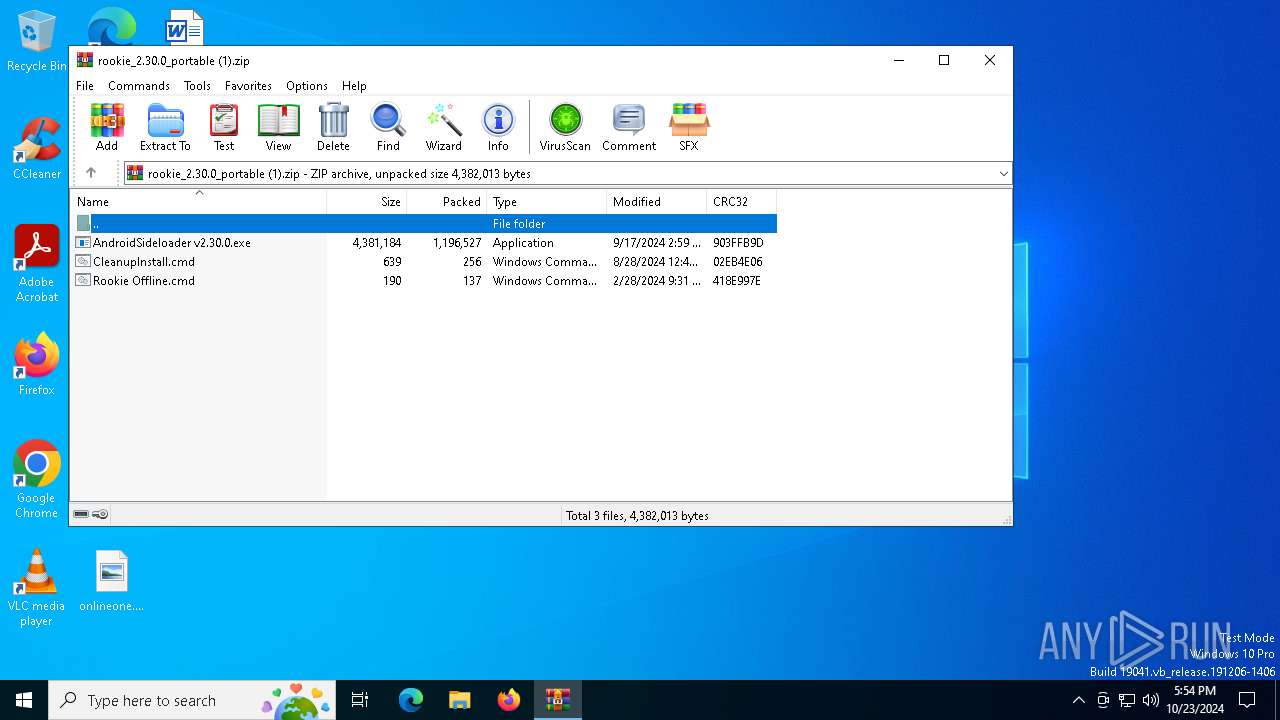
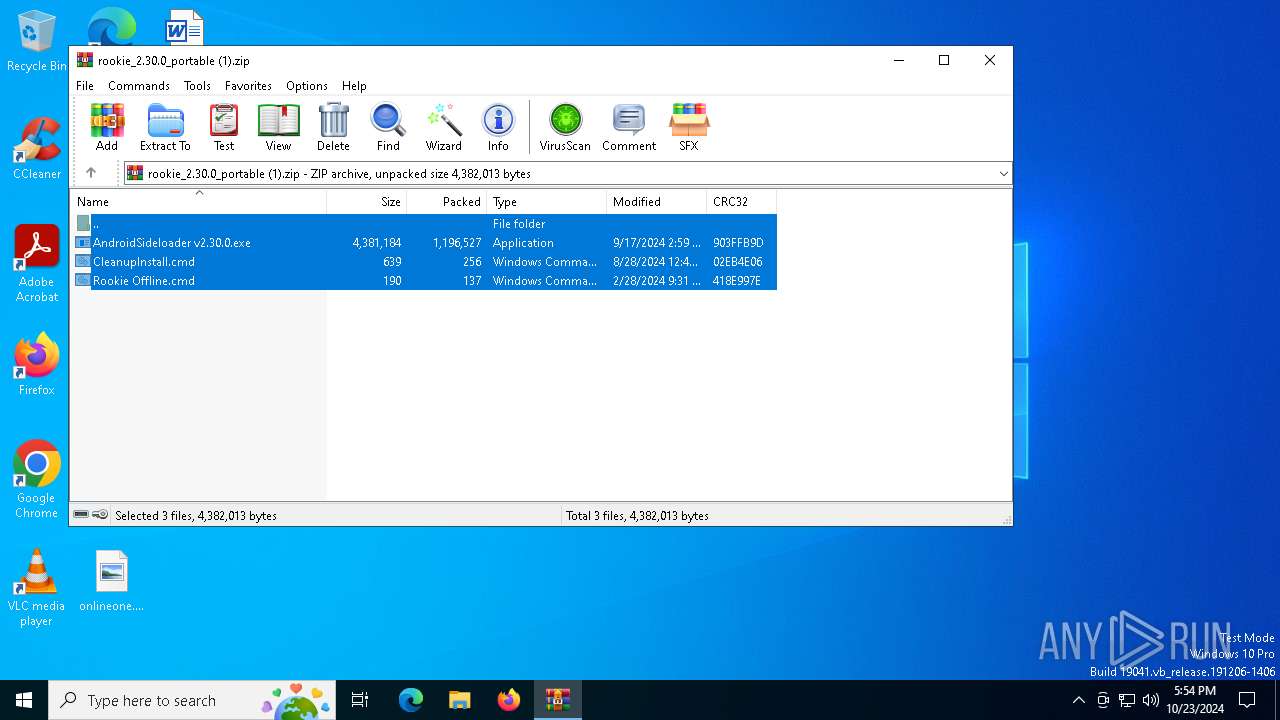
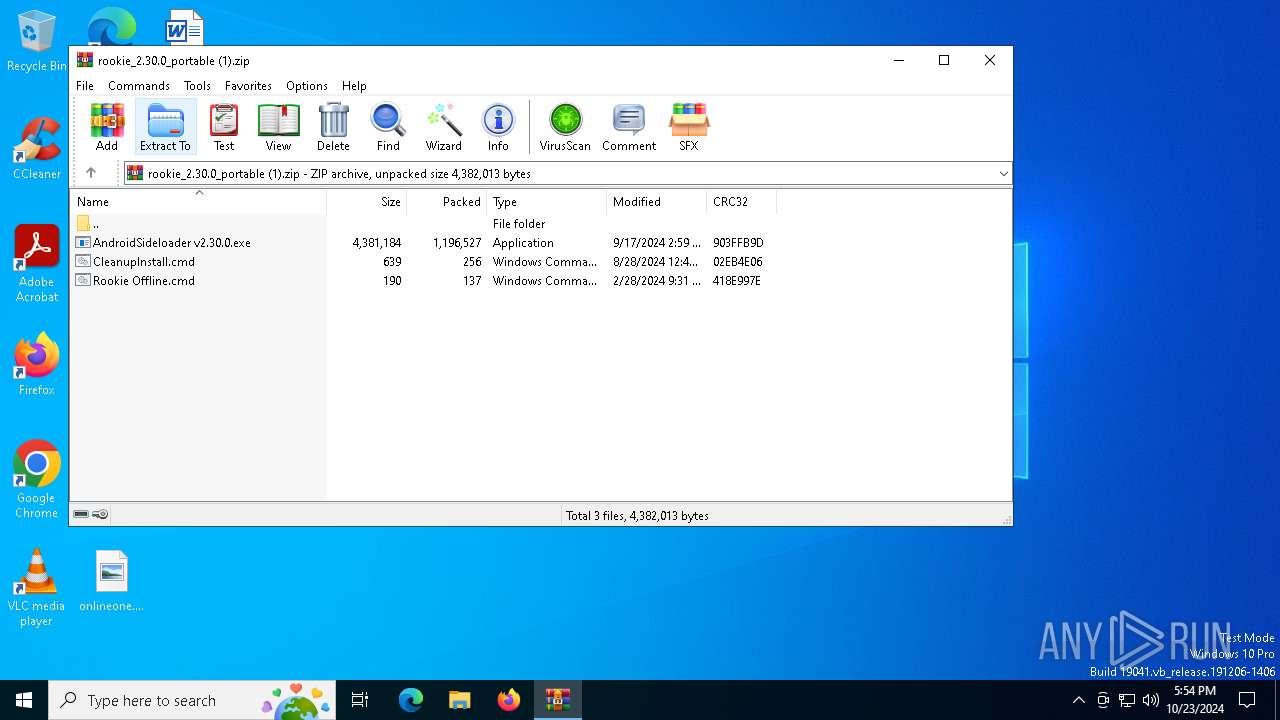
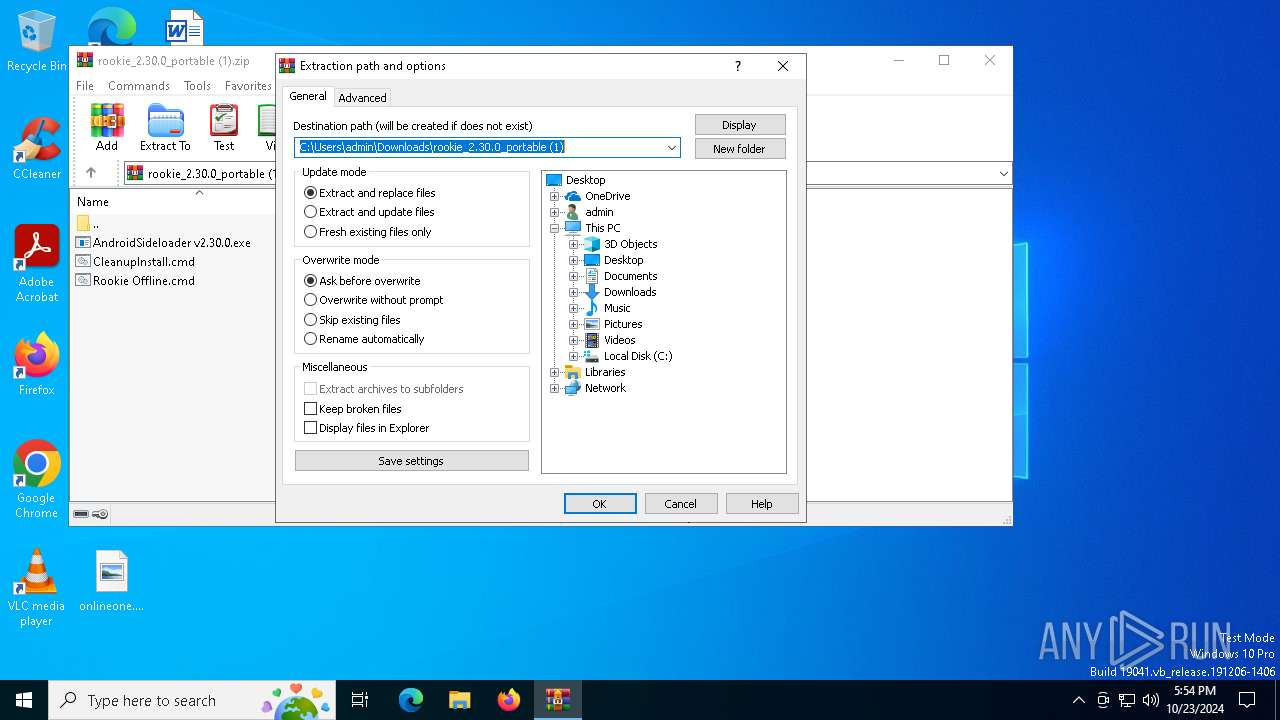
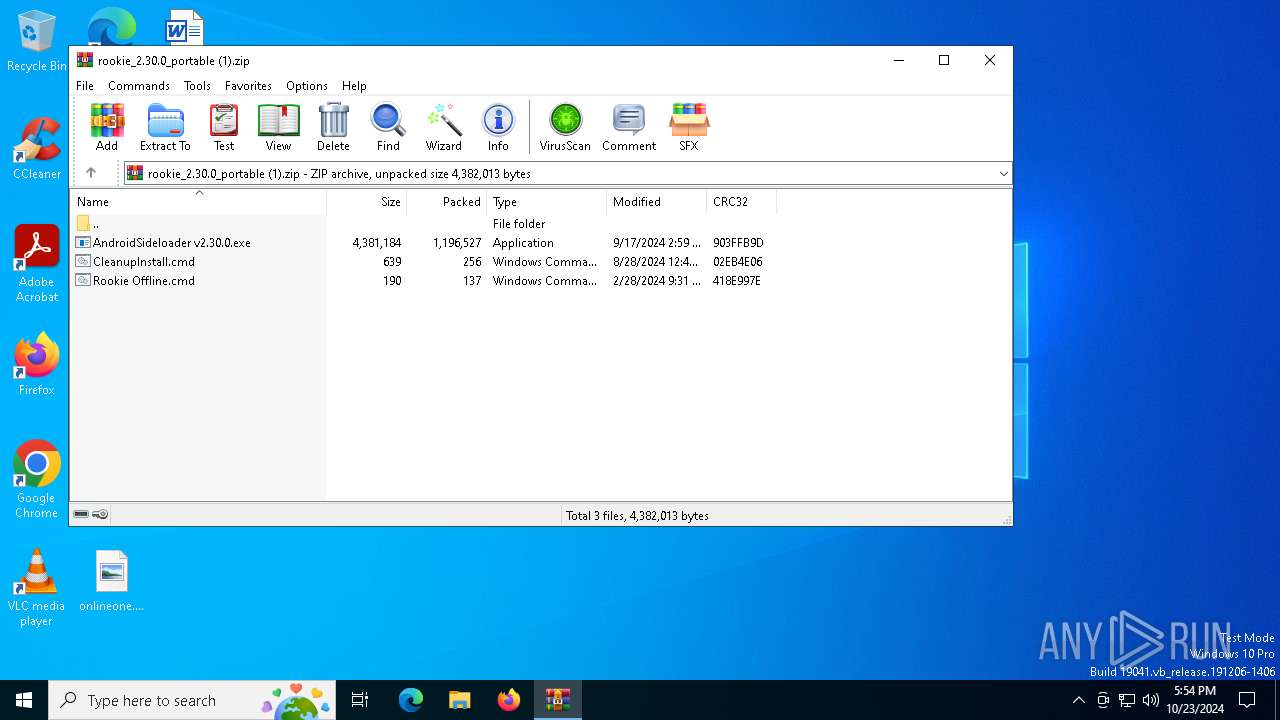
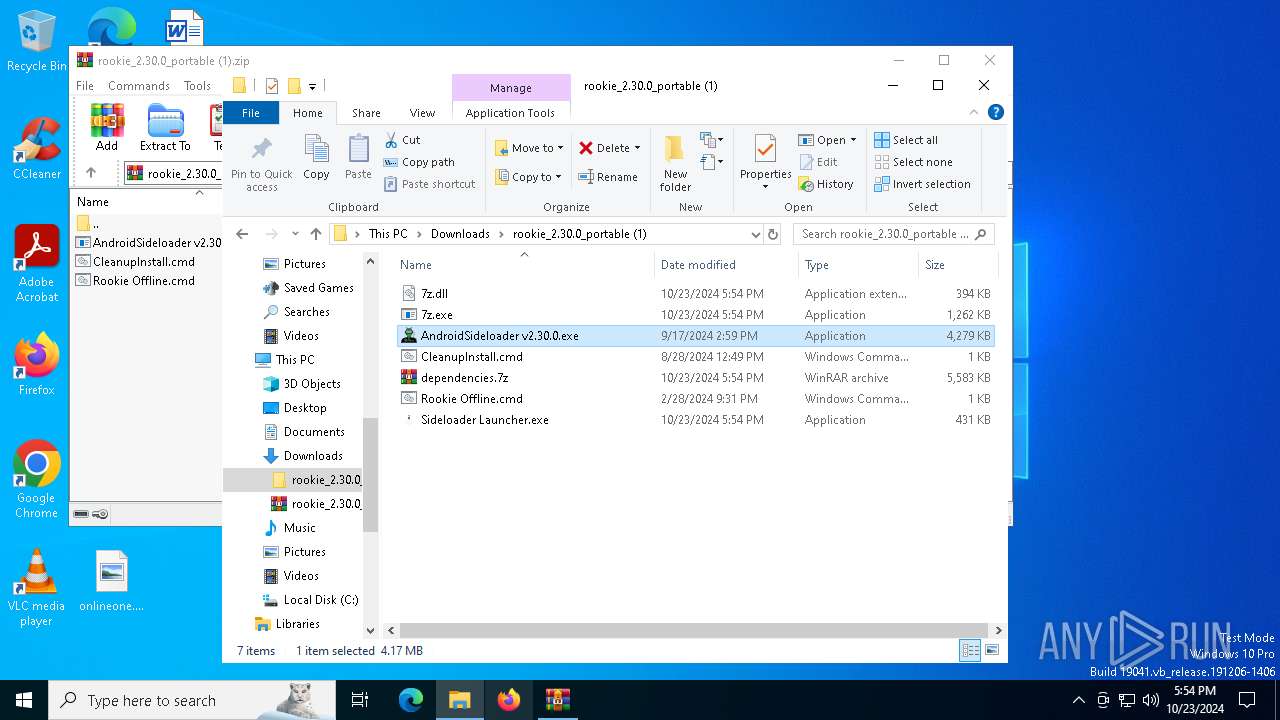
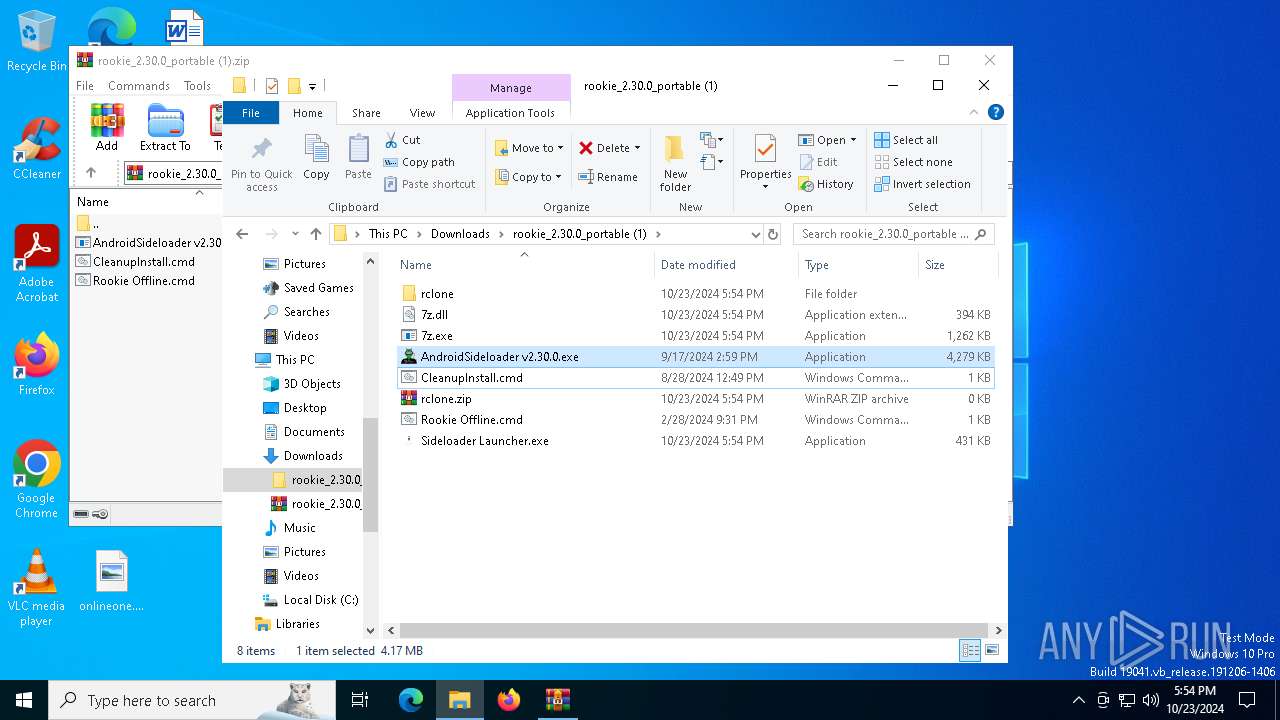
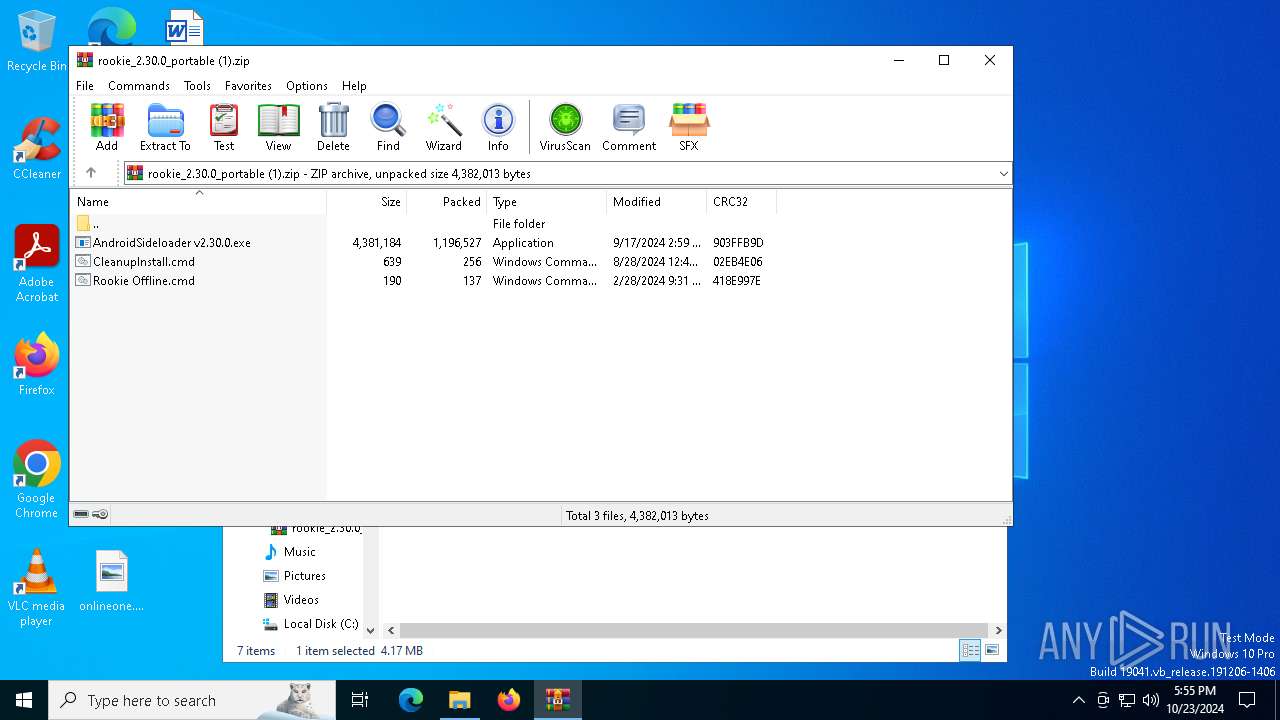
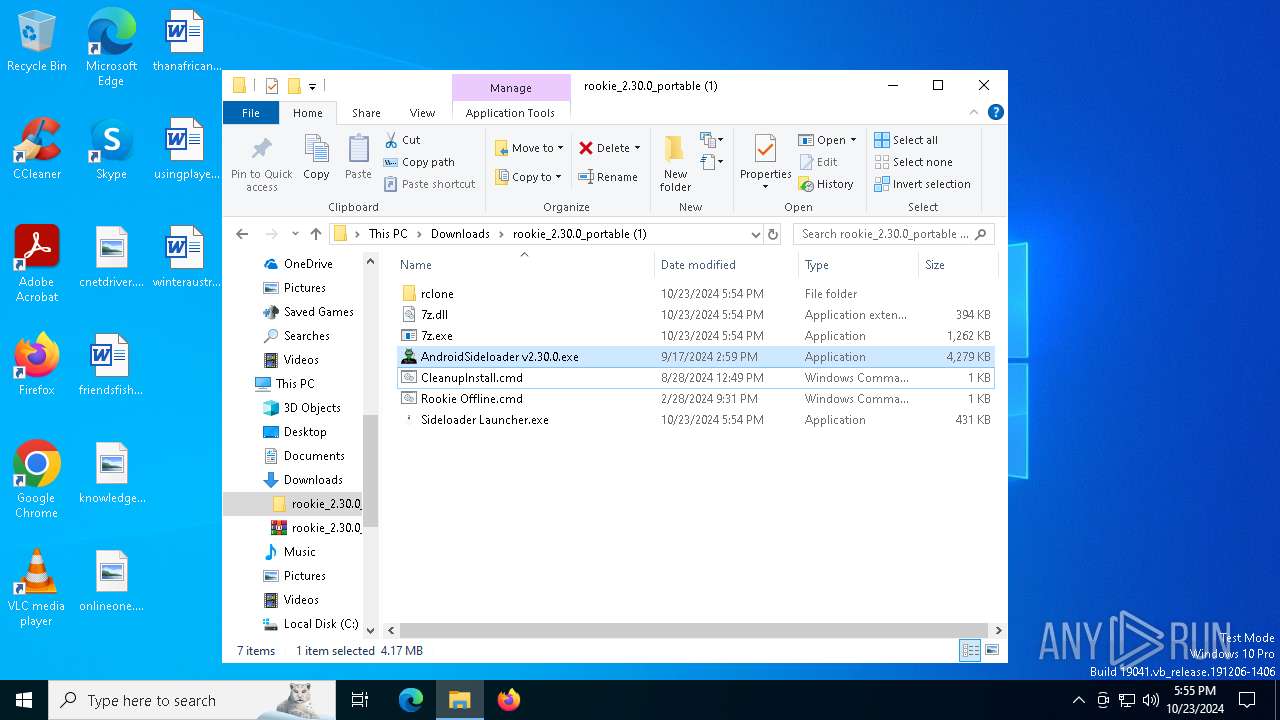
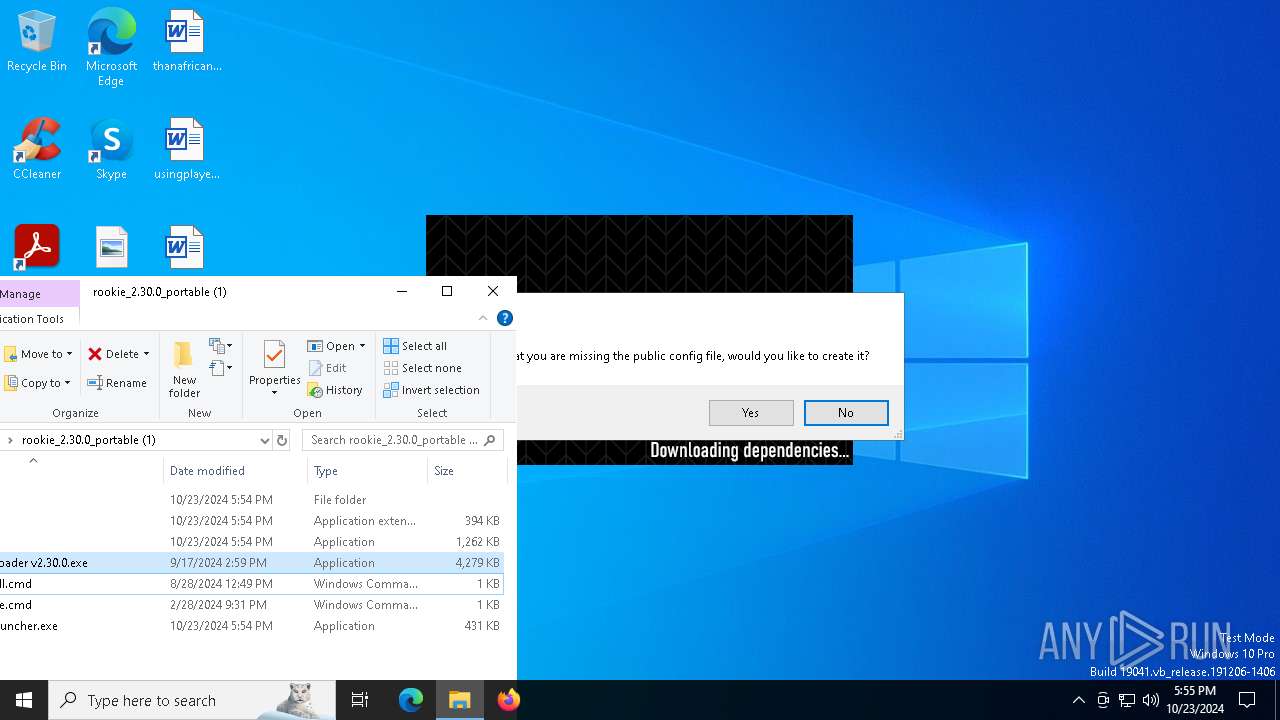
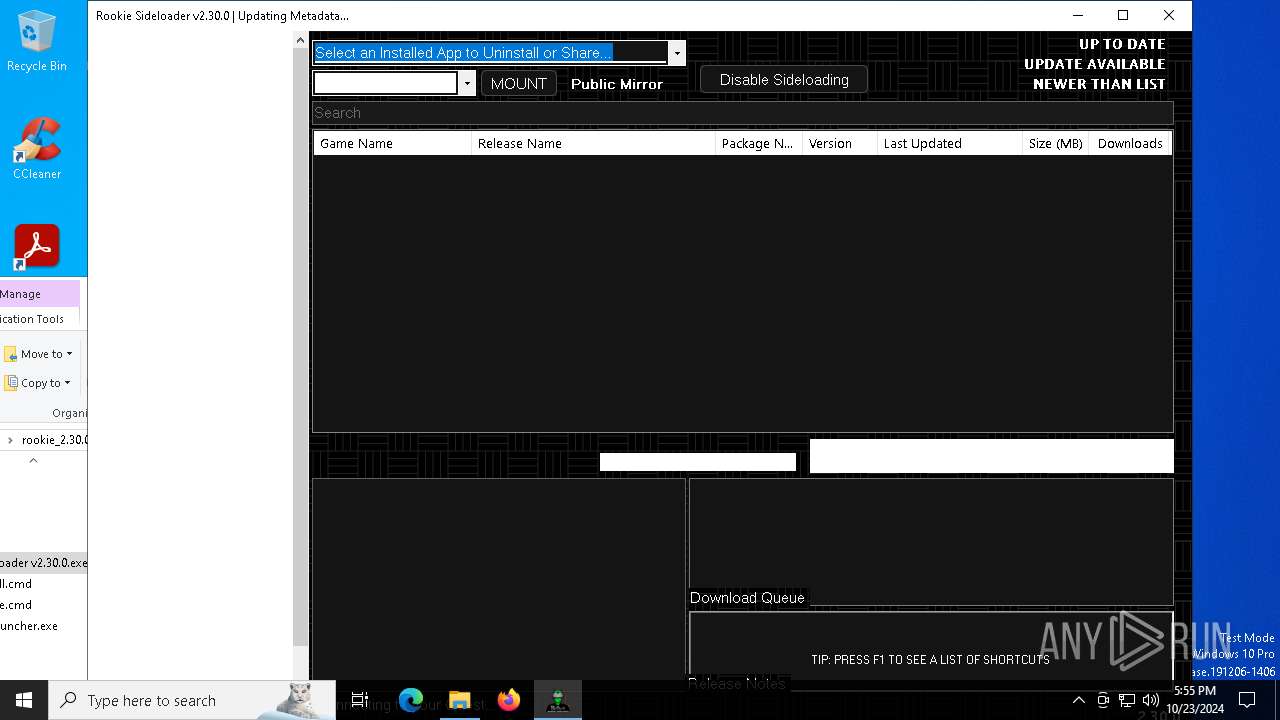
| File name: | rookie_2.30.0_portable (1).zip |
| Full analysis: | https://app.any.run/tasks/808c4a8f-5ca7-447e-bdb0-2477255d24d0 |
| Verdict: | Malicious activity |
| Analysis date: | October 23, 2024, 17:54:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 843C079644D66AACCBB5B5D177C45626 |
| SHA1: | EB8375F9EDF1D54484CD09AF94107DF9E6E08C93 |
| SHA256: | 80A992886EE740FC5320C0F27D40B528B6EBCBE9DF290AB47B519E98D76D365D |
| SSDEEP: | 49152:P1A/iVPC8CQH3dSS7G0vw1a4ehwP3WJHezG8oMsO91S7tXu6pw5EmMmVxWgkZVqw:PTZ20SMGX1/3WYGlMsY6teT5a+wSJq/F |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1176)
SUSPICIOUS
Executable content was dropped or overwritten
- 7z.exe (PID: 2980)
- AndroidSideloader v2.30.0.exe (PID: 2184)
Application launched itself
- adb.exe (PID: 6572)
Drops 7-zip archiver for unpacking
- AndroidSideloader v2.30.0.exe (PID: 2184)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1176)
Manual execution by a user
- AndroidSideloader v2.30.0.exe (PID: 2184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:09:17 09:59:46 |
| ZipCRC: | 0x903ffb9d |
| ZipCompressedSize: | 1196527 |
| ZipUncompressedSize: | 4381184 |
| ZipFileName: | AndroidSideloader v2.30.0.exe |
Total processes
146
Monitored processes
18
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 860 | "C:\Users\admin\Downloads\rookie_2.30.0_portable (1)\rclone\rclone.exe" sync ":http:/meta.7z" "C:\Users\admin\Downloads\rookie_2.30.0_portable (1)" --inplace --http-url https://theapp.vrrookie.xyz/ --tpslimit 1.0 --tpslimit-burst 3 | C:\Users\admin\Downloads\rookie_2.30.0_portable (1)\rclone\rclone.exe | AndroidSideloader v2.30.0.exe | ||||||||||||
User: admin Company: https://rclone.org Integrity Level: MEDIUM Description: Rclone Exit code: 0 Version: 1.67.0 Modules
| |||||||||||||||
| 1176 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\rookie_2.30.0_portable (1).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1884 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 7z.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2184 | "C:\Users\admin\Downloads\rookie_2.30.0_portable (1)\AndroidSideloader v2.30.0.exe" | C:\Users\admin\Downloads\rookie_2.30.0_portable (1)\AndroidSideloader v2.30.0.exe | explorer.exe | ||||||||||||
User: admin Company: Rookie.AndroidSideloader Integrity Level: MEDIUM Description: AndroidSideloader Version: 2.0.0.0 Modules
| |||||||||||||||
| 2280 | "7z.exe" x "C:\Users\admin\Downloads\rookie_2.30.0_portable (1)\meta.7z" -y -o"C:\Users\admin\Downloads\rookie_2.30.0_portable (1)\meta" -p"gL59VfgPxoHR" -bsp1 | C:\Users\admin\Downloads\rookie_2.30.0_portable (1)\7z.exe | — | AndroidSideloader v2.30.0.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Standalone Console Version: 23.01 Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\Downloads\rookie_2.30.0_portable (1)\rclone\rclone.exe" listremotes --config vrp.download.config --inplace | C:\Users\admin\Downloads\rookie_2.30.0_portable (1)\rclone\rclone.exe | — | AndroidSideloader v2.30.0.exe | |||||||||||
User: admin Company: https://rclone.org Integrity Level: MEDIUM Description: Rclone Exit code: 0 Version: 1.67.0 Modules
| |||||||||||||||
| 2708 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | adb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2816 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rclone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2980 | "7z.exe" x "C:\Users\admin\Downloads\rookie_2.30.0_portable (1)\dependencies.7z" -y -o"C:\RSL\platform-tools" -bsp1 | C:\Users\admin\Downloads\rookie_2.30.0_portable (1)\7z.exe | AndroidSideloader v2.30.0.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Standalone Console Exit code: 0 Version: 23.01 Modules
| |||||||||||||||
| 3648 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 345
Read events
13 299
Write events
33
Delete events
13
Modification events
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\rookie_2.30.0_portable (1).zip | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
Executable files
17
Suspicious files
2
Text files
1 076
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2184 | AndroidSideloader v2.30.0.exe | C:\Users\admin\Downloads\rookie_2.30.0_portable (1)\dependencies.7z | — | |
MD5:— | SHA256:— | |||
| 2980 | 7z.exe | C:\RSL\platform-tools\NOTICE.txt | text | |
MD5:E7E8B9497810834CAB9522FE5DD80560 | SHA256:D25FAFFB58D73FEF75D10B7D9B49D8D9872CBB33018F23232D04E8C3EA9DC4DB | |||
| 2184 | AndroidSideloader v2.30.0.exe | C:\Users\admin\Downloads\rookie_2.30.0_portable (1)\Sideloader Launcher.exe | executable | |
MD5:A53A5E70248EB3DA58DEFA74B0554704 | SHA256:98BC8CF1C6A59EF70D6431E1E92887984E5B21C8FBC85B4AD23CCC70589C4B1F | |||
| 1176 | WinRAR.exe | C:\Users\admin\Downloads\rookie_2.30.0_portable (1)\Rookie Offline.cmd | text | |
MD5:83B85F3A19C77666117DB1DFBBFD782B | SHA256:5286FC09CBBC098A5DA63096676B180BD7FD28DCD96A79F41F4D92784CC262D1 | |||
| 1176 | WinRAR.exe | C:\Users\admin\Downloads\rookie_2.30.0_portable (1)\CleanupInstall.cmd | text | |
MD5:E8A3ECEB3B852D4D5D583C22DDD15D2A | SHA256:13BACF3E18984C9803295C5F60B0DA92703773B2D85C54BFCB0D8AF7301C8EE3 | |||
| 2184 | AndroidSideloader v2.30.0.exe | C:\Users\admin\AppData\Local\Rookie.AndroidSideloader\AndroidSideloader_v2.30.0_Url_uzevk2jriwbqrrpxaqyy33cghazrtn4o\2.0.0.0\qhqrqpjd.newcfg | xml | |
MD5:39D8B2F7D8BE3F7B89DC213A755F6872 | SHA256:6D6CAA071F93408EC35A49DCA4EE4CCD47EF2E56A2CBDE8B82605EF292A28B39 | |||
| 2184 | AndroidSideloader v2.30.0.exe | C:\Users\admin\AppData\Local\Rookie.AndroidSideloader\AndroidSideloader_v2.30.0_Url_uzevk2jriwbqrrpxaqyy33cghazrtn4o\2.0.0.0\lqcwpbsx.newcfg | xml | |
MD5:6DC22626C68E39D1F7A92BC247D064FA | SHA256:5B1CFB327E8E4F605CDB650526AB442CC846CE97CFDC51D1DA23DFECB3ABDF60 | |||
| 2184 | AndroidSideloader v2.30.0.exe | C:\Users\admin\AppData\Local\Rookie.AndroidSideloader\AndroidSideloader_v2.30.0_Url_uzevk2jriwbqrrpxaqyy33cghazrtn4o\2.0.0.0\vpdzsdwa.newcfg | xml | |
MD5:E1FC15EB6A3CA794980C504929886A8F | SHA256:B5C1C7D31495651CB4AA92D249E25697A719588B1A724068BA02697B62927CB3 | |||
| 2184 | AndroidSideloader v2.30.0.exe | C:\Users\admin\Downloads\rookie_2.30.0_portable (1)\7z.exe | executable | |
MD5:1A7EAA1DAB7867E15D7800AE0B5AF5E3 | SHA256:356BEA8B6E9EB84DFA0DD8674E7C03428C641A47789DF605C5BEA0730DE4AED2 | |||
| 2980 | 7z.exe | C:\RSL\platform-tools\source.properties | text | |
MD5:EC771EFEE4A8AA924A7791F814221B02 | SHA256:E43DB3B096E922AFD7607090E626C9D0600AAAAB6E312AE441F44263E72D1328 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
70
DNS requests
25
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4700 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7028 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7028 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6792 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1252 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4360 | SearchApp.exe | 2.16.110.168:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4700 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4700 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
github.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2184 | AndroidSideloader v2.30.0.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |