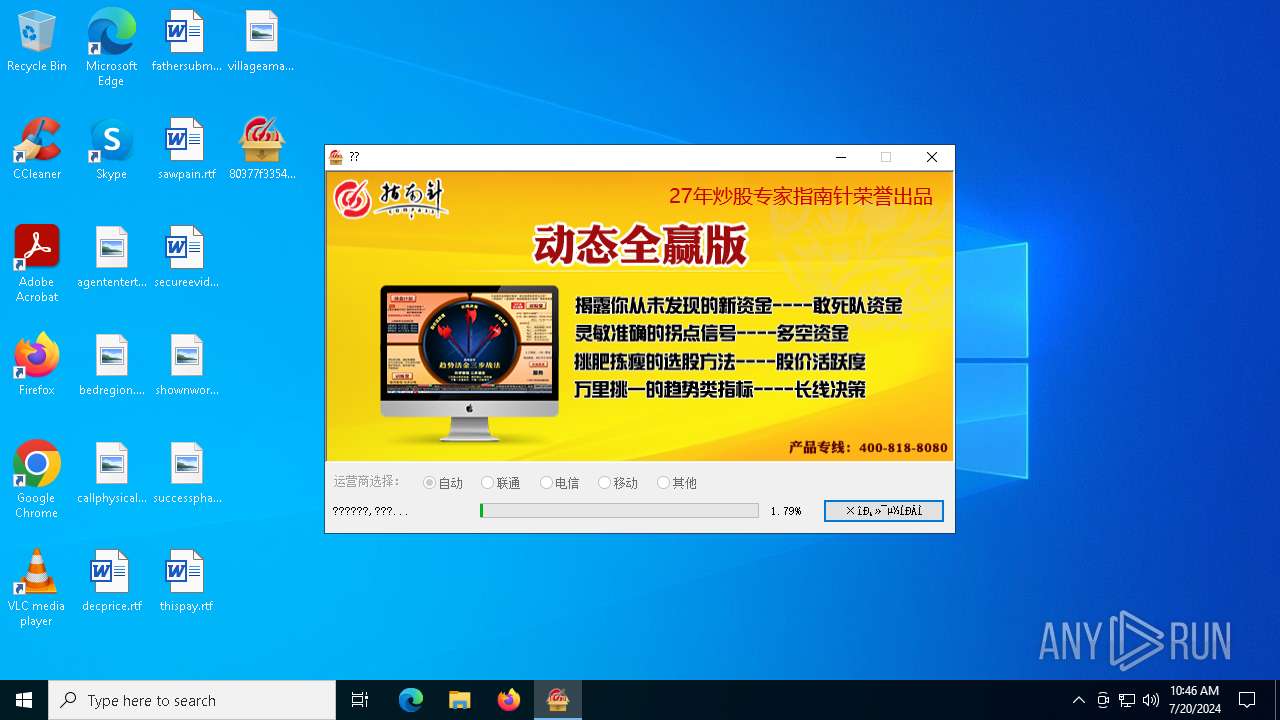
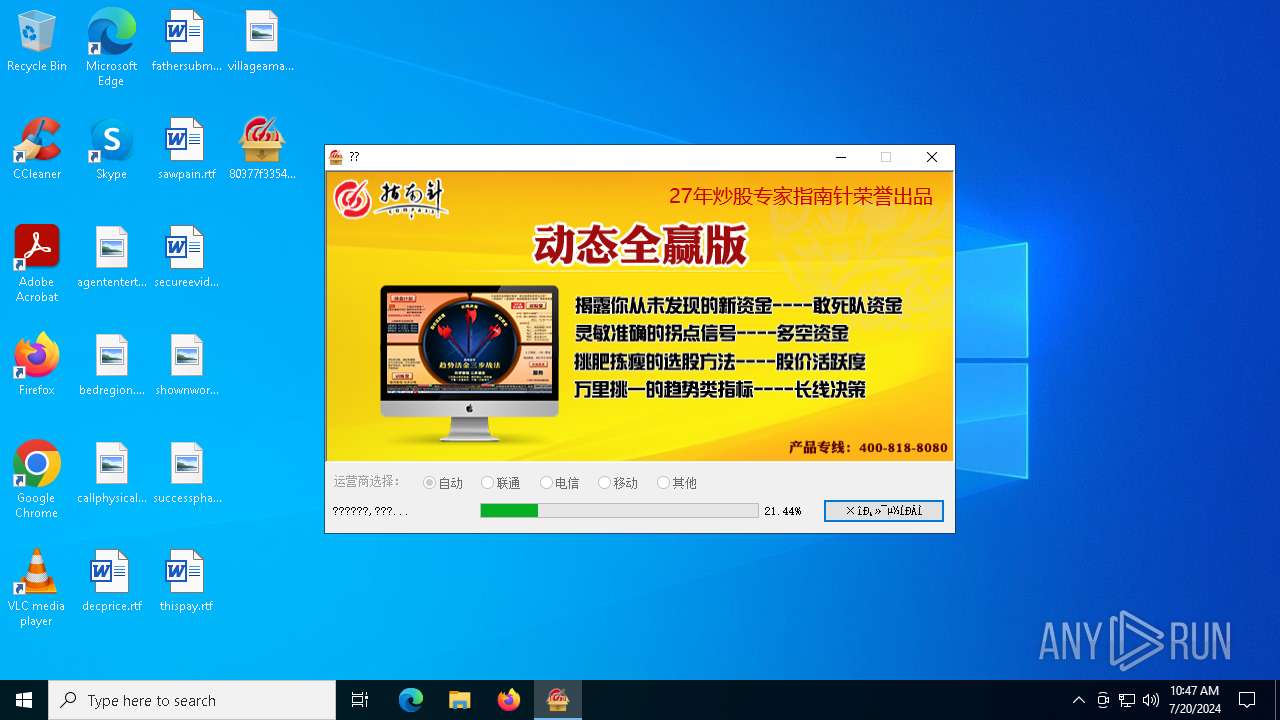
| File name: | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe |
| Full analysis: | https://app.any.run/tasks/714ca5df-5874-449f-8871-1be608cf109f |
| Verdict: | Malicious activity |
| Analysis date: | July 20, 2024, 10:45:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 73BCF4528162C221496131CF769F8609 |
| SHA1: | 181FE6005295BC58105E86BA571D5EC3D6B4D4C6 |
| SHA256: | 80377F3354DE3DA5B2BB94EB9EB4844C37BA25BBFDEACA6F4E398574528259A3 |
| SSDEEP: | 3072:MTrqjDCSr3c+uoIh6ltns1rbMLlGbbeD+4:MTrwrcb4GbaS4 |
MALICIOUS
Drops the executable file immediately after the start
- 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe (PID: 6148)
Scans artifacts that could help determine the target
- 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe (PID: 6148)
SUSPICIOUS
Reads security settings of Internet Explorer
- 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe (PID: 6148)
Reads Microsoft Outlook installation path
- 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe (PID: 6148)
Reads Internet Explorer settings
- 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe (PID: 6148)
Connects to unusual port
- 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe (PID: 6148)
Process requests binary or script from the Internet
- 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe (PID: 6148)
INFO
Checks supported languages
- 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe (PID: 6148)
Reads the computer name
- 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe (PID: 6148)
Process checks Internet Explorer phishing filters
- 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe (PID: 6148)
Checks proxy server information
- 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe (PID: 6148)
- slui.exe (PID: 7024)
Creates files or folders in the user directory
- 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe (PID: 6148)
Reads the software policy settings
- slui.exe (PID: 7024)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:01:30 09:14:02+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 66560 |
| InitializedDataSize: | 50176 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1072c |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 22.12.30.1 |
| ProductVersionNumber: | 22.12.30.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | upexLite Microsoft 基础类应用程序 |
| FileVersion: | 22, 12, 30, 1 |
| InternalName: | upexLite |
| LegalCopyright: | 版权所有 (C) 2012 |
| LegalTrademarks: | - |
| OriginalFileName: | upexLite.EXE |
| PrivateBuild: | - |
| ProductName: | upexLite 应用程序 |
| ProductVersion: | 22, 12, 30, 1 |
| SpecialBuild: | - |
Total processes
136
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6148 | "C:\Users\admin\Desktop\80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe" | C:\Users\admin\Desktop\80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: upexLite Microsoft 基础类应用程序 Version: 22, 12, 30, 1 Modules
| |||||||||||||||
| 7024 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 076
Read events
5 063
Write events
13
Delete events
0
Modification events
| (PID) Process: | (6148) 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6148) 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6148) 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6148) 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6148) 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6148) 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6148) 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6148) 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main\WindowsSearch |
| Operation: | write | Name: | Version |
Value: WS not running | |||
| (PID) Process: | (6148) 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
Executable files
1
Suspicious files
206
Text files
6
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | C:\Compass\WavMain\__upv3_temp\00000059.udp | binary | |
MD5:6757FDCFD061B6929F6803EE7BD3E64B | SHA256:43E6D21BB81C04DDC6999C6906FA49EEE8FF35E21A3735E3600F1C8D0D0F83E7 | |||
| 6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | C:\Compass\WavMain\__upv3_temp\00000066.udp | binary | |
MD5:FFABBC21DE4DCAD656765B43A696AF7C | SHA256:9BF37F2C9509C0C04EFB0237D3A022F98D4A4FDEA425F1D9E1D89DEEEBACF3BF | |||
| 6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\dispatcher[1].htm | html | |
MD5:AB0678F0DC202369267B489C08E1DEC6 | SHA256:A0102ADF9E1ED3D3A1775CDD8B4D7DDB7B22F2975B8A1E03FEC8CE37DA973F4F | |||
| 6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\dispatcher[2].htm | html | |
MD5:AB0678F0DC202369267B489C08E1DEC6 | SHA256:A0102ADF9E1ED3D3A1775CDD8B4D7DDB7B22F2975B8A1E03FEC8CE37DA973F4F | |||
| 6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | C:\Compass\WavMain\__upv3_temp\00000116.udp | binary | |
MD5:FB39BE75F1FE3475E963E7B8AB18910A | SHA256:F5165AE5292F1305B97C70F8586D6592EA3493D8EB104799FEB76998D3FCAFD3 | |||
| 6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | C:\Compass\WavMain\__upv3_temp\00000153.udp | binary | |
MD5:835B779C129C8BE408AD14744699DE50 | SHA256:00835B2DEC003F6B345E717D4877CF871F5BE6158286D9D6EE7CB5F58D1B0C05 | |||
| 6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | C:\Compass\WavMain\__upv3_temp\00000146.udp | binary | |
MD5:FF5607CD39DC20E5EDC91591D353776F | SHA256:FA812434796CF60E7D57CA1DDAB13691B1D9BCC70967F2015AC0F2ECF9F34F74 | |||
| 6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | C:\Compass\WavMain\__upv3_temp\00000145.udp | binary | |
MD5:74D24169DDF11E868E3395E6CB0542F0 | SHA256:20640ECB7B2FDD700DD84BC7027633CEB2E05B34A69C1B1ED5BE16C18C12434A | |||
| 6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | C:\Compass\WavMain\__upv3_temp\00000115.udp | binary | |
MD5:01C510A6BBD884B25F8DFCFE82D83FD3 | SHA256:FF65BBCDC8CF0928CC54F61683C7147BE56DF9563F58B31867A4B1BB95719858 | |||
| 6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | C:\Compass\WavMain\__upv3_temp\00000147.udp | binary | |
MD5:9A3BB1BA7A2E08D95EE2D6748A6D1878 | SHA256:A1D6FD1CD28B027CB3C125AFDE41A34D276400632337111C072561DEE16B1A14 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
52
DNS requests
20
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | GET | 200 | 49.233.125.252:80 | http://cweb.compass.cn/dispatcher/?action=install&gid=13&pid=5740&exename=80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe&step=0&channelid=1&ts=4370000 | unknown | — | — | unknown |
6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | GET | — | 180.76.118.5:80 | http://trace.compass.cn/ujs.php?v=36 | unknown | — | — | unknown |
6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | GET | — | 180.76.118.5:80 | http://trace.compass.cn/nohijack.js?v=36 | unknown | — | — | unknown |
6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | GET | 200 | 49.233.125.252:80 | http://cweb.compass.cn/dispatcher/?action=install&gid=13&pid=5740&exename=80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe&step=1&channelid=1&ts=4371593 | unknown | — | — | unknown |
6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | GET | 200 | 118.212.230.35:80 | http://image2-cdn.compass.cn/actions/install/13/background.jpg?v=14 | unknown | — | — | unknown |
6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | GET | 200 | 180.76.118.5:80 | http://trace.compass.cn/nohijack.js?v=36 | unknown | — | — | unknown |
6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | GET | 200 | 180.76.118.5:80 | http://trace.compass.cn/ujs.php?v=36 | unknown | — | — | unknown |
6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | GET | 200 | 183.240.240.35:80 | http://misc-cdn.compass.cn/cweb/js/jquery-1.11.1.min.js?v=14 | unknown | — | — | unknown |
— | — | GET | 304 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 13.85.23.206:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4716 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5620 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7856 | svchost.exe | 4.209.33.156:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | 49.233.125.252:80 | cweb.compass.cn | Shenzhen Tencent Computer Systems Company Limited | CN | unknown |
7484 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | 180.76.118.5:80 | trace.compass.cn | Beijing Baidu Netcom Science and Technology Co., Ltd. | CN | unknown |
6148 | 80377f3354de3da5b2bb94eb9eb4844c37ba25bbfdeaca6f4e398574528259a3.exe | 61.135.173.233:5215 | u3.compass.cn | China Unicom Beijing Province Network | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
cweb.compass.cn |
| unknown |
arc.msn.com |
| whitelisted |
misc-cdn.compass.cn |
| unknown |
image2-cdn.compass.cn |
| unknown |
trace.compass.cn |
| unknown |
u3.compass.cn |
| unknown |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |