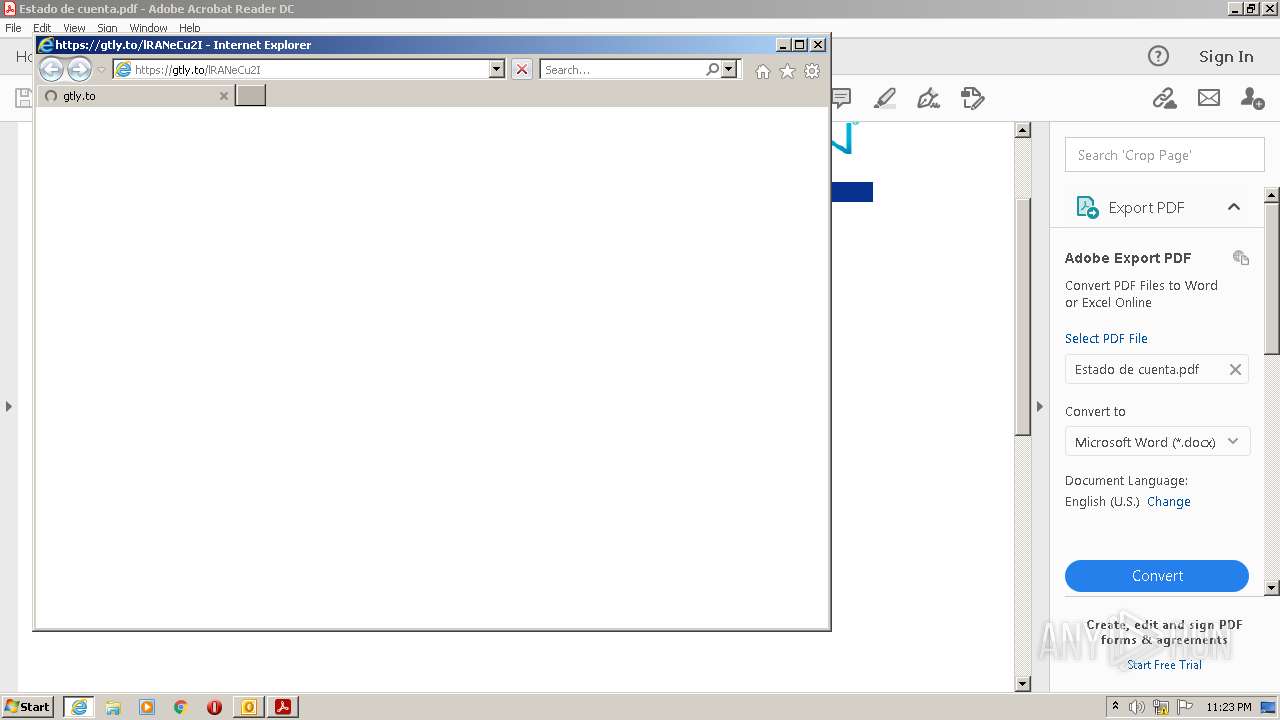
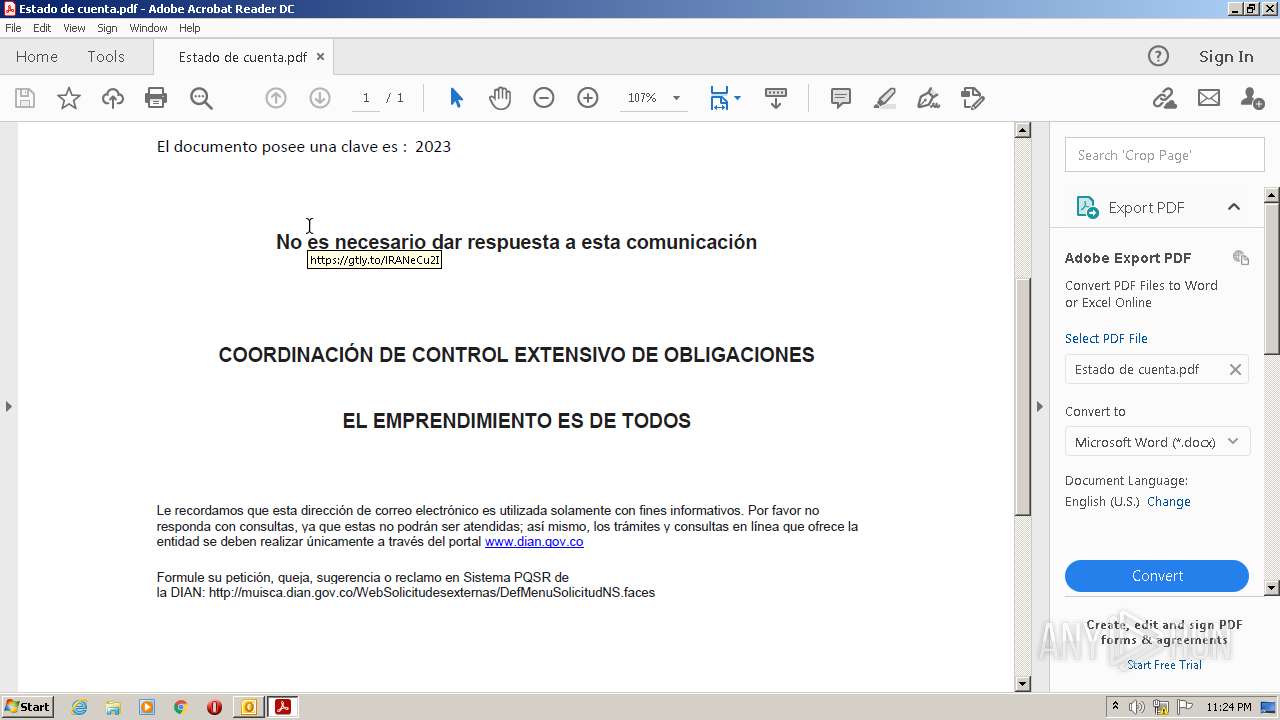
3064 | iexplore.exe | 34.107.207.124:443 | gtly.to | GOOGLE | US | suspicious |
3064 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3064 | iexplore.exe | 8.241.11.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
3064 | iexplore.exe | 104.47.58.28:443 | nam10.safelinks.protection.outlook.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | suspicious |
1900 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3276 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3064 | iexplore.exe | 142.250.185.78:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
nam10.safelinks.protection.outlook.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
gtly.to |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
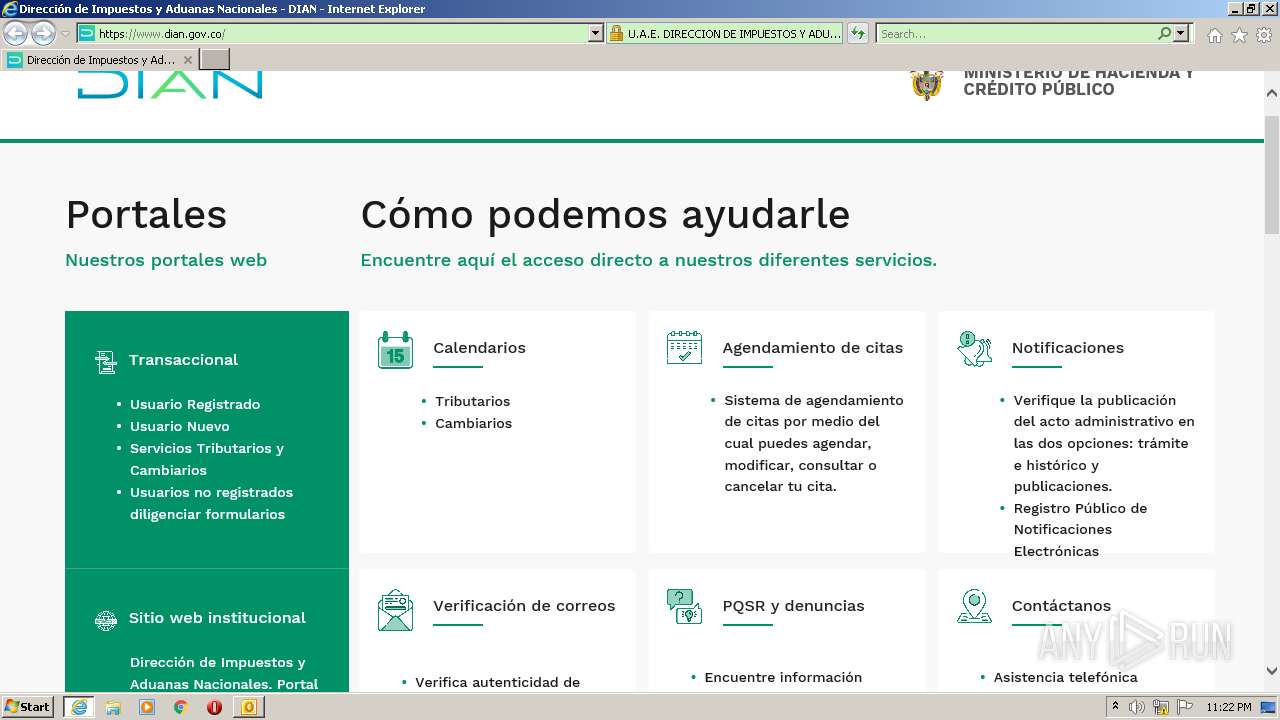
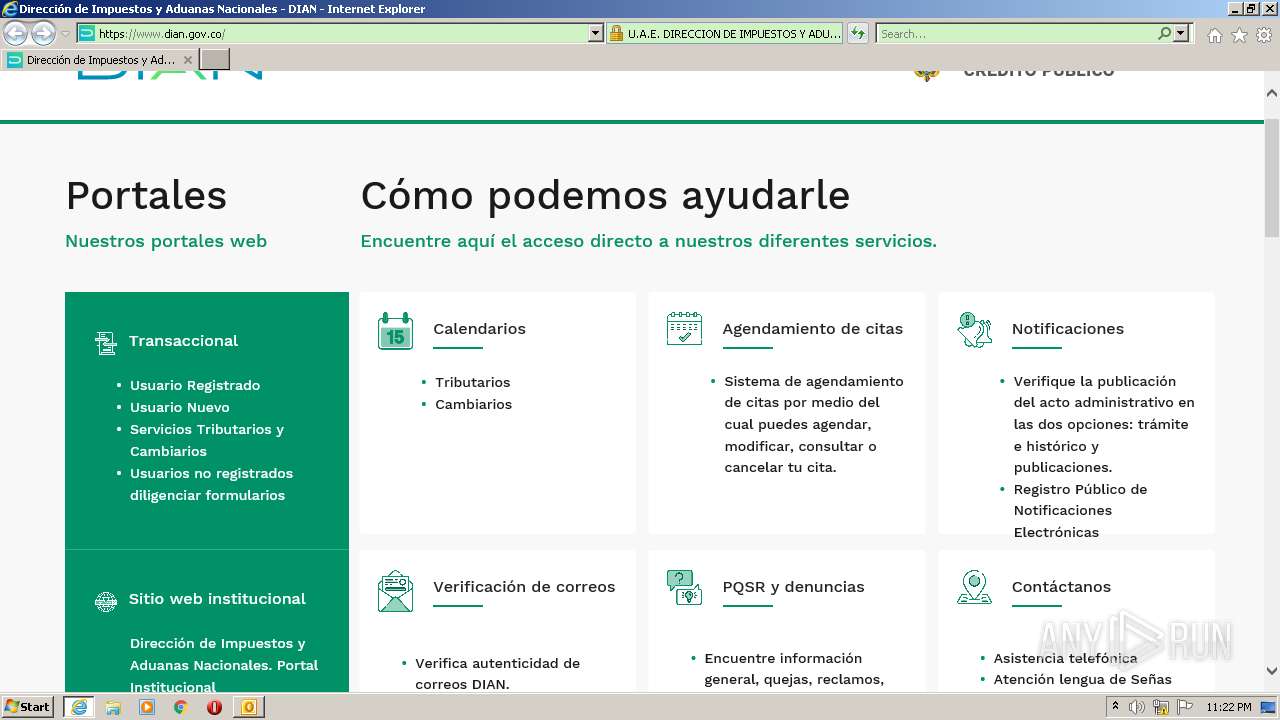
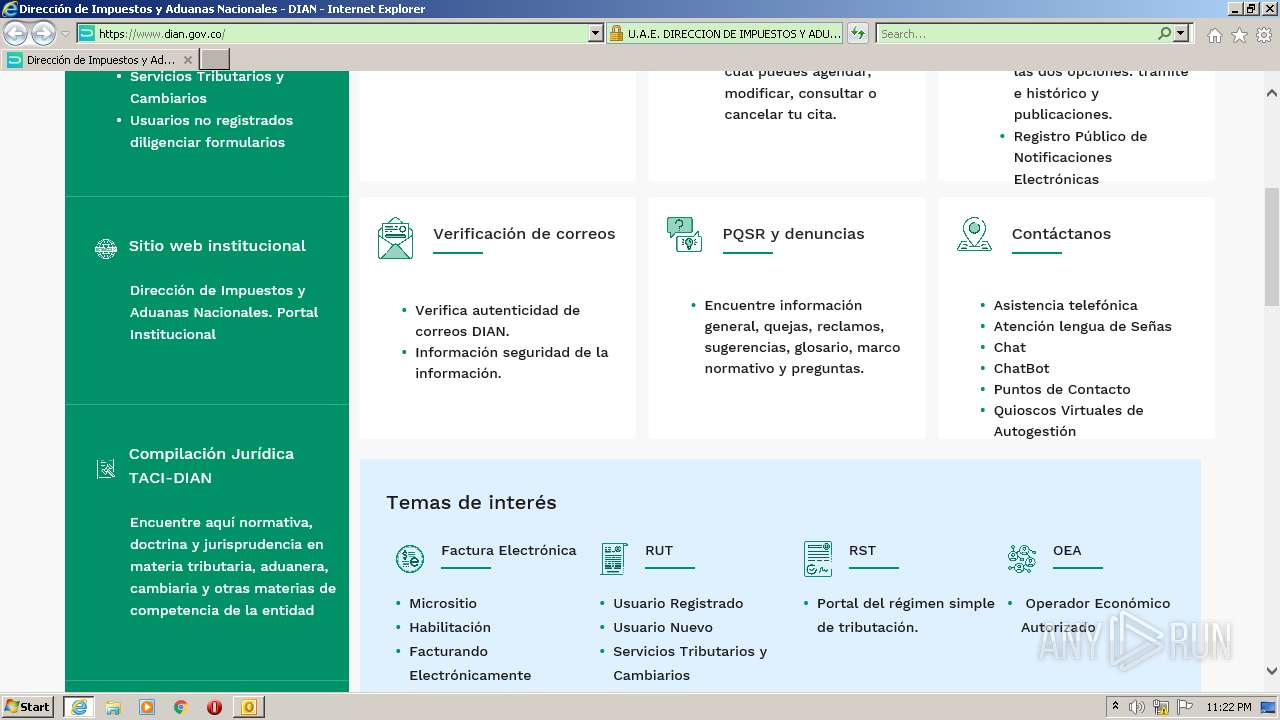
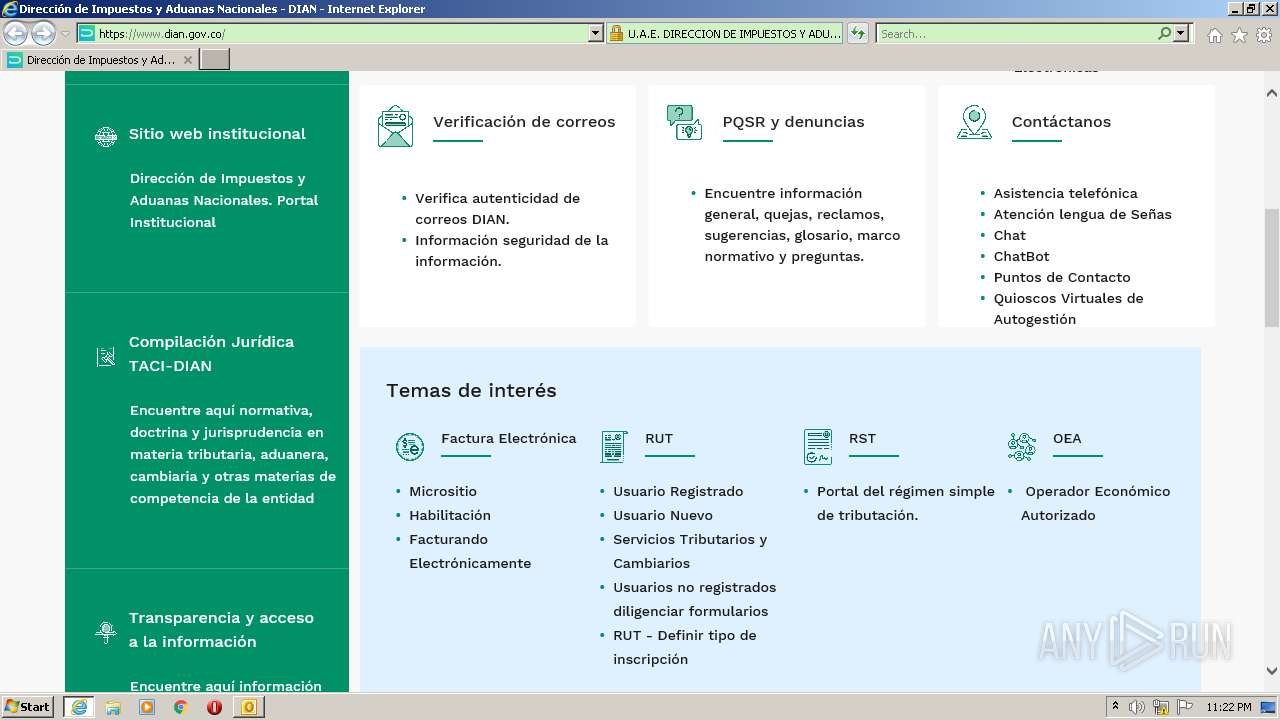
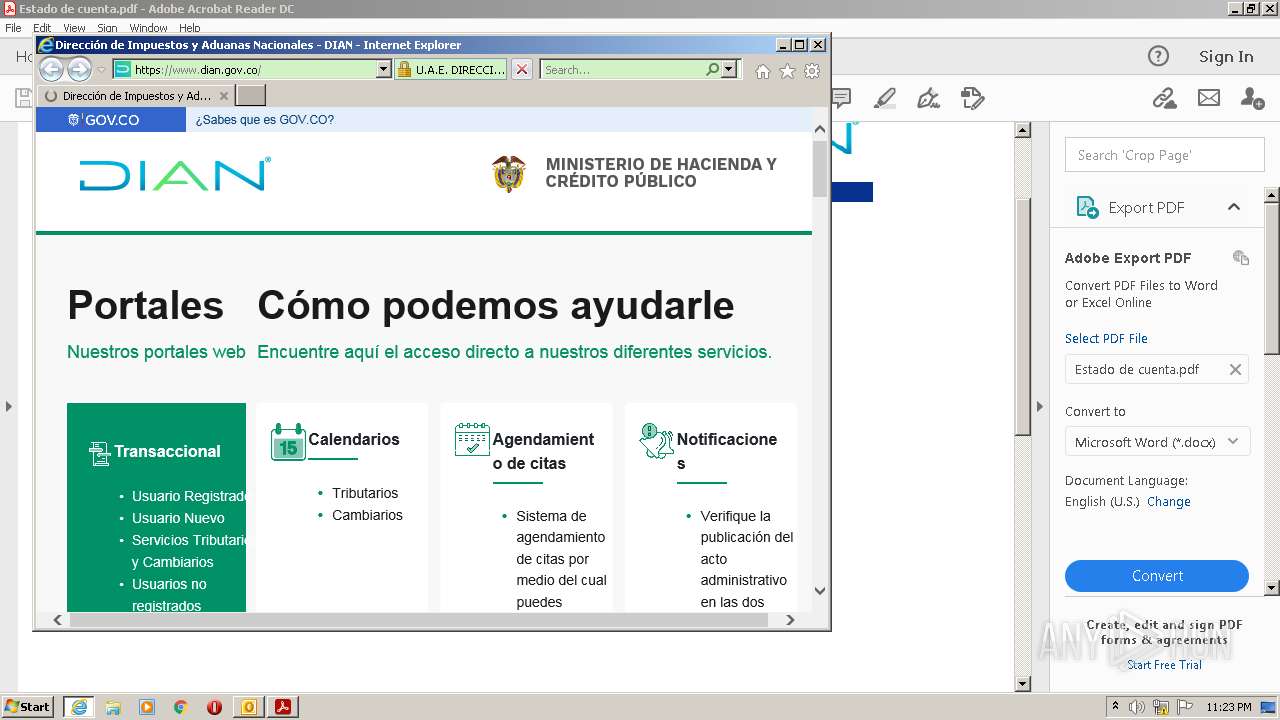
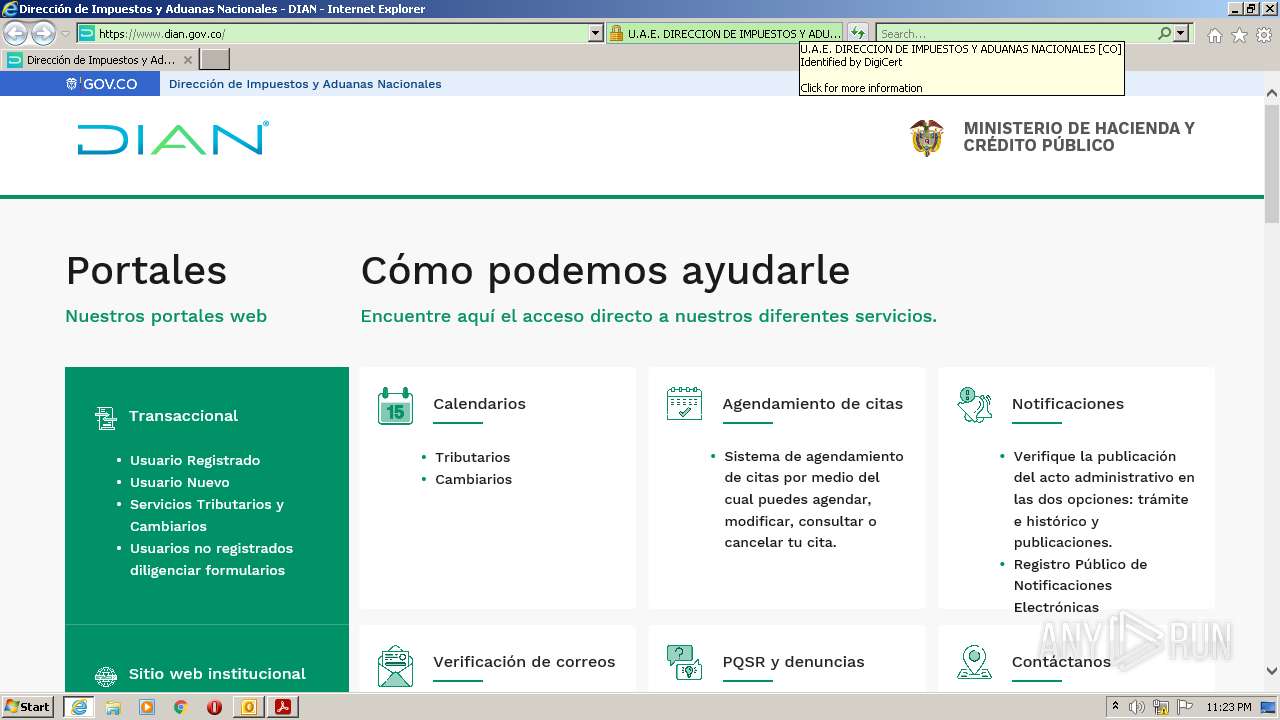
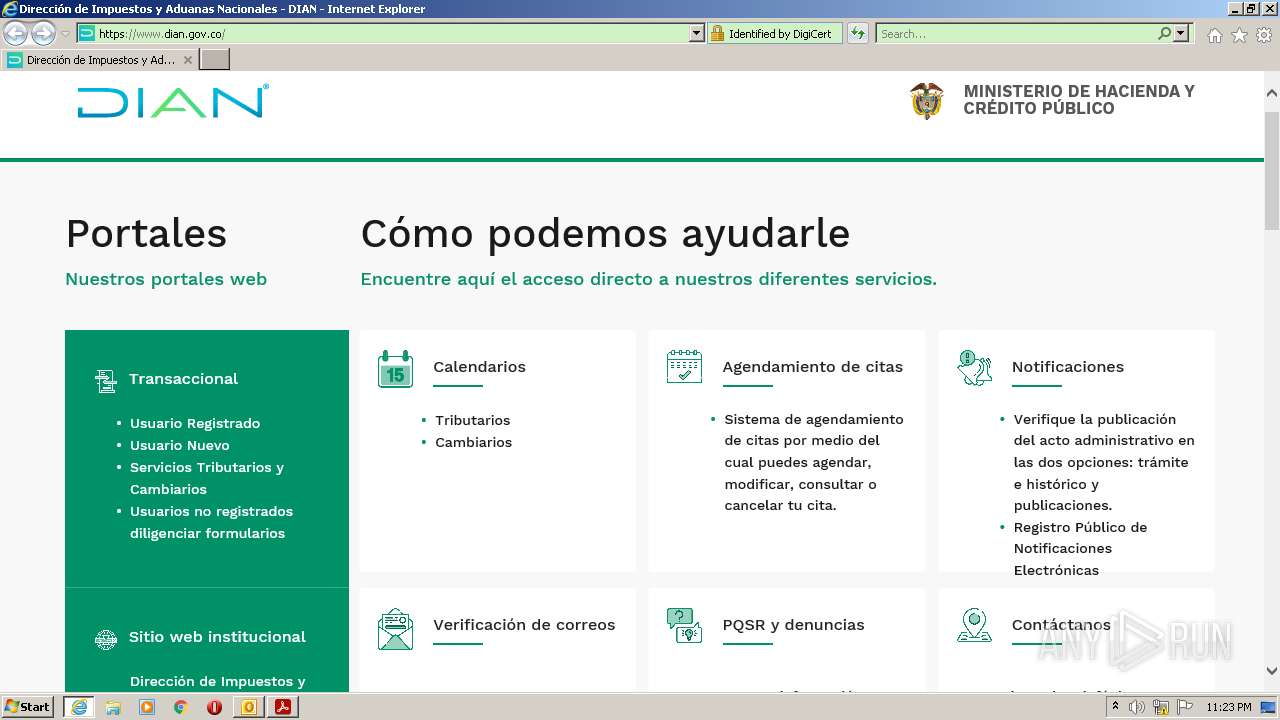
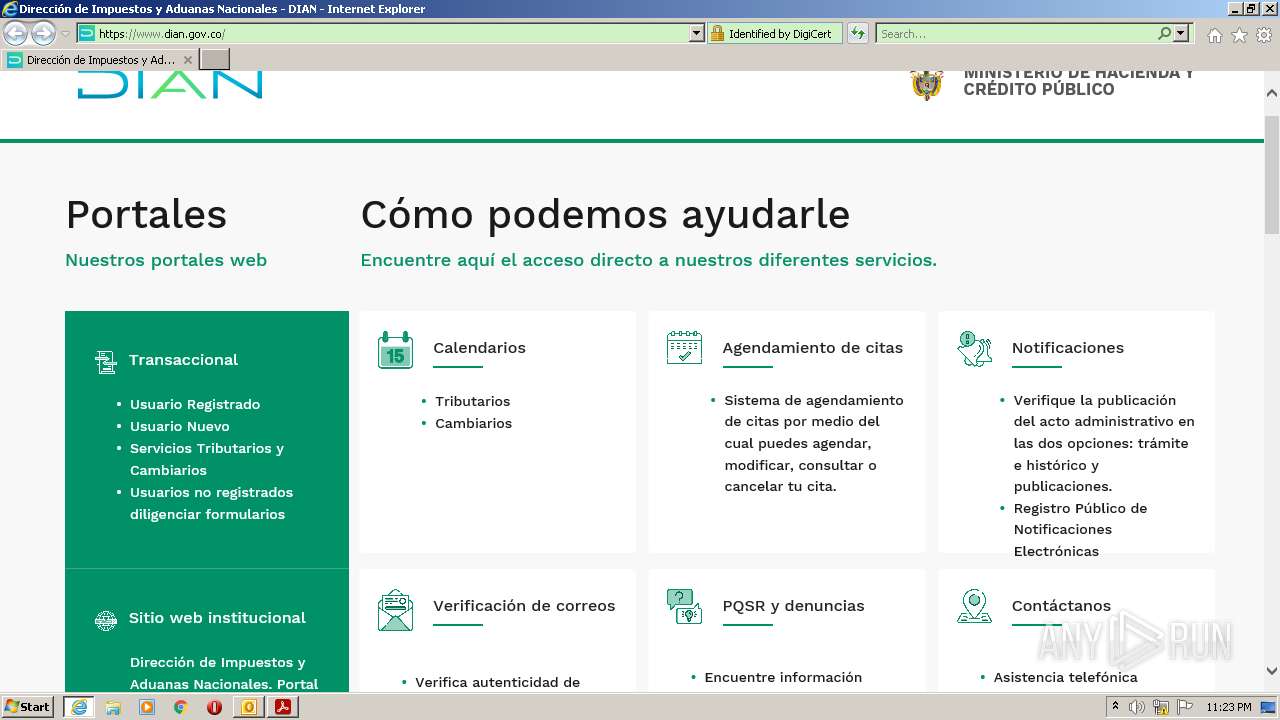
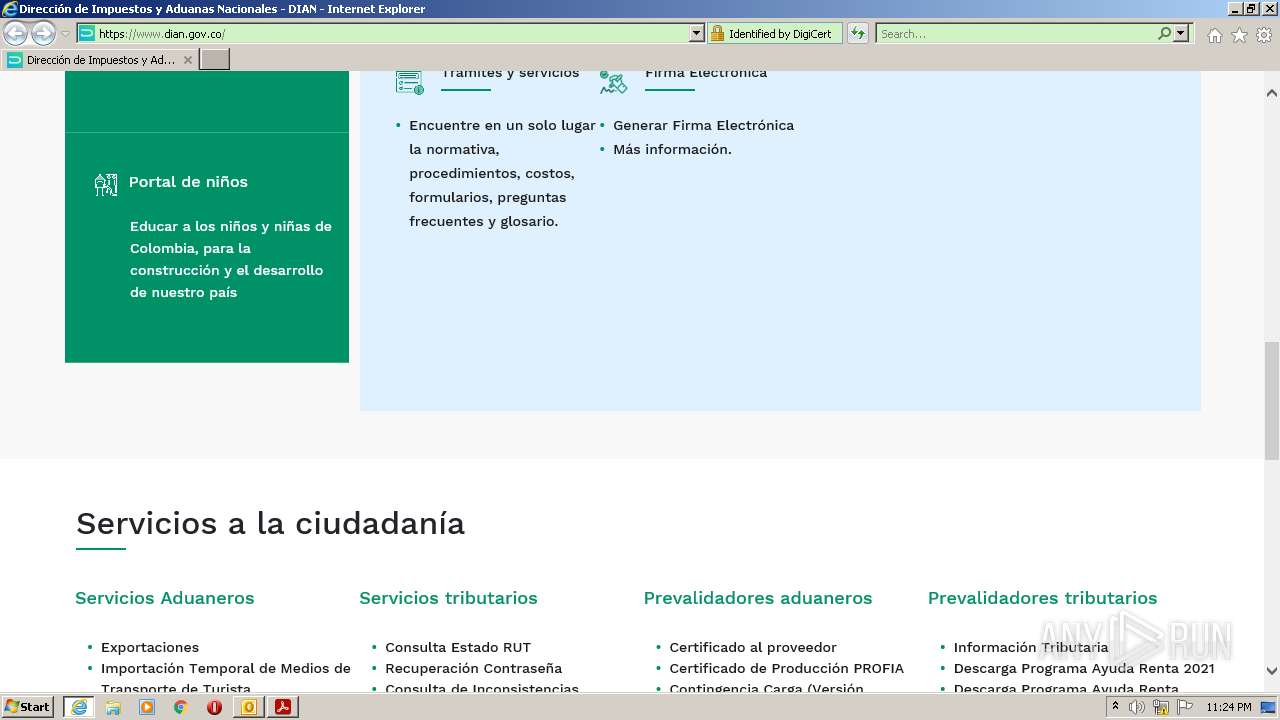
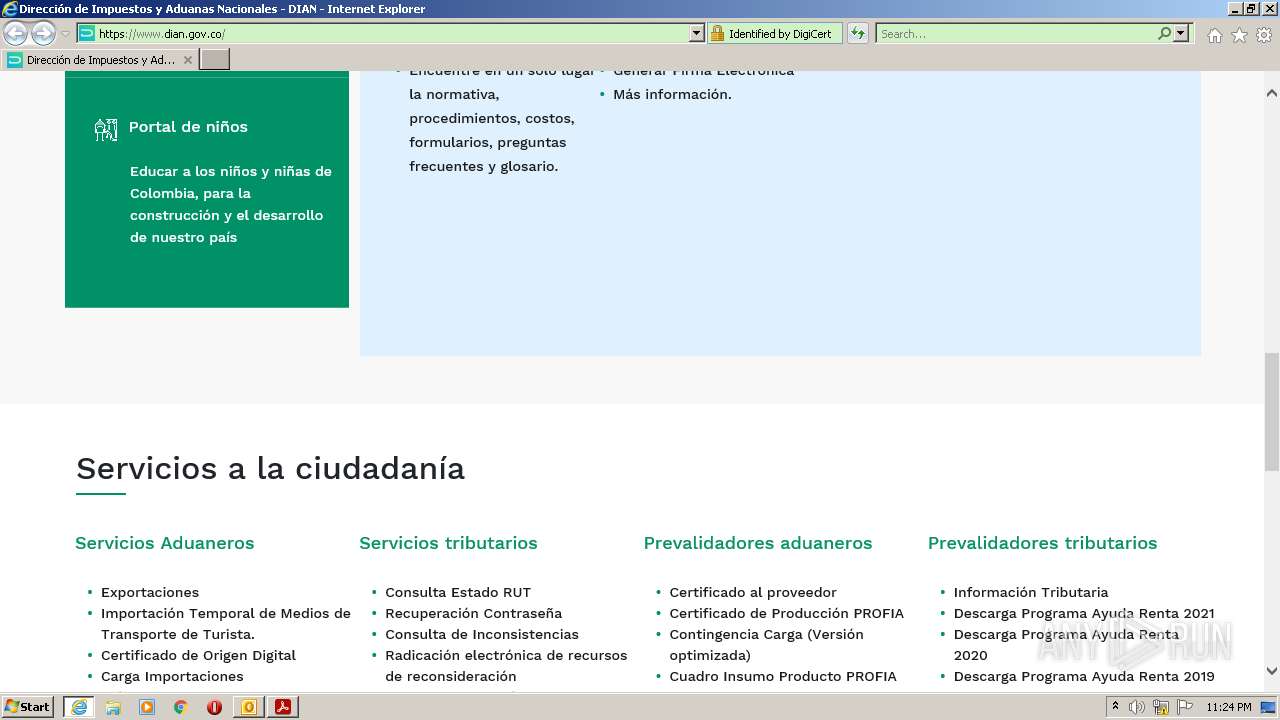
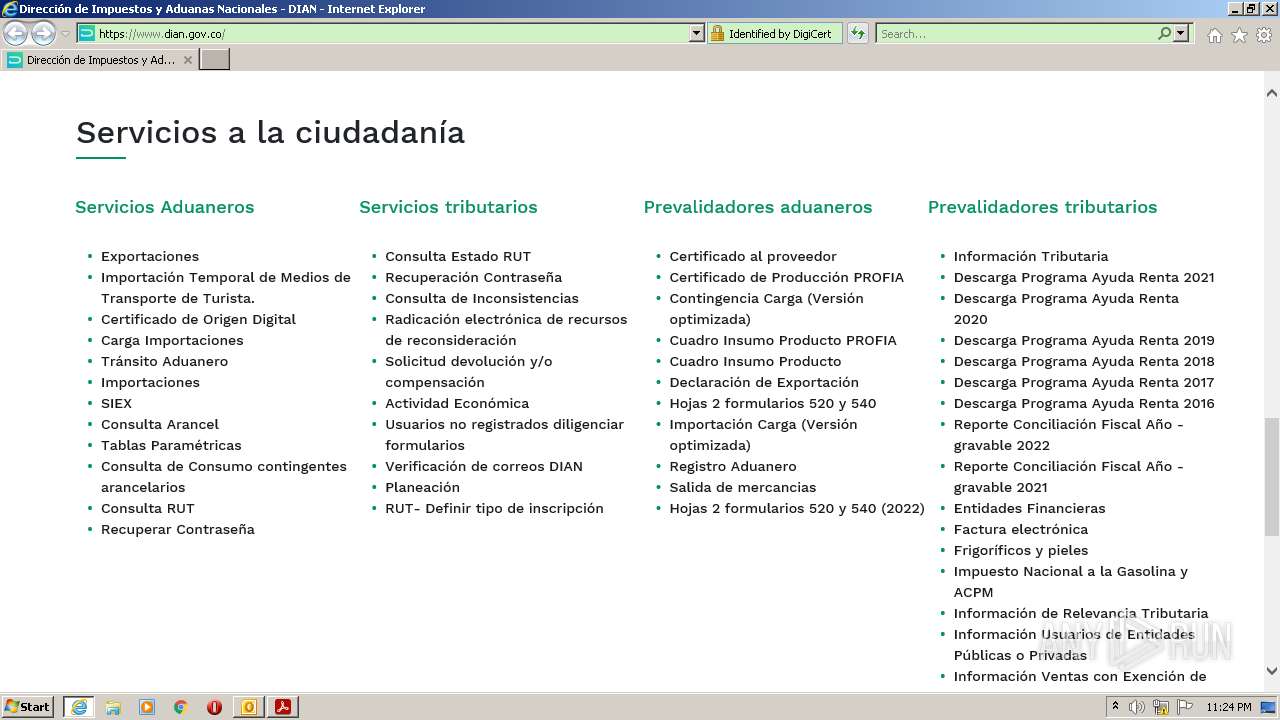
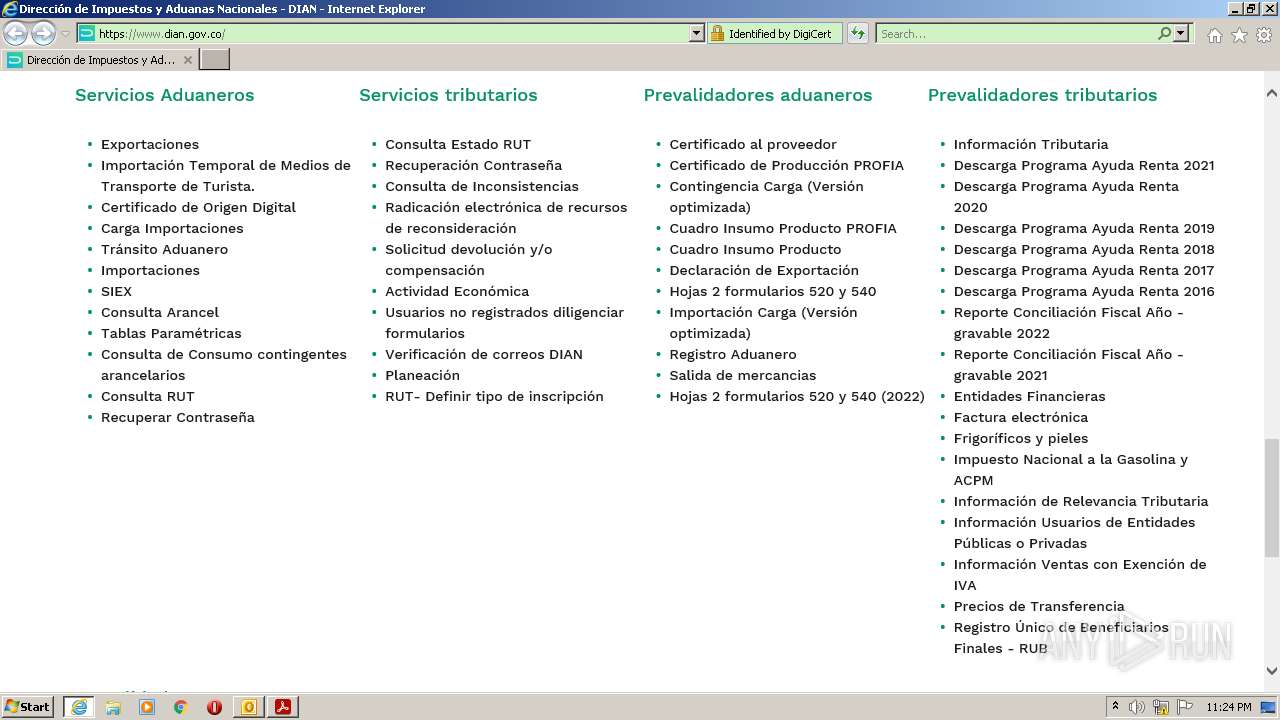
www.dian.gov.co |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
status.geotrust.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET DNS Query for .to TLD |
— | — | Potentially Bad Traffic | ET DNS Query for .to TLD |
860 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2 ETPRO signatures available at the full report