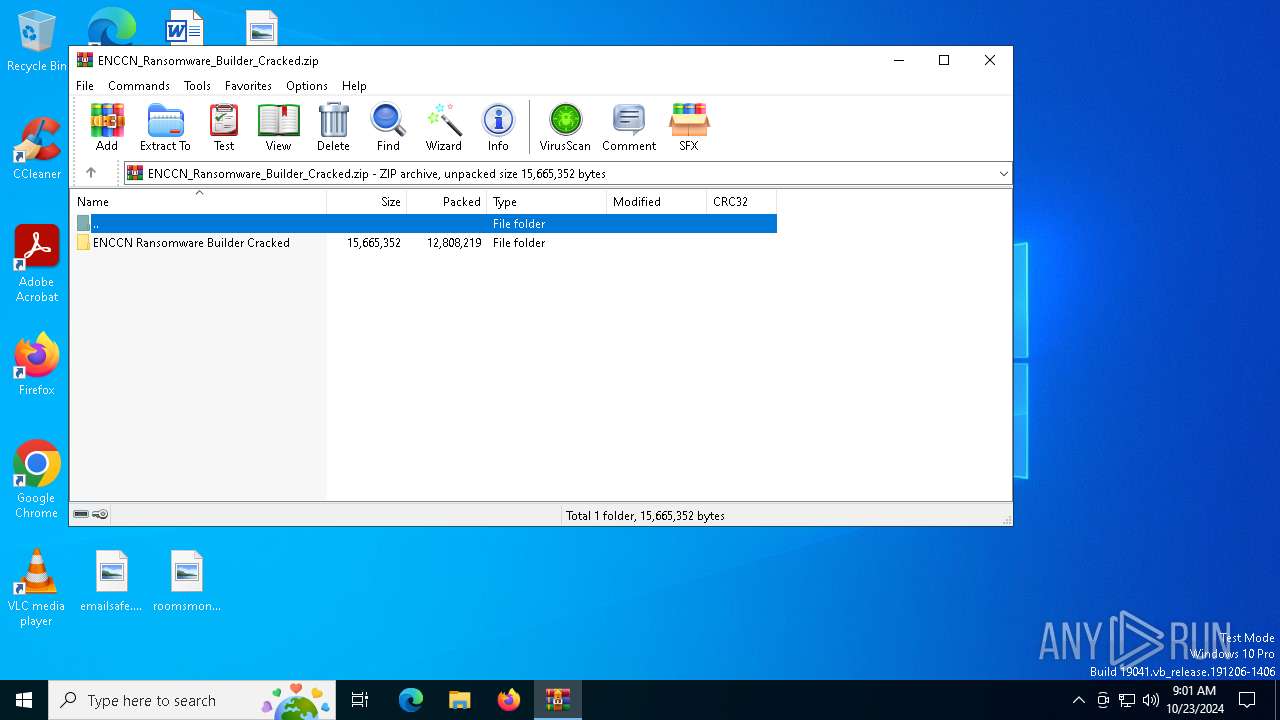
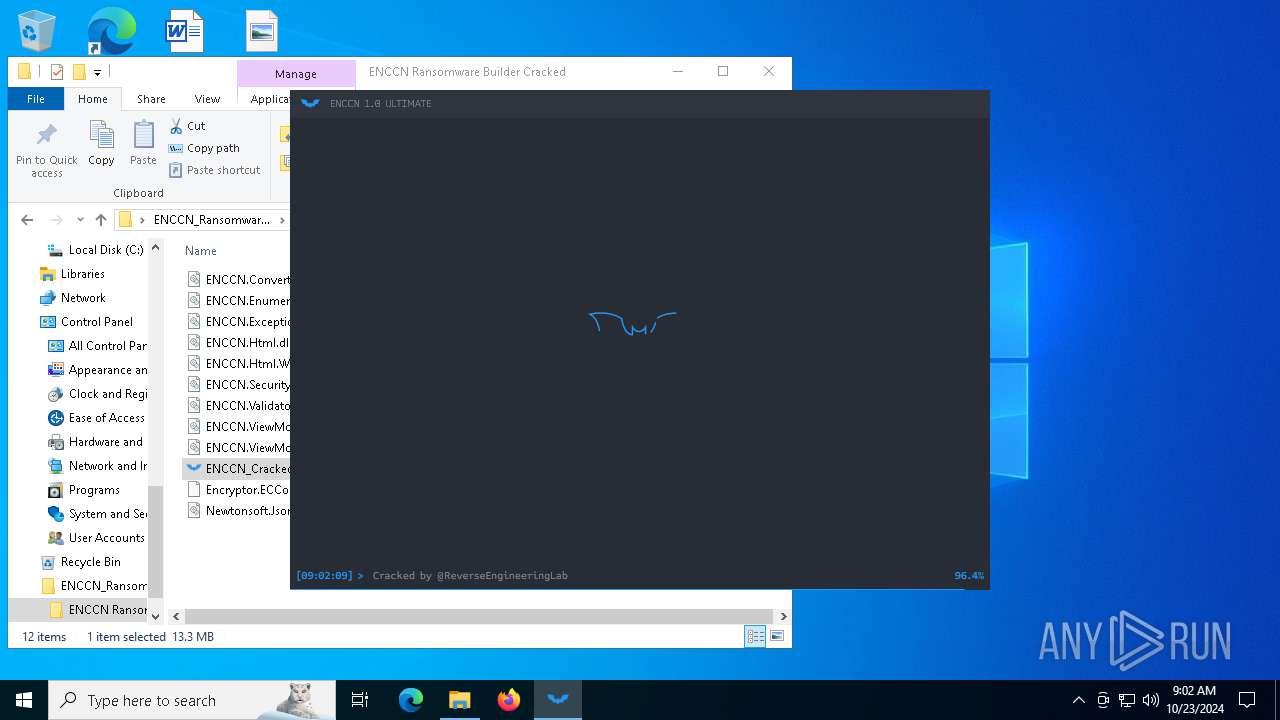
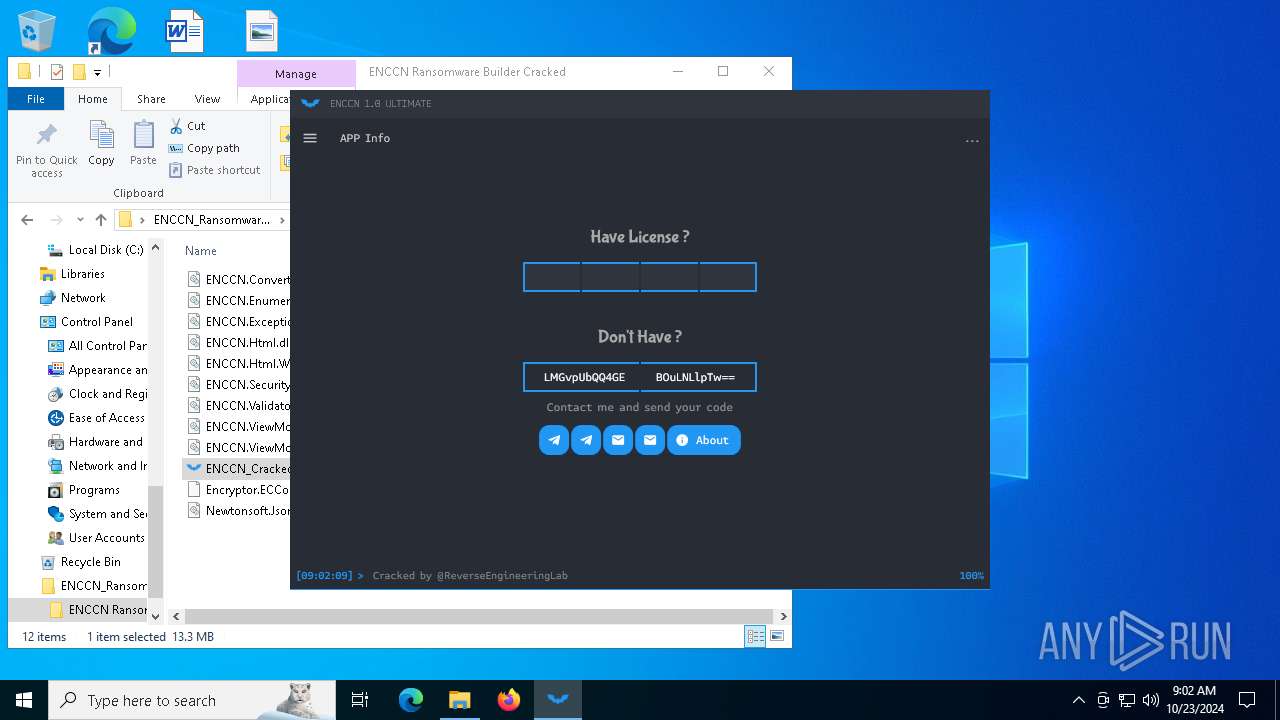
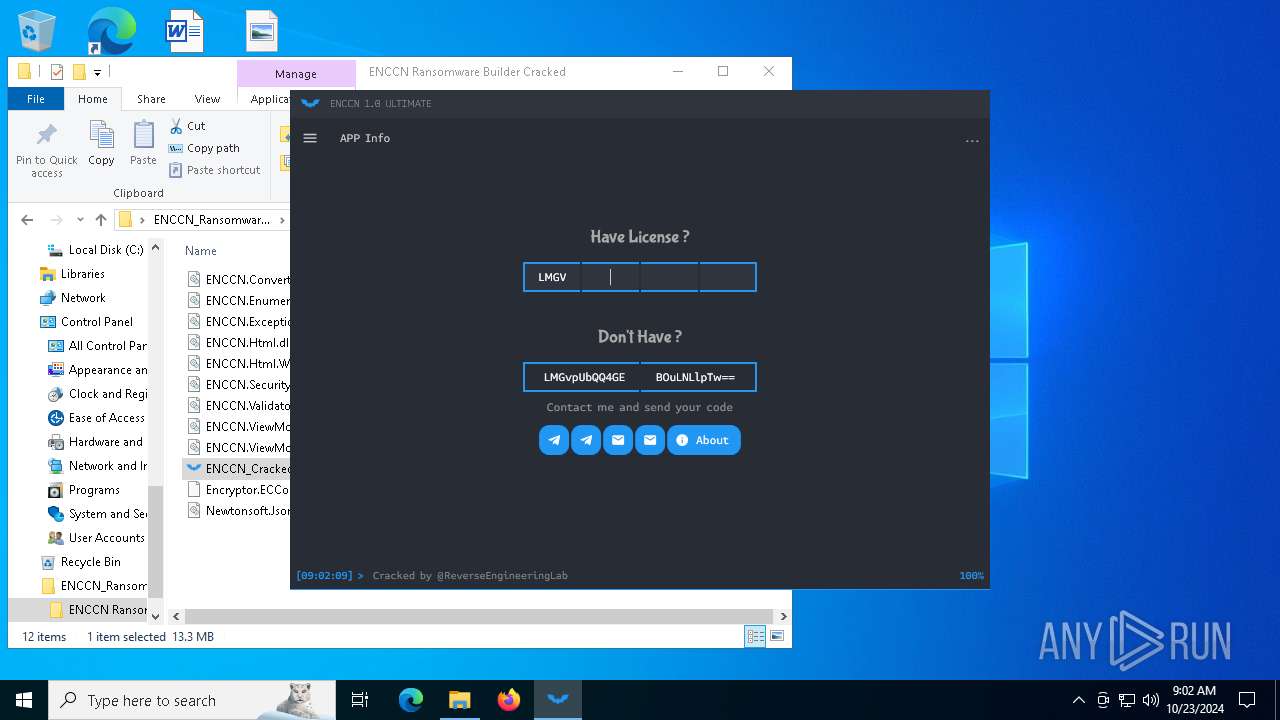
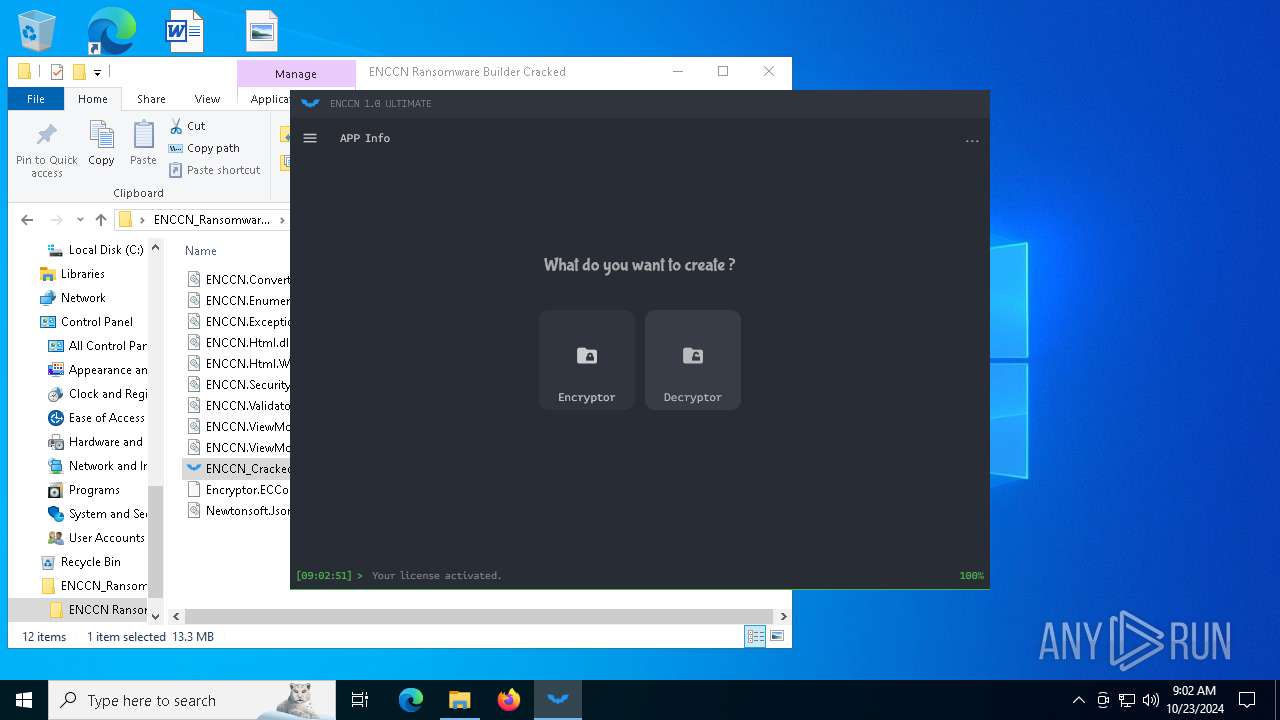
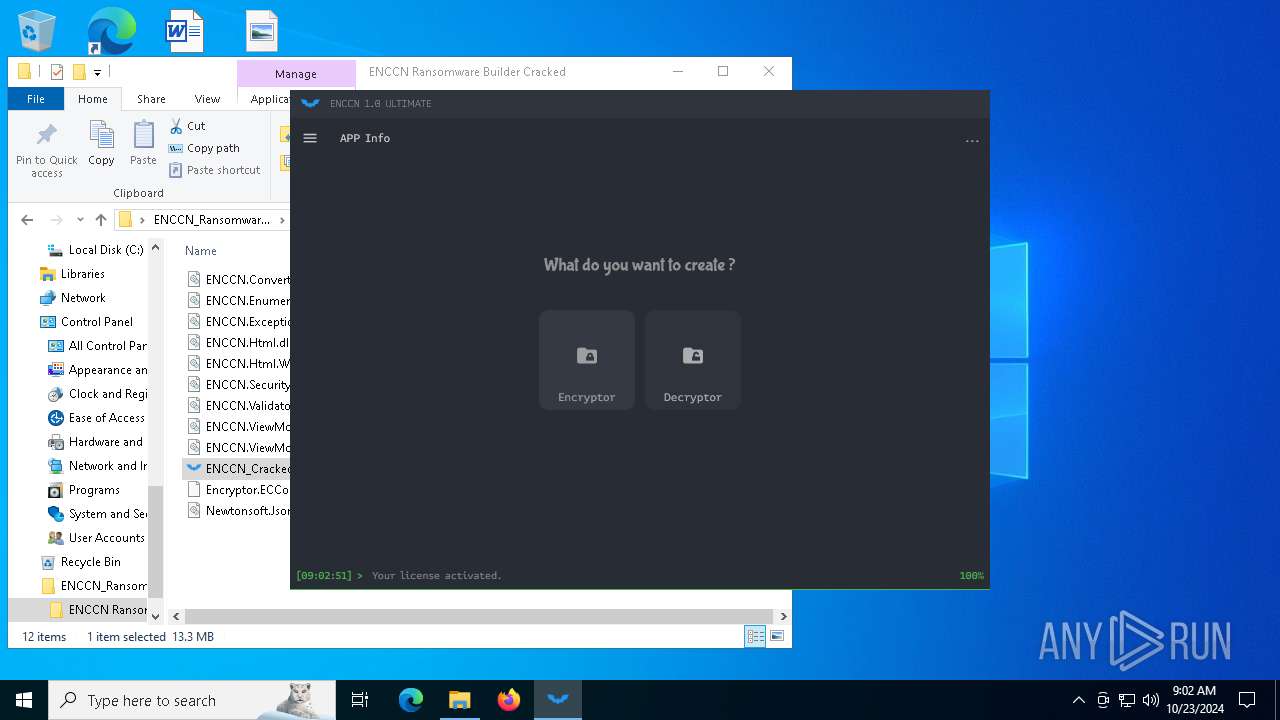
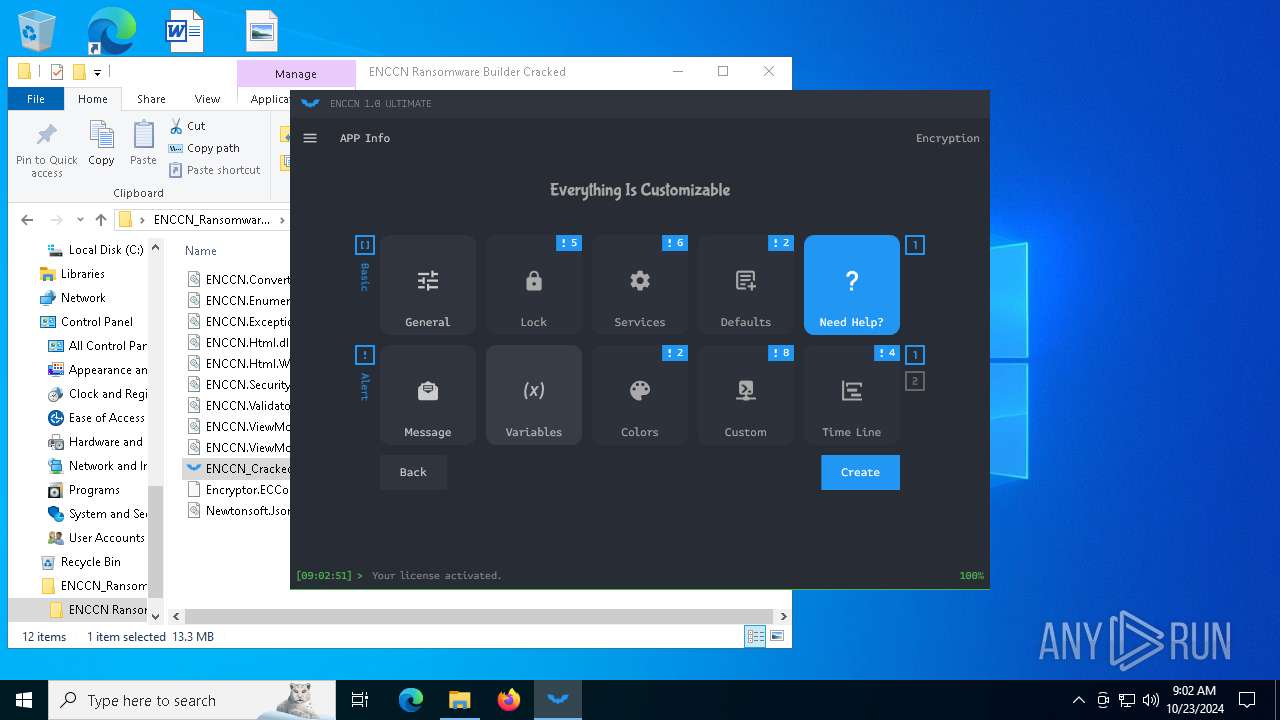
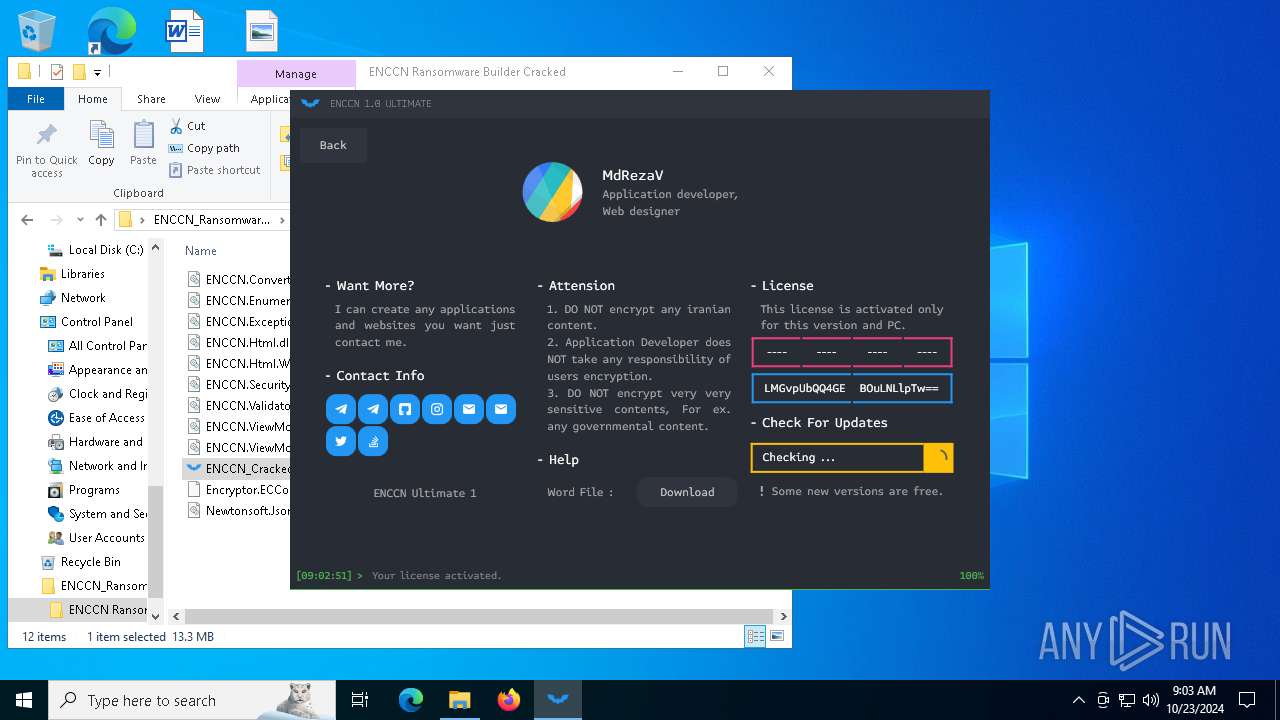
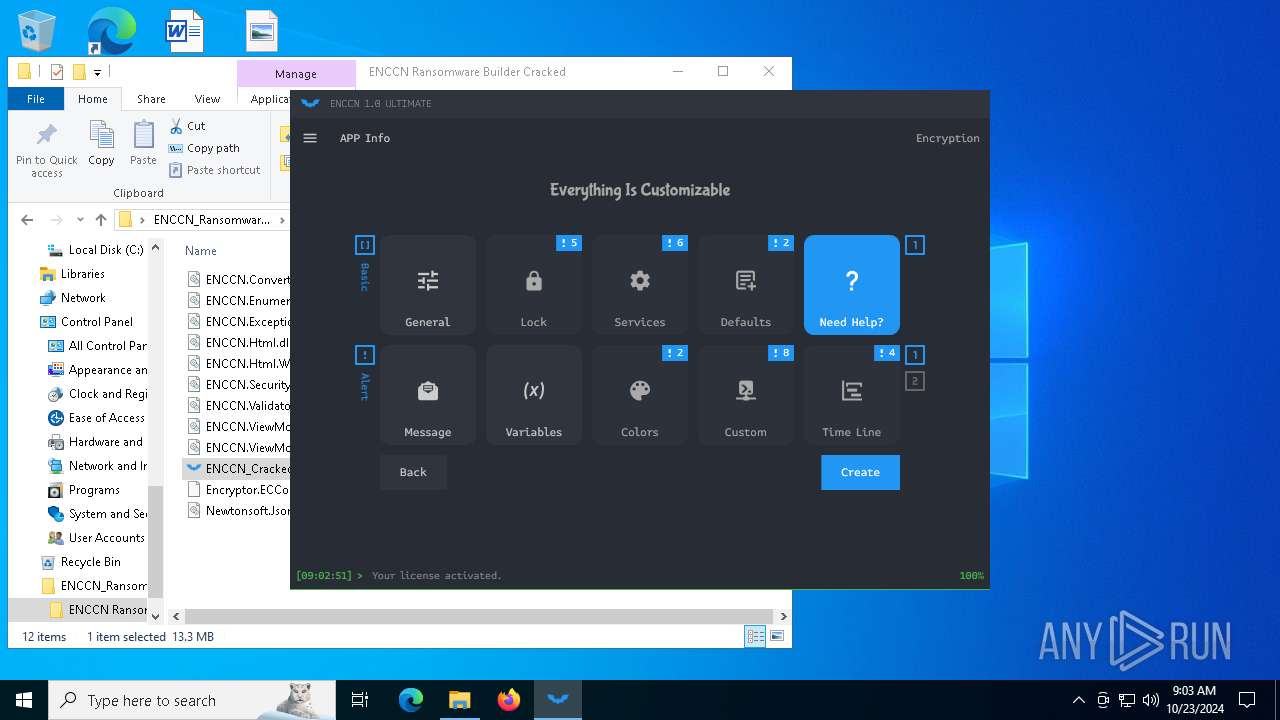
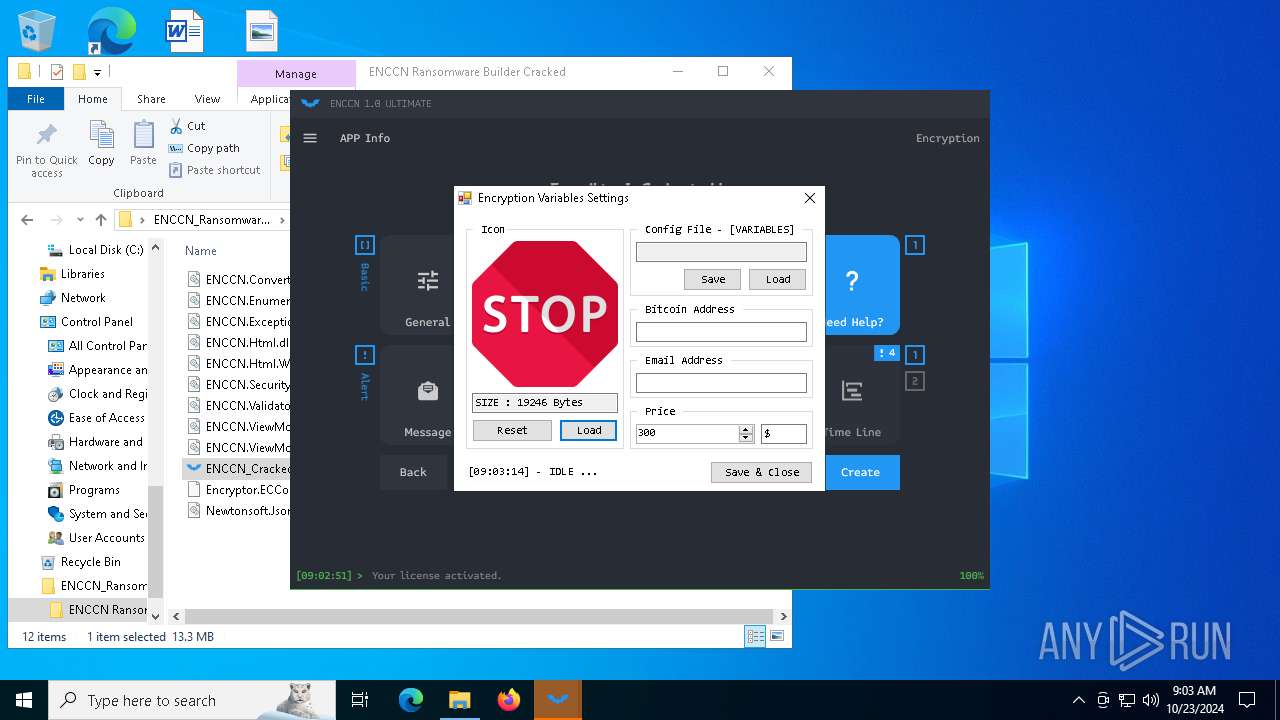
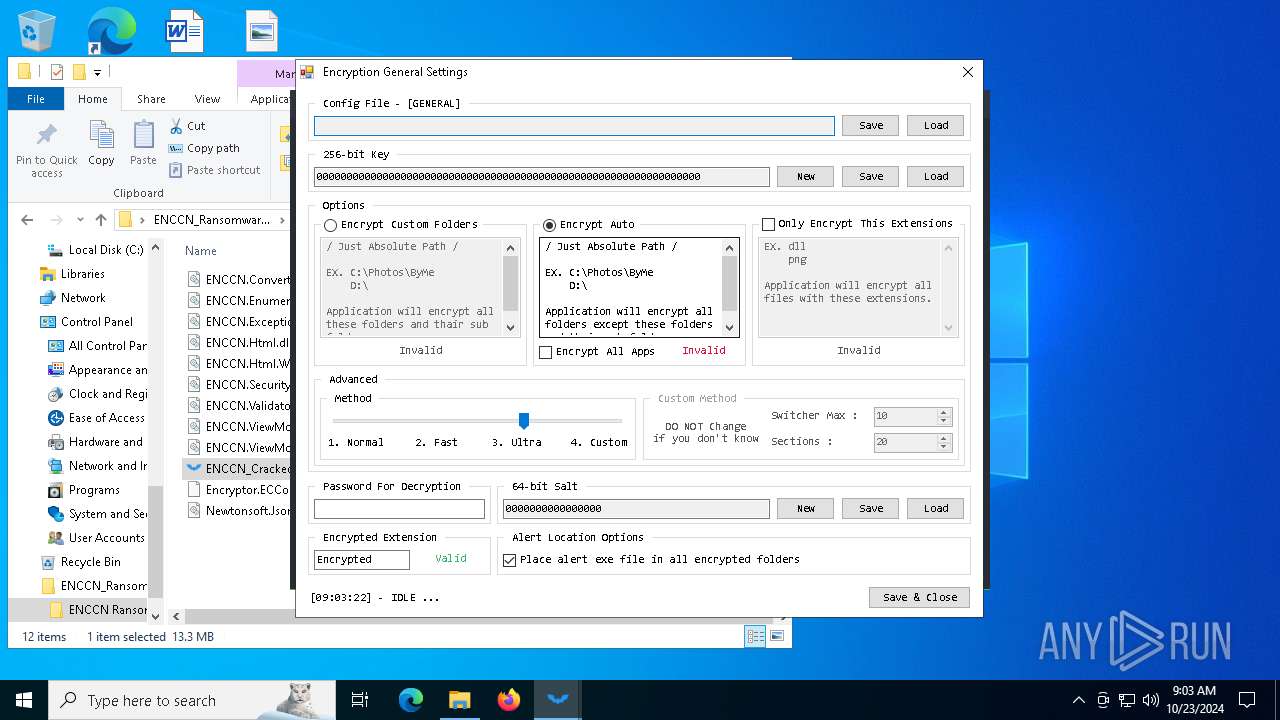
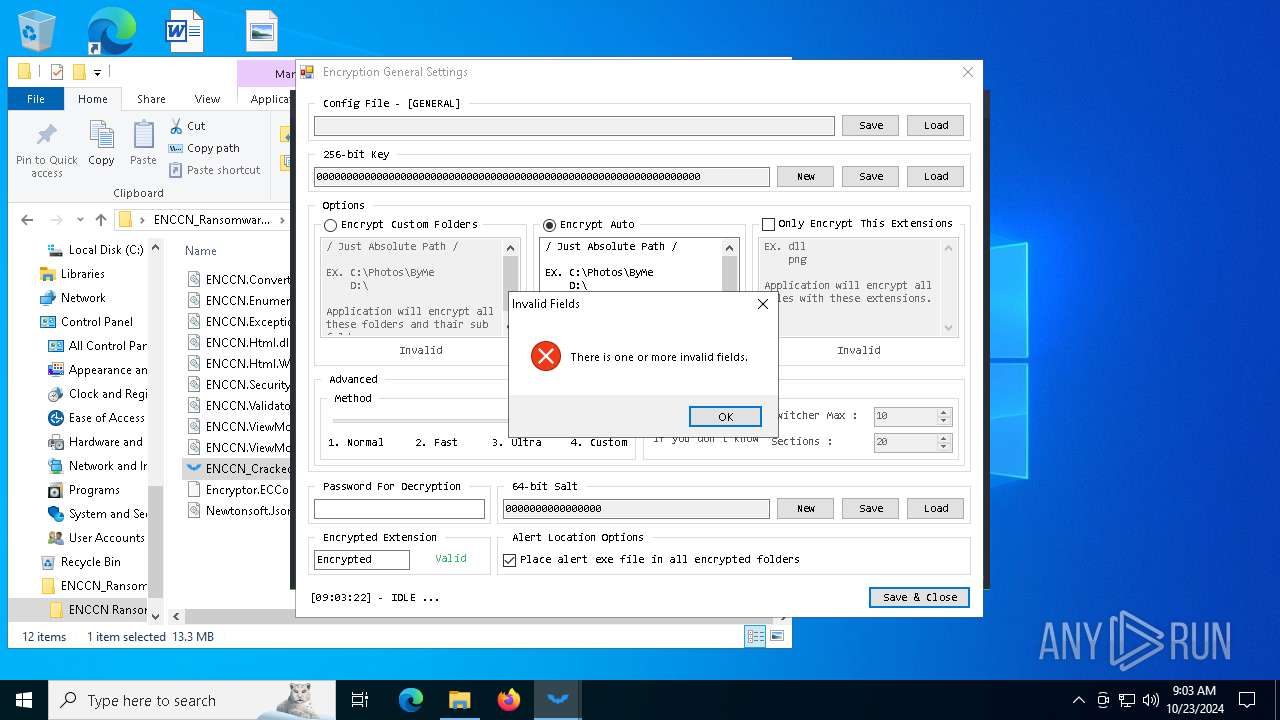
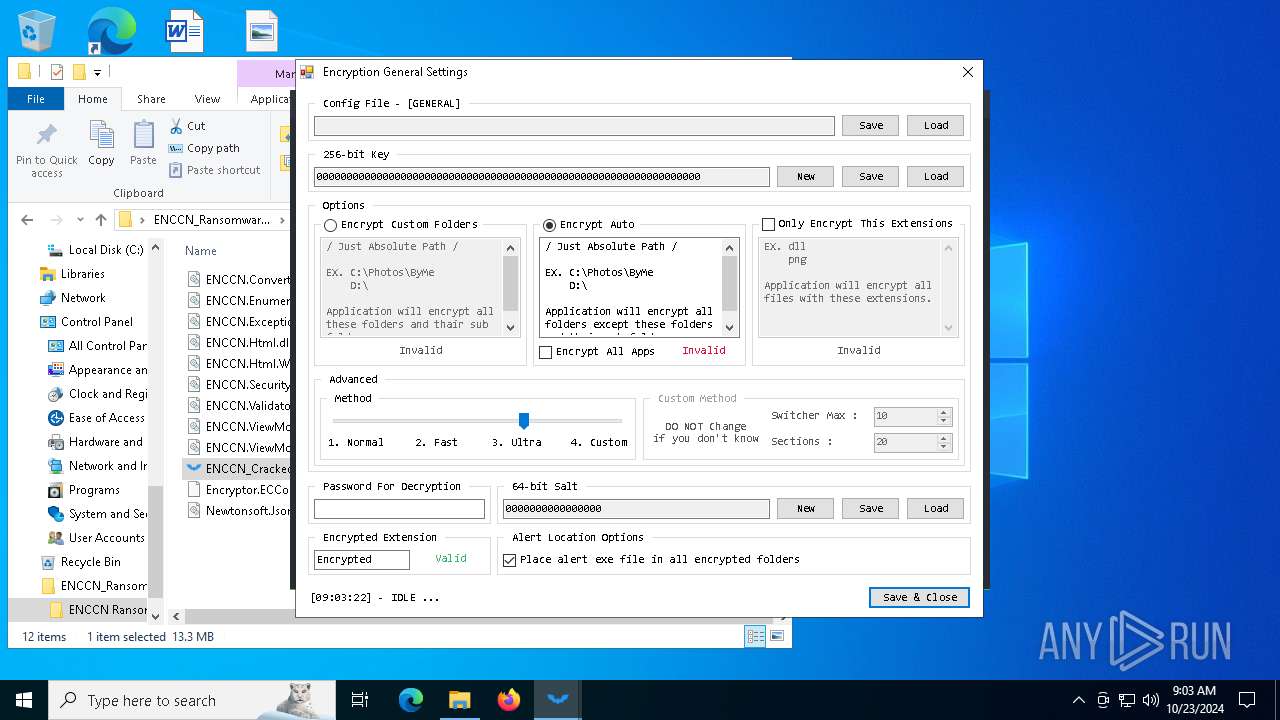
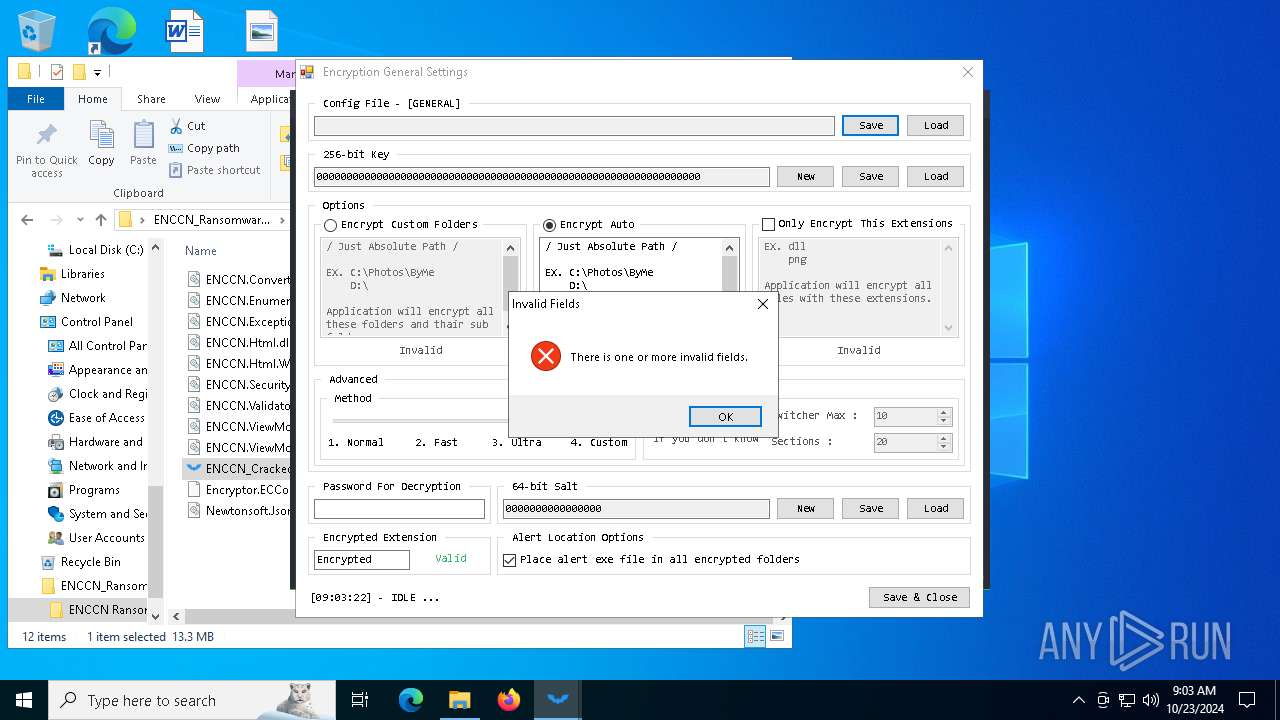
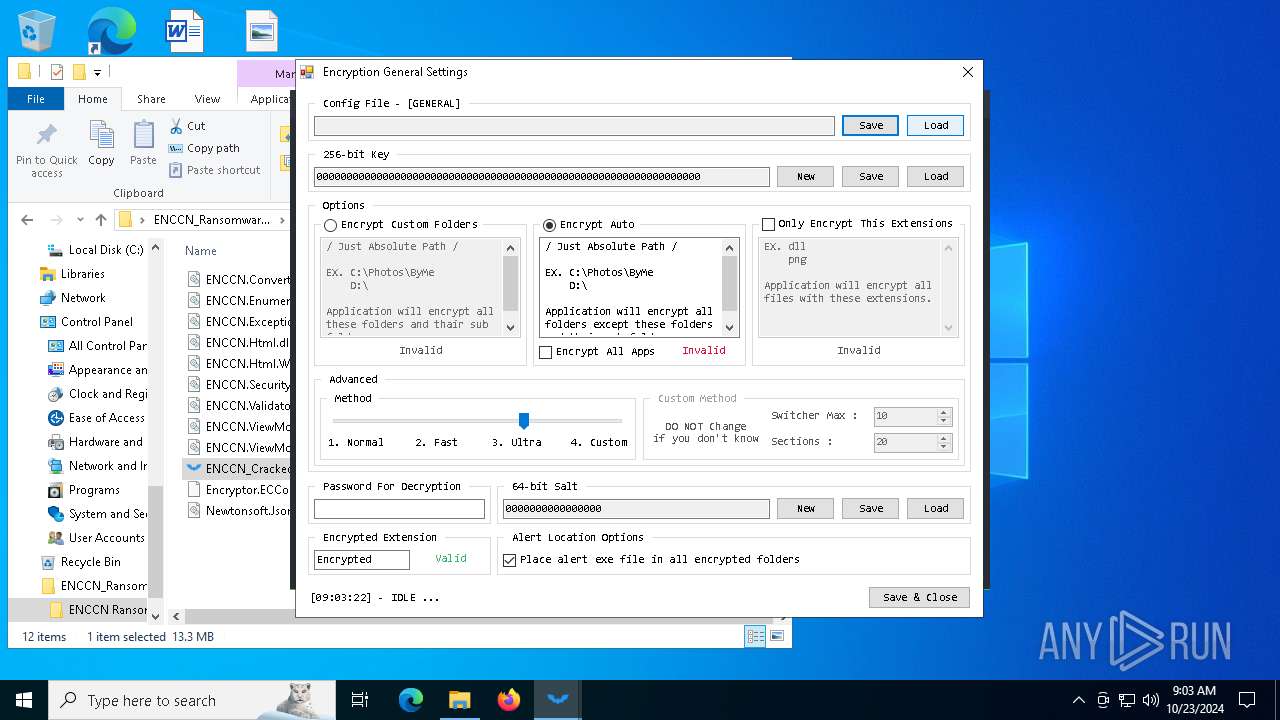
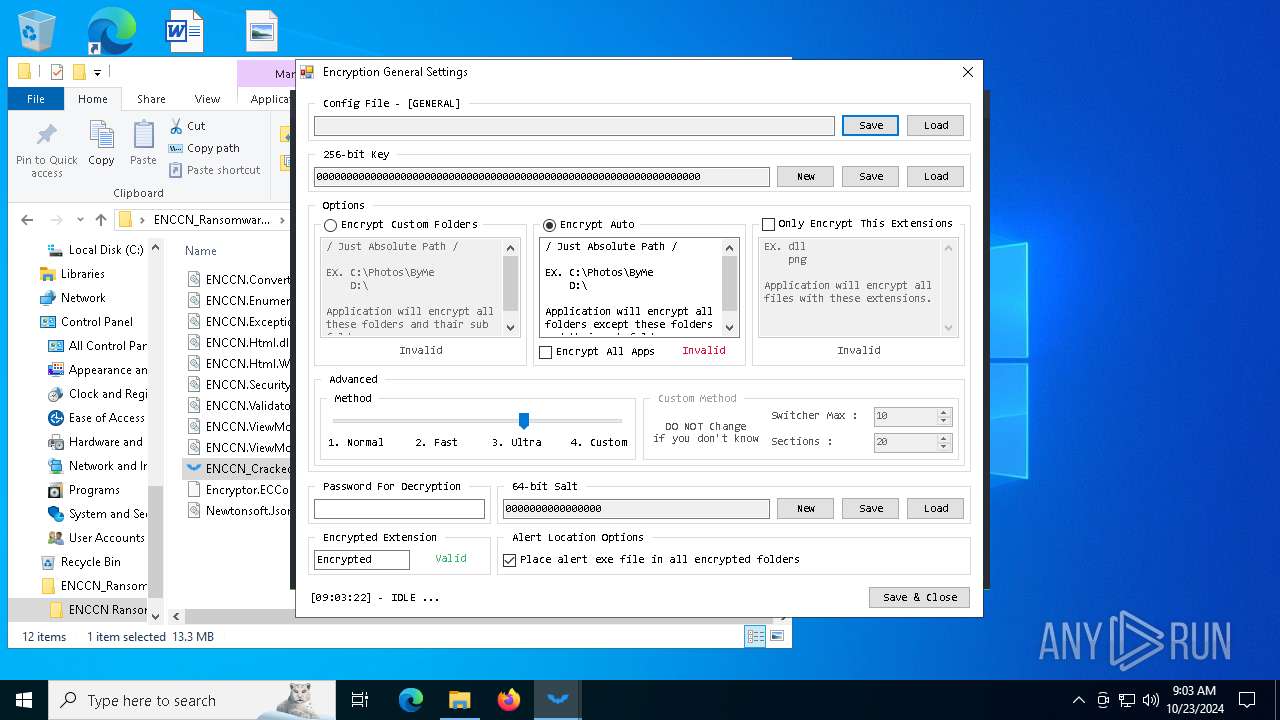
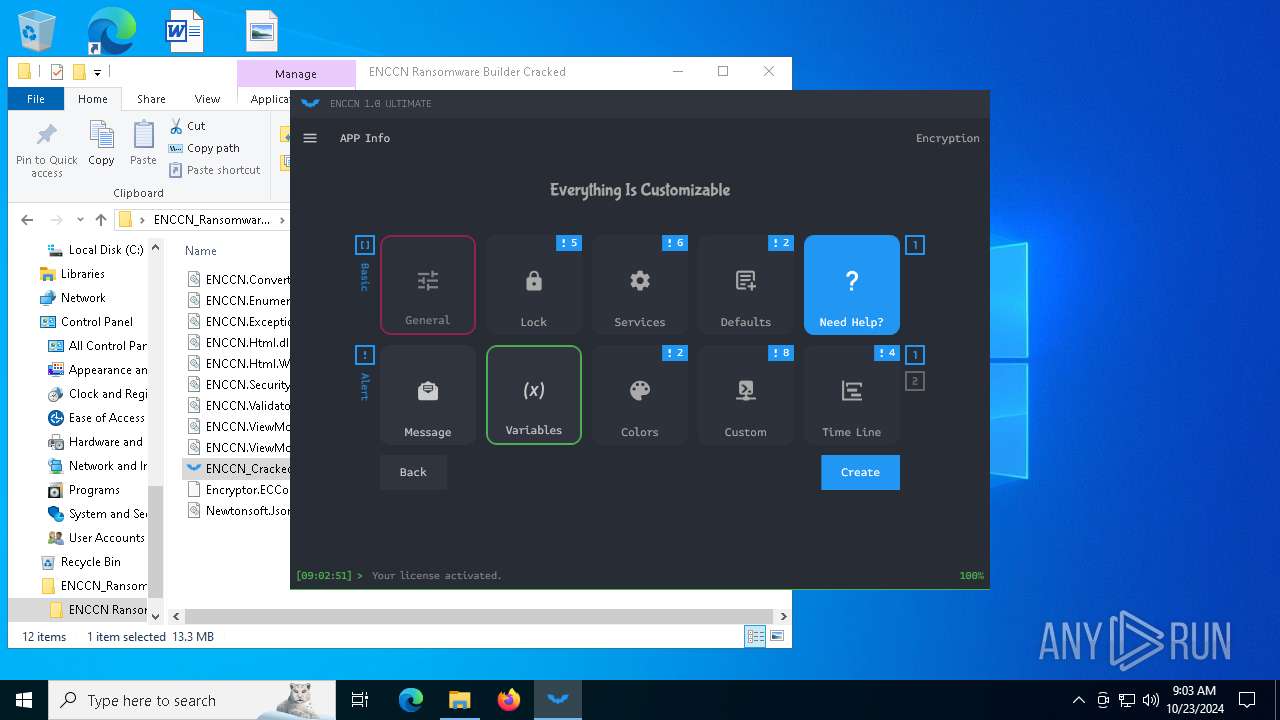
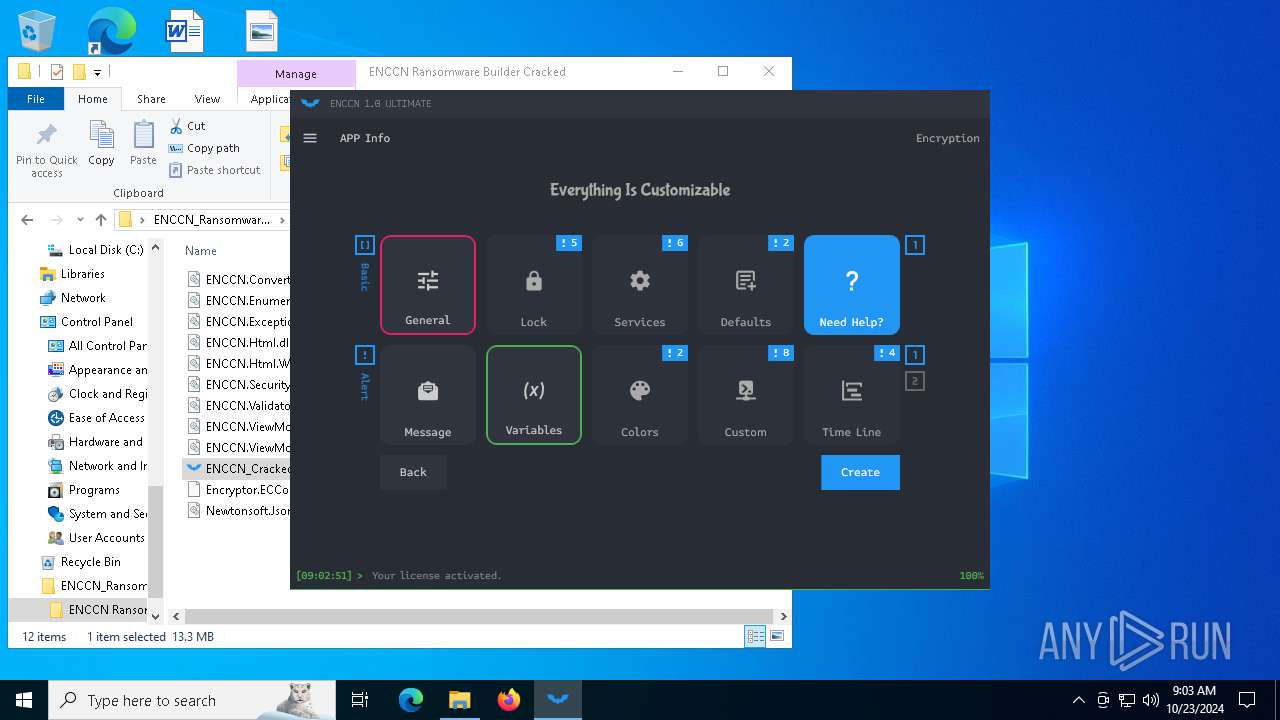
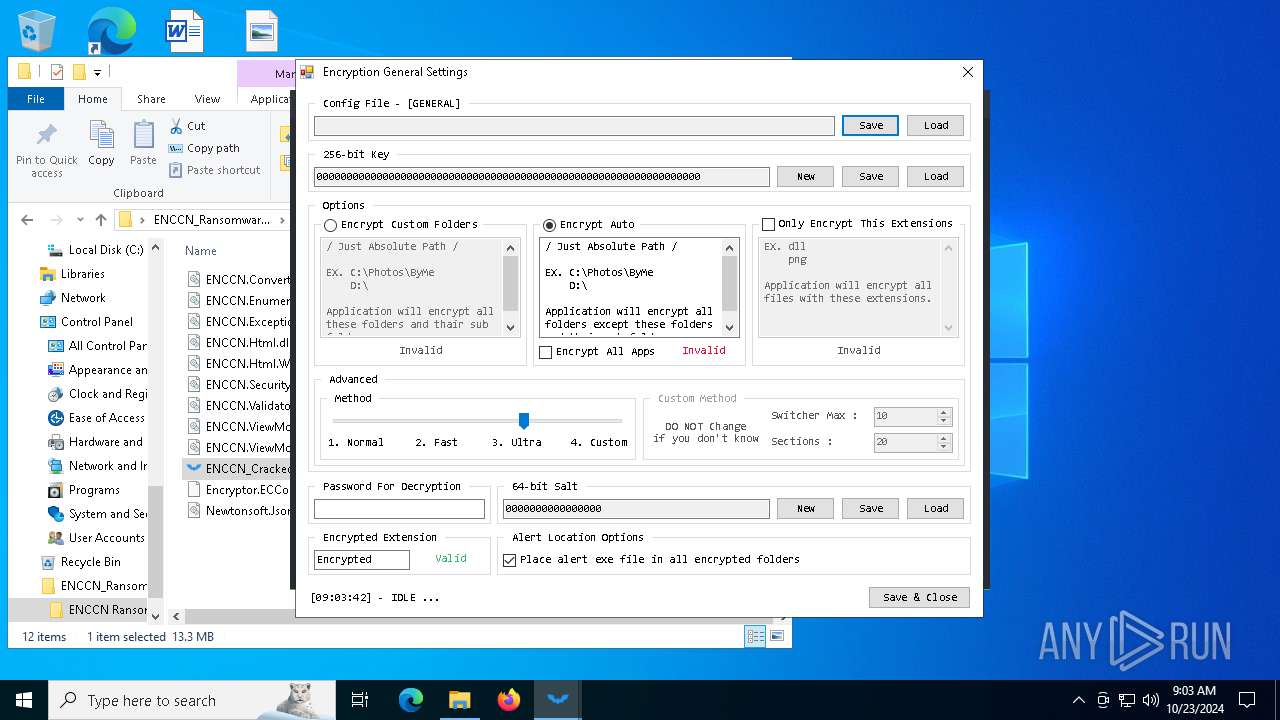
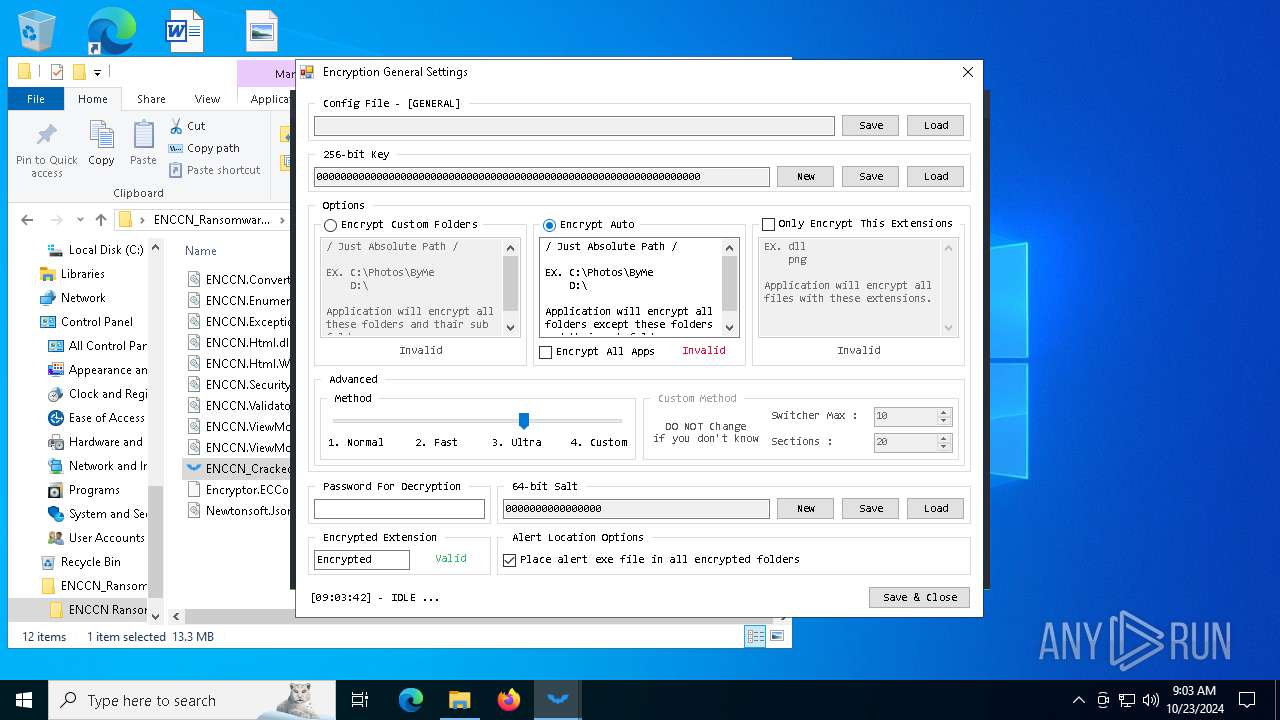
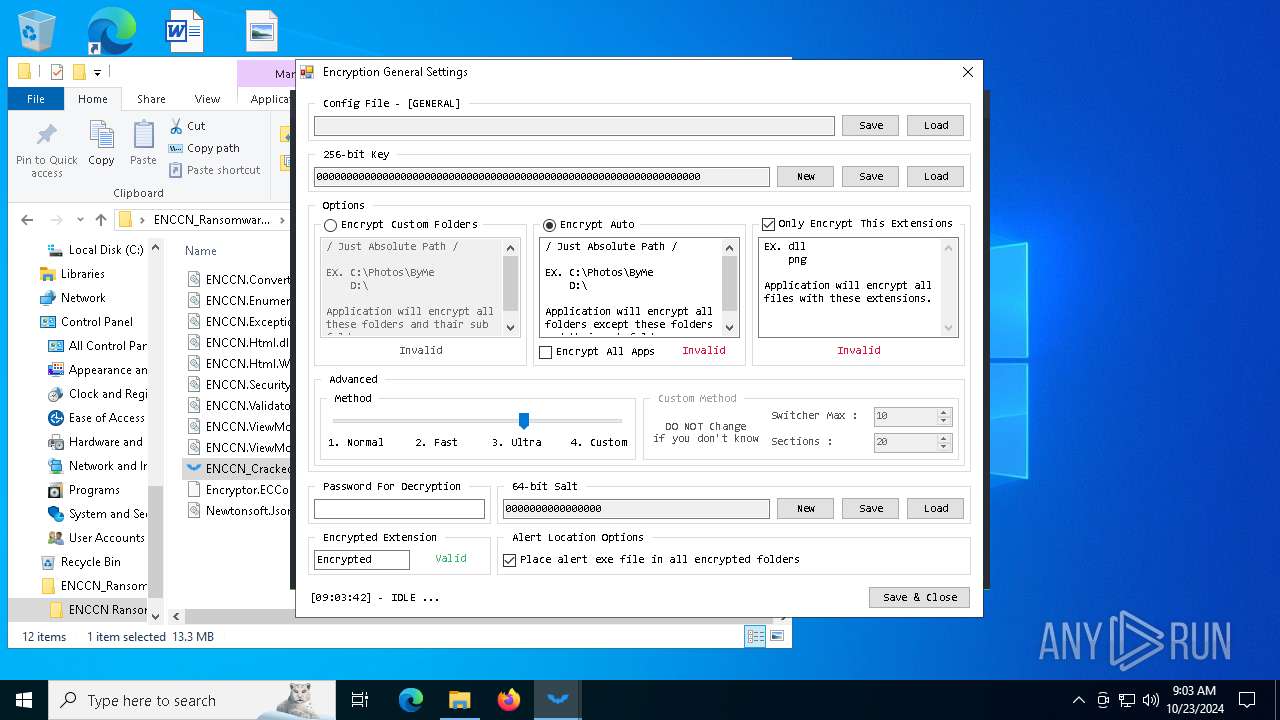
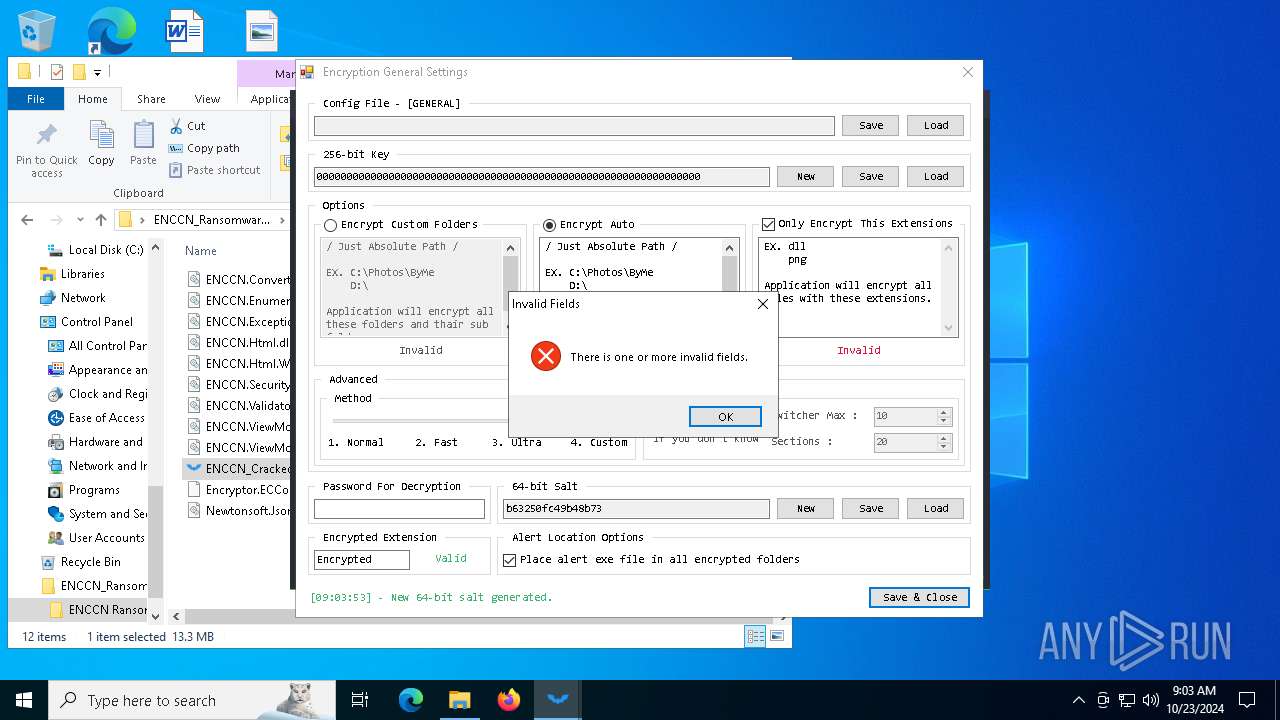
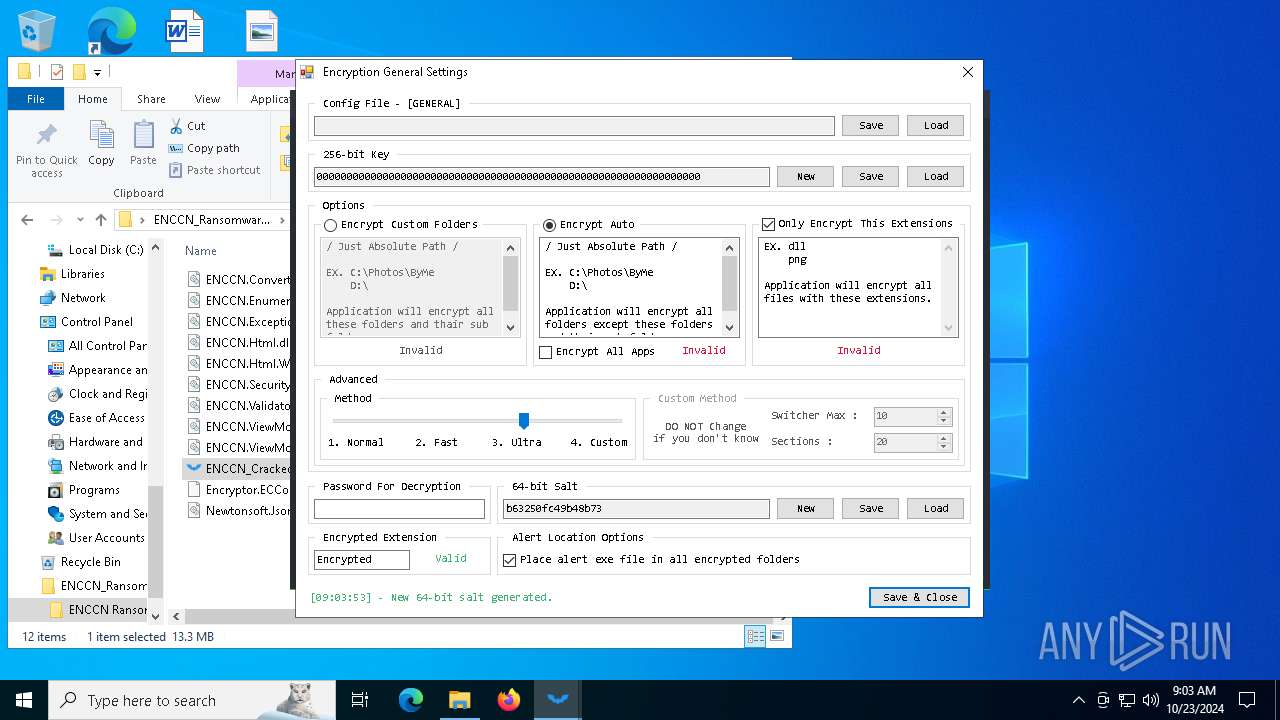
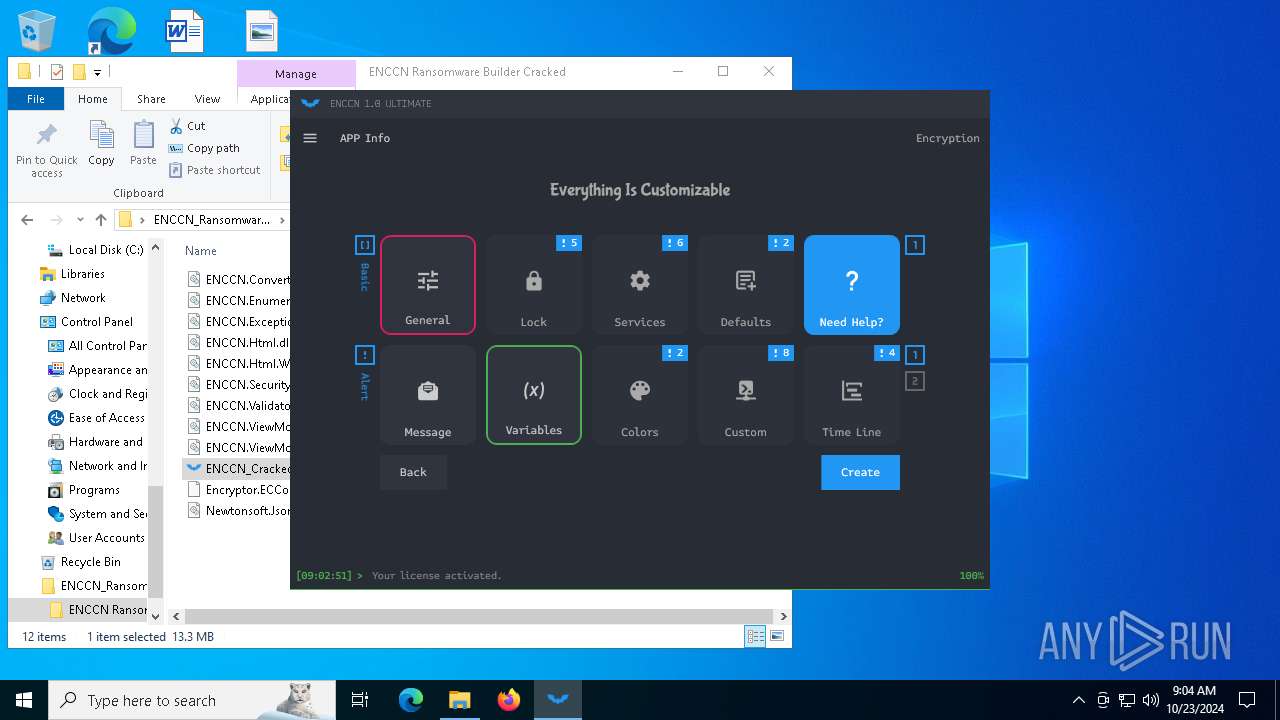
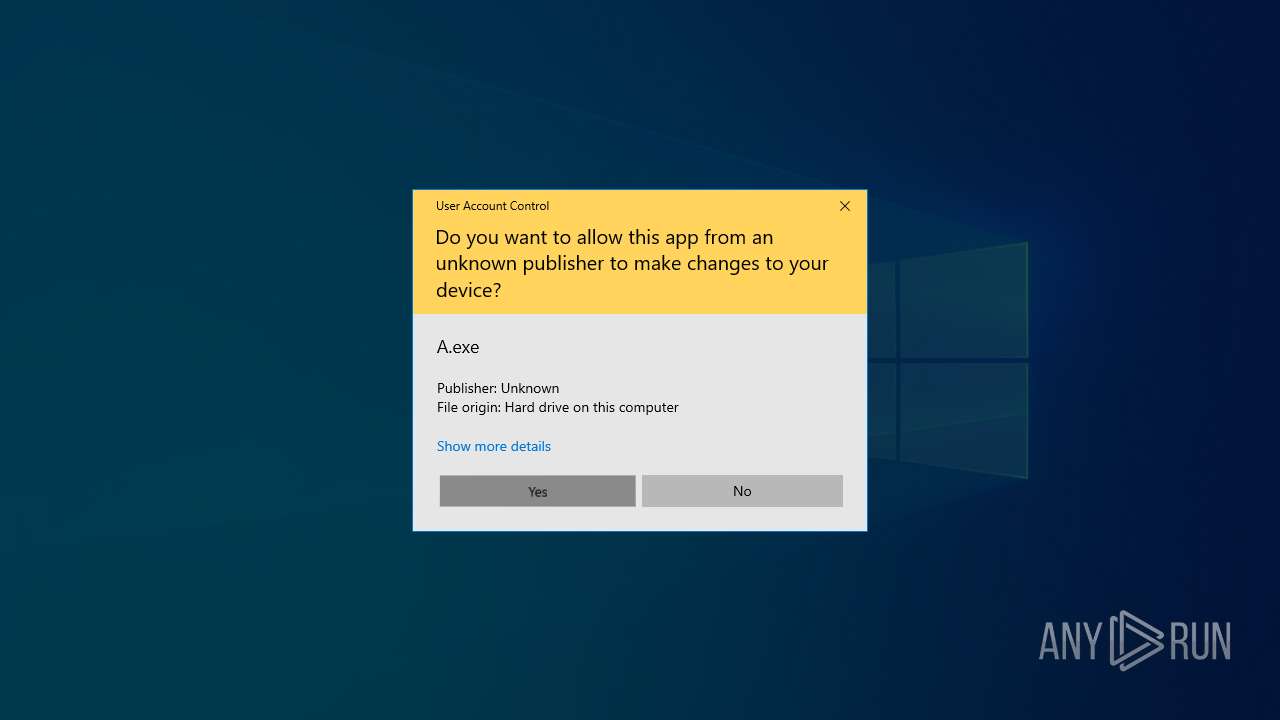
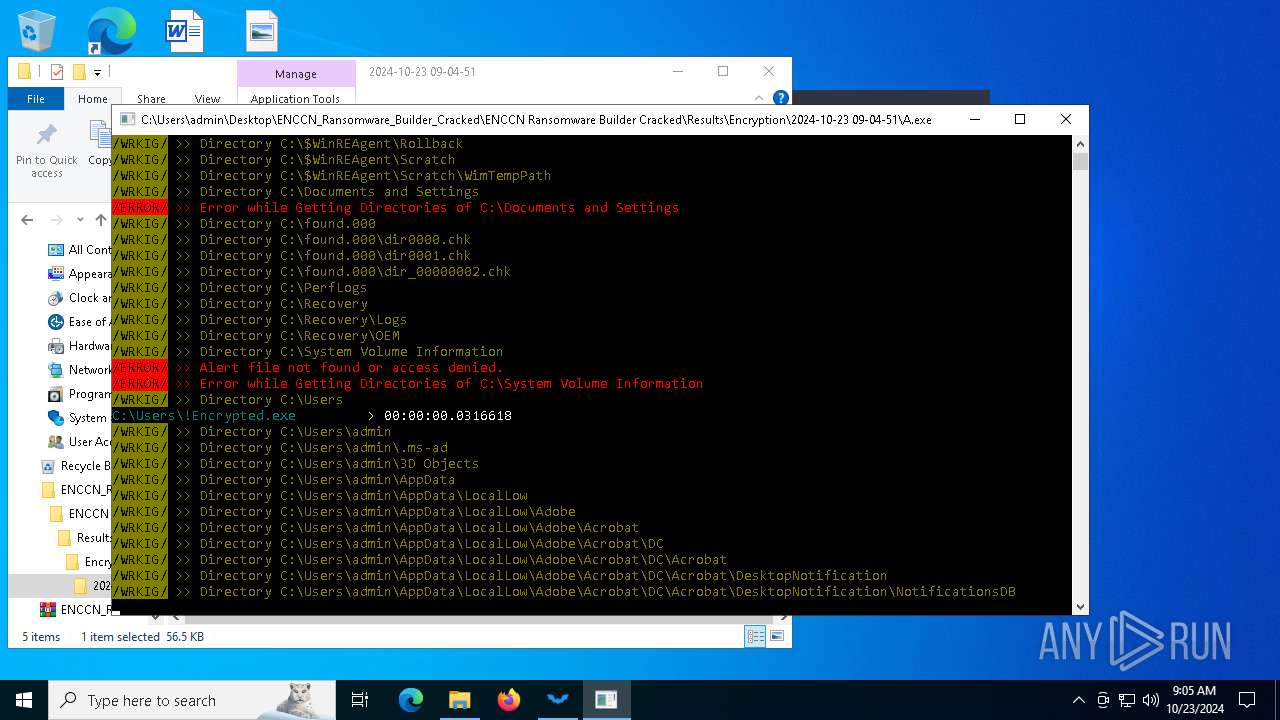
| File name: | ENCCN_Ransomware_Builder_Cracked.zip |
| Full analysis: | https://app.any.run/tasks/6fa6b87f-20fd-4dd0-a147-b71a6166c78c |
| Verdict: | Malicious activity |
| Analysis date: | October 23, 2024, 09:01:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 484AAC6D76A5AC96E0FD8F95A3C01ECE |
| SHA1: | 290D8036312D3C1214B73AE8E7B324ECECB16B77 |
| SHA256: | 80D50C97FAC897FEAA17E1667E61E7208354E0025EC4E5BBB5358DF4F1DA61A4 |
| SSDEEP: | 98304:wv5IC+08Vzw9UAybJEe63Tlkizdazdmr56bJk1bUTMwzNR/5jODdNfUJppy0K/uw:/eKQ14teq9MSyPB8+EifQ6w7khQU |
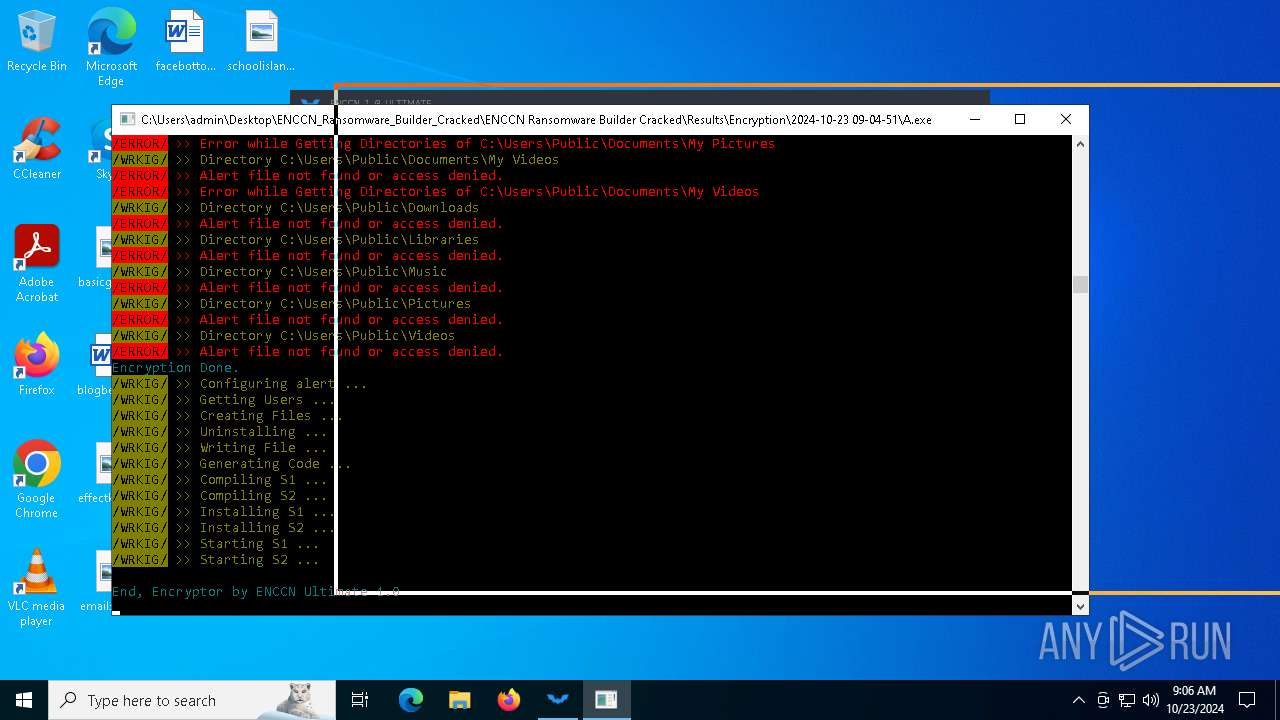
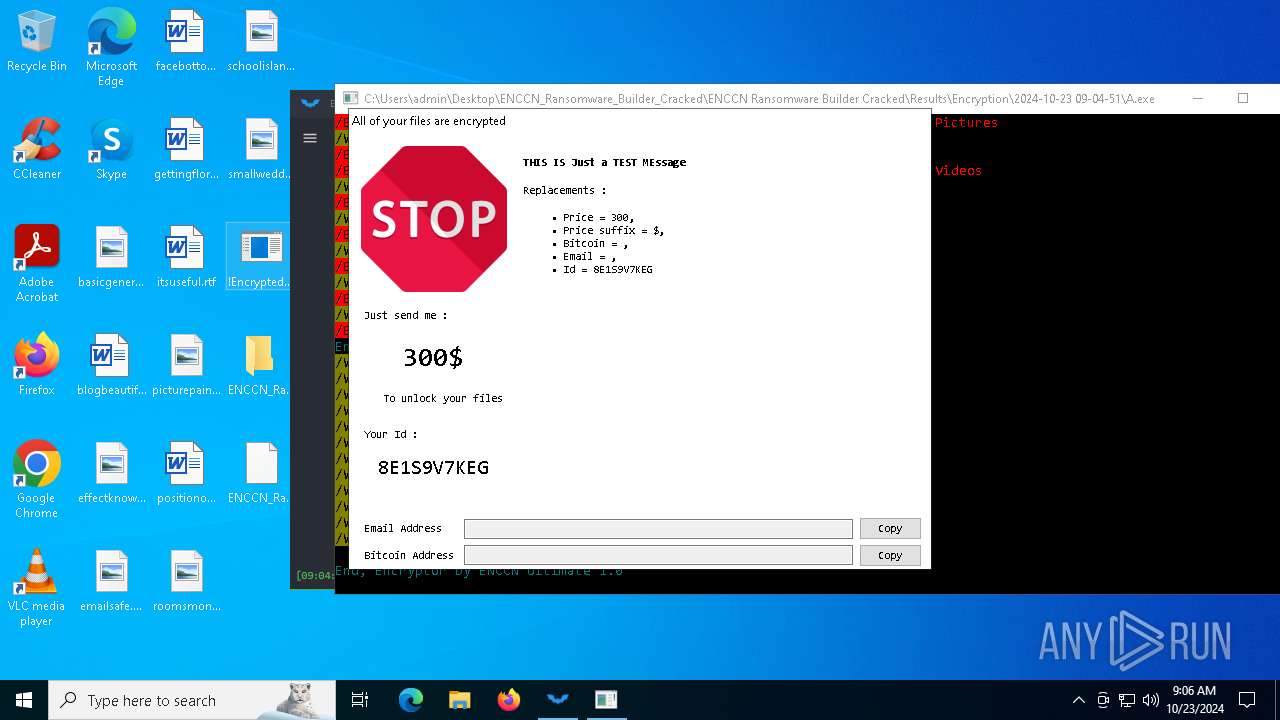
MALICIOUS
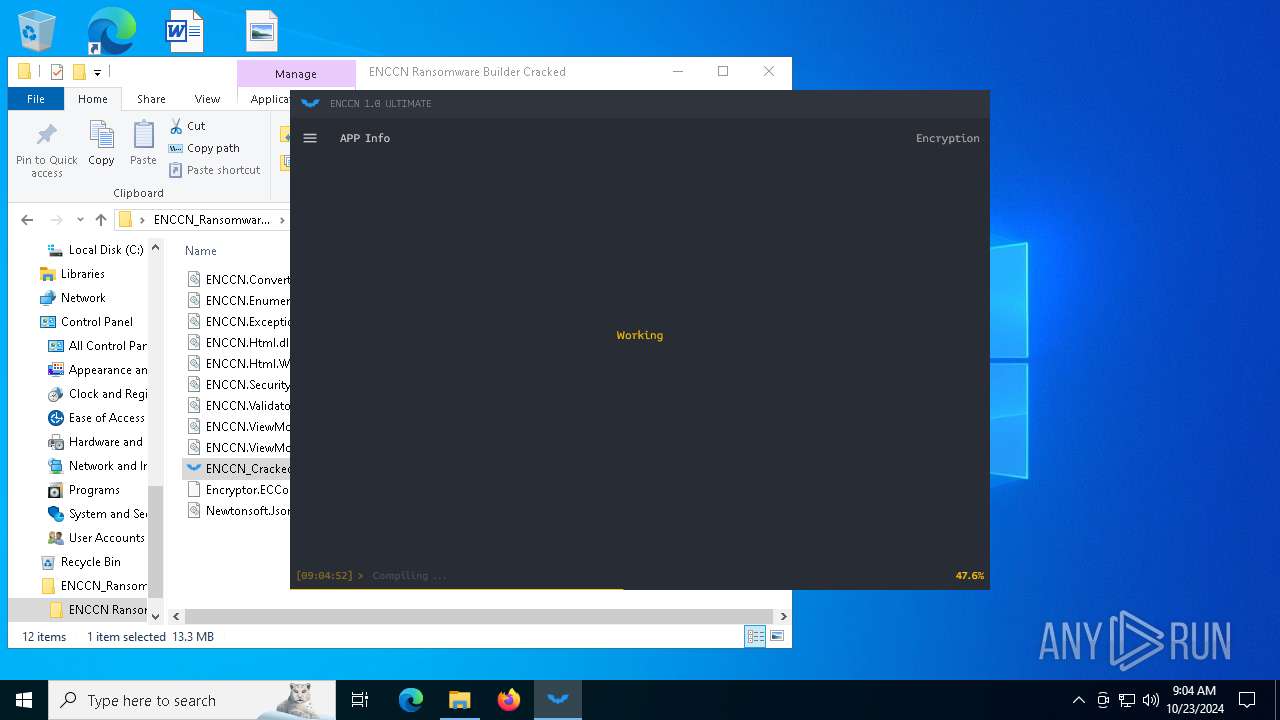
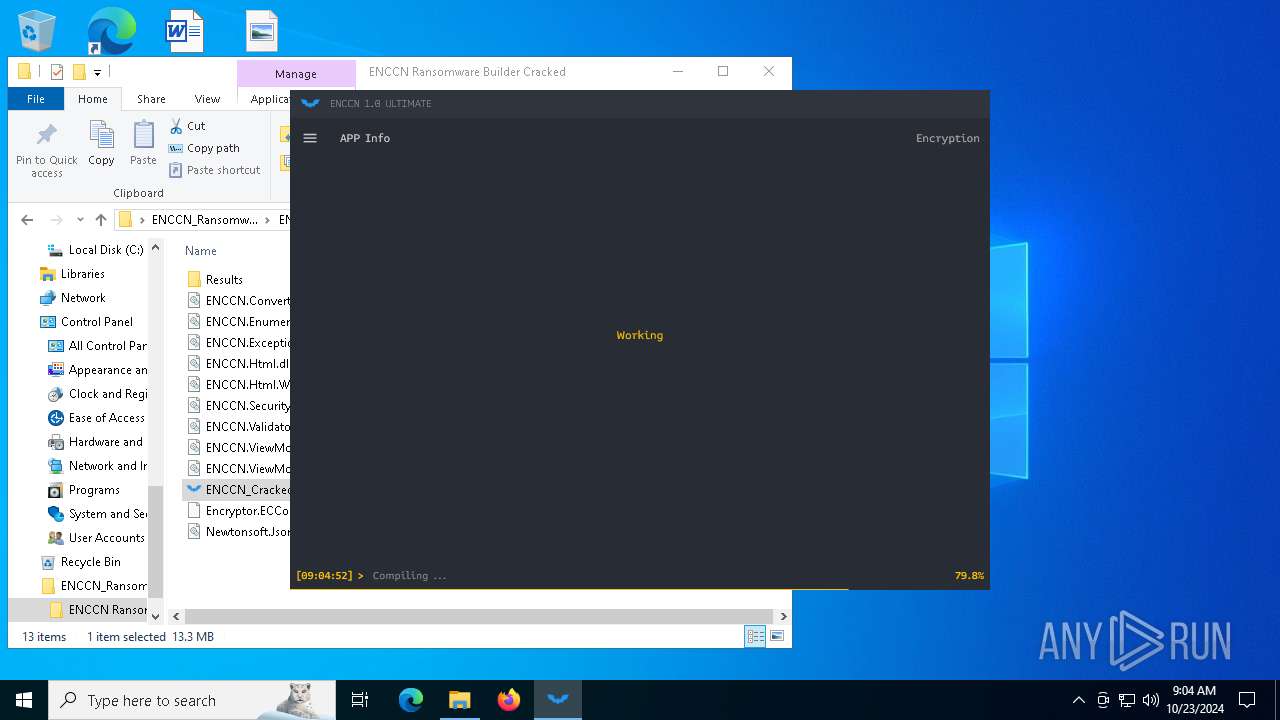
Starts Visual C# compiler
- ENCCN_Cracked.exe (PID: 5232)
SUSPICIOUS
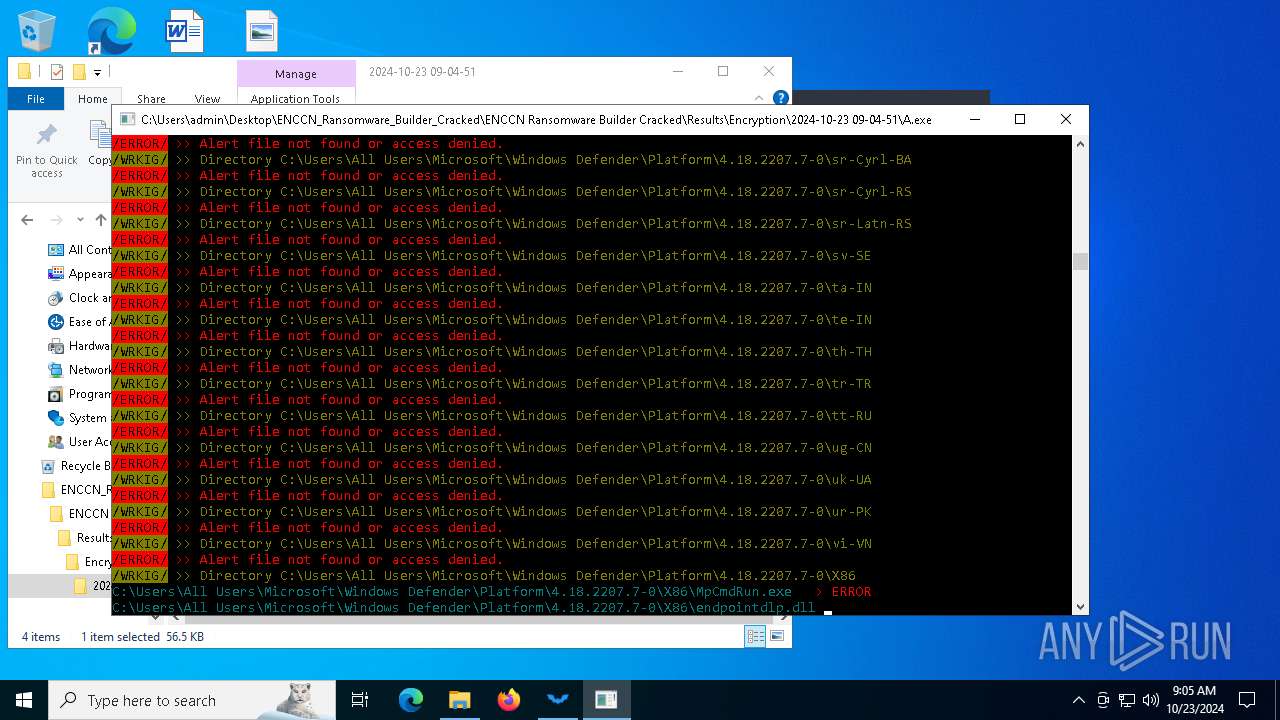
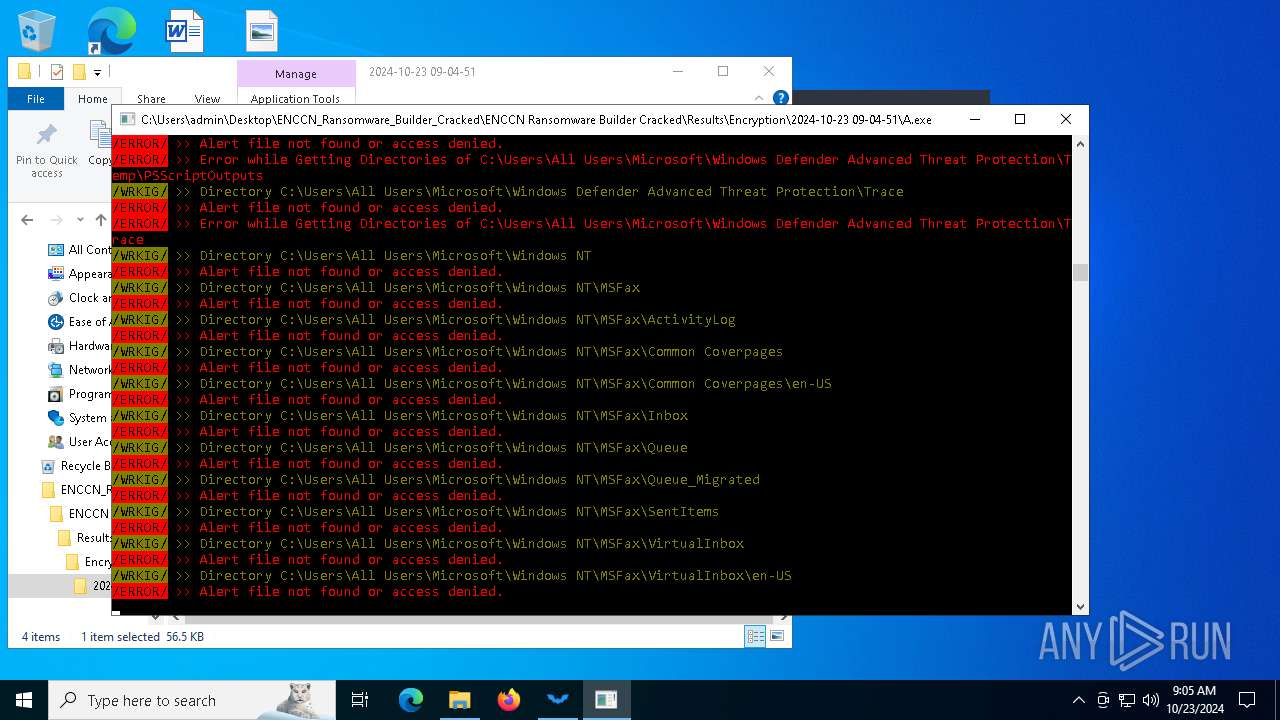
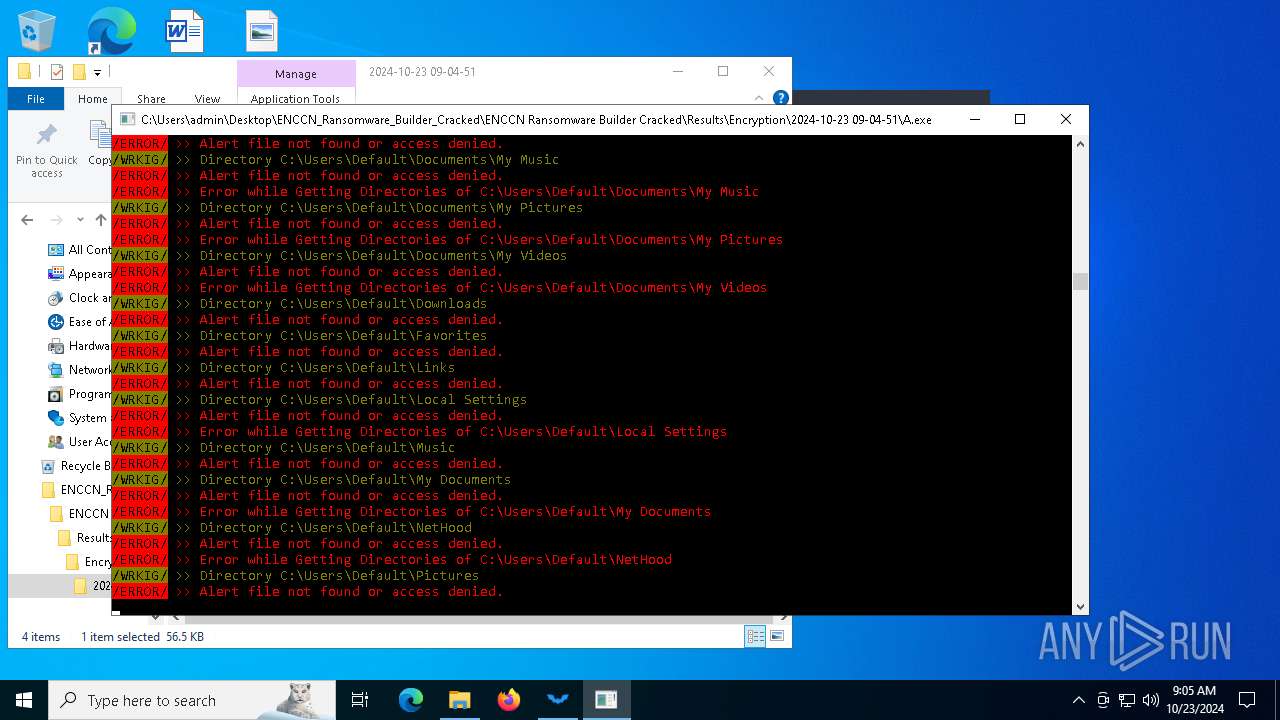
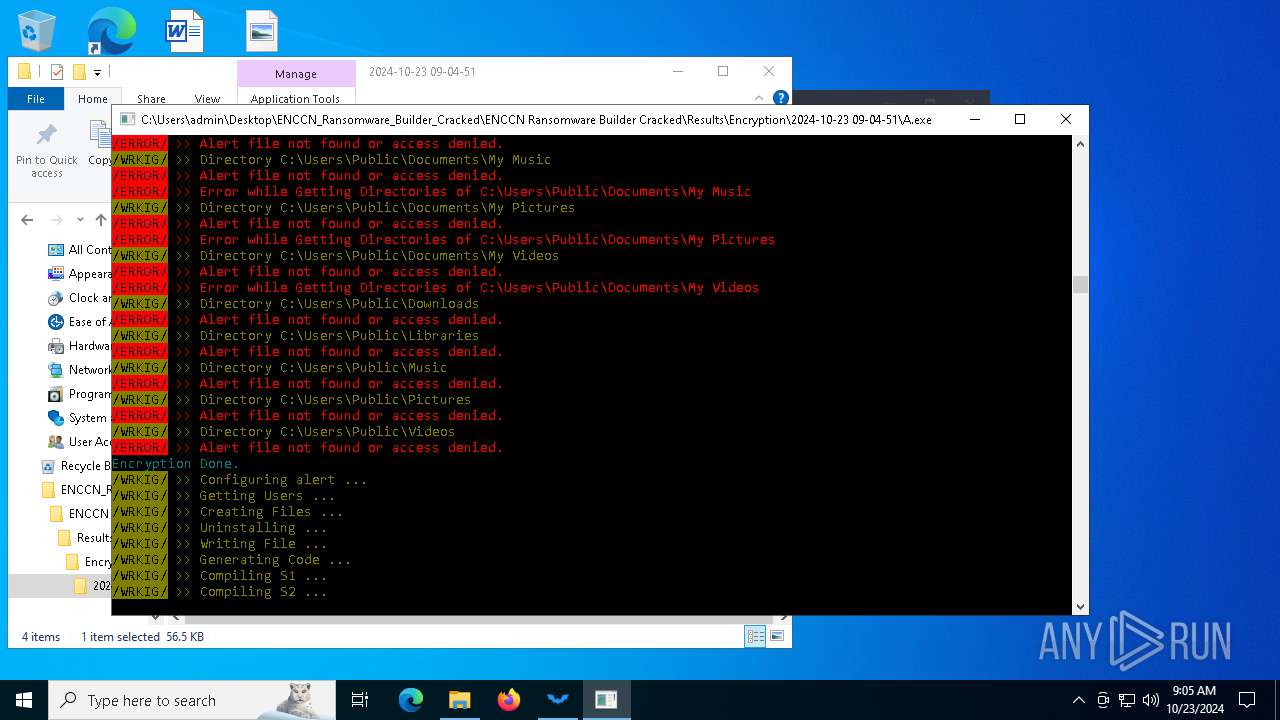
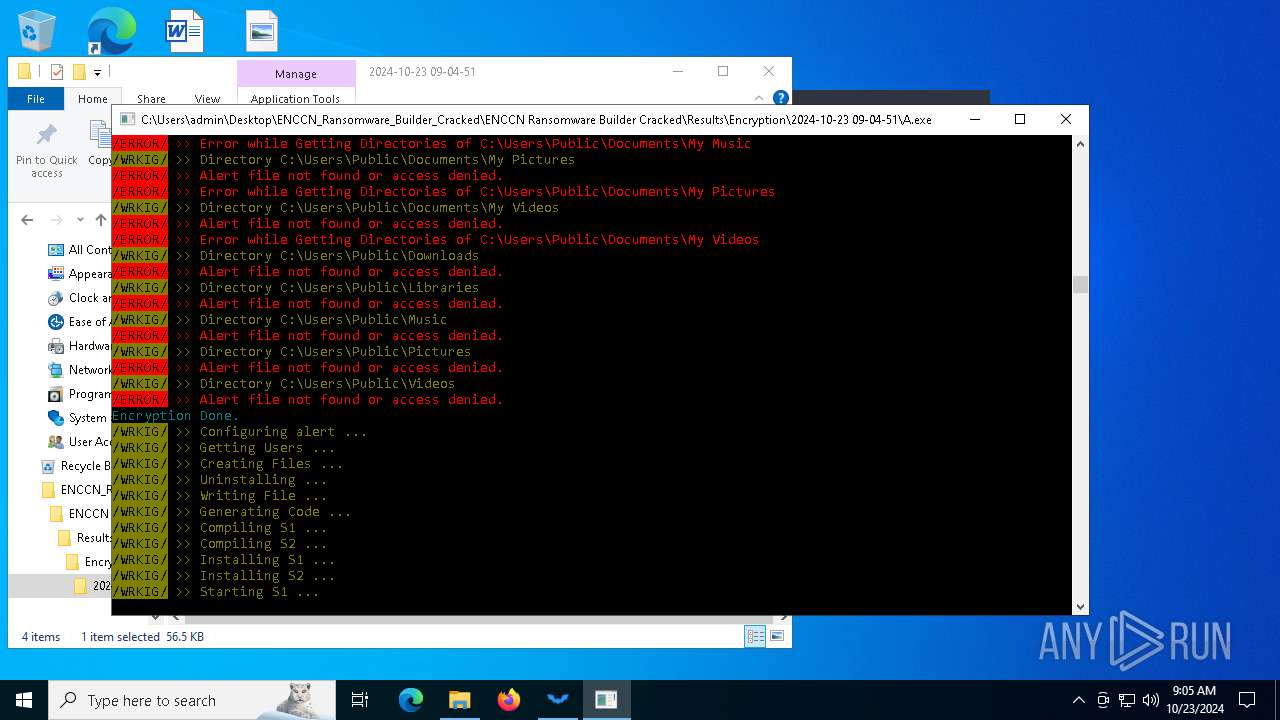
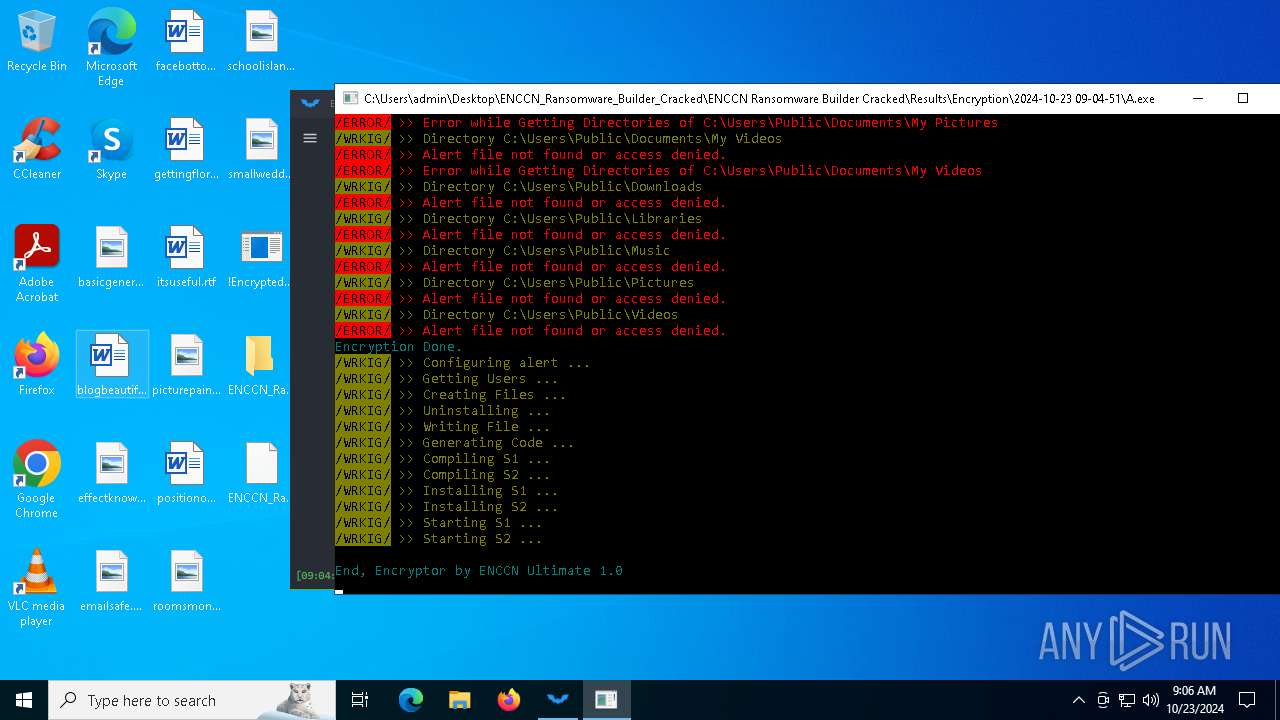
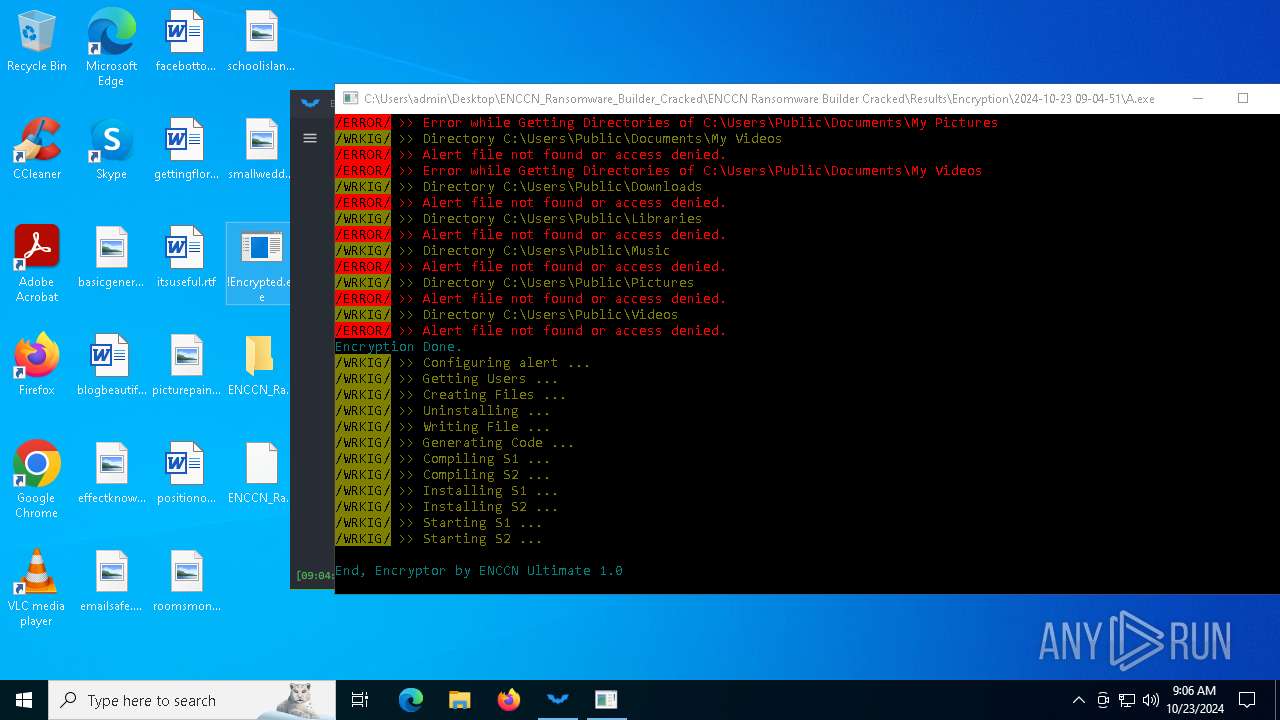
Executable content was dropped or overwritten
- csc.exe (PID: 860)
- ENCCN_Cracked.exe (PID: 5232)
- csc.exe (PID: 4448)
- A.exe (PID: 1084)
- csc.exe (PID: 3832)
- csc.exe (PID: 3940)
- Microsoft.ServiceHub.exe (PID: 4164)
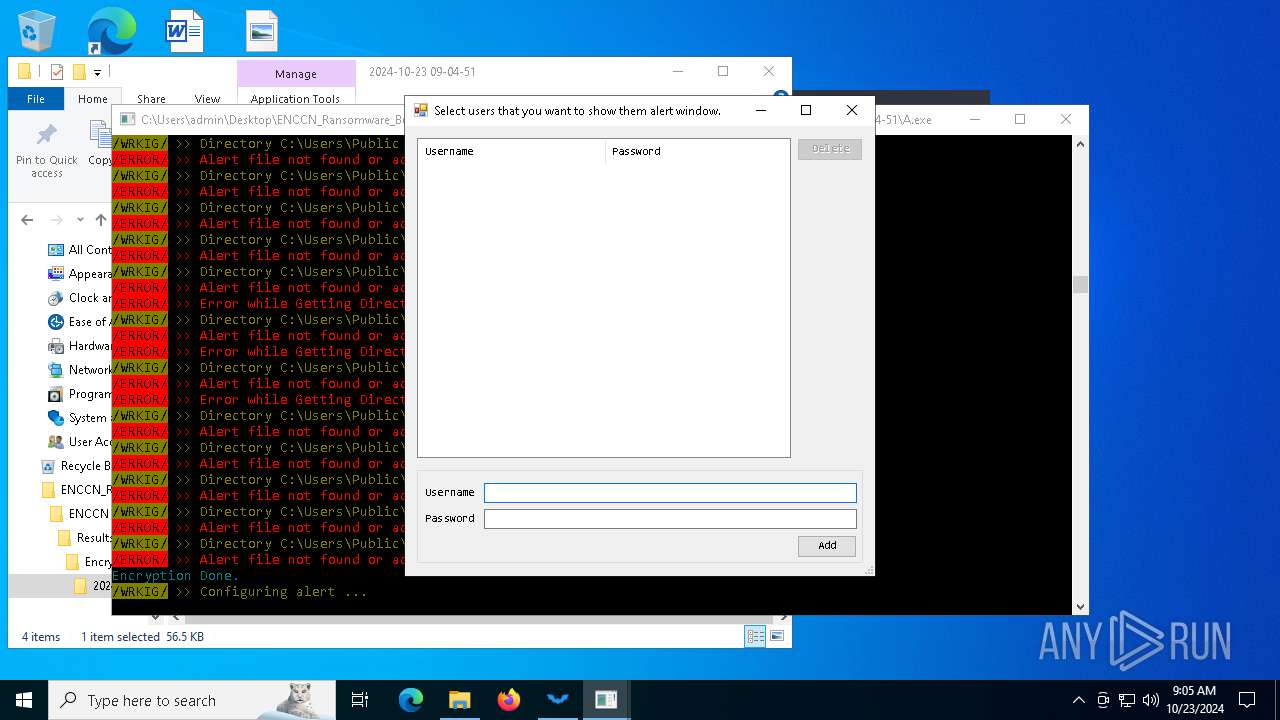
There is functionality for taking screenshot (YARA)
- ENCCN_Cracked.exe (PID: 5232)
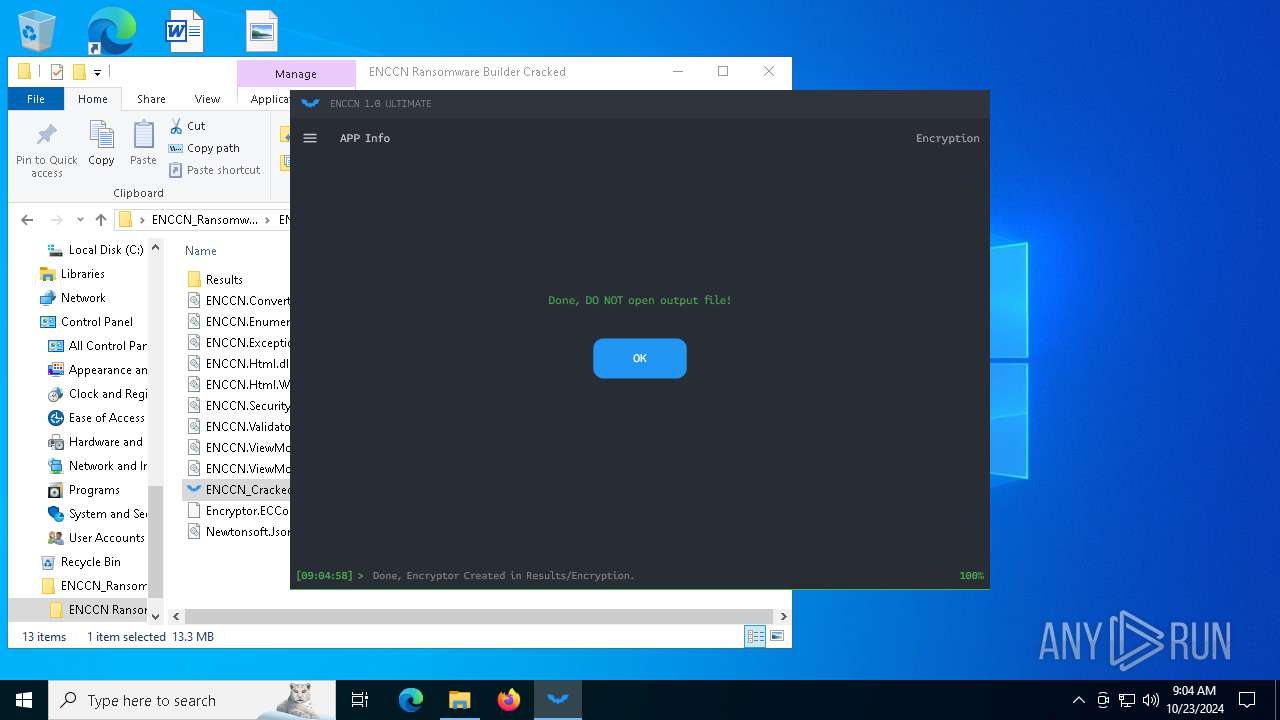
Process drops legitimate windows executable
- ENCCN_Cracked.exe (PID: 5232)
Uses .NET C# to load dll
- ENCCN_Cracked.exe (PID: 5232)
Executes as Windows Service
- Microsoft.ServiceHub.exe (PID: 4164)
- Runtime Broker.exe (PID: 6160)
INFO
Manual execution by a user
- WinRAR.exe (PID: 5172)
- ENCCN_Cracked.exe (PID: 5232)
- A.exe (PID: 1084)
- !Encrypted.exe (PID: 7060)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5172)
Potential access to remote process (Base64 Encoded 'OpenProcess')
- A.exe (PID: 1084)
Potential library load (Base64 Encoded 'LoadLibrary')
- A.exe (PID: 1084)
Potential dynamic function import (Base64 Encoded 'GetProcAddress')
- A.exe (PID: 1084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:10:19 09:20:40 |
| ZipCRC: | 0x3dcba6fa |
| ZipCompressedSize: | 23995 |
| ZipUncompressedSize: | 54304 |
| ZipFileName: | ENCCN Ransomware Builder Cracked/ENCCN.Converters.dll |
Total processes
154
Monitored processes
27
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 692 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 860 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\4smluuqi.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | ENCCN_Cracked.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 920 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESB461.tmp" "c:\Program Files\ECCT\CSCF4C68FBA2CA4DC8A423EAD717854DFA.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
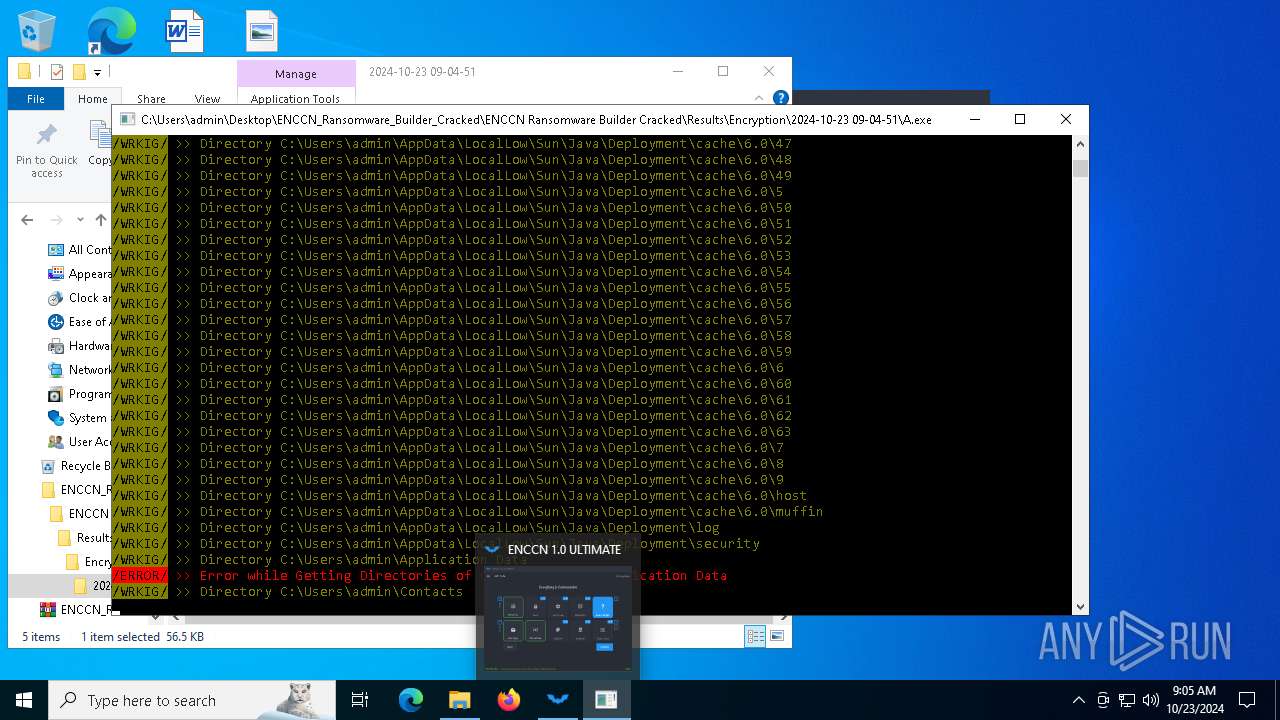
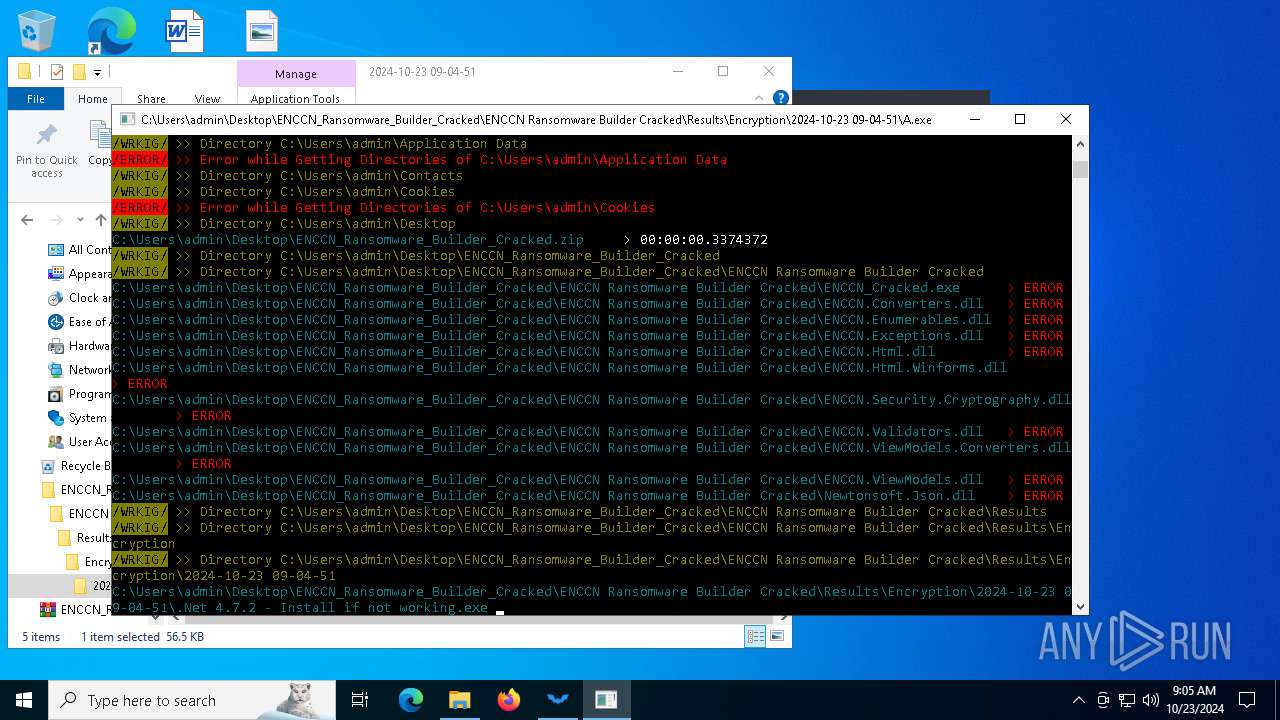
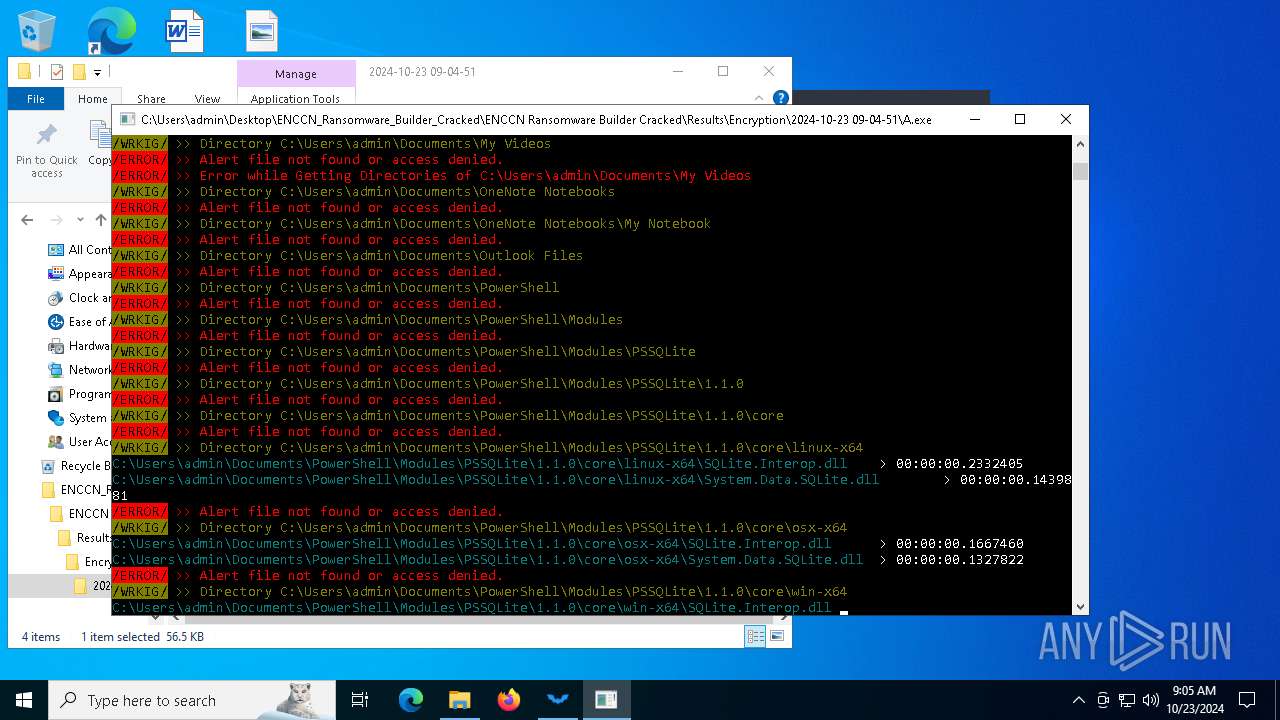
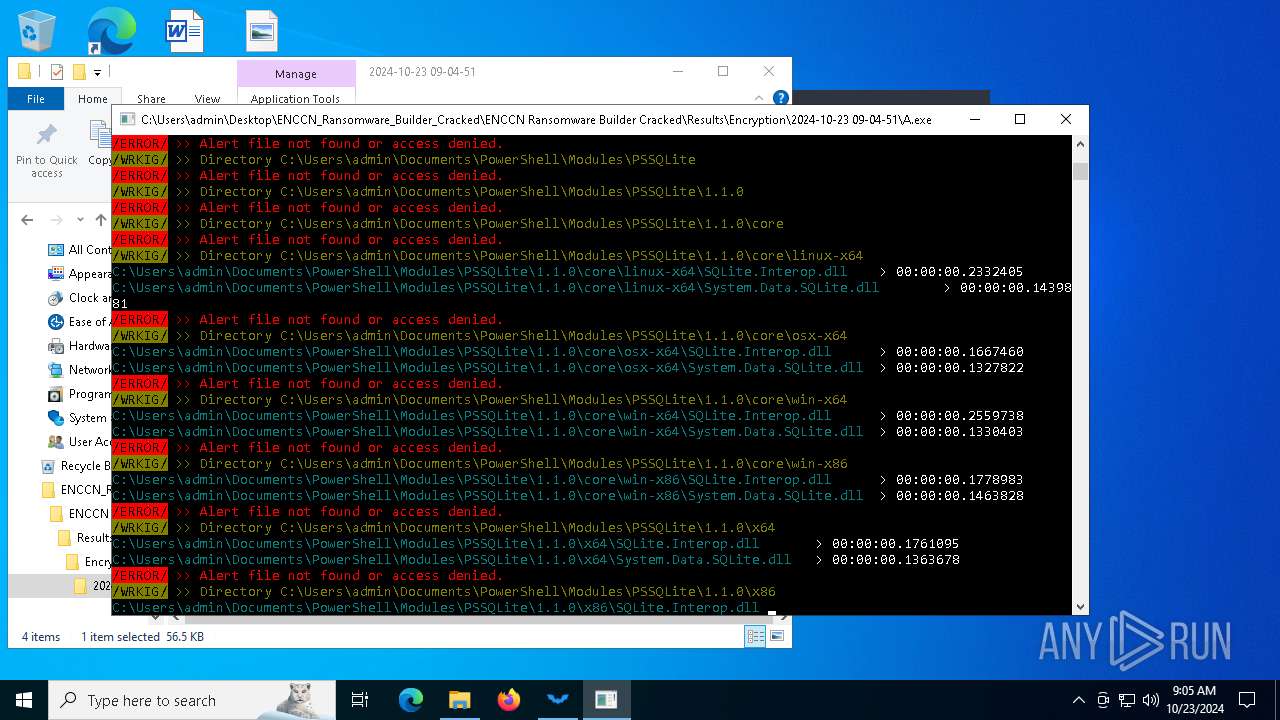
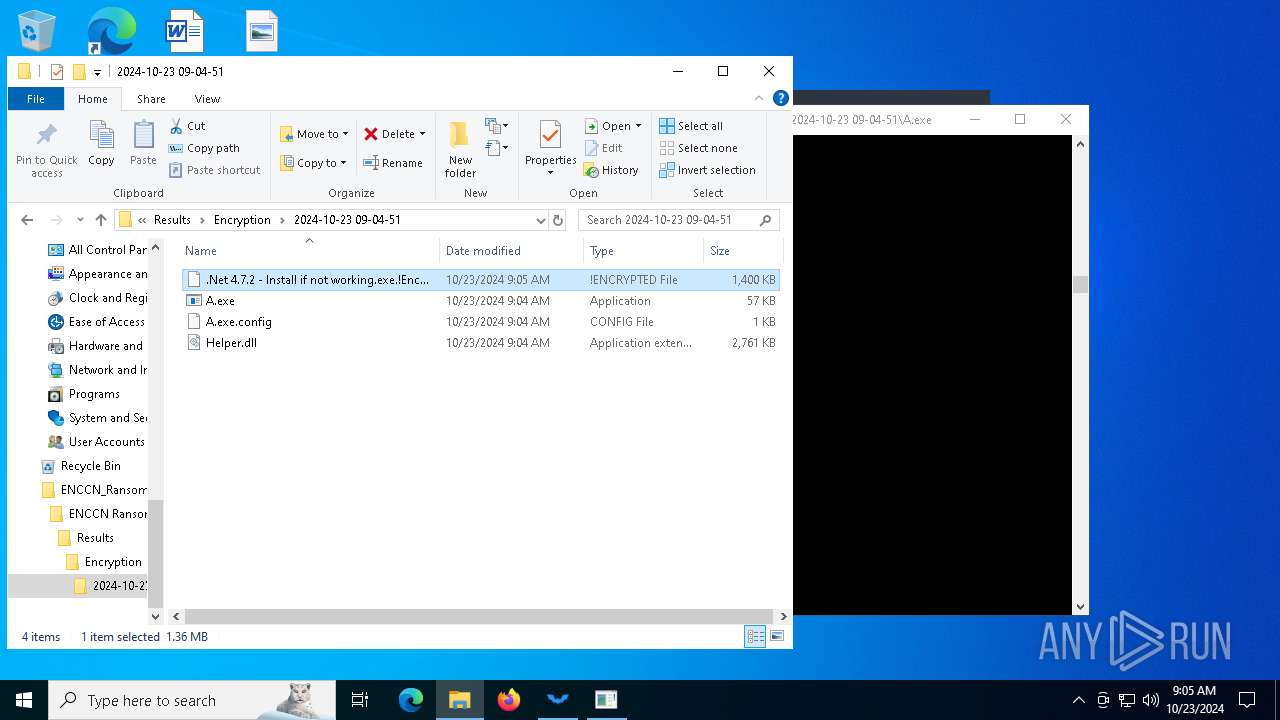
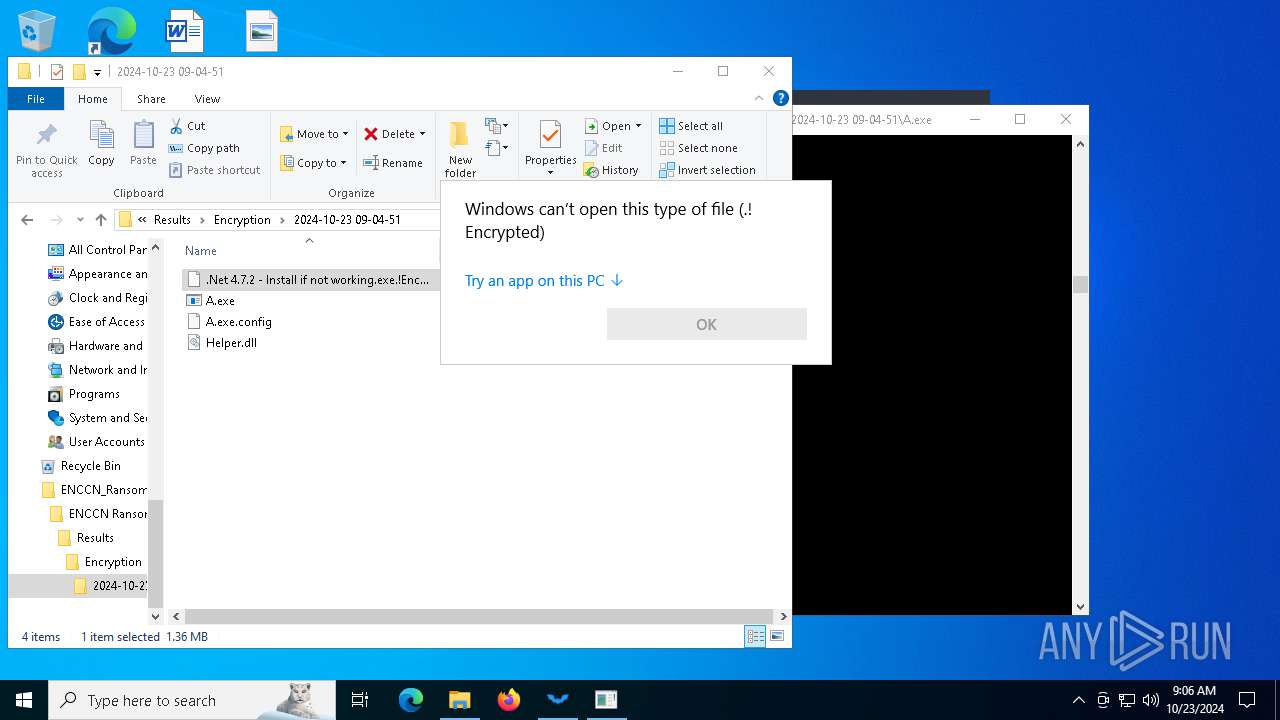
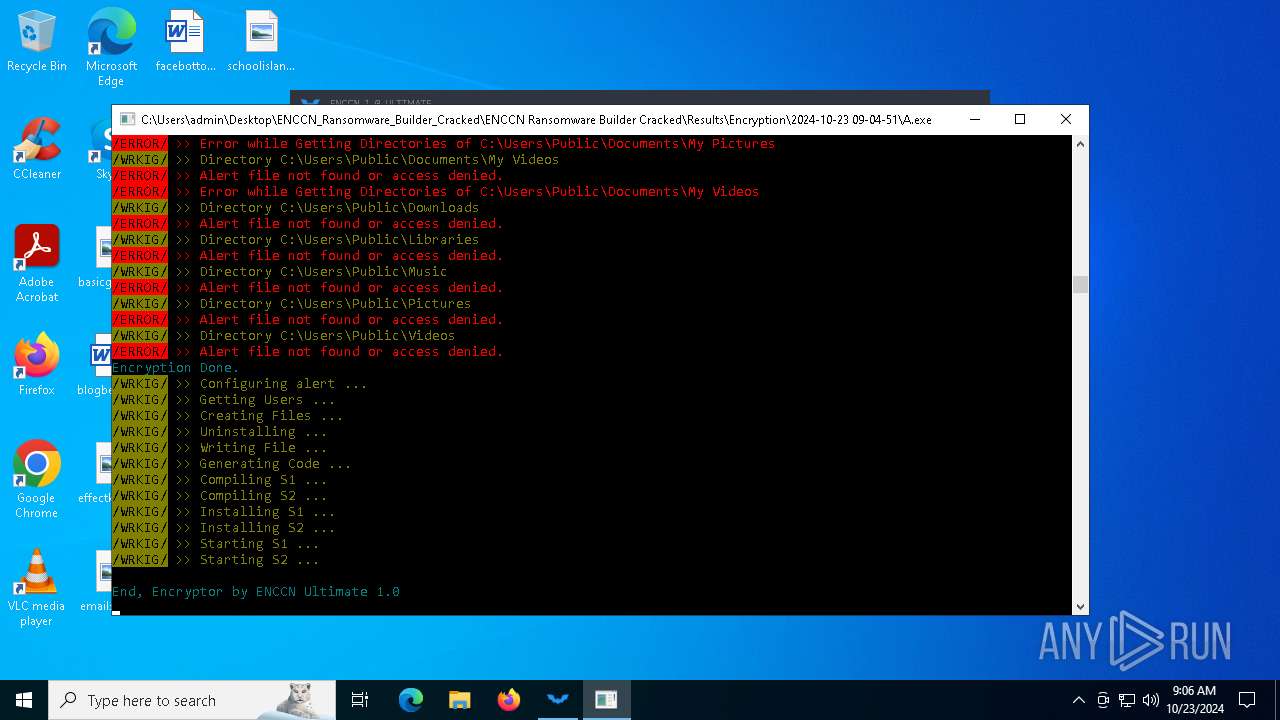
| 1084 | "C:\Users\admin\Desktop\ENCCN_Ransomware_Builder_Cracked\ENCCN Ransomware Builder Cracked\Results\Encryption\2024-10-23 09-04-51\A.exe" | C:\Users\admin\Desktop\ENCCN_Ransomware_Builder_Cracked\ENCCN Ransomware Builder Cracked\Results\Encryption\2024-10-23 09-04-51\A.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 1196 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\WINDOWS\TEMP\2ugbupvb\2ugbupvb.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | — | Microsoft.ServiceHub.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1344 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESE029.tmp" "c:\Users\admin\Desktop\ENCCN_Ransomware_Builder_Cracked\ENCCN Ransomware Builder Cracked\Results\Encryption\2024-10-23 09-04-51\CSCC09A8D8D28B4D71AA9DB8F35BB676B6.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 1744 | "C:\Program Files\ECCT\Runtime Broker.exe" install | C:\Program Files\ECCT\Runtime Broker.exe | A.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | csc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3432 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3772 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 509
Read events
13 375
Write events
115
Delete events
19
Modification events
| (PID) Process: | (5940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\ENCCN_Ransomware_Builder_Cracked.zip | |||
| (PID) Process: | (5940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (5940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (5940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
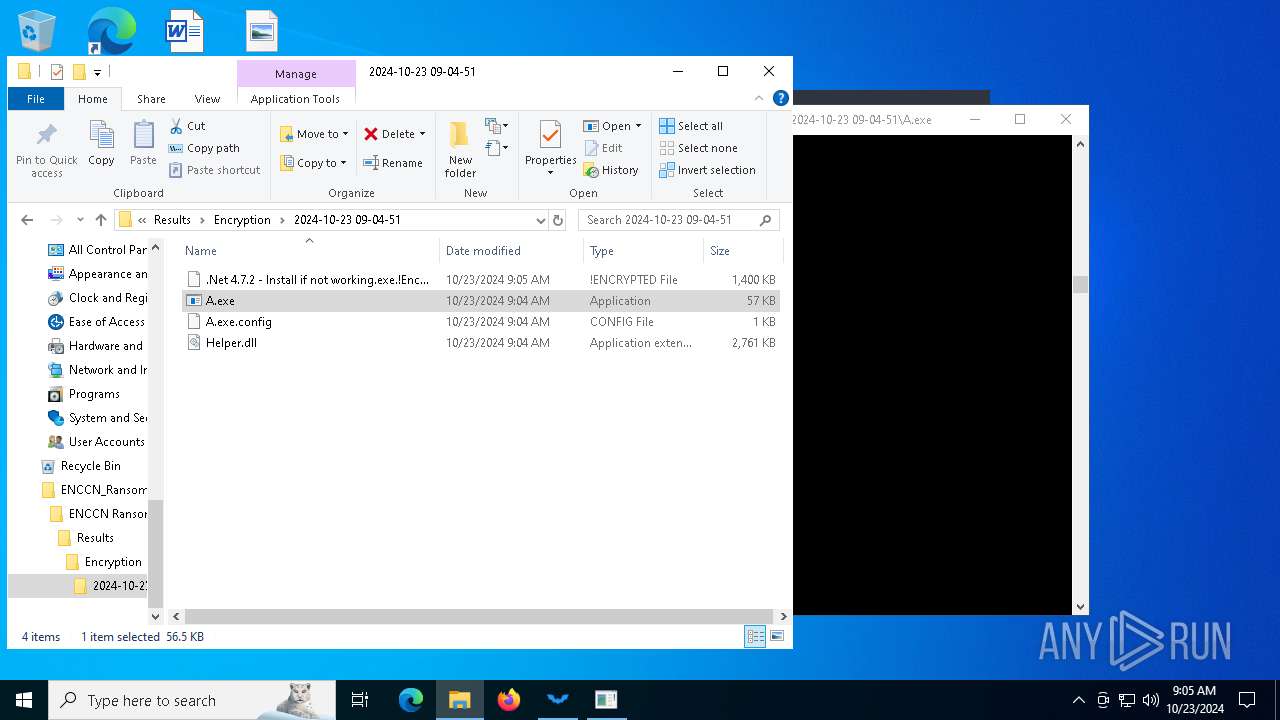
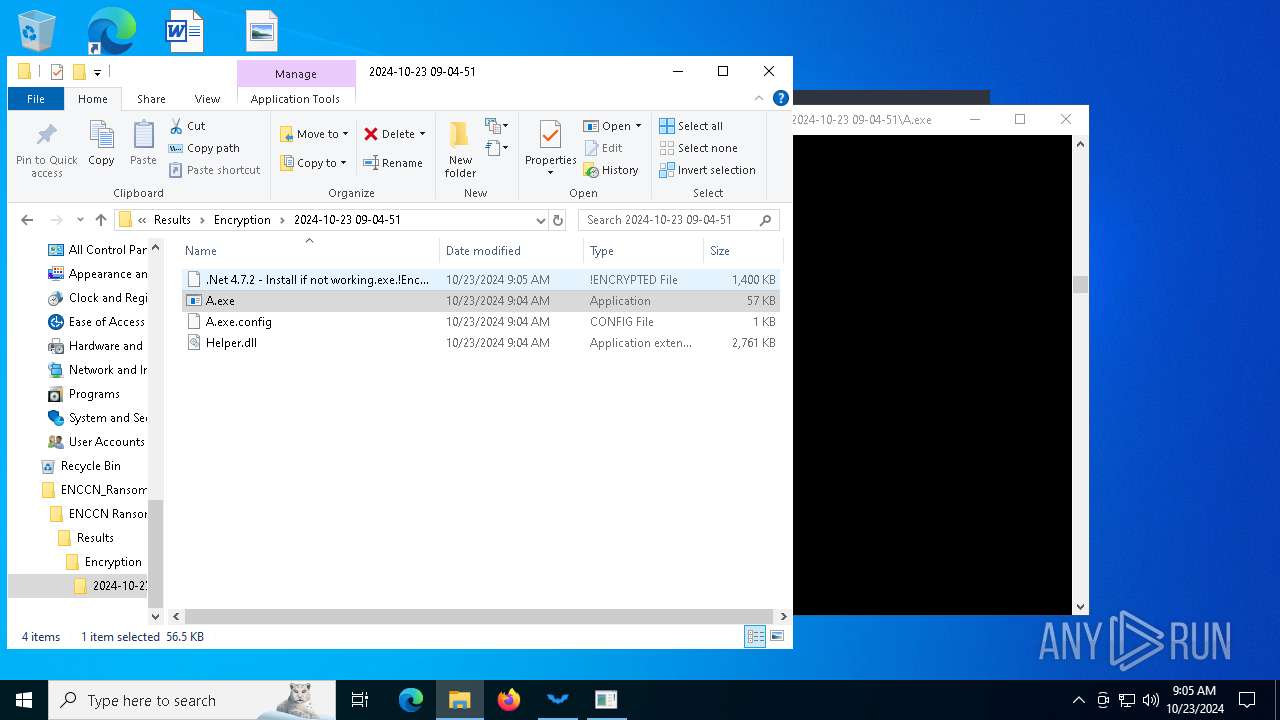
Executable files
202
Suspicious files
31
Text files
16
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
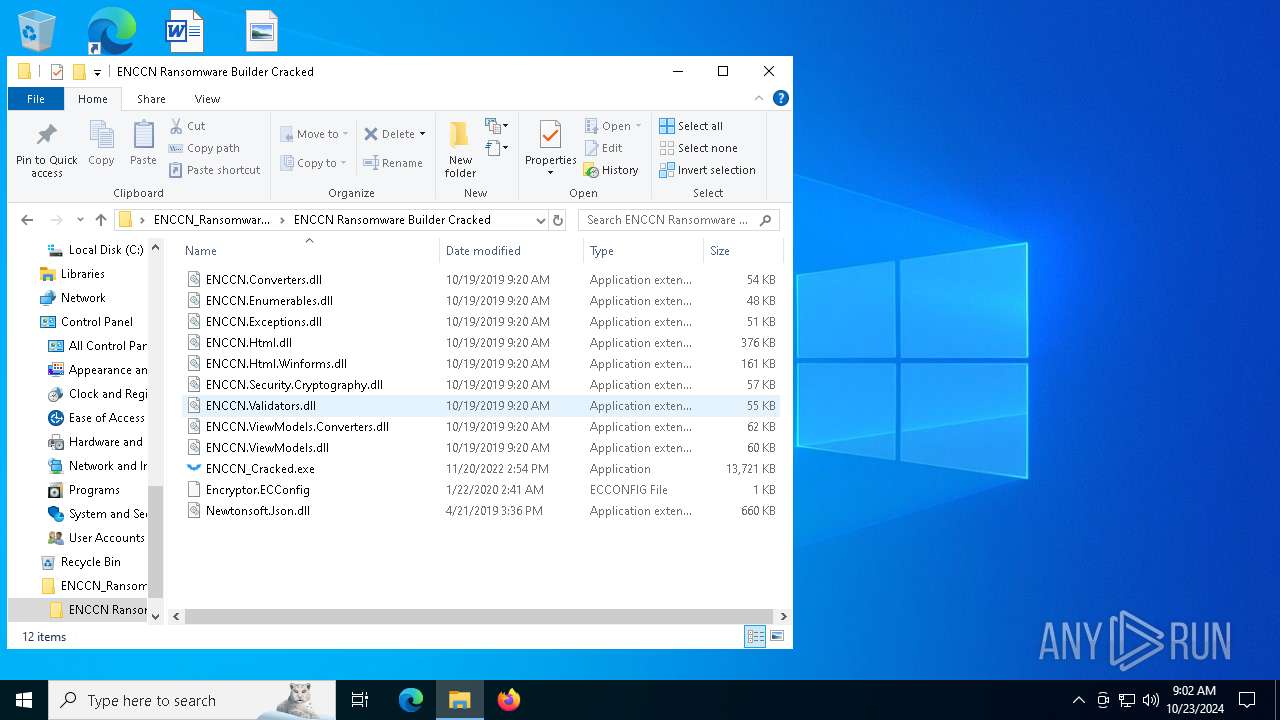
| 5172 | WinRAR.exe | C:\Users\admin\Desktop\ENCCN_Ransomware_Builder_Cracked\ENCCN Ransomware Builder Cracked\ENCCN.ViewModels.Converters.dll | executable | |
MD5:6928263F42233A3F9678BB40F2289645 | SHA256:7DD944E852242F0A5CC072E9256D68F1587CD39EB36DDB41F3A346EB652D5565 | |||
| 5172 | WinRAR.exe | C:\Users\admin\Desktop\ENCCN_Ransomware_Builder_Cracked\ENCCN Ransomware Builder Cracked\ENCCN.Converters.dll | executable | |
MD5:B47866A56F4CC171211E3EF64D6CED73 | SHA256:7514513F19CA1DFD021ACE7666B03E8DBA1940268DABEED4CE2CFC9523973301 | |||
| 5172 | WinRAR.exe | C:\Users\admin\Desktop\ENCCN_Ransomware_Builder_Cracked\ENCCN Ransomware Builder Cracked\ENCCN.Html.Winforms.dll | executable | |
MD5:D9ACD867FBAFEC0430C39DBE8A5C9EE6 | SHA256:77DE9AE6AD5EDD65F1AA514EA5FC582EA1A99AEEA7EF2E8D8D6A96BD065B3016 | |||
| 5172 | WinRAR.exe | C:\Users\admin\Desktop\ENCCN_Ransomware_Builder_Cracked\ENCCN Ransomware Builder Cracked\ENCCN.Enumerables.dll | executable | |
MD5:7C25E04937D02504063EA6B37936C6F3 | SHA256:B6EA38BA136119E7FDE123904310178A23CE46AB1D4D0FC9D80F8D40BF74FB1E | |||
| 1344 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RESE029.tmp | binary | |
MD5:C81D04A265D3368843227AFA544B28E7 | SHA256:5D1CF887EF3CBC643053B4CDCA31B9E6CC91D871F3785125B7DD76C7CC95FA6D | |||
| 5172 | WinRAR.exe | C:\Users\admin\Desktop\ENCCN_Ransomware_Builder_Cracked\ENCCN Ransomware Builder Cracked\ENCCN.Exceptions.dll | executable | |
MD5:BAC25DD9E95EBC9F8D5EC9BD5FC16069 | SHA256:DCA0B79012D5B576F9D77DD5FFFCC6FAA463E8A65CC1F60950FEF828C0E02204 | |||
| 5172 | WinRAR.exe | C:\Users\admin\Desktop\ENCCN_Ransomware_Builder_Cracked\ENCCN Ransomware Builder Cracked\ENCCN.Security.Cryptography.dll | executable | |
MD5:4F1AA4E094FF44F56B82D972842E313E | SHA256:0CECF420F96266A94433182DE1890EFFCAABFD008992C43E2CB5B14F858911C6 | |||
| 5172 | WinRAR.exe | C:\Users\admin\Desktop\ENCCN_Ransomware_Builder_Cracked\ENCCN Ransomware Builder Cracked\ENCCN.ViewModels.dll | executable | |
MD5:D0F0A621AFD7BF3873D679C7FEF5F754 | SHA256:40D629DE02437F69FDB32169E82FF5FD3CF728C88BA84448741414113A7F1721 | |||
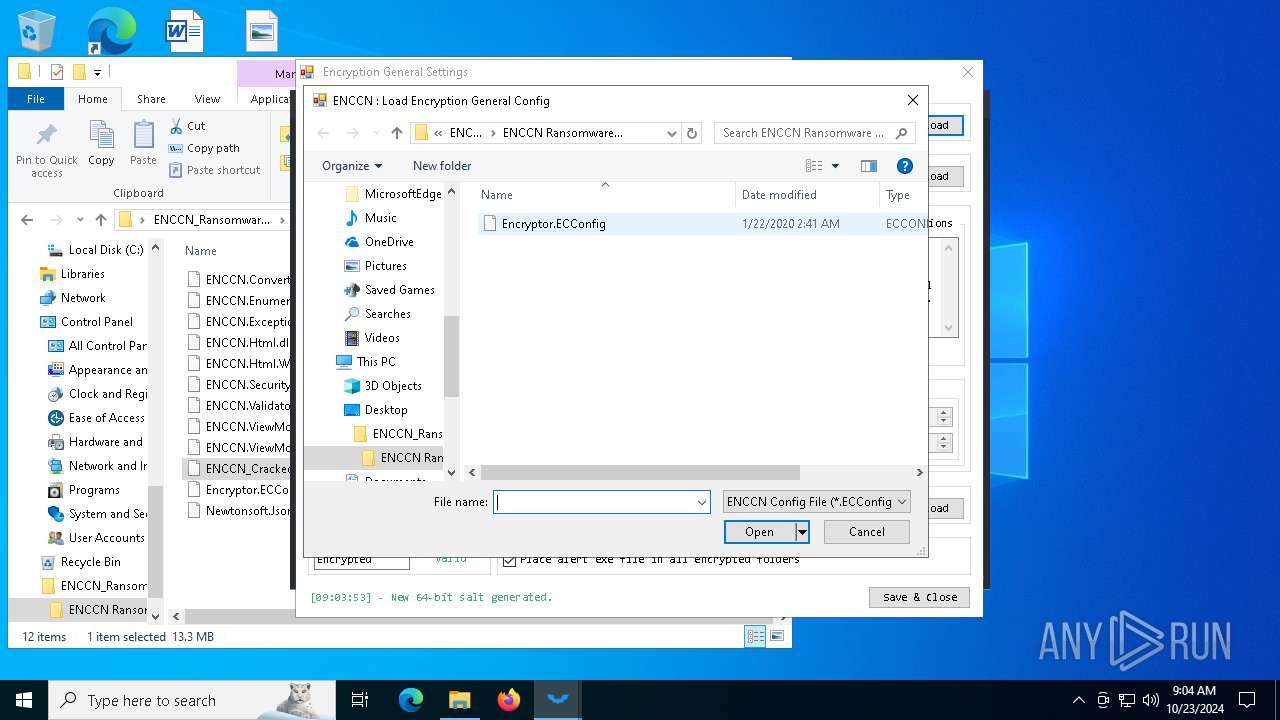
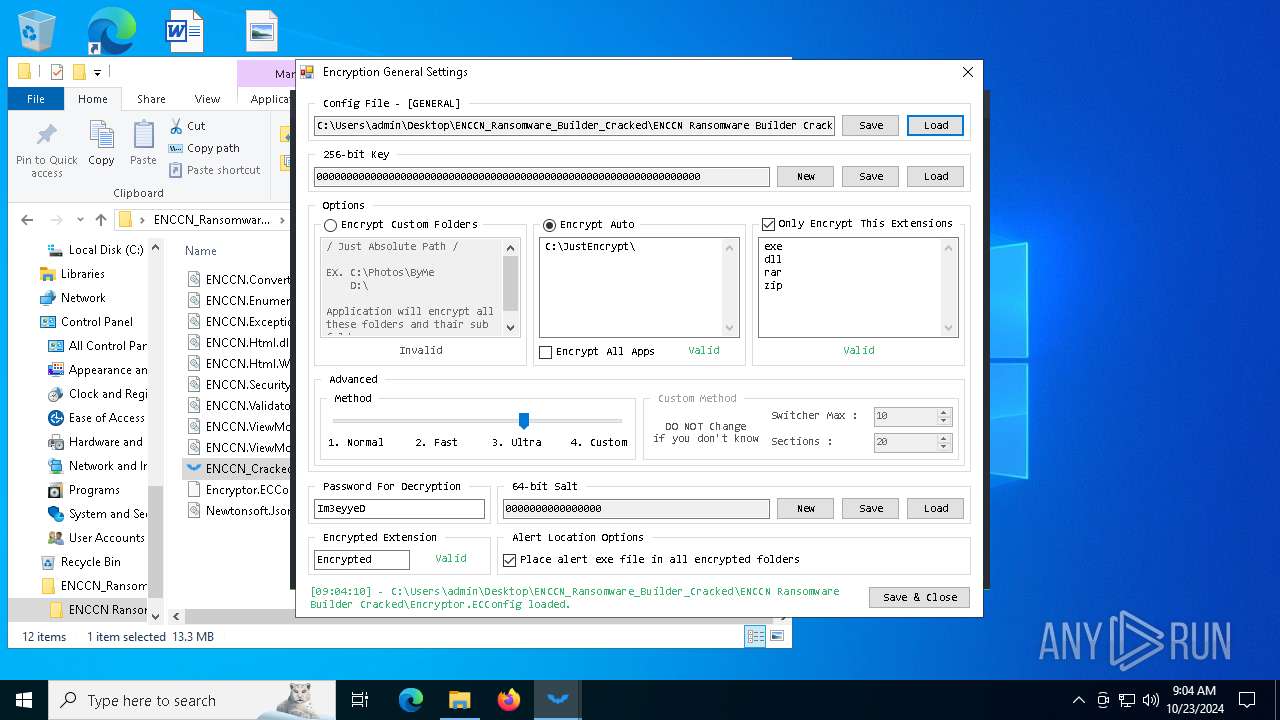
| 5172 | WinRAR.exe | C:\Users\admin\Desktop\ENCCN_Ransomware_Builder_Cracked\ENCCN Ransomware Builder Cracked\Encryptor.ECConfig | binary | |
MD5:F9516B748E6887FE6D331D296C8E89EC | SHA256:9C63848F5D91B9A78F405EAE4A30CAC68FEF660C9004A5D0ECC264789B45DE72 | |||
| 5172 | WinRAR.exe | C:\Users\admin\Desktop\ENCCN_Ransomware_Builder_Cracked\ENCCN Ransomware Builder Cracked\ENCCN.Validators.dll | executable | |
MD5:B8E810A1224F410FDB674060B9A7DB4F | SHA256:2E43CD35CBF0F9E408FA8DBF073633800DA55460DA6074E9116BA48A62FA7C3A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
55
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2364 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4232 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4232 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6800 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5700 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4360 | SearchApp.exe | 2.23.209.183:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6944 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Runtime Broker.exe | Topshelf.HostFactory Information: 0 : |
Runtime Broker.exe | Configuration Result:
[Success] Name RuntimeBroker
[Success] DisplayName Runtime Broker
[Success] Description Windows Runtime Broker local service.
[Success] ServiceName RuntimeBroker
|
Runtime Broker.exe | Topshelf.HostConfigurators.HostConfiguratorImpl Information: 0 : |
Runtime Broker.exe | Topshelf v4.2.1.215, .NET Framework v4.0.30319.42000
|
Runtime Broker.exe | Topshelf.Runtime.Windows.HostInstaller Information: 0 : |
Runtime Broker.exe | Installing Runtime Broker service
|
Microsoft.ServiceHub.exe | Topshelf.HostFactory Information: 0 : |
Microsoft.ServiceHub.exe | Configuration Result:
[Success] Name Microsoft.ServiceHub
[Success] DisplayName Microsoft ServiceHub
[Success] Description Microsoft Windows Service Hub local service.
[Success] ServiceName Microsoft.ServiceHub
|
Microsoft.ServiceHub.exe | Topshelf.HostConfigurators.HostConfiguratorImpl Information: 0 : |
Microsoft.ServiceHub.exe | Topshelf v4.2.1.215, .NET Framework v4.0.30319.42000
|