| File name: | Bewerbung.exe |
| Full analysis: | https://app.any.run/tasks/e85c6193-c4f0-4c8e-893e-9ffe9df2cd8d |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 08:23:33 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 26117E2DE6B9D91D25E1735F343C00AB |
| SHA1: | F9E2EBA291C9E968A80127F7B4D81D3D30A7A69C |
| SHA256: | 80F9B4CB76905726EDB400CD27DB2D25B4543399A0D6ADF205DEFB79CAB5F023 |
| SSDEEP: | 3072:ksz63zHerVKGLKGXWJmyxC/JRiviIbMooRm:azKn88i7bhow |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 4424)
- powershell.exe (PID: 4172)
Changes powershell execution policy (Bypass)
- Bewerbung.exe (PID: 920)
- powershell.exe (PID: 4424)
Run PowerShell with an invisible window
- powershell.exe (PID: 4172)
Create files in the Startup directory
- powershell.exe (PID: 4424)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 4424)
SUSPICIOUS
Reads security settings of Internet Explorer
- Bewerbung.exe (PID: 920)
The process executes Powershell scripts
- Bewerbung.exe (PID: 920)
Starts POWERSHELL.EXE for commands execution
- Bewerbung.exe (PID: 920)
- powershell.exe (PID: 4424)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 4424)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 4424)
Starts a new process with hidden mode (POWERSHELL)
- powershell.exe (PID: 4424)
Connects to the server without a host name
- powershell.exe (PID: 4424)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 4424)
The process hide an interactive prompt from the user
- powershell.exe (PID: 4424)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 4424)
The process hides Powershell's copyright startup banner
- powershell.exe (PID: 4424)
Application launched itself
- powershell.exe (PID: 4424)
Reverses array data (POWERSHELL)
- powershell.exe (PID: 4424)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4424)
Retrieves command line args for running process (POWERSHELL)
- powershell.exe (PID: 4424)
The process checks if it is being run in the virtual environment
- powershell.exe (PID: 4424)
INFO
Create files in a temporary directory
- Bewerbung.exe (PID: 920)
Checks supported languages
- Bewerbung.exe (PID: 920)
Reads the computer name
- Bewerbung.exe (PID: 920)
Process checks computer location settings
- Bewerbung.exe (PID: 920)
Disables trace logs
- powershell.exe (PID: 4424)
Checks proxy server information
- powershell.exe (PID: 4424)
Auto-launch of the file from Startup directory
- powershell.exe (PID: 4424)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4424)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 4424)
Gets data length (POWERSHELL)
- powershell.exe (PID: 4424)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 4424)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 4424)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 4424)
Reads the software policy settings
- slui.exe (PID: 5344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (61.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.6) |
| .exe | | | Win32 Executable (generic) (10) |
| .exe | | | Win16/32 Executable Delphi generic (4.6) |
| .exe | | | Generic Win/DOS Executable (4.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:02:01 20:22:18+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 65024 |
| InitializedDataSize: | 22528 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
137
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | "C:\Users\admin\AppData\Local\Temp\Bewerbung.exe" | C:\Users\admin\AppData\Local\Temp\Bewerbung.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2656 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
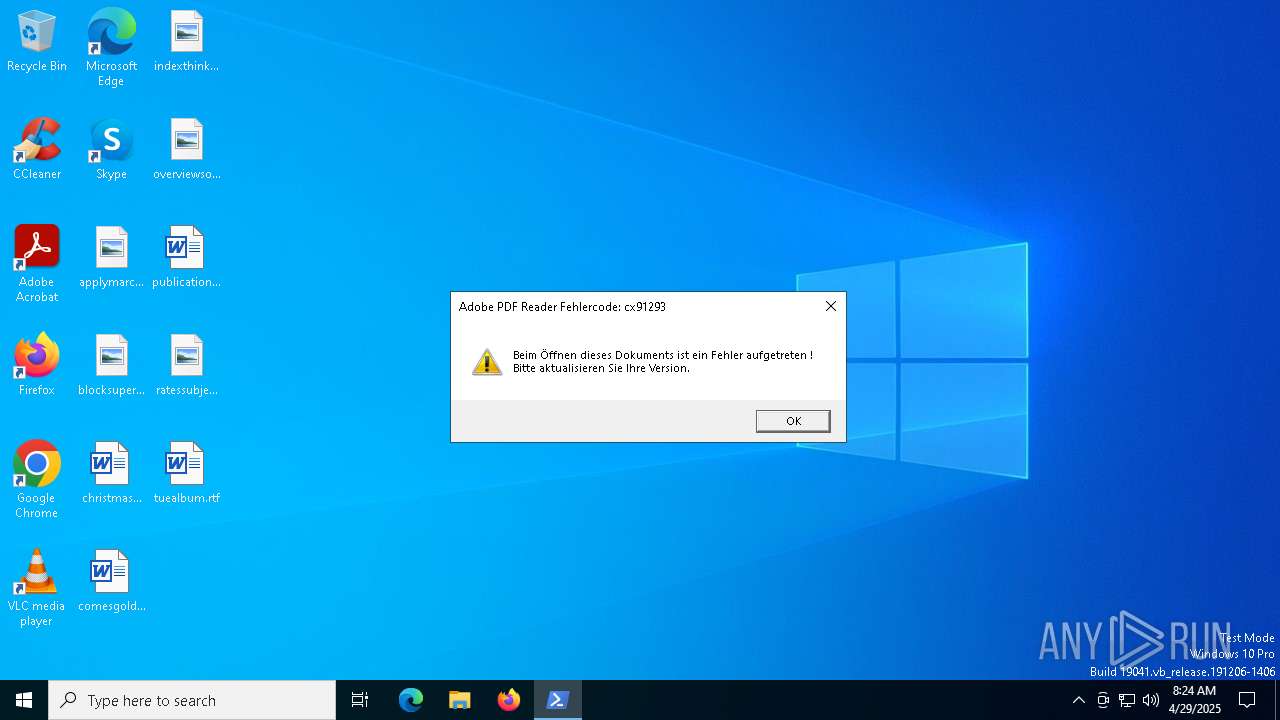
| 4172 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -WindowStyle hidden -NoLogo -NonInteractive -NoProfile -ExecutionPolicy Bypass -Command Add-Type -AssemblyName System.Windows.Forms;[System.Windows.Forms.MessageBox]::Show('Beim Öffnen dieses Dokuments ist ein Fehler aufgetreten ! Bitte aktualisieren Sie Ihre Version.', 'Adobe PDF Reader Fehlercode: cx91293', [System.Windows.Forms.MessageBoxButtons]::OK, [System.Windows.Forms.MessageBoxIcon]::Exclamation);Exit | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4424 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" –NoProfile -ExecutionPolicy Bypass -File C:\Users\admin\AppData\Local\Temp\CD93.tmp\CD94.tmp\CD95.ps1 | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | Bewerbung.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5344 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5512 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5968 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7084 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 278
Read events
11 264
Write events
14
Delete events
0
Modification events
| (PID) Process: | (4424) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4424) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4424) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4424) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4424) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (4424) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (4424) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (4424) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4424) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4424) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
0
Suspicious files
7
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4424 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_avzw0ypn.x33.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4172 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wegovh3p.gw3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4172 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:2562D1F258713870C96380A1EFC6953D | SHA256:CA4788A3EC4D4764A23A27160066675200284AC7FA66046BFADD670C640E6A1B | |||
| 4424 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Windows.lnk | binary | |
MD5:032B5155674EFF19566F5BA401B45C99 | SHA256:243EEA57F37AE38213FC02BD80C1DCDEC466CA9D34244B10B0DF4C0C3F8D3218 | |||
| 4172 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jczmns1y.eo3.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4172 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\JGCRQYW1IER4GX39DJJ8.temp | binary | |
MD5:2562D1F258713870C96380A1EFC6953D | SHA256:CA4788A3EC4D4764A23A27160066675200284AC7FA66046BFADD670C640E6A1B | |||
| 4424 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5ovw0gfv.ihe.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 920 | Bewerbung.exe | C:\Users\admin\AppData\Local\Temp\CD93.tmp\CD94.tmp\CD95.ps1 | binary | |
MD5:0454D9892758512B5CD2C818B66FF3D4 | SHA256:4C977BB417F2183623893957EC856E3C680C196DBAB960175AC5FE5E58EFC8F0 | |||
| 4424 | powershell.exe | C:\Users\admin\AppData\Roaming\2.pdf | binary | |
MD5:6B3CFFA1BC572DD444B852FF99BFCA11 | SHA256:59C146AFB3468B86F759AEBC0420A08E60240D7539AE5A96B70DDB50F7AE6457 | |||
| 4424 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:8E7D26D71A1CAF822C338431F0651251 | SHA256:495E7C4588626236C39124CCE568968E874BEDA950319BA391665B43DE111084 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
27
DNS requests
15
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4424 | powershell.exe | GET | 200 | 83.138.53.186:80 | http://83.138.53.186/1.txt | unknown | — | — | unknown |
4424 | powershell.exe | GET | 200 | 45.15.162.16:80 | http://45.15.162.16/gigant.txt | unknown | — | — | unknown |
4424 | powershell.exe | GET | 200 | 83.138.53.186:80 | http://83.138.53.186/2.pdf | unknown | — | — | unknown |
7036 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7036 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6940 | WmiPrvSE.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl%20 | unknown | — | — | whitelisted |
6940 | WmiPrvSE.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6544 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
— | — | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4424 | powershell.exe | 83.138.53.186:80 | — | HOSTHATCH | NL | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4424 | powershell.exe | Potentially Bad Traffic | ET HUNTING Terse Request for .txt - Likely Hostile |
4424 | powershell.exe | Potentially Bad Traffic | ET ATTACK_RESPONSE PowerShell NoProfile Command Received In Powershell Stagers |
4424 | powershell.exe | Potentially Bad Traffic | ET HUNTING PowerShell NonInteractive Command Common In Powershell Stagers |
4424 | powershell.exe | A Network Trojan was detected | LOADER [ANY.RUN] Gen.Powershell.Downloader Script Payload |
4424 | powershell.exe | Potentially Bad Traffic | ET HUNTING PowerShell Hidden Window Command Common In Powershell Stagers M1 |
4424 | powershell.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host PDF Request |
4424 | powershell.exe | Misc activity | ET INFO Request for PDF via PowerShell |
4424 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |