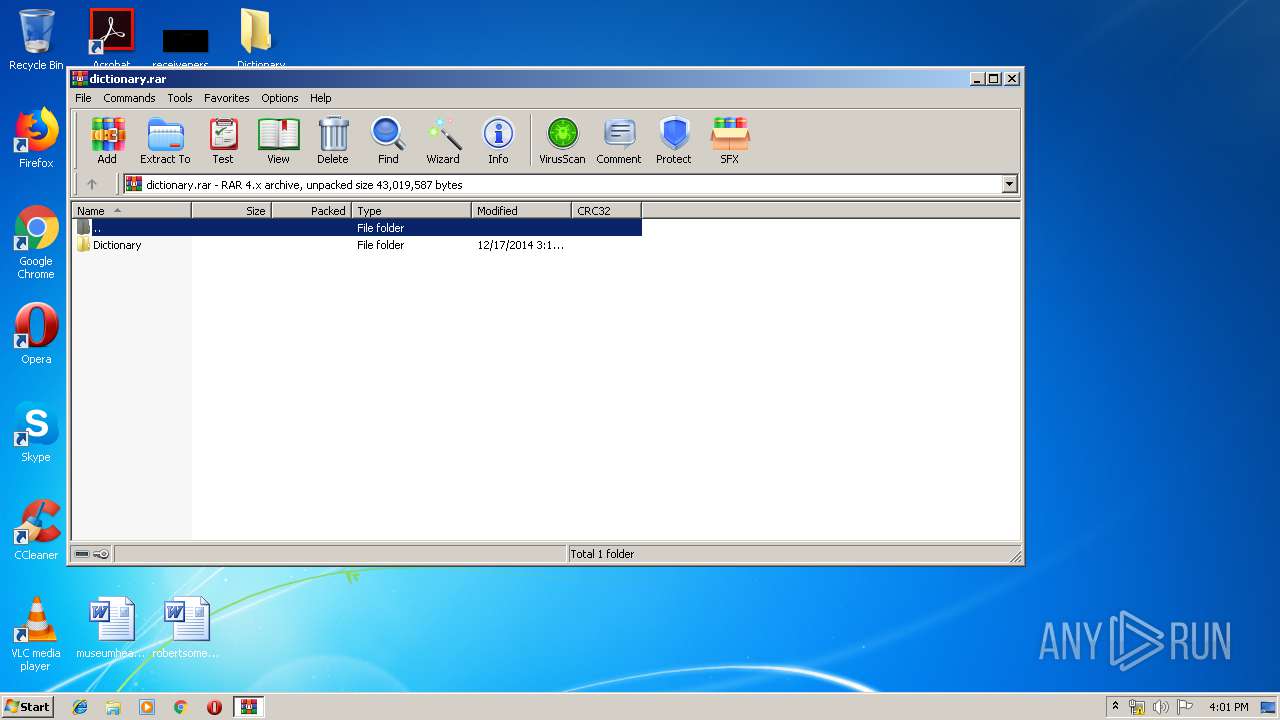
| download: | dictionary.rar |
| Full analysis: | https://app.any.run/tasks/2431fdd6-add6-4229-8650-d051329b2914 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2019, 15:00:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 2295CEC207946E625CFEAF54499328CA |
| SHA1: | C164FB74D1E29569AAC78F864BE4FEECA33DC582 |
| SHA256: | 805F8D811FE3B0C0EC0FCC5A54A7B50D062D7235941243ED9FD94D6841D9BD8B |
| SSDEEP: | 786432:W09VE5lCN6RJG5ZOyBY4nMwwvWPVXOWwvH9q60dYlO3uH:W04lc6SywY4nMsV8Mdp3+ |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1540)
Application was dropped or rewritten from another process
- dictionary.exe (PID: 1732)
SUSPICIOUS
Writes to a desktop.ini file (may be used to cloak folders)
- WinRAR.exe (PID: 3380)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3380)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 30127 |
|---|---|
| UncompressedSize: | 141842 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2008:12:11 01:31:24 |
| PackingMethod: | Normal |
| ArchivedFileName: | Dictionary\anc_dictionary.ico |
Total processes
35
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1540 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
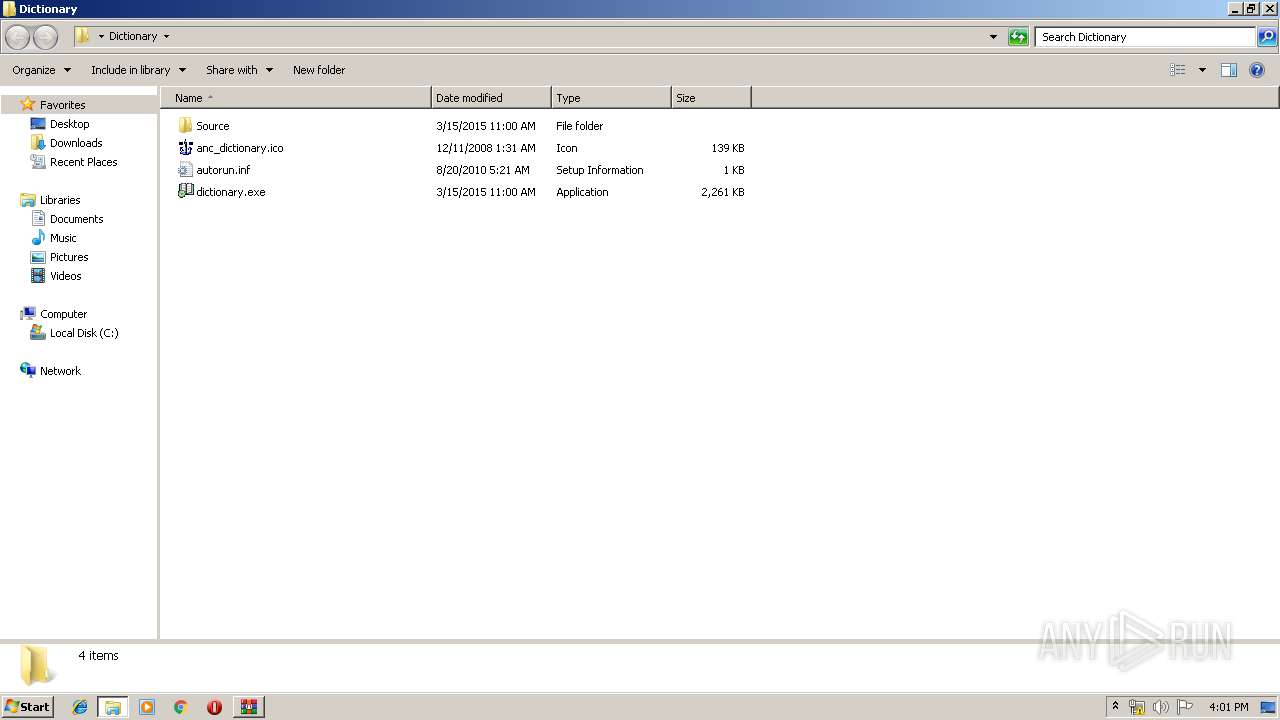
| 1732 | "C:\Users\admin\Desktop\Dictionary\dictionary.exe" | C:\Users\admin\Desktop\Dictionary\dictionary.exe | — | explorer.exe | |||||||||||
User: admin Company: EC Software Integrity Level: MEDIUM Description: Help & Manual Multimedia Viewer Exit code: 0 Version: 1.0.1.0 Modules
| |||||||||||||||
| 3380 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\dictionary.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
796
Read events
775
Write events
21
Delete events
0
Modification events
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\dictionary.rar | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (1540) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
7
Suspicious files
17
Text files
396
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3380 | WinRAR.exe | C:\Users\admin\Desktop\Dictionary\Source\Alpha Lub.pdf | — | |
MD5:— | SHA256:— | |||
| 3380 | WinRAR.exe | C:\Users\admin\Desktop\Dictionary\anc_dictionary.ico | image | |
MD5:C58F8DFE8C06FA98073D8A9FC3D033D9 | SHA256:0989640CEAABB765B85AF3D1F8A071E10547981F880CFEA7617AAE83EABA196D | |||
| 3380 | WinRAR.exe | C:\Users\admin\Desktop\Dictionary\Source\breadcrumbs.png | image | |
MD5:1E62D3E319DB49038EF17B40340D7894 | SHA256:E2FE44F064AE00AF5F90C4A8347F44D8A59426804155252CD5A2091E47BE35C5 | |||
| 3380 | WinRAR.exe | C:\Users\admin\Desktop\Dictionary\Source\Beaufort_Scale.pdf | ||
MD5:85DCF7CE263CAF37272ADE2624D1C8F3 | SHA256:7782241D71A32A28A2E70C0F6141D9E945322767C65970FB4AD5884B5B09D018 | |||
| 3380 | WinRAR.exe | C:\Users\admin\Desktop\Dictionary\Source\Batteries.pdf | ||
MD5:1037166F018EFA3D3B8C41ADF32ECDB7 | SHA256:D2DB8D243BF3E74B0636CC288121CA3BF3D110681EBFB923EE77A8185AA7E125 | |||
| 3380 | WinRAR.exe | C:\Users\admin\Desktop\Dictionary\Source\Bearings.pdf | ||
MD5:0C24DC0BE49F6025D24CCE82406883C8 | SHA256:73A15B5066F10767B435DB59AA9D2B75E4A8FA12C62AFD542655DBB3A679FE62 | |||
| 3380 | WinRAR.exe | C:\Users\admin\Desktop\Dictionary\Source\Breathing Apparatus.jpg | image | |
MD5:B039492F6ACBFBC925E8D8ADF78930D5 | SHA256:353E904CA0919A4B85C291E39089727377C37FB36C5CFB047542CA8292BC7ACE | |||
| 3380 | WinRAR.exe | C:\Users\admin\Desktop\Dictionary\Source\boats.gif | image | |
MD5:86EDCA6AD1932042DA8900B6554375C9 | SHA256:4B7F7A926A3D684E25FA7023D235E30AE5295B4F3EC8647B5BD83C2C209AF2B3 | |||
| 3380 | WinRAR.exe | C:\Users\admin\Desktop\Dictionary\Source\btn_hsp_net.png | image | |
MD5:661D8FA5E0172A6C073CFF5F96245083 | SHA256:16F3445BF74982C3D6086A6A1E55CC1BB4B9DA4BDEC5305299633E6BE99DBADF | |||
| 3380 | WinRAR.exe | C:\Users\admin\Desktop\Dictionary\Source\btn_hsp_file.png | image | |
MD5:E256106D223A14C5E12D98DBB9304A10 | SHA256:6932B3050AA7CD8CA10F204793552920E2EEE2FCE1EC1E0D37CA2B444F9FCF5F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report