| File name: | pclanding.exe |
| Full analysis: | https://app.any.run/tasks/a938d3af-fee4-413b-a026-5b525cf88de7 |
| Verdict: | Malicious activity |
| Analysis date: | August 31, 2024, 06:36:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 213415C0F31083BC016CDE4ED349B7A5 |
| SHA1: | 27EE2565F5E8C93A6A034CED7296F9157DC7B9D4 |
| SHA256: | 803246CAFB893B840C02DA8F263D67004683C00CD4245B24AFFE6E468832EF9F |
| SSDEEP: | 1536:V+ijrrYdu7Ol5Atf3ZvUZZYniZwqSDXBGSOcNQ4Wfr4NNgWf0:VbjvJ7Q4ZvU7Yi2qOGR4UBr |
MALICIOUS
Changes the autorun value in the registry
- moontonlauncher.exe (PID: 4132)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- WatcherofRealms_PC_Setup_v1.0.12.exe (PID: 1044)
Drops the executable file immediately after the start
- WatcherofRealms_PC_Setup_v1.0.12.exe (PID: 1044)
Starts CMD.EXE for commands execution
- WatcherofRealms_PC_Setup_v1.0.12.exe (PID: 1044)
- moontonlauncher.exe (PID: 4132)
The process creates files with name similar to system file names
- WatcherofRealms_PC_Setup_v1.0.12.exe (PID: 1044)
Executing commands from a ".bat" file
- WatcherofRealms_PC_Setup_v1.0.12.exe (PID: 1044)
Executable content was dropped or overwritten
- WatcherofRealms_PC_Setup_v1.0.12.exe (PID: 1044)
Drops 7-zip archiver for unpacking
- WatcherofRealms_PC_Setup_v1.0.12.exe (PID: 1044)
Checks for external IP
- curl.exe (PID: 2992)
- moontonlauncher.exe (PID: 4132)
Process drops legitimate windows executable
- WatcherofRealms_PC_Setup_v1.0.12.exe (PID: 1044)
Connects to unusual port
- curl.exe (PID: 2992)
- moontonlauncher.exe (PID: 4132)
The process drops C-runtime libraries
- WatcherofRealms_PC_Setup_v1.0.12.exe (PID: 1044)
Creates a software uninstall entry
- WatcherofRealms_PC_Setup_v1.0.12.exe (PID: 1044)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 5292)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 7096)
Uses WMIC.EXE to obtain operating system information
- moontonlauncher.exe (PID: 4132)
Uses WMIC.EXE to obtain CPU information
- moontonlauncher.exe (PID: 4132)
Starts POWERSHELL.EXE for commands execution
- moontonlauncher.exe (PID: 4132)
Starts NET.EXE to map network drives
- moontonlauncher.exe (PID: 4132)
Uses WMIC.EXE to obtain computer system information
- moontonlauncher.exe (PID: 4132)
Uses WMIC.EXE to obtain user accounts information
- moontonlauncher.exe (PID: 4132)
Get information on the list of running processes
- moontonlauncher.exe (PID: 4132)
There is functionality for taking screenshot (YARA)
- moontonlauncher.exe (PID: 4132)
Uses WMIC.EXE
- cmd.exe (PID: 5376)
INFO
Reads the computer name
- WatcherofRealms_PC_Setup_v1.0.12.exe (PID: 1044)
- pclanding.exe (PID: 2180)
- curl.exe (PID: 2992)
- moontonlauncher.exe (PID: 4132)
- logger.exe (PID: 4444)
Checks supported languages
- pclanding.exe (PID: 2180)
- curl.exe (PID: 2992)
- WatcherofRealms_PC_Setup_v1.0.12.exe (PID: 1044)
- logger.exe (PID: 4444)
- moontonlauncher.exe (PID: 4132)
Reads the software policy settings
- pclanding.exe (PID: 2180)
- moontonlauncher.exe (PID: 4132)
- slui.exe (PID: 6556)
Create files in a temporary directory
- WatcherofRealms_PC_Setup_v1.0.12.exe (PID: 1044)
Creates files in the program directory
- WatcherofRealms_PC_Setup_v1.0.12.exe (PID: 1044)
- moontonlauncher.exe (PID: 4132)
Manual execution by a user
- moontonlauncher.exe (PID: 4132)
- moontonlauncher.exe (PID: 892)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7096)
- WMIC.exe (PID: 6456)
- WMIC.exe (PID: 2520)
- WMIC.exe (PID: 5772)
- WMIC.exe (PID: 2248)
- WMIC.exe (PID: 4040)
- WMIC.exe (PID: 4076)
- WMIC.exe (PID: 7120)
- WMIC.exe (PID: 2640)
- WMIC.exe (PID: 5712)
Checks proxy server information
- moontonlauncher.exe (PID: 4132)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3328)
Reads the machine GUID from the registry
- moontonlauncher.exe (PID: 4132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:12:20 06:03:07+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.35 |
| CodeSize: | 28160 |
| InitializedDataSize: | 47616 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6e5c |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
187
Monitored processes
54
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 740 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | Powershell.exe "Get-WmiObject Win32_Processor | select Description,Manufacturer,MaxClockSpeed,Name,NumberOfCores,SocketDesignation,NumberOfLogicalProcessors,L2CacheSize,L3CacheSize,Revision | fl" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | moontonlauncher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 892 | "C:\Program Files (x86)\Watcher of Realms\moontonlauncher.exe" | C:\Program Files (x86)\Watcher of Realms\moontonlauncher.exe | — | explorer.exe | |||||||||||
User: admin Company: com.moonton.muf Integrity Level: MEDIUM Description: launcher Exit code: 3221226540 Version: 1.0.12 Modules
| |||||||||||||||
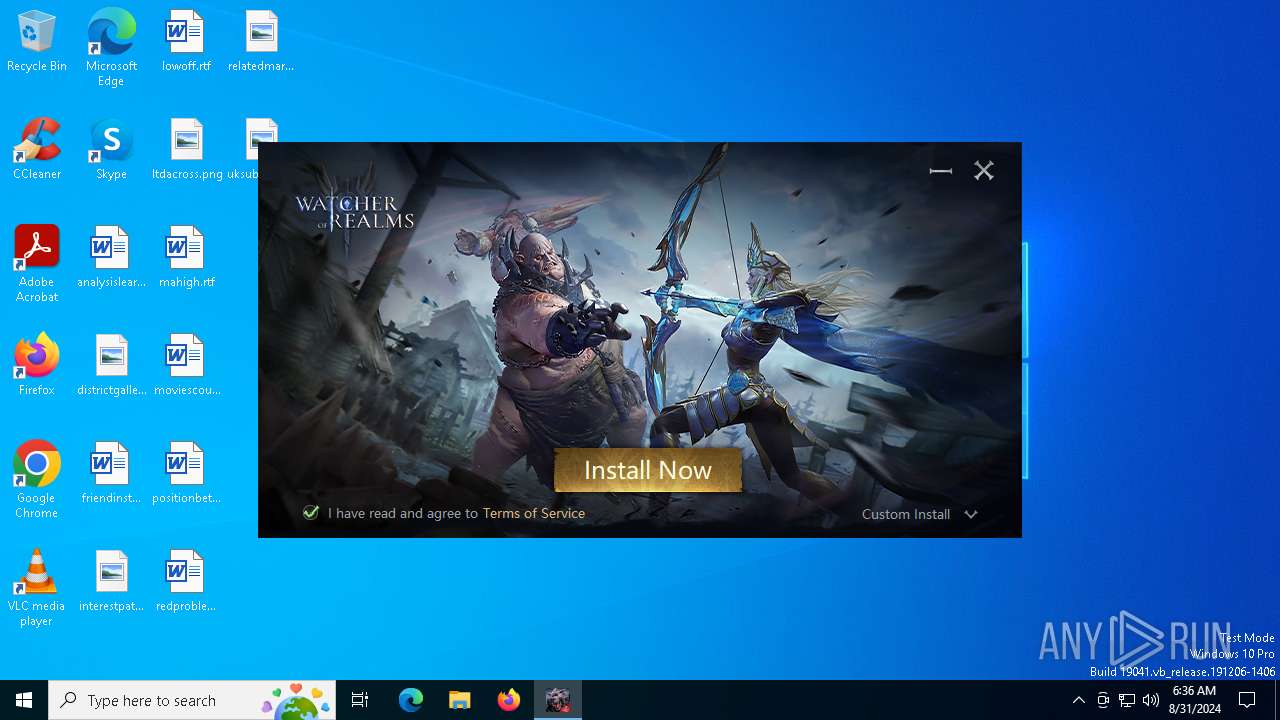
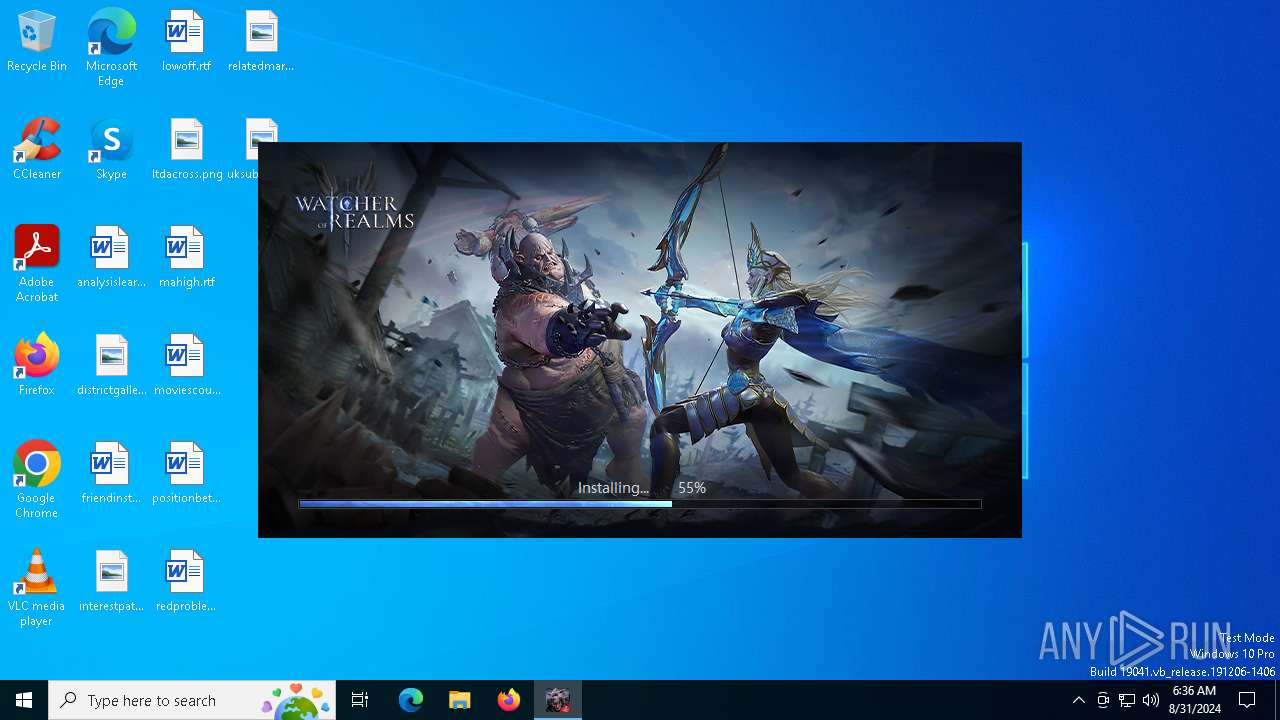
| 1044 | "WatcherofRealms_PC_Setup_v1.0.12.exe" | C:\Users\admin\AppData\Local\Temp\WatcherofRealms_PC_Setup_v1.0.12.exe | pclanding.exe | ||||||||||||
User: admin Company: Moonton Integrity Level: HIGH Description: Watcher of Realms Exit code: 0 Version: 0.0.0.1 Modules
| |||||||||||||||
| 1076 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1104 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1360 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tasklist.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1448 | Powershell.exe "Get-CimInstance -Namespace root\WMI -ClassName WmiMonitorConnectionParams | fl" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | moontonlauncher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1840 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
52 642
Read events
52 629
Write events
12
Delete events
1
Modification events
| (PID) Process: | (2180) pclanding.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Watcher of Realms |
| Operation: | write | Name: | Watcher_Of_Reaml_ClidId |
Value: pclanding | |||
| (PID) Process: | (1044) WatcherofRealms_PC_Setup_v1.0.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\WOR_PC |
| Operation: | write | Name: | shortcut |
Value: true | |||
| (PID) Process: | (1044) WatcherofRealms_PC_Setup_v1.0.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 12 | |||
| (PID) Process: | (1044) WatcherofRealms_PC_Setup_v1.0.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Watcher of Realms |
Value: | |||
| (PID) Process: | (1044) WatcherofRealms_PC_Setup_v1.0.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\WOR_PC |
| Operation: | write | Name: | autorun |
Value: false | |||
| (PID) Process: | (1044) WatcherofRealms_PC_Setup_v1.0.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\WOR_PC |
| Operation: | write | Name: | InstPath |
Value: C:\Program Files (x86)\Watcher of Realms | |||
| (PID) Process: | (1044) WatcherofRealms_PC_Setup_v1.0.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\WOR_PC |
| Operation: | write | Name: | LanguageID |
Value: 1033 | |||
| (PID) Process: | (1044) WatcherofRealms_PC_Setup_v1.0.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\WOR_PC |
| Operation: | write | Name: | DisplayName |
Value: Watcher of Realms | |||
| (PID) Process: | (1044) WatcherofRealms_PC_Setup_v1.0.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\WOR_PC |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files (x86)\Watcher of Realms\uninst.exe | |||
| (PID) Process: | (1044) WatcherofRealms_PC_Setup_v1.0.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\WOR_PC |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\Watcher of Realms\moontonlauncher.exe | |||
Executable files
30
Suspicious files
185
Text files
128
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2180 | pclanding.exe | C:\Users\admin\AppData\Local\Temp\WatcherofRealms_PC_Setup_v1.0.12.exe | — | |
MD5:— | SHA256:— | |||
| 1044 | WatcherofRealms_PC_Setup_v1.0.12.exe | C:\Program Files (x86)\Watcher of Realms\app.7z | — | |
MD5:— | SHA256:— | |||
| 1044 | WatcherofRealms_PC_Setup_v1.0.12.exe | C:\Program Files (x86)\Watcher of Realms\data\app.so | — | |
MD5:— | SHA256:— | |||
| 1044 | WatcherofRealms_PC_Setup_v1.0.12.exe | C:\Users\admin\AppData\Local\Temp\nso767.tmp\logger.exe | executable | |
MD5:5006FCAE24CB158D66EE851583CC8C3F | SHA256:ADA3DA64E792F72FFEA33682772CAD9DD53D4DF562DDFBB56E007A81F6E11ED5 | |||
| 1044 | WatcherofRealms_PC_Setup_v1.0.12.exe | C:\Users\admin\AppData\Local\Temp\nso767.tmp\licence_1033.rtf | text | |
MD5:606D179661061BE4F56D251DC8BD815B | SHA256:31DD0628D0799ADAB476FA2D124B366CC61FCDBAE8B35FAF214DFB28F4F74FFE | |||
| 1044 | WatcherofRealms_PC_Setup_v1.0.12.exe | C:\Users\admin\AppData\Local\Temp\nso767.tmp\licence_2052.rtf | text | |
MD5:2F9BE4592F28B531B7464762FE3A95B4 | SHA256:7DC2D01197D1364CE61EBF240F822E1590F793F89DA258E28449D69F3E761A16 | |||
| 1044 | WatcherofRealms_PC_Setup_v1.0.12.exe | C:\Users\admin\AppData\Local\Temp\nso767.tmp\global.ini | text | |
MD5:C2D0A642B94098190FDFA8169128414D | SHA256:996812A5341A397241D919E06D9E9B518E63DDFF30DB285CE5CD5D715652217C | |||
| 1044 | WatcherofRealms_PC_Setup_v1.0.12.exe | C:\Users\admin\AppData\Local\Temp\nso767.tmp\System.dll | executable | |
MD5:E38D8FF9F749EE1B141A122FEC7280E0 | SHA256:00F7604D4F36A728C7759F4D9CF3E30C9728C503557AAC49BBCD55CFC3E4FCB4 | |||
| 1044 | WatcherofRealms_PC_Setup_v1.0.12.exe | C:\Users\admin\AppData\Local\Temp\nso767.tmp\skin.zip | compressed | |
MD5:18F77BE545E98FBE8AF11180AD46E03A | SHA256:FB65A166ADD3B06D28A6959D67C314E643C98894D95ADEB48C9F11239A65440E | |||
| 1044 | WatcherofRealms_PC_Setup_v1.0.12.exe | C:\Users\admin\AppData\Local\Temp\nso767.tmp\logo.ico | image | |
MD5:3C8773FC596D2630ABCF322764936FA2 | SHA256:719D42608E0C3ACAD82CF551B1E8A76C65D3E5CE3D916D0AB811C0EBD10BAD6C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
72
DNS requests
21
Threats
25
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1828 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2636 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2636 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2992 | curl.exe | GET | 200 | 169.46.193.4:30220 | http://ip.ml.youngjoygame.com:30220/myip | unknown | — | — | suspicious |
4132 | moontonlauncher.exe | GET | 200 | 169.46.193.109:30220 | http://169.46.193.109:30220/myip?format= | unknown | — | — | unknown |
4132 | moontonlauncher.exe | GET | 200 | 2.19.126.219:80 | http://2.19.126.219:80/activity_pic/zglauncher/pc_pcfaq_all.jpg | unknown | — | — | unknown |
4132 | moontonlauncher.exe | HEAD | 200 | 2.19.126.219:80 | http://2.19.126.219:80/pc_res_version5/out/515.1/1.4.29.515.1.tgrp | unknown | — | — | unknown |
4132 | moontonlauncher.exe | GET | 200 | 169.46.193.47:30220 | http://169.46.193.47:30220/myip?format= | unknown | — | — | unknown |
4132 | moontonlauncher.exe | GET | 200 | 2.19.126.219:80 | http://2.19.126.219:80/activity_pic/zglauncher/icon_facebook_01.png | unknown | — | — | unknown |
4132 | moontonlauncher.exe | GET | 200 | 2.19.126.219:80 | http://2.19.126.219:80/activity_pic/zglauncher/global/dabaonu.jpg | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6420 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6056 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2180 | pclanding.exe | 104.16.111.63:443 | alxcdn.ztdheros.com | CLOUDFLARENET | — | unknown |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1828 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1828 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4324 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
alxcdn.ztdheros.com |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
ip.ml.youngjoygame.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2992 | curl.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |
4132 | moontonlauncher.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |
4132 | moontonlauncher.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |
22 ETPRO signatures available at the full report
Process | Message |
|---|---|
WatcherofRealms_PC_Setup_v1.0.12.exe | Window, size, 764,396
|
WatcherofRealms_PC_Setup_v1.0.12.exe | Window, sizebox, 0,0,0,0
|
WatcherofRealms_PC_Setup_v1.0.12.exe | Window, caption, 0,0,0,432
|
WatcherofRealms_PC_Setup_v1.0.12.exe | Window, bktrans, true
|
WatcherofRealms_PC_Setup_v1.0.12.exe | Window, forcegditext, true
|
WatcherofRealms_PC_Setup_v1.0.12.exe | ControlUI, padding, 354,85,0,0
|
WatcherofRealms_PC_Setup_v1.0.12.exe | ControlUI, width, 130
|
WatcherofRealms_PC_Setup_v1.0.12.exe | ControlUI, height, 130
|
WatcherofRealms_PC_Setup_v1.0.12.exe | ControlUI, bkimage, images\logo2.png
|
WatcherofRealms_PC_Setup_v1.0.12.exe | ControlUI, visible, false
|