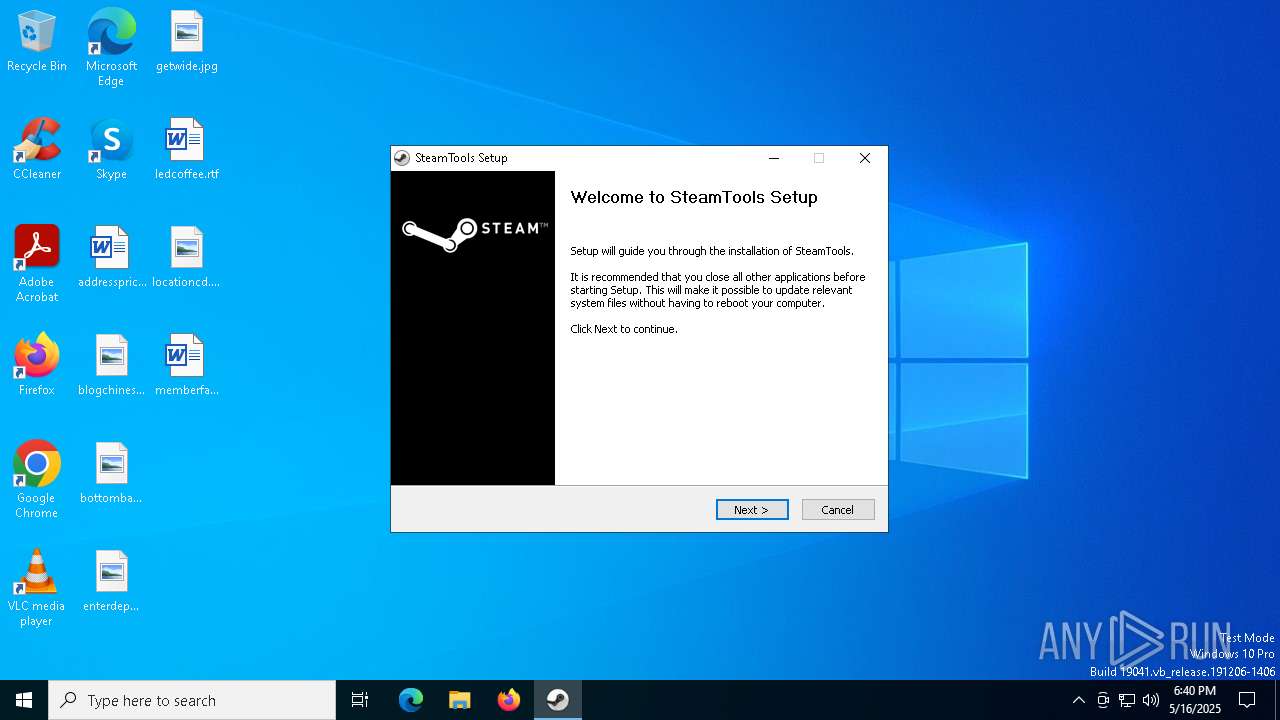
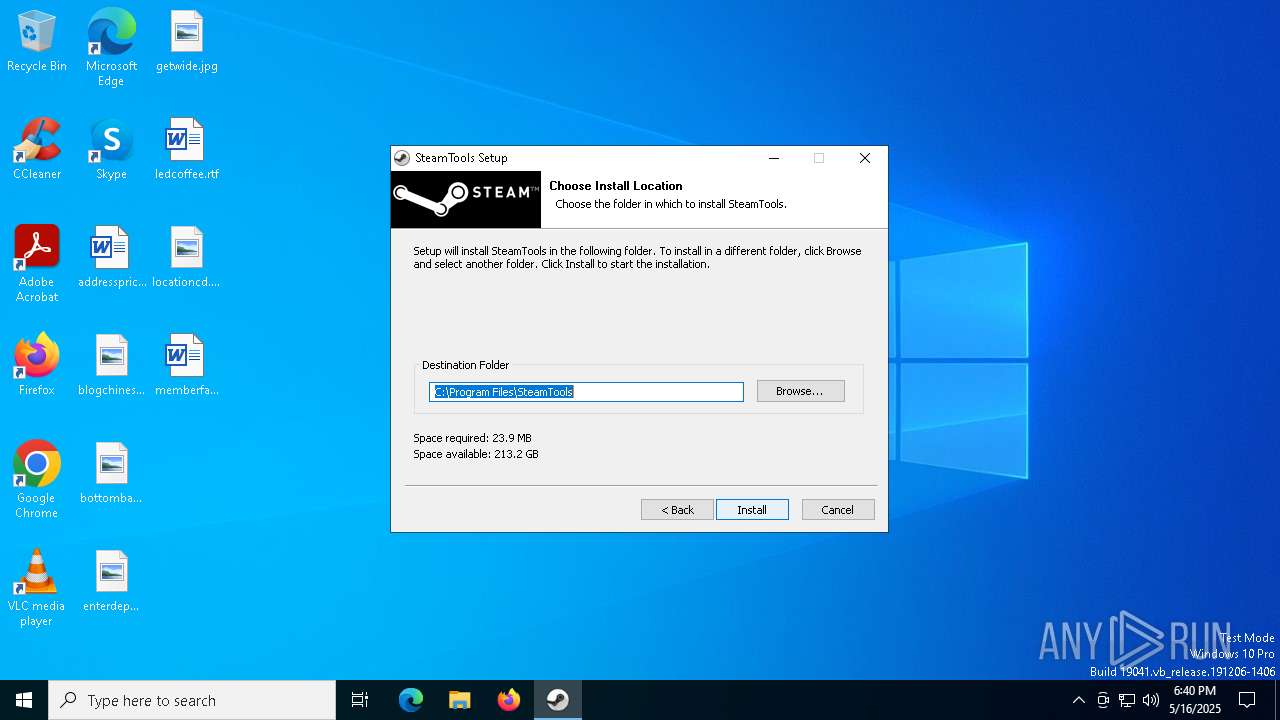
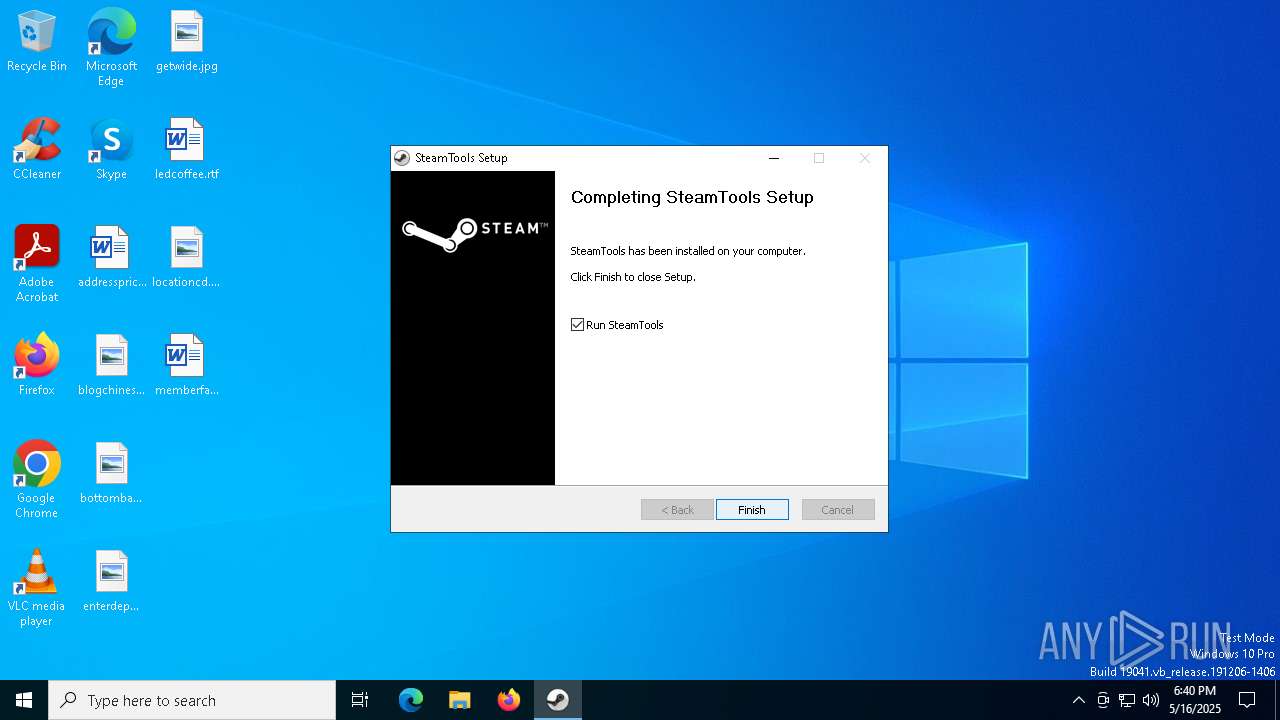
| File name: | st-setup-1.8.16.exe |
| Full analysis: | https://app.any.run/tasks/4b068f4c-61b7-452e-beeb-3bf437c5d55a |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 18:40:09 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64 (stripped to external PDB), for MS Windows, 9 sections |
| MD5: | 9C42F5CCAE30AFC9C70C924D543924F8 |
| SHA1: | 4E3C555CFEE82D23ACFDDA4754C0870F455156E8 |
| SHA256: | 80B6573208F2179C97CE64FF731269E349A07A3969C1198BF5A9092C5A01555C |
| SSDEEP: | 98304:J+dm8gYux7Ede4oqZSYVgnSoPV7dquc8GV+x7YjvyeSdRYTUhQ5WwwFPc7xqSG6i:PvI2akT6ZJJW6dEQK |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process creates files with name similar to system file names
- st-setup-1.8.16.exe (PID: 5548)
Malware-specific behavior (creating "System.dll" in Temp)
- st-setup-1.8.16.exe (PID: 5548)
Process drops legitimate windows executable
- st-setup-1.8.16.exe (PID: 5548)
Executable content was dropped or overwritten
- st-setup-1.8.16.exe (PID: 5548)
Uses ICACLS.EXE to modify access control lists
- st-setup-1.8.16.exe (PID: 5548)
The process drops C-runtime libraries
- st-setup-1.8.16.exe (PID: 5548)
Creates a software uninstall entry
- st-setup-1.8.16.exe (PID: 5548)
Explorer used for Indirect Command Execution
- explorer.exe (PID: 4172)
Executing commands from a ".bat" file
- explorer.exe (PID: 5756)
There is functionality for taking screenshot (YARA)
- st-setup-1.8.16.exe (PID: 5548)
Starts CMD.EXE for commands execution
- explorer.exe (PID: 5756)
INFO
Creates files in the program directory
- st-setup-1.8.16.exe (PID: 5548)
The sample compiled with english language support
- st-setup-1.8.16.exe (PID: 5548)
Create files in a temporary directory
- st-setup-1.8.16.exe (PID: 5548)
Creates files or folders in the user directory
- st-setup-1.8.16.exe (PID: 5548)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5756)
Checks supported languages
- SteamTools.exe (PID: 2340)
Checks proxy server information
- SteamTools.exe (PID: 2340)
Reads the computer name
- SteamTools.exe (PID: 2340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:02:08 08:30:59+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 2.38 |
| CodeSize: | 36352 |
| InitializedDataSize: | 51200 |
| UninitializedDataSize: | 246784 |
| EntryPoint: | 0x4560 |
| OSVersion: | 5.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
139
Monitored processes
11
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\SteamTools_launcher.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2340 | "C:\Program Files\SteamTools\SteamTools.exe" | C:\Program Files\SteamTools\SteamTools.exe | cmd.exe | ||||||||||||
User: admin Company: steamtools.net Integrity Level: MEDIUM Description: Steamtools Version: 1.8.1.5 Modules
| |||||||||||||||
| 4172 | "C:\WINDOWS\explorer.exe" "C:\Users\admin\AppData\Local\Temp\SteamTools_launcher.bat" | C:\Windows\explorer.exe | — | st-setup-1.8.16.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4620 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5116 | icacls "C:\Program Files\SteamTools" /grant:r "*S-1-5-32-545:(OI)(CI)F" /T | C:\Windows\System32\icacls.exe | — | st-setup-1.8.16.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5176 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5548 | "C:\Users\admin\AppData\Local\Temp\st-setup-1.8.16.exe" | C:\Users\admin\AppData\Local\Temp\st-setup-1.8.16.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 5756 | C:\WINDOWS\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6620 | "C:\Users\admin\AppData\Local\Temp\st-setup-1.8.16.exe" | C:\Users\admin\AppData\Local\Temp\st-setup-1.8.16.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
1 223
Read events
1 212
Write events
11
Delete events
0
Modification events
| (PID) Process: | (5548) st-setup-1.8.16.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SteamTools |
| Operation: | write | Name: | DisplayName |
Value: SteamTools | |||
| (PID) Process: | (5548) st-setup-1.8.16.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SteamTools |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\SteamTools\Uninstall.exe" | |||
| (PID) Process: | (5548) st-setup-1.8.16.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SteamTools |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Program Files\SteamTools\Uninstall.exe" /S | |||
| (PID) Process: | (5548) st-setup-1.8.16.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SteamTools |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\SteamTools | |||
| (PID) Process: | (5548) st-setup-1.8.16.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SteamTools |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\SteamTools\SteamTools.exe,0 | |||
| (PID) Process: | (5548) st-setup-1.8.16.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SteamTools |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (5548) st-setup-1.8.16.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SteamTools |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
| (PID) Process: | (5548) st-setup-1.8.16.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\SteamTools |
| Operation: | write | Name: | Language |
Value: 1033 | |||
| (PID) Process: | (2340) SteamTools.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Valve\Steamtools |
| Operation: | write | Name: | fScreenIndex |
Value: 0 | |||
| (PID) Process: | (2340) SteamTools.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Valve\Steamtools |
| Operation: | write | Name: | fPosition |
Value: @Point(610 100) | |||
Executable files
17
Suspicious files
3
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5548 | st-setup-1.8.16.exe | C:\Users\admin\AppData\Local\Temp\nshD4B9.tmp\nsDialogs.dll | executable | |
MD5:9CBB2C67258DF6CFC08E060BD8AB8309 | SHA256:4AEC3A5A78295861C8AD96B70B0520C541EA4DF60651615802AD066780CE2296 | |||
| 5548 | st-setup-1.8.16.exe | C:\Users\admin\AppData\Local\Temp\nshD4B9.tmp\modern-wizard.bmp | image | |
MD5:3614A4BE6B610F1DAF6C801574F161FE | SHA256:16E0EDC9F47E6E95A9BCAD15ADBDC46BE774FBCD045DD526FC16FC38FDC8D49B | |||
| 5548 | st-setup-1.8.16.exe | C:\Users\admin\AppData\Local\Temp\nshD4B9.tmp\System.dll | executable | |
MD5:E74573CE106DD95B148BB8B1EF8E3418 | SHA256:D12BC87BF84C51C13F0877949BCD719C5B90D9DF8658A2F8036DDC262CB0D87B | |||
| 5548 | st-setup-1.8.16.exe | C:\Program Files\SteamTools\vcruntime140.dll | executable | |
MD5:0C583614EB8FFB4C8C2D9E9880220F1D | SHA256:6CADB4FEF773C23B511ACC8B715A084815C6E41DD8C694BC70090A97B3B03FB9 | |||
| 5548 | st-setup-1.8.16.exe | C:\Users\admin\AppData\Local\Temp\nshD4B8.tmp | — | |
MD5:— | SHA256:— | |||
| 5548 | st-setup-1.8.16.exe | C:\Program Files\SteamTools\imageformats\qico.dll | executable | |
MD5:A9ABD4329CA364D4F430EDDCB471BE59 | SHA256:1982A635DB9652304131C9C6FF9A693E70241600D2EF22B354962AA37997DE0B | |||
| 5548 | st-setup-1.8.16.exe | C:\Program Files\SteamTools\Qt5Svg.dll | executable | |
MD5:03761F923E52A7269A6E3A7452F6BE93 | SHA256:7348CFC6444438B8845FB3F59381227325D40CA2187D463E82FC7B8E93E38DB5 | |||
| 5548 | st-setup-1.8.16.exe | C:\Users\admin\AppData\Local\Temp\nshD4B9.tmp\nsExec.dll | executable | |
MD5:DAD419C254E3D26C6329061B8D404093 | SHA256:1B19124DF239FA052CE3E8E3746022E38C149F75A11D7474D6EB60038E86B853 | |||
| 5548 | st-setup-1.8.16.exe | C:\Program Files\SteamTools\platforms\qwindows.dll | executable | |
MD5:4931FCD0E86C4D4F83128DC74E01EAAD | SHA256:3333BA244C97264E3BD19DB5953EFA80A6E47AACED9D337AC3287EC718162B85 | |||
| 5548 | st-setup-1.8.16.exe | C:\Program Files\SteamTools\Qt5Core.dll | executable | |
MD5:817520432A42EFA345B2D97F5C24510E | SHA256:8D2FF4CE9096DDCCC4F4CD62C2E41FC854CFD1B0D6E8D296645A7F5FD4AE565A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
20
DNS requests
16
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2340 | SteamTools.exe | GET | 302 | 122.188.44.139:80 | http://new-service.biliapi.net/picture/chatres/update/version2.txt | unknown | — | — | unknown |
2340 | SteamTools.exe | GET | 200 | 8.133.135.83:80 | http://stools.oss-cn-shanghai.aliyuncs.com/version2.txt | unknown | — | — | unknown |
4620 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4620 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
976 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.164:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6544 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
steamtools.info |
| unknown |
new-service.biliapi.net |
| unknown |
stools.oss-cn-shanghai.aliyuncs.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2340 | SteamTools.exe | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
2196 | svchost.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
2340 | SteamTools.exe | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |