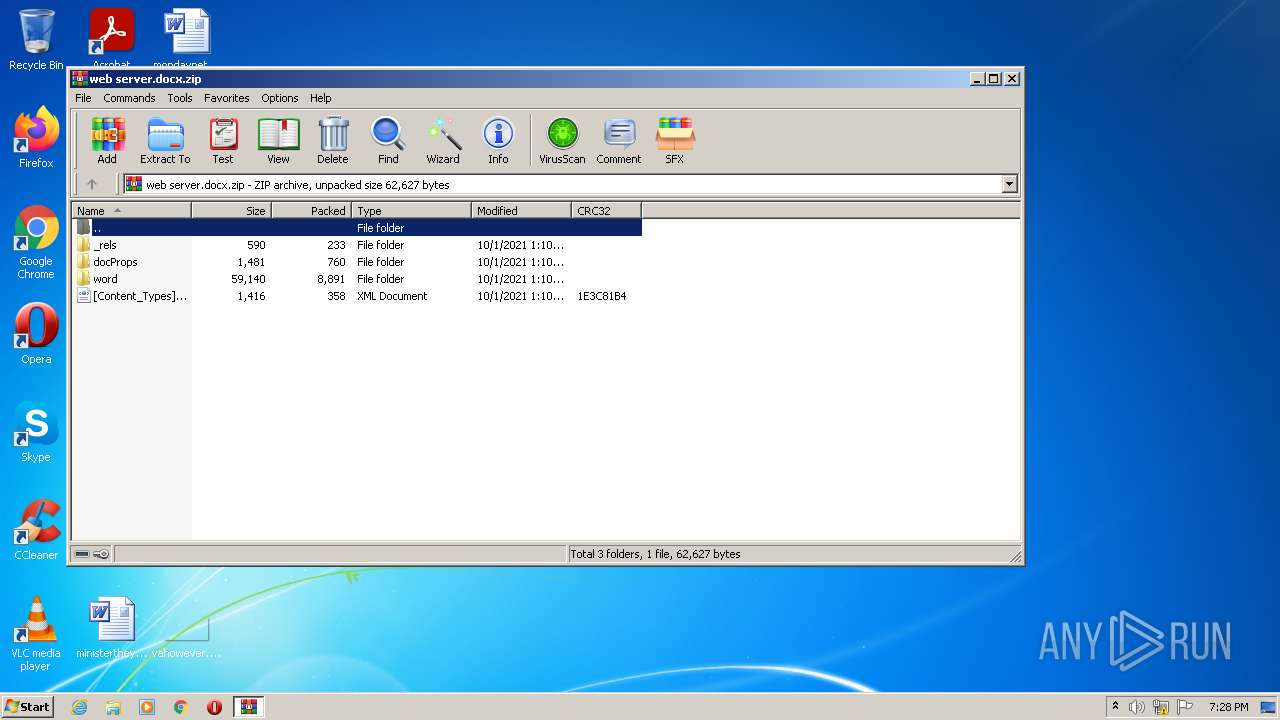
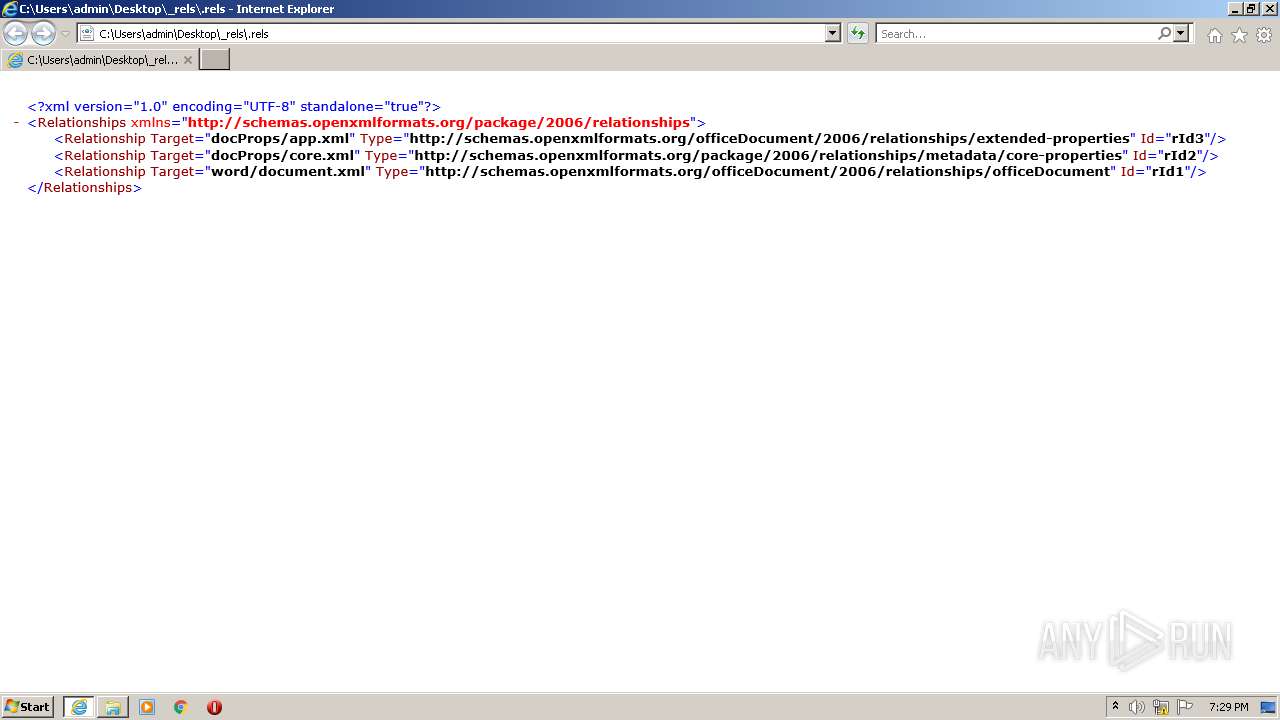
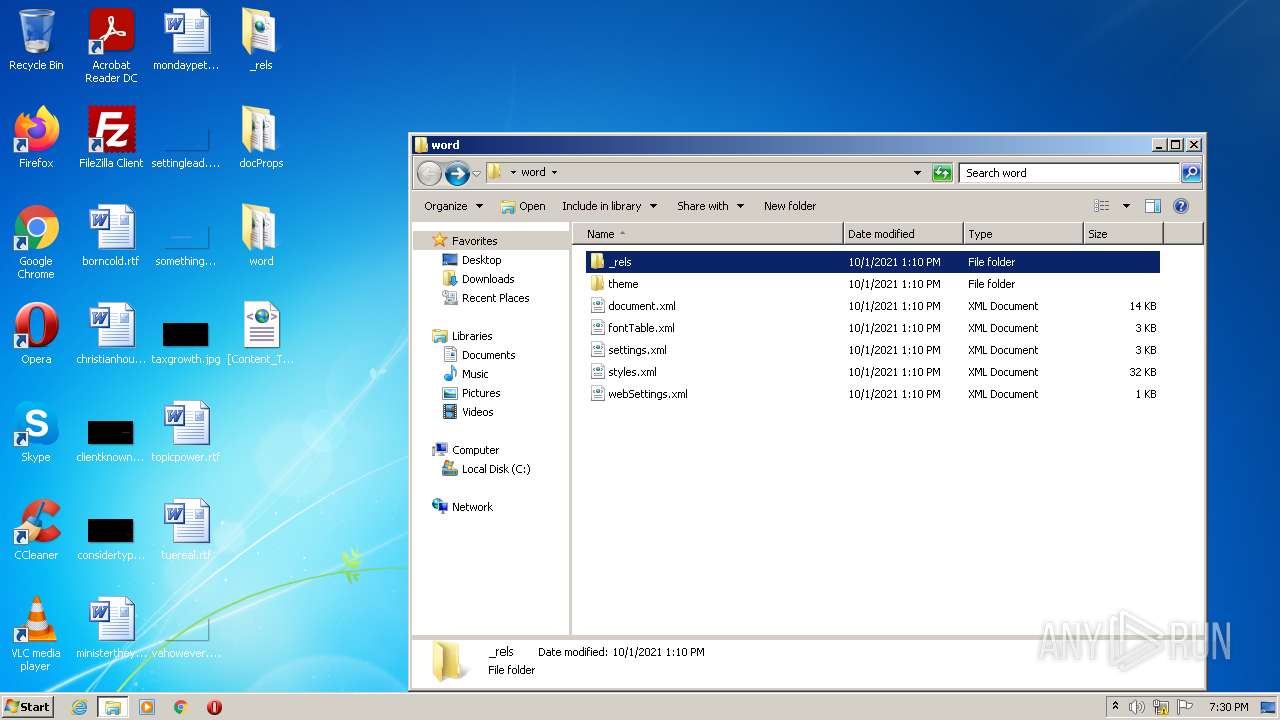
| File name: | web server.docx |
| Full analysis: | https://app.any.run/tasks/1827b29f-e9f2-44df-8060-beea16a3bfca |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2022, 19:28:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | Microsoft OOXML |
| MD5: | 0B831F6459C1FFD39E02385F8095B4C1 |
| SHA1: | DF8E387F3DE994E824901CD4C61CB143C7009706 |
| SHA256: | 8098212842D59D08E99D5D98C32CBBB0A52098B49FABBBAA85991982797A0763 |
| SSDEEP: | 192:R6Sv7mQOJ2wc3rMKkzekcaP18H111M05AgPekjD2h0vcPp0:R6SviQIhzegWH111/eahvCp0 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 2180)
Checks supported languages
- WinRAR.exe (PID: 2180)
Starts Internet Explorer
- MSOXMLED.EXE (PID: 3492)
- MSOXMLED.EXE (PID: 3400)
- MSOXMLED.EXE (PID: 2724)
- MSOXMLED.EXE (PID: 3052)
- MSOXMLED.EXE (PID: 3312)
- MSOXMLED.EXE (PID: 2436)
- MSOXMLED.EXE (PID: 2208)
- MSOXMLED.EXE (PID: 3868)
- MSOXMLED.EXE (PID: 120)
- MSOXMLED.EXE (PID: 556)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2176)
- iexplore.exe (PID: 2496)
- iexplore.exe (PID: 1448)
- iexplore.exe (PID: 3416)
- iexplore.exe (PID: 3608)
- iexplore.exe (PID: 2740)
- iexplore.exe (PID: 2768)
- iexplore.exe (PID: 2416)
- iexplore.exe (PID: 3620)
- iexplore.exe (PID: 3276)
- iexplore.exe (PID: 2596)
- iexplore.exe (PID: 3132)
- iexplore.exe (PID: 3788)
- iexplore.exe (PID: 2300)
- iexplore.exe (PID: 3104)
- iexplore.exe (PID: 1012)
- iexplore.exe (PID: 1444)
- iexplore.exe (PID: 3052)
- iexplore.exe (PID: 2404)
- iexplore.exe (PID: 3304)
INFO
Checks supported languages
- MSOXMLED.EXE (PID: 3492)
- iexplore.exe (PID: 2176)
- iexplore.exe (PID: 2496)
- iexplore.exe (PID: 4092)
- MSOXMLED.EXE (PID: 3400)
- iexplore.exe (PID: 3416)
- iexplore.exe (PID: 1448)
- iexplore.exe (PID: 2620)
- iexplore.exe (PID: 2240)
- iexplore.exe (PID: 3608)
- MSOXMLED.EXE (PID: 2436)
- iexplore.exe (PID: 2740)
- MSOXMLED.EXE (PID: 2724)
- iexplore.exe (PID: 3000)
- iexplore.exe (PID: 2768)
- iexplore.exe (PID: 2416)
- MSOXMLED.EXE (PID: 3052)
- iexplore.exe (PID: 3400)
- iexplore.exe (PID: 3620)
- iexplore.exe (PID: 3276)
- MSOXMLED.EXE (PID: 3312)
- iexplore.exe (PID: 304)
- iexplore.exe (PID: 2596)
- iexplore.exe (PID: 3132)
- MSOXMLED.EXE (PID: 2208)
- iexplore.exe (PID: 3520)
- iexplore.exe (PID: 2300)
- iexplore.exe (PID: 3788)
- MSOXMLED.EXE (PID: 3868)
- iexplore.exe (PID: 3820)
- iexplore.exe (PID: 3104)
- iexplore.exe (PID: 1012)
- MSOXMLED.EXE (PID: 120)
- iexplore.exe (PID: 3928)
- iexplore.exe (PID: 2404)
- iexplore.exe (PID: 1444)
- MSOXMLED.EXE (PID: 556)
- iexplore.exe (PID: 692)
- iexplore.exe (PID: 3052)
- iexplore.exe (PID: 3304)
Application launched itself
- iexplore.exe (PID: 4092)
- iexplore.exe (PID: 2620)
- iexplore.exe (PID: 2240)
- iexplore.exe (PID: 3000)
- iexplore.exe (PID: 3400)
- iexplore.exe (PID: 304)
- iexplore.exe (PID: 3520)
- iexplore.exe (PID: 3820)
- iexplore.exe (PID: 3928)
- iexplore.exe (PID: 692)
Reads the computer name
- MSOXMLED.EXE (PID: 3492)
- iexplore.exe (PID: 2176)
- iexplore.exe (PID: 2496)
- iexplore.exe (PID: 4092)
- MSOXMLED.EXE (PID: 3400)
- iexplore.exe (PID: 2620)
- iexplore.exe (PID: 1448)
- iexplore.exe (PID: 3416)
- MSOXMLED.EXE (PID: 2436)
- iexplore.exe (PID: 2240)
- iexplore.exe (PID: 2740)
- iexplore.exe (PID: 3608)
- MSOXMLED.EXE (PID: 2724)
- iexplore.exe (PID: 3000)
- iexplore.exe (PID: 2768)
- iexplore.exe (PID: 2416)
- MSOXMLED.EXE (PID: 3052)
- iexplore.exe (PID: 3400)
- iexplore.exe (PID: 3620)
- iexplore.exe (PID: 3276)
- iexplore.exe (PID: 304)
- MSOXMLED.EXE (PID: 3312)
- MSOXMLED.EXE (PID: 2208)
- iexplore.exe (PID: 3132)
- iexplore.exe (PID: 2596)
- iexplore.exe (PID: 3520)
- iexplore.exe (PID: 2300)
- iexplore.exe (PID: 3788)
- MSOXMLED.EXE (PID: 3868)
- iexplore.exe (PID: 3820)
- MSOXMLED.EXE (PID: 120)
- iexplore.exe (PID: 3928)
- iexplore.exe (PID: 2404)
- iexplore.exe (PID: 3104)
- iexplore.exe (PID: 1012)
- iexplore.exe (PID: 1444)
- MSOXMLED.EXE (PID: 556)
- iexplore.exe (PID: 3052)
- iexplore.exe (PID: 3304)
- iexplore.exe (PID: 692)
Reads internet explorer settings
- iexplore.exe (PID: 2496)
- iexplore.exe (PID: 2176)
- iexplore.exe (PID: 1448)
- iexplore.exe (PID: 3416)
- iexplore.exe (PID: 2740)
- iexplore.exe (PID: 3608)
- iexplore.exe (PID: 2416)
- iexplore.exe (PID: 2768)
- iexplore.exe (PID: 3620)
- iexplore.exe (PID: 3276)
- iexplore.exe (PID: 3132)
- iexplore.exe (PID: 2596)
- iexplore.exe (PID: 2300)
- iexplore.exe (PID: 3788)
- iexplore.exe (PID: 1012)
- iexplore.exe (PID: 3104)
- iexplore.exe (PID: 1444)
- iexplore.exe (PID: 2404)
- iexplore.exe (PID: 3304)
- iexplore.exe (PID: 3052)
Reads settings of System Certificates
- iexplore.exe (PID: 4092)
- iexplore.exe (PID: 2620)
- iexplore.exe (PID: 2240)
Manual execution by user
- MSOXMLED.EXE (PID: 3492)
- MSOXMLED.EXE (PID: 3400)
- MSOXMLED.EXE (PID: 2436)
- MSOXMLED.EXE (PID: 2724)
- MSOXMLED.EXE (PID: 3052)
- MSOXMLED.EXE (PID: 3312)
- MSOXMLED.EXE (PID: 2208)
- MSOXMLED.EXE (PID: 3868)
- MSOXMLED.EXE (PID: 120)
- MSOXMLED.EXE (PID: 556)
Reads the date of Windows installation
- iexplore.exe (PID: 4092)
- iexplore.exe (PID: 2620)
- iexplore.exe (PID: 2240)
- iexplore.exe (PID: 3000)
- iexplore.exe (PID: 3400)
- iexplore.exe (PID: 304)
- iexplore.exe (PID: 3520)
- iexplore.exe (PID: 3820)
- iexplore.exe (PID: 3928)
- iexplore.exe (PID: 692)
Changes internet zones settings
- iexplore.exe (PID: 4092)
- iexplore.exe (PID: 2620)
- iexplore.exe (PID: 2240)
- iexplore.exe (PID: 3000)
- iexplore.exe (PID: 3400)
- iexplore.exe (PID: 304)
- iexplore.exe (PID: 3520)
- iexplore.exe (PID: 3928)
- iexplore.exe (PID: 3820)
- iexplore.exe (PID: 692)
Checks Windows Trust Settings
- iexplore.exe (PID: 4092)
- iexplore.exe (PID: 2240)
- iexplore.exe (PID: 2620)
Creates files in the user directory
- iexplore.exe (PID: 3820)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | Open Packaging Conventions container (81.3) |
|---|---|---|
| .zip | | | ZIP compressed archive (18.6) |
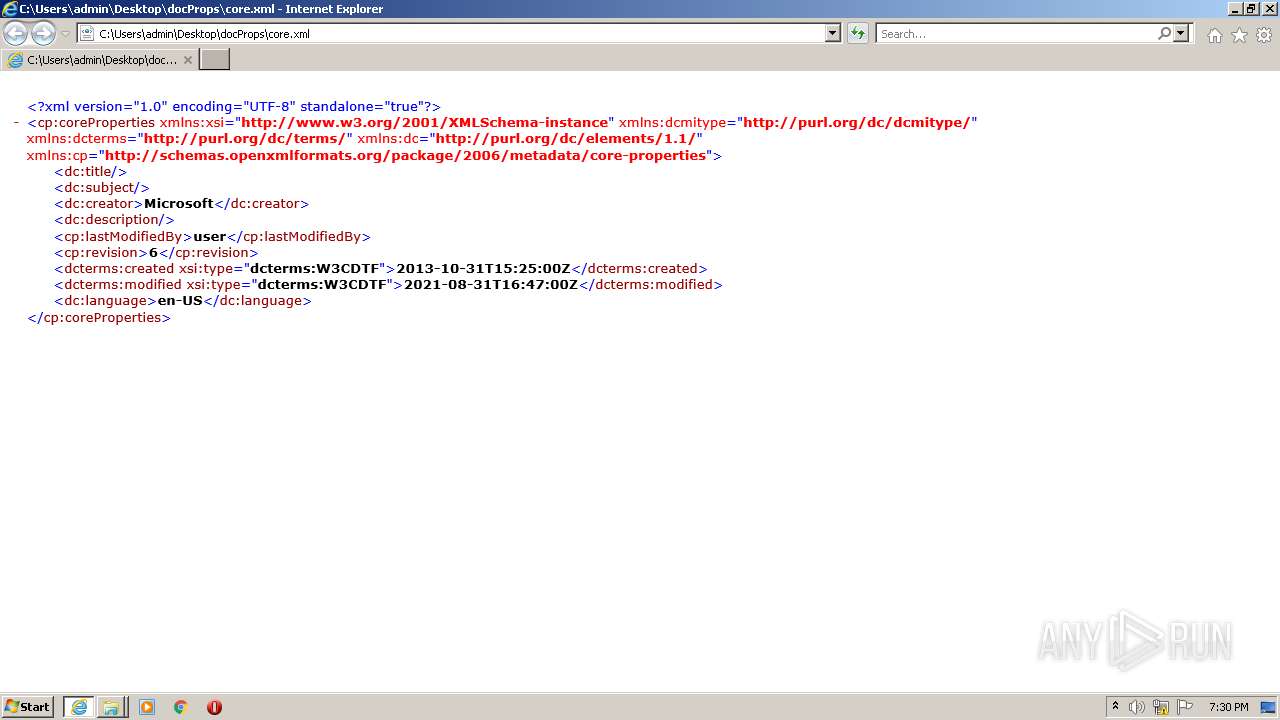
EXIF
XMP
| Language: | en-US |
|---|---|
| Description: | - |
| Creator: | Microsoft |
| Subject: | - |
| Title: | - |
XML
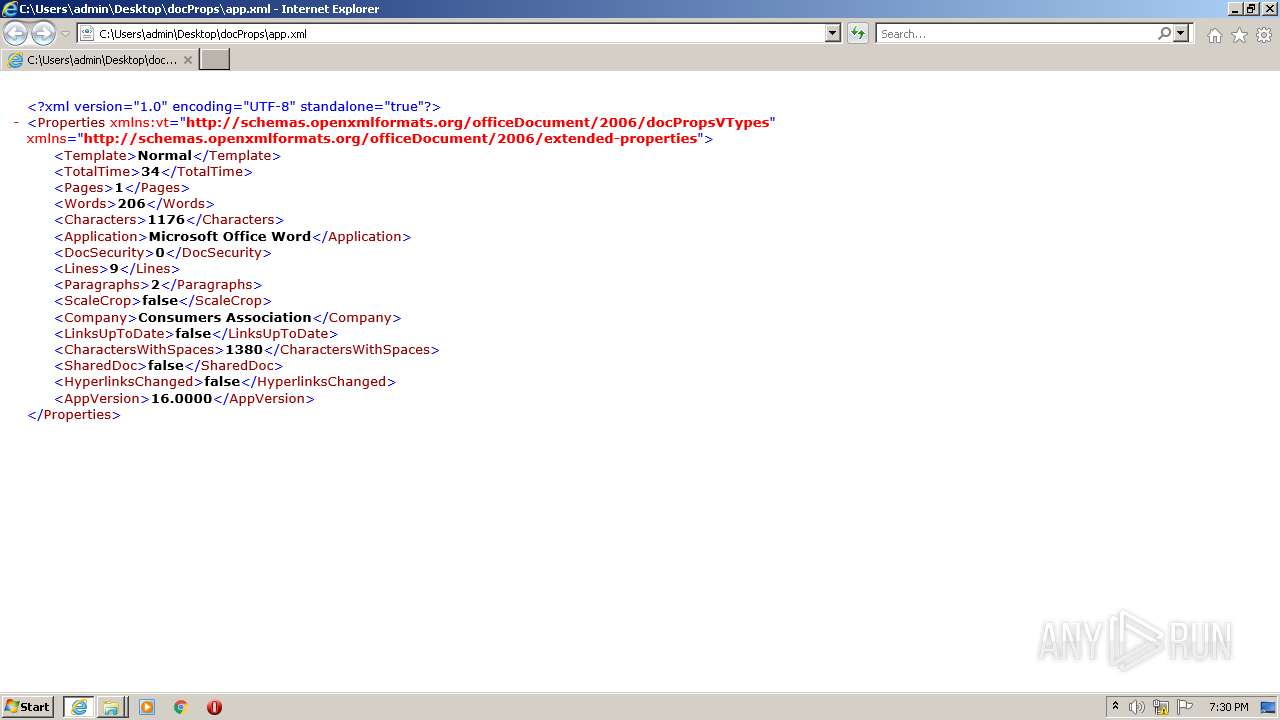
| ModifyDate: | 2021:08:31 16:47:00Z |
|---|---|
| CreateDate: | 2013:10:31 15:25:00Z |
| RevisionNumber: | 6 |
| LastModifiedBy: | user |
| AppVersion: | 16 |
| HyperlinksChanged: | No |
| SharedDoc: | No |
| CharactersWithSpaces: | 1380 |
| LinksUpToDate: | No |
| Company: | Consumers Association |
| ScaleCrop: | No |
| Paragraphs: | 2 |
| Lines: | 9 |
| DocSecurity: | None |
| Application: | Microsoft Office Word |
| Characters: | 1176 |
| Words: | 206 |
| Pages: | 1 |
| TotalEditTime: | 34 minutes |
| Template: | Normal |
ZIP
| ZipFileName: | [Content_Types].xml |
|---|---|
| ZipUncompressedSize: | 1416 |
| ZipCompressedSize: | 358 |
| ZipCRC: | 0x1e3c81b4 |
| ZipModifyDate: | 2021:10:01 14:10:17 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
84
Monitored processes
41
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Program Files\Common Files\Microsoft Shared\OFFICE14\MSOXMLED.EXE" /verb open "C:\Users\admin\Desktop\word\webSettings.xml" | C:\Program Files\Common Files\Microsoft Shared\OFFICE14\MSOXMLED.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: XML Editor Exit code: 0 Version: 14.0.4750.1000 Modules
| |||||||||||||||
| 304 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | — | MSOXMLED.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 556 | "C:\Program Files\Common Files\Microsoft Shared\OFFICE14\MSOXMLED.EXE" /verb open "C:\Users\admin\Desktop\word\styles.xml" | C:\Program Files\Common Files\Microsoft Shared\OFFICE14\MSOXMLED.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: XML Editor Exit code: 0 Version: 14.0.4750.1000 Modules
| |||||||||||||||
| 692 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | — | MSOXMLED.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1012 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3820 CREDAT:78849 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1444 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3928 CREDAT:78849 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1448 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2620 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2176 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:4092 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2180 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\web server.docx.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
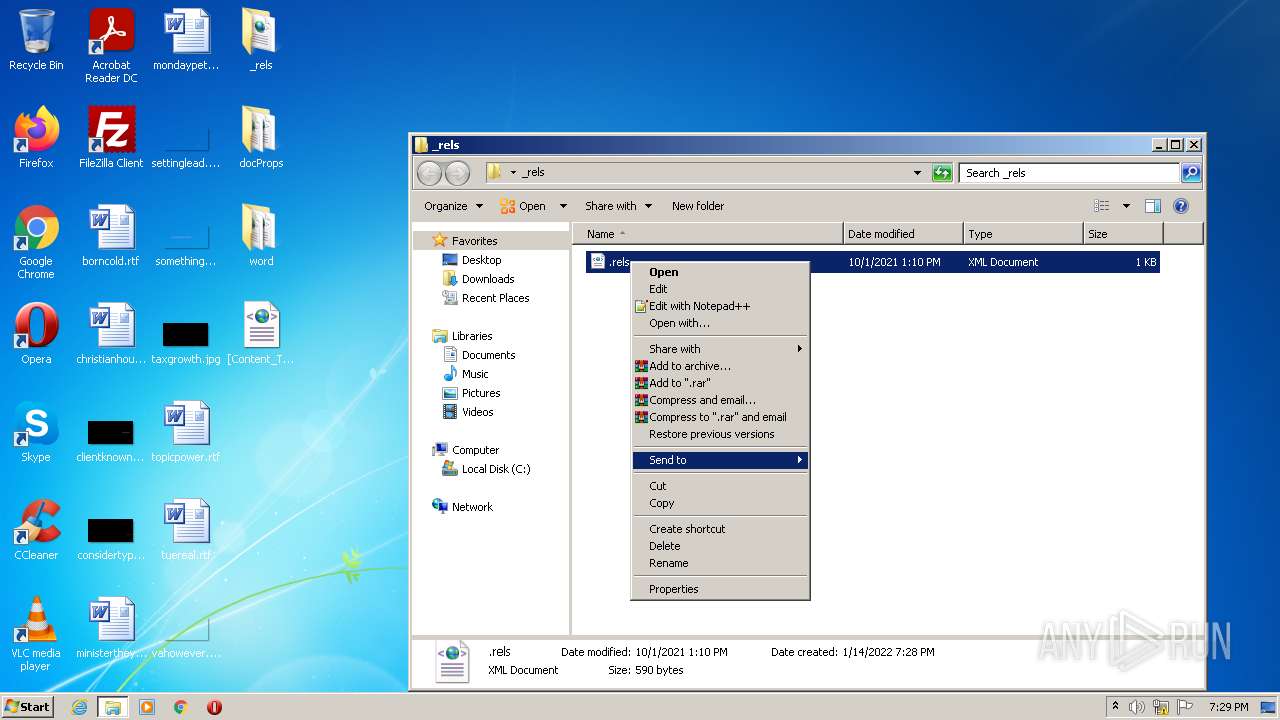
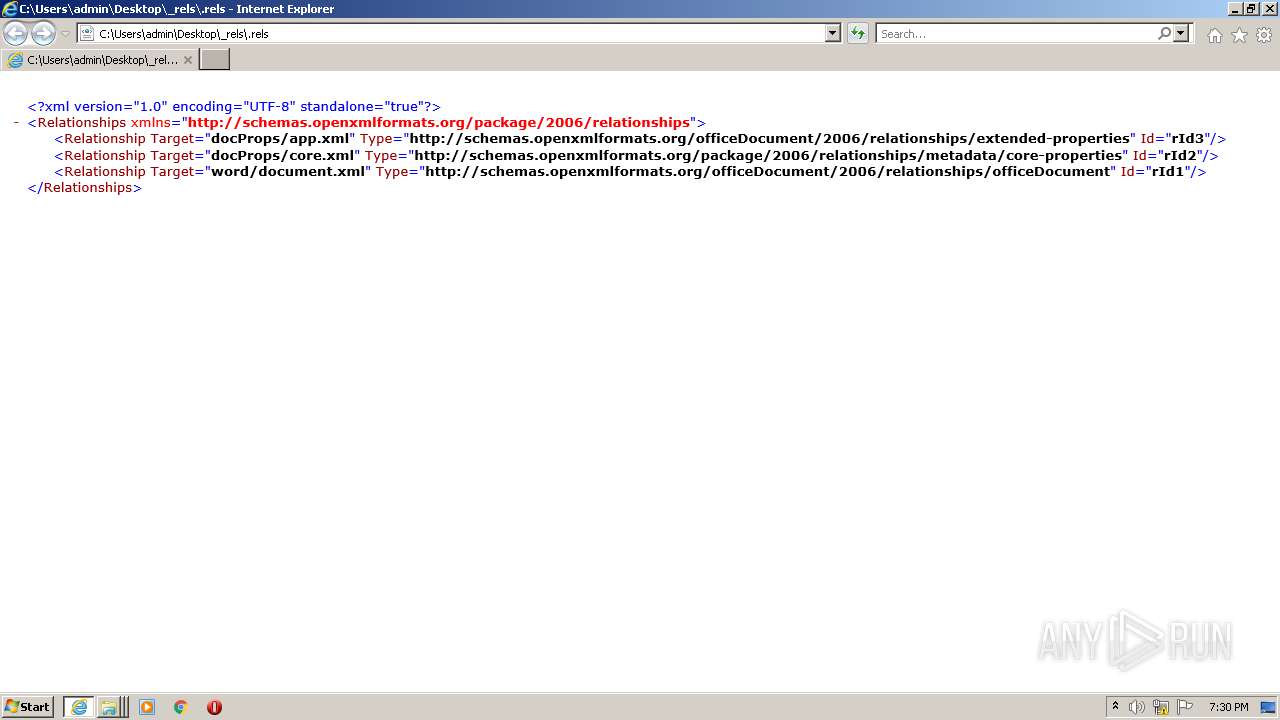
| 2208 | "C:\Program Files\Common Files\Microsoft Shared\OFFICE14\MSOXMLED.EXE" /verb open "C:\Users\admin\Desktop\_rels\.rels" | C:\Program Files\Common Files\Microsoft Shared\OFFICE14\MSOXMLED.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: XML Editor Exit code: 0 Version: 14.0.4750.1000 Modules
| |||||||||||||||
Total events
41 359
Read events
40 255
Write events
1 091
Delete events
13
Modification events
| (PID) Process: | (2180) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2180) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2180) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2180) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2180) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2180) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\web server.docx.zip | |||
| (PID) Process: | (2180) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2180) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2180) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2180) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
73
Text files
15
Unknown types
76
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{3D2B7FC8-7570-11EC-BB61-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
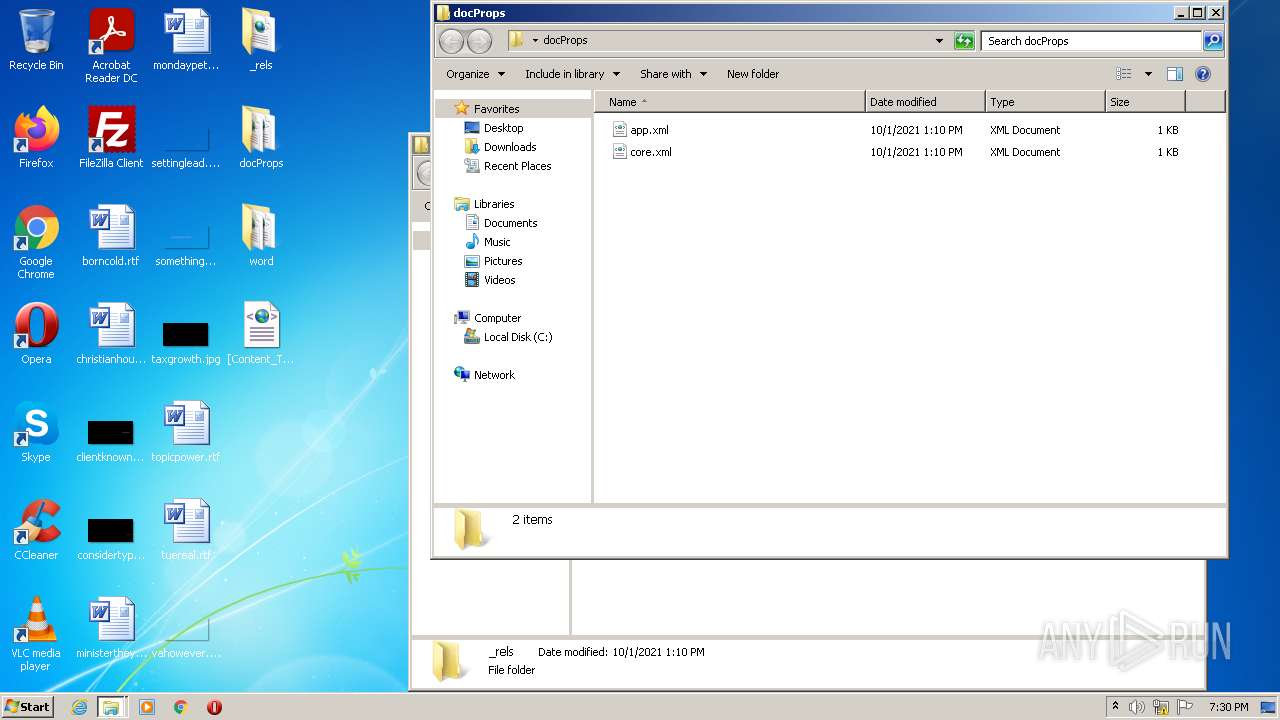
| 2180 | WinRAR.exe | C:\Users\admin\Desktop\docProps\app.xml | xml | |
MD5:D30F4F2D029CC73CADA7BB56400FD5A3 | SHA256:0A19559906AE13C878243ED37D658ABE0BD079778B8623973806A85C6102C2A4 | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF1B0CC8010FEF6053.TMP | gmc | |
MD5:— | SHA256:— | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFDF1806DEB0841426.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2180 | WinRAR.exe | C:\Users\admin\Desktop\[Content_Types].xml | xml | |
MD5:ABEB644A73D4E97D7D35A886F0079C16 | SHA256:26201DA18A2B735BEE149BFB4E3A65AD3716CACECC910373E36E66E0F2237E8C | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 2180 | WinRAR.exe | C:\Users\admin\Desktop\word\styles.xml | xml | |
MD5:DB935F61774828487D71F67313E60BF5 | SHA256:E4740B3C4FB52502D65B3B52C7ADE190D1411DE88088A499F983181AF257382A | |||
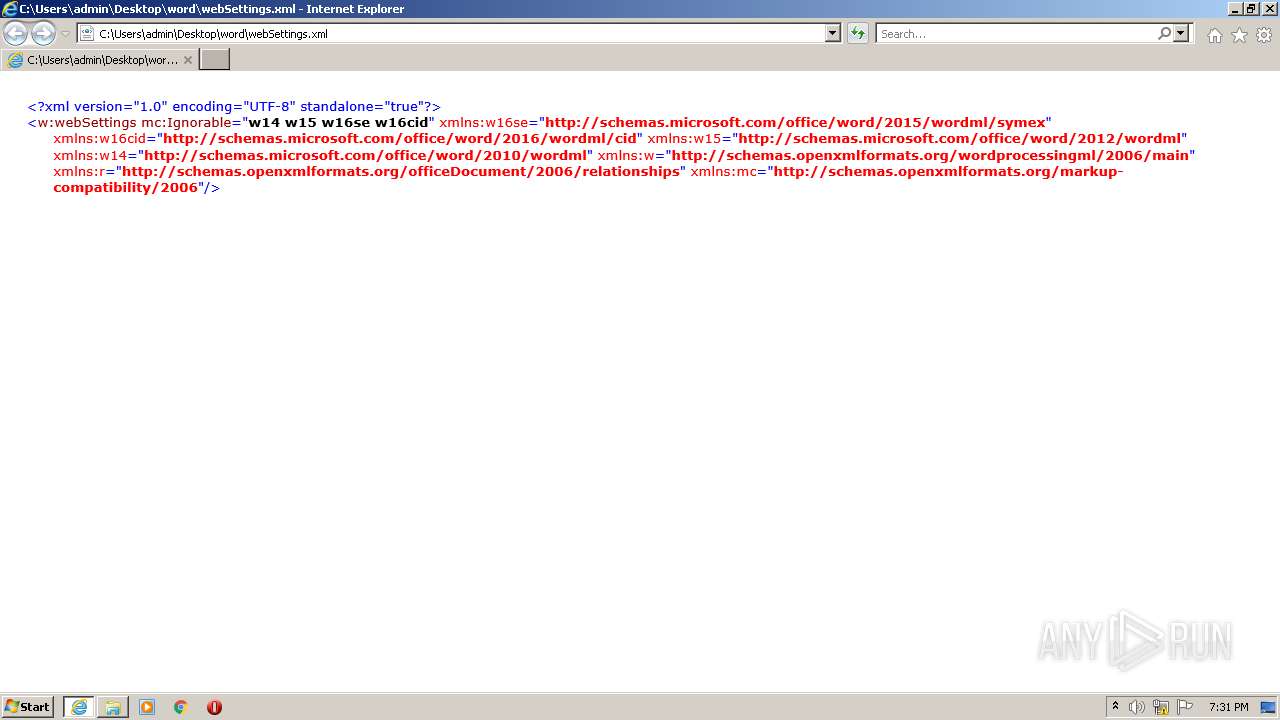
| 2180 | WinRAR.exe | C:\Users\admin\Desktop\word\webSettings.xml | xml | |
MD5:F62A317270FEE7A5B243E3EFD71B1DA4 | SHA256:3D7800A2AC39A10A7FEB274B8C176E6376685E50D46689DBCDA4B2AD66EDDCF8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
11
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4092 | iexplore.exe | GET | 200 | 178.79.242.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d55e9ef32f7fc9c8 | DE | compressed | 4.70 Kb | whitelisted |
2240 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
4092 | iexplore.exe | GET | 200 | 178.79.242.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fdebcea962adf0c3 | DE | compressed | 4.70 Kb | whitelisted |
4092 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4092 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2240 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4092 | iexplore.exe | 131.253.33.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
4092 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4092 | iexplore.exe | 178.79.242.0:80 | ctldl.windowsupdate.com | Limelight Networks, Inc. | DE | whitelisted |
2240 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2620 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |