| File name: | Setup.exe |
| Full analysis: | https://app.any.run/tasks/d845533b-e8db-4036-b77b-3b6ff865e4bb |
| Verdict: | Malicious activity |
| Analysis date: | July 01, 2024, 20:23:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 15C6CC6632EDEEB6F9D796B1420FA60C |
| SHA1: | AB81151992FD3B85CCE93FB73A75BA2E1FA72232 |
| SHA256: | 810858BC4DC8A0771CE99CCCFE79A958EA2F2D7D10338C2CC0DC4771E61393AC |
| SSDEEP: | 98304:FlCJnh/6c7Kvt3HXCMUo4rimRQ5Smuex8ZaAGa0NHD2noKTYexdpBZe14MVuDgDN:pbag+28aoTbks8kEtmvLRS |
MALICIOUS
Drops the executable file immediately after the start
- Setup.exe (PID: 4596)
- Setup.exe (PID: 5776)
- cks.exe (PID: 1660)
- SETUPEX.EXE (PID: 1736)
- Setup.tmp (PID: 4564)
Creates a writable file in the system directory
- SETUPEX.EXE (PID: 1736)
Registers / Runs the DLL via REGSVR32.EXE
- Setup.tmp (PID: 4564)
SUSPICIOUS
Executable content was dropped or overwritten
- Setup.exe (PID: 4596)
- Setup.exe (PID: 5776)
- Setup.tmp (PID: 4564)
- cks.exe (PID: 1660)
- SETUPEX.EXE (PID: 1736)
Reads the date of Windows installation
- Setup.tmp (PID: 1928)
Reads security settings of Internet Explorer
- Setup.tmp (PID: 1928)
- edb.exe (PID: 6592)
Process drops legitimate windows executable
- Setup.tmp (PID: 4564)
Uses ICACLS.EXE to modify access control lists
- SETUPEX.EXE (PID: 1736)
Drops a system driver (possible attempt to evade defenses)
- cks.exe (PID: 1660)
- SETUPEX.EXE (PID: 1736)
Executes as Windows Service
- Crypserv.exe (PID: 2056)
Reads Microsoft Outlook installation path
- regsvr32.exe (PID: 6244)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 6416)
- regsvr32.exe (PID: 6244)
Reads the Windows owner or organization settings
- Setup.tmp (PID: 4564)
INFO
Create files in a temporary directory
- Setup.exe (PID: 4596)
- Setup.exe (PID: 5776)
- Setup.tmp (PID: 4564)
Checks supported languages
- Setup.exe (PID: 4596)
- Setup.tmp (PID: 1928)
- Setup.exe (PID: 5776)
- Setup.tmp (PID: 4564)
- mpchk.exe (PID: 4104)
- cks.exe (PID: 1660)
- SETUPEX.EXE (PID: 1736)
- Setup_ck.exe (PID: 2124)
- Crypserv.exe (PID: 2056)
- edb.exe (PID: 6592)
Reads the computer name
- Setup.tmp (PID: 1928)
- Setup.tmp (PID: 4564)
- Setup_ck.exe (PID: 2124)
- SETUPEX.EXE (PID: 1736)
- Crypserv.exe (PID: 2056)
- edb.exe (PID: 6592)
Process checks computer location settings
- Setup.tmp (PID: 1928)
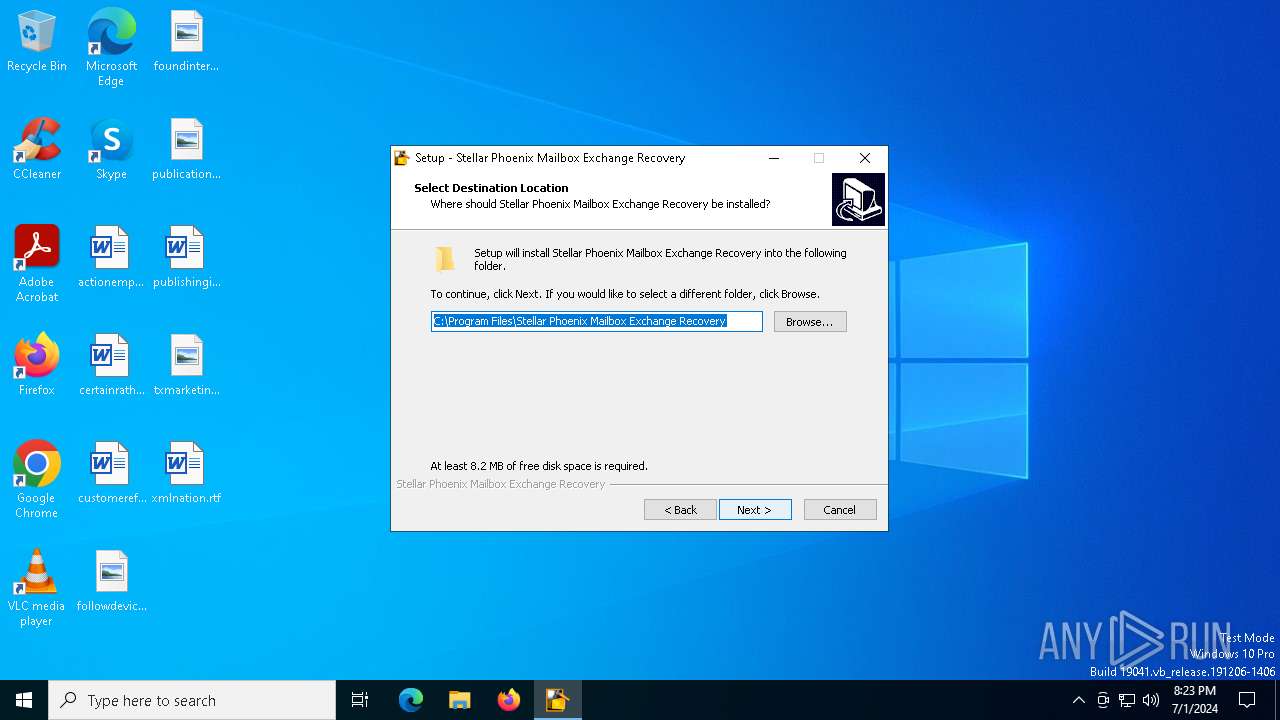
Creates files in the program directory
- Setup.tmp (PID: 4564)
- SETUPEX.EXE (PID: 1736)
Creates a software uninstall entry
- Setup.tmp (PID: 4564)
Reads Microsoft Office registry keys
- regsvr32.exe (PID: 6244)
- regsvr32.exe (PID: 6416)
Checks proxy server information
- edb.exe (PID: 6592)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (74.3) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (9.6) |
| .scr | | | Windows screen saver (8.8) |
| .exe | | | Win32 Executable (generic) (3) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 40448 |
| InitializedDataSize: | 172544 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa5f8 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.0.0.0 |
| ProductVersionNumber: | 6.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
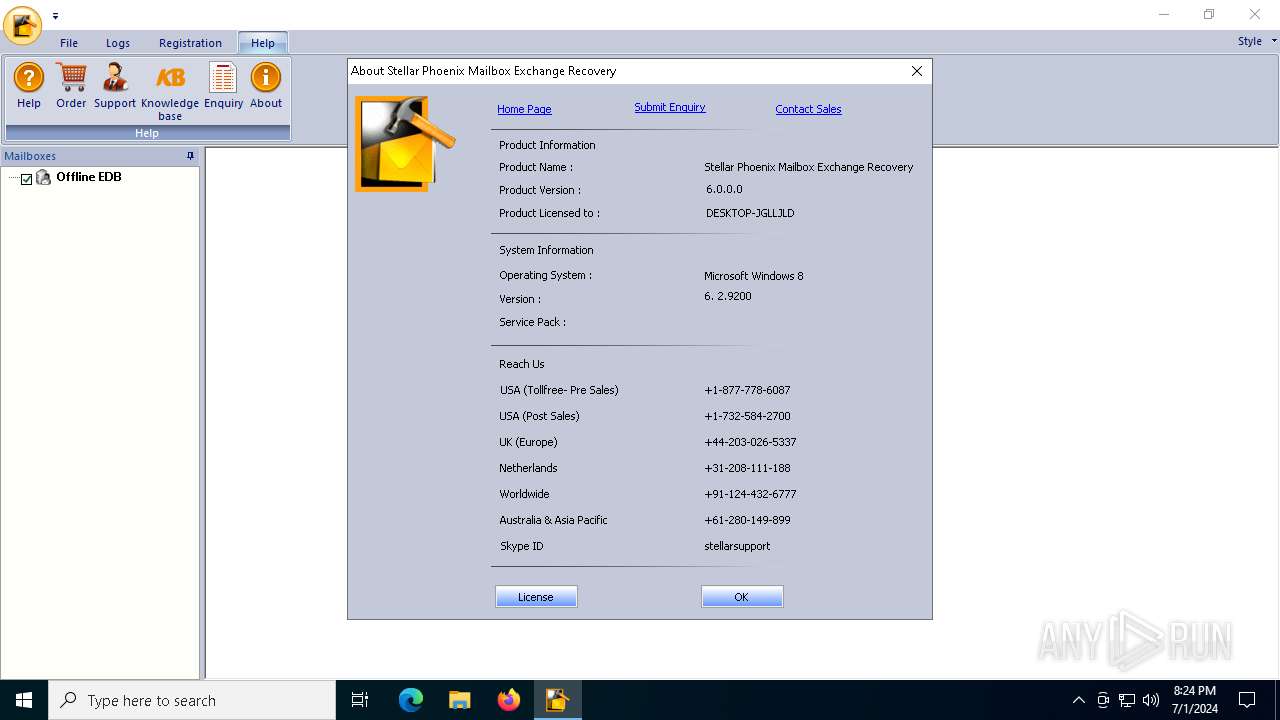
| CompanyName: | Stellar Information Technology Pvt Ltd. |
| FileDescription: | Stellar Information Technology Pvt Ltd. |
| FileVersion: | 6.0.0.0 |
| LegalCopyright: | Stellar Information Technology Pvt Ltd. |
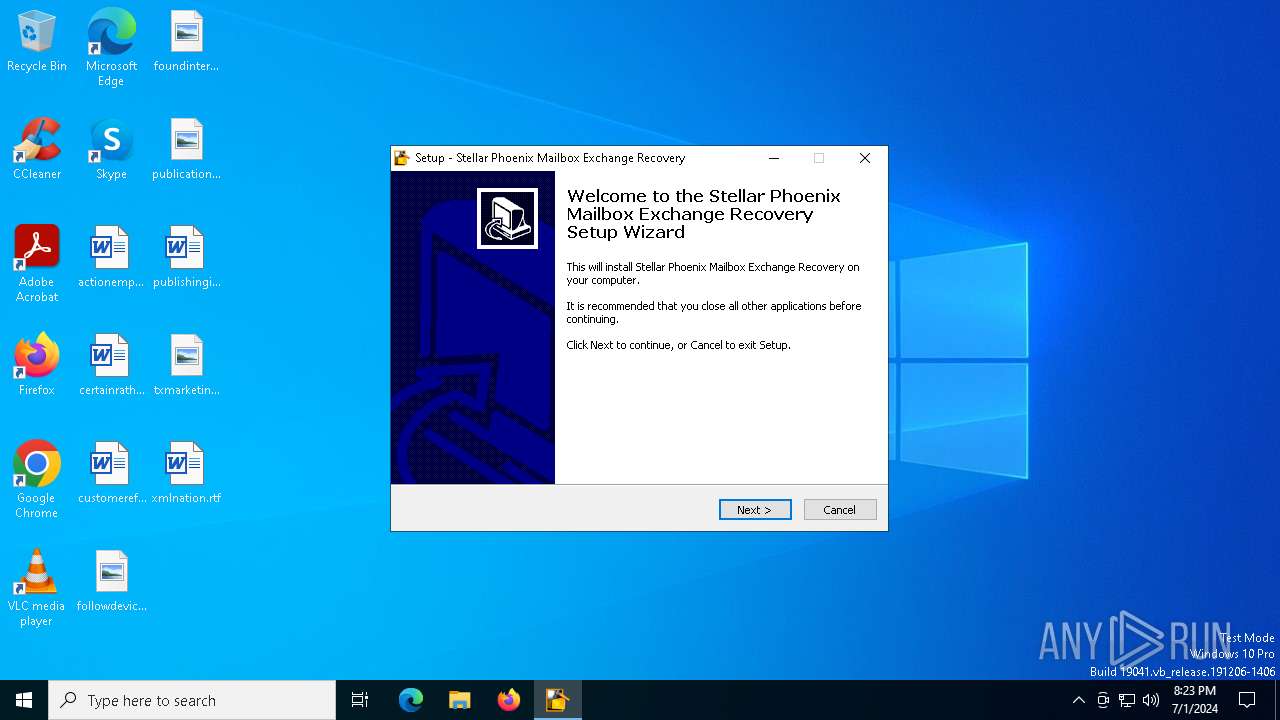
| ProductName: | Stellar Phoenix Mailbox Exchange Recovery |
| ProductVersion: | 6.0.0.0 |
Total processes
152
Monitored processes
19
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1540 | cacls.exe C:\Program Files\Stellar Phoenix Mailbox Exchange Recovery /e /g system:f | C:\Windows\System32\cacls.exe | — | SETUPEX.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 160 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | C:\PROGRA~1\STELLA~1\cks -overwrite -times=all | C:\Program Files\Stellar Phoenix Mailbox Exchange Recovery\cks.exe | SETUPEX.EXE | ||||||||||||
User: admin Company: PKWARE, Inc Integrity Level: HIGH Description: PKUNZIPC for Windows Command Line Exit code: 0 Version: 4.0.1.1 Modules
| |||||||||||||||
| 1736 | "C:\Program Files\Stellar Phoenix Mailbox Exchange Recovery\SETUPEX.exe" | C:\Program Files\Stellar Phoenix Mailbox Exchange Recovery\SETUPEX.EXE | Setup.tmp | ||||||||||||
User: admin Company: CrypKey Integrity Level: HIGH Description: CrypKey License Service Install Exit code: 0 Version: 7.102 Modules
| |||||||||||||||
| 1928 | "C:\Users\admin\AppData\Local\Temp\is-PAIOU.tmp\Setup.tmp" /SL5="$60348,13193943,214016,C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\is-PAIOU.tmp\Setup.tmp | — | Setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2056 | crypserv.exe | C:\Windows\System32\Crypserv.exe | — | services.exe | |||||||||||
User: SYSTEM Company: CrypKey (Canada) Ltd. Integrity Level: SYSTEM Description: CrypKey License Service Version: 1, 1, 0, 2 Modules
| |||||||||||||||
| 2124 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2124 | "C:\WINDOWS\Setup_ck.exe" | C:\Windows\Setup_ck.exe | — | SETUPEX.EXE | |||||||||||
User: admin Integrity Level: HIGH Exit code: 2 Modules
| |||||||||||||||
| 2392 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Setup_ck.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3868 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4104 | "C:\Program Files\Stellar Phoenix Mailbox Exchange Recovery\mpchk.exe" | C:\Program Files\Stellar Phoenix Mailbox Exchange Recovery\mpchk.exe | — | Setup.tmp | |||||||||||
User: admin Integrity Level: HIGH Description: chkoutlook MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
Total events
7 455
Read events
6 810
Write events
639
Delete events
6
Modification events
| (PID) Process: | (4564) Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: D41100008B6BA682F4CBDA01 | |||
| (PID) Process: | (4564) Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 23B212704AC863F2E1C1519D4744EA4F9988455B74047D6EAD67435F0FB8B82C | |||
| (PID) Process: | (4564) Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (4564) Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\Stellar Phoenix Mailbox Exchange Recovery\casper.dll | |||
| (PID) Process: | (4564) Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 25D3D7BE1CEE7B46DFA44E3D15D41DC52CDF47C0C2D053D40D5B6CD2FE28CD97 | |||
| (PID) Process: | (4564) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Stellar Data Recovery\Stellar Phoenix Mailbox Exchange Recovery |
| Operation: | write | Name: | Path |
Value: C:\Program Files\Stellar Phoenix Mailbox Exchange Recovery | |||
| (PID) Process: | (4564) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Stellar Data Recovery\Stellar Phoenix Mailbox Exchange Recovery |
| Operation: | write | Name: | Version |
Value: 6.0.0.0 | |||
| (PID) Process: | (4564) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Stellar Data Recovery\Stellar Phoenix Mailbox Exchange Recovery |
| Operation: | write | Name: | ExeName |
Value: edb | |||
| (PID) Process: | (4564) Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers |
| Operation: | write | Name: | C:\Program Files\Stellar Phoenix Mailbox Exchange Recovery\edb.exe |
Value: RUNASADMIN | |||
| (PID) Process: | (4564) Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers |
| Operation: | write | Name: | C:\Program Files\Stellar Phoenix Mailbox Exchange Recovery\ActivationOption.exe |
Value: RUNASADMIN | |||
Executable files
60
Suspicious files
3
Text files
12
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4564 | Setup.tmp | C:\Program Files\Stellar Phoenix Mailbox Exchange Recovery\is-5EI0D.tmp | executable | |
MD5:0CFDB5C3BF55B845A19277378769916E | SHA256:539C16B150B8CF87A4D56F31B39C7DF342486FDA9632041FB19DFF2A6D0DAC60 | |||
| 4564 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-CLUU6.tmp\_isetup\_setup64.tmp | executable | |
MD5:526426126AE5D326D0A24706C77D8C5C | SHA256:B20A8D88C550981137ED831F2015F5F11517AEB649C29642D9D61DEA5EBC37D1 | |||
| 4564 | Setup.tmp | C:\Program Files\Stellar Phoenix Mailbox Exchange Recovery\unins000.exe | executable | |
MD5:0CFDB5C3BF55B845A19277378769916E | SHA256:539C16B150B8CF87A4D56F31B39C7DF342486FDA9632041FB19DFF2A6D0DAC60 | |||
| 4564 | Setup.tmp | C:\Program Files\Stellar Phoenix Mailbox Exchange Recovery\APP.ICO | image | |
MD5:1876C0072656EF1E7D66DF6C48F44556 | SHA256:3A212526D0659A3FBDEC240C6F3CFDCC8A20BE50354EFAC0F242EB7EDE0708F9 | |||
| 4564 | Setup.tmp | C:\Program Files\Stellar Phoenix Mailbox Exchange Recovery\is-V4B6A.tmp | executable | |
MD5:1AB948505EB40200D4565429061D86B2 | SHA256:0811249ECF715937442CAB471959E015DCE03DE9FE9EF8095CB375082A2F26CC | |||
| 4564 | Setup.tmp | C:\Program Files\Stellar Phoenix Mailbox Exchange Recovery\is-J62PP.tmp | text | |
MD5:1CBEEB72D54B311FCE01B6EF0ABEF950 | SHA256:11C40F9EF99C777C93B4D057DDE25C6646F3AB55997675C72041D02547E8237A | |||
| 4596 | Setup.exe | C:\Users\admin\AppData\Local\Temp\is-PAIOU.tmp\Setup.tmp | executable | |
MD5:D3A2379EC72821FB0C6942BE779D4BD0 | SHA256:A26104F9A842C8FB51122F6F0C35803D091613C1EA9C7CE93C0E2518F34CF752 | |||
| 4564 | Setup.tmp | C:\Program Files\Stellar Phoenix Mailbox Exchange Recovery\is-L0LVT.tmp | image | |
MD5:1876C0072656EF1E7D66DF6C48F44556 | SHA256:3A212526D0659A3FBDEC240C6F3CFDCC8A20BE50354EFAC0F242EB7EDE0708F9 | |||
| 4564 | Setup.tmp | C:\Program Files\Stellar Phoenix Mailbox Exchange Recovery\is-ADQ2P.tmp | executable | |
MD5:CB7D4AC7BF19FEF6CA9F9B11B992FF22 | SHA256:921B3B30393A86FDFC517B8FD1BD2281E07CC3B38C552565AB63134057E93DA7 | |||
| 4564 | Setup.tmp | C:\Program Files\Stellar Phoenix Mailbox Exchange Recovery\crp32dll.dll | executable | |
MD5:79C8827FEA8E68C918E9816AACA13779 | SHA256:FDB802E85E4B4EFE1D876CF5278D64D73DD400E93166FC8D4B583709BE48EF8C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
58
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
692 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
5040 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
692 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6004 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
2476 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4632 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4656 | SearchApp.exe | 104.126.37.177:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
1544 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | unknown |
1544 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | unknown |
1060 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |