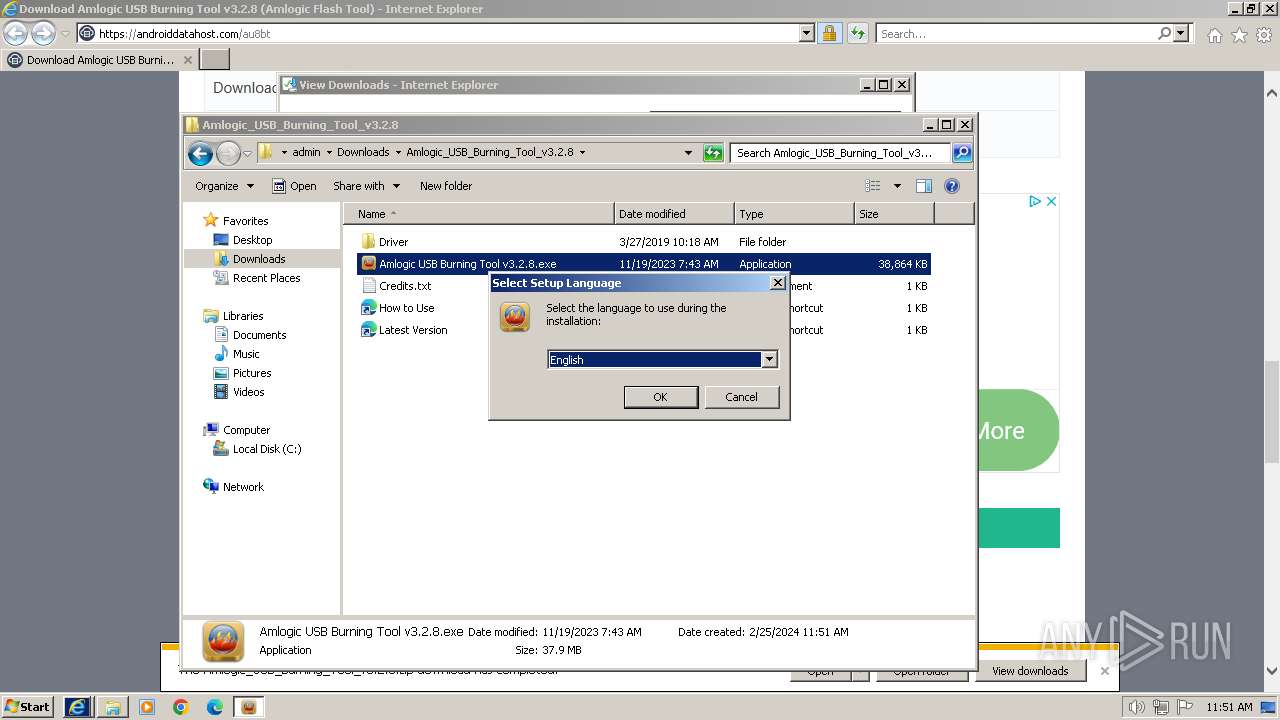
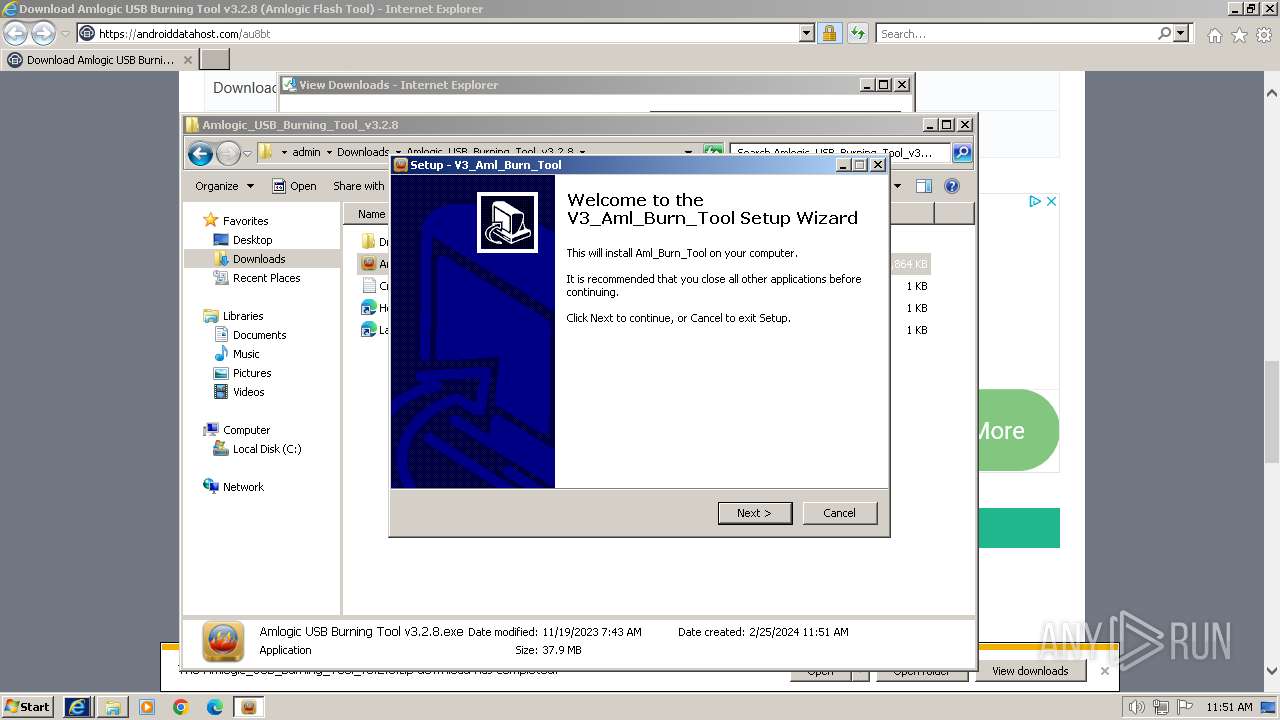
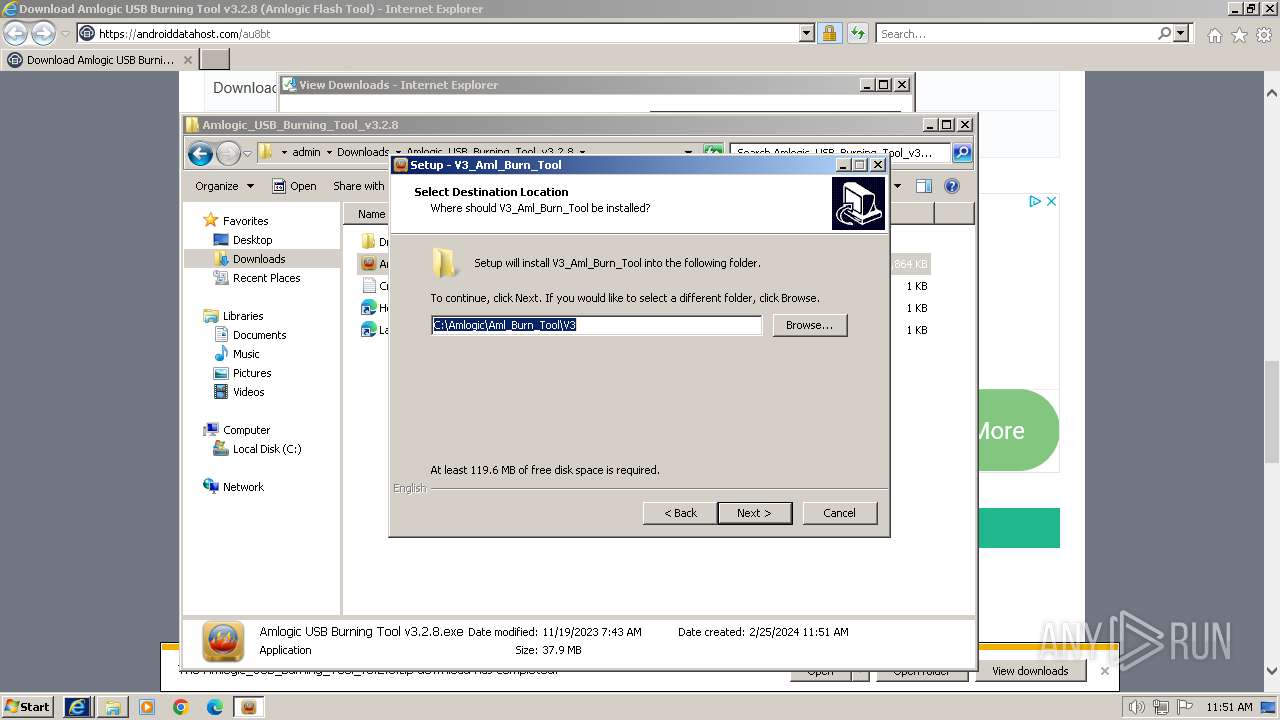
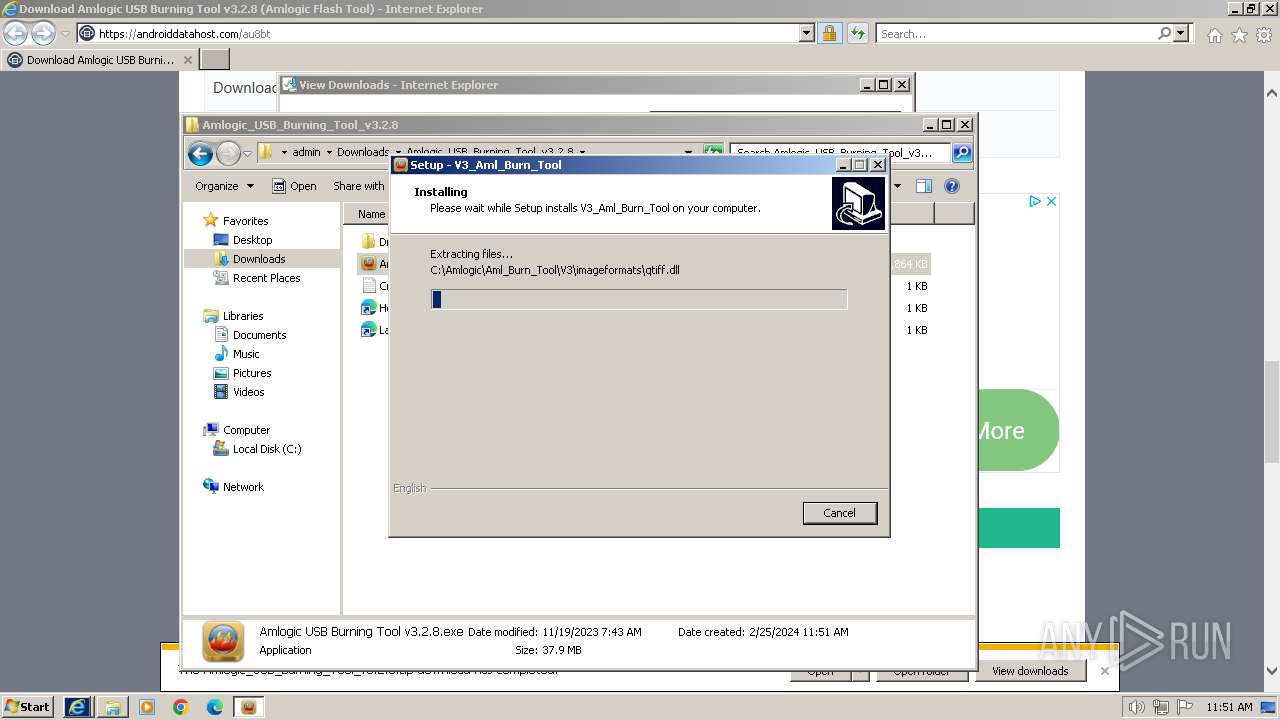
| URL: | https://androiddatahost.com/au8bt |
| Full analysis: | https://app.any.run/tasks/50e4f263-0df6-48ba-bfaf-3f951414e1d1 |
| Verdict: | Malicious activity |
| Analysis date: | February 25, 2024, 11:50:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 3E591DB749B4BE5F885131627050864C |
| SHA1: | BB5B4D43B52747829BBA98E952C1B564794E72FD |
| SHA256: | 8050093B2E589E04BB570467E35C57AD452BE6262A45D43429B3E95E2128515F |
| SSDEEP: | 3:N8FMB4qIi:22B4qIi |
MALICIOUS
Drops the executable file immediately after the start
- Amlogic USB Burning Tool v3.2.8.exe (PID: 3800)
- Amlogic USB Burning Tool v3.2.8.exe (PID: 296)
- Amlogic USB Burning Tool v3.2.8.tmp (PID: 316)
SUSPICIOUS
Executable content was dropped or overwritten
- Amlogic USB Burning Tool v3.2.8.exe (PID: 296)
- Amlogic USB Burning Tool v3.2.8.exe (PID: 3800)
- Amlogic USB Burning Tool v3.2.8.tmp (PID: 316)
Reads the Windows owner or organization settings
- Amlogic USB Burning Tool v3.2.8.tmp (PID: 316)
Process drops legitimate windows executable
- Amlogic USB Burning Tool v3.2.8.tmp (PID: 316)
Starts CMD.EXE for commands execution
- Amlogic USB Burning Tool v3.2.8.tmp (PID: 316)
The process drops C-runtime libraries
- Amlogic USB Burning Tool v3.2.8.tmp (PID: 316)
Reads security settings of Internet Explorer
- Amlogic USB Burning Tool v3.2.8.tmp (PID: 316)
Reads the Internet Settings
- Amlogic USB Burning Tool v3.2.8.tmp (PID: 316)
Drops a system driver (possible attempt to evade defenses)
- Amlogic USB Burning Tool v3.2.8.tmp (PID: 316)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3520)
INFO
Manual execution by a user
- explorer.exe (PID: 1740)
- WinRAR.exe (PID: 3404)
- Amlogic USB Burning Tool v3.2.8.exe (PID: 3800)
The process uses the downloaded file
- iexplore.exe (PID: 4052)
- WinRAR.exe (PID: 3404)
Modifies the phishing filter of IE
- iexplore.exe (PID: 4052)
Application launched itself
- iexplore.exe (PID: 4052)
Create files in a temporary directory
- Amlogic USB Burning Tool v3.2.8.exe (PID: 3800)
- Amlogic USB Burning Tool v3.2.8.exe (PID: 296)
- Amlogic USB Burning Tool v3.2.8.tmp (PID: 316)
Checks supported languages
- Amlogic USB Burning Tool v3.2.8.tmp (PID: 2772)
- Amlogic USB Burning Tool v3.2.8.tmp (PID: 316)
- Amlogic USB Burning Tool v3.2.8.exe (PID: 3800)
- Amlogic USB Burning Tool v3.2.8.exe (PID: 296)
Reads the computer name
- Amlogic USB Burning Tool v3.2.8.tmp (PID: 2772)
- Amlogic USB Burning Tool v3.2.8.tmp (PID: 316)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
54
Monitored processes
10
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
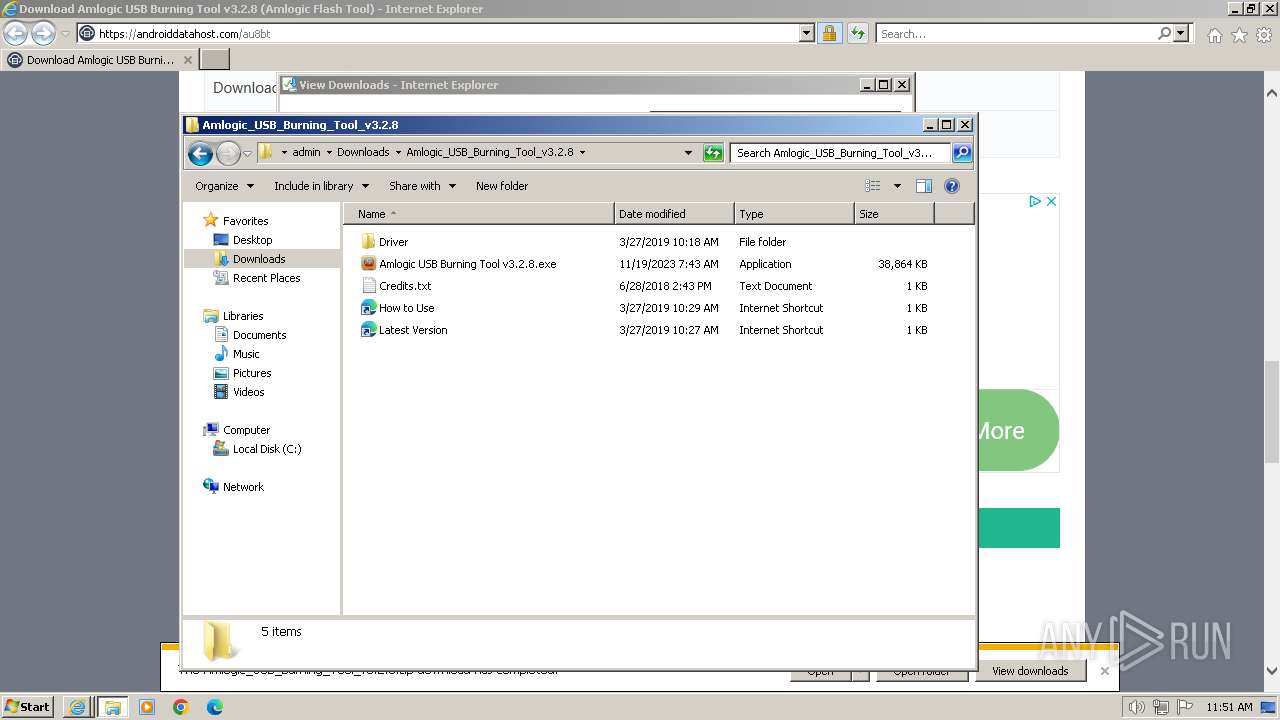
| 296 | "C:\Users\admin\Downloads\Amlogic_USB_Burning_Tool_v3.2.8\Amlogic USB Burning Tool v3.2.8.exe" /SPAWNWND=$30272 /NOTIFYWND=$4027C | C:\Users\admin\Downloads\Amlogic_USB_Burning_Tool_v3.2.8\Amlogic USB Burning Tool v3.2.8.exe | Amlogic USB Burning Tool v3.2.8.tmp | ||||||||||||
User: admin Company: Amlogic, Inc. Integrity Level: HIGH Description: V3_Aml_Burn_Tool Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 316 | "C:\Users\admin\AppData\Local\Temp\is-UVNAI.tmp\Amlogic USB Burning Tool v3.2.8.tmp" /SL5="$402B2,39316483,437760,C:\Users\admin\Downloads\Amlogic_USB_Burning_Tool_v3.2.8\Amlogic USB Burning Tool v3.2.8.exe" /SPAWNWND=$30272 /NOTIFYWND=$4027C | C:\Users\admin\AppData\Local\Temp\is-UVNAI.tmp\Amlogic USB Burning Tool v3.2.8.tmp | Amlogic USB Burning Tool v3.2.8.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1740 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1840 | taskkill /f /t /im Aml_Burn_Tool.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2772 | "C:\Users\admin\AppData\Local\Temp\is-5PRAV.tmp\Amlogic USB Burning Tool v3.2.8.tmp" /SL5="$4027C,39316483,437760,C:\Users\admin\Downloads\Amlogic_USB_Burning_Tool_v3.2.8\Amlogic USB Burning Tool v3.2.8.exe" | C:\Users\admin\AppData\Local\Temp\is-5PRAV.tmp\Amlogic USB Burning Tool v3.2.8.tmp | — | Amlogic USB Burning Tool v3.2.8.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2920 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:4052 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
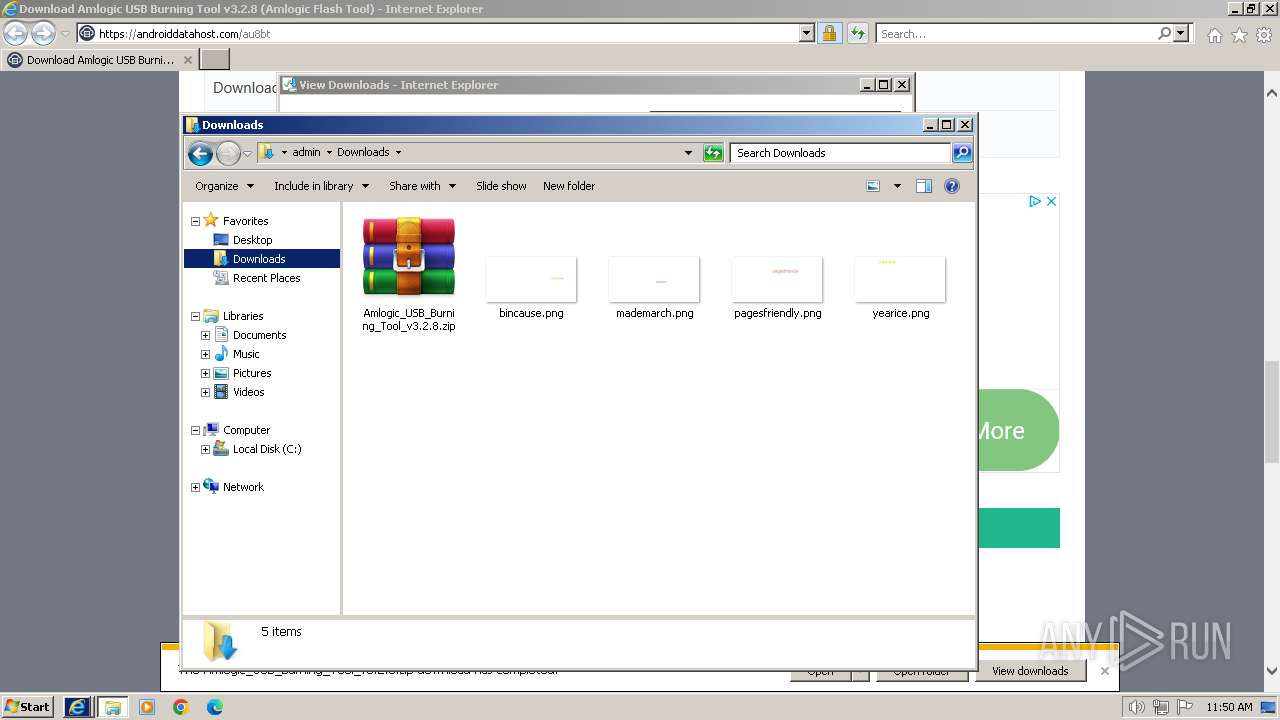
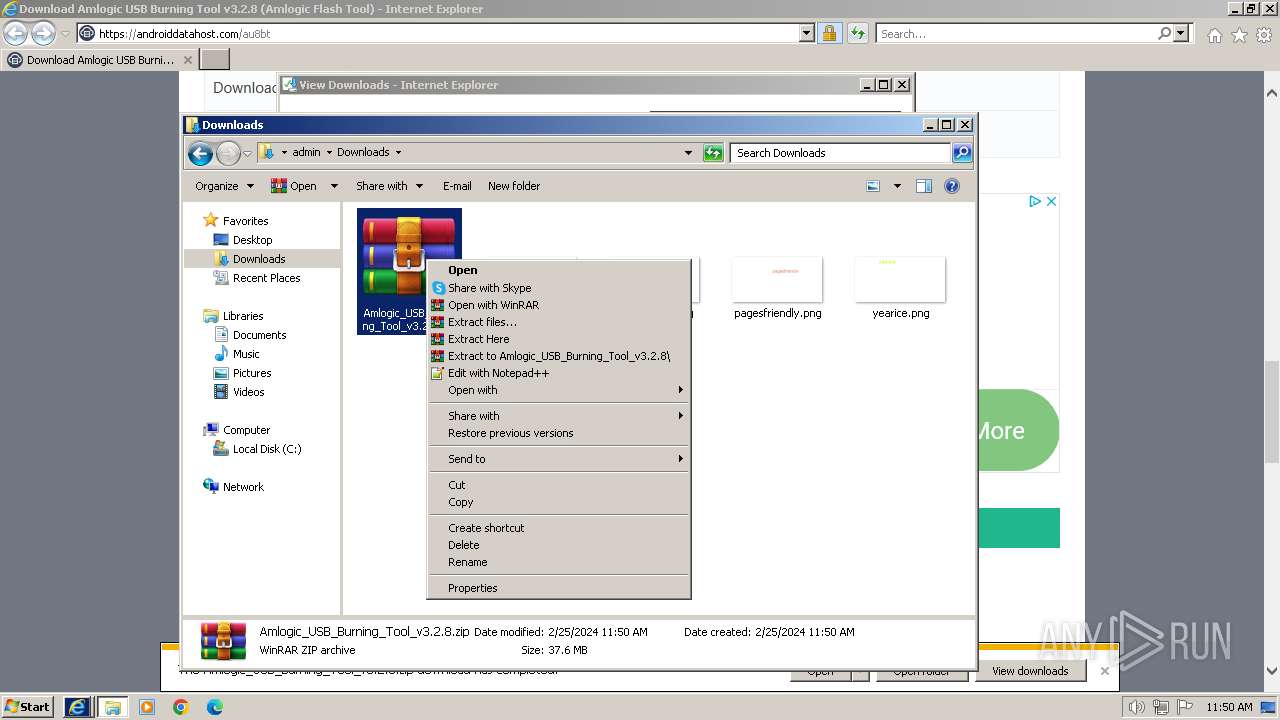
| 3404 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\Amlogic_USB_Burning_Tool_v3.2.8.zip" C:\Users\admin\Downloads\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3520 | "C:\Windows\system32\cmd.exe" /c taskkill /f /t /im Aml_Burn_Tool.exe | C:\Windows\System32\cmd.exe | — | Amlogic USB Burning Tool v3.2.8.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3800 | "C:\Users\admin\Downloads\Amlogic_USB_Burning_Tool_v3.2.8\Amlogic USB Burning Tool v3.2.8.exe" | C:\Users\admin\Downloads\Amlogic_USB_Burning_Tool_v3.2.8\Amlogic USB Burning Tool v3.2.8.exe | explorer.exe | ||||||||||||
User: admin Company: Amlogic, Inc. Integrity Level: MEDIUM Description: V3_Aml_Burn_Tool Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 4052 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://androiddatahost.com/au8bt" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
27 865
Read events
27 686
Write events
135
Delete events
44
Modification events
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31090656 | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31090656 | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
299
Suspicious files
120
Text files
76
Unknown types
29
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2920 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\84AFE219AEC53B0C9251F5E19EF019BD_2C9D5E6D83DF507CBE6C15521D5D3562 | binary | |
MD5:D9B2F49553884778A0F682A83321C576 | SHA256:0458989634E3B38F1A466C135155198F080B265FA71CE257E00F7601CD1CD291 | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A16C6C16D94F76E0808C087DFC657D99_279EB7E7074697CADB0A3844954F1B7D | binary | |
MD5:F3B3B97C64905DD19D6EA1E37FF3AF86 | SHA256:38AECAC24524CB24E7DFEECBA9C3BD54006C5BE8BA8E9CBAE0F0893CBC23FC66 | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\84AFE219AEC53B0C9251F5E19EF019BD_2C9D5E6D83DF507CBE6C15521D5D3562 | binary | |
MD5:2AF33D02FCBA44CFBC4472BD56909EF3 | SHA256:9482C49F918FFD2D561E7B37278A57892DD49114E6F6D23D6A2BB62ECA54E3B8 | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\au8bt[1].htm | html | |
MD5:0ABB0ED1C01A749AFEBE63CF013FE9AF | SHA256:7F73DC1F70596C5C15CB3E81A6348816981525715A7DEF0502B5CF7D503F3FC0 | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\analytics[1].js | text | |
MD5:575B5480531DA4D14E7453E2016FE0BC | SHA256:DE36E50194320A7D3EF1ACE9BD34A875A8BD458B253C061979DD628E9BF49AFD | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:6F671AB5ACDF8D8EFF19B7F6FA14536D | SHA256:CE8F36F6A2793B4B802C99613B25F5966DF2776BB796B6E71B4FA62DCF83EE31 | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\V4ERP3DH.txt | text | |
MD5:CFC59744FBE43ACADDE3345ACC9FC8F3 | SHA256:A5C8FABA18AC56109D4FA1A528A50E37320092E6459B94954B568DACFF9A64C7 | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\DOMStore\DOTBATAV\androiddatahost[1].xml | text | |
MD5:C1DDEA3EF6BBEF3E7060A1A9AD89E4C5 | SHA256:B71E4D17274636B97179BA2D97C742735B6510EB54F22893D3A2DAFF2CEB28DB | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F07644E38ED7C9F37D11EEC6D4335E02_E8AB3F6B94D563A8B6A387168D3E7B81 | binary | |
MD5:D1C12EDF8815173AA00B85438A54D402 | SHA256:3901B2F4BE7C5B603DF6E8BD6AC374AE0BDCD0A78949ABB449E57FE445DEC28A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
65
DNS requests
31
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2920 | iexplore.exe | GET | 304 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d362edf7b65e9a48 | unknown | — | — | unknown |
2920 | iexplore.exe | GET | 304 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?927e0d673a39dd41 | unknown | — | — | unknown |
2920 | iexplore.exe | GET | 200 | 192.124.249.24:80 | http://ocsp.starfieldtech.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQUwPiEZQ6%2FsVZNPaFToNfxx8ZwqAQUfAwyH6fZMH%2FEfWijYqihzqsHWycCAQc%3D | unknown | binary | 2.05 Kb | unknown |
2920 | iexplore.exe | GET | 200 | 192.124.249.24:80 | http://ocsp.starfieldtech.com//MEowSDBGMEQwQjAJBgUrDgMCGgUABBT1ZqtwV0O1KcYi0gdzcFkHM%2BuArAQUJUWBaFAmOD07LSy%2BzWrZtj2zZmMCCQDmZP4f8TnvHA%3D%3D | unknown | binary | 2.10 Kb | unknown |
2920 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
2920 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
2920 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEH1ZfRmkcbmIEJt1GKpWSOU%3D | unknown | binary | 471 b | unknown |
2920 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGHsycmQas7CCZXEOfu%2B%2Bqs%3D | unknown | binary | 471 b | unknown |
2920 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDDidhelLJLaQnsKqlsZYpa | unknown | binary | 472 b | unknown |
4052 | iexplore.exe | GET | 304 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bdc5ae628aaf0bd4 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2920 | iexplore.exe | 192.124.249.38:443 | androiddatahost.com | SUCURI-SEC | US | unknown |
2920 | iexplore.exe | 184.24.77.194:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2920 | iexplore.exe | 192.124.249.24:80 | ocsp.starfieldtech.com | SUCURI-SEC | US | unknown |
2920 | iexplore.exe | 142.250.181.226:443 | pagead2.googlesyndication.com | GOOGLE | US | whitelisted |
2920 | iexplore.exe | 142.250.185.238:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
2920 | iexplore.exe | 172.217.16.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2920 | iexplore.exe | 142.250.186.72:443 | www.googletagmanager.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
androiddatahost.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.starfieldtech.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
googleads.g.doubleclick.net |
| whitelisted |
fundingchoicesmessages.google.com |
| whitelisted |
lh3.googleusercontent.com |
| whitelisted |