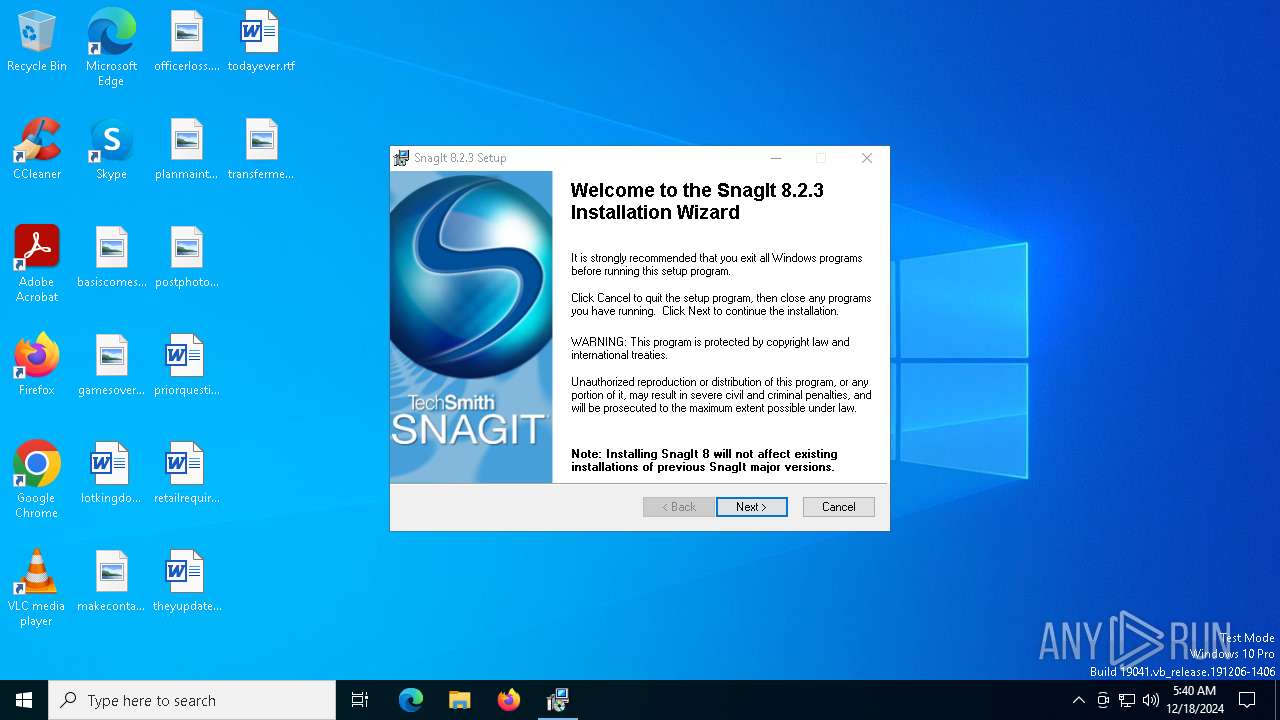
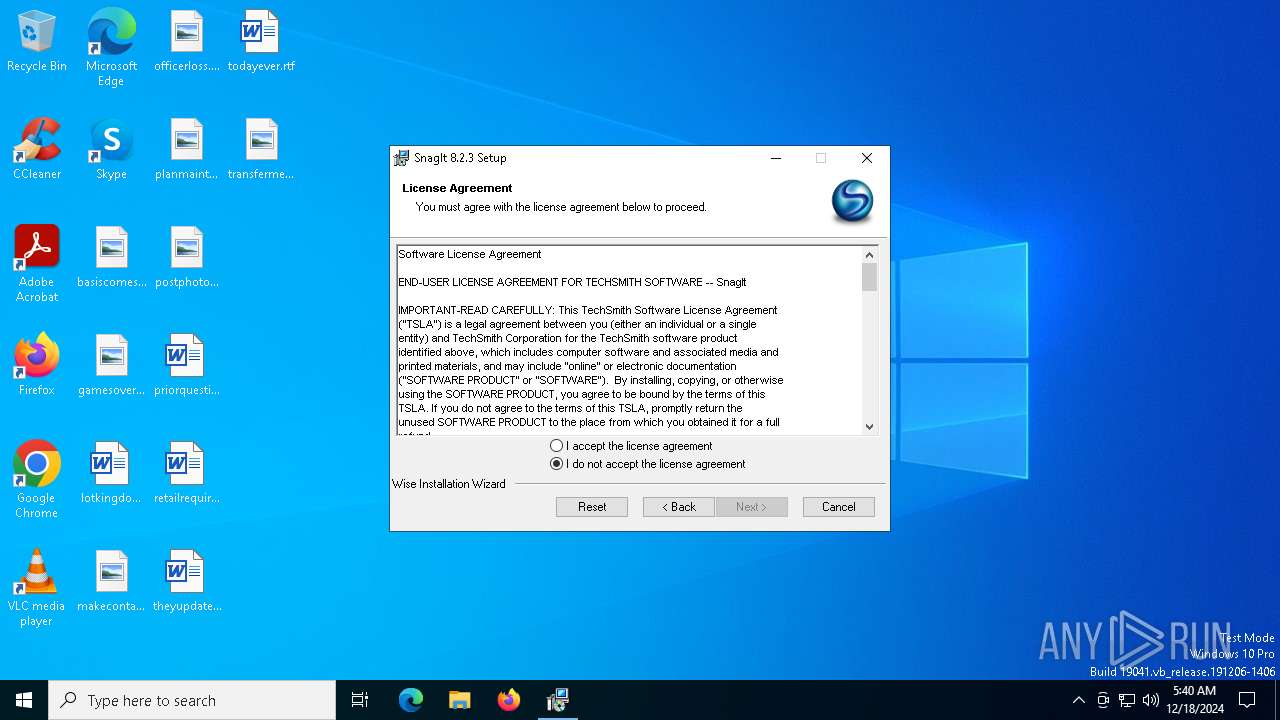
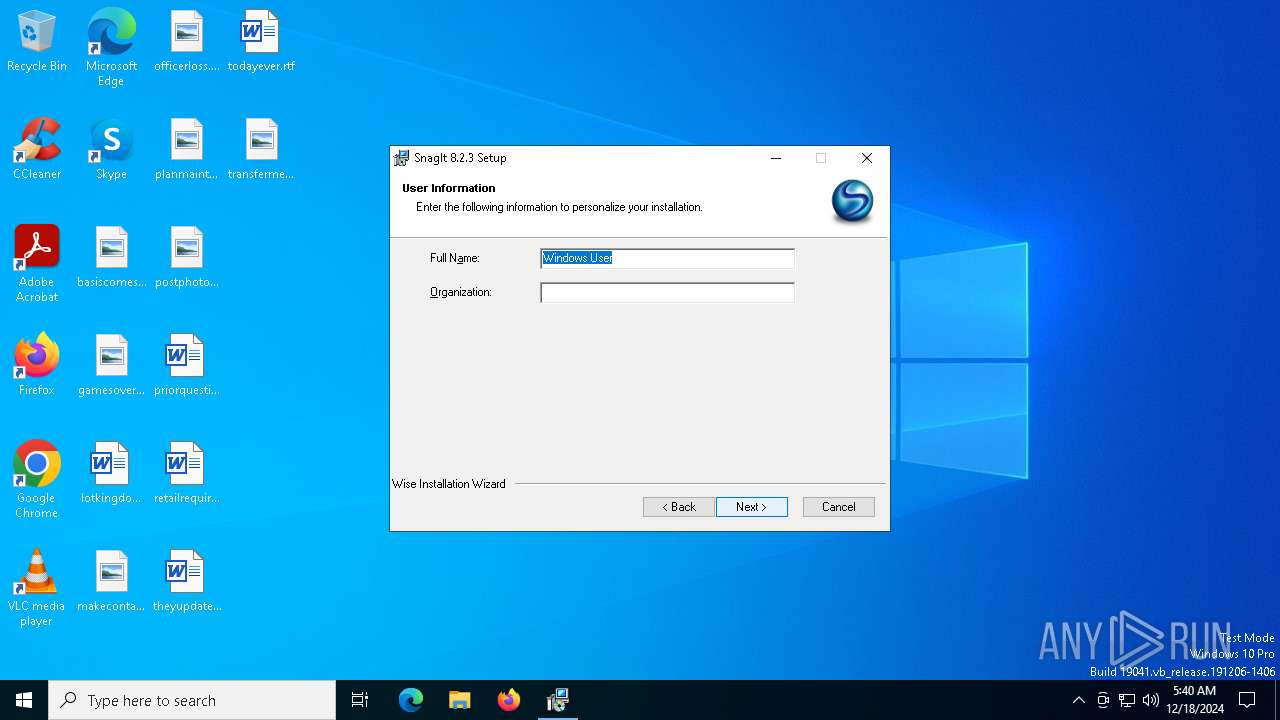
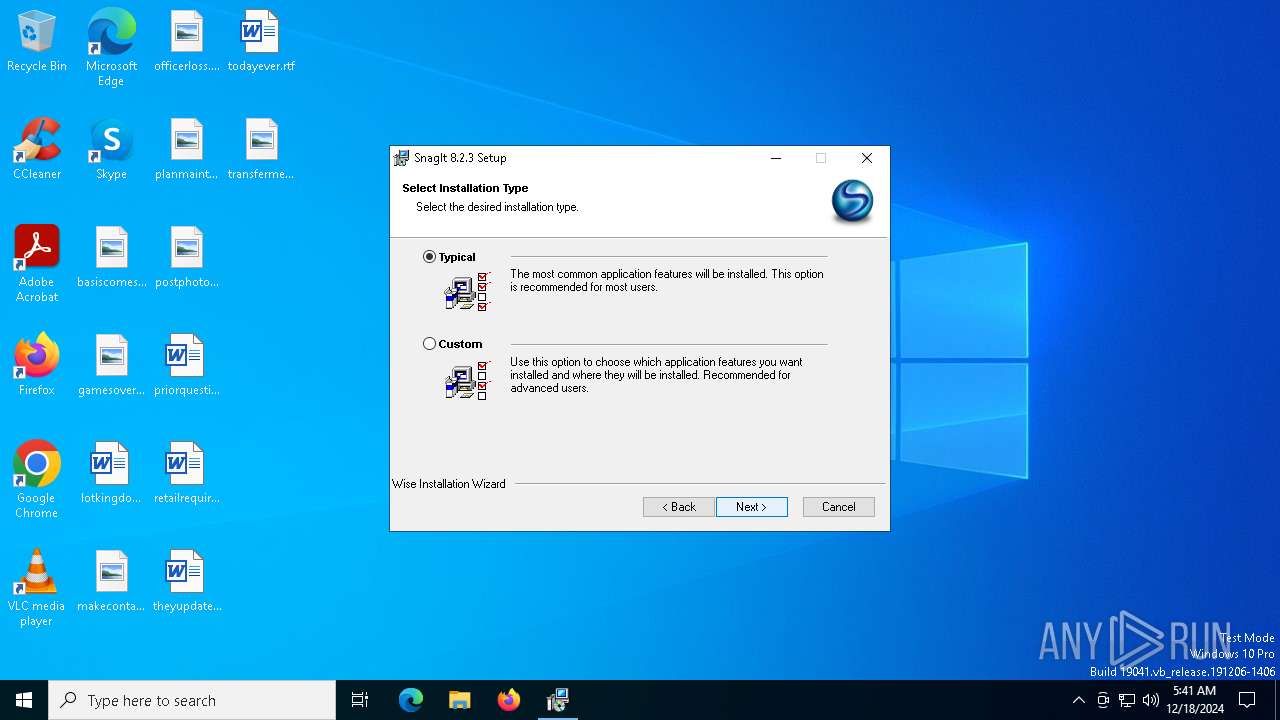
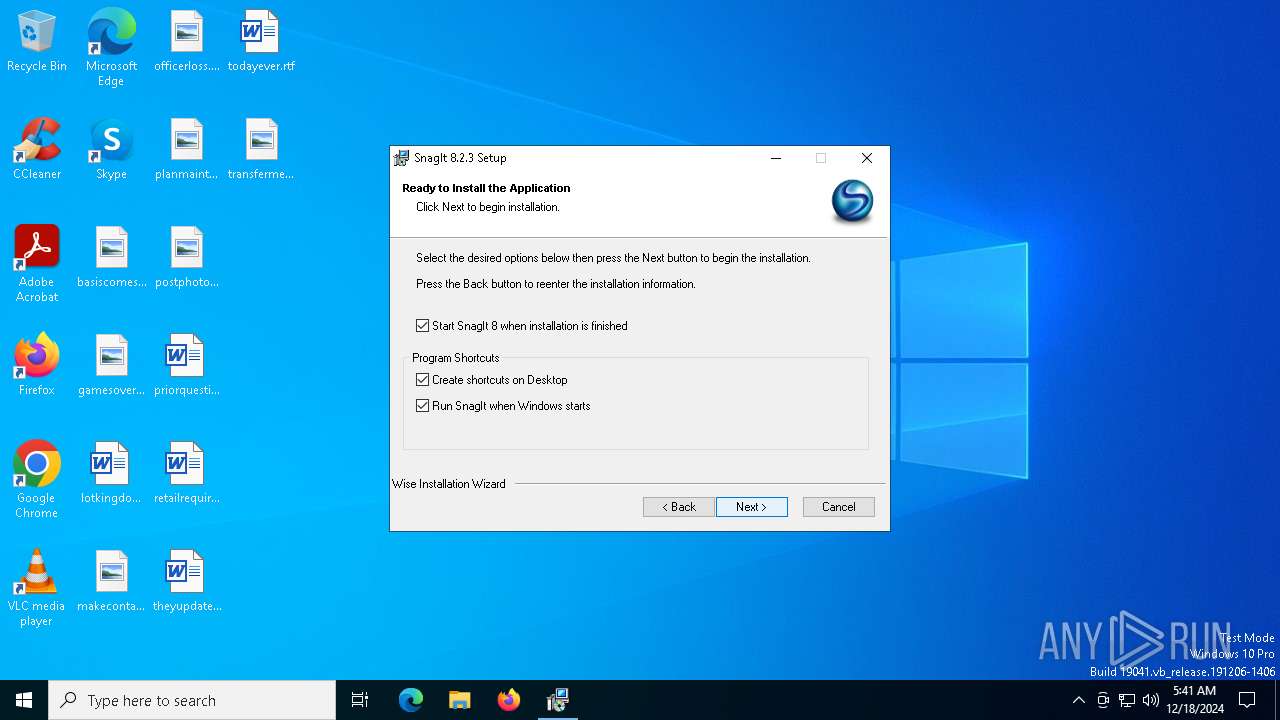
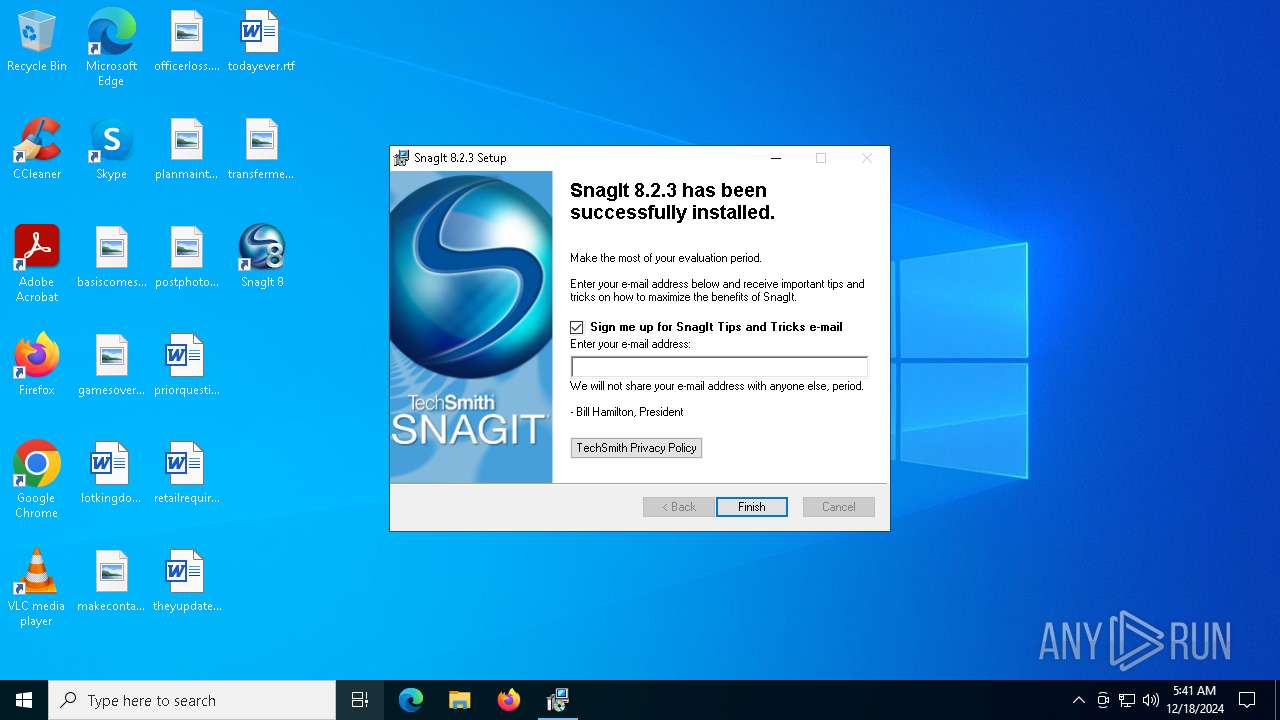
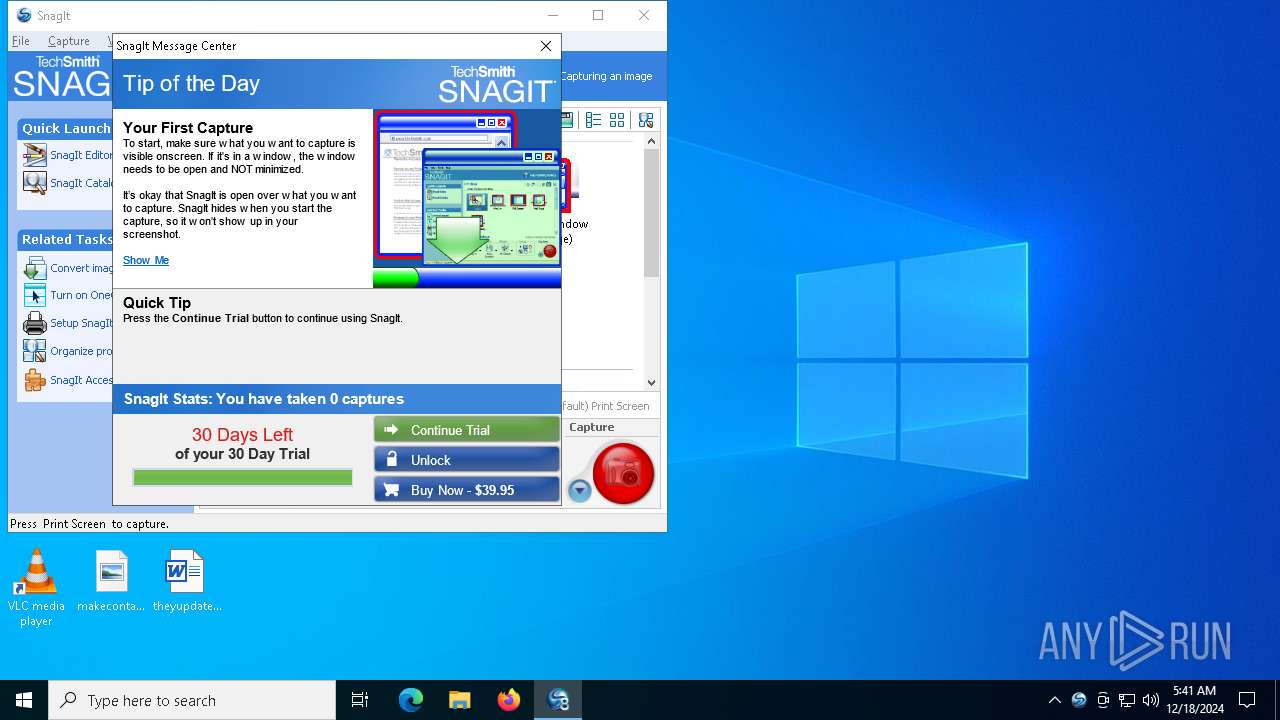
| File name: | snagit.exe |
| Full analysis: | https://app.any.run/tasks/7ec2446b-7fae-4919-b6e8-b74580d501d5 |
| Verdict: | Malicious activity |
| Analysis date: | December 18, 2024, 05:40:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, WISE installer self-extracting archive, 5 sections |
| MD5: | 7A950E0312A48E9CD3783E3307CC4F5D |
| SHA1: | 6314A99F2378DE9D072C174EA894D9697A08A546 |
| SHA256: | 8103B0FEC76ED477F60114CA13974E9547DD077E40E9754F93807C113D36D745 |
| SSDEEP: | 98304:s0Mq/3oUAiOnXW7sNiEEsfd8yH9JpDslS2RoWzUyvYgRQAzyXTN+SsztCQD9zpMw:EIUmDF4RvfhajRkZ+bXnpIbq |
MALICIOUS
Executing a file with an untrusted certificate
- SnagIt32.exe (PID: 7004)
- TSMSIhlp.EXE (PID: 4504)
- TSMSIhlp.EXE (PID: 3696)
- TSMSIhlp.EXE (PID: 2008)
- TSMSIhlp.EXE (PID: 4444)
- TSMSIhlp.EXE (PID: 3296)
- SnagItPI.exe (PID: 6776)
- SnagItPI64.exe (PID: 4968)
- SnagIt32.exe (PID: 4428)
- TscHelp.exe (PID: 6416)
- SnagPriv.exe (PID: 7000)
- SnagPriv.exe (PID: 2992)
Registers / Runs the DLL via REGSVR32.EXE
- msiexec.exe (PID: 5268)
- GLB152C.tmp (PID: 3640)
- GLB19A1.tmp (PID: 5308)
SUSPICIOUS
Reads security settings of Internet Explorer
- snagit.exe (PID: 7064)
- SnagIt32.exe (PID: 7004)
- SnagIt32.exe (PID: 4428)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5268)
Checks Windows Trust Settings
- msiexec.exe (PID: 5268)
- SnagIt32.exe (PID: 4428)
Executes as Windows Service
- VSSVC.exe (PID: 6184)
The process drops C-runtime libraries
- msiexec.exe (PID: 5268)
Process drops legitimate windows executable
- msiexec.exe (PID: 5268)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 5268)
- msiexec.exe (PID: 6336)
- msiexec.exe (PID: 6744)
- SnagIt32.exe (PID: 7004)
- regsvr32.exe (PID: 716)
- regsvr32.exe (PID: 6212)
- regsvr32.exe (PID: 848)
- regsvr32.exe (PID: 6312)
- regsvr32.exe (PID: 3884)
- regsvr32.exe (PID: 6216)
- SnagIt32.exe (PID: 4428)
Executable content was dropped or overwritten
- TSMSIhlp.EXE (PID: 4504)
- TSMSIhlp.EXE (PID: 2008)
- GLB152C.tmp (PID: 3640)
- TSMSIhlp.EXE (PID: 4444)
- TSMSIhlp.EXE (PID: 3696)
- GLB19A1.tmp (PID: 5308)
- TSMSIhlp.EXE (PID: 3296)
- SnagItPI64.exe (PID: 4968)
- SnagIt32.exe (PID: 4428)
Starts application with an unusual extension
- TSMSIhlp.EXE (PID: 4504)
- TSMSIhlp.EXE (PID: 3696)
- TSMSIhlp.EXE (PID: 2008)
- TSMSIhlp.EXE (PID: 4444)
- TSMSIhlp.EXE (PID: 3296)
Reads Internet Explorer settings
- SnagIt32.exe (PID: 4428)
Reads Microsoft Outlook installation path
- SnagIt32.exe (PID: 4428)
INFO
The process uses the downloaded file
- snagit.exe (PID: 7064)
- SnagIt32.exe (PID: 4428)
Create files in a temporary directory
- snagit.exe (PID: 7064)
- TSMSIhlp.EXE (PID: 4504)
- TSMSIhlp.EXE (PID: 3696)
- TSMSIhlp.EXE (PID: 4444)
- SnagIt32.exe (PID: 4428)
The sample compiled with english language support
- snagit.exe (PID: 7064)
- msiexec.exe (PID: 6872)
- msiexec.exe (PID: 5268)
- TSMSIhlp.EXE (PID: 4504)
- TSMSIhlp.EXE (PID: 3696)
- TSMSIhlp.EXE (PID: 2008)
- TSMSIhlp.EXE (PID: 4444)
- TSMSIhlp.EXE (PID: 3296)
- SnagItPI64.exe (PID: 4968)
- SnagIt32.exe (PID: 4428)
Process checks computer location settings
- snagit.exe (PID: 7064)
- SnagIt32.exe (PID: 7004)
- SnagIt32.exe (PID: 4428)
Reads the computer name
- snagit.exe (PID: 7064)
- msiexec.exe (PID: 6872)
- TscHelp.exe (PID: 6748)
- SnagIt32.exe (PID: 7004)
- GLB152C.tmp (PID: 3640)
- GLB19A1.tmp (PID: 5308)
- SnagItPI64.exe (PID: 4968)
- msiexec.exe (PID: 5092)
- SnagIt32.exe (PID: 4428)
- SnagPriv.exe (PID: 2992)
- TscHelp.exe (PID: 6416)
Checks supported languages
- snagit.exe (PID: 7064)
- msiexec.exe (PID: 5268)
- msiexec.exe (PID: 6872)
- SnagIt32.exe (PID: 7004)
- TscHelp.exe (PID: 6748)
- TSMSIhlp.EXE (PID: 4504)
- TSMSIhlp.EXE (PID: 3696)
- GLB152C.tmp (PID: 3640)
- TSMSIhlp.EXE (PID: 2008)
- TSMSIhlp.EXE (PID: 3296)
- SnagItPI.exe (PID: 6776)
- SnagItPI64.exe (PID: 4968)
- TSMSIhlp.EXE (PID: 4444)
- GLB19A1.tmp (PID: 5308)
- msiexec.exe (PID: 5092)
- SnagIt32.exe (PID: 4428)
- TscHelp.exe (PID: 6416)
- SnagPriv.exe (PID: 2992)
Manages system restore points
- SrTasks.exe (PID: 4160)
Reads the machine GUID from the registry
- msiexec.exe (PID: 5268)
- SnagIt32.exe (PID: 4428)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5268)
- msiexec.exe (PID: 7136)
- msiexec.exe (PID: 6872)
Reads the software policy settings
- msiexec.exe (PID: 5268)
- SnagIt32.exe (PID: 4428)
The sample compiled with korean language support
- msiexec.exe (PID: 5268)
The sample compiled with chinese language support
- msiexec.exe (PID: 5268)
The sample compiled with spanish language support
- msiexec.exe (PID: 5268)
The sample compiled with french language support
- msiexec.exe (PID: 5268)
The sample compiled with Italian language support
- msiexec.exe (PID: 5268)
The sample compiled with japanese language support
- msiexec.exe (PID: 5268)
Creates a software uninstall entry
- msiexec.exe (PID: 5268)
Reads Microsoft Office registry keys
- msiexec.exe (PID: 5268)
The sample compiled with german language support
- msiexec.exe (PID: 5268)
- SnagIt32.exe (PID: 4428)
Checks proxy server information
- SnagIt32.exe (PID: 4428)
Creates files or folders in the user directory
- SnagIt32.exe (PID: 4428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Wise Installer executable (74.8) |
|---|---|---|
| .exe | | | InstallShield setup (6.8) |
| .exe | | | Win32 EXE PECompact compressed (generic) (6.5) |
| .exe | | | Win32 Executable MS Visual C++ (generic) (4.9) |
| .exe | | | Win64 Executable (generic) (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2004:08:12 13:48:03+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 7.1 |
| CodeSize: | 23040 |
| InitializedDataSize: | 14549504 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x4091 |
| OSVersion: | 4 |
| ImageVersion: | 4 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.2.3.0 |
| ProductVersionNumber: | 8.2.3.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | TechSmith Corporation |
| FileDescription: | SnagIt 8 |
| FileVersion: | 8.2.3 |
| LegalCopyright: | TechSmith Corporation |
Total processes
162
Monitored processes
40
Malicious processes
12
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 716 | /s "C:\Program Files (x86)\TechSmith\SnagIt 8\SnagItIEAddin.dll" | C:\Windows\SysWOW64\regsvr32.exe | regsvr32.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 848 | regsvr32.exe /s "C:\Program Files (x86)\TechSmith\SnagIt 8\DLLx64\SnagItBHO64.dll" | C:\Windows\System32\regsvr32.exe | — | GLB152C.tmp | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1200 | C:\Users\admin\AppData\Local\Temp\GLB1D3B.tmp DoOpenWith4736 C:\PROGRA~2\TECHSM~1\SNAGIT~1\TSMSIhlp.EXE | C:\Users\admin\AppData\Local\Temp\GLB1D3B.tmp | — | TSMSIhlp.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 | |||||||||||||||
| 2008 | "C:\Program Files (x86)\TechSmith\SnagIt 8\TSMSIhlp.EXE" RegSvr64 /s "C:\Program Files (x86)\TechSmith\SnagIt 8\DLLx64\SnagItBHO64.dll" | C:\Program Files (x86)\TechSmith\SnagIt 8\TSMSIhlp.EXE | msiexec.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 2992 | "C:\Program Files (x86)\TechSmith\SnagIt 8\SnagPriv.exe" | C:\Program Files (x86)\TechSmith\SnagIt 8\SnagPriv.exe | SnagIt32.exe | ||||||||||||
User: admin Company: TechSmith Corporation Integrity Level: HIGH Description: SnagIt RPC Helper Version: 8.2.3.14 | |||||||||||||||
| 3296 | "C:\Program Files (x86)\TechSmith\SnagIt 8\TSMSIhlp.EXE" DoOpenWith | C:\Program Files (x86)\TechSmith\SnagIt 8\TSMSIhlp.EXE | msiexec.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 3640 | C:\Users\admin\AppData\Local\Temp\GLB152C.tmp RegSvr64 /s "C:\Program Files (x86)\TechSmith\SnagIt 8\DLLx64\SnagItBHO64.dll"4736 C:\PROGRA~2\TECHSM~1\SNAGIT~1\TSMSIhlp.EXE | C:\Users\admin\AppData\Local\Temp\GLB152C.tmp | TSMSIhlp.EXE | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 | |||||||||||||||
| 3696 | "C:\Program Files (x86)\TechSmith\SnagIt 8\TSMSIhlp.EXE" RegSvr64 /s "C:\Program Files (x86)\TechSmith\SnagIt 8\DLLx64\SnagItIEAddin64.dll" | C:\Program Files (x86)\TechSmith\SnagIt 8\TSMSIhlp.EXE | msiexec.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 3884 | /s "C:\Program Files (x86)\TechSmith\SnagIt 8\SnagItBHO.dll" | C:\Windows\SysWOW64\regsvr32.exe | regsvr32.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 4160 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
38 066
Read events
29 407
Write events
8 375
Delete events
284
Modification events
| (PID) Process: | (7064) snagit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | WiseStubReboot |
Value: | |||
| (PID) Process: | (5268) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000CB51F36E0F51DB0194140000841A0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5268) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000CB51F36E0F51DB0194140000841A0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5268) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000007F11366F0F51DB0194140000841A0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5268) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000007F11366F0F51DB0194140000841A0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5268) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000E476386F0F51DB0194140000841A0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5268) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000B03F3D6F0F51DB0194140000841A0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5268) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (5268) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 48000000000000002817B26F0F51DB0194140000841A0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5268) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000639AB46F0F51DB0194140000E80E0000E8030000010000000000000000000000A060DD5AC3FCF949B38A9360A4E17BF000000000000000000000000000000000 | |||
Executable files
111
Suspicious files
36
Text files
175
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7064 | snagit.exe | C:\Users\admin\AppData\Local\Temp\GLC5FF6.tmp | — | |
MD5:— | SHA256:— | |||
| 5268 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 5268 | msiexec.exe | C:\Windows\Installer\13f06e.msi | — | |
MD5:— | SHA256:— | |||
| 7136 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\3C3948BE6E525B8A8CEE9FAC91C9E392_D3D55CBE324A29C2A03FC3B24EE172C8 | binary | |
MD5:5BFA51F3A417B98E7443ECA90FC94703 | SHA256:BEBE2853A3485D1C2E5C5BE4249183E0DDAFF9F87DE71652371700A89D937128 | |||
| 7136 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI6B51.tmp | executable | |
MD5:246B351C9B333FAFD274FB83DD087860 | SHA256:56D667605D54FDD13DFC60603050E5076DF0ABBCE818EA4785566412043A1478 | |||
| 7136 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI6BFF.tmp | executable | |
MD5:246B351C9B333FAFD274FB83DD087860 | SHA256:56D667605D54FDD13DFC60603050E5076DF0ABBCE818EA4785566412043A1478 | |||
| 7136 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\60E31627FDA0A46932B0E5948949F2A5 | binary | |
MD5:044CF686D0739662A4DCAF22AFE35071 | SHA256:01A0F9963929183CD52E654381196D8714BBF18E0ABA3B27DC9616D60CDB13AC | |||
| 7136 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI6AC3.tmp | executable | |
MD5:A11D3839094AD12E29A44A57DC423E8C | SHA256:673AF7653C60606F835FCB8CF13438A7896D8A7EA384CB5EE74F149AA5AF6502 | |||
| 7136 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI6C1F.tmp | executable | |
MD5:A11D3839094AD12E29A44A57DC423E8C | SHA256:673AF7653C60606F835FCB8CF13438A7896D8A7EA384CB5EE74F149AA5AF6502 | |||
| 7136 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\3C3948BE6E525B8A8CEE9FAC91C9E392_D3D55CBE324A29C2A03FC3B24EE172C8 | binary | |
MD5:5BDCB7A39CC201F44C66C9E37F0981C6 | SHA256:6279EF5A6CB885C971864F8F97EE01C0D1FCCD99A938FFC5F6CDB583620AC481 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
41
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3220 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3220 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 152.199.19.74:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ%2FxkCfyHfJr7GQ6M658NRZ4SHo%2FAQUCPVR6Pv%2BPT1kNnxoz1t4qN%2B5xTcCEACQCpYx40L3IEwq%2Fvemggs%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://crl.verisign.com/pca3.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3220 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3220 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.130:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
crl.verisign.com |
| whitelisted |
ocsp.verisign.com |
| whitelisted |