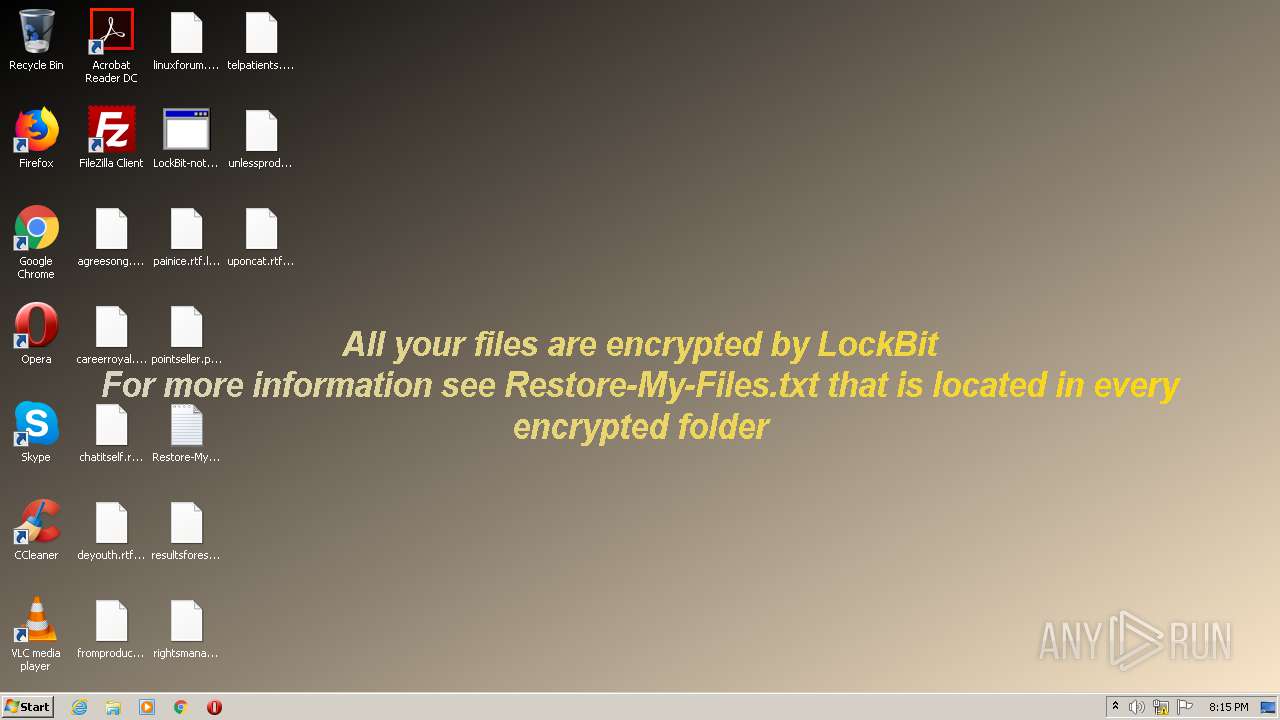
| File name: | Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe |
| Full analysis: | https://app.any.run/tasks/f8843975-bc2a-4293-8790-1dcf14f50e1d |
| Verdict: | Malicious activity |
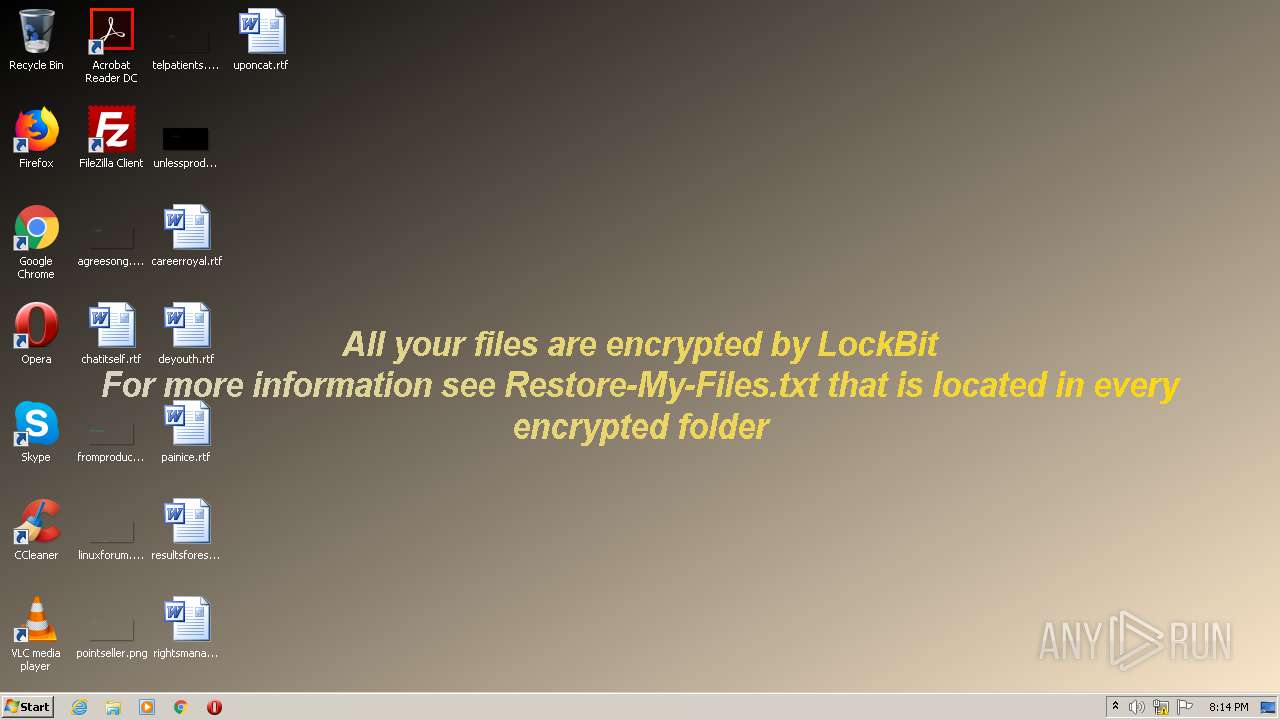
| Threats: | LockBit, a ransomware variant, encrypts data on infected machines, demanding a ransom payment for decryption. Used in targeted attacks, It's a significant risk to organizations. |
| Analysis date: | July 12, 2020, 19:12:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 35E799C0C2B973E3C021558B4E8C79BB |
| SHA1: | D7A0A1C6EF79D32F81AD6940242B31B519F46913 |
| SHA256: | 80F2904D6B331CF689249DF1C73E25EAF49A60960BCCD46BB4A9816137036146 |
| SSDEEP: | 3072:vLkDwmTtinfaDoM1oo+WLMEOig8xNIO54QU+0vf7kJlrbdT031Md3GlWXY:vLk7MTMyoBO3Ff72rbvZGlKY |
MALICIOUS
LOCKBIT was detected
- Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe (PID: 3112)
Starts BCDEDIT.EXE to disable recovery
- cmd.exe (PID: 3844)
- cmd.exe (PID: 2784)
- cmd.exe (PID: 2340)
Deletes shadow copies
- cmd.exe (PID: 2776)
- cmd.exe (PID: 3928)
- cmd.exe (PID: 2340)
Loads the Task Scheduler COM API
- wbengine.exe (PID: 2080)
Renames files like Ransomware
- Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe (PID: 3112)
Changes the autorun value in the registry
- Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe (PID: 3112)
SUSPICIOUS
Uses WEVTUTIL.EXE to clean Windows Eventlog
- cmd.exe (PID: 3204)
- cmd.exe (PID: 2688)
- cmd.exe (PID: 988)
- cmd.exe (PID: 3456)
- cmd.exe (PID: 2812)
- cmd.exe (PID: 652)
Executed as Windows Service
- vssvc.exe (PID: 2036)
- vds.exe (PID: 3956)
- wbengine.exe (PID: 2080)
Executed via COM
- DllHost.exe (PID: 1916)
- DllHost.exe (PID: 1696)
- vdsldr.exe (PID: 1000)
Starts CMD.EXE for commands execution
- Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe (PID: 3112)
Low-level read access rights to disk partition
- vds.exe (PID: 3956)
- wbengine.exe (PID: 2080)
Starts MSHTA.EXE for opening HTA or HTMLS files
- Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe (PID: 3112)
Changes the desktop background image
- Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe (PID: 3112)
Starts CMD.EXE for self-deleting
- Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe (PID: 3112)
Creates files in the Windows directory
- wbadmin.exe (PID: 3992)
Executable content was dropped or overwritten
- Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe (PID: 3112)
Reads Internet Cache Settings
- mshta.exe (PID: 1756)
- mshta.exe (PID: 1984)
Creates files in the program directory
- Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe (PID: 3112)
INFO
Reads internet explorer settings
- mshta.exe (PID: 1984)
- mshta.exe (PID: 1756)
Manual execution by user
- mshta.exe (PID: 1756)
Dropped object may contain Bitcoin addresses
- Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe (PID: 3112)
Dropped object may contain TOR URL's
- Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe (PID: 3112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:05:11 11:03:38+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 104960 |
| InitializedDataSize: | 8853504 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5b0c |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.1 |
| ProductVersionNumber: | 1.0.0.1 |
| FileFlagsMask: | 0x006f |
| FileFlags: | Pre-release, Patched |
| FileOS: | Unknown (0x40304) |
| ObjectFileType: | Static library |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileVersionz: | 1.2.6.1 |
| InternalSurnames: | edzgkphvesw.ixe |
| Copyright: | Copyrighd (C) 2020, odfrjv |
| ProductVersion: | 1.0.4.4 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 11-May-2019 09:03:38 |
| Detected languages: |
|
| FileVersionz: | 1.2.6.1 |
| InternalSurnames: | edzgkphvesw.ixe |
| Copyright: | Copyrighd (C) 2020, odfrjv |
| ProductVersion: | 1.0.4.4 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 11-May-2019 09:03:38 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x0086C000 | 0x00016380 | 0x00015600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99129 |
.rdata | 0x0001B000 | 0x00008640 | 0x00008800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.68293 |
.data | 0x00024000 | 0x00847828 | 0x00005800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.45526 |
.rsrc | 0x00883000 | 0x0000A3F0 | 0x0000A400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.48961 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.42278 | 480 | UNKNOWN | UNKNOWN | RT_VERSION |
2 | 5.757 | 1384 | UNKNOWN | Swedish - Finland | RT_ICON |
3 | 5.14688 | 9640 | UNKNOWN | Swedish - Finland | RT_ICON |
4 | 6.75868 | 1128 | UNKNOWN | Swedish - Finland | RT_ICON |
5 | 4.94699 | 3752 | UNKNOWN | Swedish - Finland | RT_ICON |
6 | 5.7251 | 2216 | UNKNOWN | Swedish - Finland | RT_ICON |
7 | 5.1288 | 1384 | UNKNOWN | Swedish - Finland | RT_ICON |
8 | 4.94601 | 9640 | UNKNOWN | Swedish - Finland | RT_ICON |
9 | 5.41822 | 4264 | UNKNOWN | Swedish - Finland | RT_ICON |
10 | 5.46054 | 2440 | UNKNOWN | Swedish - Finland | RT_ICON |
Imports
KERNEL32.dll |
Total processes
120
Monitored processes
55
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 376 | /c wbadmin DELETE SYSTEMSTATEBACKUP | C:\Windows\system32\cmd.exe | — | Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 4294967293 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 392 | /c wmic SHADOWCOPY /nointeractive | C:\Windows\system32\cmd.exe | — | Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 44124 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 652 | /c wevtutil cl application | C:\Windows\system32\cmd.exe | — | Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 852 | "C:\Users\admin\AppData\Local\Temp\Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe" | C:\Users\admin\AppData\Local\Temp\Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 892 | /c bcdedit /set {default} bootstatuspolicy ignoreallfailures | C:\Windows\system32\cmd.exe | — | Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 988 | /c wevtutil cl application | C:\Windows\system32\cmd.exe | — | Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1000 | C:\Windows\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1112 | bcdedit /set {default} recoveryenabled no | C:\Windows\system32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1480 | bcdedit /set {default} bootstatuspolicy ignoreallfailures | C:\Windows\system32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1696 | C:\Windows\system32\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 046
Read events
997
Write events
48
Delete events
1
Modification events
| (PID) Process: | (1696) DllHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ICM\Calibration |
| Operation: | write | Name: | DisplayCalibrator |
Value: C:\Users\admin\AppData\Local\Temp\Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | |||
| (PID) Process: | (1916) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1916) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3112) Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | XO1XADpO01 |
Value: "C:\Users\admin\AppData\Local\Temp\Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe" | |||
| (PID) Process: | (3112) Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3112) Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3112) Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | Key: | HKEY_CURRENT_USER\Software\LockBit |
| Operation: | write | Name: | full |
Value: 7591A1C72B18808CBC5C211669617D3B45EF6CC2ED3A25643CB59D65B9DB427FFEACD20409788A578B4E8D5E2E116B5CB4DF5AE8E54506C1684FA3A5553D8B4B479D55BE17331653BB9CF9E09E59E5C3BAFAE64C939635A495EE4FDBB030C3873809B8426C49B74826404C2503F342BFF0E27ECD89A41699F3E258DC1D4D7D2A0E57EC88FF407AAD592C4268CDBD3ADE7F9E8DD5B977F251D2486C41D559A55D70E0DCD33438E900C39C3FDE21191AEF0BE78F45474A811CD934B444042BC683C306FD97ACC830BA41F9AD2CC3EED01724F9C8E9F65BCCAC6000B0FF726368387C8A90528064BF43971D93D37D6E007D1CC73CA0A1F393F3C213384604070FDB2F42A0A1DE7A92CDF12D7BB87B42F86C2239FA6D33877DCA00500531F3BF49E34E3A0C96076380207DD1148908CFE73CCDF790D12C2ED8BAE242410B54AB6132ADB4E1C9E2942ECC1DFDFBECFC2FD8C750C10A05B2527DC18B84194F488432AB0A61CF99E06433A9835348CD9284B30D8BE352999B53D377ADA9DAEFBAA1E4A936497CF5B41FD069B24CDD0385919395ADAB2D29334E662759093B23A752A4CD91C2411583169EC609DE0C1ABB2D9D1908FCD0CD05A4C22D846E0EC4D0DBA79B6836CE22D20ABFAEAE6805FDAE8468EF8F330131F2C3B34D8E928889D5F94F09709A1A3AE1CCCD6EB9B962C088AC7EB16E4E9E8F487371CFEEC7ECF42FD95CBC542AB07C25FB7D810AE2B35DCC589EE4AA1F98BDAABF7EE88B1C41C90B6C275FA13110F746EF5F4D94950A080B043F2E3562DCC40724C103EDD338E22EEA5D90015E8C4F745E03DA019FC349D53E9811DC482B12FBC02C2CA682CDE27AD32967BCD2DD53341CF3FF1A4B7A9F0FD501B31AD2DF0F4208689228553A35AE5FF540F976DF8D410CEA5619EB57852047B24CC728829EE38E19BFC72F2032E6D47A22EC55FCF03B091E22E8E6B08B7C88B0FA6196EAEB1998537F44D6FDF43DE2DD03AC6E311CFEF55ABEA9916B6AD101B5730434D7EAA1DCBA83AC6A5F1F9F9104A716909B6B422F5461C25D3A84DF61749429B04360CD683295637BF93D37E598F0A5A70D1C1E477790F0F16BFEE8ACF91B879543C3EC7168CC9B160950A2F762322F0F0B4D6894630E4B6DF97E7B00125D39152B4E0214A4CE76B1447FDB82B781206A6596C5922800C11D50AC1C2ECC347B3587F1F3DF7B43694639A933213CCFCD071A814BBC298463A8AA71932096F6BC4603B514D2AD9627AF58FB96A0B9A8C5BBB6BFCBAA76EA084FF433B2F8B2C89481235822051F1CDA8D238AA80824AEA7DFD9772433E2148949C3E92BDA514939247A2A6148D60558488DFBB582BEBCFF86251A4B52AC0F4B472A44071E36FC3F5E841C4FA4A306C3139DDF2721D7D8287755378F27405E5492F19F462EAEDB62AC4ABEE1F3910EFFF74E15C12D29AA576C1B33B084172E8504FB85BCF24C440687710F95DEE4459F4F7AC4F024464F9D82ECC3CDB358FDEE9A72888B352B79DB5A92A422000F593BF1C68E9EC3AB87E9D5903E9A7042056C4FE97297E8B9DCFD88143227A16688D879D773DC5462E9E6322D21988DDD3B2BF508FBD57F571CA071333547B7E08400D5CDB77EDEC15099C2CC11CD4D45E832A4224D8069B07CE30DF802198A10525DA6457094DF434BBDA67A7D0B4442A851D88CC2BFCB675C69E3B0D62D96886DB1AC7E9DEB58DB64488ADA630609844AFE051A6EB5A6A478336415DDF99525A19F97A1BDE293E010BC346086AD7F3732DAC36F124BE7B000A95FBDA85CA089AF98CD73D8B4A1819B | |||
| (PID) Process: | (3112) Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | Key: | HKEY_CURRENT_USER\Software\LockBit |
| Operation: | write | Name: | Public |
Value: D197B7C6B5E8AF66064D06C7E7EC9535C79AA5BF8B0FEBEEF7B71D408C6A95C05E8D665B7A32484FB8AD794E56FA9D581284CA0FFD4720B561D4DA630F955829A42F8FF6B584E617BC5ECB33DF3524779DF1B679E16F967174517B7B33AE0A0F3F4BB72838F59366927AE7138FF85C64271FF6905FE1FE1629F06677B710322ED35109F3B8E9AE29AB32A58499D29F1302D7F6A2CE7B949B89DB4E433078D1572F1BC470FC77B179849B4FD56F12C97DBA7DB291390898C6BB38BA3D694343B7914D23F30CA91061279DA9AD2E683A7F576B696F155A4C591F643BC26811D6C86CA277C45A18CF65FF76937B6AFAD38DEC79C2679457E1DCBAAFF6D78E38AFA3010001 | |||
| (PID) Process: | (2168) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\16000009 |
| Operation: | write | Name: | Element |
Value: 00 | |||
| (PID) Process: | (1480) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\250000e0 |
| Operation: | write | Name: | Element |
Value: 0100000000000000 | |||
Executable files
1
Suspicious files
13 261
Text files
1 691
Unknown types
383
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3112 | Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | C:\Program Files\Adobe\Acrobat Reader DC\Leame.htm.lockbit | binary | |
MD5:— | SHA256:— | |||
| 3112 | Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | C:\Program Files\Adobe\Acrobat Reader DC\Benioku.htm.lockbit | binary | |
MD5:— | SHA256:— | |||
| 3112 | Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | C:\Program Files\Adobe\Acrobat Reader DC\LeiaMe.htm.lockbit | binary | |
MD5:— | SHA256:— | |||
| 3112 | Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | C:\Program Files\Adobe\Acrobat Reader DC\Lisezmoi.htm.lockbit | binary | |
MD5:— | SHA256:— | |||
| 3112 | Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | C:\Program Files\Adobe\Acrobat Reader DC\LeesMij.htm.lockbit | binary | |
MD5:— | SHA256:— | |||
| 3112 | Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | C:\Program Files\Adobe\Acrobat Reader DC\IrakHau.htm.lockbit | binary | |
MD5:— | SHA256:— | |||
| 3112 | Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | C:\Program Files\Adobe\Acrobat Reader DC\Berime.htm.lockbit | binary | |
MD5:— | SHA256:— | |||
| 3112 | Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | C:\Program Files\Adobe\Acrobat Reader DC\Restore-My-Files.txt | text | |
MD5:— | SHA256:— | |||
| 3112 | Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | C:\Program Files\Adobe\Acrobat Reader DC\Liesmich.htm.lockbit | binary | |
MD5:— | SHA256:— | |||
| 3112 | Trojan.Autorun.ATA_virussign.com_35e799c0c2b973e3c021558b4e8c79bb.exe | C:\Program Files\Adobe\Acrobat Reader DC\Leggimi.htm.lockbit | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report