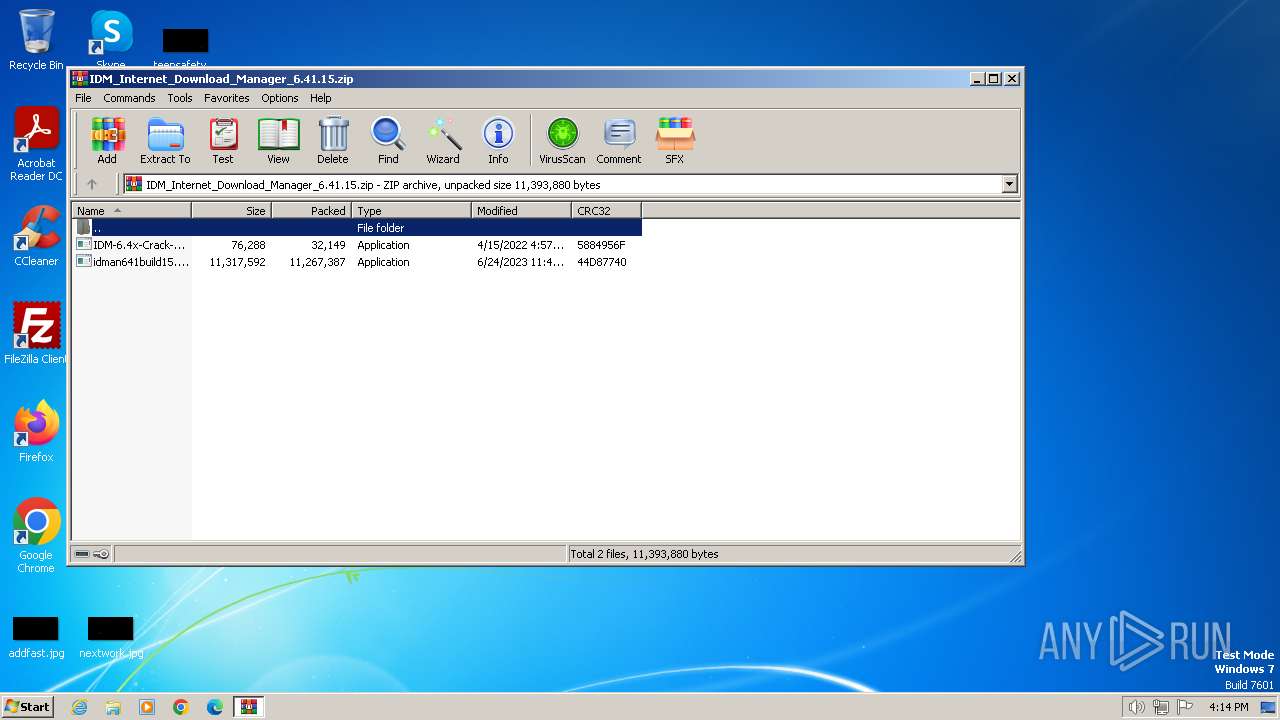
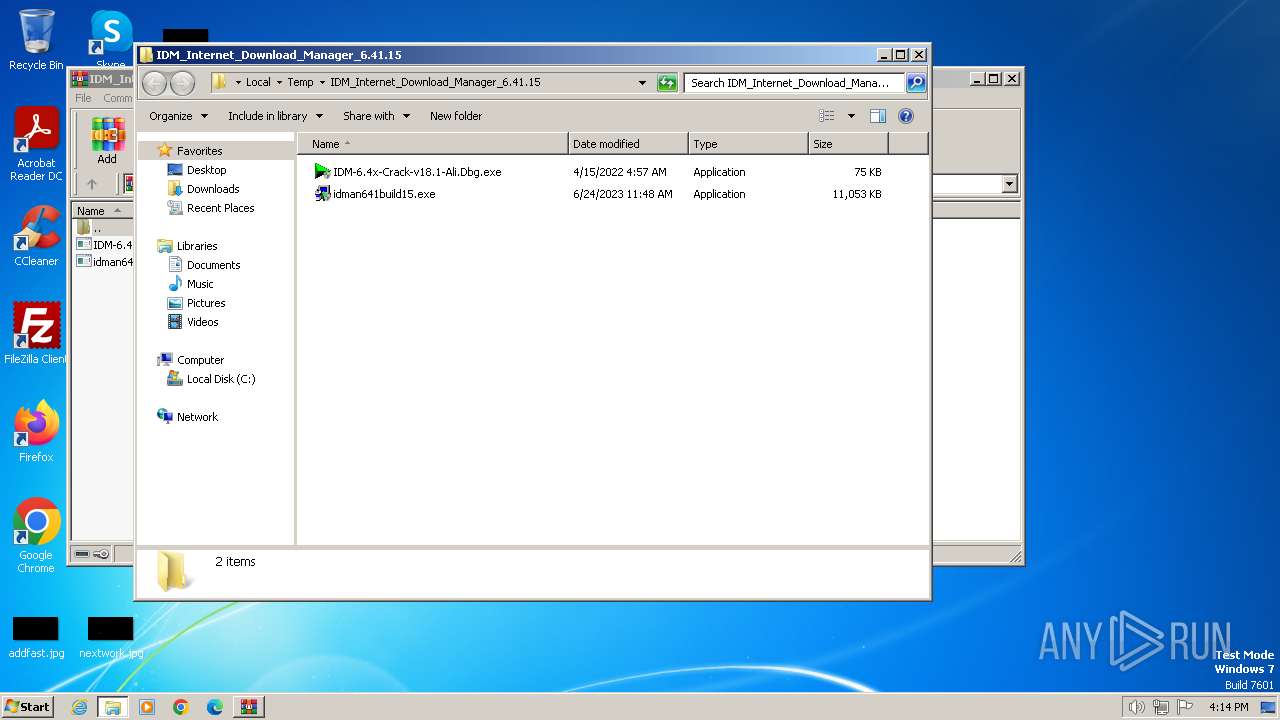
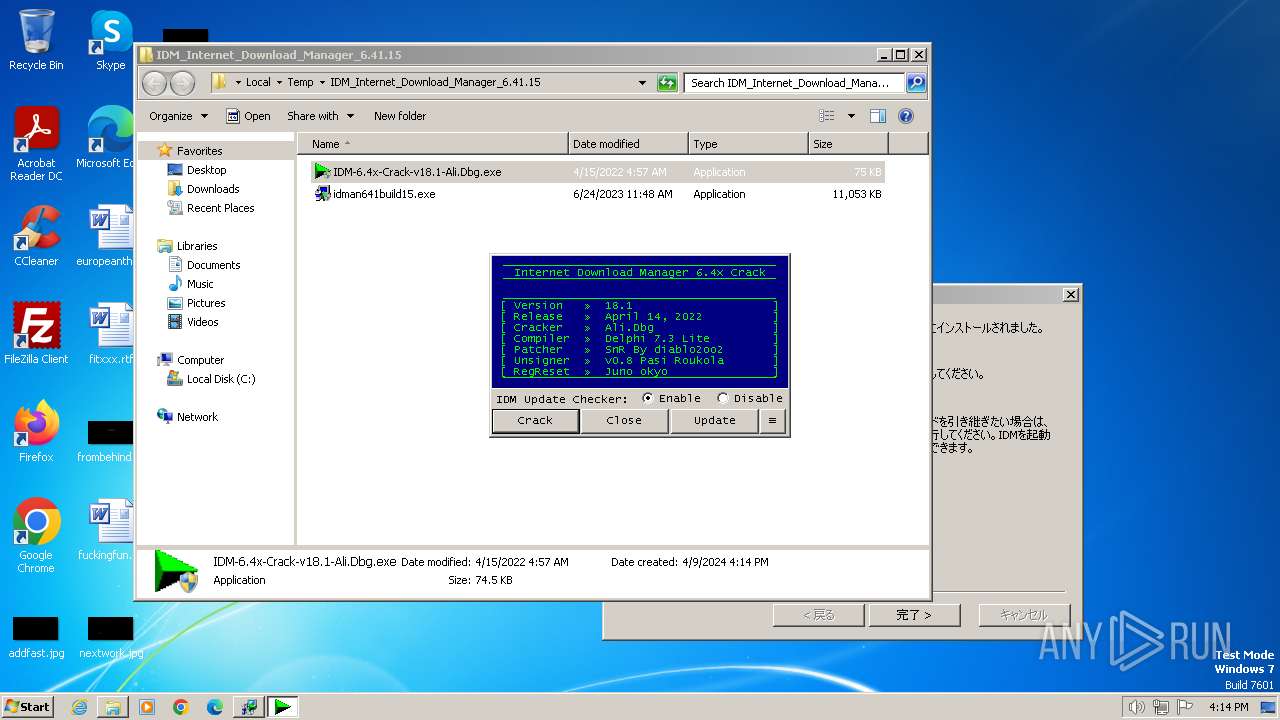
| File name: | IDM_Internet_Download_Manager_6.41.15.zip |
| Full analysis: | https://app.any.run/tasks/2a508e60-16b7-49e4-b439-93a6bf1c4a22 |
| Verdict: | Malicious activity |
| Analysis date: | April 09, 2024, 15:13:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 7FB595779FE077CFD365F9ADF0CA6BF8 |
| SHA1: | 1404659A1C3299BE54E13DC68CF6D38B849AF325 |
| SHA256: | 80CB63A22CED20C7DFD25EAE76355D196774F7571D871337FE123FB1A4D3A478 |
| SSDEEP: | 98304:EwTPbw0q5i173PEdLBfQmOA38QSV1Du9KK8F9wllFUYc2LBIWSRFH2uWByifDbLg:CvbXsR3DpQkM2KUVljjJeAzb4NE5 |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2120)
- IDM-6.4x-Crack-v18.1-Ali.Dbg.exe (PID: 1340)
- wscript.exe (PID: 2260)
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 2260)
- wscript.exe (PID: 1784)
- wscript.exe (PID: 2504)
Gets a file object corresponding to the file in a specified path (SCRIPT)
- wscript.exe (PID: 2260)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 2504)
- wscript.exe (PID: 1784)
Deletes a file (SCRIPT)
- wscript.exe (PID: 2260)
- wscript.exe (PID: 1784)
- wscript.exe (PID: 2504)
Copies file to a new location (SCRIPT)
- wscript.exe (PID: 2260)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 2504)
- wscript.exe (PID: 1784)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 2504)
- wscript.exe (PID: 1784)
Unusual connection from system programs
- wscript.exe (PID: 1784)
- wscript.exe (PID: 2504)
SUSPICIOUS
The process creates files with name similar to system file names
- IDM1.tmp (PID: 2168)
Creates a software uninstall entry
- IDM1.tmp (PID: 2168)
Searches for installed software
- IDM-6.4x-Crack-v18.1-Ali.Dbg.exe (PID: 1340)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 2260)
- wscript.exe (PID: 2504)
- wscript.exe (PID: 1784)
Executable content was dropped or overwritten
- IDM-6.4x-Crack-v18.1-Ali.Dbg.exe (PID: 1340)
- wscript.exe (PID: 2260)
Checks whether a specific file exists (SCRIPT)
- wscript.exe (PID: 2260)
The process executes VB scripts
- IDM-6.4x-Crack-v18.1-Ali.Dbg.exe (PID: 1340)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 2260)
- wscript.exe (PID: 2504)
- wscript.exe (PID: 1784)
Reads the Internet Settings
- wscript.exe (PID: 2504)
- wscript.exe (PID: 1784)
Starts application with an unusual extension
- idman641build15.exe (PID: 848)
Adds, changes, or deletes HTTP request header (SCRIPT)
- wscript.exe (PID: 1784)
- wscript.exe (PID: 2504)
INFO
Manual execution by a user
- idman641build15.exe (PID: 4044)
- IDM-6.4x-Crack-v18.1-Ali.Dbg.exe (PID: 1340)
- IDM-6.4x-Crack-v18.1-Ali.Dbg.exe (PID: 2832)
- idman641build15.exe (PID: 848)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2120)
Checks supported languages
- idman641build15.exe (PID: 848)
- IDM-6.4x-Crack-v18.1-Ali.Dbg.exe (PID: 1340)
- IDM1.tmp (PID: 2168)
Creates files or folders in the user directory
- IDM1.tmp (PID: 2168)
Reads the computer name
- IDM1.tmp (PID: 2168)
Create files in a temporary directory
- IDM1.tmp (PID: 2168)
- IDM-6.4x-Crack-v18.1-Ali.Dbg.exe (PID: 1340)
- idman641build15.exe (PID: 848)
Creates files in the program directory
- wscript.exe (PID: 2260)
- IDM1.tmp (PID: 2168)
Reads the machine GUID from the registry
- IDM1.tmp (PID: 2168)
Checks proxy server information
- wscript.exe (PID: 1784)
- wscript.exe (PID: 2504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2022:04:15 11:57:32 |
| ZipCRC: | 0x5884956f |
| ZipCompressedSize: | 32149 |
| ZipUncompressedSize: | 76288 |
| ZipFileName: | IDM-6.4x-Crack-v18.1-Ali.Dbg.exe |
Total processes
54
Monitored processes
9
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | "C:\Users\admin\AppData\Local\Temp\IDM_Internet_Download_Manager_6.41.15\idman641build15.exe" | C:\Users\admin\AppData\Local\Temp\IDM_Internet_Download_Manager_6.41.15\idman641build15.exe | explorer.exe | ||||||||||||
User: admin Company: Tonec Inc. Integrity Level: HIGH Description: Internet Download Manager installer Exit code: 0 Version: 6, 41, 15, 1 Modules
| |||||||||||||||
| 1340 | "C:\Users\admin\AppData\Local\Temp\IDM_Internet_Download_Manager_6.41.15\IDM-6.4x-Crack-v18.1-Ali.Dbg.exe" | C:\Users\admin\AppData\Local\Temp\IDM_Internet_Download_Manager_6.41.15\IDM-6.4x-Crack-v18.1-Ali.Dbg.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1784 | wscript.exe "C:\Users\admin\AppData\Local\Temp\\UPDT.vbs" /browser:"C:\Program Files\Google\Chrome\Application\chrome.exe" /crkver:"18.1" | C:\Windows\System32\wscript.exe | IDM-6.4x-Crack-v18.1-Ali.Dbg.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\IDM_Internet_Download_Manager_6.41.15.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2168 | "C:\Users\admin\AppData\Local\Temp\IDM_Setup_Temp\IDM1.tmp" -d "C:\Users\admin\AppData\Local\Temp\IDM_Setup_Temp\" | C:\Users\admin\AppData\Local\Temp\IDM_Setup_Temp\IDM1.tmp | — | idman641build15.exe | |||||||||||
User: admin Company: Tonec Inc. Integrity Level: HIGH Description: Internet Download Manager installer Version: 6, 41, 9, 1 Modules
| |||||||||||||||
| 2260 | wscript.exe "C:\Users\admin\AppData\Local\Temp\IDM_BAK.vbs" /idmdir:"C:\Program Files\Internet Download Manager\" | C:\Windows\System32\wscript.exe | IDM-6.4x-Crack-v18.1-Ali.Dbg.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2504 | wscript.exe "C:\Users\admin\AppData\Local\Temp\\UPDT.vbs" /browser:"C:\Program Files\Google\Chrome\Application\chrome.exe" /crkver:"18.1" | C:\Windows\System32\wscript.exe | IDM-6.4x-Crack-v18.1-Ali.Dbg.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2832 | "C:\Users\admin\AppData\Local\Temp\IDM_Internet_Download_Manager_6.41.15\IDM-6.4x-Crack-v18.1-Ali.Dbg.exe" | C:\Users\admin\AppData\Local\Temp\IDM_Internet_Download_Manager_6.41.15\IDM-6.4x-Crack-v18.1-Ali.Dbg.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 4044 | "C:\Users\admin\AppData\Local\Temp\IDM_Internet_Download_Manager_6.41.15\idman641build15.exe" | C:\Users\admin\AppData\Local\Temp\IDM_Internet_Download_Manager_6.41.15\idman641build15.exe | — | explorer.exe | |||||||||||
User: admin Company: Tonec Inc. Integrity Level: MEDIUM Description: Internet Download Manager installer Exit code: 3221226540 Version: 6, 41, 15, 1 Modules
| |||||||||||||||
Total events
15 079
Read events
14 918
Write events
142
Delete events
19
Modification events
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\IDM_Internet_Download_Manager_6.41.15.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
4
Suspicious files
17
Text files
3
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\IDM_Internet_Download_Manager_6.41.15\IDM-6.4x-Crack-v18.1-Ali.Dbg.exe | executable | |
MD5:— | SHA256:— | |||
| 2120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\IDM_Internet_Download_Manager_6.41.15\idman641build15.exe | executable | |
MD5:— | SHA256:— | |||
| 2168 | IDM1.tmp | C:\Users\admin\AppData\Local\Temp\IDM_Setup_Temp\IDMSetup2.log | binary | |
MD5:— | SHA256:— | |||
| 2168 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Uninstall IDM.lnk | binary | |
MD5:— | SHA256:— | |||
| 2168 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Uninstall IDM.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2168 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\license.lnk | binary | |
MD5:— | SHA256:— | |||
| 2168 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\license.lnk | binary | |
MD5:— | SHA256:— | |||
| 2168 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\IDM Help.lnk | binary | |
MD5:— | SHA256:— | |||
| 2168 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\IDM Help.lnk | binary | |
MD5:— | SHA256:— | |||
| 2168 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Internet Download Manager.lnk | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
9
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2504 | wscript.exe | GET | — | 104.110.191.158:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6e5b653400f9c322 | unknown | — | — | unknown |
2504 | wscript.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
2504 | wscript.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | — | — | unknown |
1784 | wscript.exe | GET | 304 | 104.110.191.139:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c851e7346fecb774 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
2504 | wscript.exe | 172.67.164.61:443 | idm.ckk.ir | CLOUDFLARENET | US | unknown |
2504 | wscript.exe | 104.110.191.158:80 | ctldl.windowsupdate.com | Akamai International B.V. | NL | unknown |
2504 | wscript.exe | 142.250.184.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1784 | wscript.exe | 172.67.164.61:443 | idm.ckk.ir | CLOUDFLARENET | US | unknown |
1784 | wscript.exe | 104.110.191.139:80 | ctldl.windowsupdate.com | Akamai International B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
idm.ckk.ir |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |