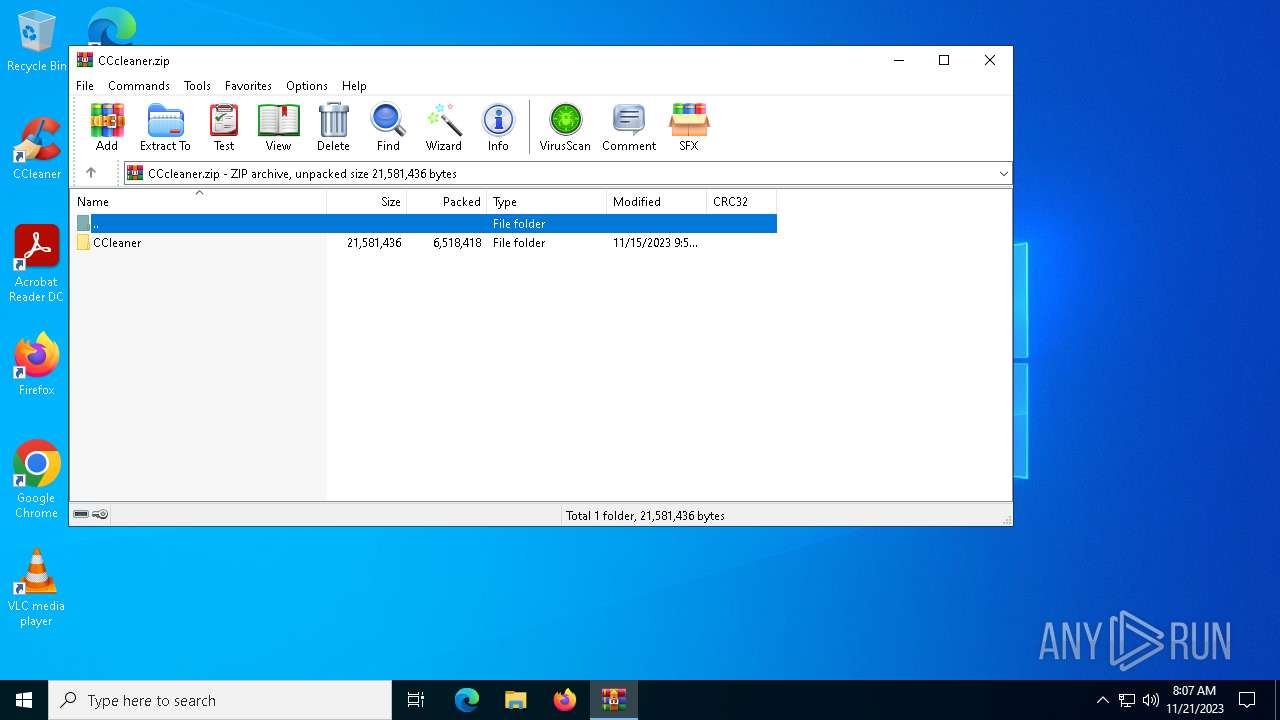
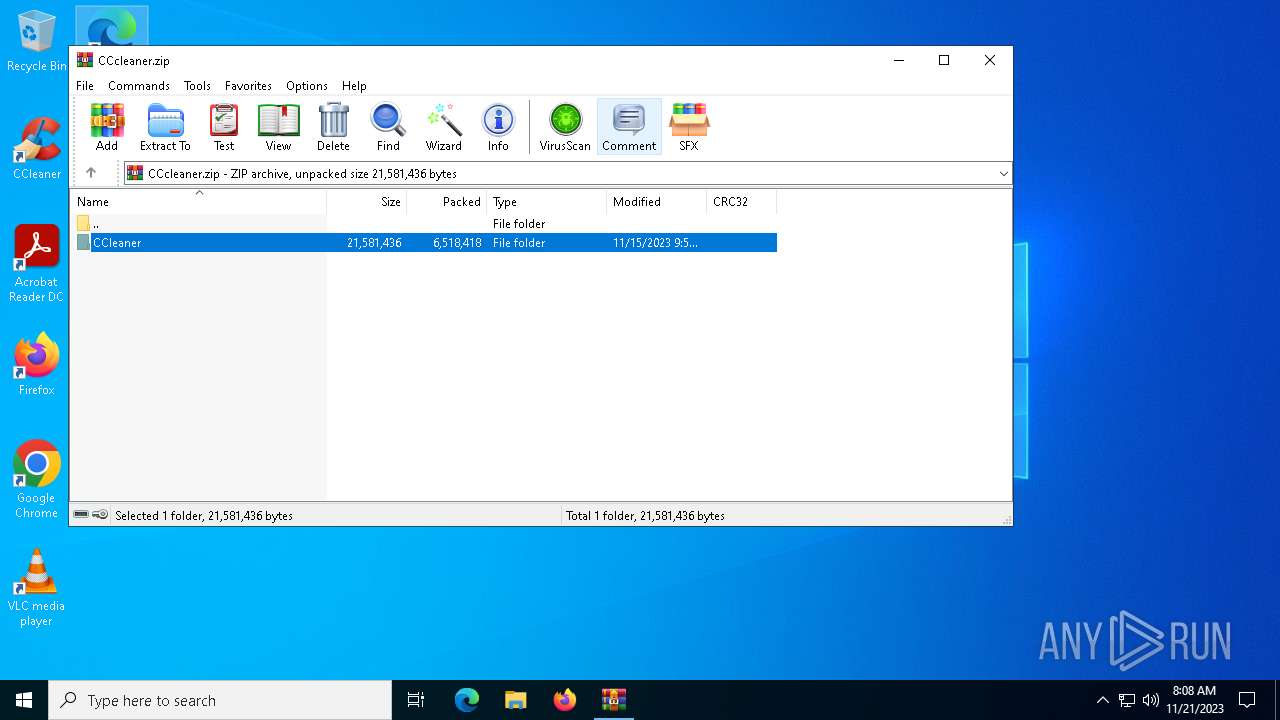
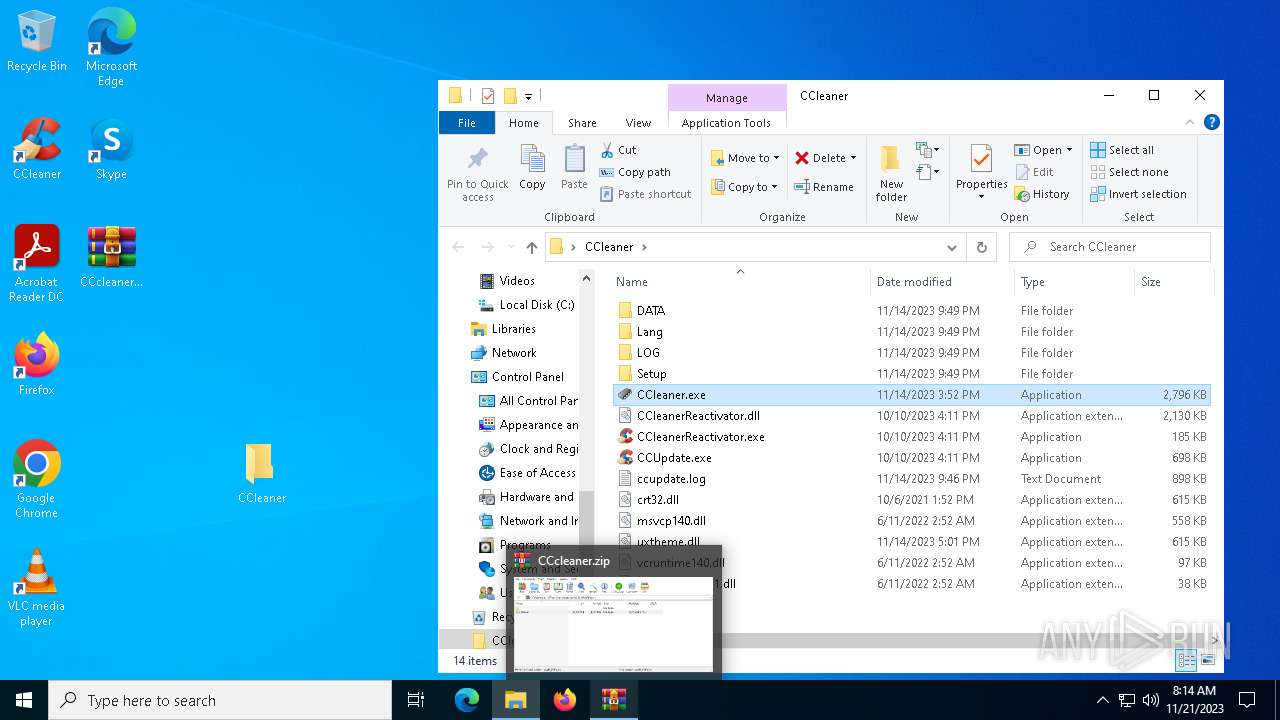
| File name: | CCcleaner.zip |
| Full analysis: | https://app.any.run/tasks/8fd920a0-f2e5-4335-83f1-2e80006e35a0 |
| Verdict: | Malicious activity |
| Analysis date: | November 21, 2023, 08:07:43 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 619601435755A37E712CF52706AD0383 |
| SHA1: | 6FD9C3C14B7263E85A60A37F5C5A339877053B5A |
| SHA256: | 80B33A175007E37759BC6F1AD34F8C88AAFD45DC03FE452168DB85FFEC490809 |
| SSDEEP: | 98304:hZTdsDCPt9SY/Xs37pzyzL3O2ikjRFUbVDQhEiMtYDnFQ3kmvRlP2pOFyOFeqFb2:VU0B4vccv5tHHZQ44 |
MALICIOUS
Application was injected by another process
- explorer.exe (PID: 384)
Runs injected code in another process
- rundll32.exe (PID: 1624)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 4928)
Uses RUNDLL32.EXE to load library
- CCleaner.exe (PID: 2884)
Executes application which crashes
- explorer.exe (PID: 384)
The process creates files with name similar to system file names
- WerFault.exe (PID: 940)
Reads security settings of Internet Explorer
- SearchApp.exe (PID: 5612)
Checks Windows Trust Settings
- SearchApp.exe (PID: 5612)
INFO
Manual execution by a user
- CCleaner.exe (PID: 2884)
Checks supported languages
- CCleaner.exe (PID: 2884)
- GameBar.exe (PID: 1720)
- TextInputHost.exe (PID: 4992)
- StartMenuExperienceHost.exe (PID: 1484)
- SearchApp.exe (PID: 5612)
- SystemSettings.exe (PID: 3864)
Checks proxy server information
- explorer.exe (PID: 384)
- SearchApp.exe (PID: 5612)
Reads the computer name
- GameBar.exe (PID: 1720)
- TextInputHost.exe (PID: 4992)
- StartMenuExperienceHost.exe (PID: 1484)
- SystemSettings.exe (PID: 3864)
- SearchApp.exe (PID: 5612)
Reads security settings of Internet Explorer
- explorer.exe (PID: 384)
Reads the software policy settings
- explorer.exe (PID: 384)
- SearchApp.exe (PID: 5612)
Creates files or folders in the user directory
- WerFault.exe (PID: 940)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 1484)
- SearchApp.exe (PID: 5612)
Process checks Internet Explorer phishing filters
- SearchApp.exe (PID: 5612)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5612)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:11:15 01:53:30 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | CCleaner/ |
Total processes
162
Monitored processes
15
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 384 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1467 Version: 10.0.19041.1023 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 940 | C:\WINDOWS\system32\WerFault.exe -u -p 384 -s 9504 | C:\Windows\System32\WerFault.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1312 | C:\Windows\System32\oobe\UserOOBEBroker.exe -Embedding | C:\Windows\System32\oobe\UserOOBEBroker.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: User OOBE Broker Exit code: 0 Version: 10.0.19041.746 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1484 | "C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1624 | rundll32 ccupdate.log, #45 | C:\Windows\System32\rundll32.exe | — | CCleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1720 | "C:\Program Files\WindowsApps\Microsoft.XboxGamingOverlay_2.34.28001.0_x64__8wekyb3d8bbwe\GameBar.exe" -ServerName:App.AppXbdkk0yrkwpcgeaem8zk81k8py1eaahny.mca | C:\Program Files\WindowsApps\Microsoft.XboxGamingOverlay_2.34.28001.0_x64__8wekyb3d8bbwe\GameBar.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
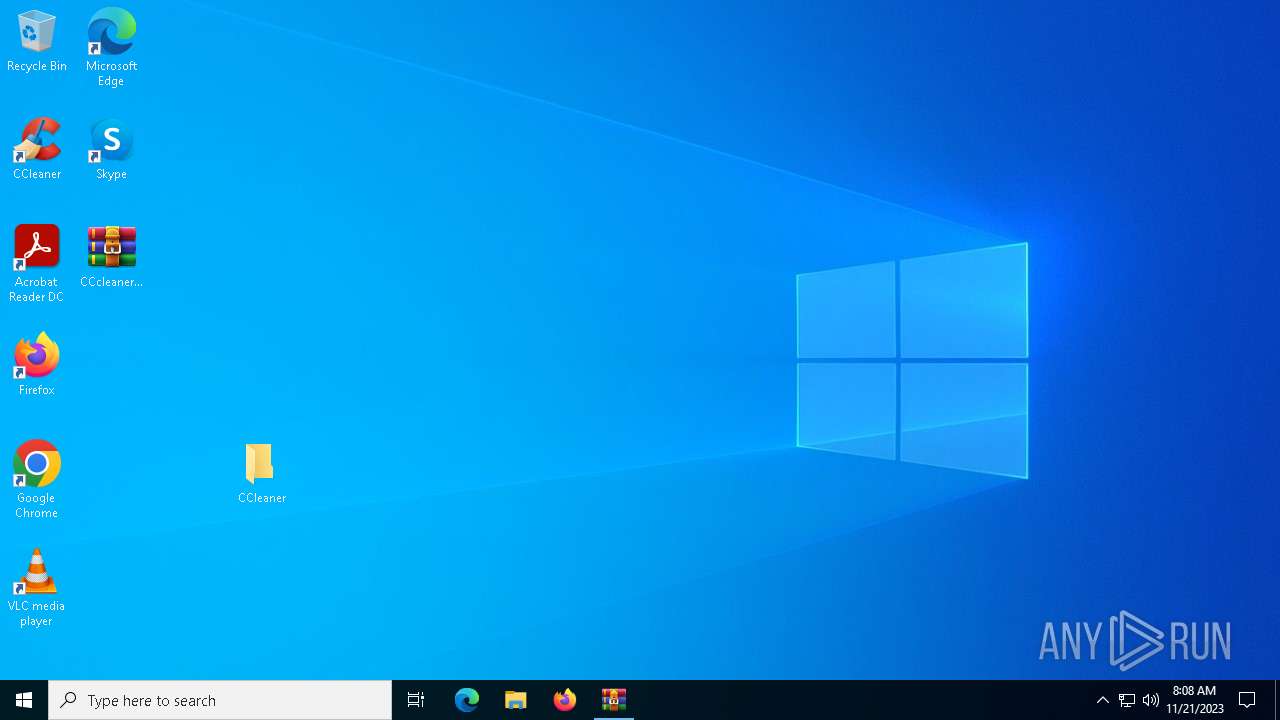
| 2884 | "C:\Users\admin\Desktop\CCleaner\CCleaner.exe" | C:\Users\admin\Desktop\CCleaner\CCleaner.exe | — | explorer.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: CPU Stress Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3112 | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe -Embedding | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 19.043.0304.0013 Modules
| |||||||||||||||
| 3864 | "C:\Windows\ImmersiveControlPanel\SystemSettings.exe" -ServerName:microsoft.windows.immersivecontrolpanel | C:\Windows\ImmersiveControlPanel\SystemSettings.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Settings Exit code: 0 Version: 10.0.19041.1266 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4036 | C:\WINDOWS\System32\mobsync.exe -Embedding | C:\Windows\System32\mobsync.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 404
Read events
14 276
Write events
127
Delete events
1
Modification events
| (PID) Process: | (384) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F00620000000000000000000000010000000000000014001F50 | |||
| (PID) Process: | (4928) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | VerInfo |
Value: 003C050012F8FE6A437AD701 | |||
| (PID) Process: | (384) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010008000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C00000019000000000000004100630072006F0062006100740020005200650061006400650072002000440043002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C00000001000000000000000200010000000000000000000100000000000000020001000000000000000000110000000600000001000000080000000000000000000000000000000000000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F0700 | |||
| (PID) Process: | (384) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (384) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010009000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C00000019000000000000004100630072006F0062006100740020005200650061006400650072002000440043002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C00000011000000000000004300430063006C00650061006E00650072002E007A00690070003E0020002000000001000000000000000200010000000000000000000100000000000000020001000000000000000000110000000600000001000000090000000000000000000000000000000000000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F07000000803F000000400800 | |||
| (PID) Process: | (384) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: AA70CD6400000000 | |||
| (PID) Process: | (4928) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\SpybotAntiBeaconPortable-safer-networking.org_3.7.0.paf.zip | |||
| (PID) Process: | (4928) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\MicrosoftEdgePolicyTemplates.cab | |||
| (PID) Process: | (4928) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\MicrosoftEdgePolicyTemplates.zip | |||
| (PID) Process: | (4928) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
71
Suspicious files
23
Text files
122
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4928.7598\CCleaner\CCleanerReactivator.exe | executable | |
MD5:BB73936B4FEC1E25EF5686BB98ED3643 | SHA256:CC7821006F58120EC7C5B97777E39760C0C295B8BE806253D5CEBEFE23AD0588 | |||
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4928.7598\CCleaner\CCUpdate.exe | executable | |
MD5:0F0B90A01F049665CA511335F9F0BF2E | SHA256:4AD9635351C8E8579C4D4C2BDD679EA7B135EC329ADC6FD5D8211255E2E666BE | |||
| 384 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4928.7598\CCleaner\Lang\lang-1027.dll | executable | |
MD5:17F5CECE4737701CF57683C696547472 | SHA256:E9E7E2CD174CD2CD4A309721F2FB2C68C19B6A9CA8376A572835DEBABE68D61E | |||
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4928.7598\CCleaner\Lang\lang-1025.dll | executable | |
MD5:5E2A85933677F7852FD56D19182A3C6C | SHA256:42BD1929BA2FD149AA2F00ABC50FCB8C52575AFC35A5B6EEAA0E38781997A1EA | |||
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4928.7598\CCleaner\DATA\burger_client\8866F8A9-70C9-43A2-BFBE-EE00AA2DC417\44ED97C8-2D40-4A50-913D-673F6858B9AF | binary | |
MD5:30271AEE7B8F08D7C4780BEF4A88E460 | SHA256:301ECABE1DFA440BBC432619E41A958A11AEFF5B4EE6BDE4254D3FC0BFCC9F09 | |||
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4928.7598\CCleaner\CCleanerReactivator.dll | executable | |
MD5:DD7A2B074035E6DDE50DB98240FE7D3C | SHA256:FA58923B62197227E716C2D9AB096B8314C5478650048FD010BAC9F965CA6D34 | |||
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4928.7598\CCleaner\DATA\StateHistory\DUState 23-11-14 03-27-08.dat | binary | |
MD5:04FE9694BCF371E67C7DCDFAADE644D9 | SHA256:48D21A251C1E7723FD8925EE7187666398B1A8A820C12584F54B1DE1120B500E | |||
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Roaming\WinRAR\version.dat | binary | |
MD5:85BA0FB12F0CF5C5F68E6CF1EAEE5EA7 | SHA256:96F70D47C20EC3BCBC04ABCBA99335BAE1242FD3769240823133758AAA7F806E | |||
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4928.7598\CCleaner\DATA\DUState.dat | binary | |
MD5:04FE9694BCF371E67C7DCDFAADE644D9 | SHA256:48D21A251C1E7723FD8925EE7187666398B1A8A820C12584F54B1DE1120B500E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
21
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4832 | svchost.exe | GET | 200 | 23.58.217.29:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | binary | 814 b | unknown |
1052 | SIHClient.exe | GET | 200 | 23.58.217.29:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | binary | 409 b | unknown |
1052 | SIHClient.exe | GET | 200 | 23.58.217.29:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | binary | 418 b | unknown |
5612 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
5612 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
2980 | svchost.exe | GET | 200 | 104.80.241.249:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
1328 | MoUsoCoreWorker.exe | GET | 200 | 23.58.217.29:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | binary | 814 b | unknown |
1652 | svchost.exe | GET | 200 | 23.58.217.29:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | binary | 814 b | unknown |
2984 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3792 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1328 | MoUsoCoreWorker.exe | 23.58.217.29:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
4832 | svchost.exe | 23.58.217.29:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
1652 | svchost.exe | 23.58.217.29:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1328 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2984 | OfficeClickToRun.exe | 20.189.173.13:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2984 | OfficeClickToRun.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1052 | SIHClient.exe | 40.127.169.103:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
hangdrums.fr |
| unknown |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
ecs.office.com |
| unknown |