| File name: | n.exe |
| Full analysis: | https://app.any.run/tasks/07641c40-c598-4134-8b17-fb49a385f3e9 |
| Verdict: | Malicious activity |
| Analysis date: | August 14, 2024, 21:18:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | 720C7F71DC90ABCCF1716683F14F217B |
| SHA1: | 2A69C1190BCD09850214B5AC7C0AFCA8CD6FFA02 |
| SHA256: | 8076E15A7ED4A567E778FE2C66E03FD2D6634E5FB7D7E8FEF3C9DC0AA278A82E |
| SSDEEP: | 98304:kXEtod5RT4wiyrMtlu1lhZdam6+KLTAHNMl/v0TqKJtT9IFLdZJULG8/Gkmu/ndM:F8pPuLnSUzyaJA |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops the executable file immediately after the start
- n.exe (PID: 6452)
Executable content was dropped or overwritten
- n.exe (PID: 6452)
The process drops C-runtime libraries
- n.exe (PID: 6452)
Application launched itself
- n.exe (PID: 6452)
Process drops legitimate windows executable
- n.exe (PID: 6452)
Process drops python dynamic module
- n.exe (PID: 6452)
Loads Python modules
- n.exe (PID: 6520)
Creates file in the systems drive root
- n.exe (PID: 6520)
INFO
Checks supported languages
- n.exe (PID: 6452)
- n.exe (PID: 6520)
Create files in a temporary directory
- n.exe (PID: 6452)
- n.exe (PID: 6520)
Reads the computer name
- n.exe (PID: 6452)
- n.exe (PID: 6520)
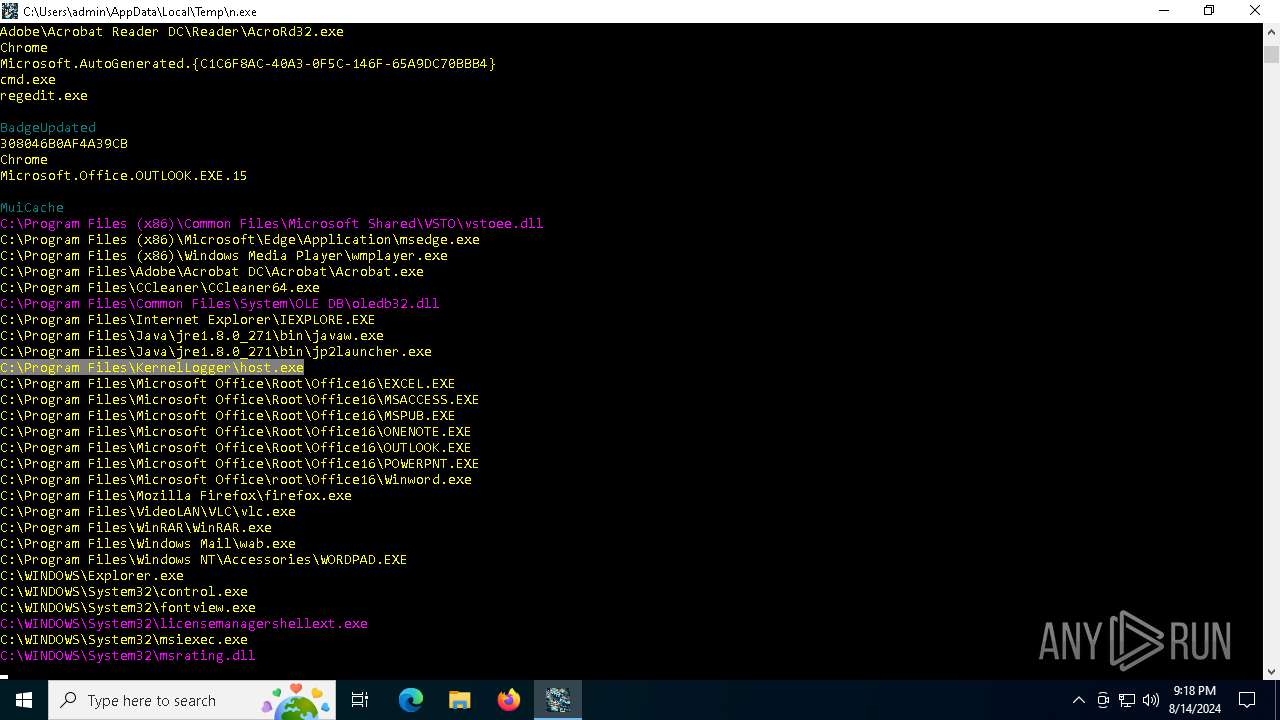
PyInstaller has been detected (YARA)
- n.exe (PID: 6452)
- n.exe (PID: 6520)
Reads the machine GUID from the registry
- n.exe (PID: 6520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:07:28 08:06:35+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.34 |
| CodeSize: | 166400 |
| InitializedDataSize: | 363520 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa6a0 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.3.3.7 |
| ProductVersionNumber: | 1.3.3.7 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | Cheat Checker by rovert |
| FileVersion: | 1.3.3.7 |
| ProductName: | rovert_checker |
| ProductVersion: | 1.3.3.7 |
| OriginalFileName: | rovertchecker.exe |
| LegalCopyright: | © rovert. All rights refused. |
Total processes
130
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6452 | "C:\Users\admin\AppData\Local\Temp\n.exe" | C:\Users\admin\AppData\Local\Temp\n.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Cheat Checker by rovert Version: 1.3.3.7 Modules
| |||||||||||||||
| 6460 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | n.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6520 | "C:\Users\admin\AppData\Local\Temp\n.exe" | C:\Users\admin\AppData\Local\Temp\n.exe | n.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Cheat Checker by rovert Version: 1.3.3.7 Modules
| |||||||||||||||
Total events
3 500
Read events
3 500
Write events
0
Delete events
0
Modification events
Executable files
28
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6452 | n.exe | C:\Users\admin\AppData\Local\Temp\_MEI64522\python310.dll | executable | |
MD5:C80B5CB43E5FE7948C3562C1FFF1254E | SHA256:058925E4BBFCB460A3C00EC824B8390583BAEF0C780A7C7FF01D43D9EEC45F20 | |||
| 6452 | n.exe | C:\Users\admin\AppData\Local\Temp\_MEI64522\VCRUNTIME140.dll | executable | |
MD5:F12681A472B9DD04A812E16096514974 | SHA256:D66C3B47091CEB3F8D3CC165A43D285AE919211A0C0FCB74491EE574D8D464F8 | |||
| 6452 | n.exe | C:\Users\admin\AppData\Local\Temp\_MEI64522\pywin32_system32\pythoncom310.dll | executable | |
MD5:65DD753F51CD492211986E7B700983EF | SHA256:C3B33BA6C4F646151AED4172562309D9F44A83858DDFD84B2D894A8B7DA72B1E | |||
| 6452 | n.exe | C:\Users\admin\AppData\Local\Temp\_MEI64522\_decimal.pyd | executable | |
MD5:10F7B96C666F332EC512EDADE873EECB | SHA256:6314C99A3EFA15307E7BDBE18C0B49BC841C734F42923A0B44AAB42ED7D4A62D | |||
| 6452 | n.exe | C:\Users\admin\AppData\Local\Temp\_MEI64522\Pythonwin\mfc140u.dll | executable | |
MD5:03A161718F1D5E41897236D48C91AE3C | SHA256:E06C4BD078F4690AA8874A3DEB38E802B2A16CCB602A7EDC2E077E98C05B5807 | |||
| 6452 | n.exe | C:\Users\admin\AppData\Local\Temp\_MEI64522\VCRUNTIME140_1.dll | executable | |
MD5:75E78E4BF561031D39F86143753400FF | SHA256:1758085A61527B427C4380F0C976D29A8BEE889F2AC480C356A3F166433BF70E | |||
| 6452 | n.exe | C:\Users\admin\AppData\Local\Temp\_MEI64522\_socket.pyd | executable | |
MD5:E137DF498C120D6AC64EA1281BCAB600 | SHA256:8046BF64E463D5AA38D13525891156131CF997C2E6CDF47527BC352F00F5C90A | |||
| 6452 | n.exe | C:\Users\admin\AppData\Local\Temp\_MEI64522\Pythonwin\win32ui.pyd | executable | |
MD5:B505E88EB8995C2EC46129FB4B389E6C | SHA256:BE7918B4F7E7DE53674894A4B8CFADCACB4726CEA39B7DB477A6C70231C41790 | |||
| 6452 | n.exe | C:\Users\admin\AppData\Local\Temp\_MEI64522\_ctypes.pyd | executable | |
MD5:87596DB63925DBFE4D5F0F36394D7AB0 | SHA256:92D7954D9099762D81C1AE2836C11B6BA58C1883FDE8EEEFE387CC93F2F6AFB4 | |||
| 6452 | n.exe | C:\Users\admin\AppData\Local\Temp\_MEI64522\_ssl.pyd | executable | |
MD5:35F66AD429CD636BCAD858238C596828 | SHA256:58B772B53BFE898513C0EB264AE4FA47ED3D8F256BC8F70202356D20F9ECB6DC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
37
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5924 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5924 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6796 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6848 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4016 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5336 | SearchApp.exe | 92.123.104.31:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5924 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5924 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |