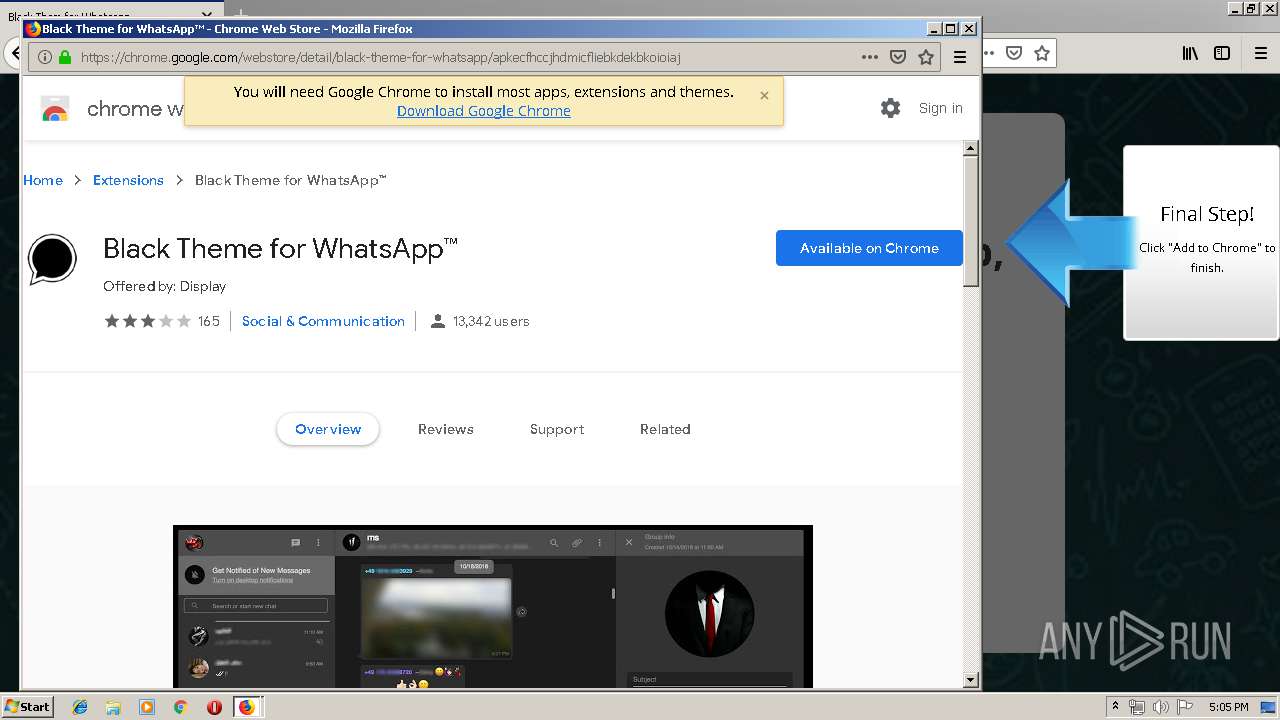
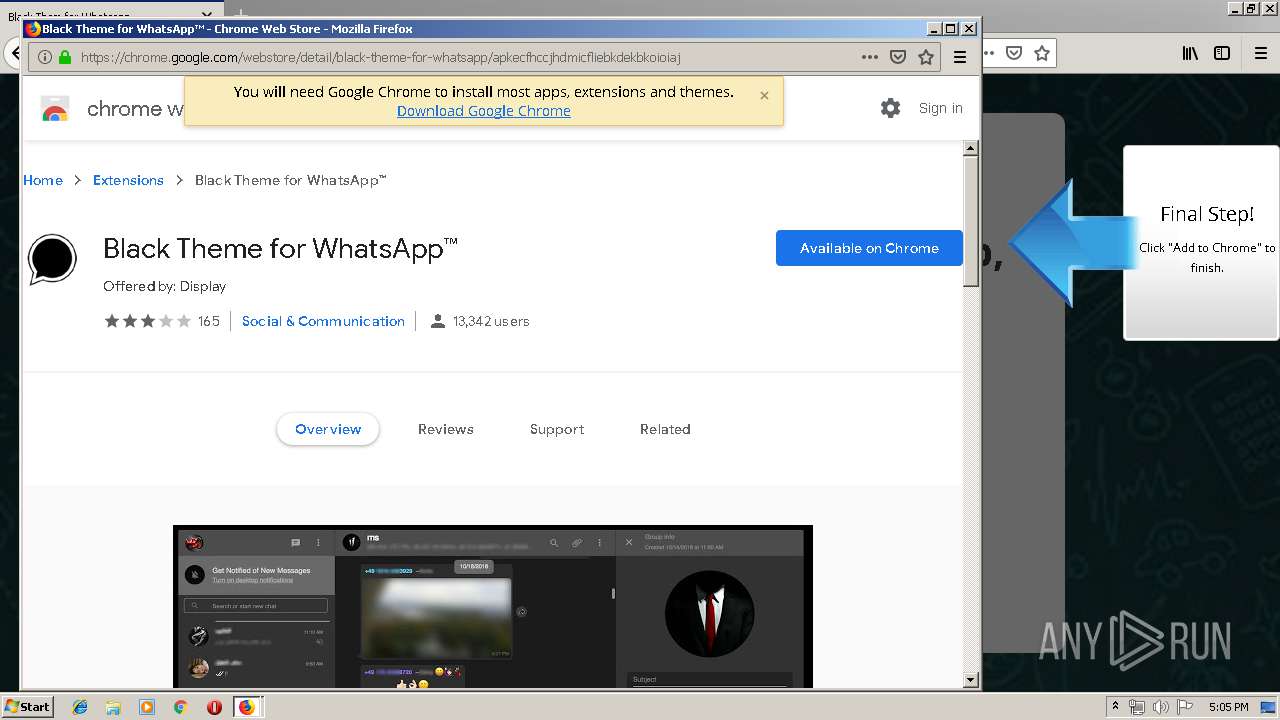
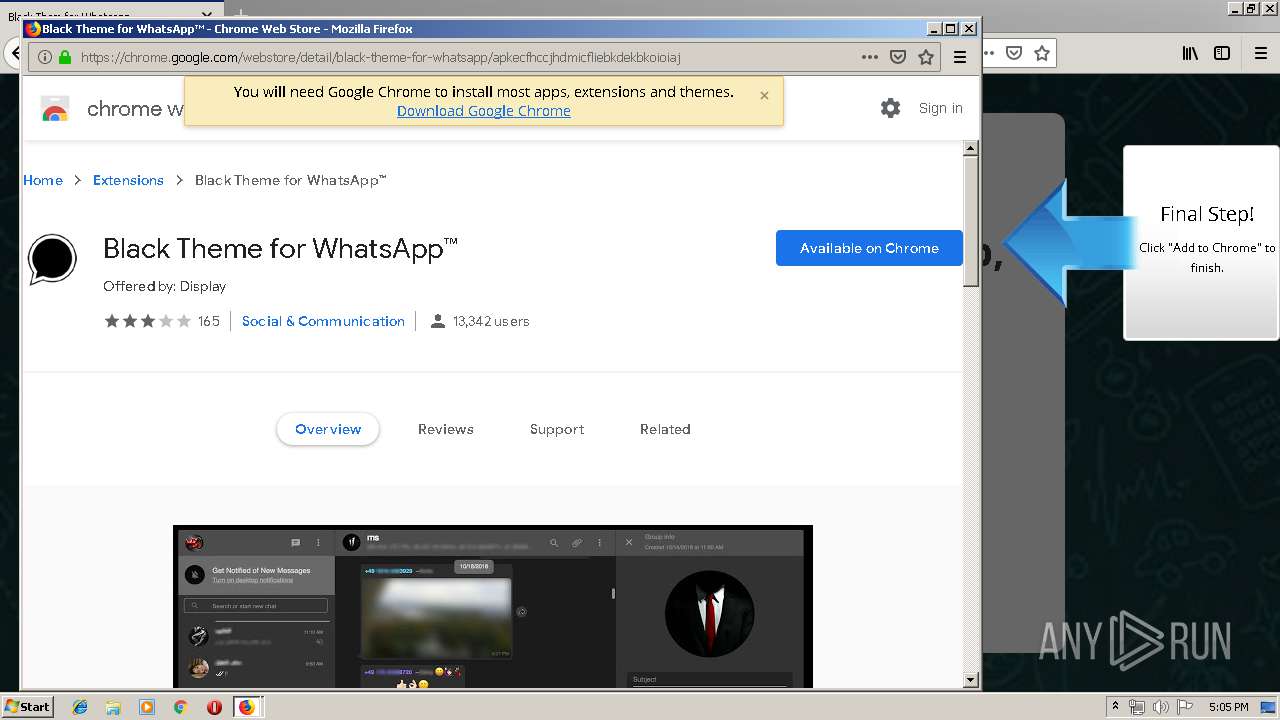
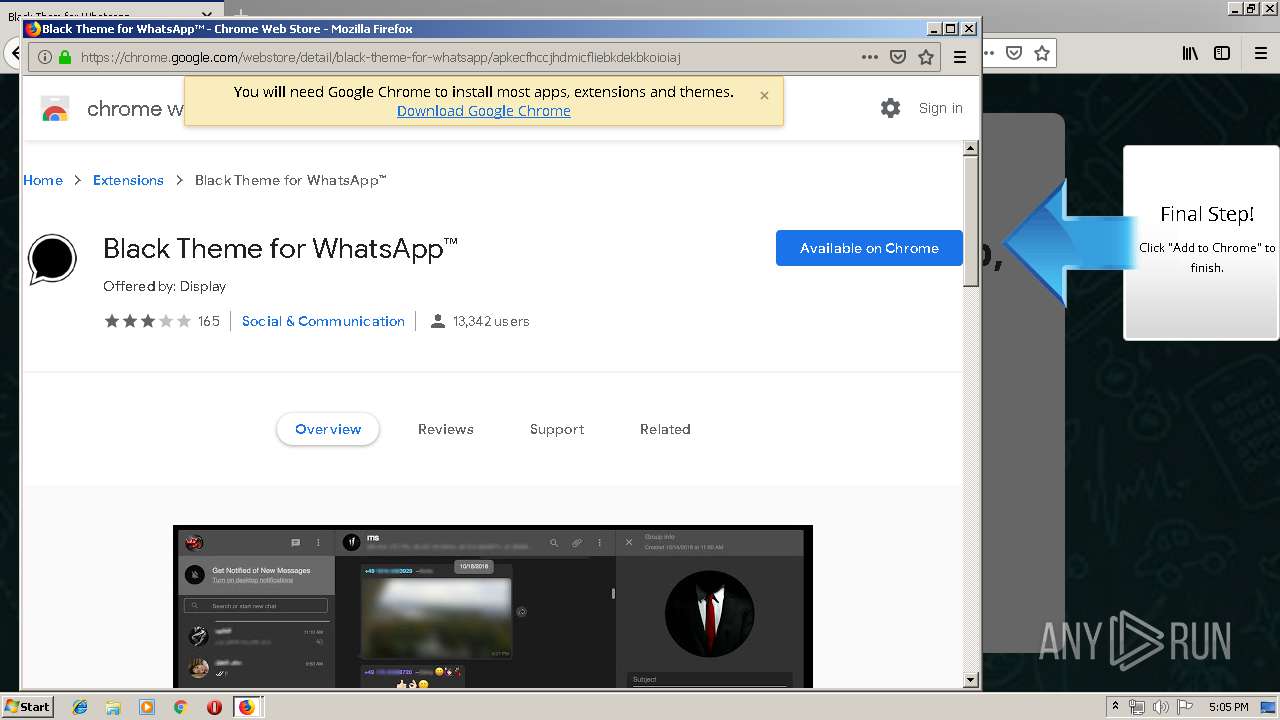
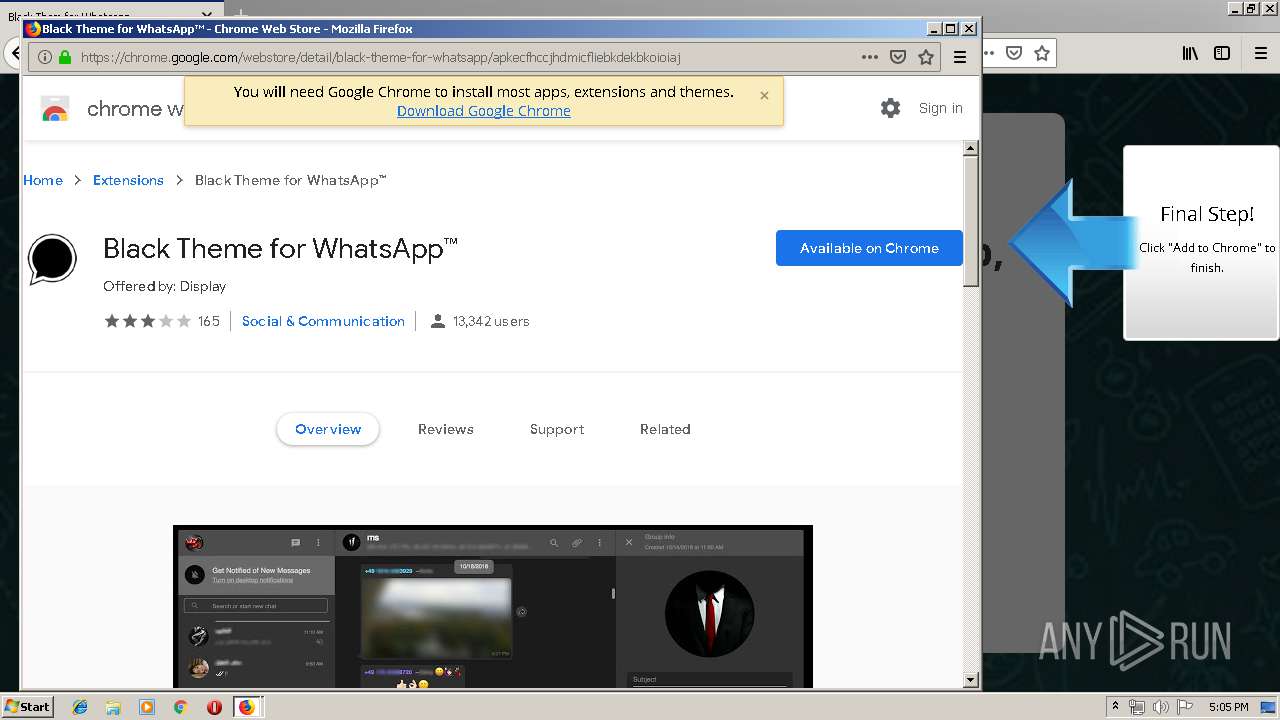
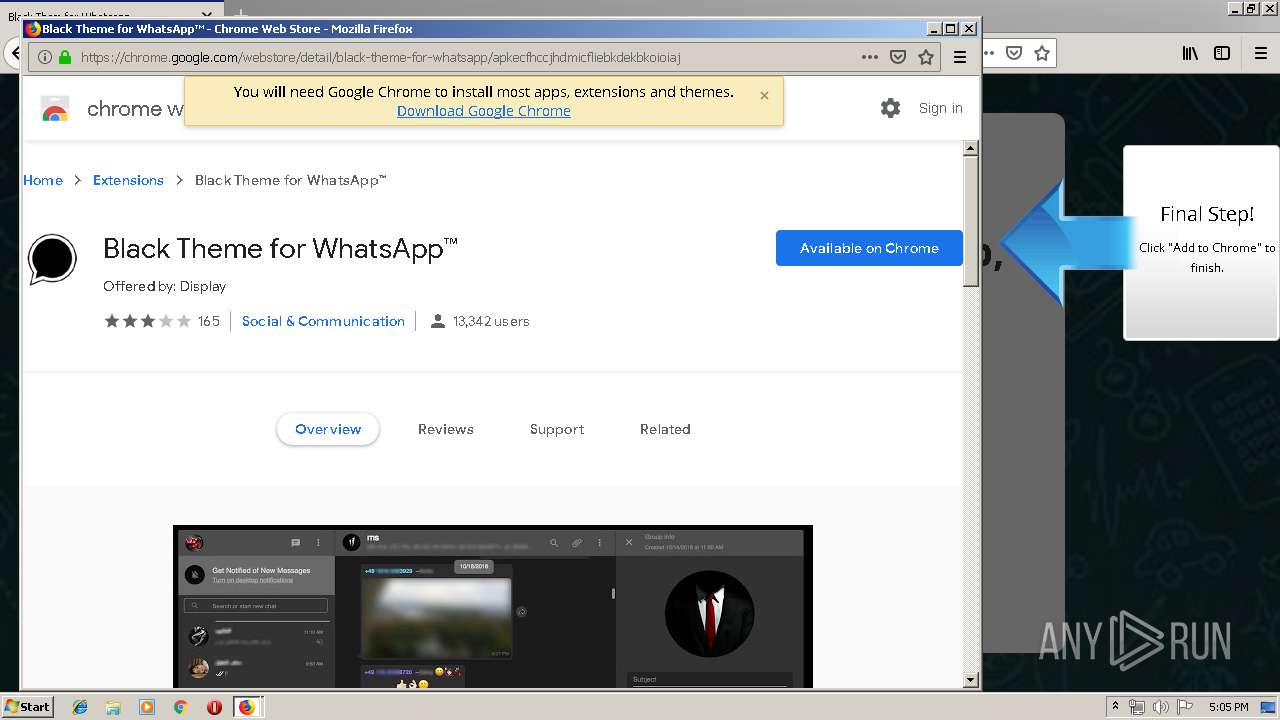
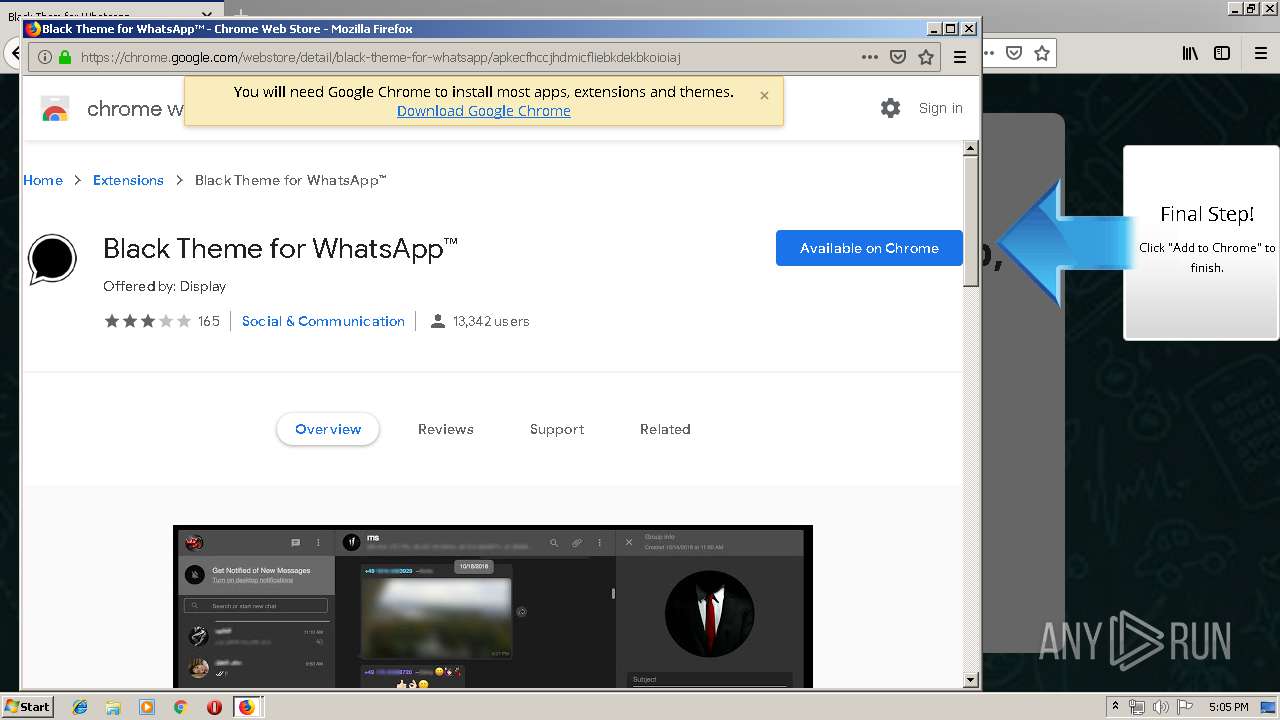
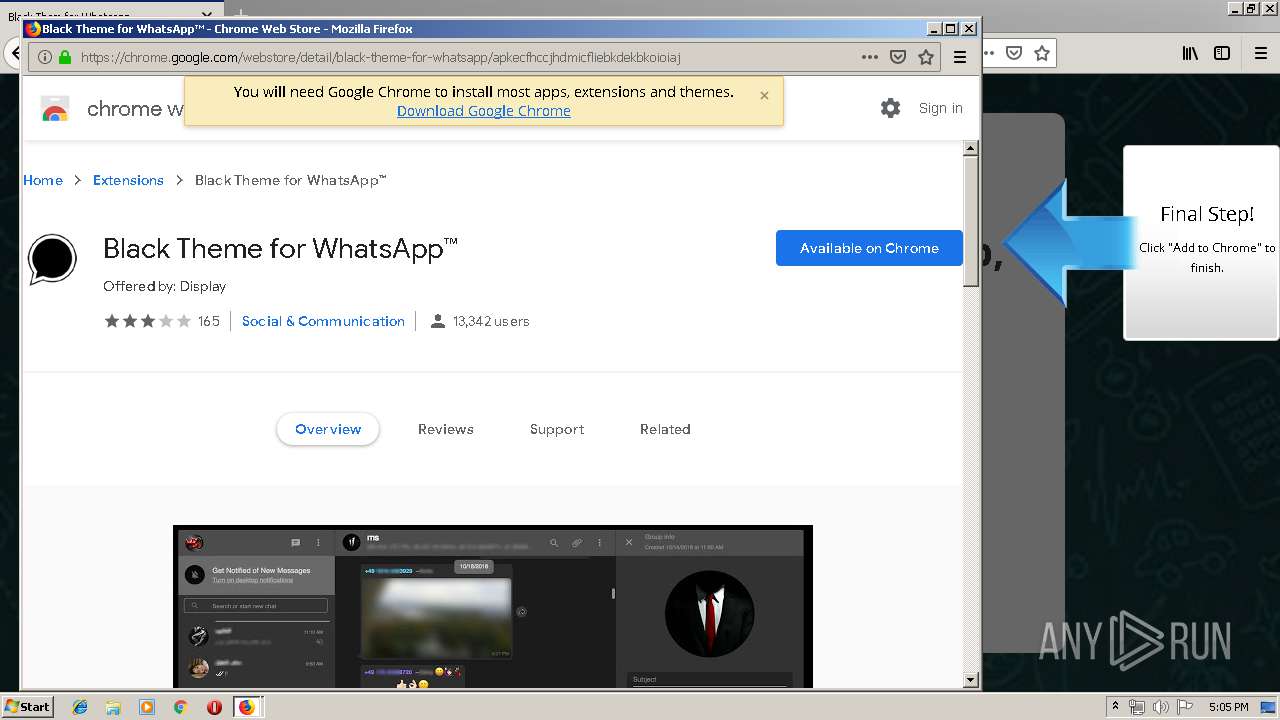
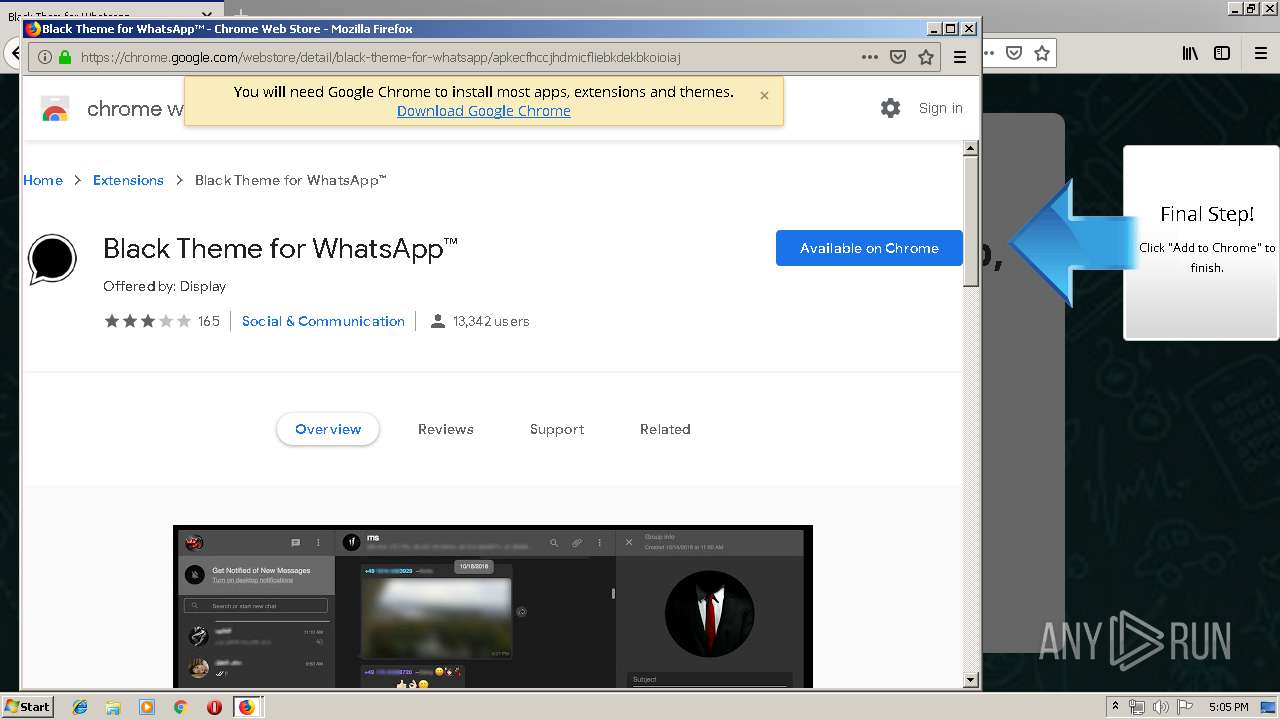
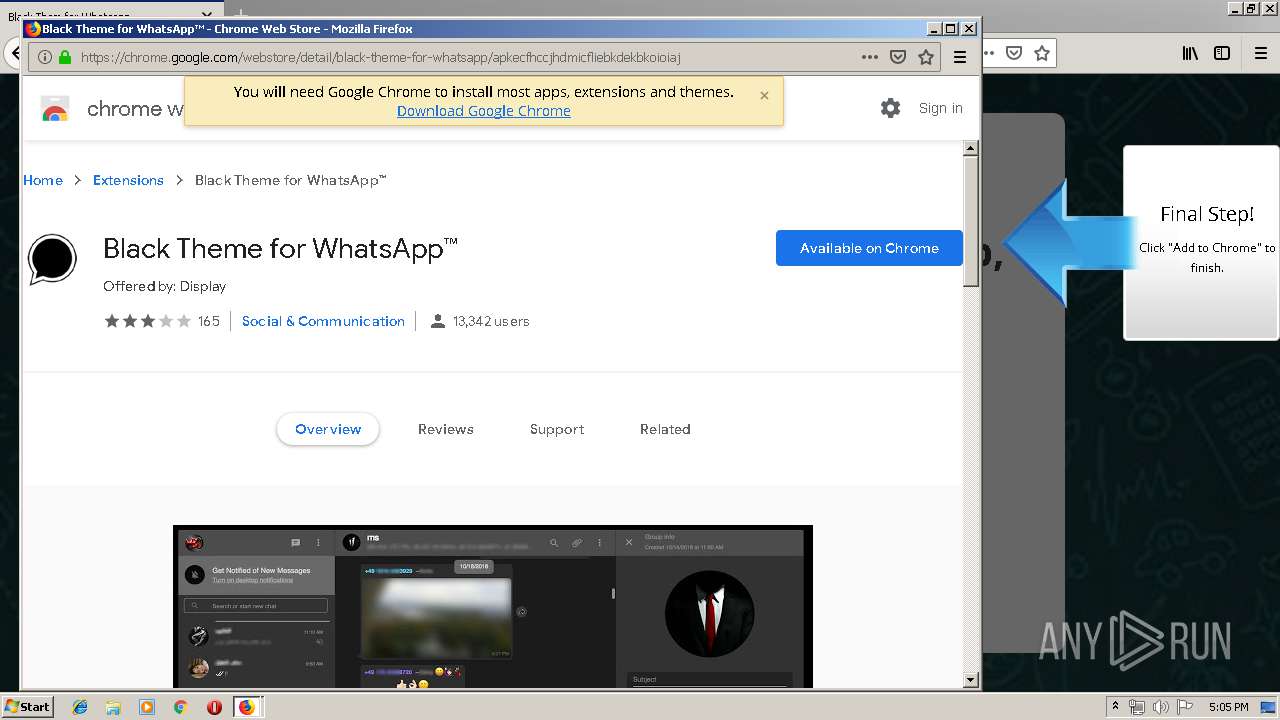
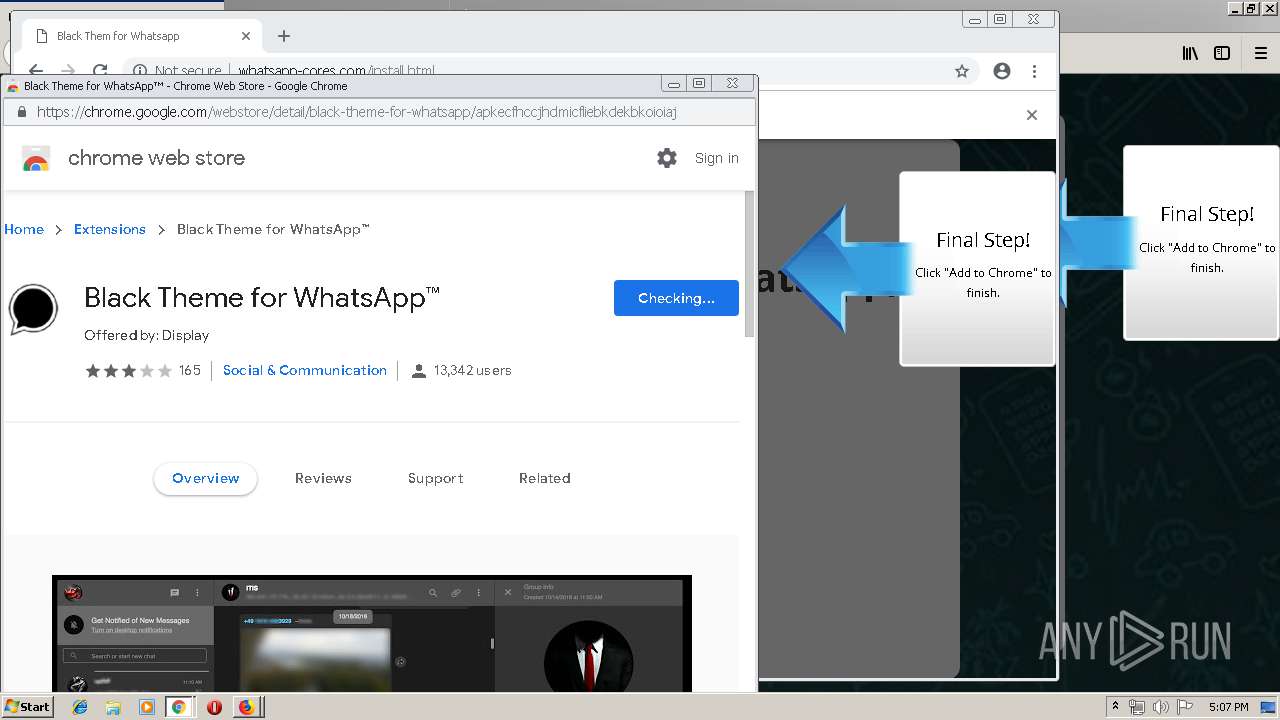
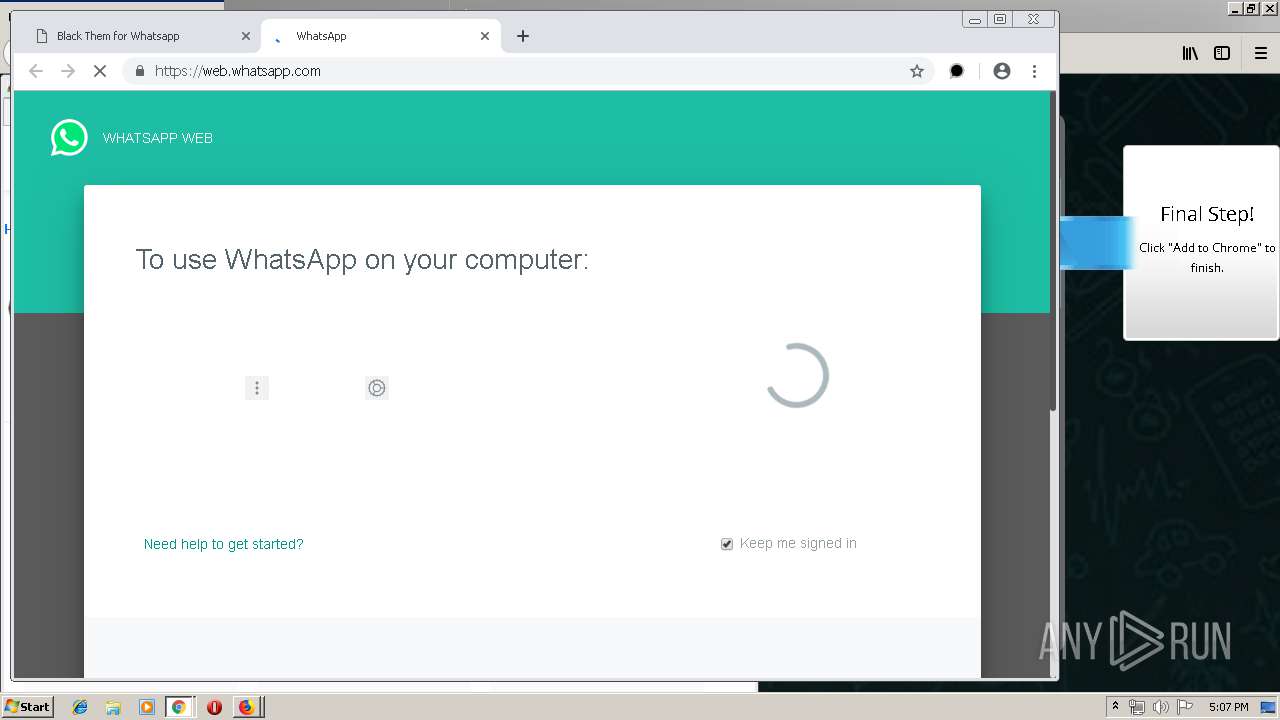
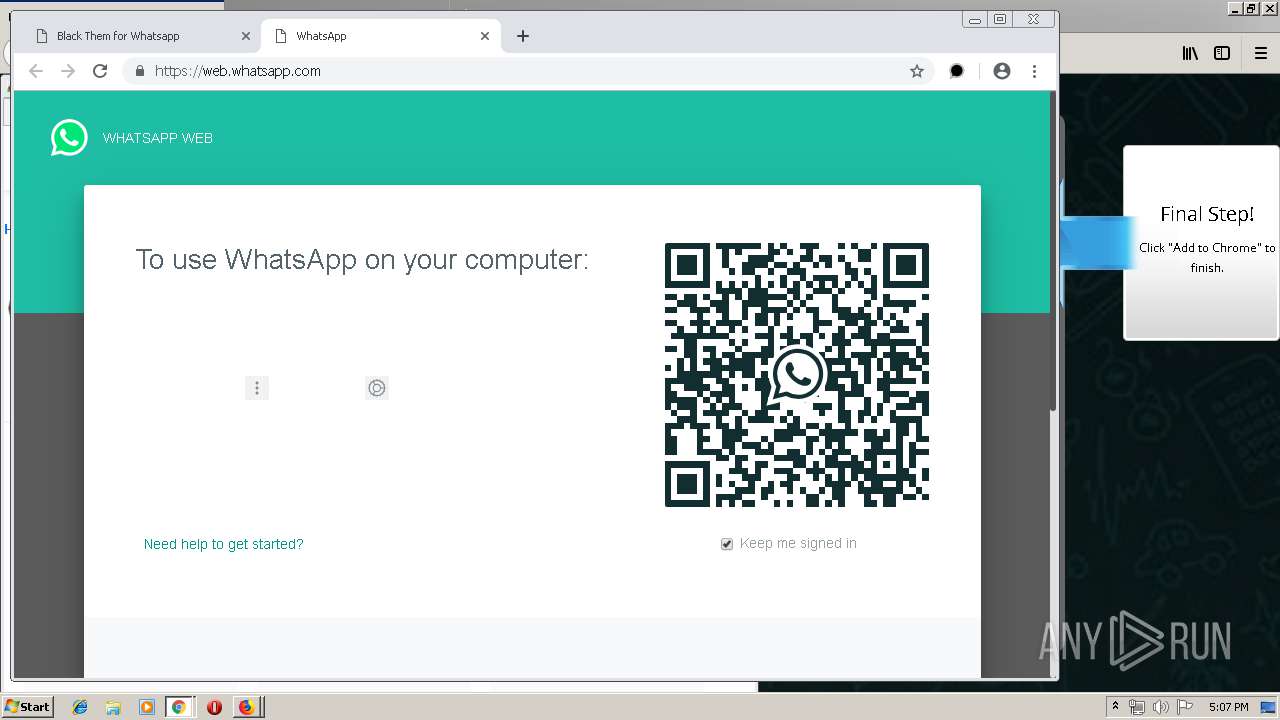
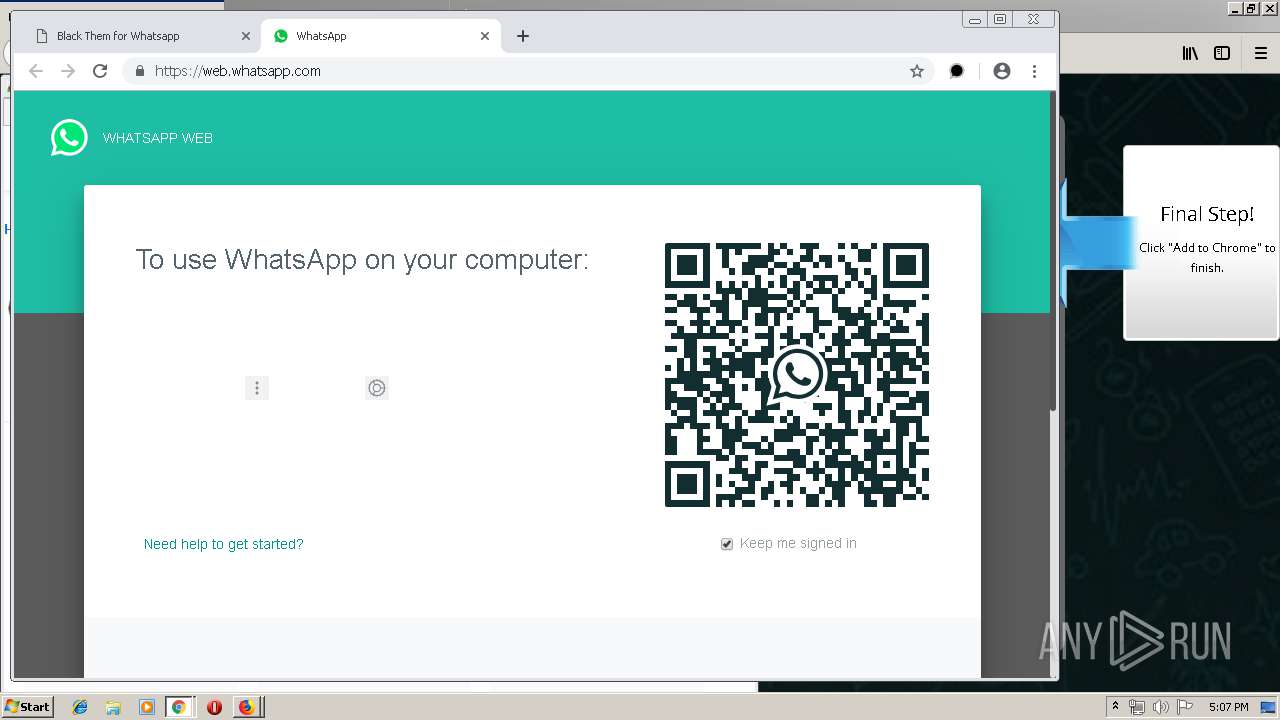
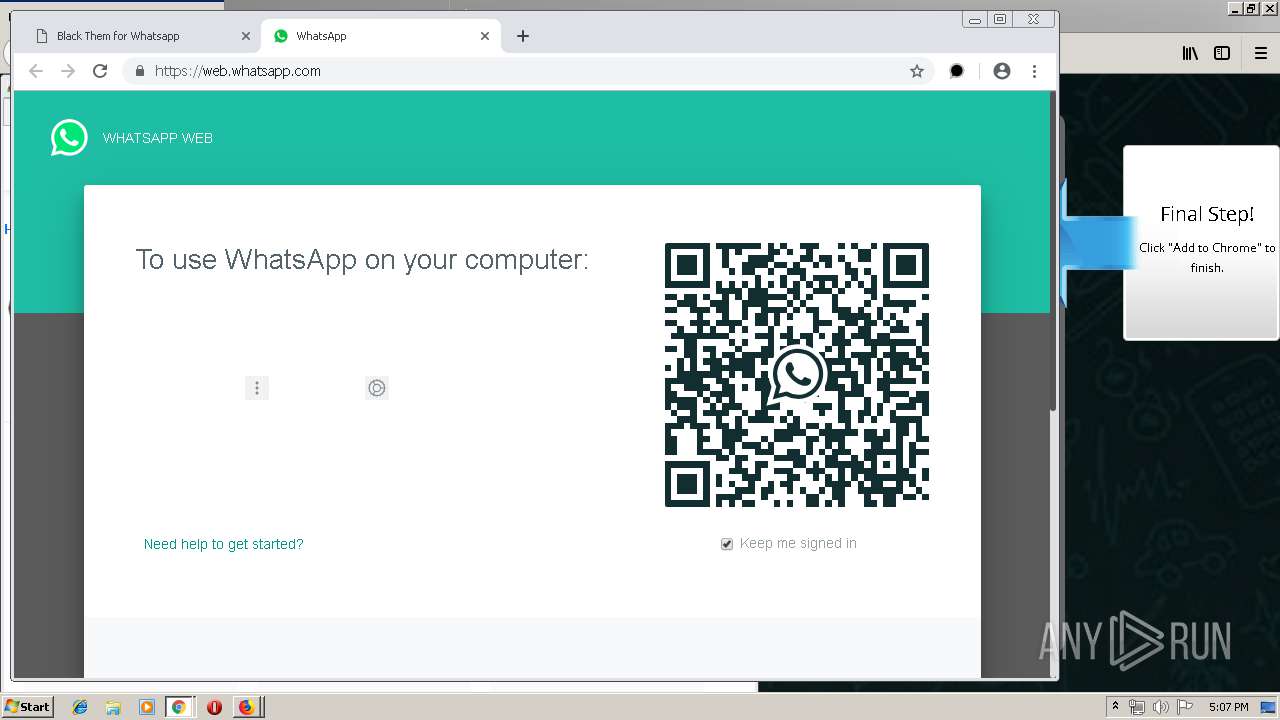
| URL: | http://spotify-br.com/?code=lyVLBxsp |
| Full analysis: | https://app.any.run/tasks/bf017a65-3008-43d2-b4aa-1026c1889f67 |
| Verdict: | Malicious activity |
| Analysis date: | April 14, 2019, 16:04:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | BEE6B7C56C6193F251E6035F8665FC83 |
| SHA1: | 8970EDF09AB7B5FED15B78215A0D92171ED7E8EB |
| SHA256: | 808C47EE6CFC5AC581FA29E9F9D52967453785AB6E9B042D501A6CC7E3D83CF7 |
| SSDEEP: | 3:N1KNVQQOSfWVn:CwQrqn |
MALICIOUS
No malicious indicators.SUSPICIOUS
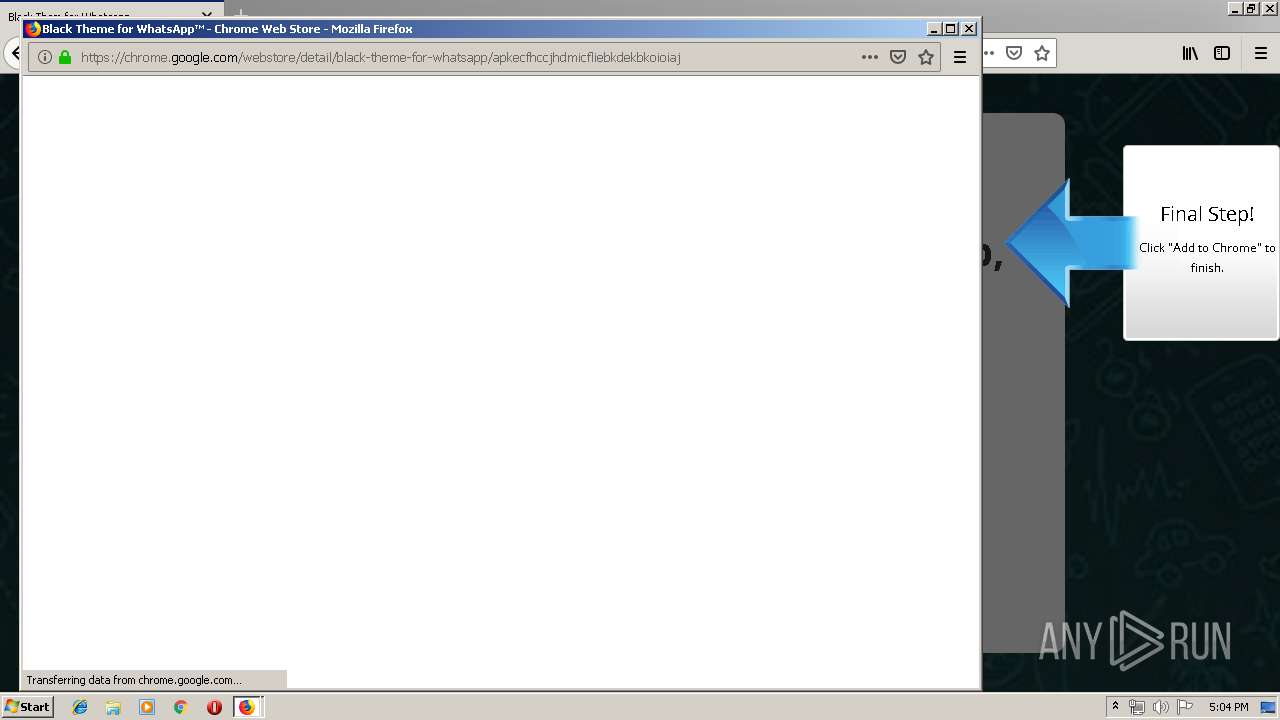
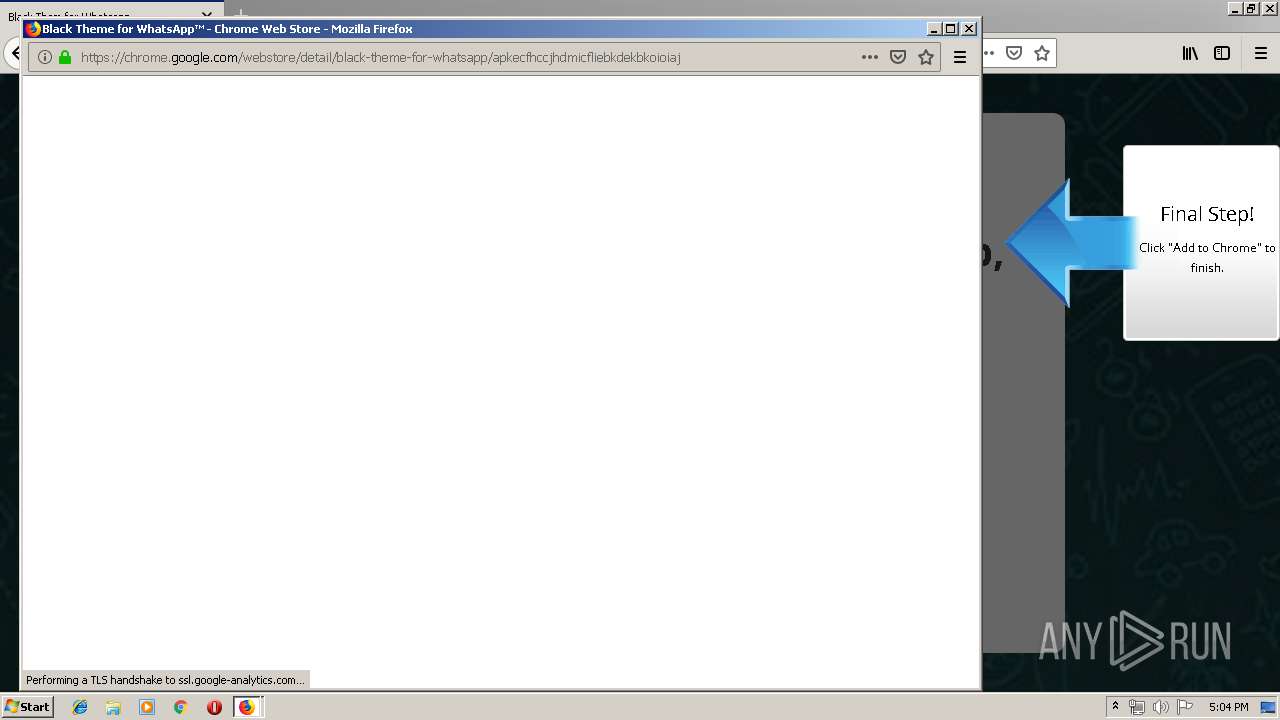
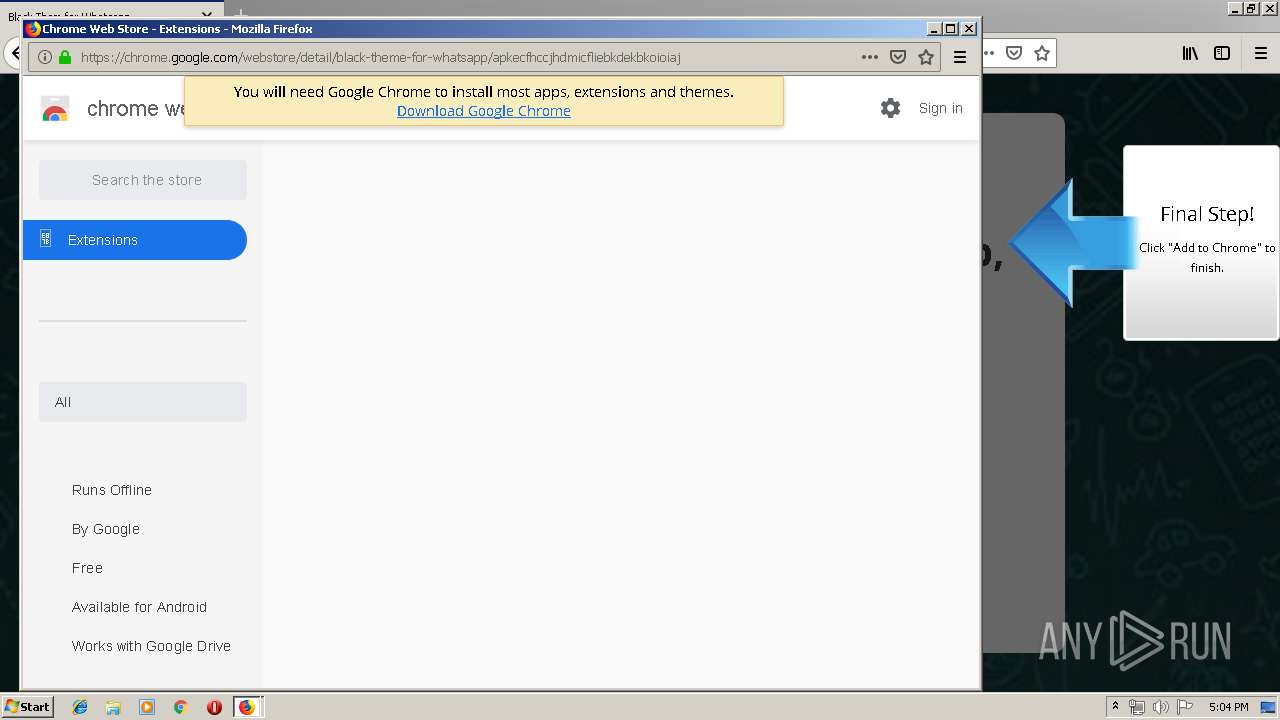
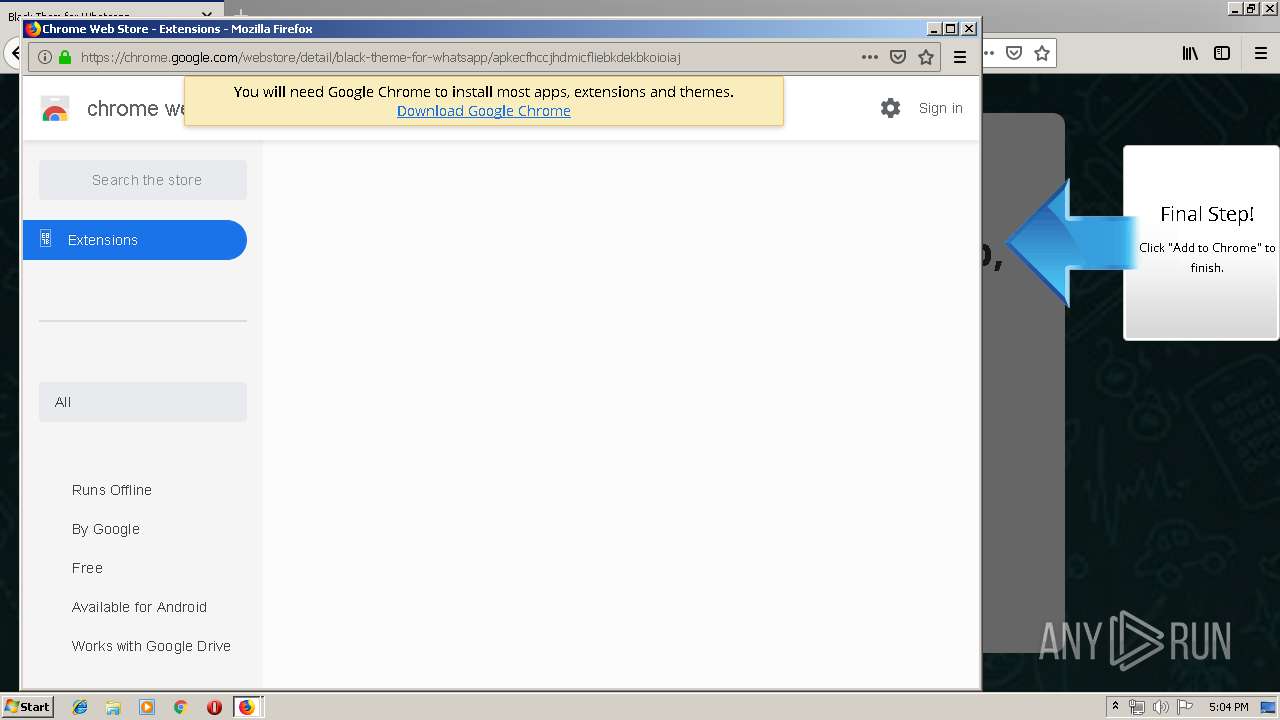
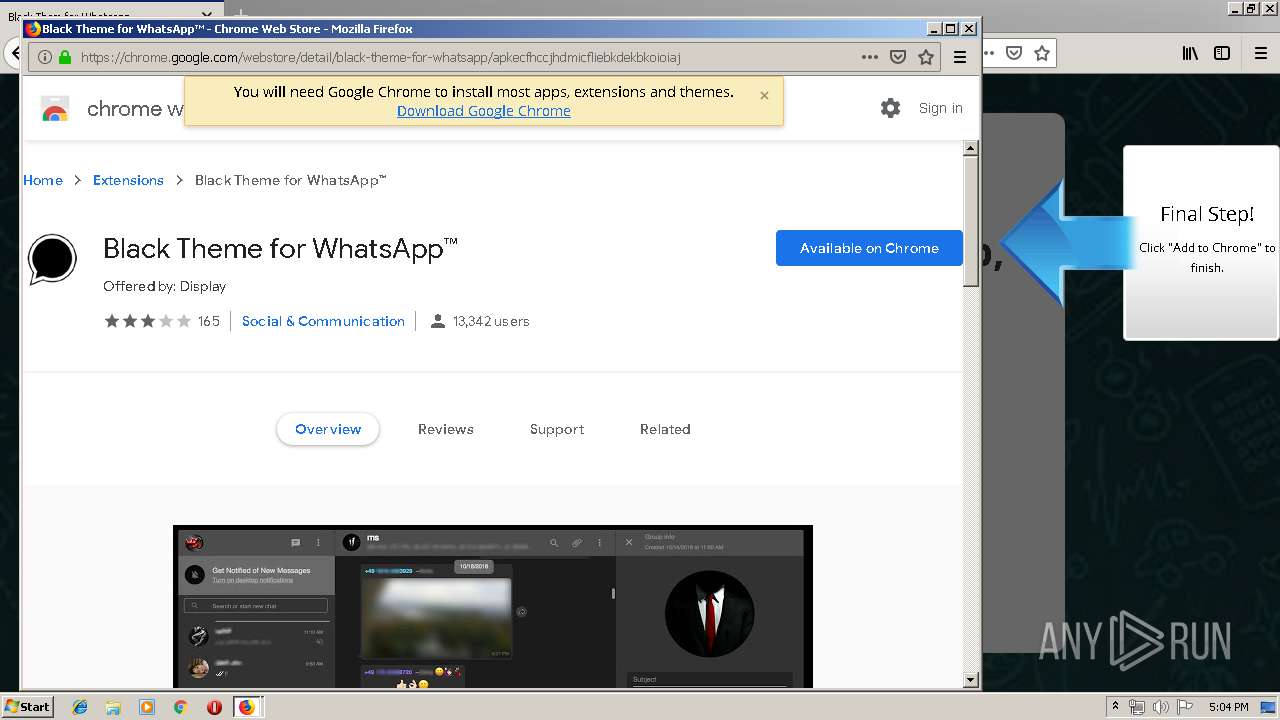
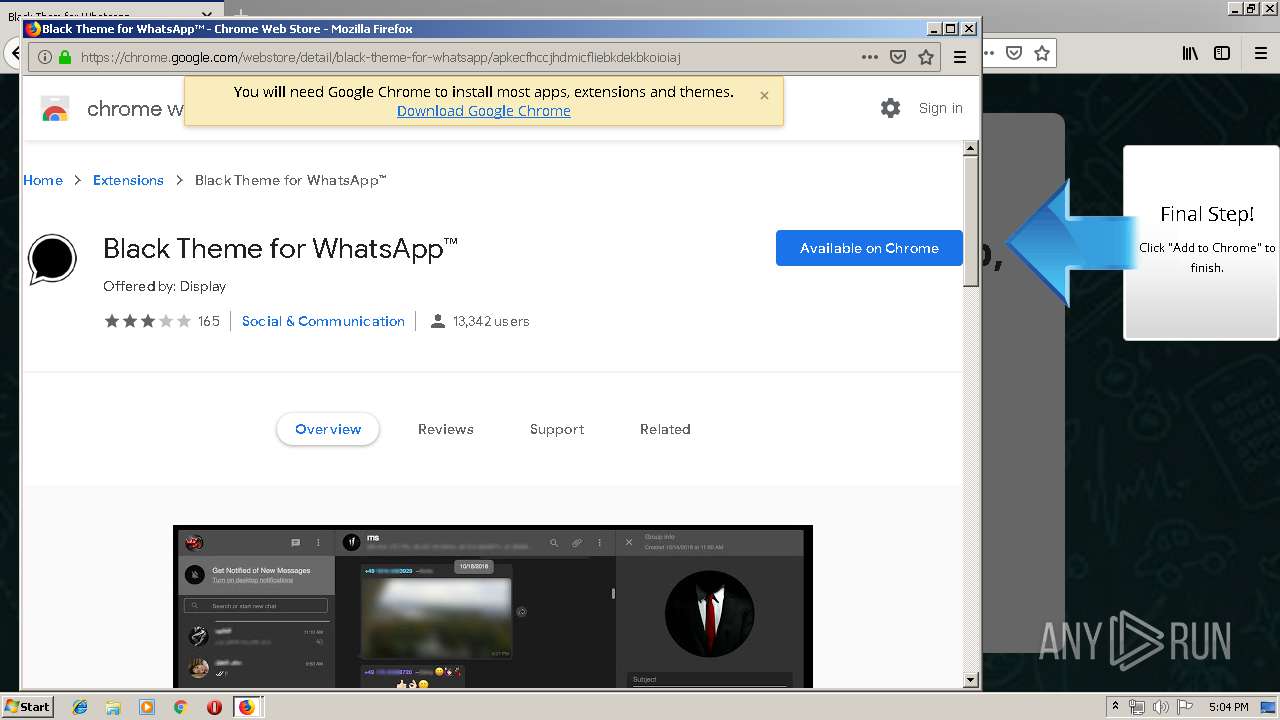
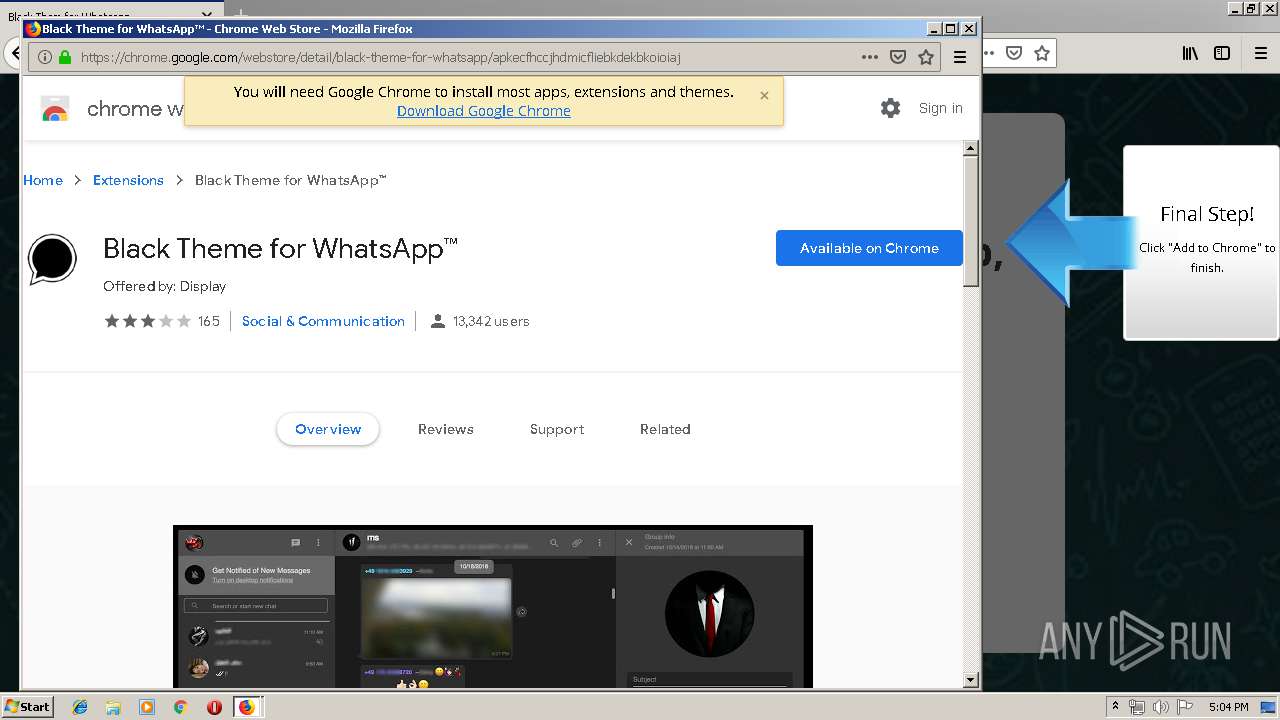
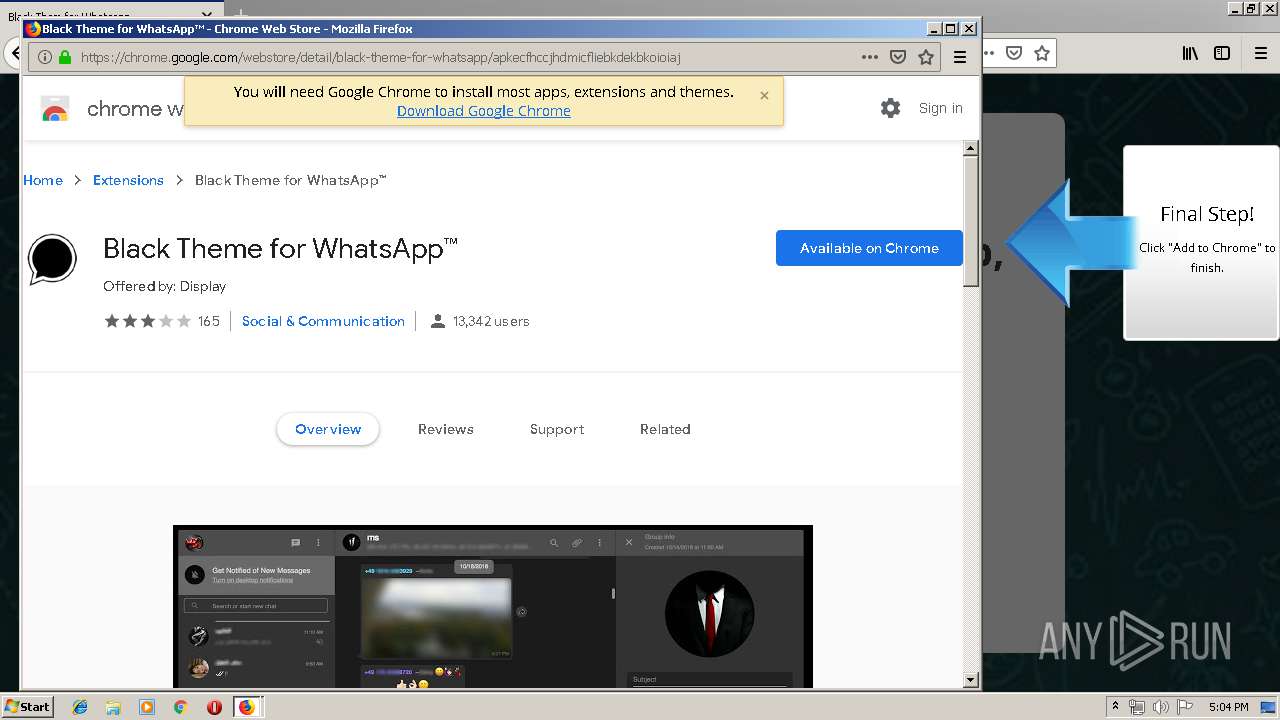
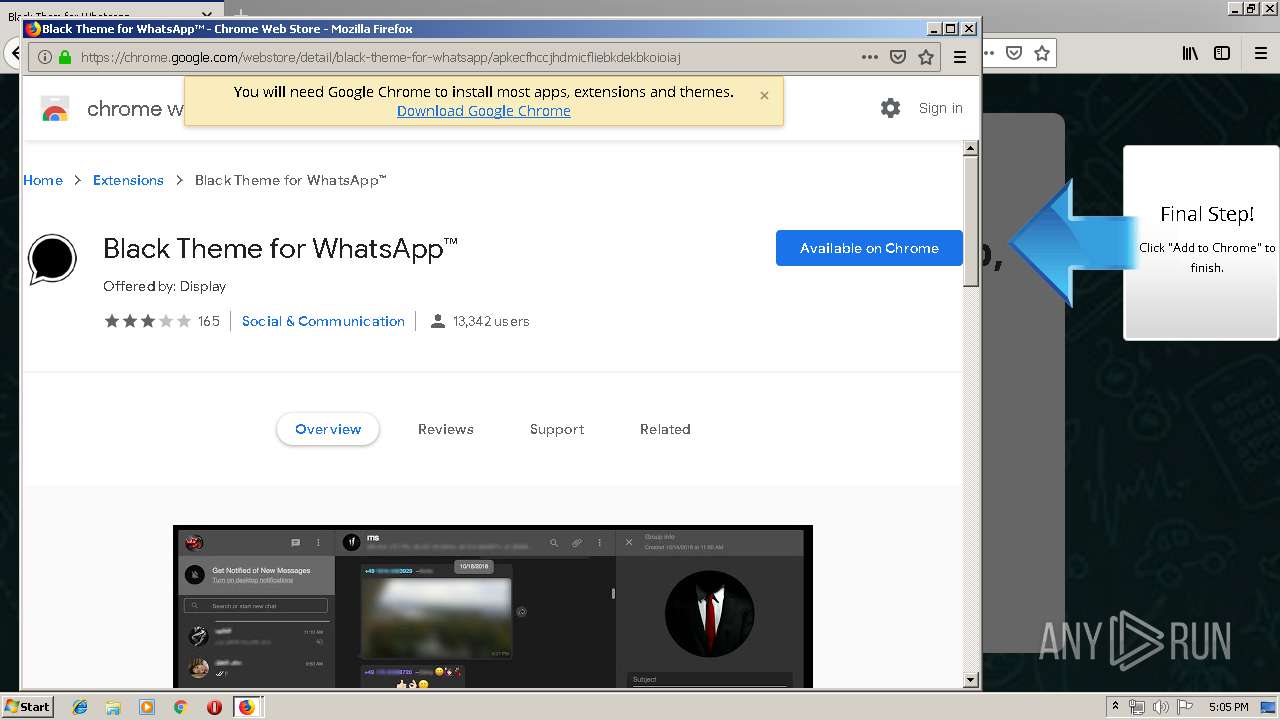
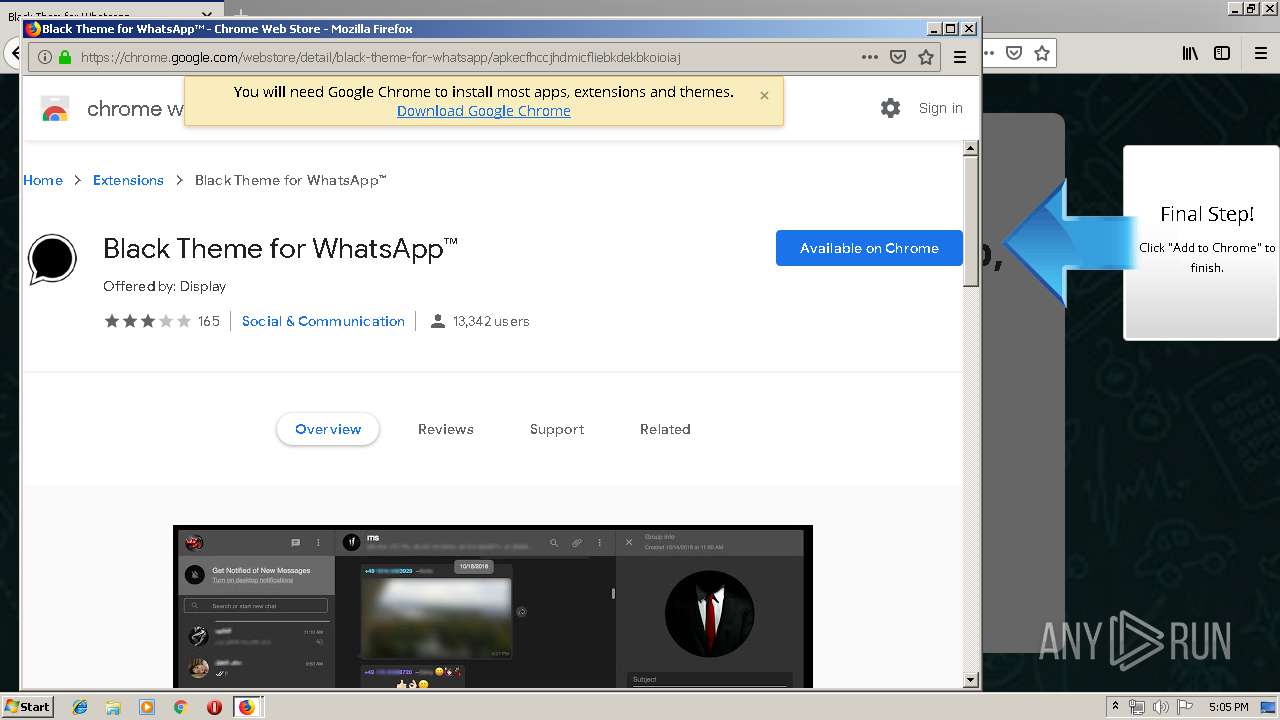
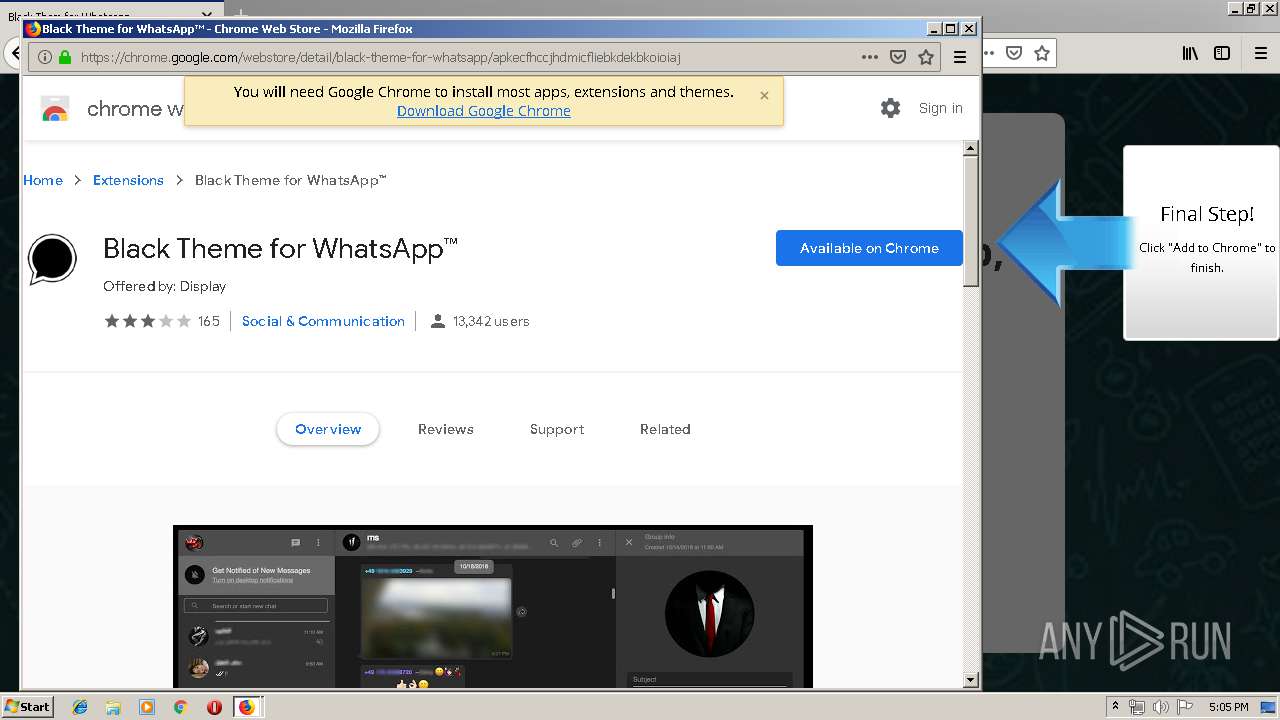
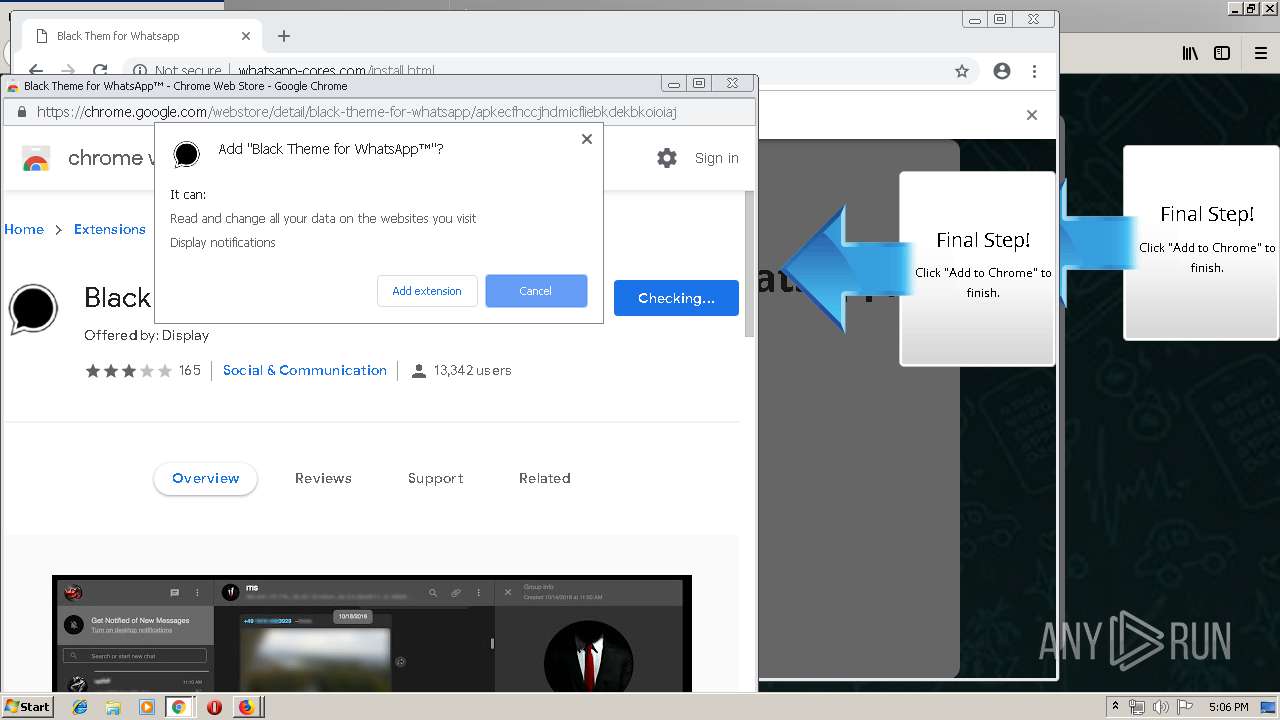
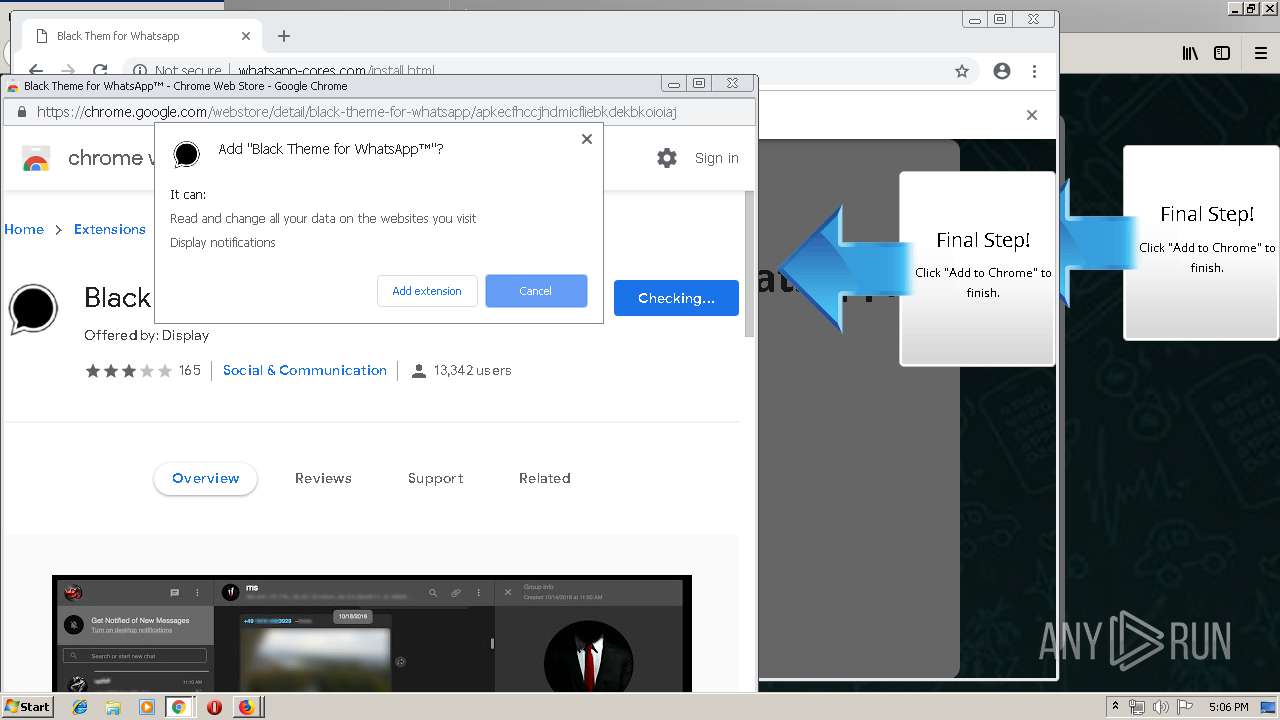
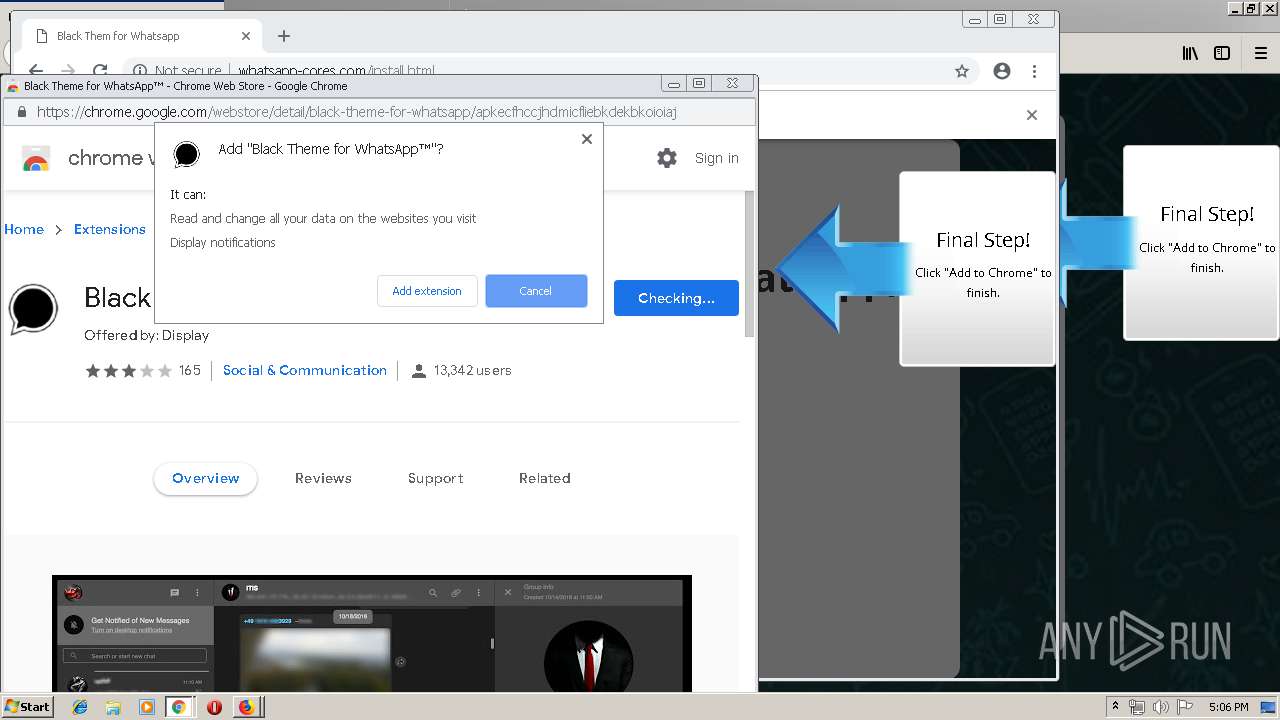
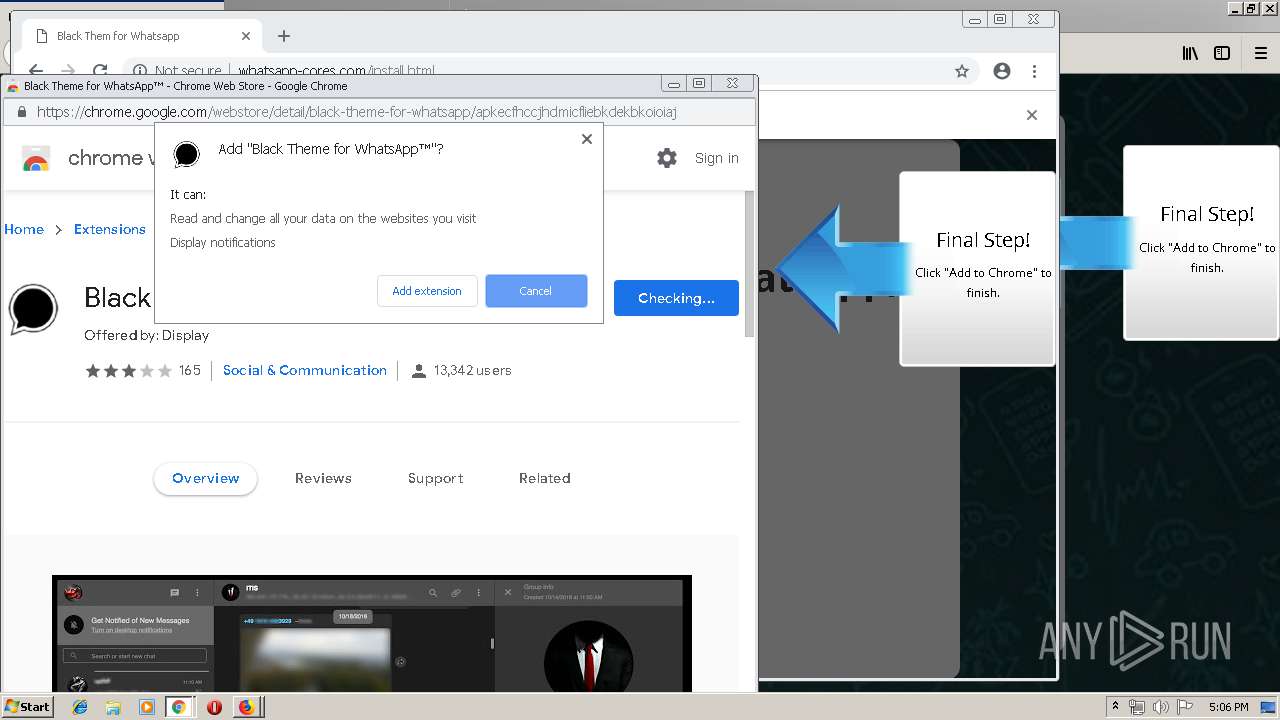
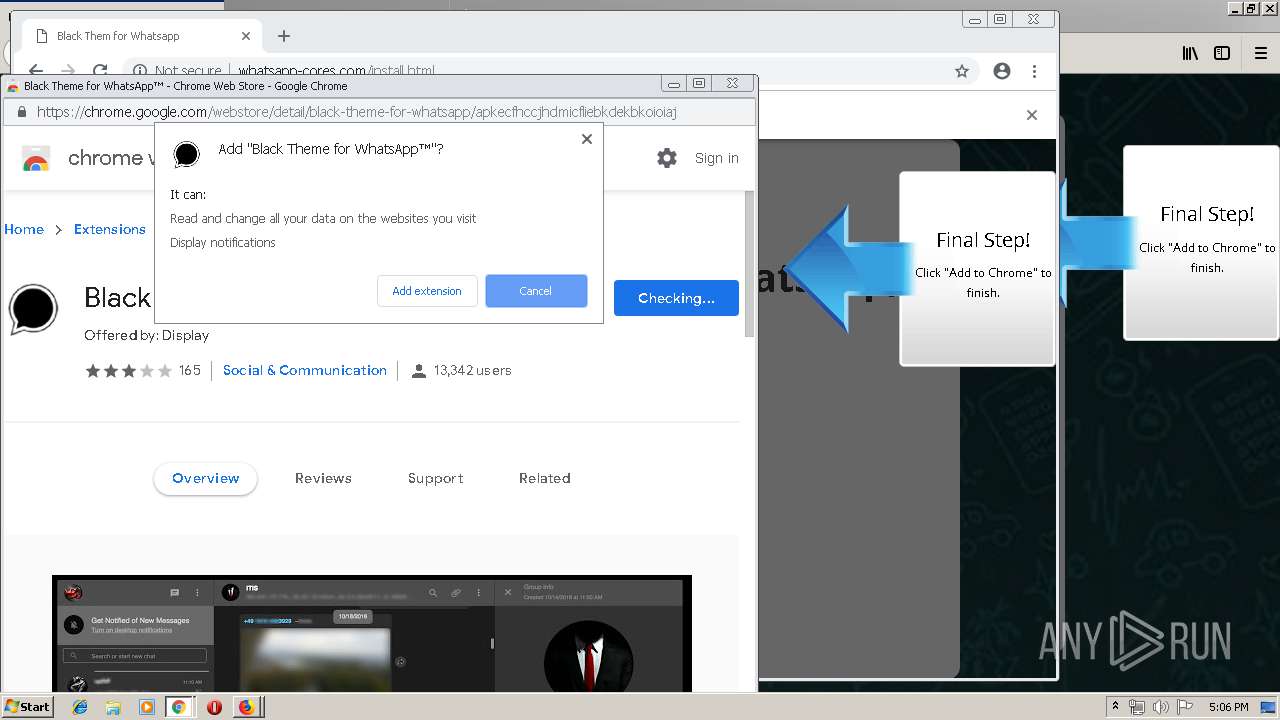
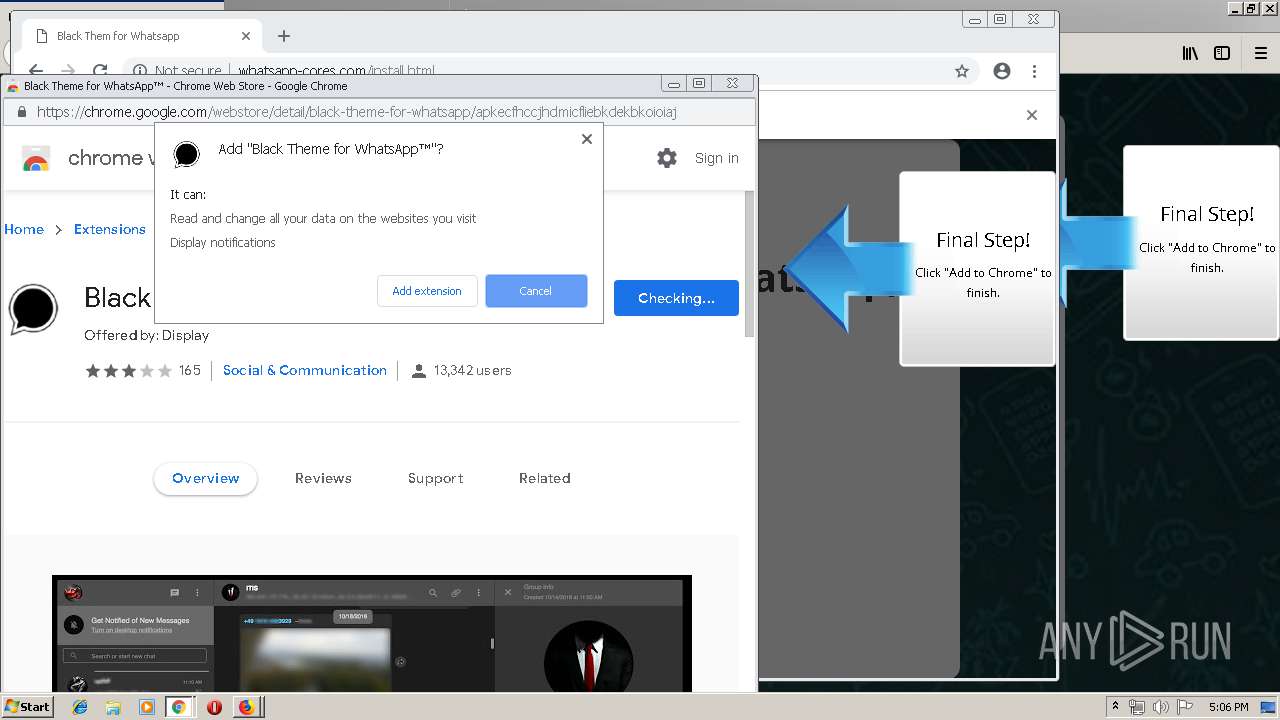
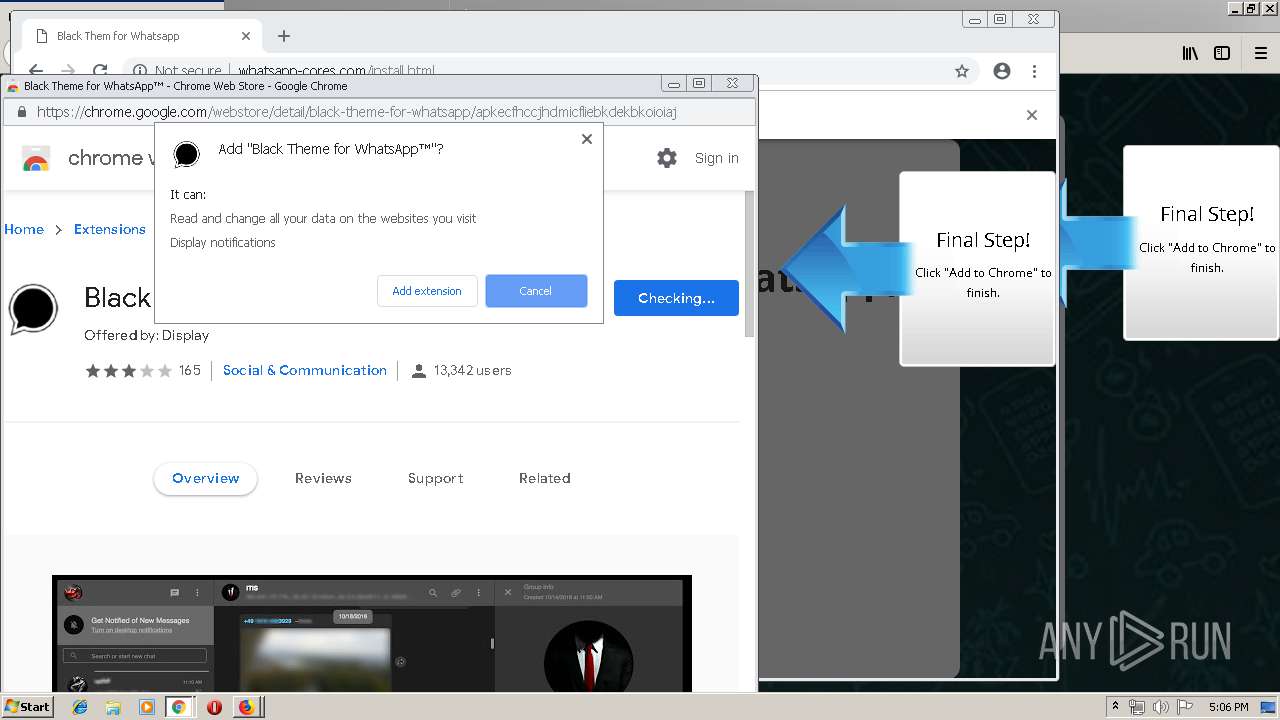
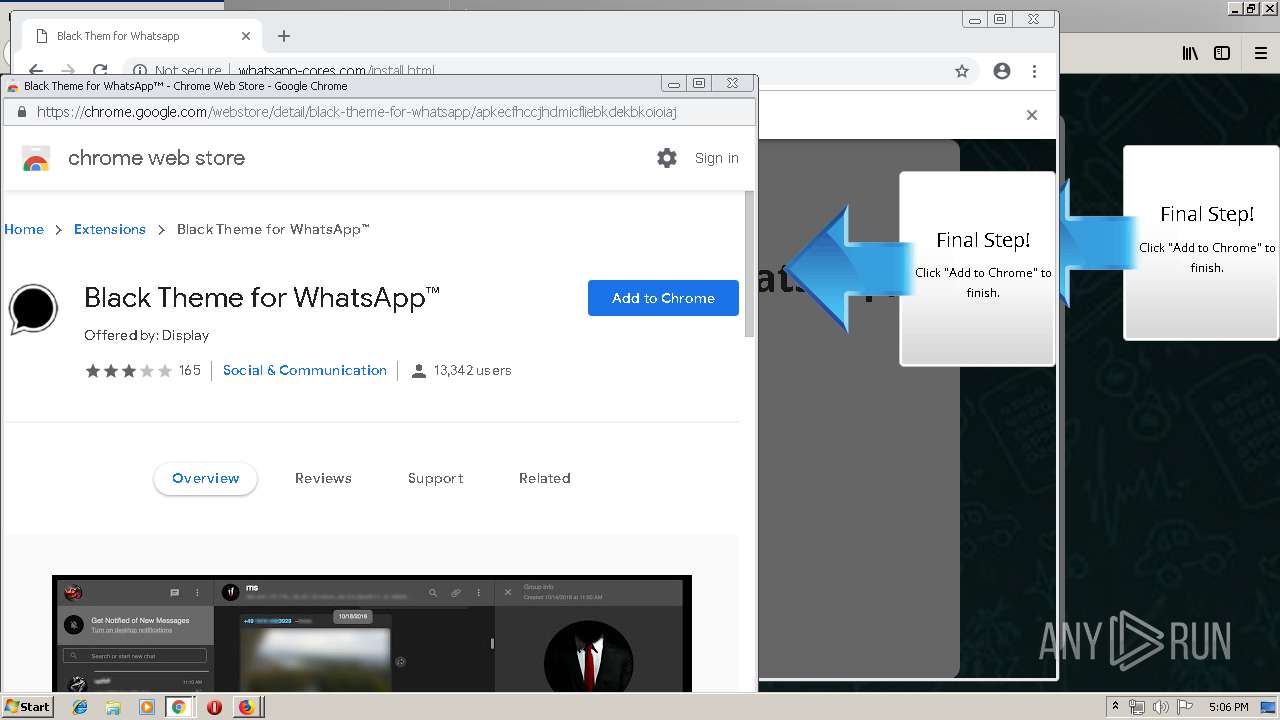
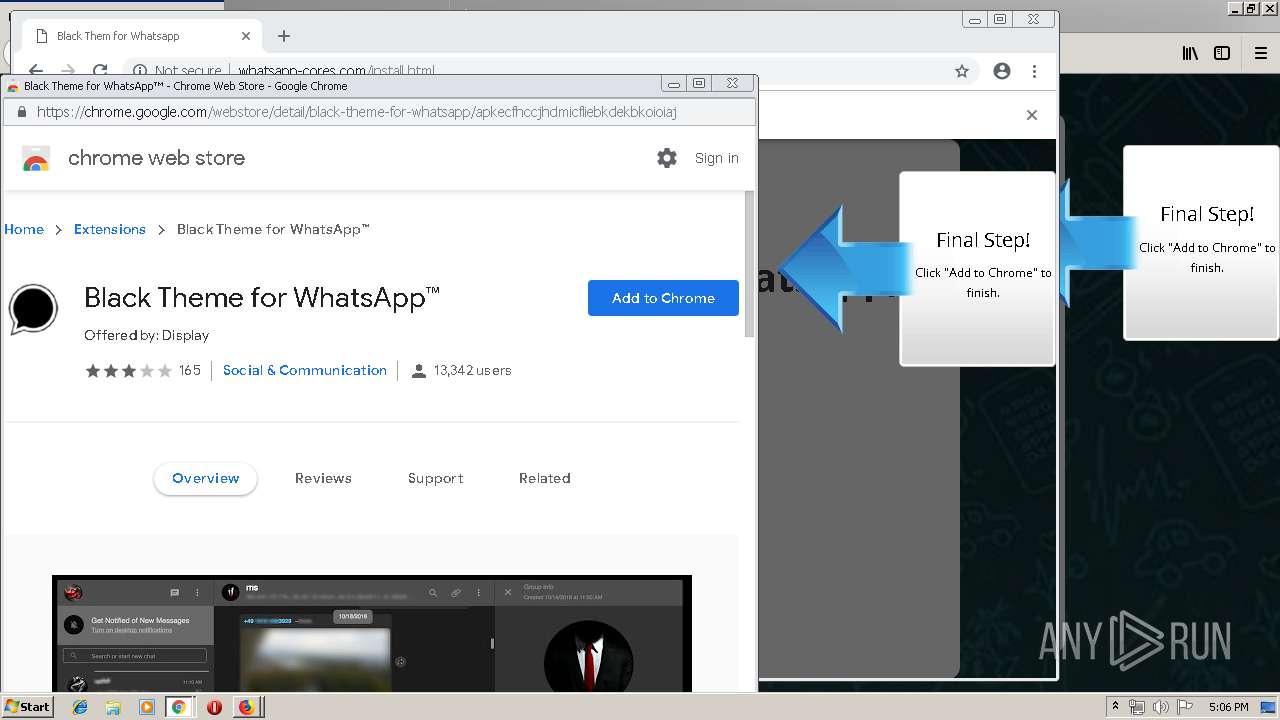
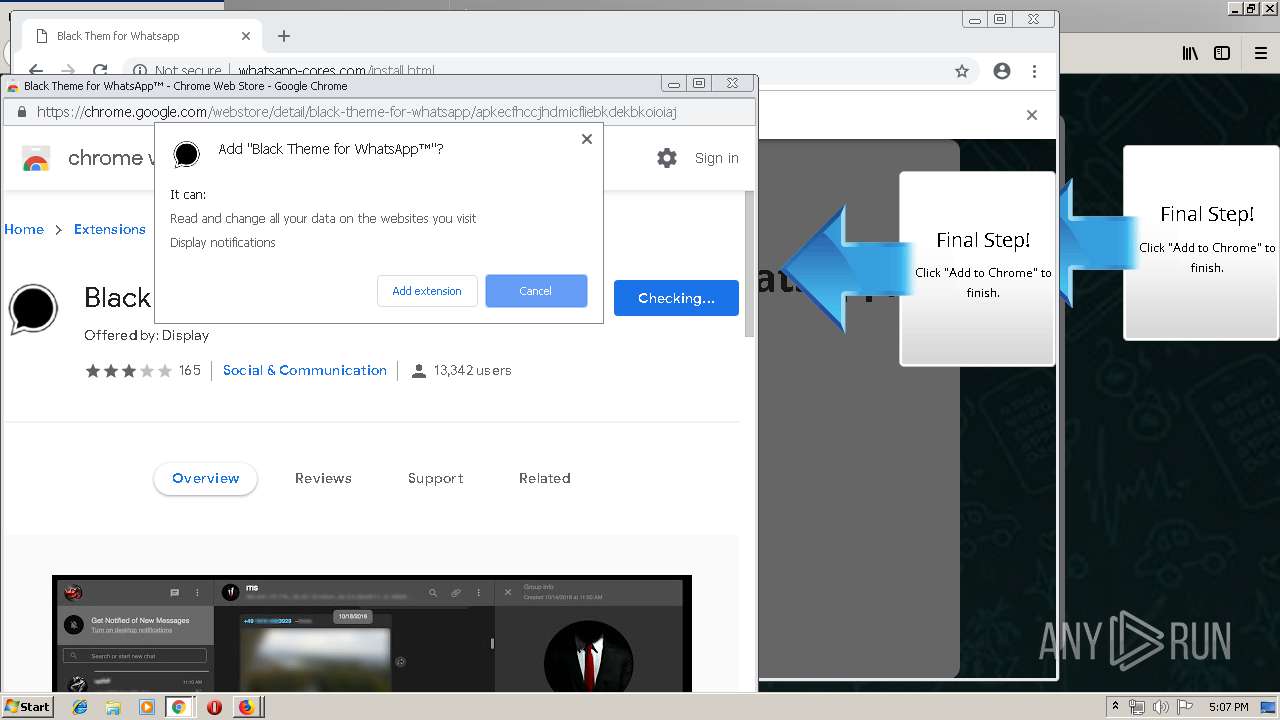
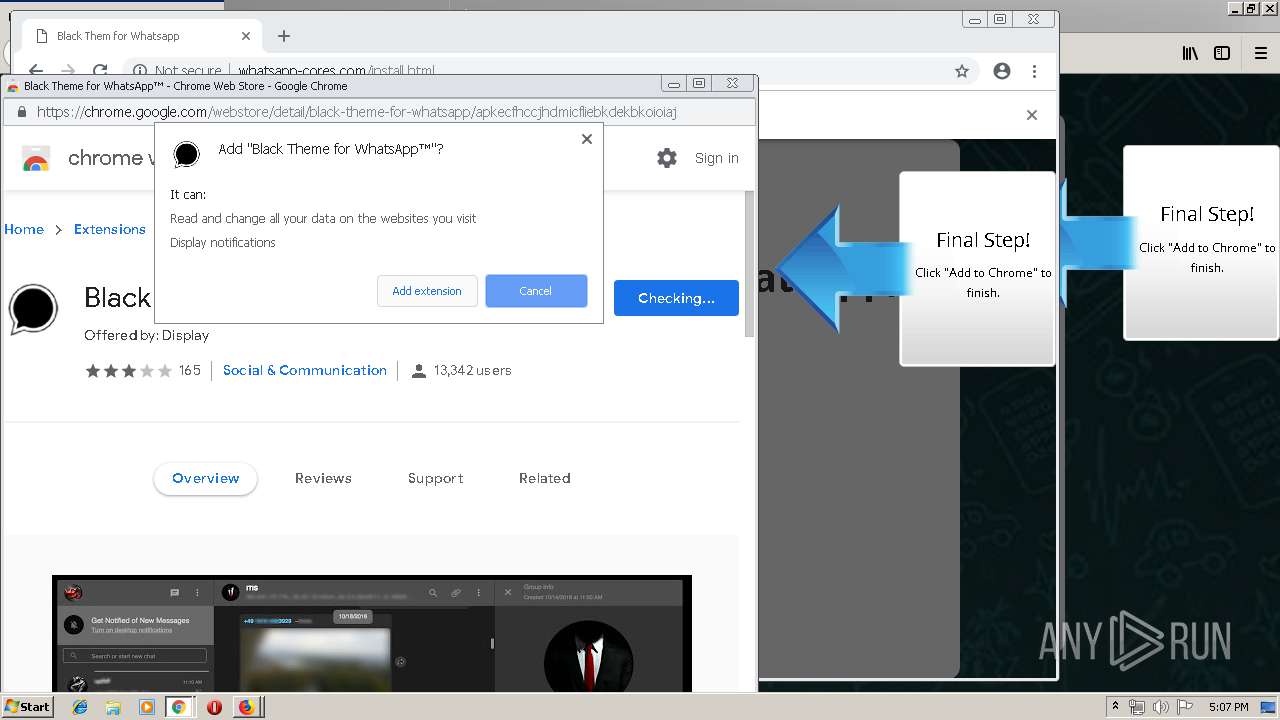
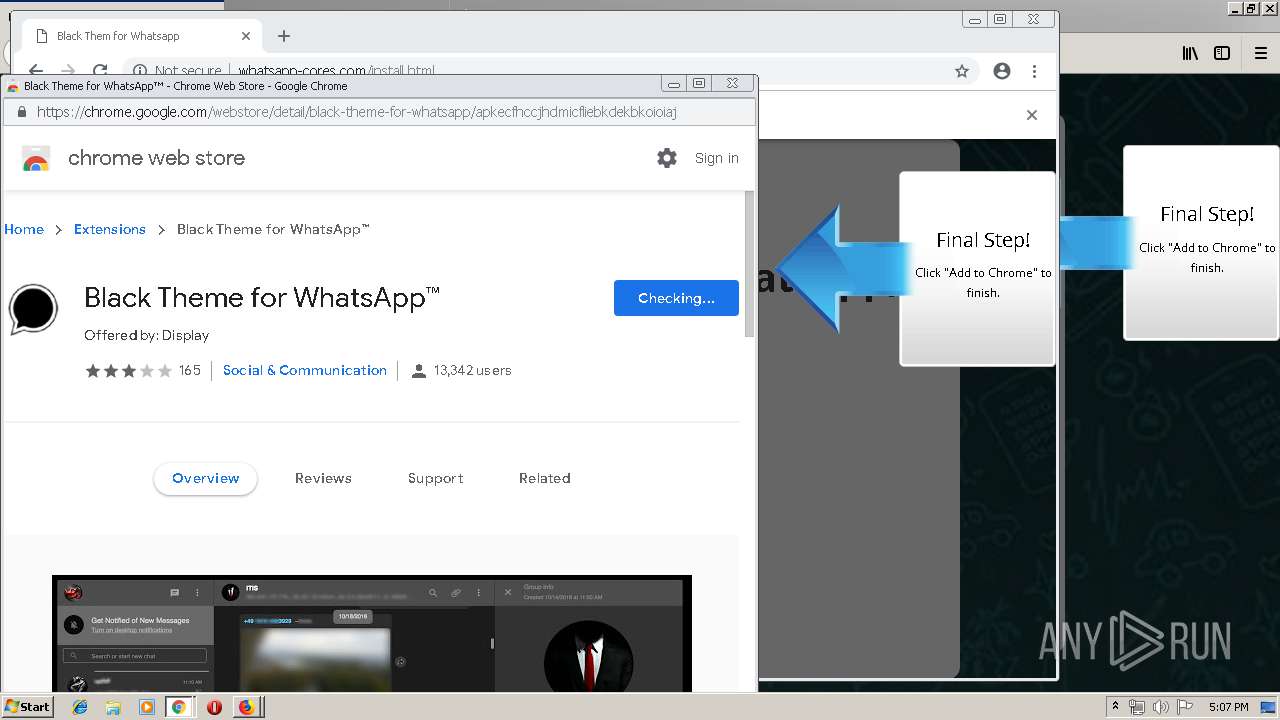
Modifies files in Chrome extension folder
- chrome.exe (PID: 304)
INFO
Application launched itself
- firefox.exe (PID: 1500)
- chrome.exe (PID: 304)
Writes to a desktop.ini file (may be used to cloak folders)
- firefox.exe (PID: 2820)
Reads CPU info
- firefox.exe (PID: 1500)
Reads settings of System Certificates
- chrome.exe (PID: 3112)
- firefox.exe (PID: 1500)
Creates files in the user directory
- firefox.exe (PID: 1500)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 304)
- firefox.exe (PID: 1500)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
72
Monitored processes
41
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 672 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,6194532380574416350,10434561395773722813,131072 --enable-features=PasswordImport --service-pipe-token=7249282508562329642 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7249282508562329642 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1928 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 760 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,6194532380574416350,10434561395773722813,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=5524763912408865800 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5524763912408865800 --renderer-client-id=16 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3828 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1012 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=964,6194532380574416350,10434561395773722813,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2921413256826358436 --mojo-platform-channel-handle=3256 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1344 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="1500.20.1154051895\40314560" -childID 3 -isForBrowser -prefsHandle 3328 -prefMapHandle 3416 -prefsLen 5824 -prefMapSize 180950 -schedulerPrefs 0001,2 -parentBuildID 20190225143501 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 1500 "\\.\pipe\gecko-crash-server-pipe.1500" 3428 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
| 1500 | "C:\Program Files\Mozilla Firefox\firefox.exe" http://spotify-br.com/?code=lyVLBxsp | C:\Program Files\Mozilla Firefox\firefox.exe | explorer.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
| 1720 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=964,6194532380574416350,10434561395773722813,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=3707127459490846287 --mojo-platform-channel-handle=2164 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1768 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="1500.0.189117376\242254238" -parentBuildID 20190225143501 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - "C:\Users\admin\AppData\LocalLow\Mozilla\Temp-{ce348e4c-7d33-445e-89f9-60108c51bcaf}" 1500 "\\.\pipe\gecko-crash-server-pipe.1500" 1120 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
| 1904 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=964,6194532380574416350,10434561395773722813,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=9898621650441749615 --mojo-platform-channel-handle=4756 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2244 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="1500.13.1421258999\615181371" -childID 2 -isForBrowser -prefsHandle 2536 -prefMapHandle 2548 -prefsLen 216 -prefMapSize 180950 -schedulerPrefs 0001,2 -parentBuildID 20190225143501 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 1500 "\\.\pipe\gecko-crash-server-pipe.1500" 2468 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
Total events
1 599
Read events
1 453
Write events
140
Delete events
6
Modification events
| (PID) Process: | (1500) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1500) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (304) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (304) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (304) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (304) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (304) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3196) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 304-13199731576238390 |
Value: 259 | |||
| (PID) Process: | (304) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (304) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
Executable files
0
Suspicious files
441
Text files
589
Unknown types
98
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1500 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 1500 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 1500 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 1500 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-child-current.bin | binary | |
MD5:— | SHA256:— | |||
| 1500 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:— | SHA256:— | |||
| 1500 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:— | SHA256:— | |||
| 1500 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\cache2\entries\DDEDA7D0965523D2AFA47FFC58005886CEF51E20 | compressed | |
MD5:— | SHA256:— | |||
| 1500 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\except-flashsubdoc-digest256.sbstore | — | |
MD5:— | SHA256:— | |||
| 1500 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\google4\goog-badbinurl-proto.metadata | — | |
MD5:— | SHA256:— | |||
| 1500 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\google4\goog-badbinurl-proto.pset | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
81
TCP/UDP connections
175
DNS requests
205
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
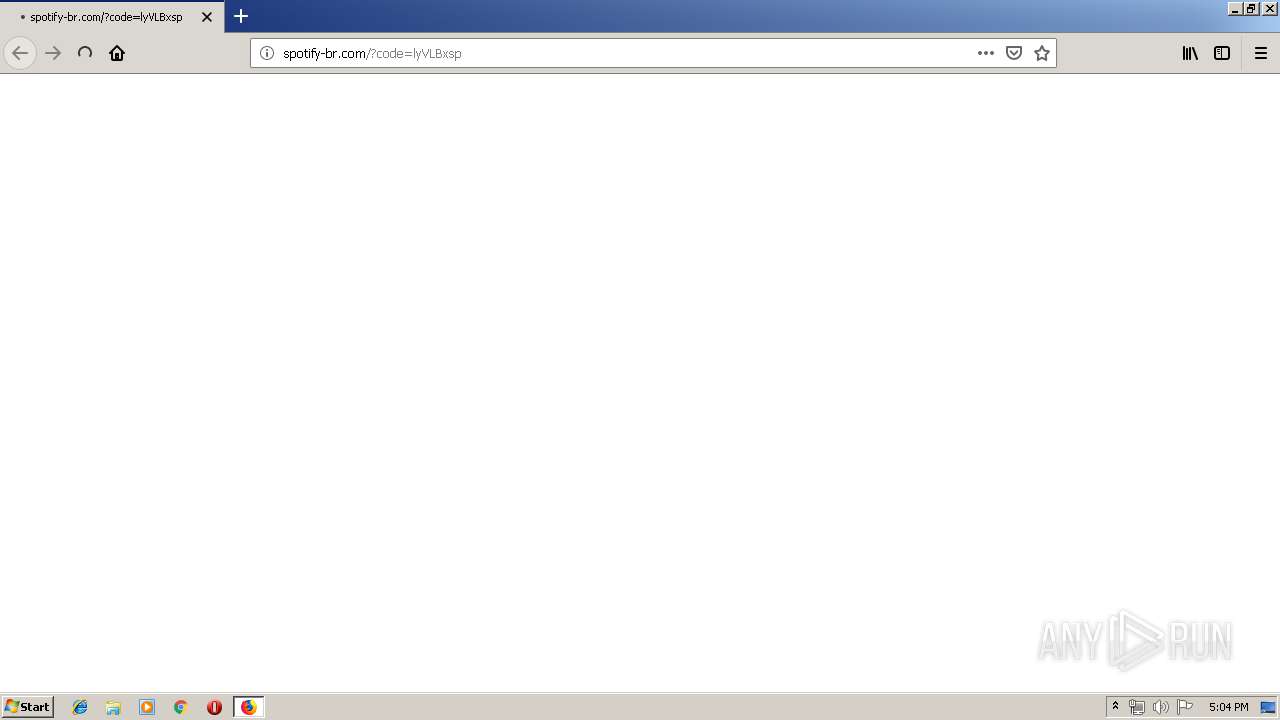
1500 | firefox.exe | GET | 200 | 3.86.233.115:80 | http://spotify-br.com/?code=lyVLBxsp | US | html | 3.93 Kb | unknown |
1500 | firefox.exe | POST | 200 | 2.21.242.245:80 | http://ocsp.int-x3.letsencrypt.org/ | NL | der | 527 b | whitelisted |
1500 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
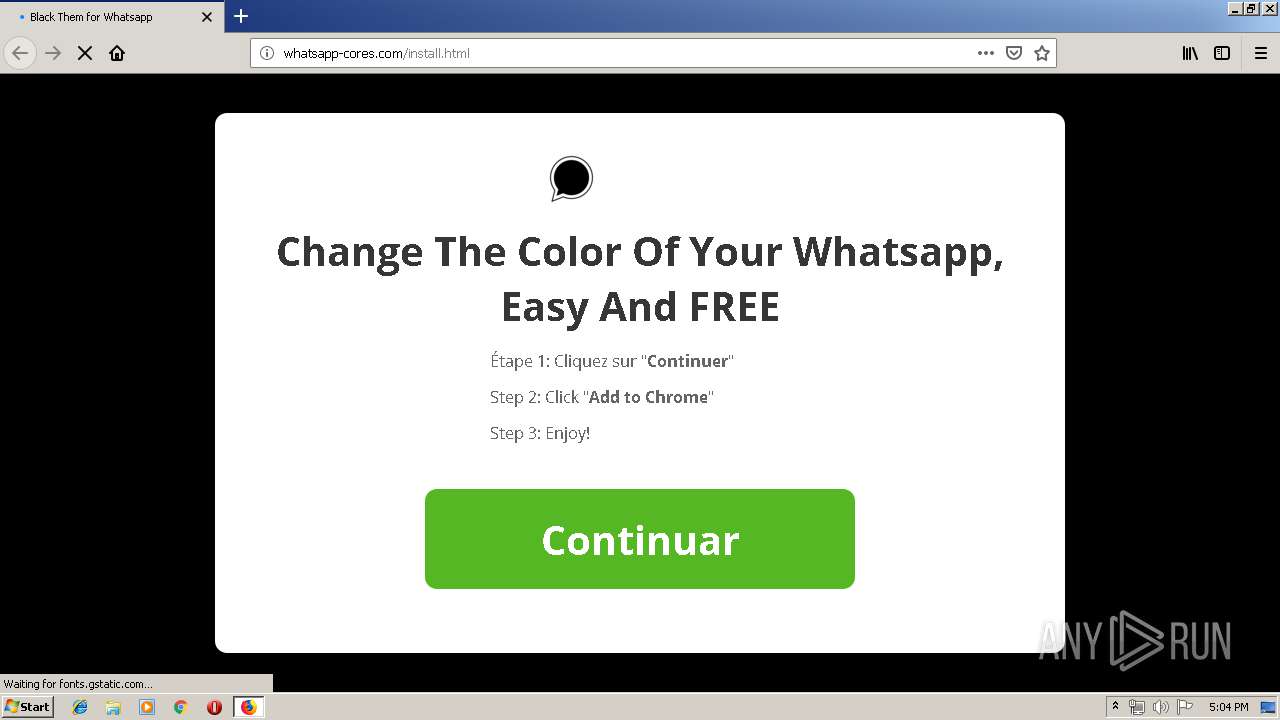
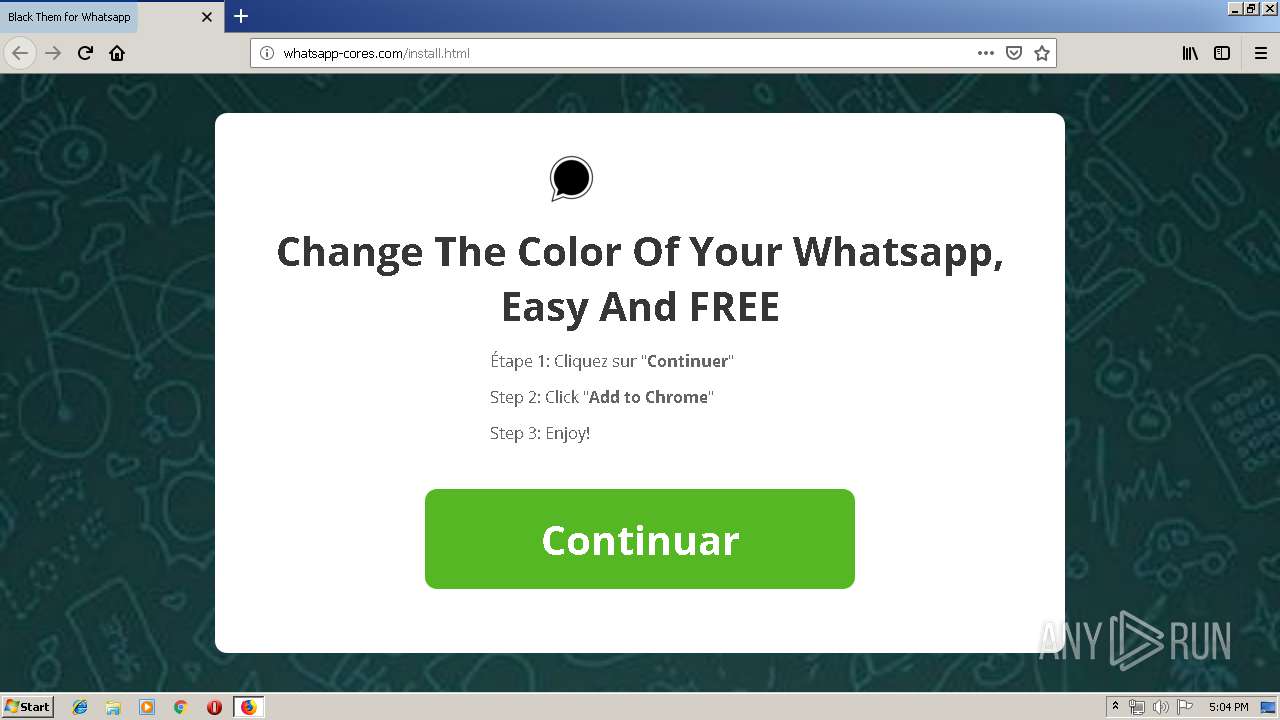
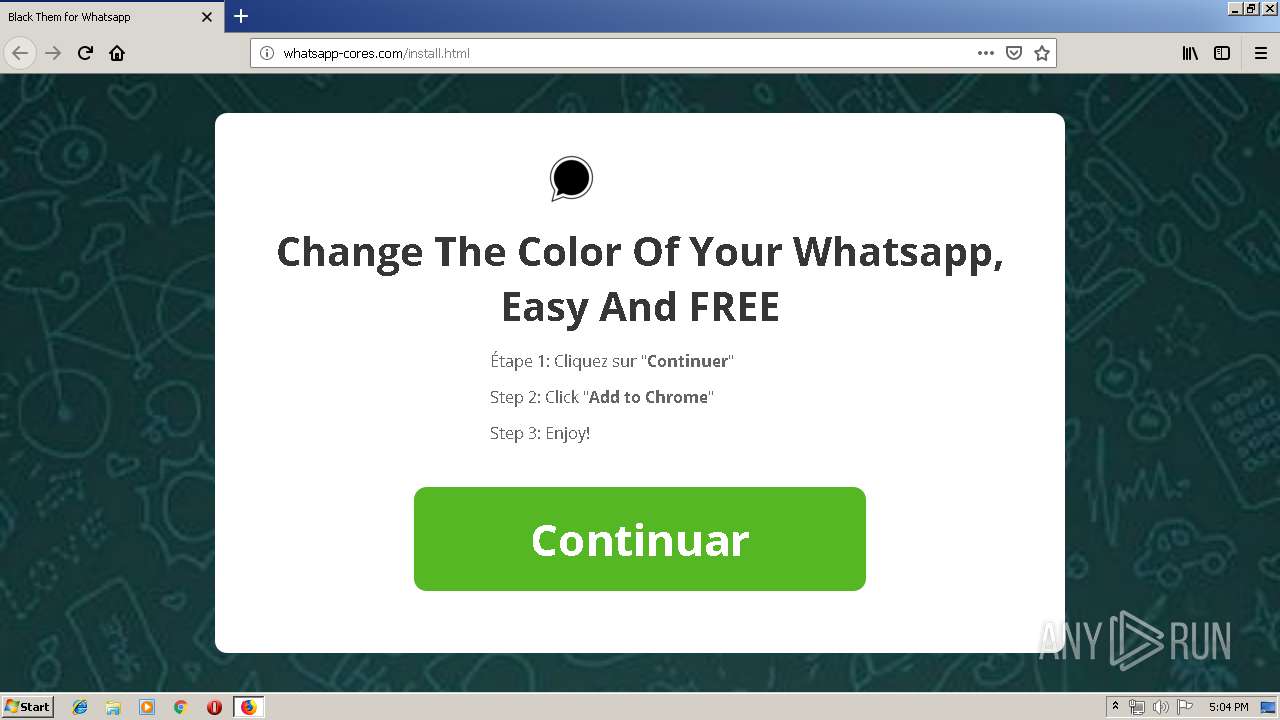
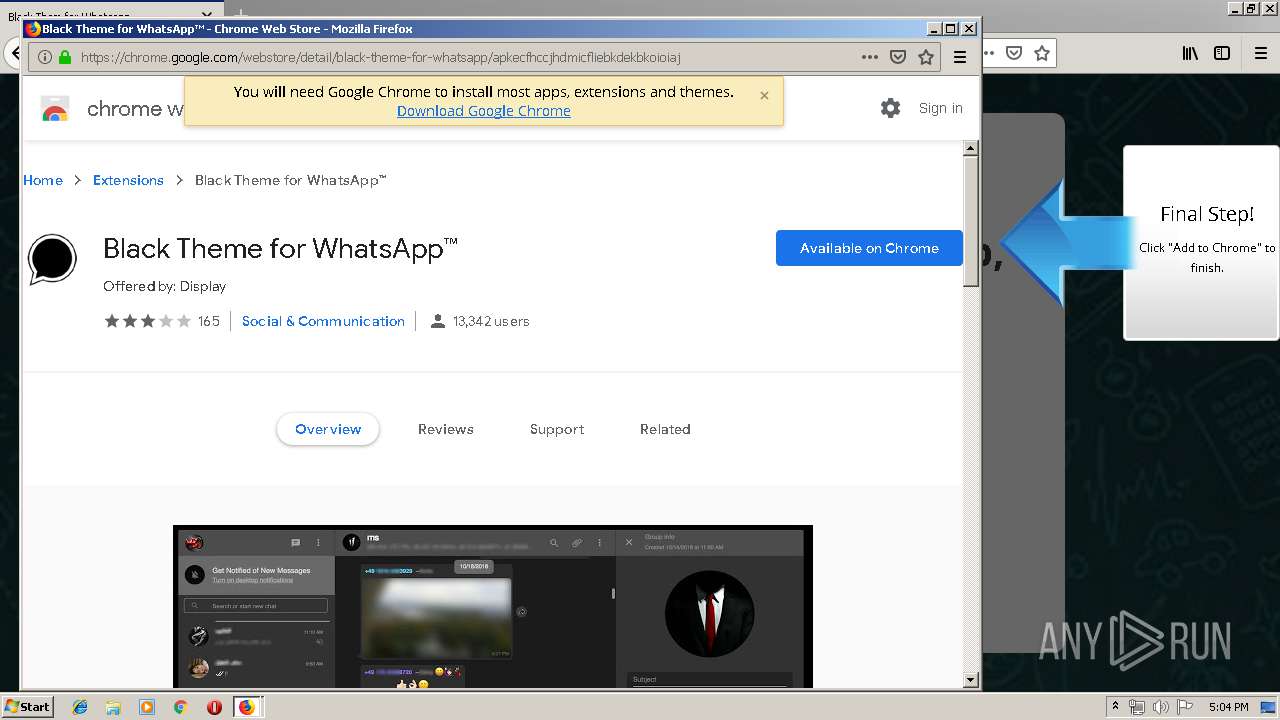
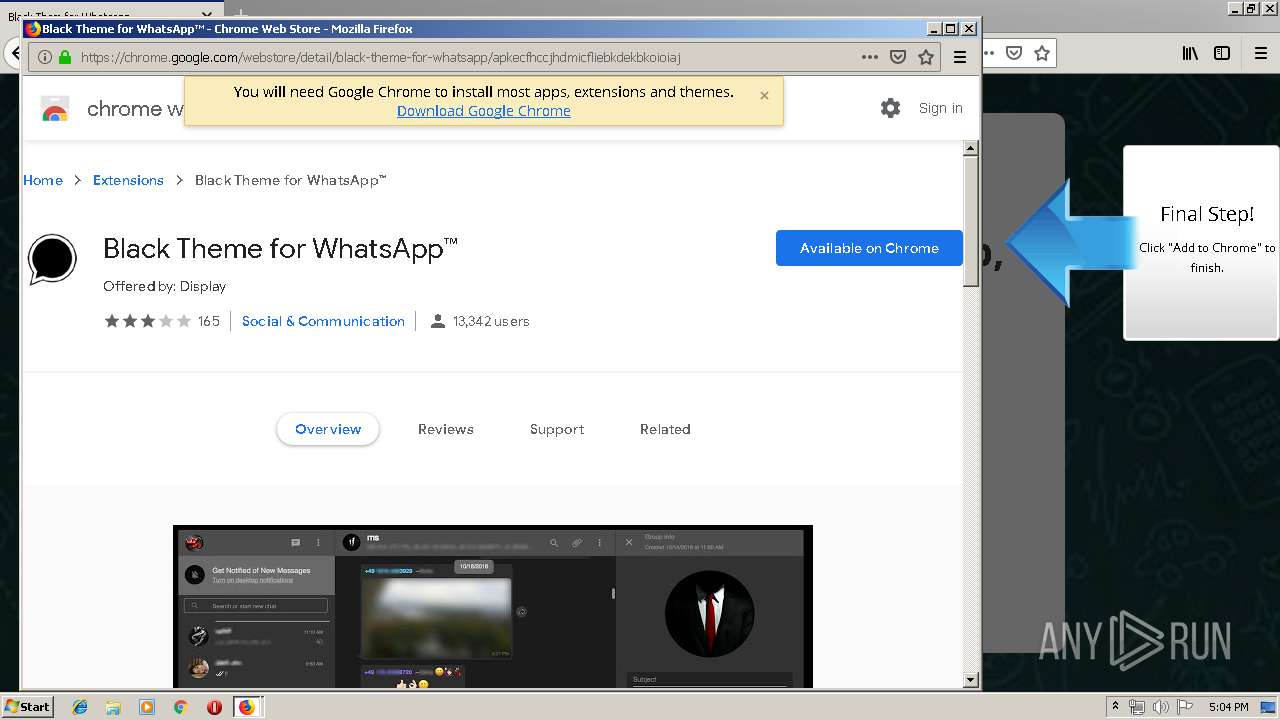
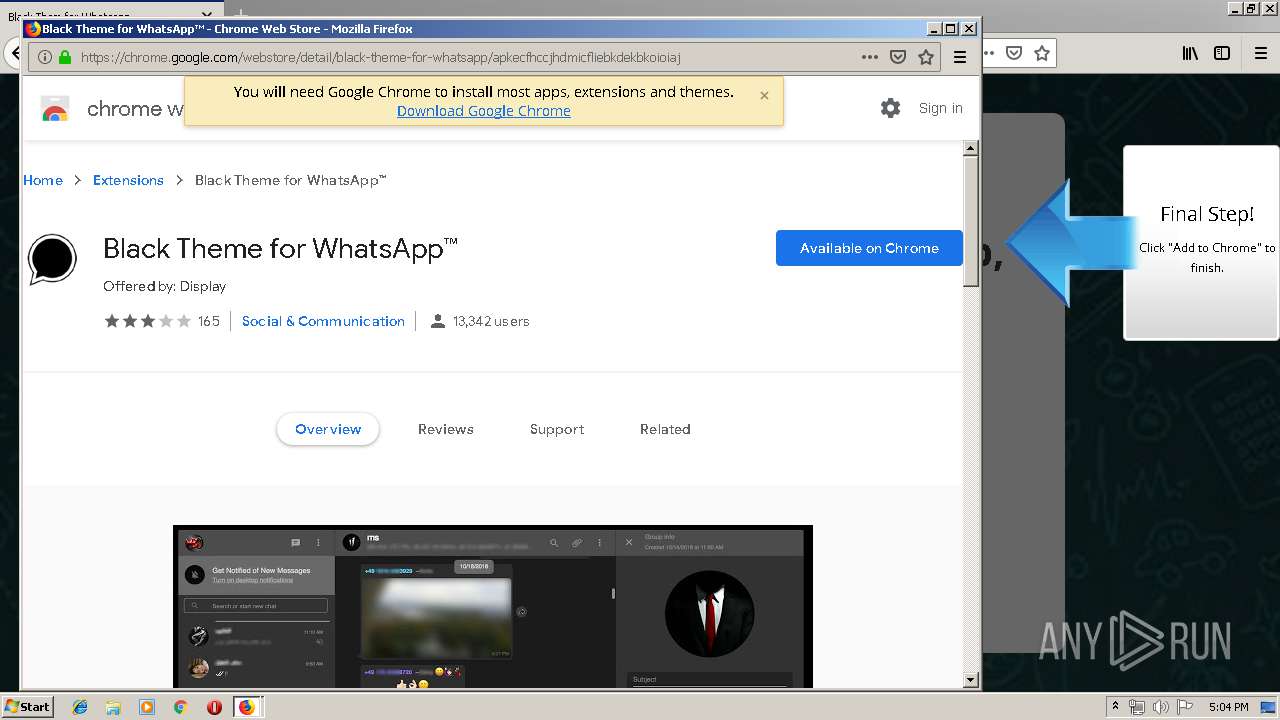
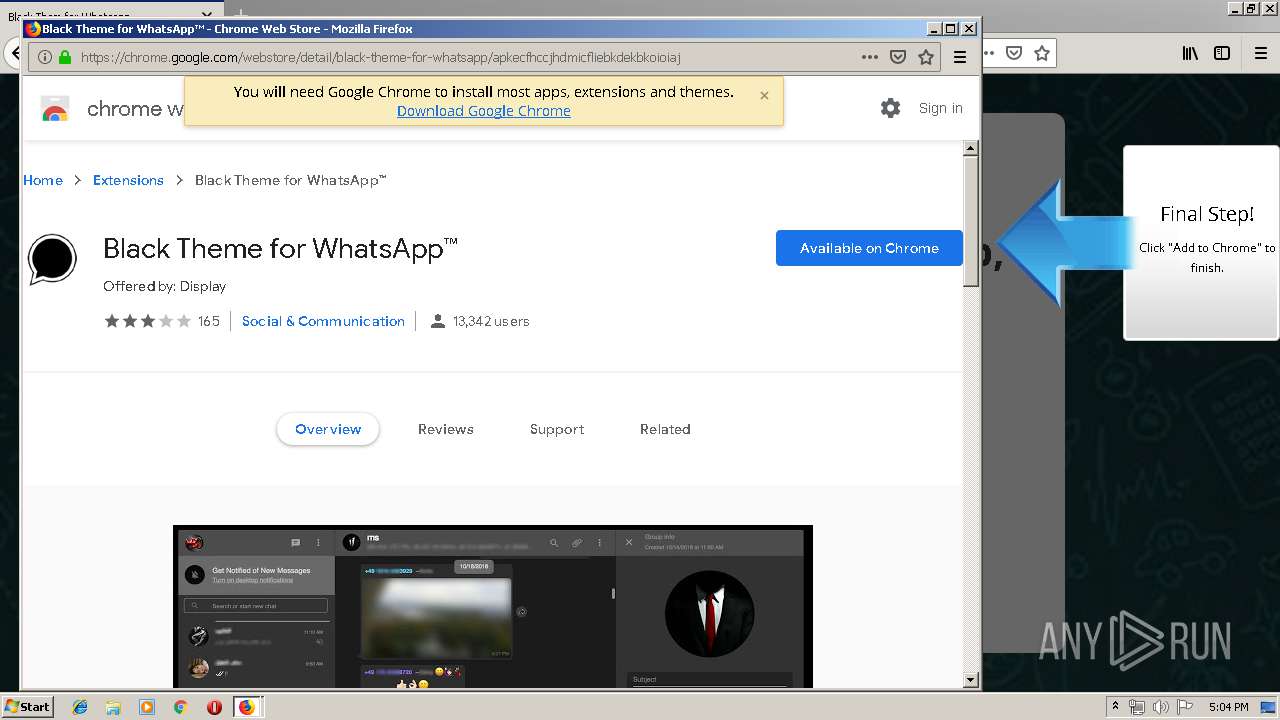
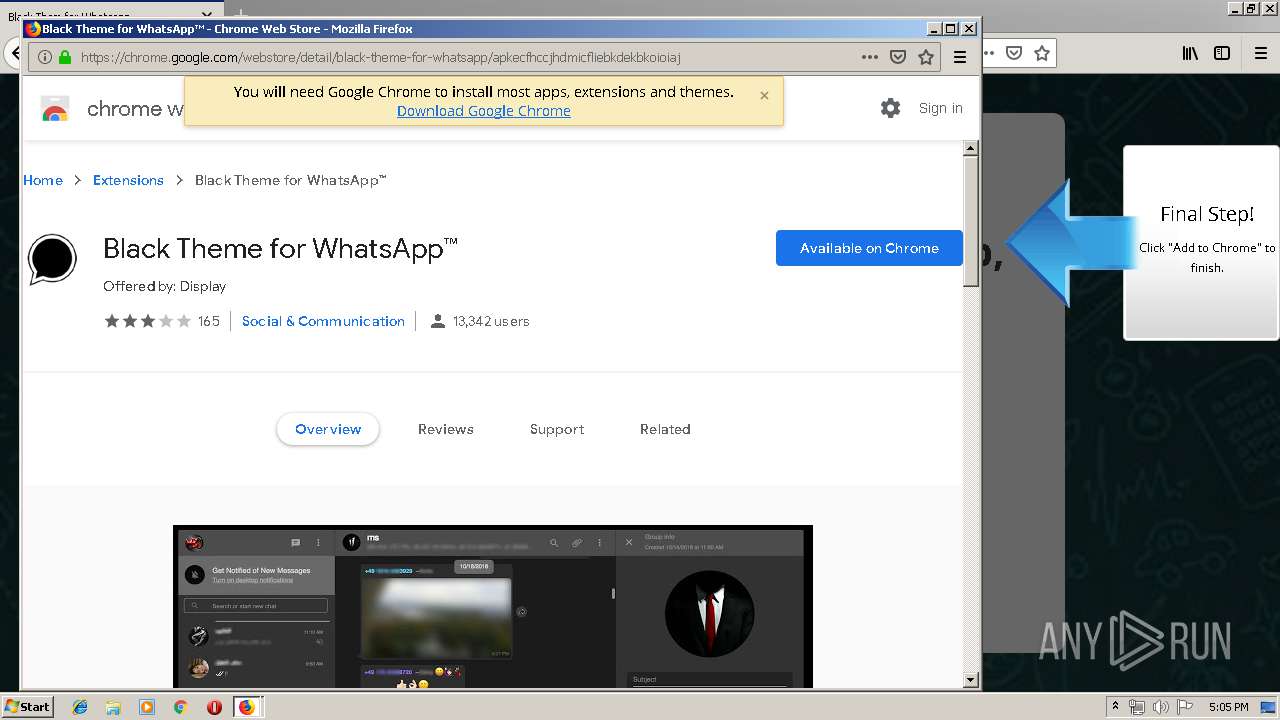
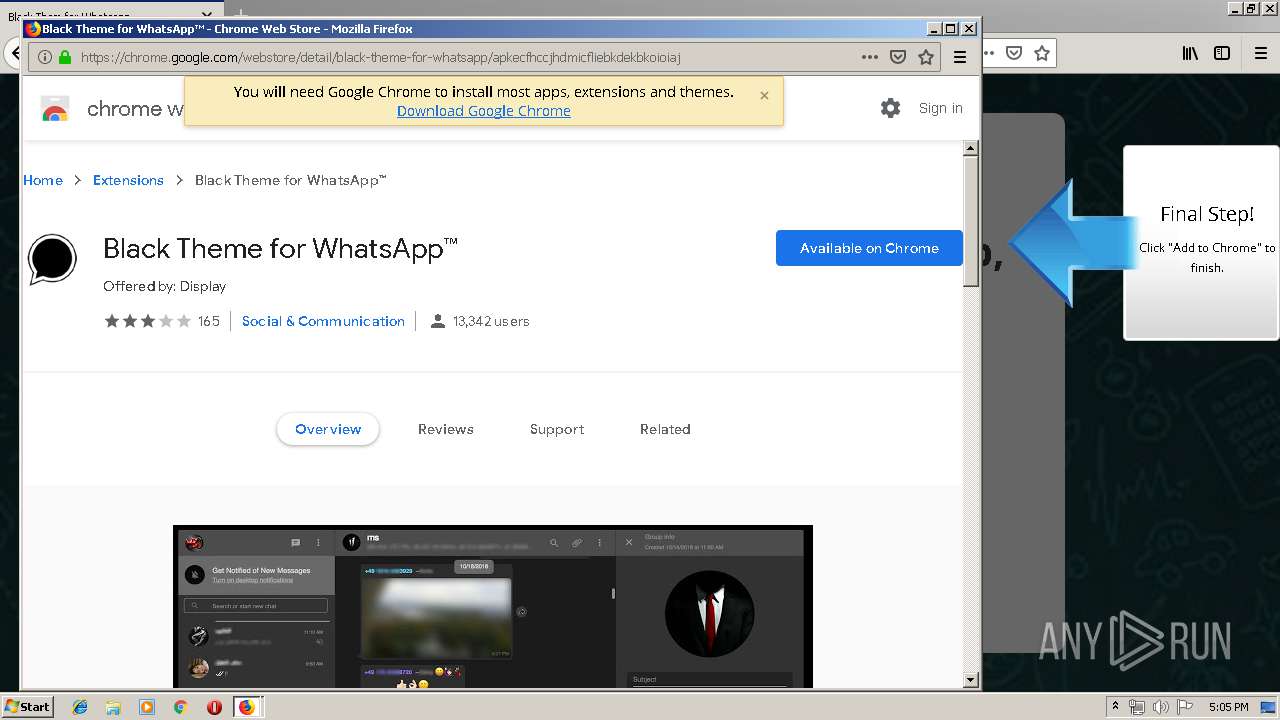
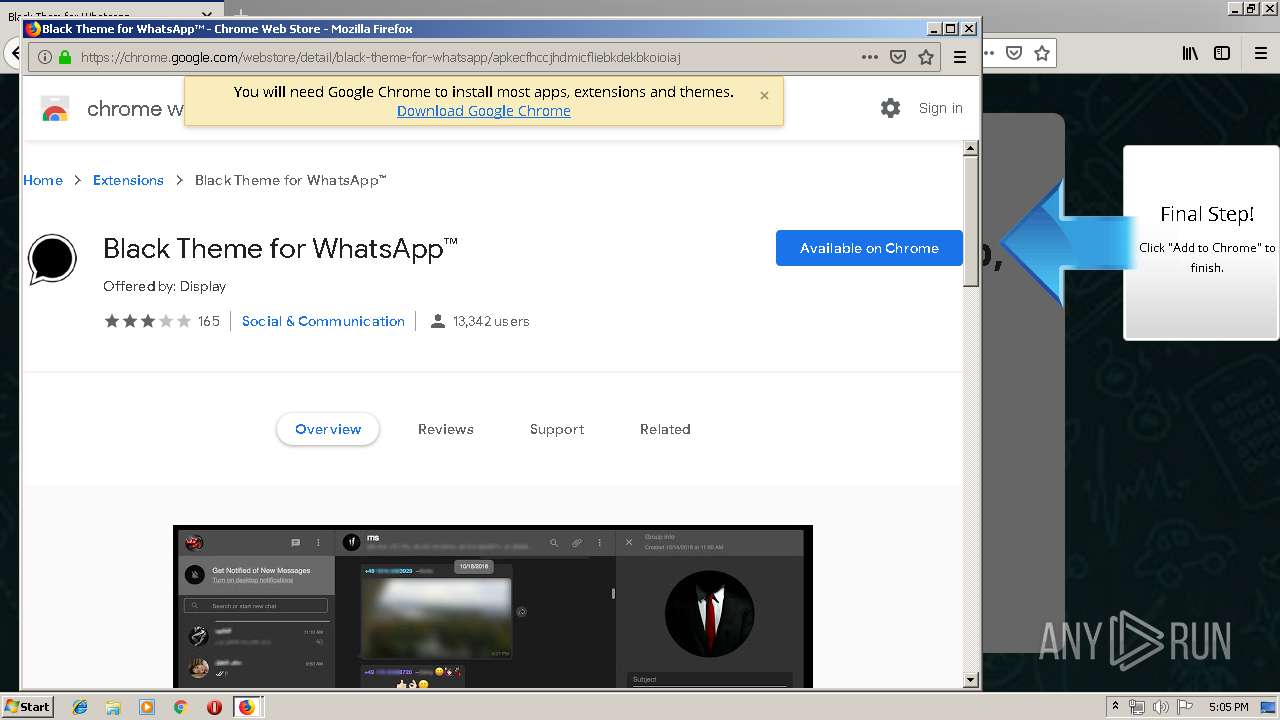
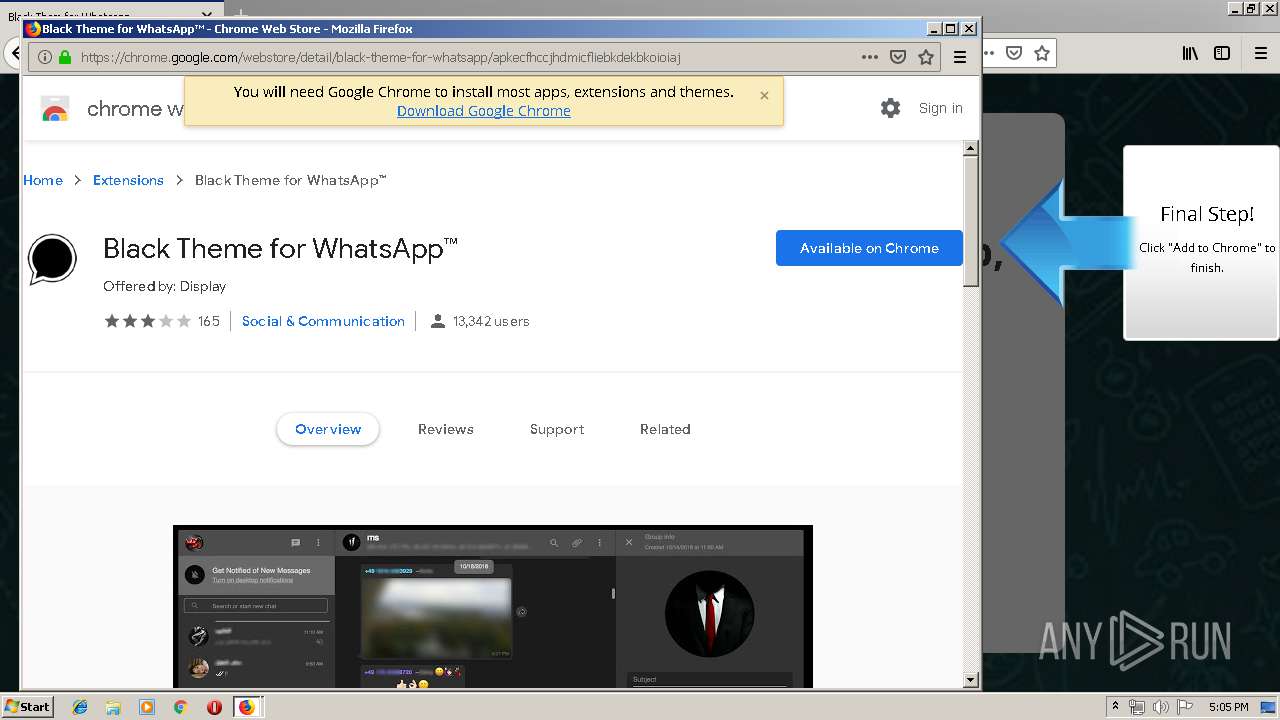
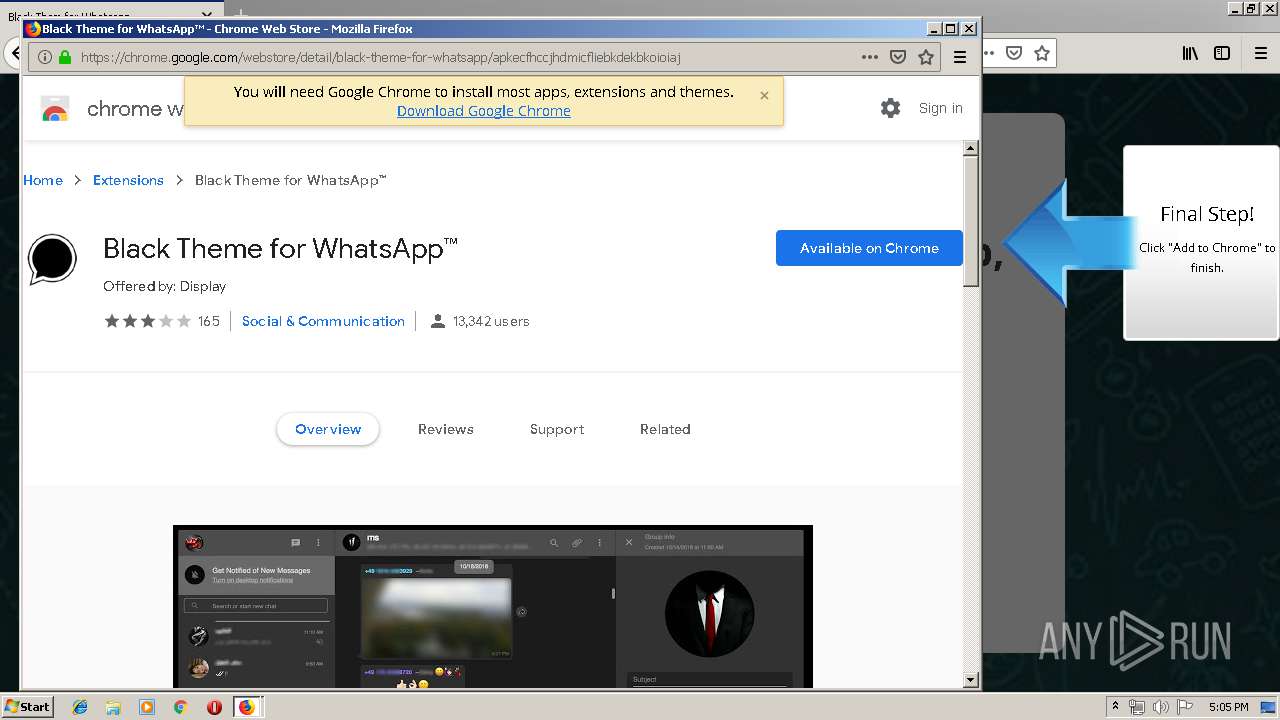
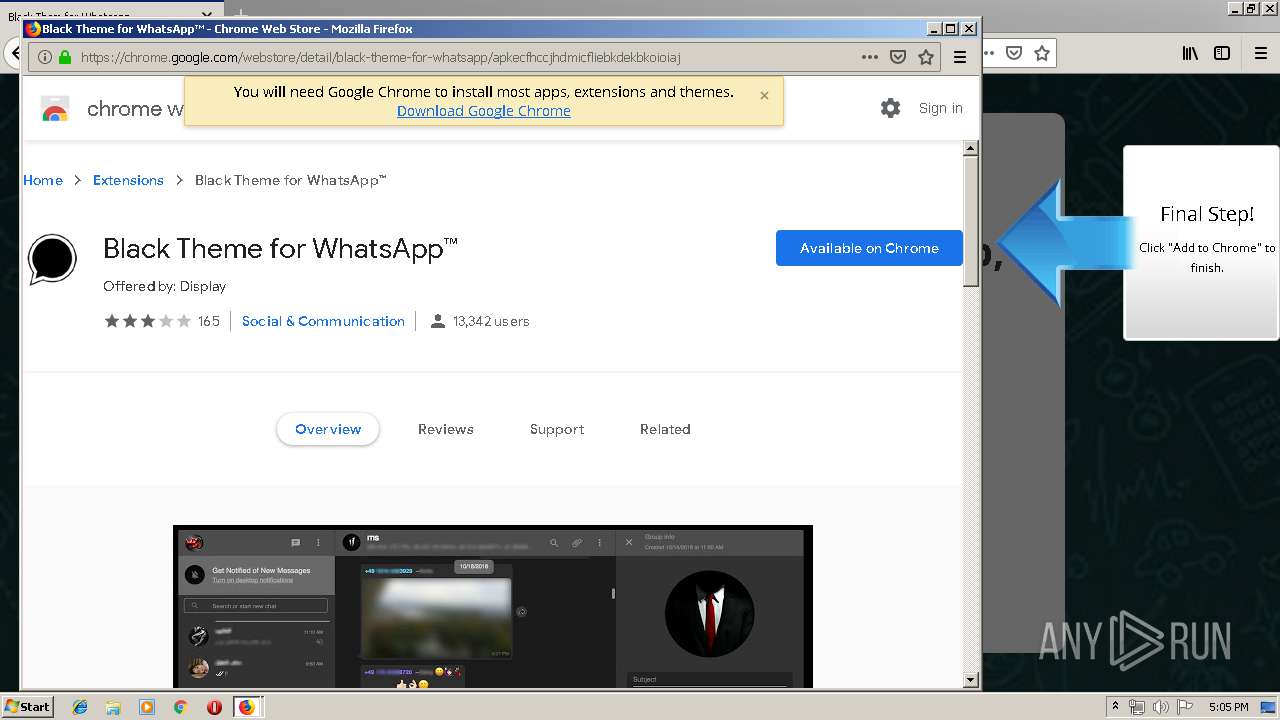
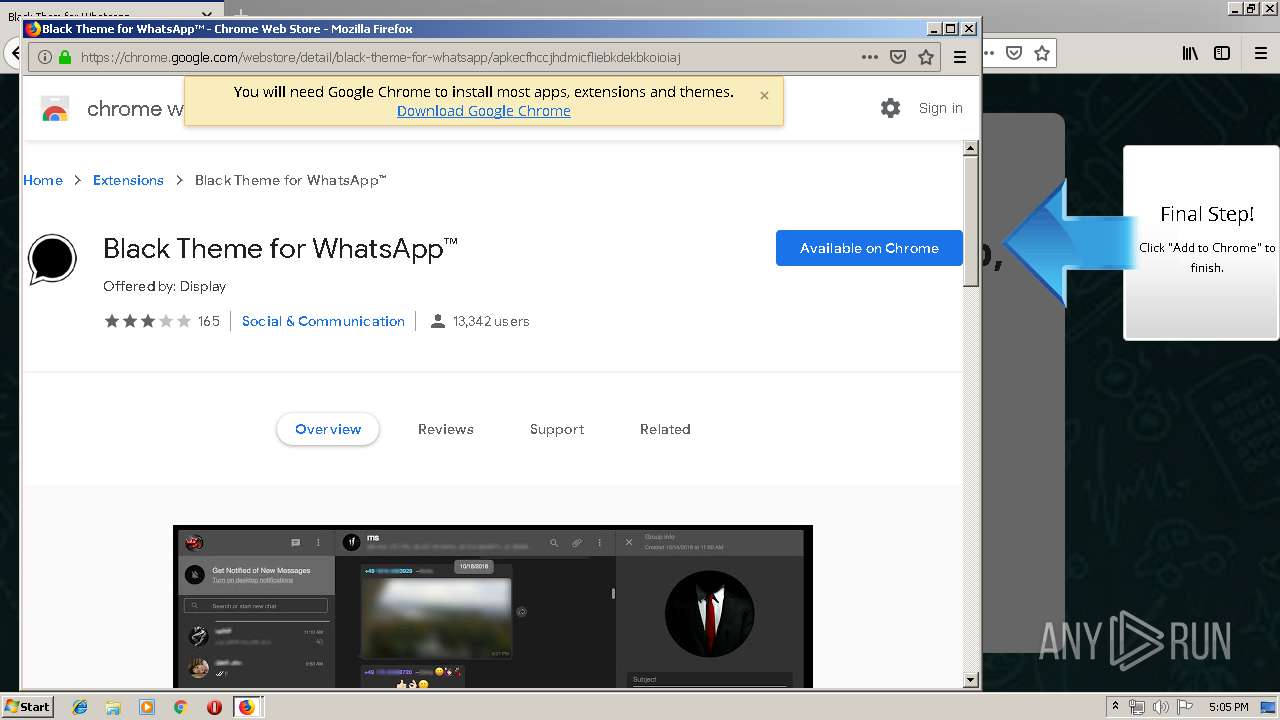
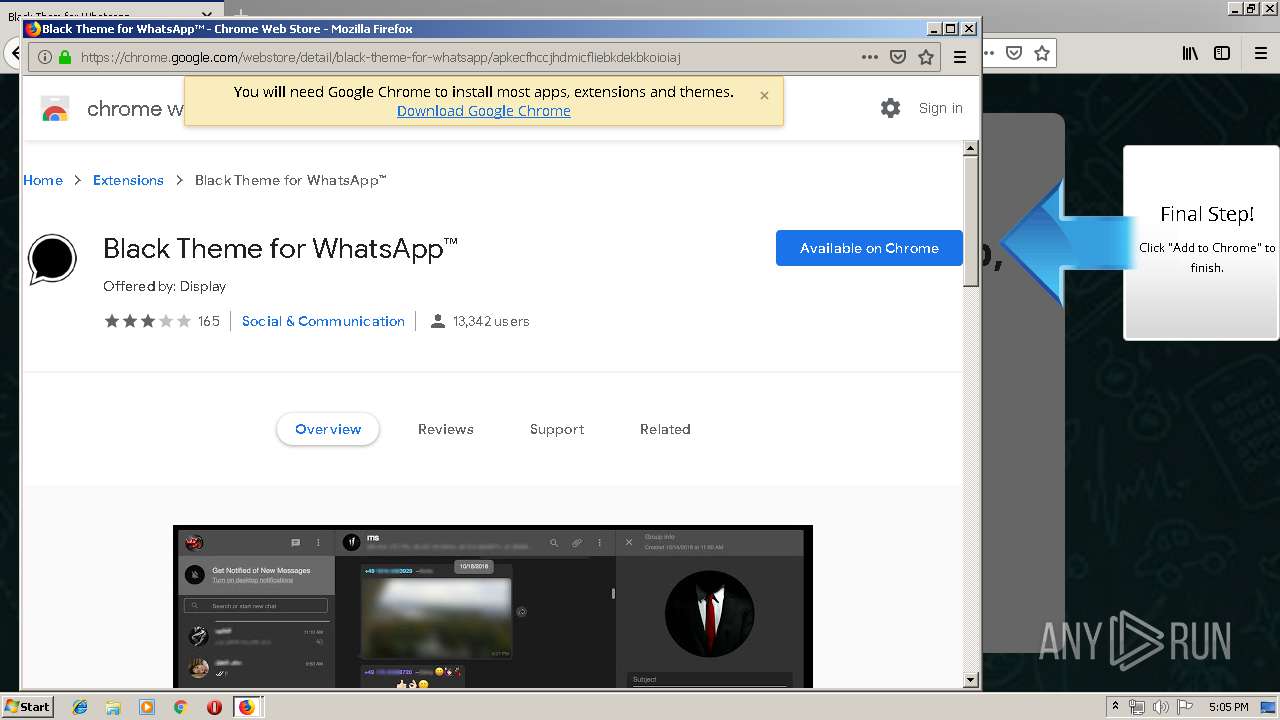
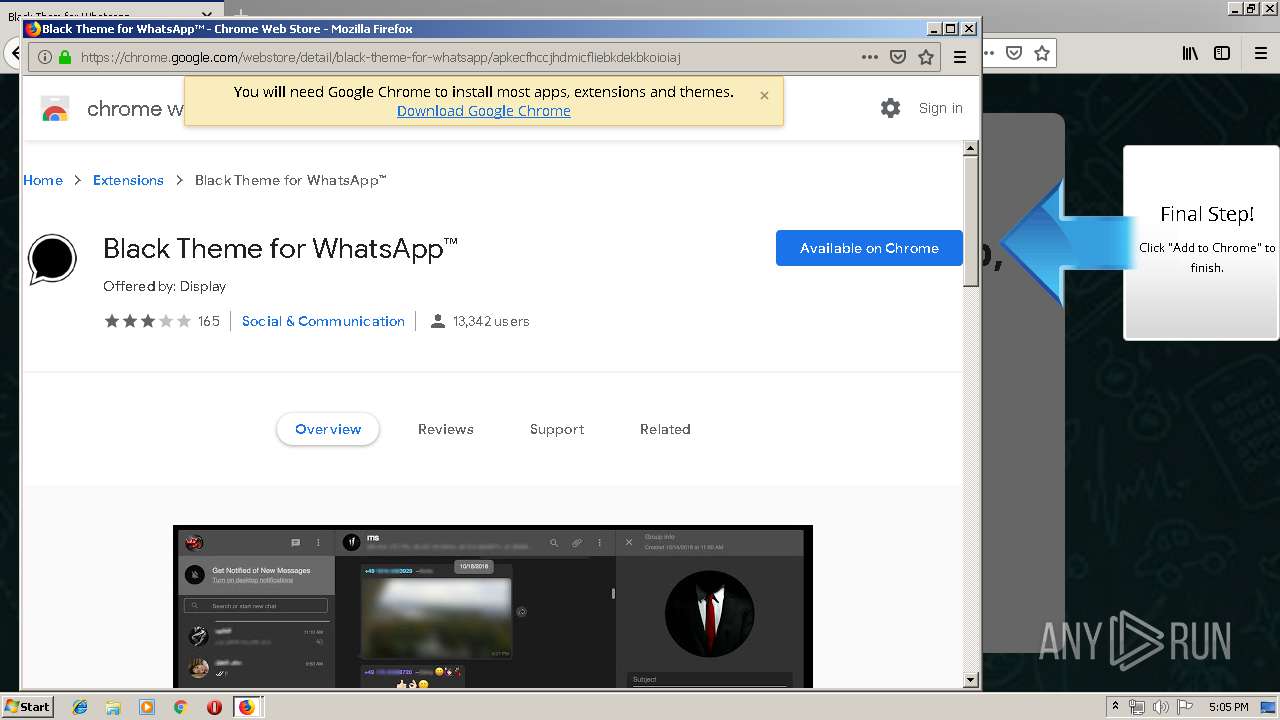
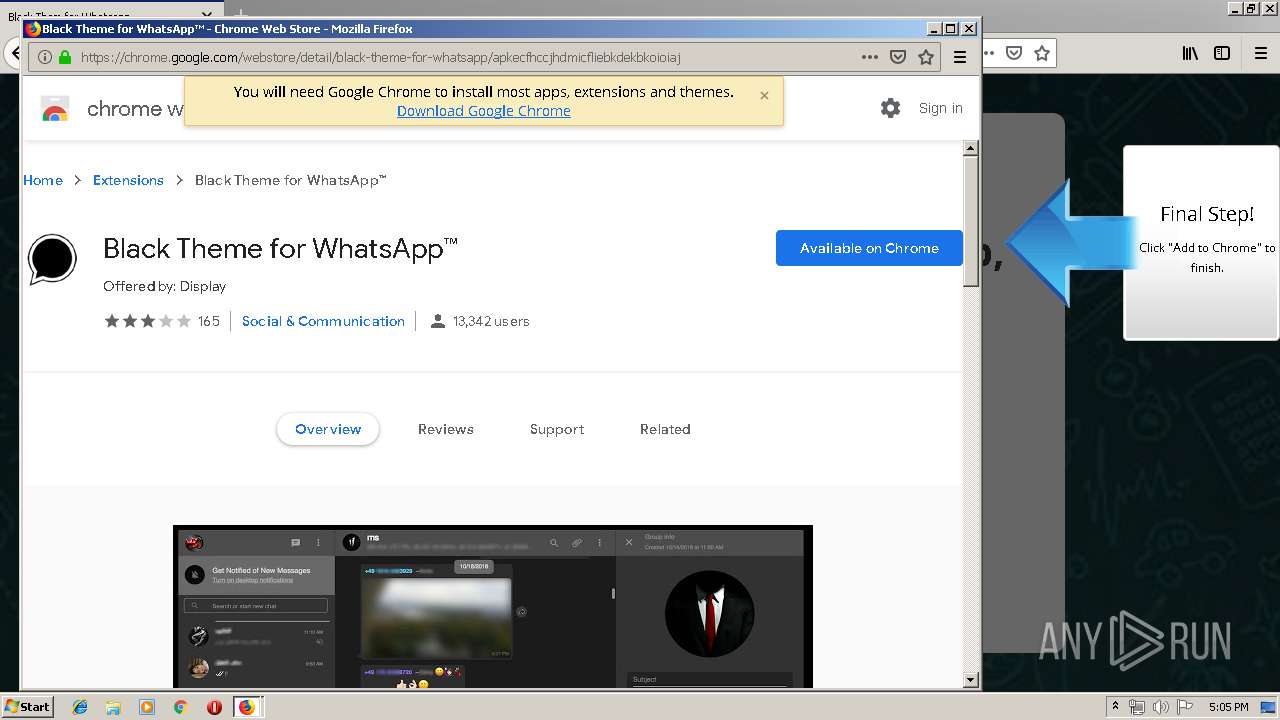
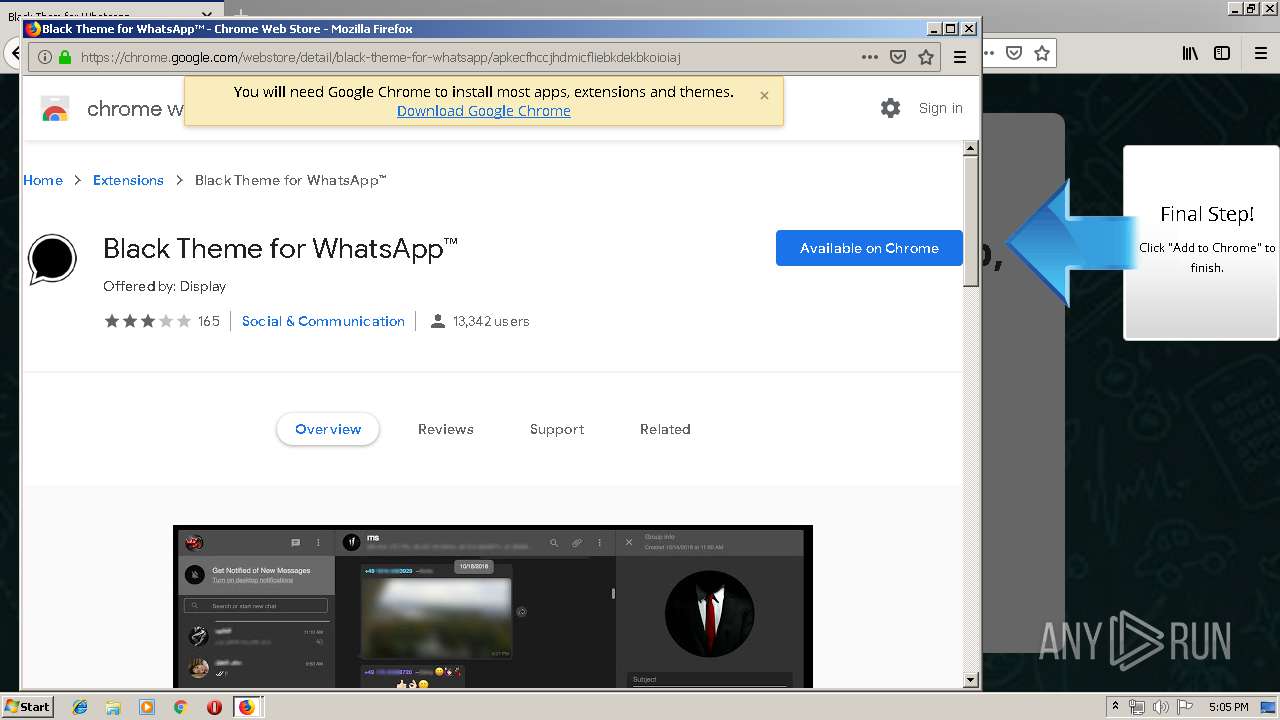
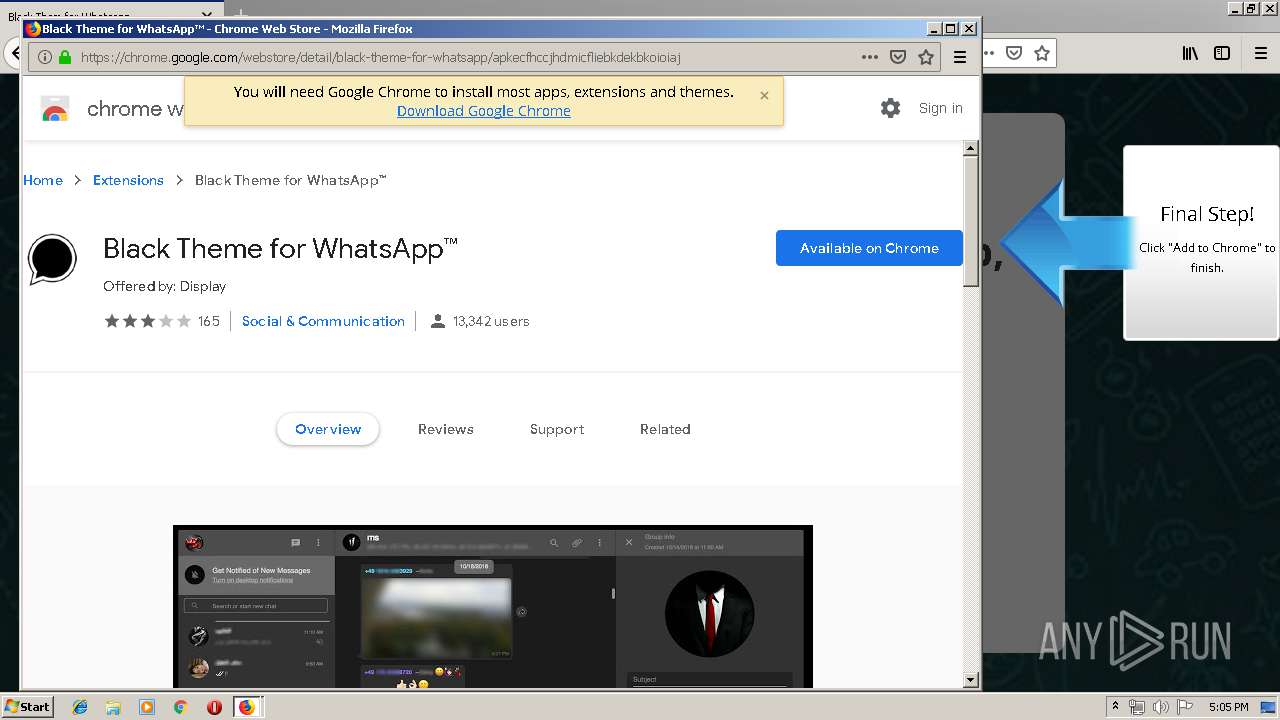
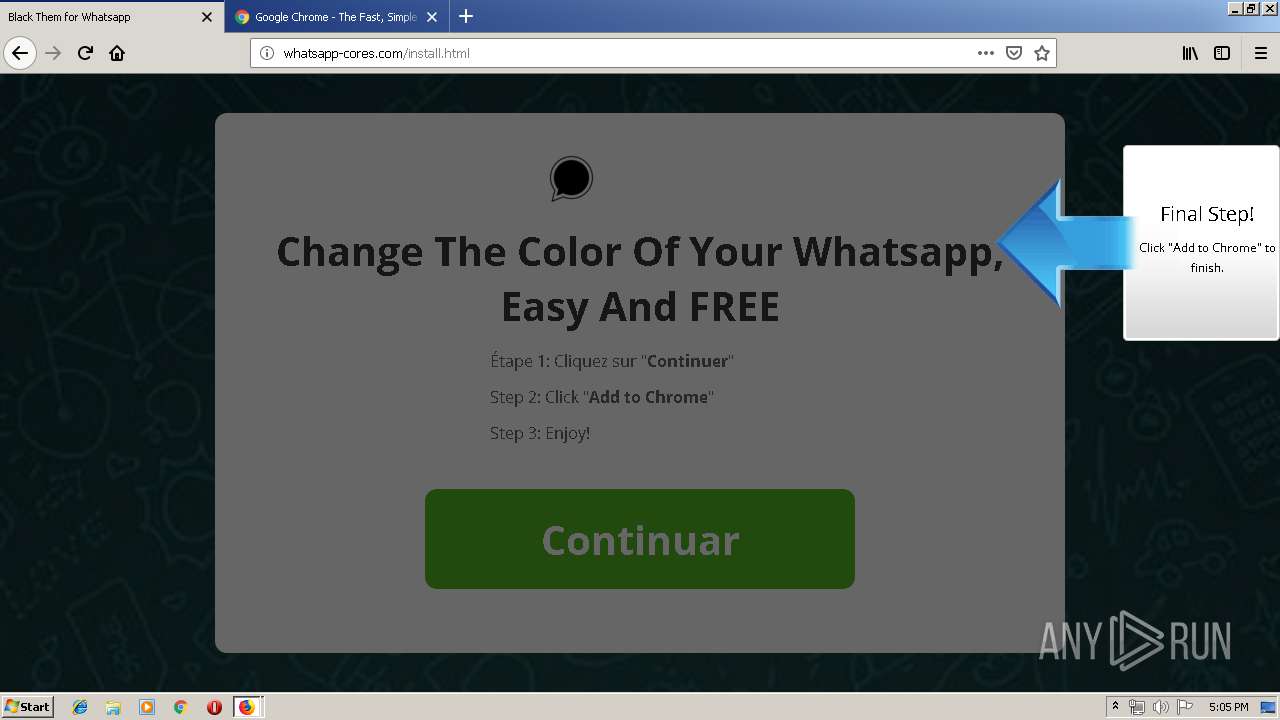
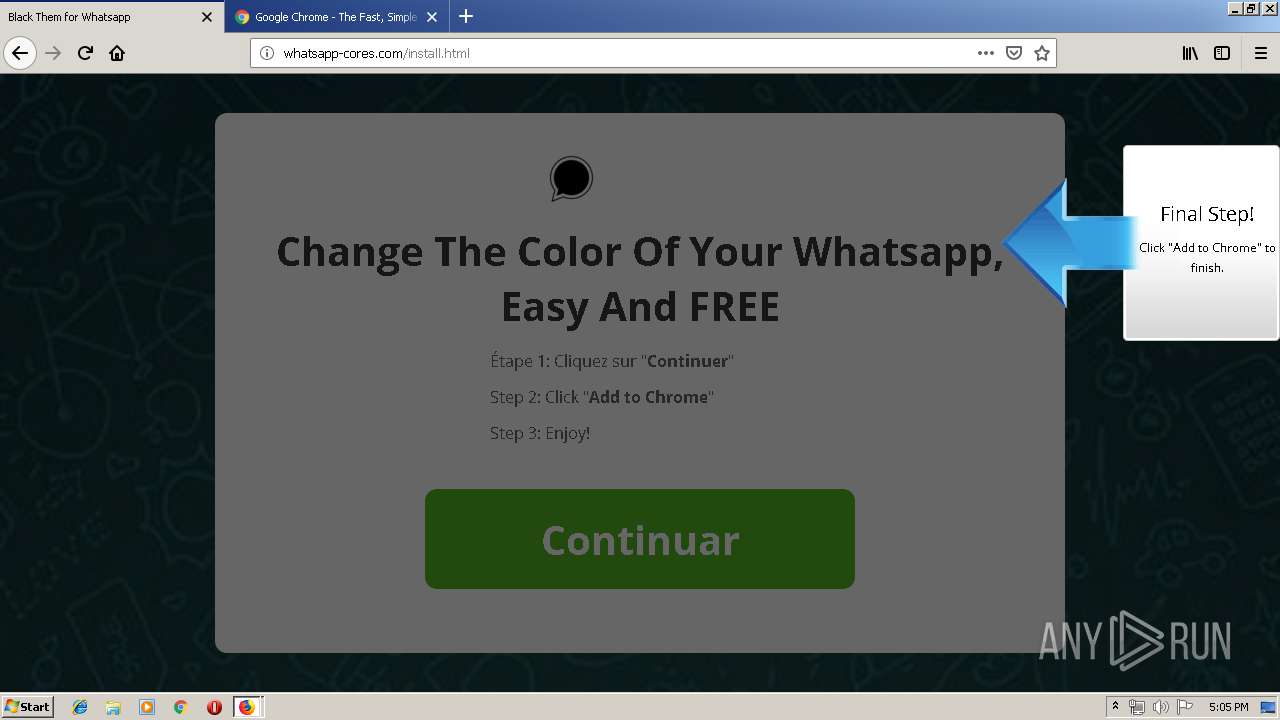
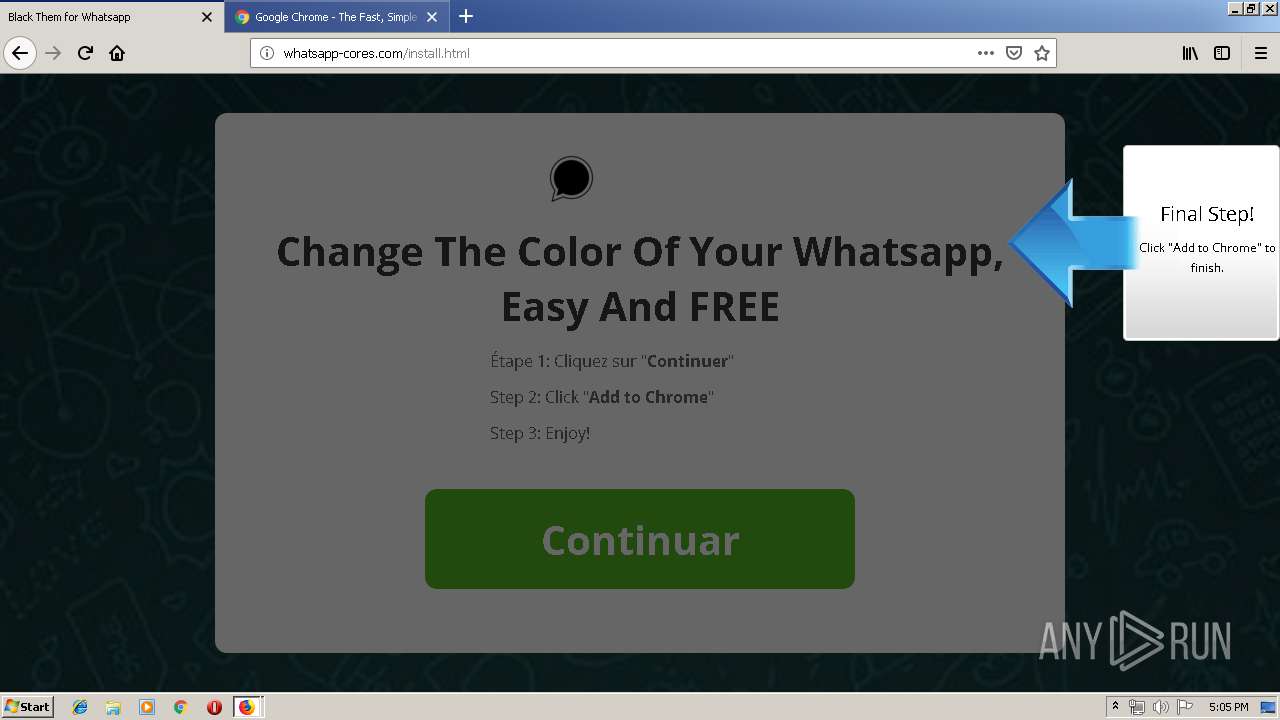
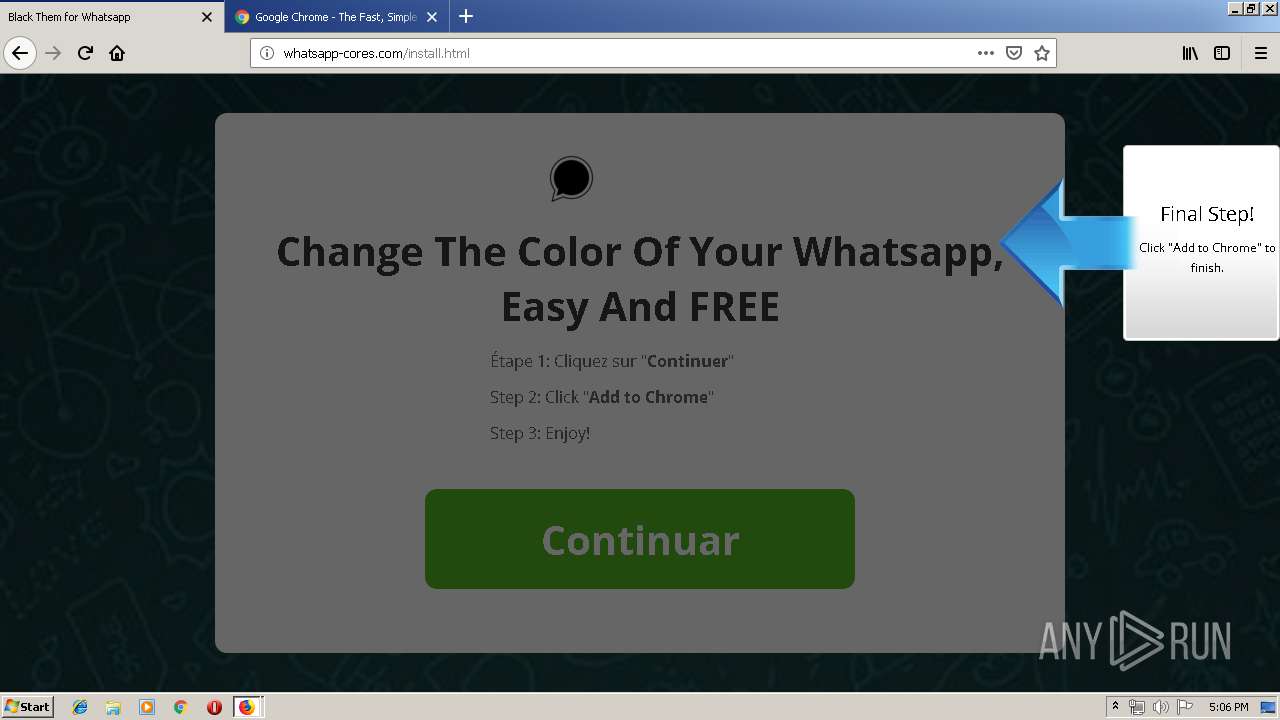
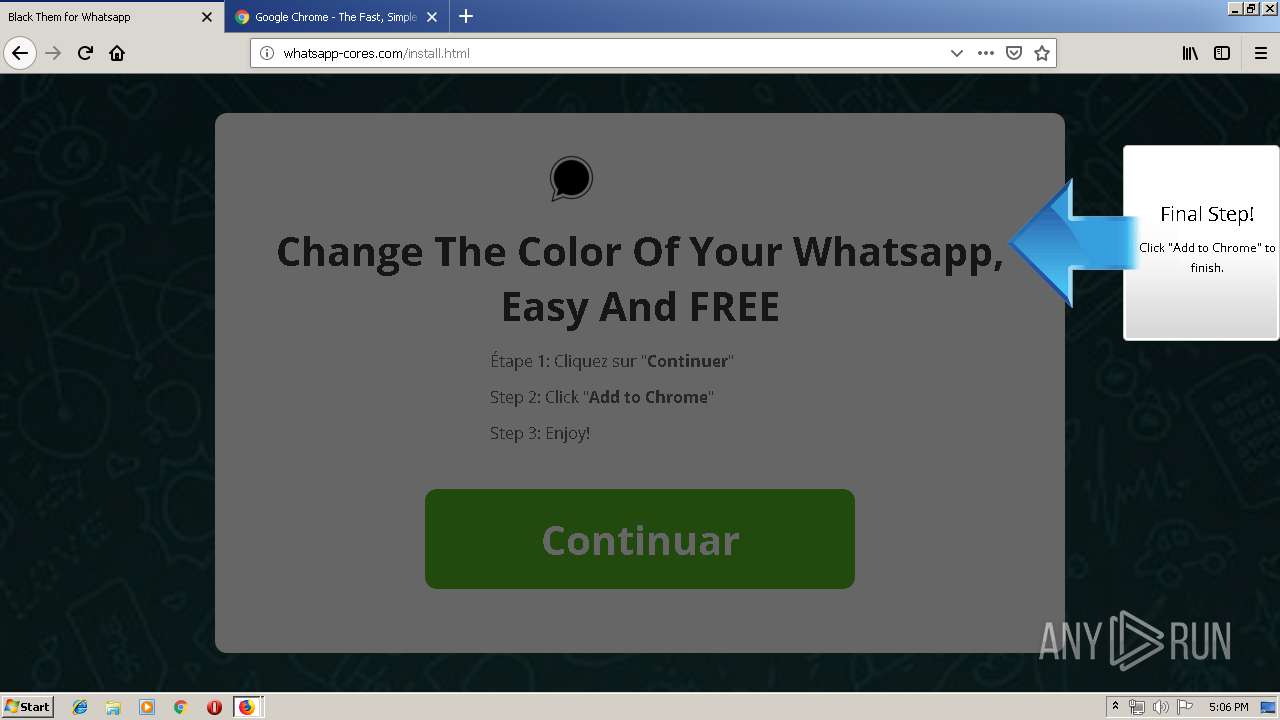
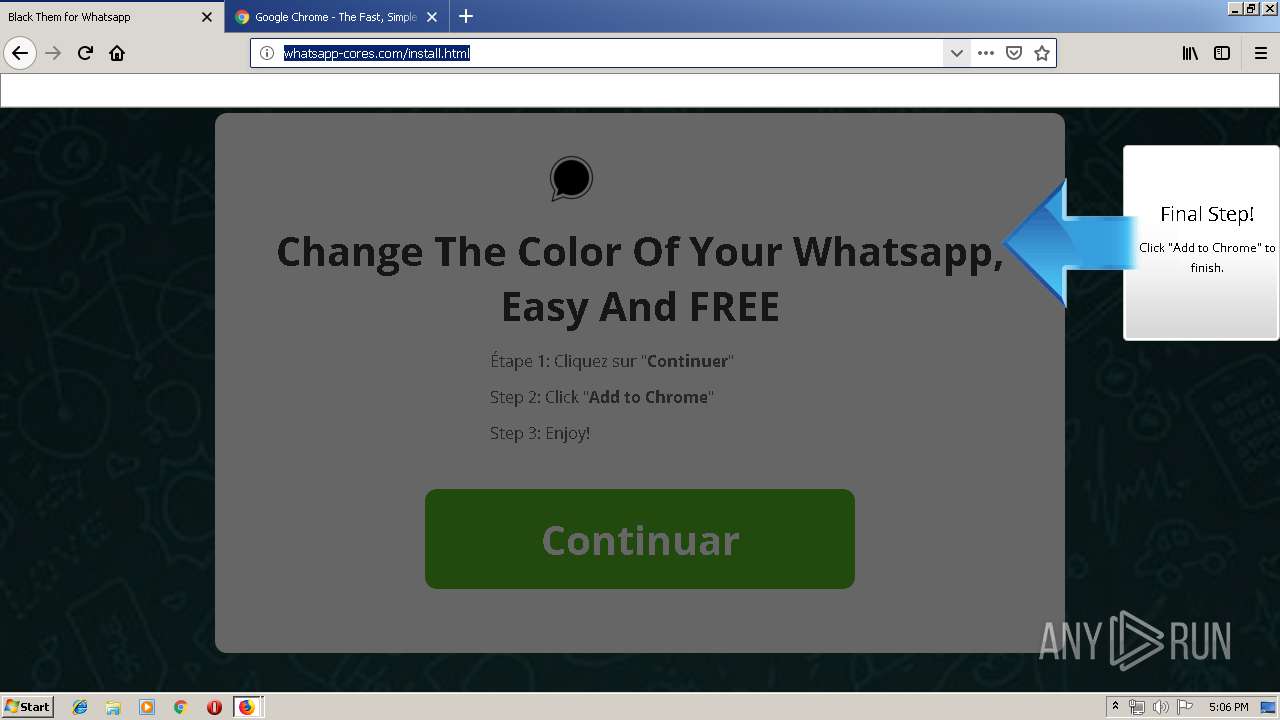
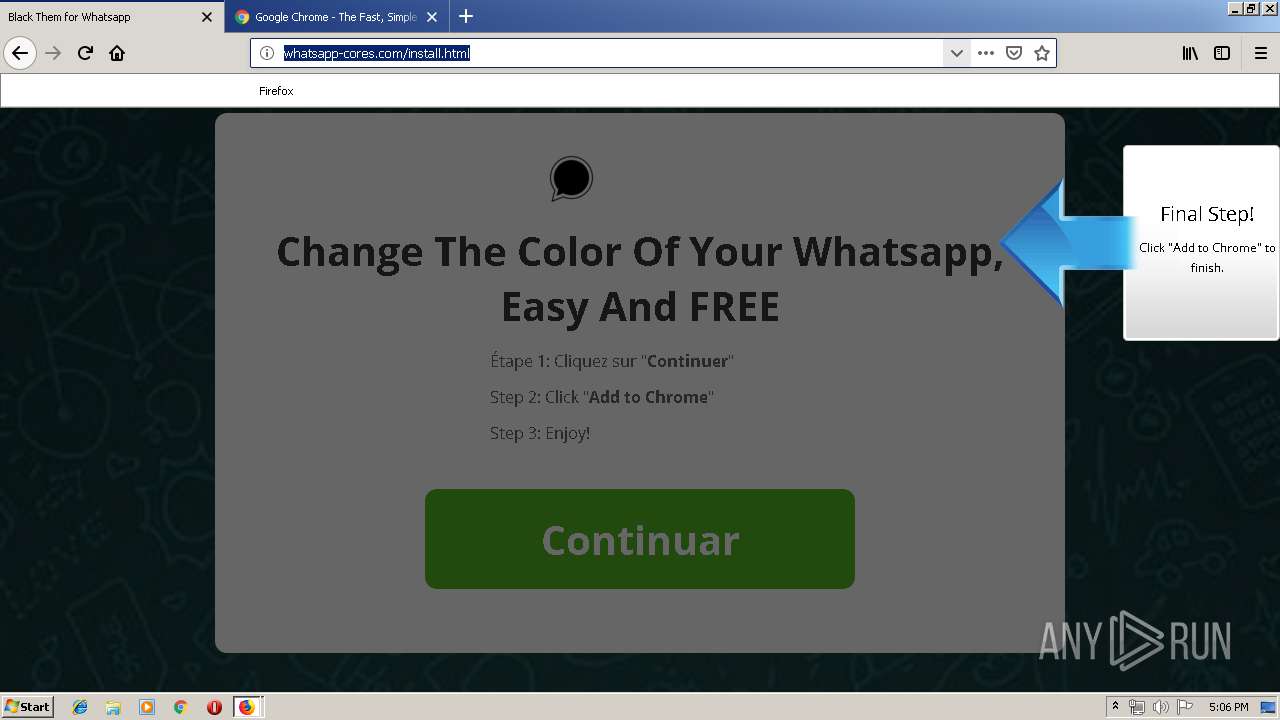
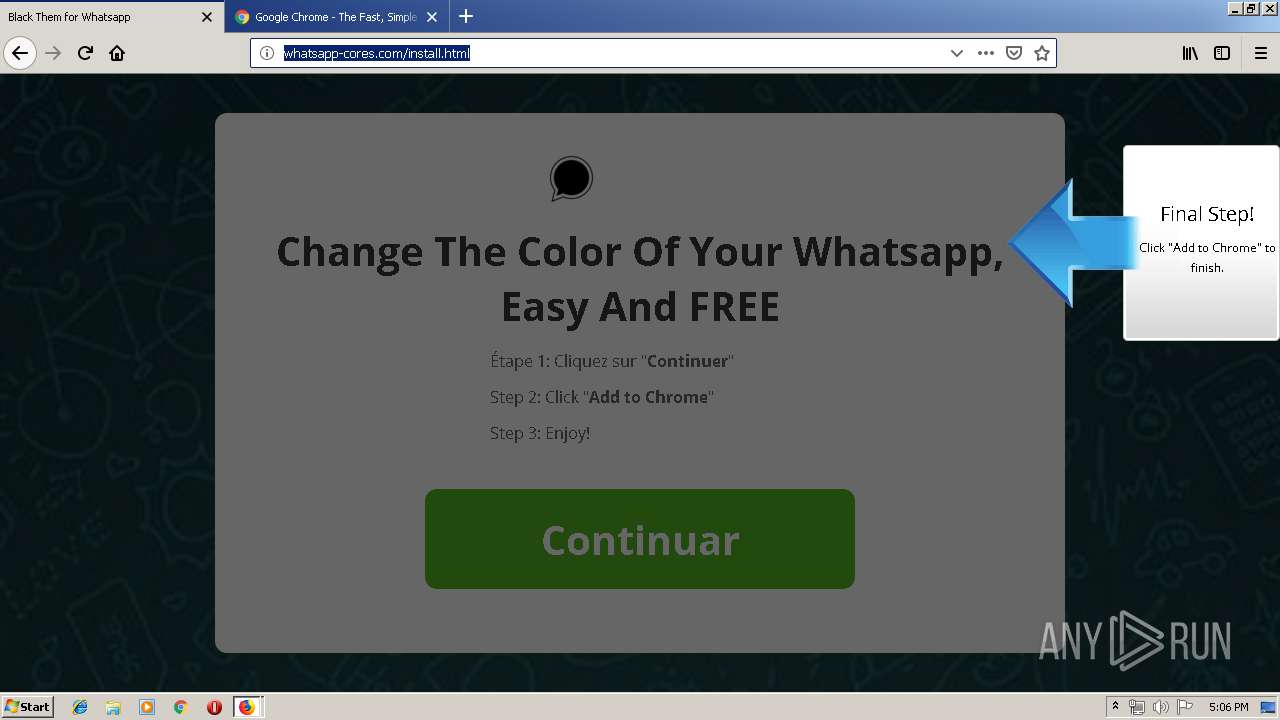
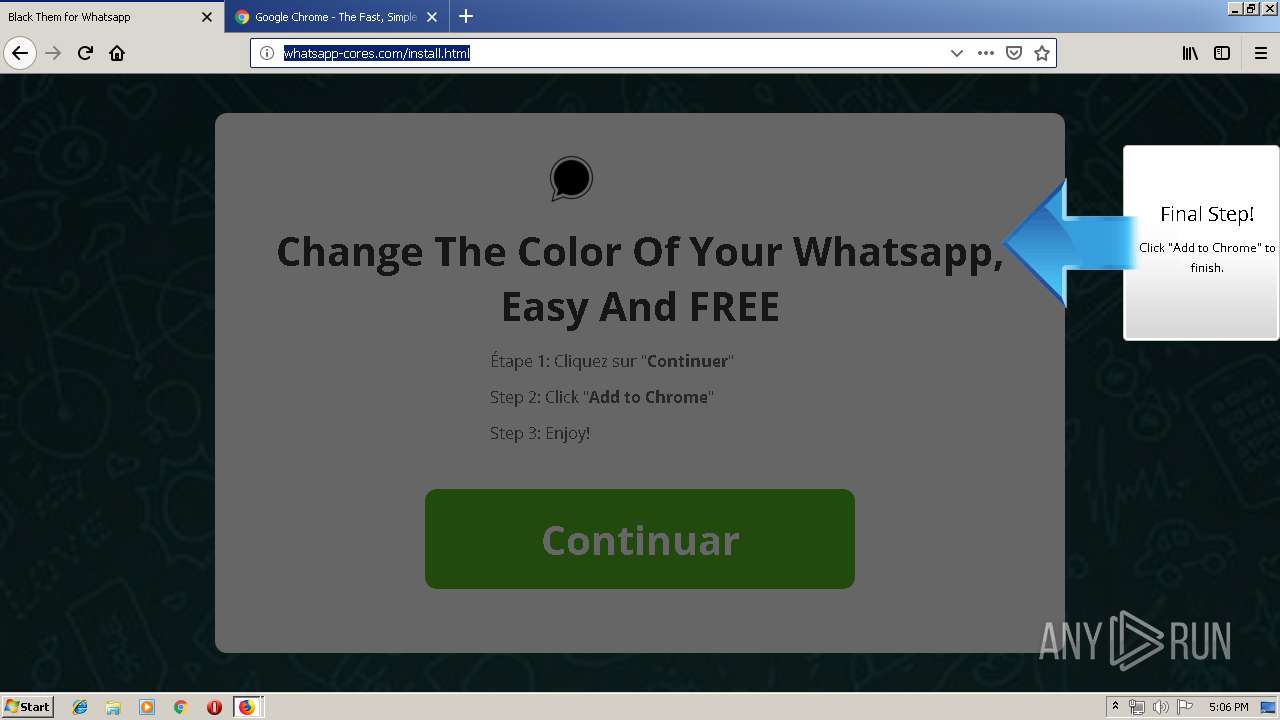
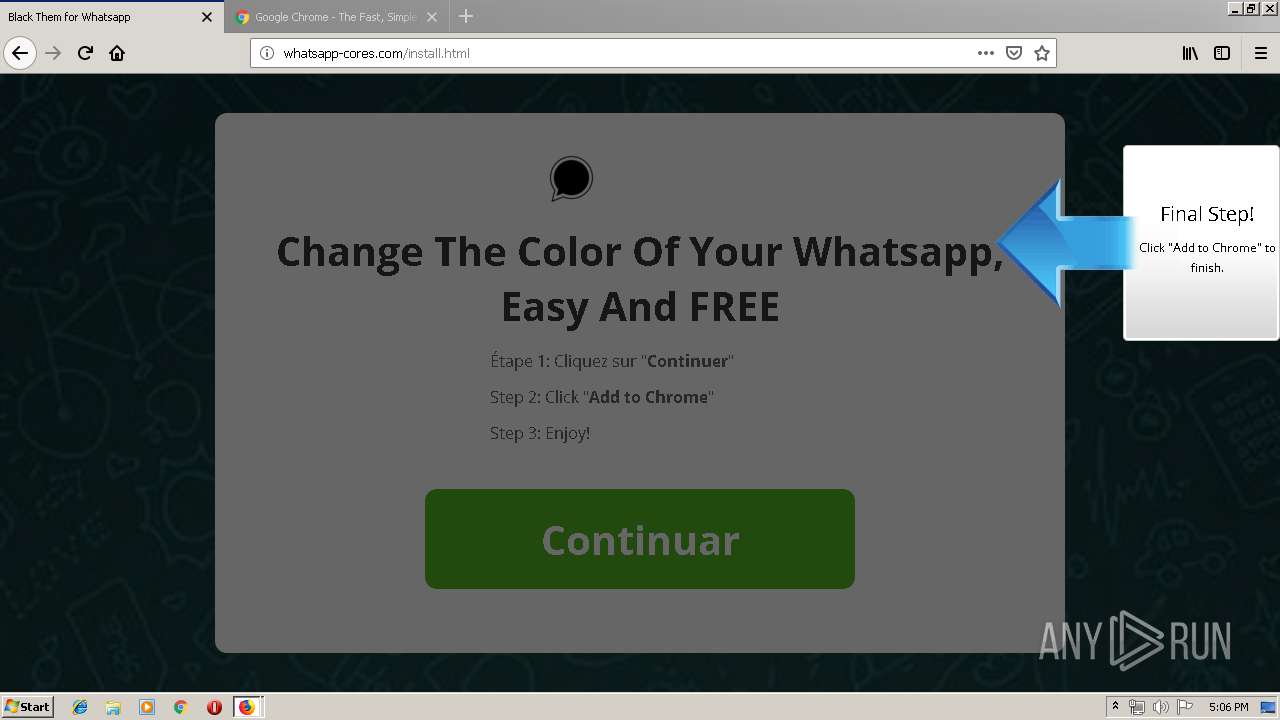
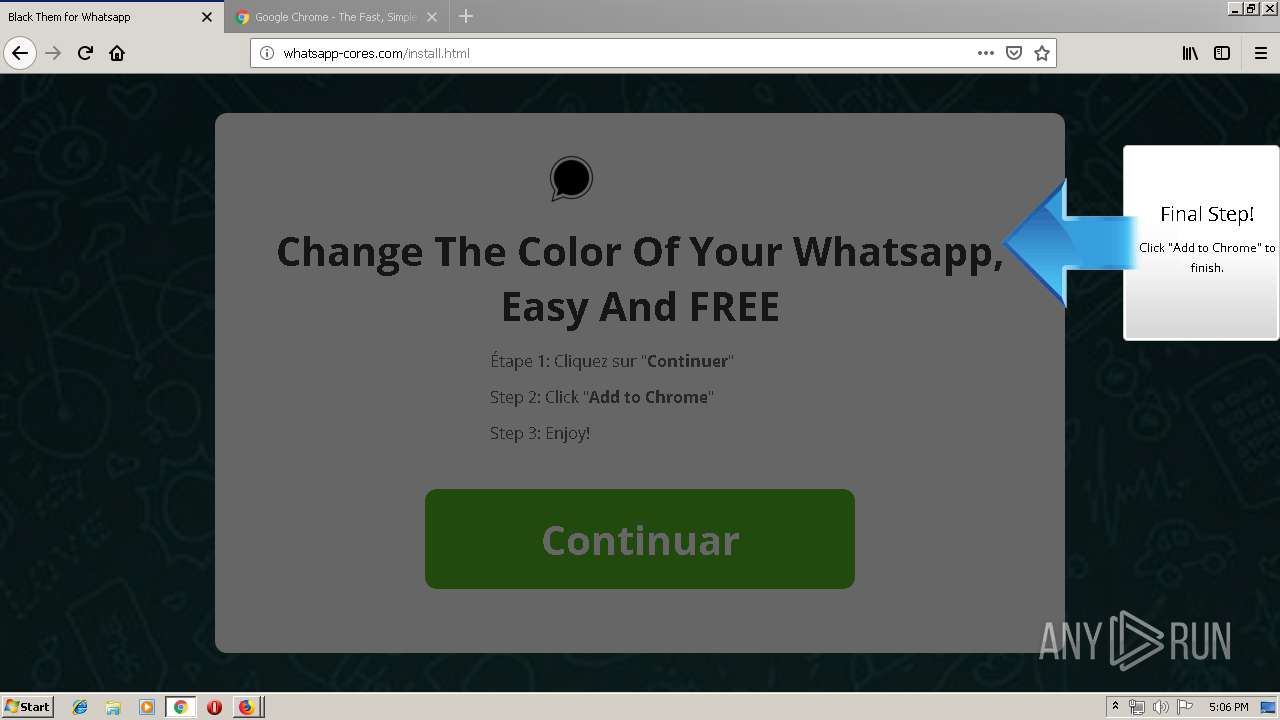
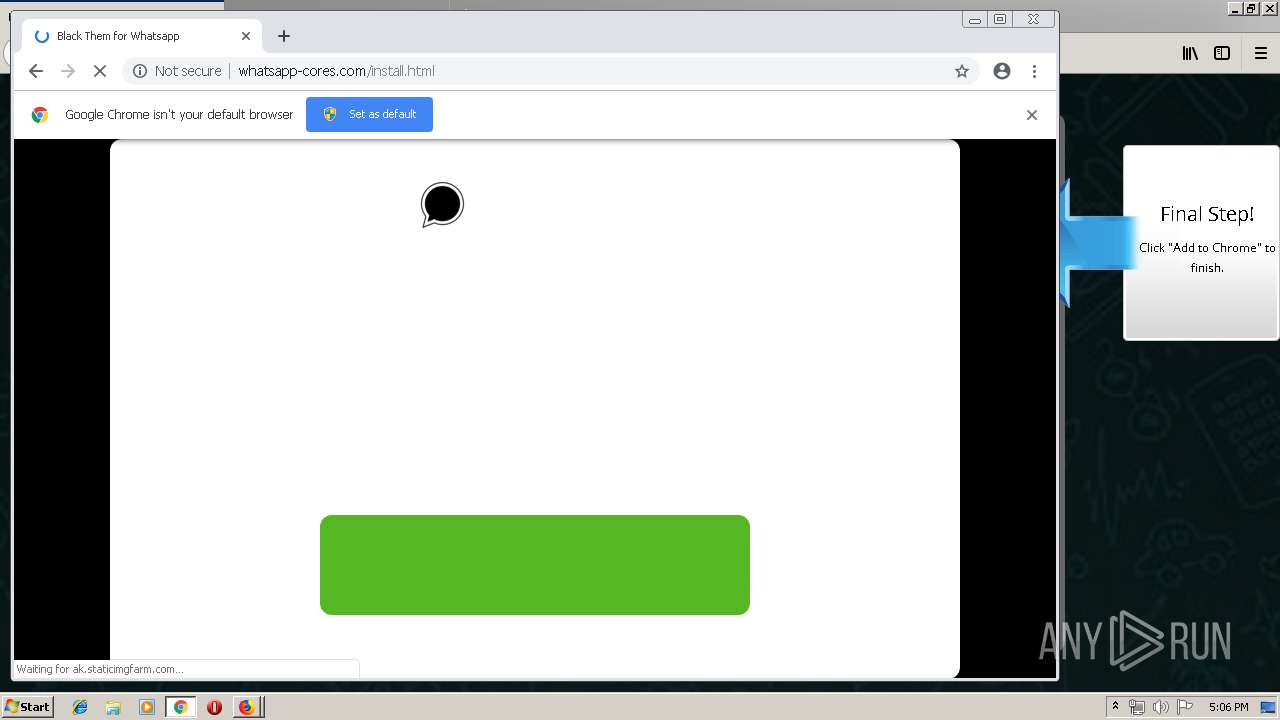
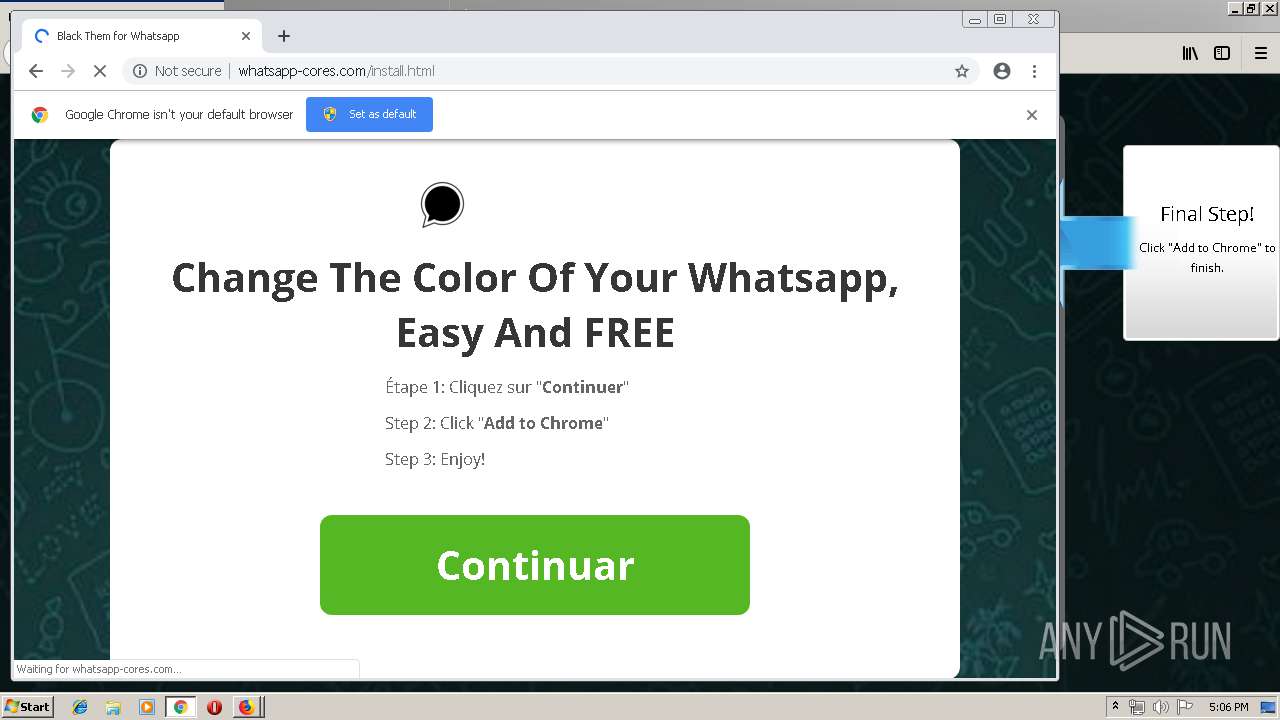
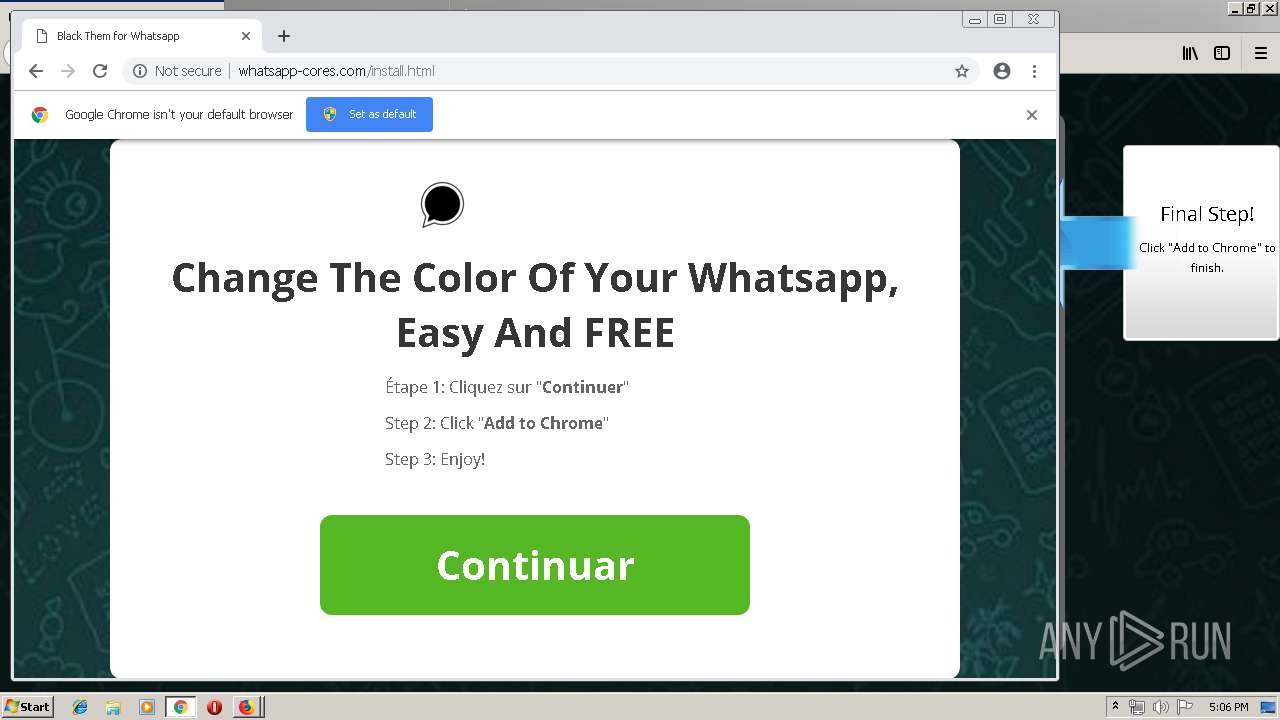
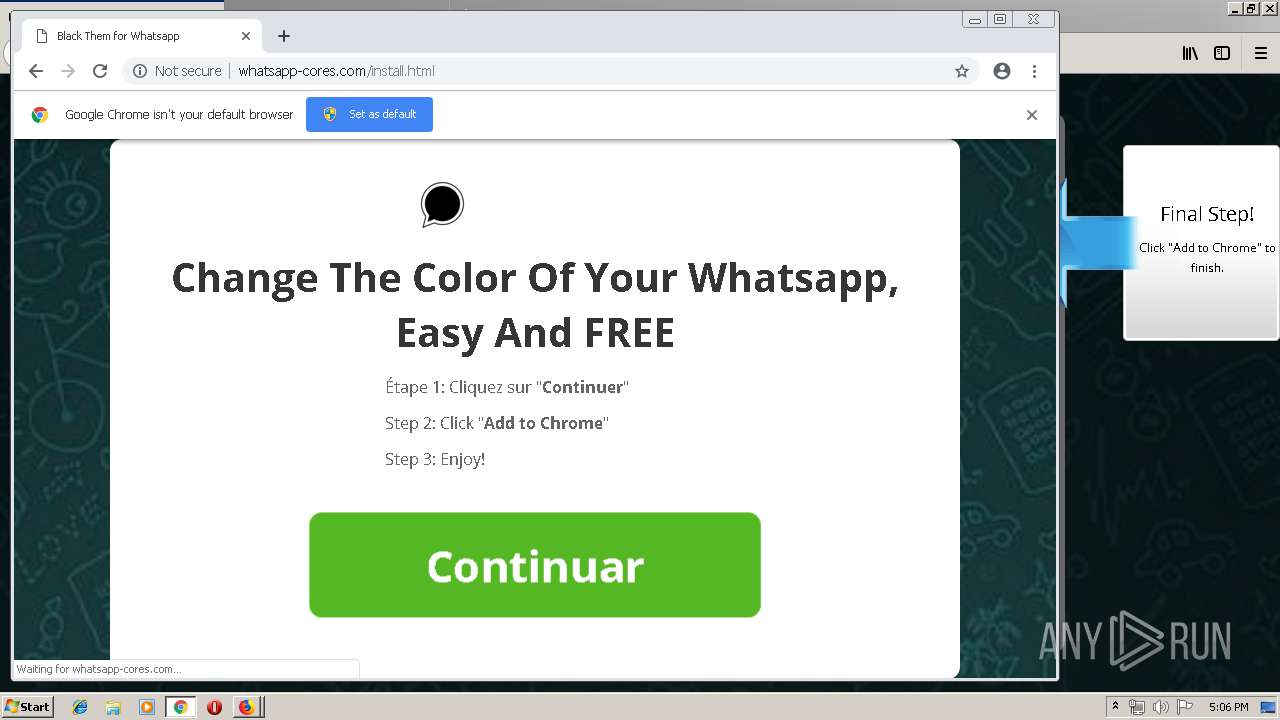
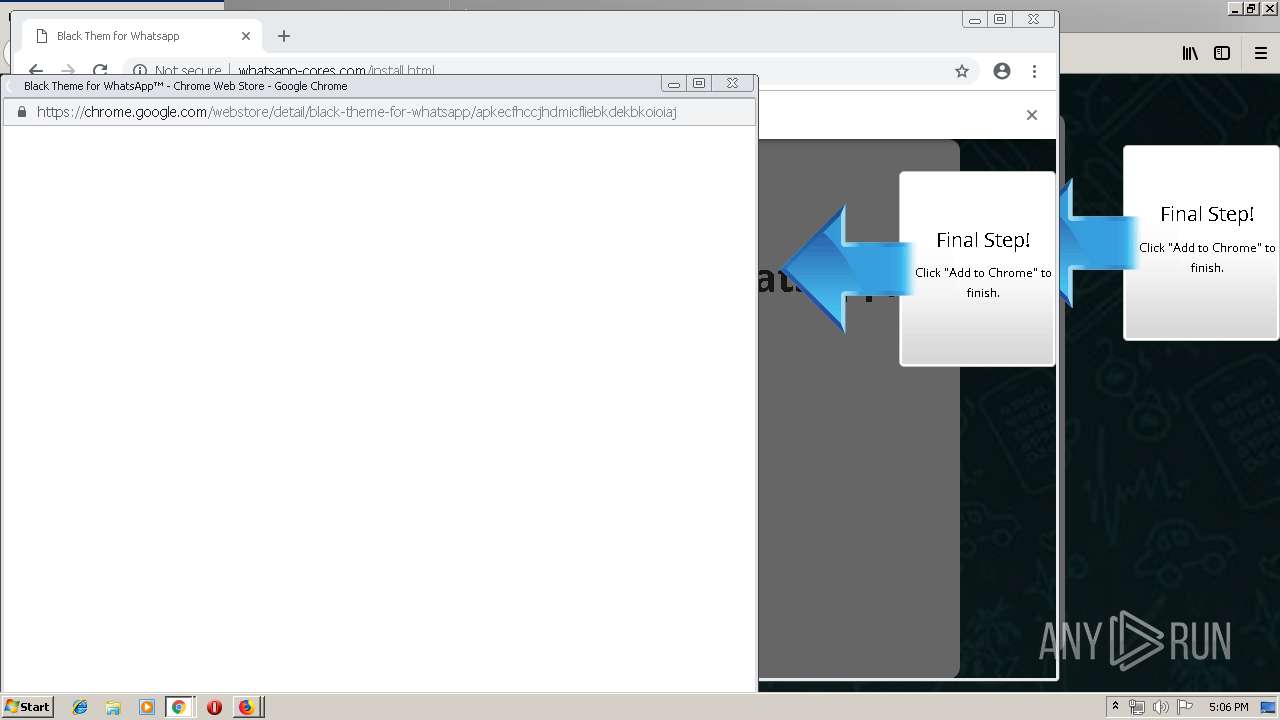
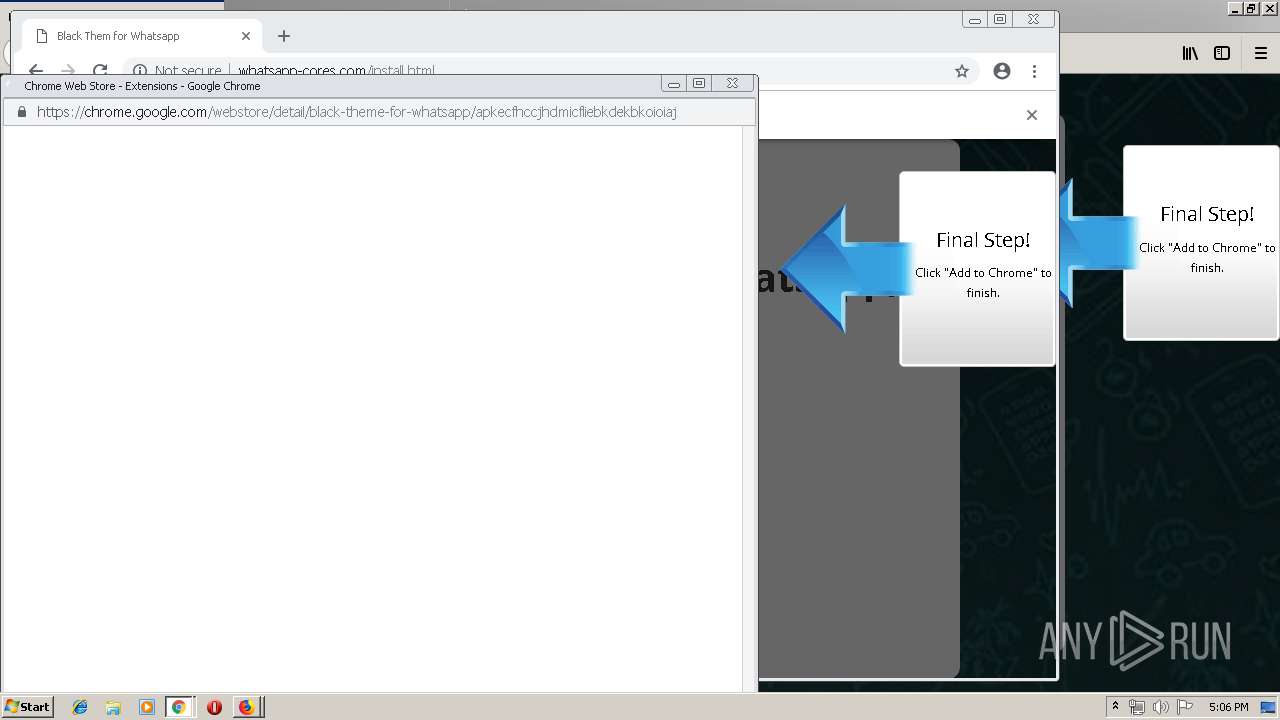
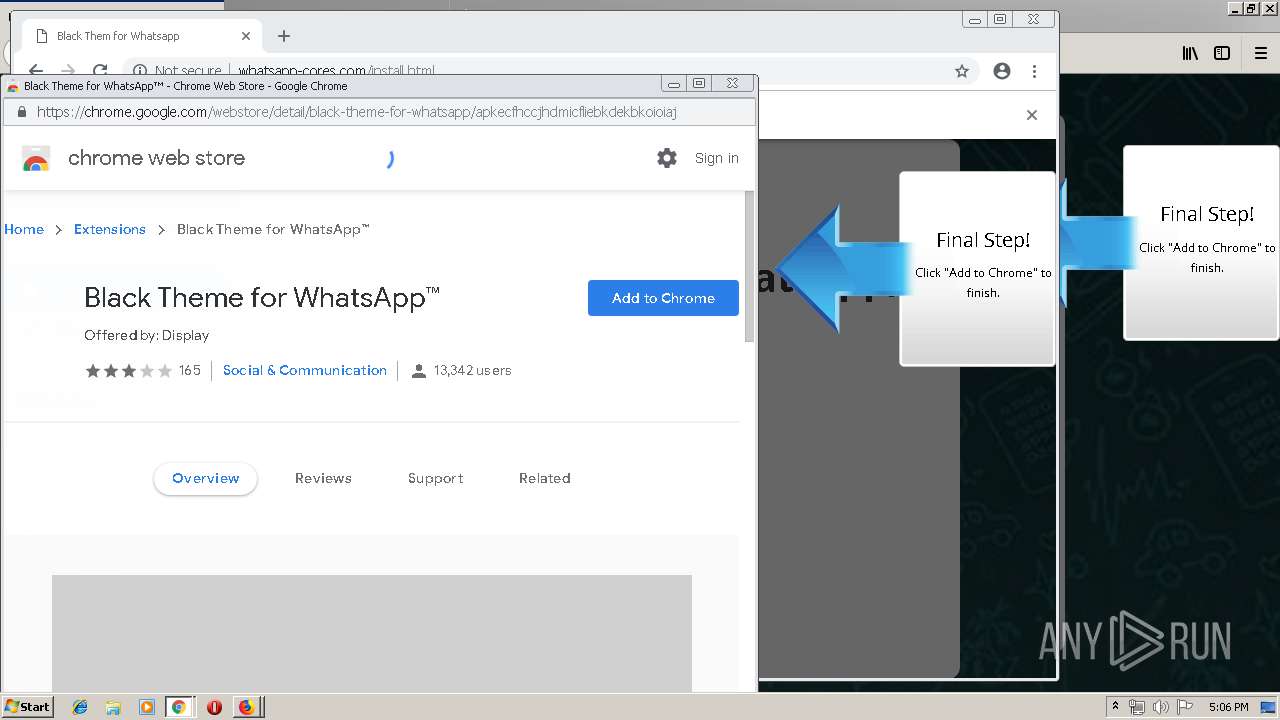
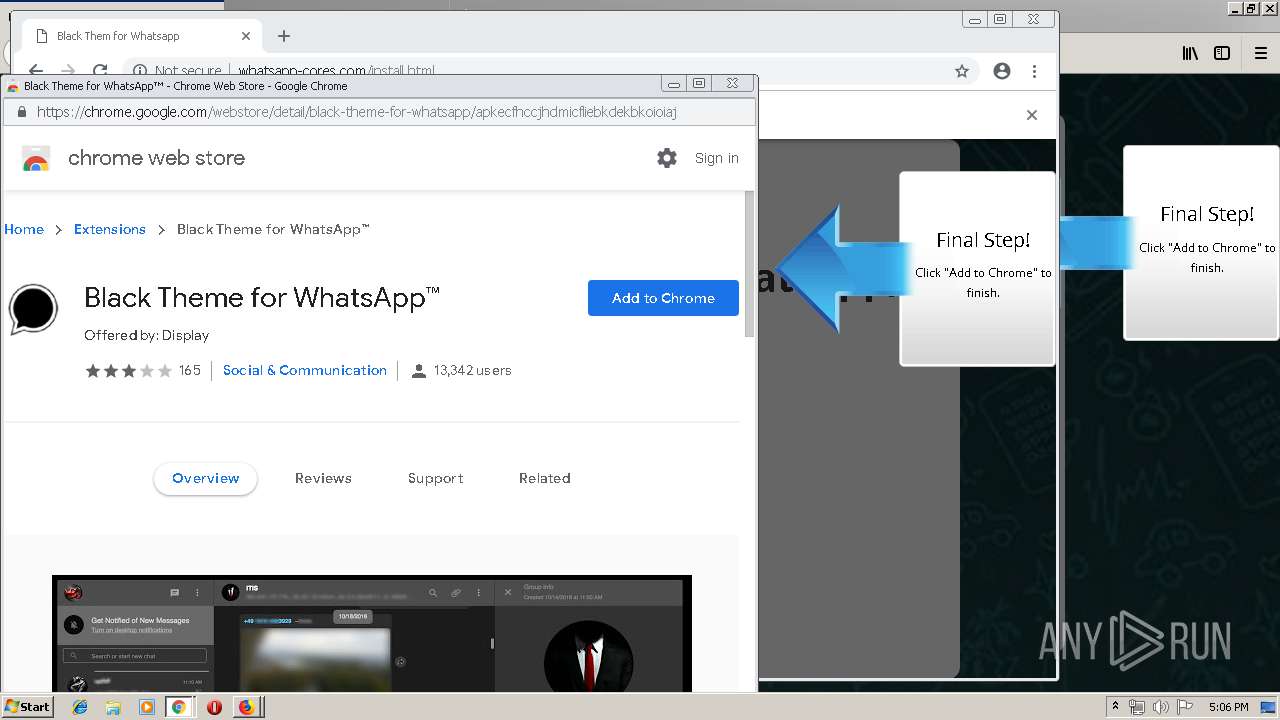
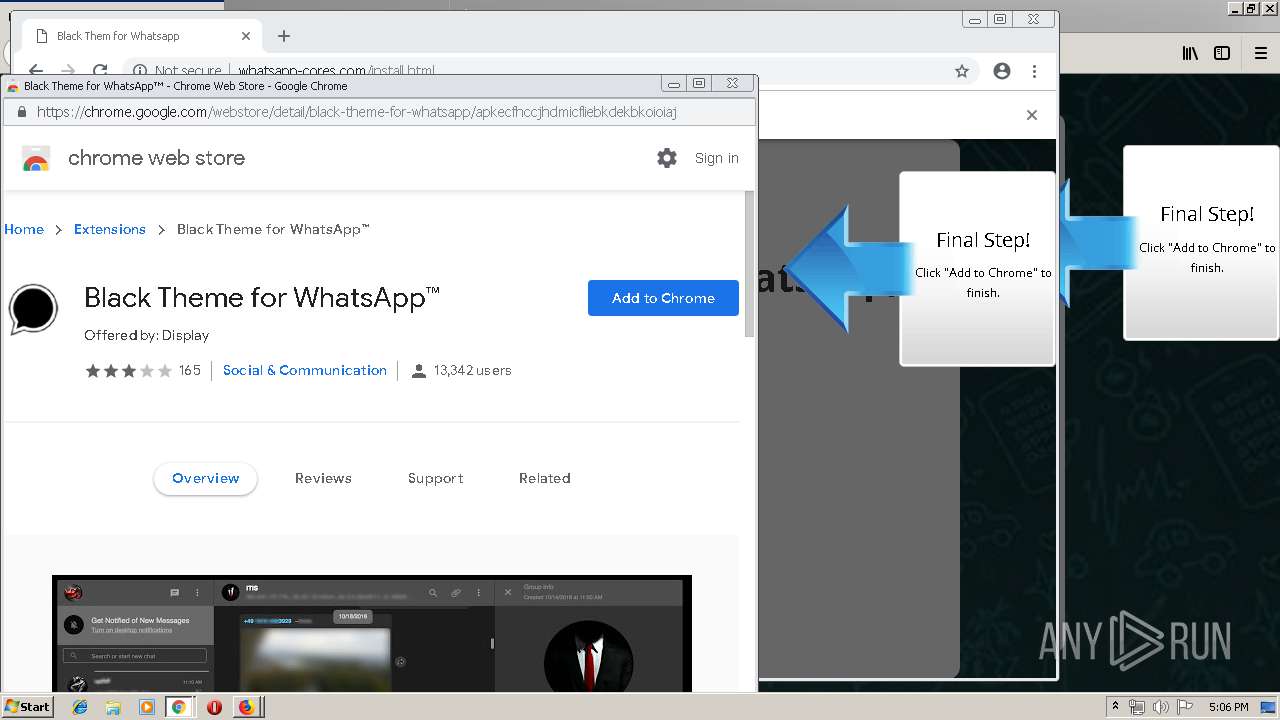
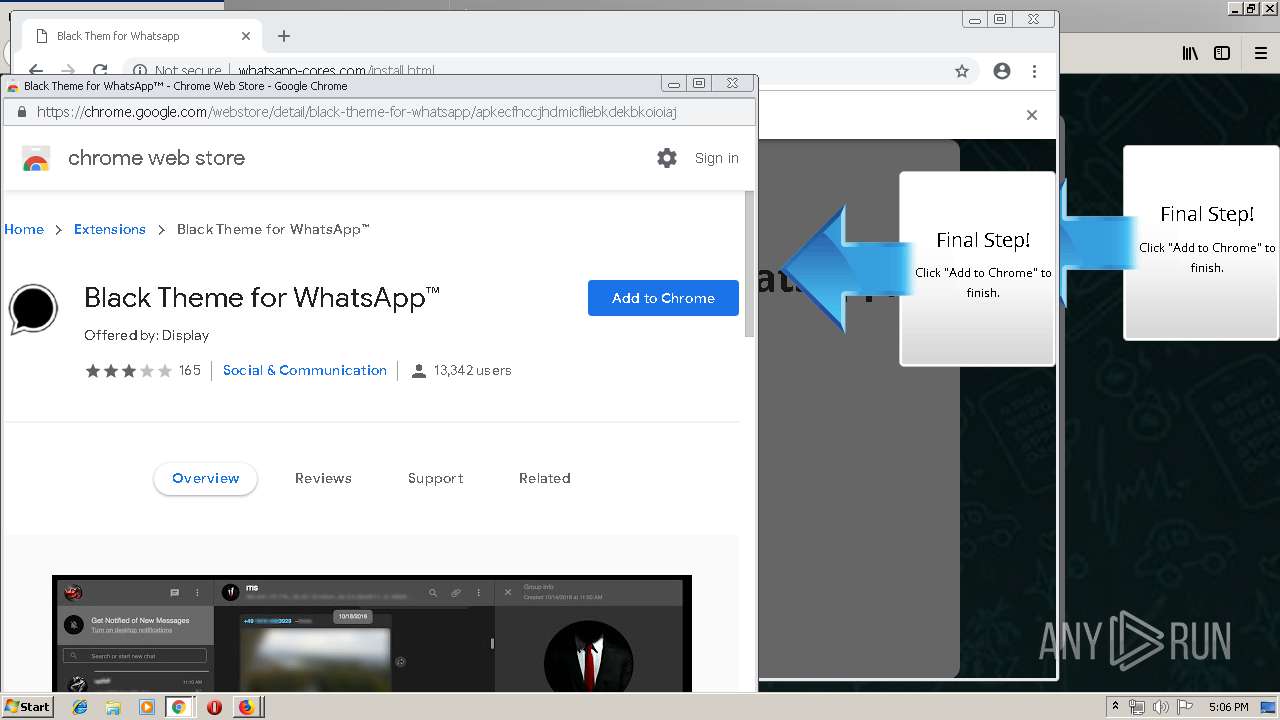
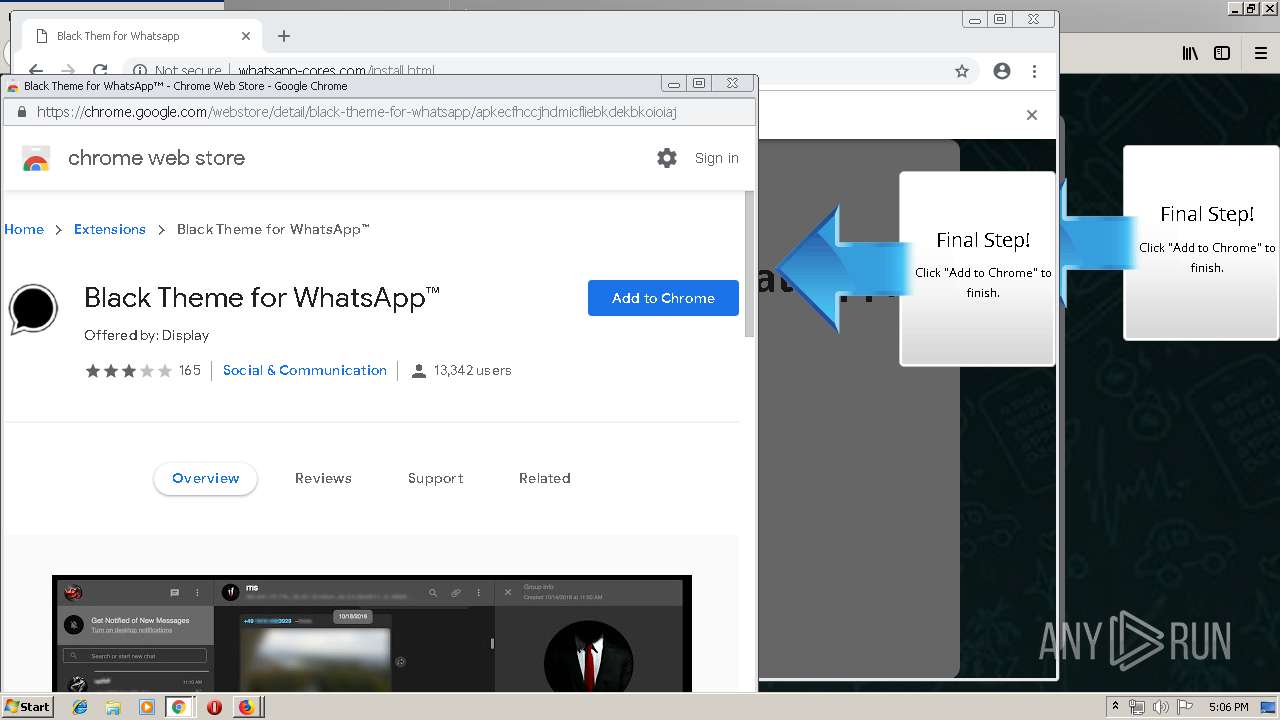
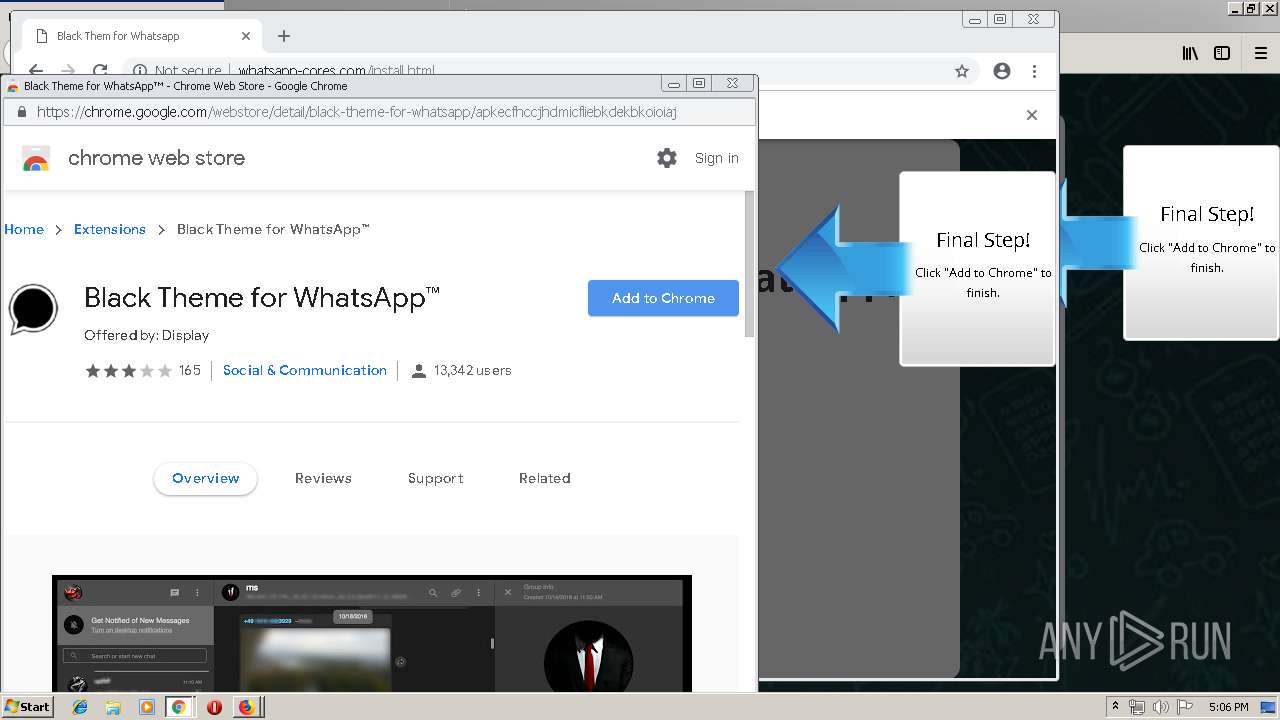
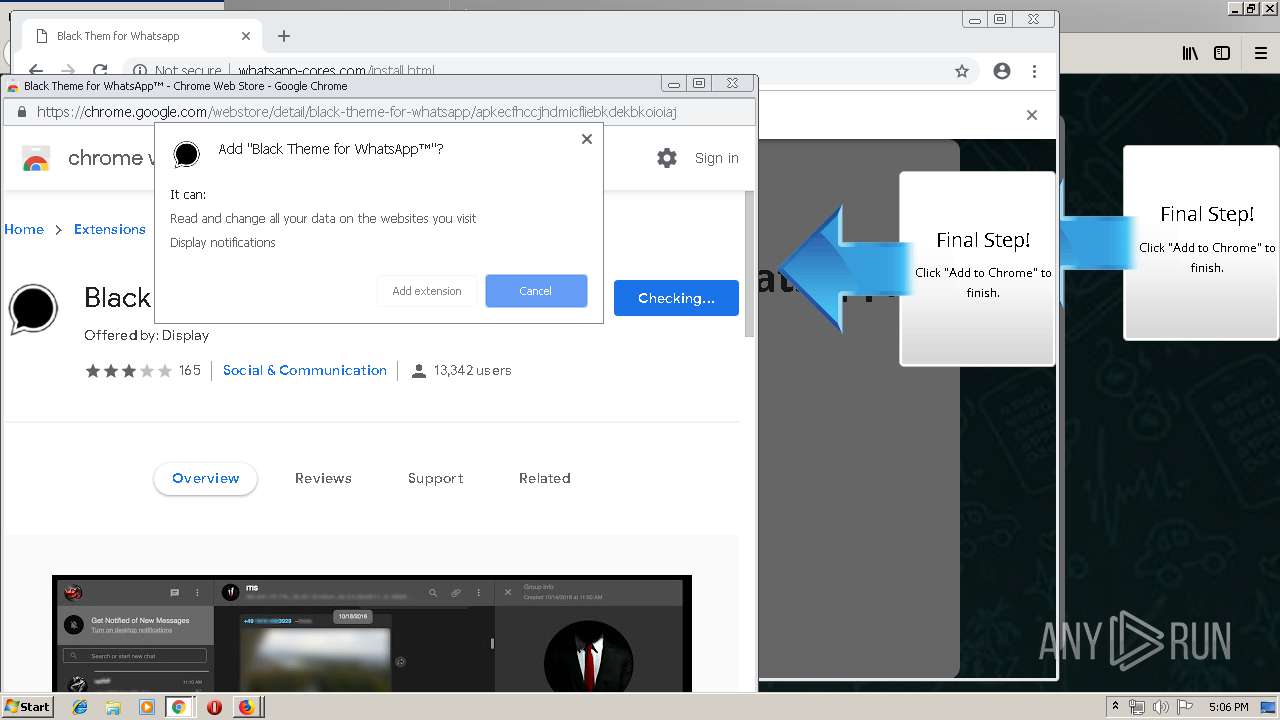
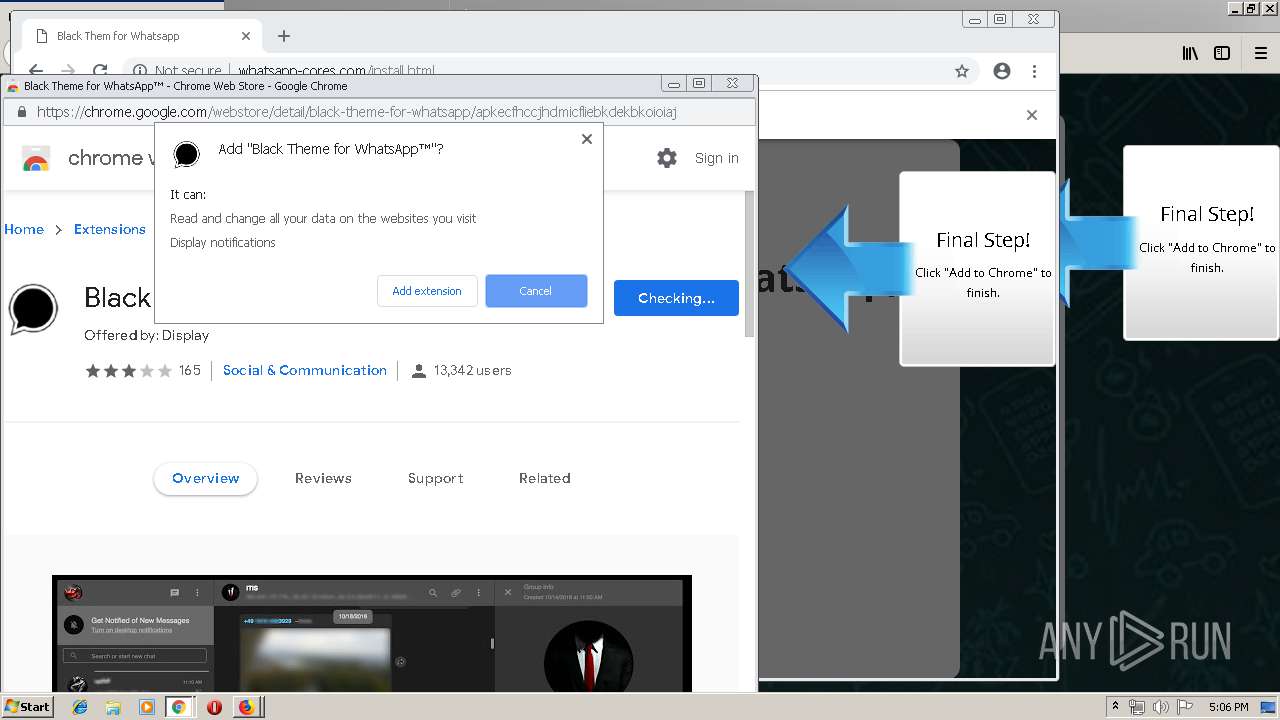
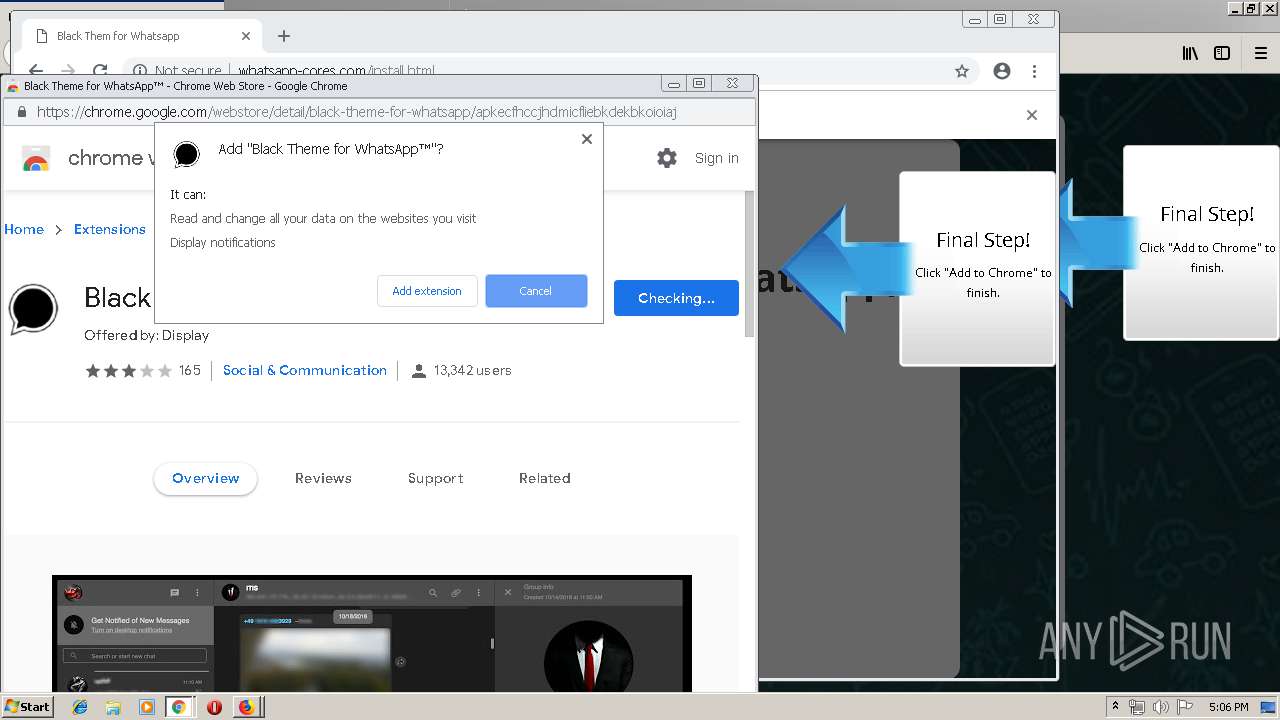
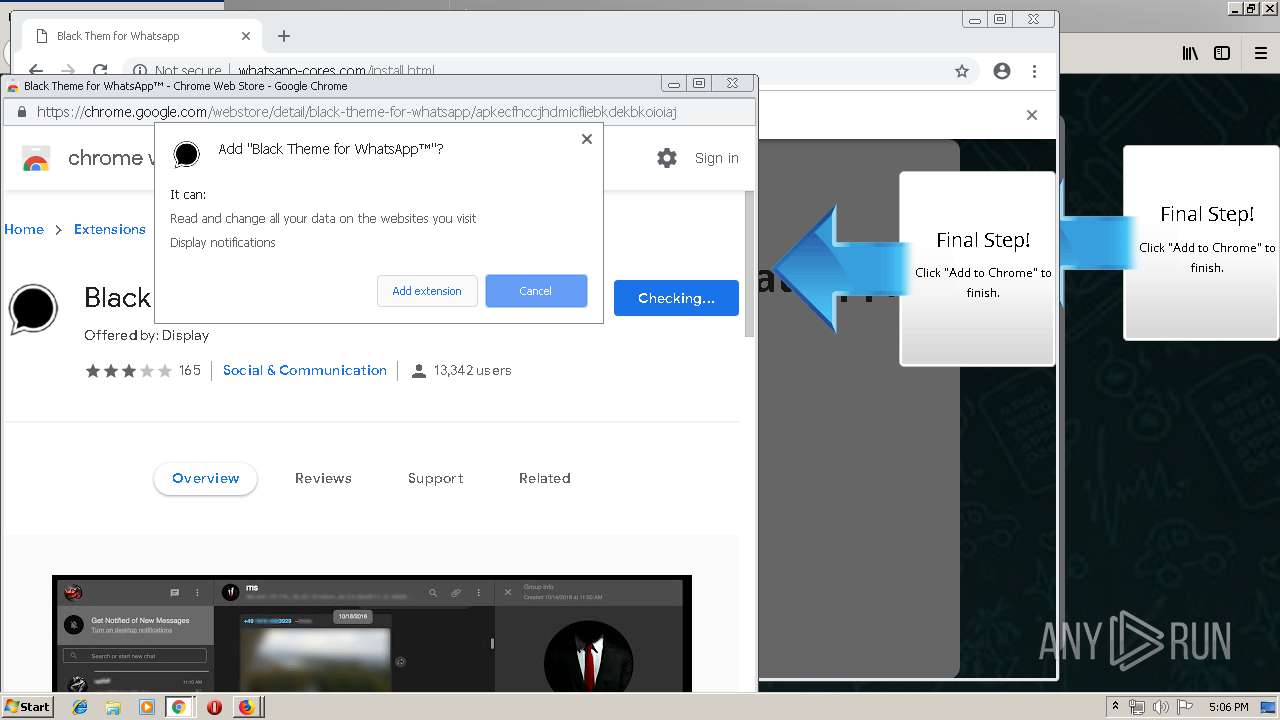
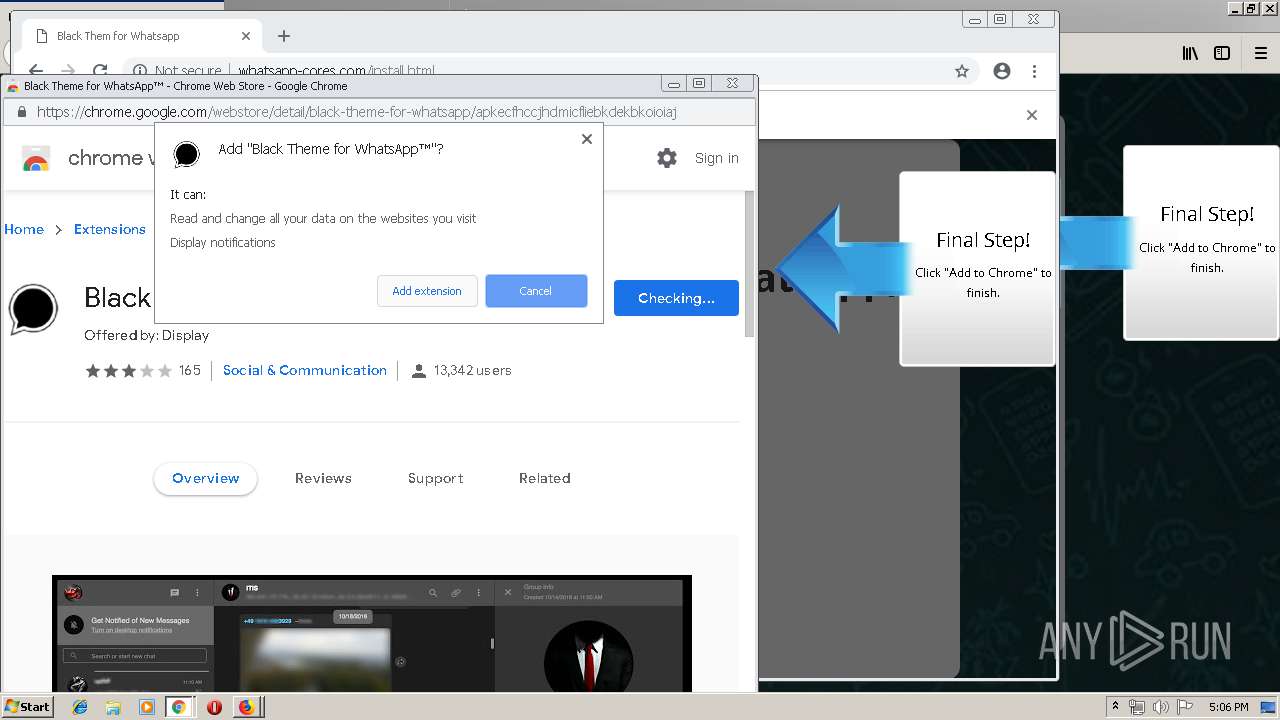
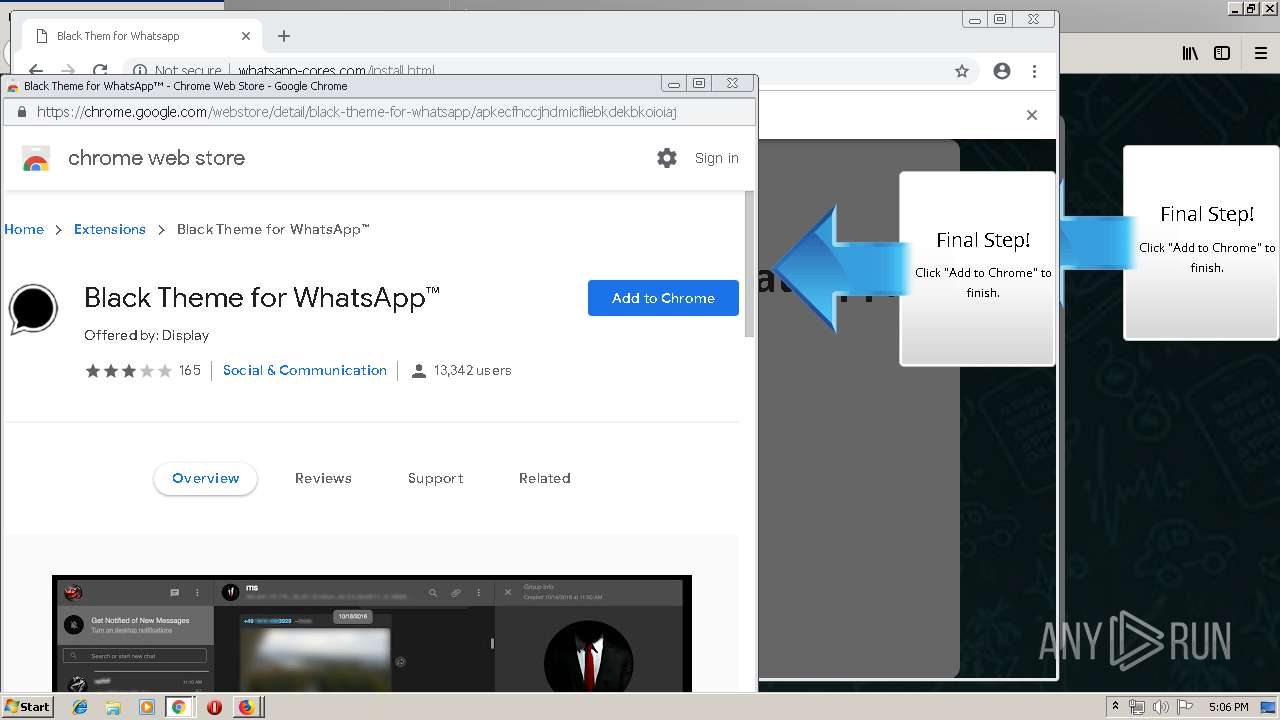
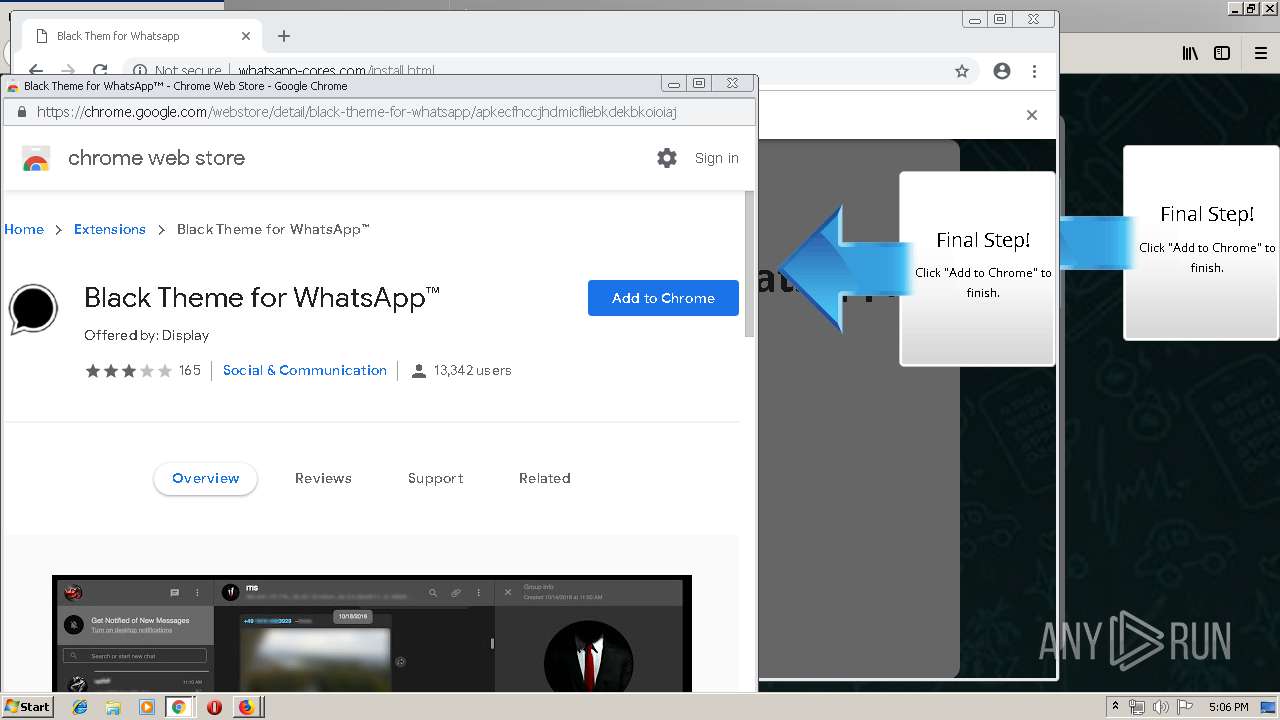
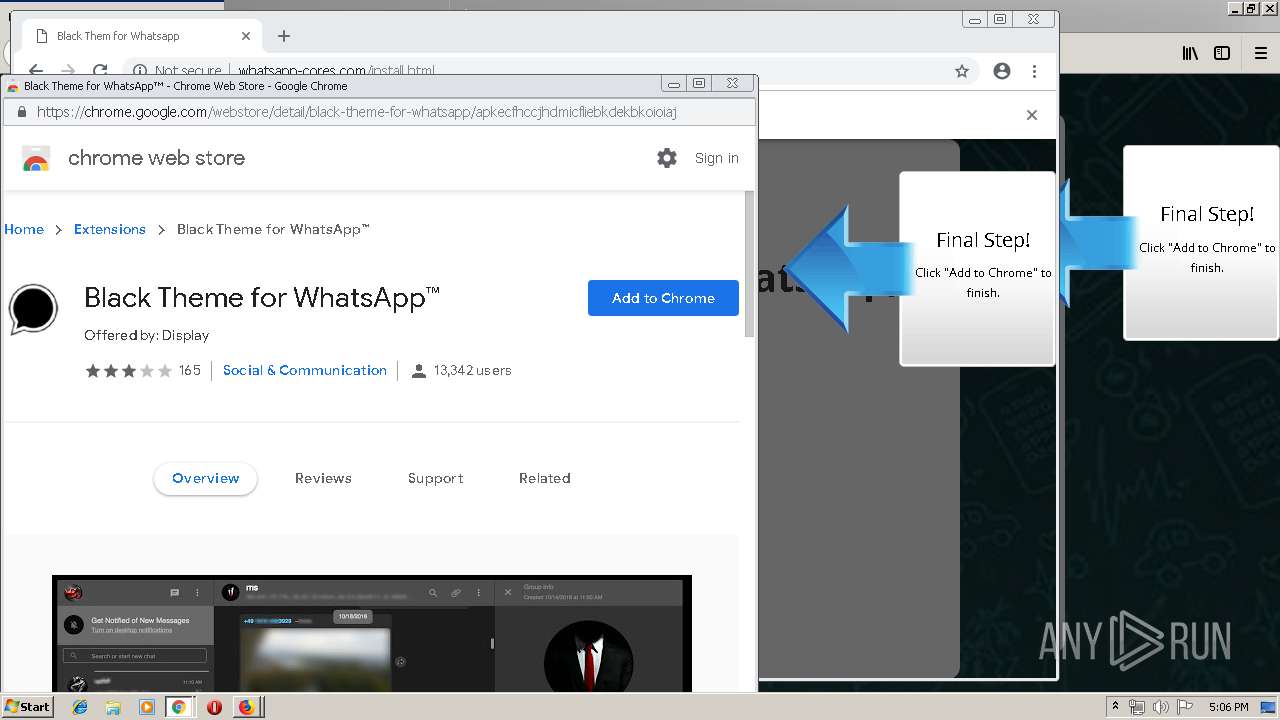
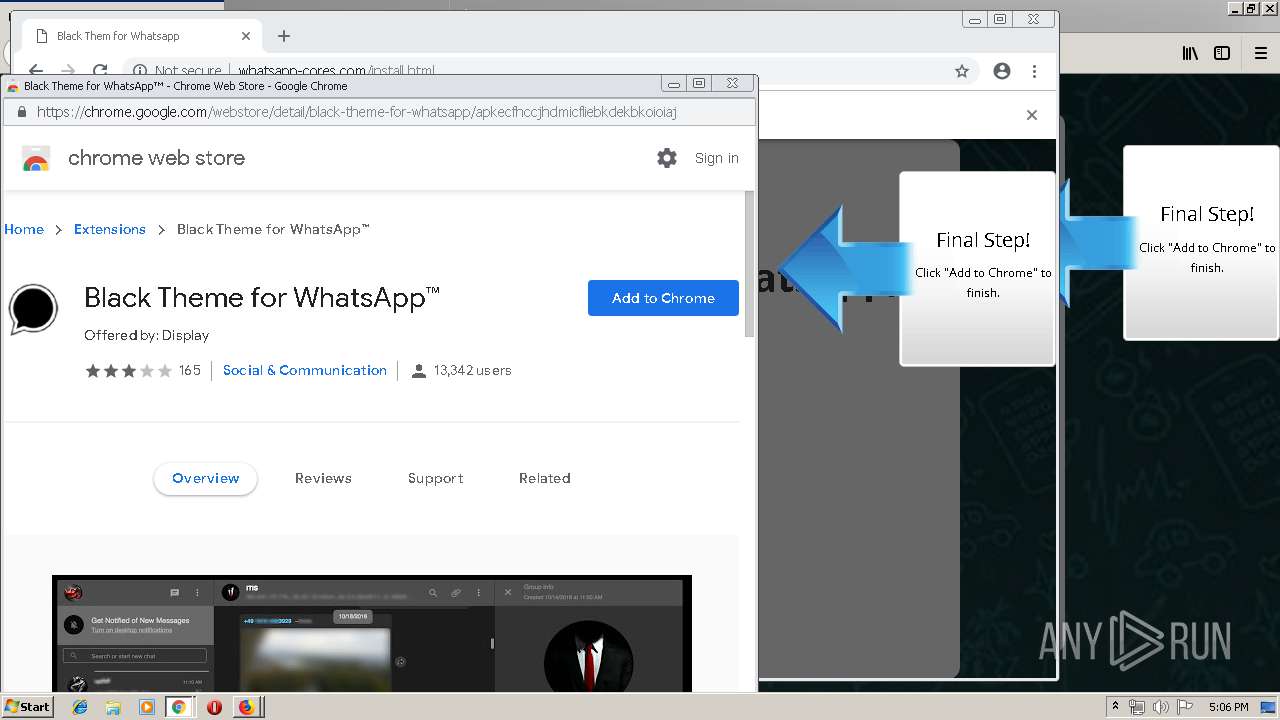
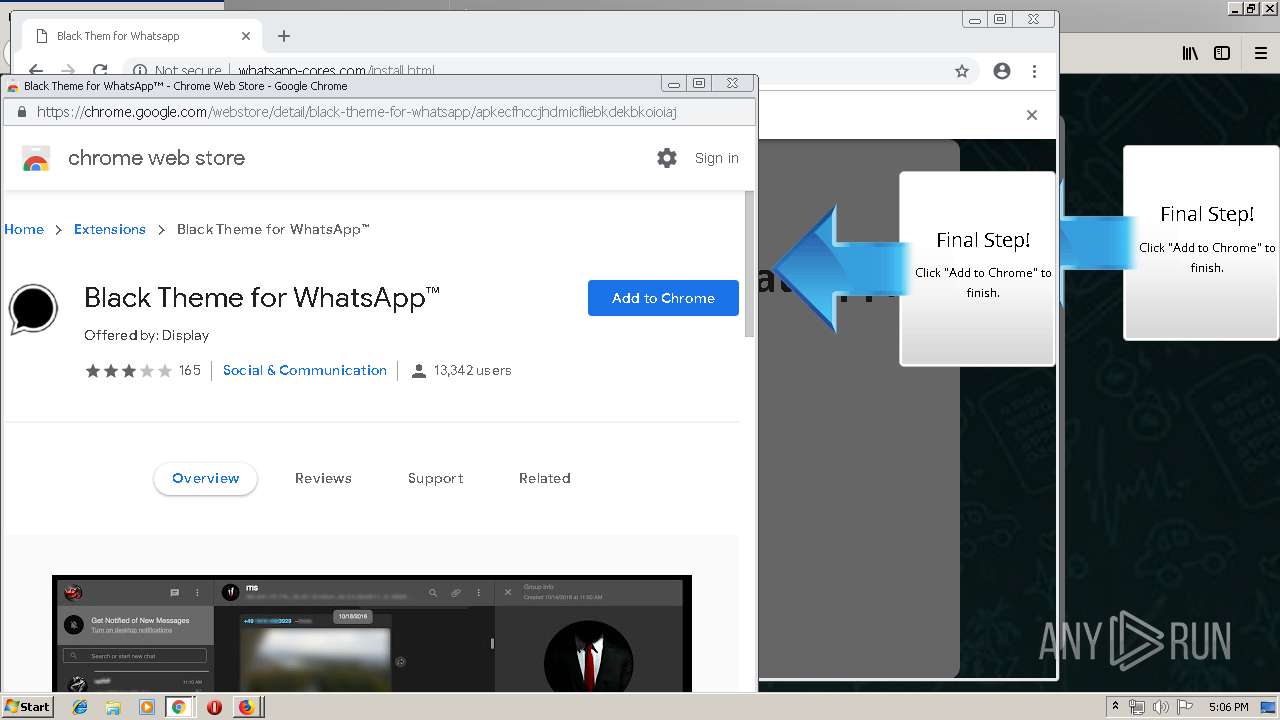
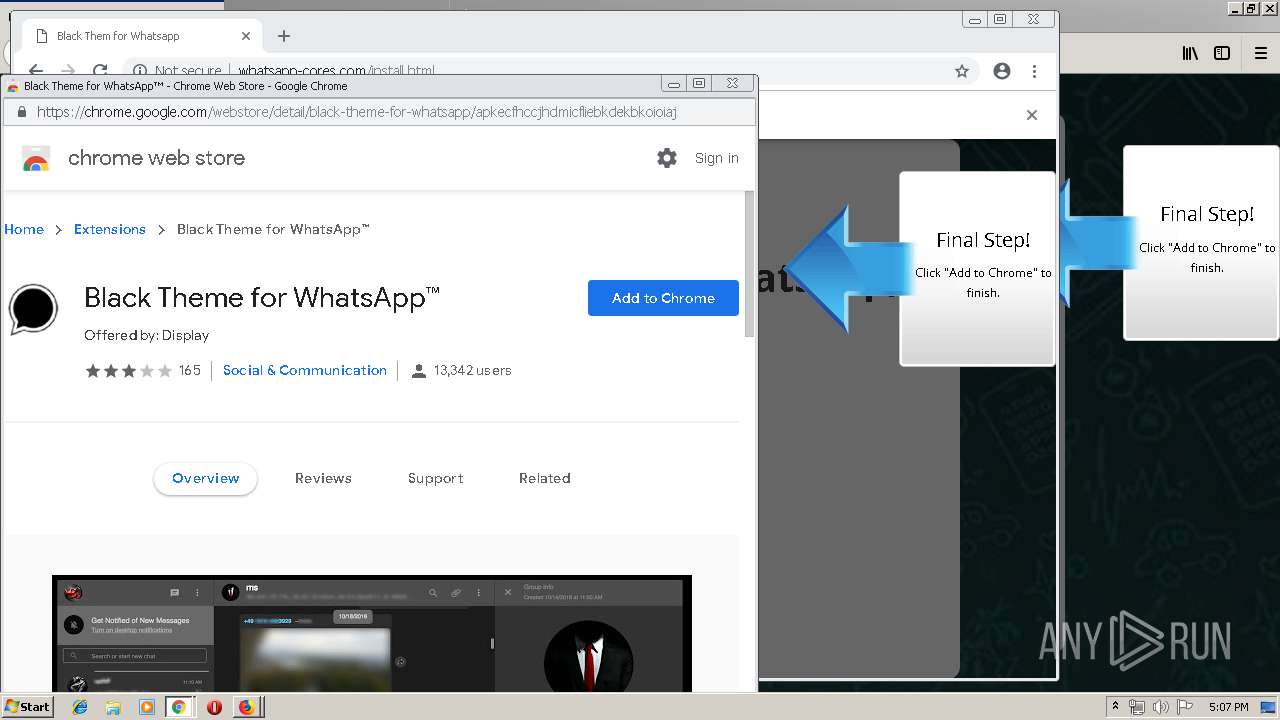
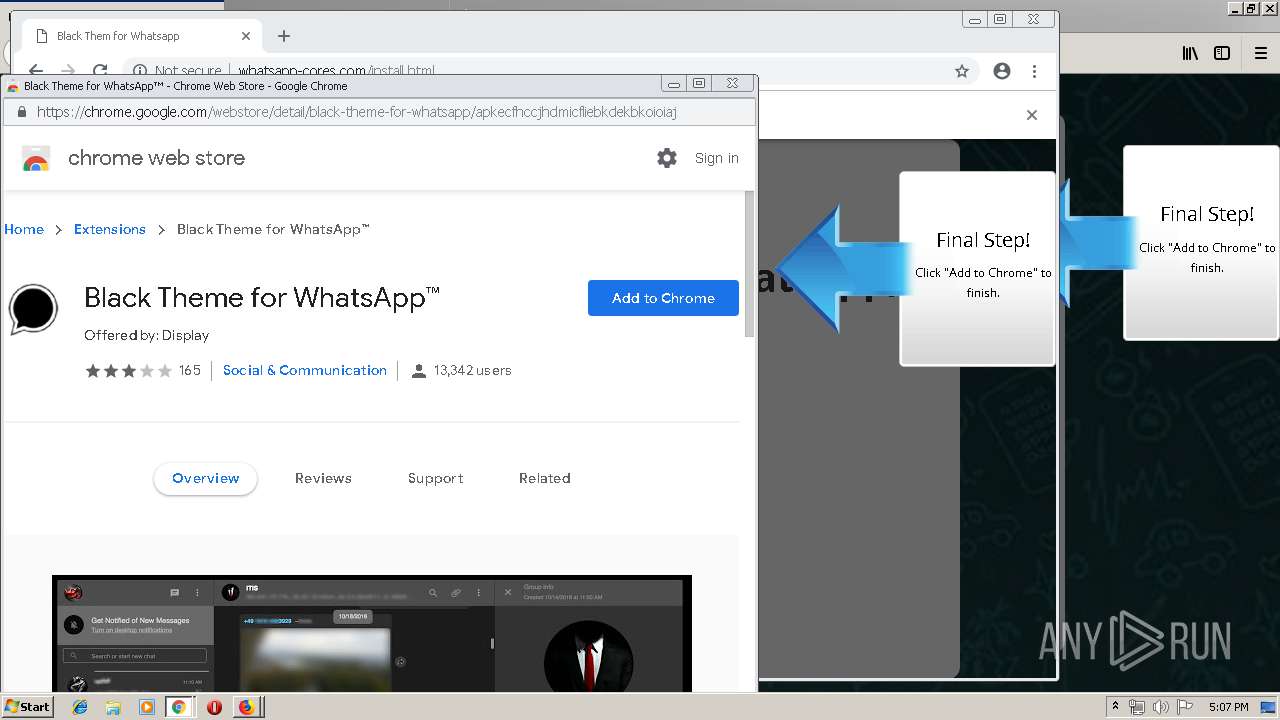
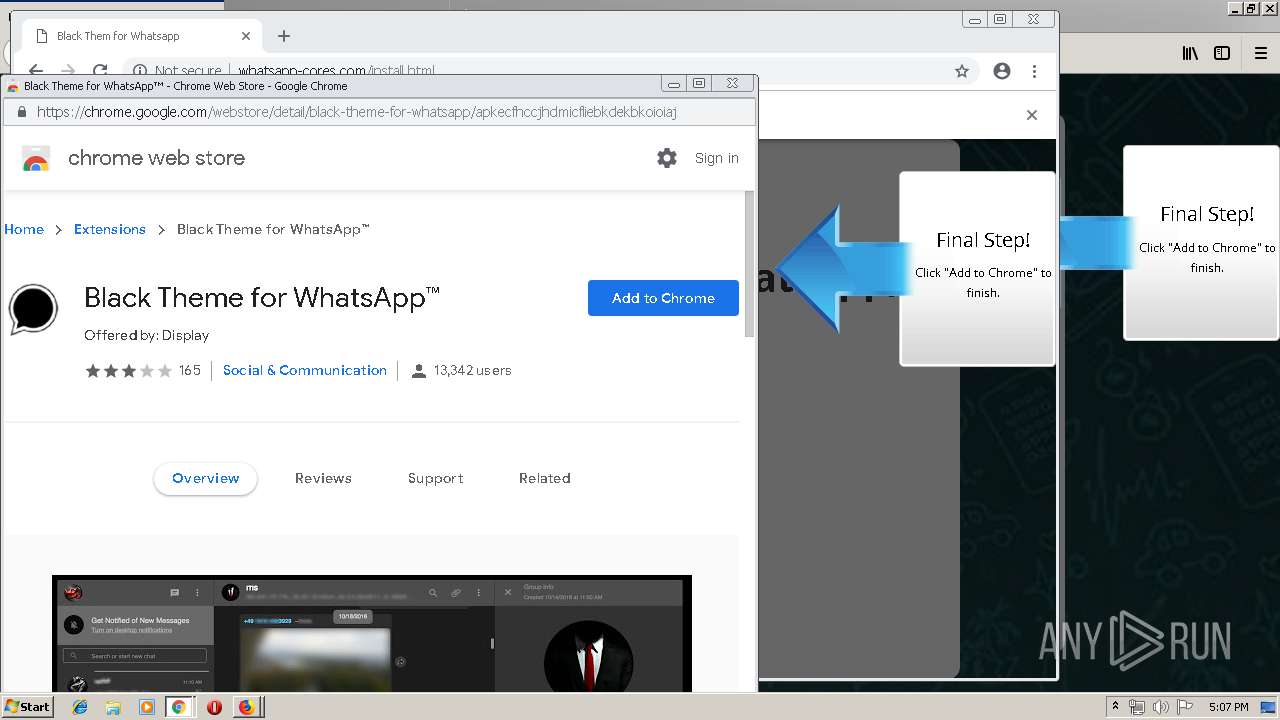
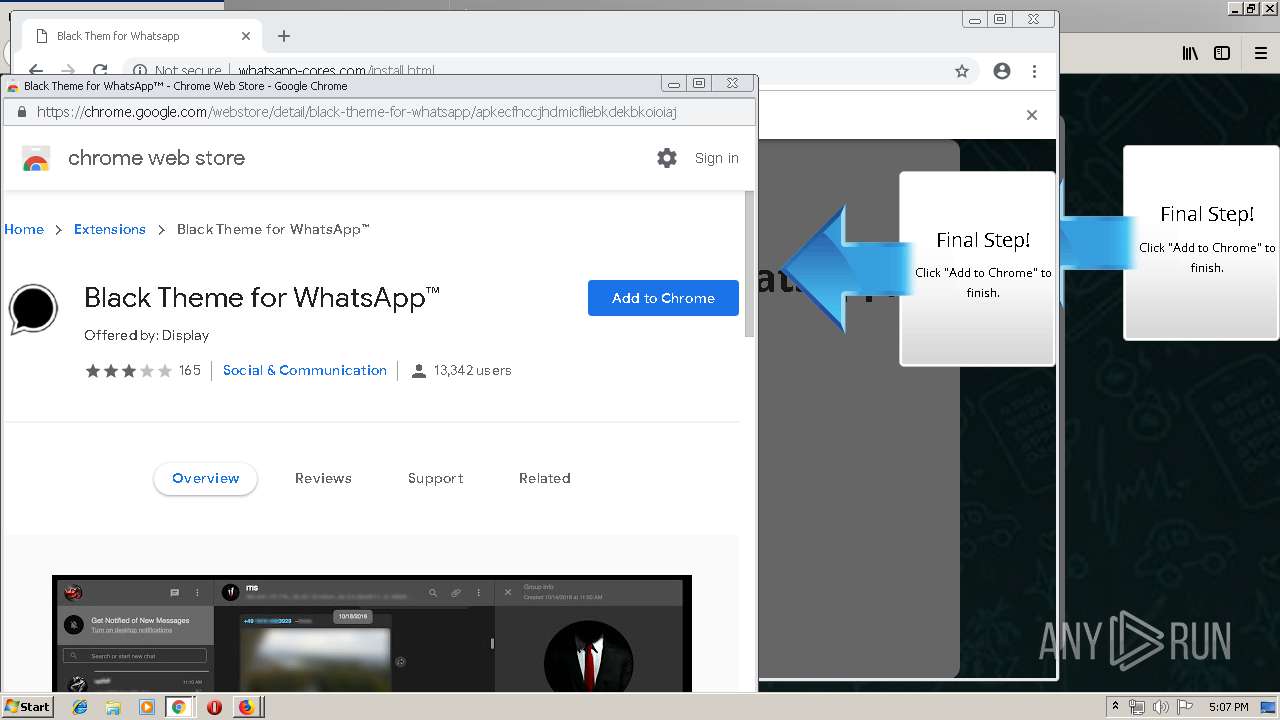
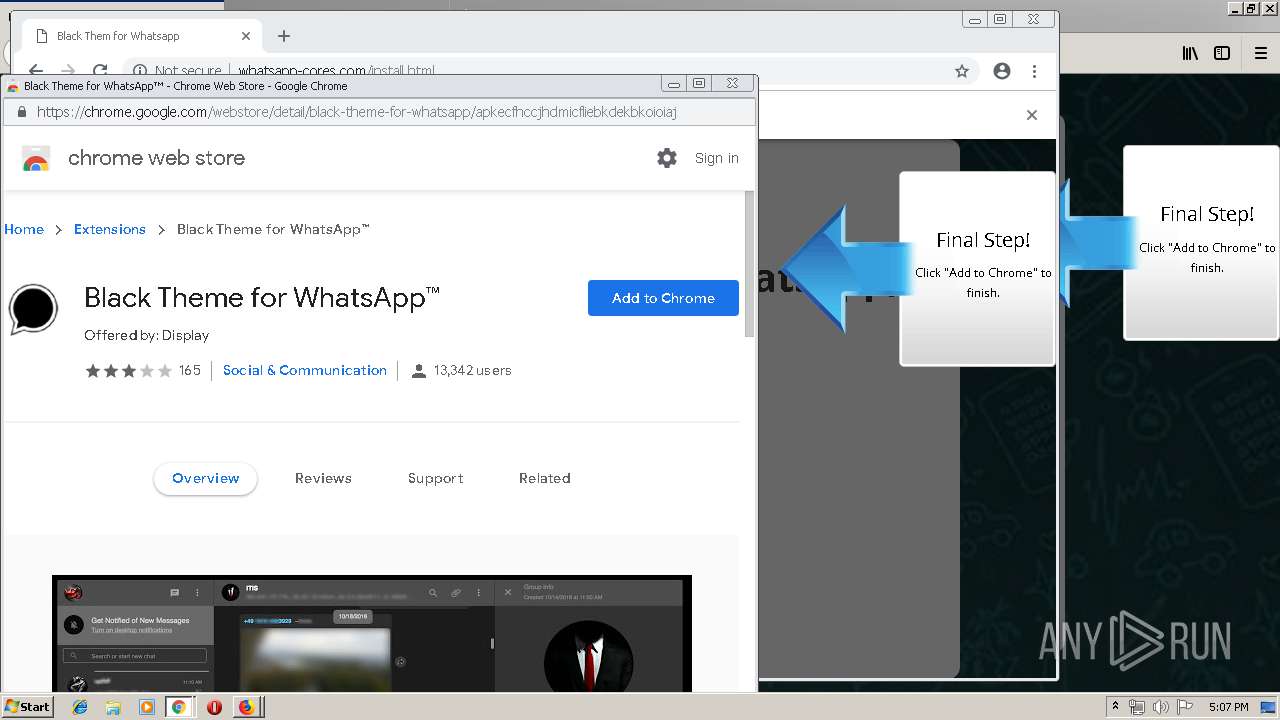
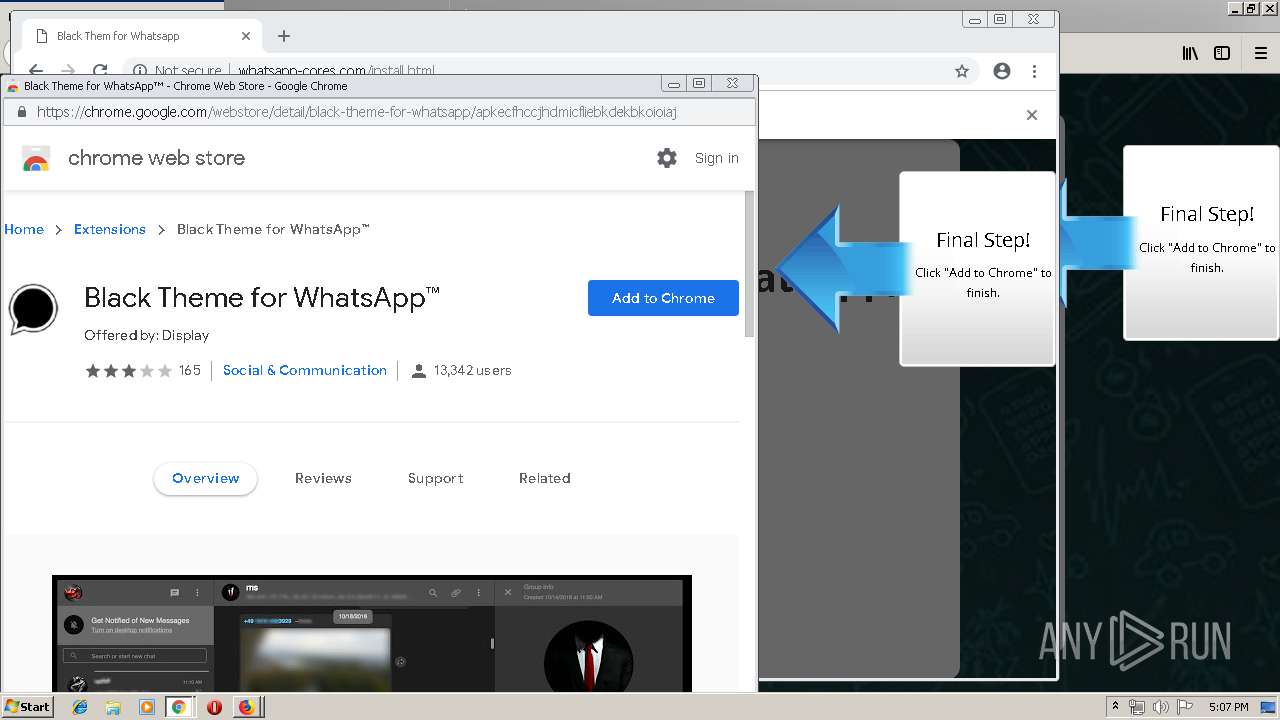
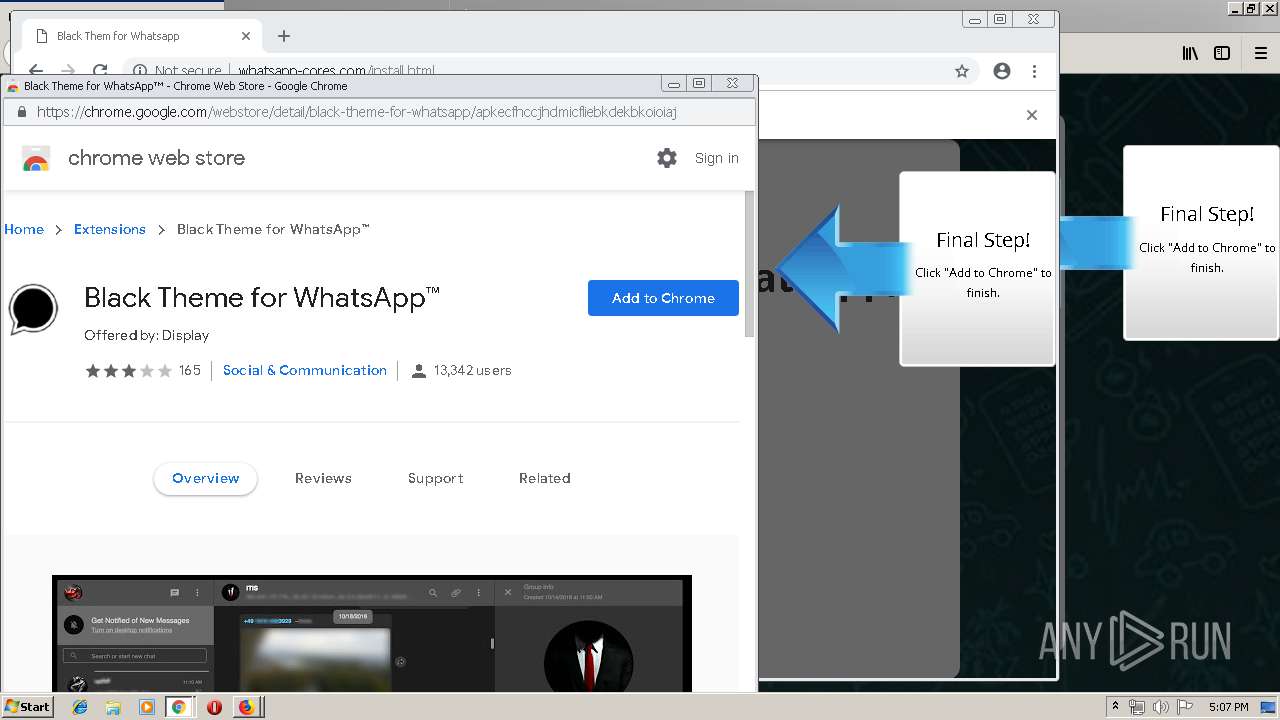
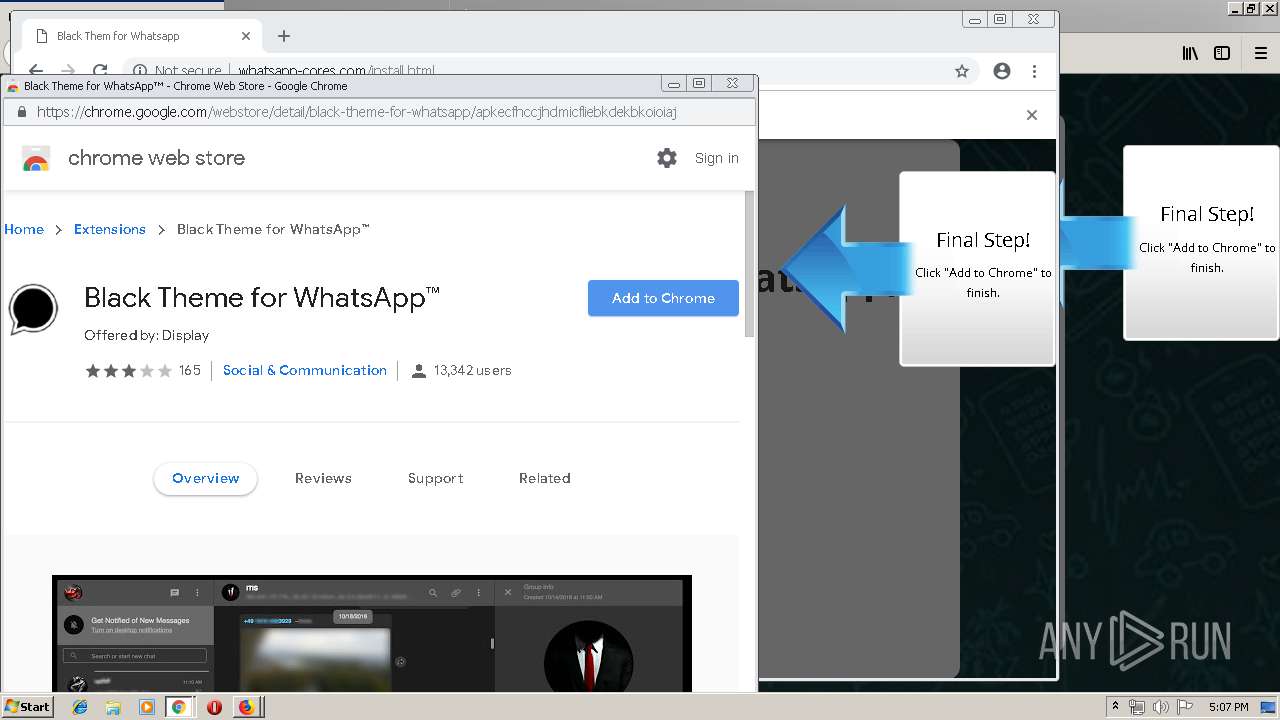
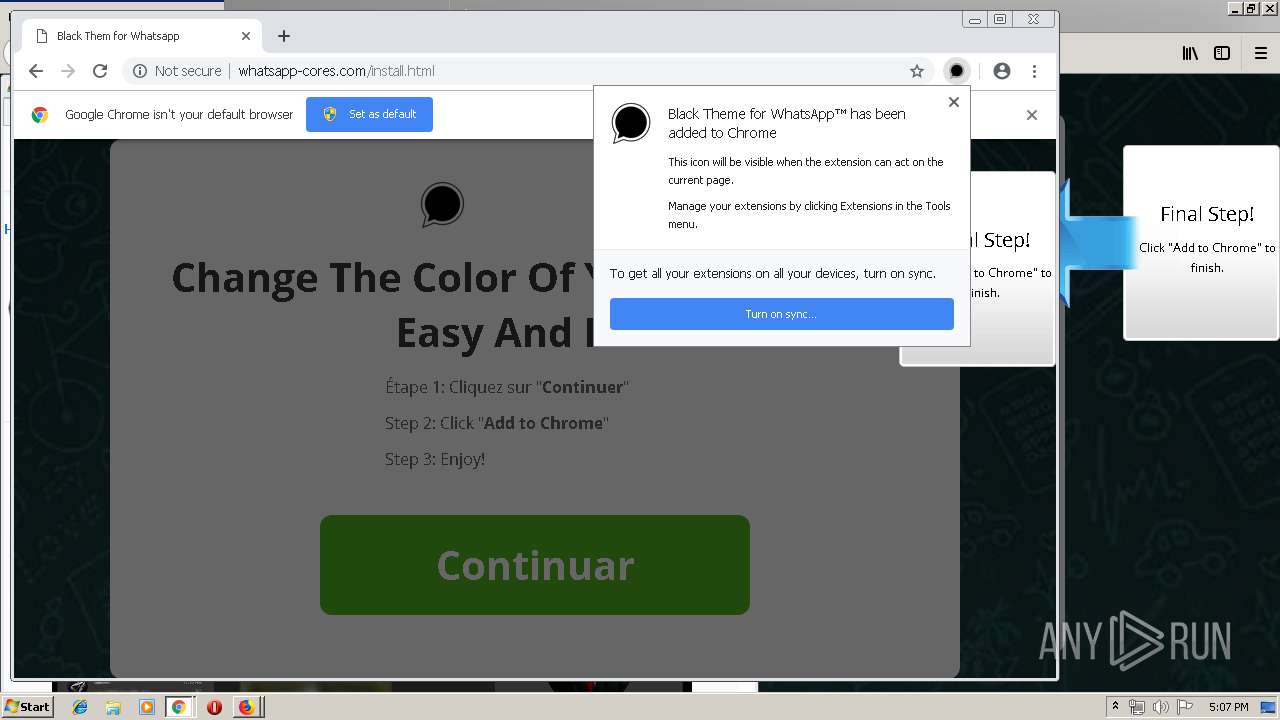
1500 | firefox.exe | GET | 200 | 34.207.109.250:80 | http://whatsapp-cores.com/files/codigos_install.js | US | text | 1.02 Kb | unknown |
1500 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
1500 | firefox.exe | GET | 200 | 34.207.109.250:80 | http://whatsapp-cores.com/install.html | US | html | 43.1 Kb | unknown |
1500 | firefox.exe | GET | 200 | 104.111.214.175:80 | http://ak.staticimgfarm.com/images/download/assist_21.gif | NL | image | 39.5 Kb | whitelisted |
1500 | firefox.exe | GET | 200 | 35.244.218.203:80 | http://fromdoctopdf.dl.myway.com/localStorage.jhtml | US | html | 2.20 Kb | whitelisted |
1500 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
1500 | firefox.exe | GET | 200 | 34.207.109.250:80 | http://whatsapp-cores.com/files/icon48.png | US | image | 1.52 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1500 | firefox.exe | 3.86.233.115:80 | spotify-br.com | — | US | unknown |
1500 | firefox.exe | 2.16.186.112:80 | detectportal.firefox.com | Akamai International B.V. | — | whitelisted |
1500 | firefox.exe | 35.166.112.39:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
1500 | firefox.exe | 52.26.103.165:443 | tiles.services.mozilla.com | Amazon.com, Inc. | US | unknown |
1500 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1500 | firefox.exe | 67.199.248.10:443 | bit.ly | Bitly Inc | US | shared |
1500 | firefox.exe | 34.207.109.250:80 | whatsapp-cores.com | Amazon.com, Inc. | US | unknown |
1500 | firefox.exe | 172.217.18.10:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
1500 | firefox.exe | 104.111.214.175:80 | ak.staticimgfarm.com | Akamai International B.V. | NL | whitelisted |
1500 | firefox.exe | 2.18.232.251:80 | akz.imgfarm.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
spotify-br.com |
| unknown |
detectportal.firefox.com |
| whitelisted |
a1089.dscd.akamai.net |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
tiles.services.mozilla.com |
| whitelisted |
tiles.r53-2.services.mozilla.com |
| whitelisted |
snippets.cdn.mozilla.net |
| whitelisted |
drcwo519tnci7.cloudfront.net |
| shared |
href.li |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1500 | firefox.exe | Generic Protocol Command Decode | SURICATA STREAM reassembly overlap with different data |
1500 | firefox.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
1500 | firefox.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |