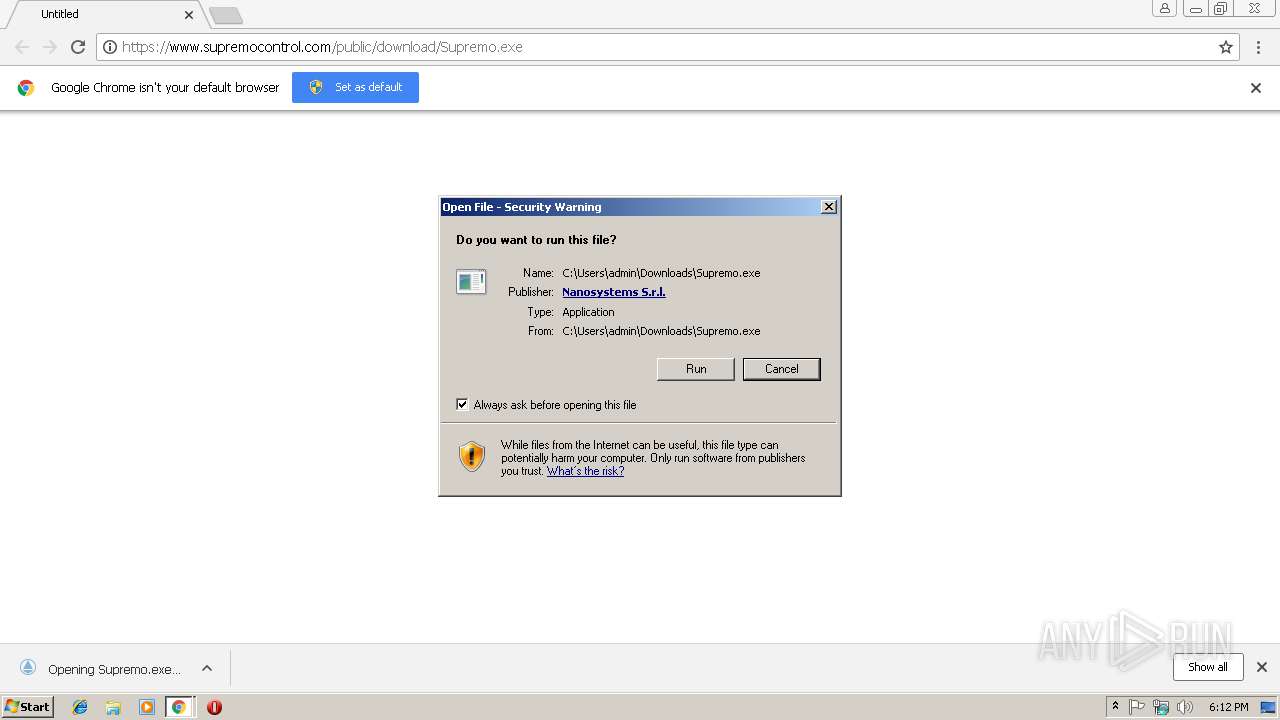
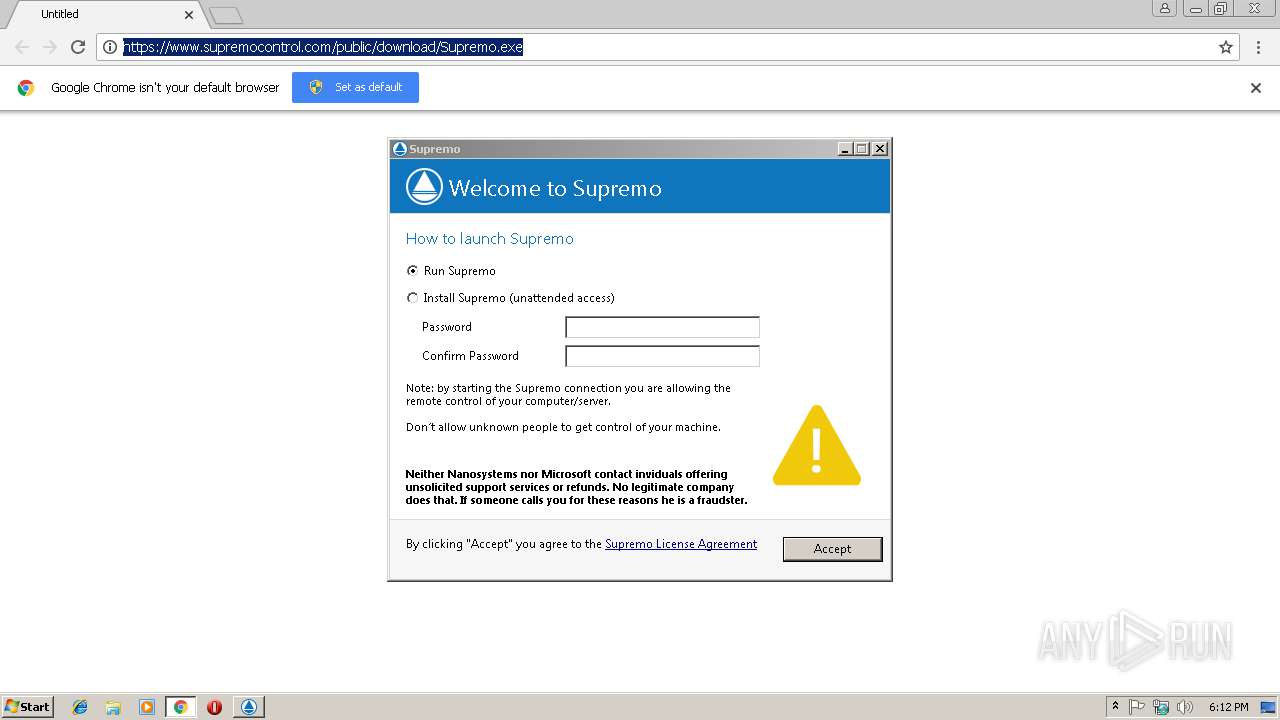
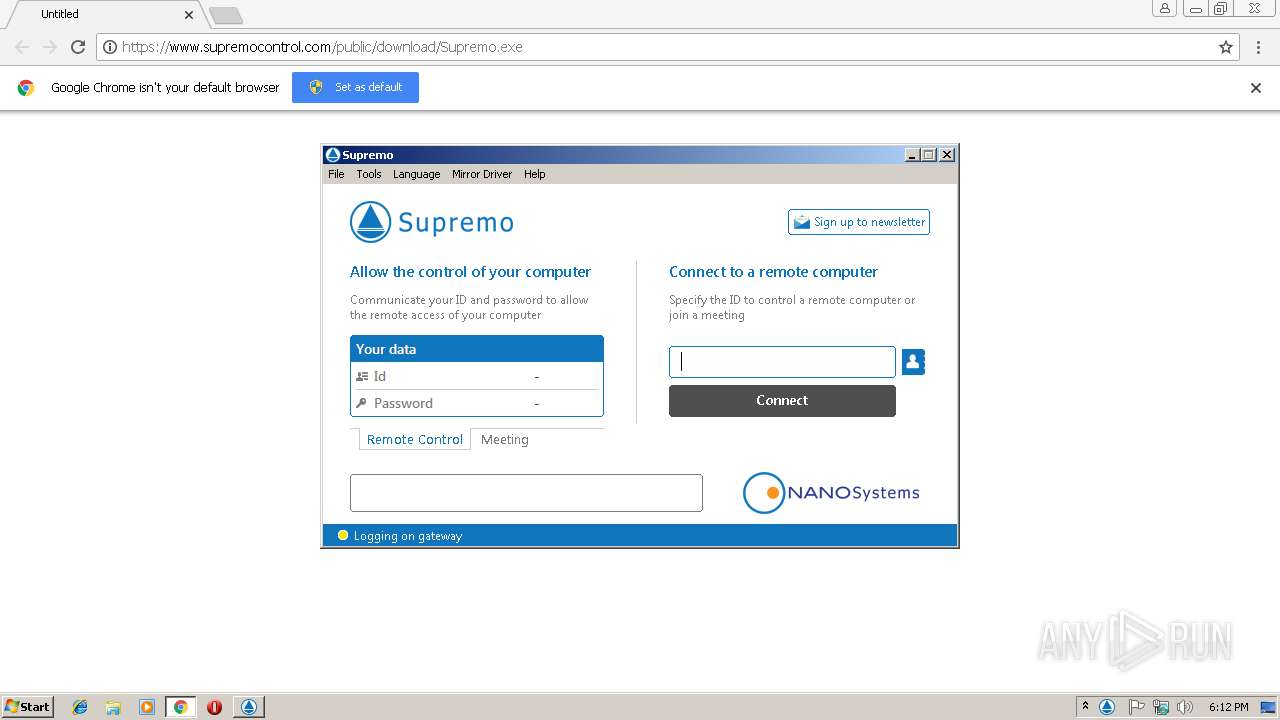
| URL: | https://www.supremocontrol.com/public/download/Supremo.exe |
| Full analysis: | https://app.any.run/tasks/c479bee2-f64c-4f54-af33-8525ee4caa7a |
| Verdict: | Malicious activity |
| Analysis date: | January 03, 2019, 18:11:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | CDC3DBCE22EA400ACB3D534D03AC51AF |
| SHA1: | E05269A07BAC4ABA519FB715261E1DA341F6ABD6 |
| SHA256: | 803A00FF55B46382F2EA37805C69D54590090F1A4ACEC8762065E5BCBB6866FB |
| SSDEEP: | 3:N8DSLyIIlX+lQHJJ3eL4A:2OLbItHJdekA |
MALICIOUS
Application was dropped or rewritten from another process
- Supremo.exe (PID: 2352)
- Supremo.exe (PID: 3936)
- SupremoSystem.exe (PID: 3184)
- SupremoSystem.exe (PID: 2388)
- SupremoHelper.exe (PID: 2984)
Changes settings of System certificates
- Supremo.exe (PID: 3936)
LATENTBOT was detected
- Supremo.exe (PID: 3936)
Connects to CnC server
- Supremo.exe (PID: 3936)
SUSPICIOUS
Reads Windows Product ID
- Supremo.exe (PID: 2352)
Creates files in the program directory
- Supremo.exe (PID: 3936)
- Supremo.exe (PID: 2352)
Executable content was dropped or overwritten
- Supremo.exe (PID: 3936)
- chrome.exe (PID: 2816)
- Supremo.exe (PID: 2352)
Modifies the open verb of a shell class
- Supremo.exe (PID: 3936)
Removes files from Windows directory
- Supremo.exe (PID: 3936)
Creates files in the Windows directory
- Supremo.exe (PID: 3936)
Adds / modifies Windows certificates
- Supremo.exe (PID: 3936)
Checks for external IP
- Supremo.exe (PID: 3936)
INFO
Reads settings of System Certificates
- Supremo.exe (PID: 3936)
- chrome.exe (PID: 2816)
Application launched itself
- chrome.exe (PID: 2816)
Changes settings of System certificates
- chrome.exe (PID: 2816)
Reads Internet Cache Settings
- chrome.exe (PID: 2816)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
44
Monitored processes
13
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 972 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,9987952195804178757,15423214775214894844,131072 --enable-features=PasswordImport --service-pipe-token=DC9C3EDD48FAE28DBEF7029386D5F84E --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=DC9C3EDD48FAE28DBEF7029386D5F84E --renderer-client-id=4 --mojo-platform-channel-handle=1872 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,9987952195804178757,15423214775214894844,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=9BE3D58A2B1DE86F20BDFE21D948EAEA --mojo-platform-channel-handle=2400 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2352 | "C:\Users\admin\Downloads\Supremo.exe" | C:\Users\admin\Downloads\Supremo.exe | chrome.exe | ||||||||||||
User: admin Company: Nanosystems S.r.l. Integrity Level: MEDIUM Description: Supremo Exit code: 0 Version: 3.3.4.995 Modules
| |||||||||||||||
| 2388 | C:\Users\admin\AppData\Local\Temp\SupremoRemoteDesktop\SupremoSystem.exe | C:\Users\admin\AppData\Local\Temp\SupremoRemoteDesktop\SupremoSystem.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Nanosystems Srl Integrity Level: SYSTEM Description: Supremo System Exit code: 0 Version: 1.0.0.0000 Modules
| |||||||||||||||
| 2620 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1004,9987952195804178757,15423214775214894844,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=EF3224A180BB3EC36418894659820823 --mojo-platform-channel-handle=3896 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2796 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2820 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2816 | "C:\Program Files\Google\Chrome\Application\chrome.exe" https://www.supremocontrol.com/public/download/Supremo.exe | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2984 | C:\Windows\Temp\SupremoRemoteDesktop\SupremoHelper.exe | C:\Windows\Temp\SupremoRemoteDesktop\SupremoHelper.exe | — | Supremo.exe | |||||||||||
User: admin Company: Nanosystems S.r.l. Integrity Level: MEDIUM Description: Supremo Helper Exit code: 0 Version: 3.3.4.995 Modules
| |||||||||||||||
| 3184 | "C:\Users\admin\AppData\Local\Temp\SupremoRemoteDesktop\SupremoSystem.exe" "C:\Users\admin\Downloads\Supremo.exe" "/SYSRUN" | C:\Users\admin\AppData\Local\Temp\SupremoRemoteDesktop\SupremoSystem.exe | Supremo.exe | ||||||||||||
User: admin Company: Nanosystems Srl Integrity Level: HIGH Description: Supremo System Exit code: 0 Version: 1.0.0.0000 Modules
| |||||||||||||||
| 3240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,9987952195804178757,15423214775214894844,131072 --enable-features=PasswordImport --service-pipe-token=B8981CEDF72E3252EF56E9177B9C2305 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=B8981CEDF72E3252EF56E9177B9C2305 --renderer-client-id=3 --mojo-platform-channel-handle=2072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
1 283
Read events
1 204
Write events
76
Delete events
3
Modification events
| (PID) Process: | (2816) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2816) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2816) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2796) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2816-13191012743304875 |
Value: 259 | |||
| (PID) Process: | (2816) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2816) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2816) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (2816) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2816) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2816-13191012743304875 |
Value: 259 | |||
| (PID) Process: | (2816) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
4
Suspicious files
30
Text files
84
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\db06a69b-b6f6-45b5-b684-9a617fdb0f69.tmp | — | |
MD5:— | SHA256:— | |||
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\0660d59d-7b72-4ee9-b198-45518e00909b.tmp | — | |
MD5:— | SHA256:— | |||
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 3584 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:B59113C2DCD2D346F31A64F231162ADA | SHA256:1D97C69AEA85D3B06787458EA47576B192CE5C5DB9940E5EAA514FF977CE2DC2 | |||
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF1997d1.TMP | text | |
MD5:— | SHA256:— | |||
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF1997a2.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
26
DNS requests
16
Threats
22
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2816 | chrome.exe | GET | 200 | 104.107.210.17:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCECdm7lbrSfOOq9dwovyE3iI%3D | NL | der | 471 b | whitelisted |
3936 | Supremo.exe | POST | 200 | 51.75.144.32:80 | http://supremogw32.nanosystems.it/gatewaylist.php | GB | text | 1.65 Kb | suspicious |
2816 | chrome.exe | GET | 200 | 2.16.106.113:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCEAanQ4DU6%2F7UNbWj9%2BFqvdg%3D | unknown | der | 727 b | whitelisted |
3936 | Supremo.exe | POST | 200 | 51.77.9.172:443 | http://51.77.9.172:443/$rdgate?ACTION=HELLO&ID=NEW | GB | binary | 29 b | suspicious |
3936 | Supremo.exe | POST | 200 | 51.77.9.172:443 | http://51.77.9.172:443/$rdgate?ACTION=START&ID=2D5E9E93C4694FE9AC597F053C22C0DB | GB | binary | 29 b | suspicious |
3936 | Supremo.exe | POST | 200 | 51.77.9.172:443 | http://51.77.9.172:443/$rdgate?ID=2D5E9E93C4694FE9AC597F053C22C0DB | GB | binary | 14 b | suspicious |
3936 | Supremo.exe | POST | — | 51.77.9.172:443 | http://51.77.9.172:443/$rdgate?ID=2D5E9E93C4694FE9AC597F053C22C0DB | GB | — | — | suspicious |
3936 | Supremo.exe | POST | 200 | 51.77.9.172:443 | http://51.77.9.172:443/$rdgate?ID=2D5E9E93C4694FE9AC597F053C22C0DB | GB | text | 15 b | suspicious |
3936 | Supremo.exe | POST | 200 | 51.77.9.172:443 | http://51.77.9.172:443/$rdgate?ID=2D5E9E93C4694FE9AC597F053C22C0DB | GB | binary | 12 b | suspicious |
3936 | Supremo.exe | POST | 200 | 51.77.9.172:443 | http://51.77.9.172:443/$rdgate?ACTION=HELLO&ID=NEW | GB | binary | 26 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2816 | chrome.exe | 216.58.206.3:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2816 | chrome.exe | 151.80.237.21:443 | www.supremocontrol.com | OVH SAS | FR | suspicious |
2816 | chrome.exe | 172.217.22.13:443 | accounts.google.com | Google Inc. | US | whitelisted |
2816 | chrome.exe | 91.199.212.52:80 | crt.comodoca.com | Comodo CA Ltd | GB | suspicious |
2816 | chrome.exe | 104.107.210.17:80 | ocsp.usertrust.com | Akamai International B.V. | NL | whitelisted |
2816 | chrome.exe | 172.217.22.46:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
2816 | chrome.exe | 216.58.208.36:443 | www.google.com | Google Inc. | US | whitelisted |
2816 | chrome.exe | 216.58.210.3:80 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2816 | chrome.exe | 172.217.22.14:443 | clients4.google.com | Google Inc. | US | whitelisted |
3936 | Supremo.exe | 216.239.34.21:443 | ipinfo.io | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.supremocontrol.com |
| malicious |
clientservices.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
accounts.google.com |
| shared |
crt.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3936 | Supremo.exe | A Network Trojan was detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
3936 | Supremo.exe | Potential Corporate Privacy Violation | ET POLICY Possible External IP Lookup SSL Cert Observed (ipinfo.io) |
3936 | Supremo.exe | A Network Trojan was detected | MALWARE [PTsecurity] LatentBot HTTP POST Checkin |
3936 | Supremo.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3936 | Supremo.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3936 | Supremo.exe | A Network Trojan was detected | SUSPICIOUS [PTsecurity] eStream SQL Remote Desktop |
3936 | Supremo.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3936 | Supremo.exe | A Network Trojan was detected | SUSPICIOUS [PTsecurity] eStream SQL Remote Desktop |
3936 | Supremo.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3936 | Supremo.exe | A Network Trojan was detected | SUSPICIOUS [PTsecurity] eStream SQL Remote Desktop |
4 ETPRO signatures available at the full report