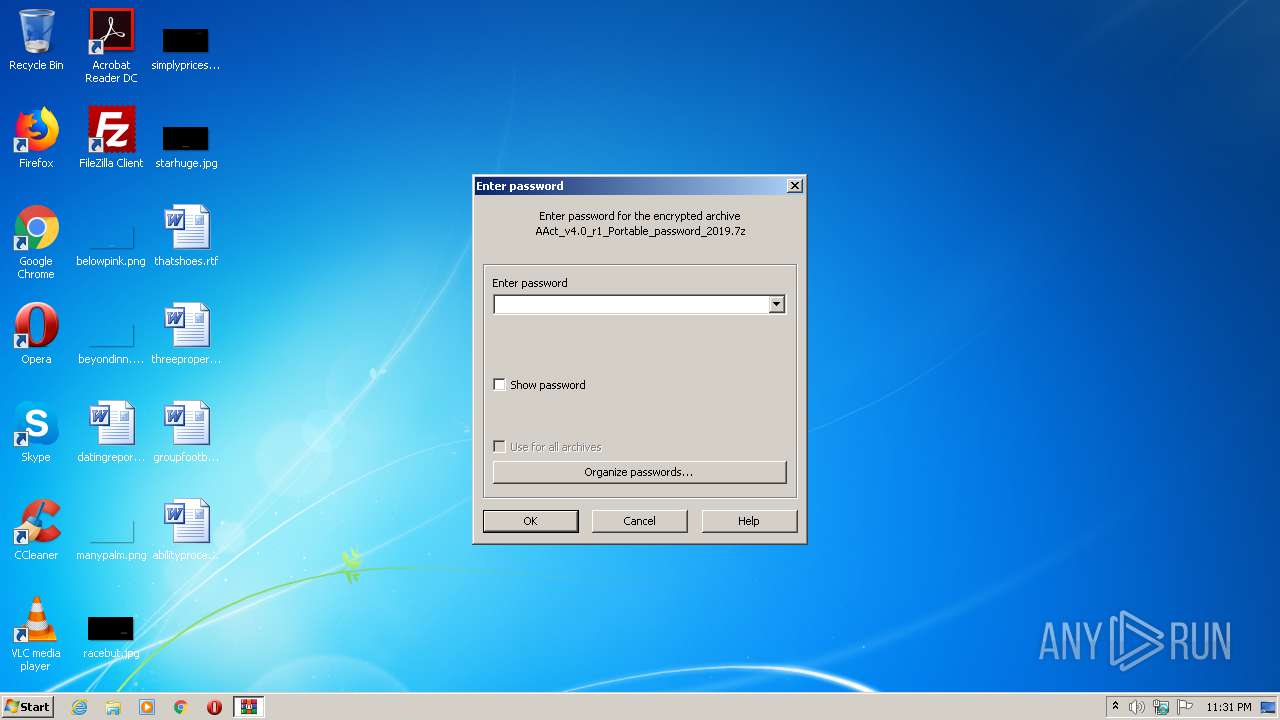
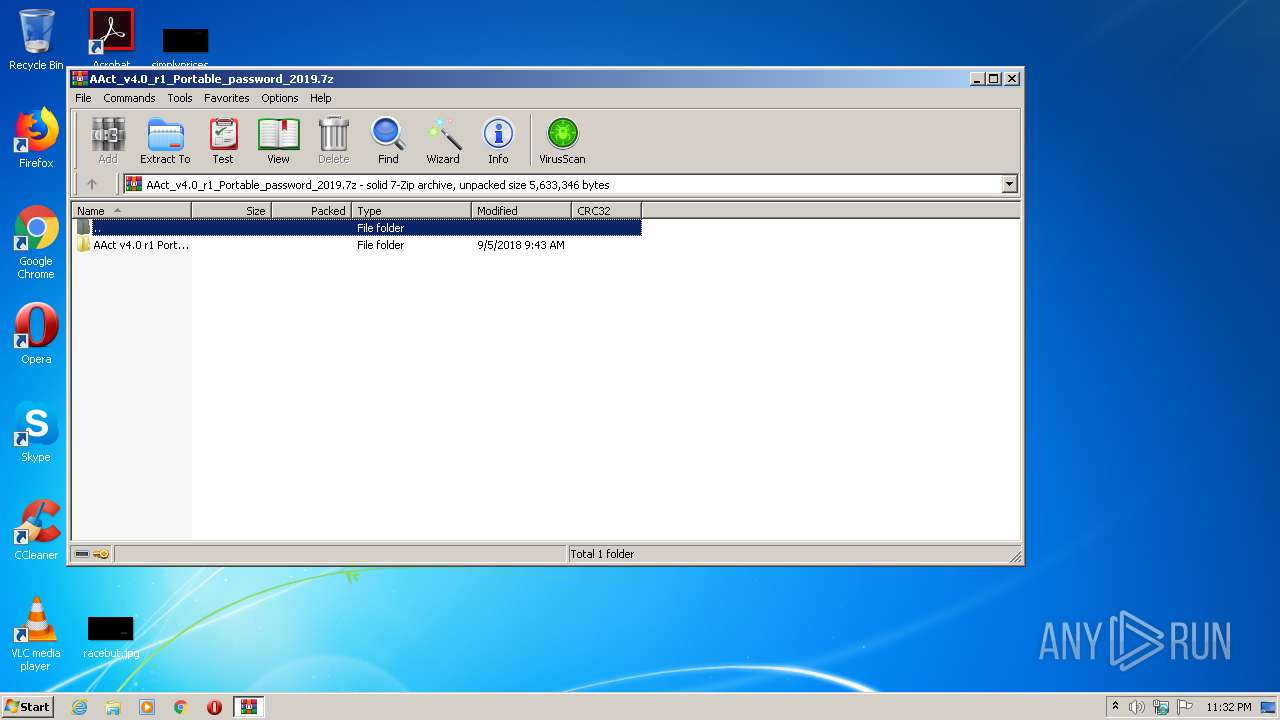
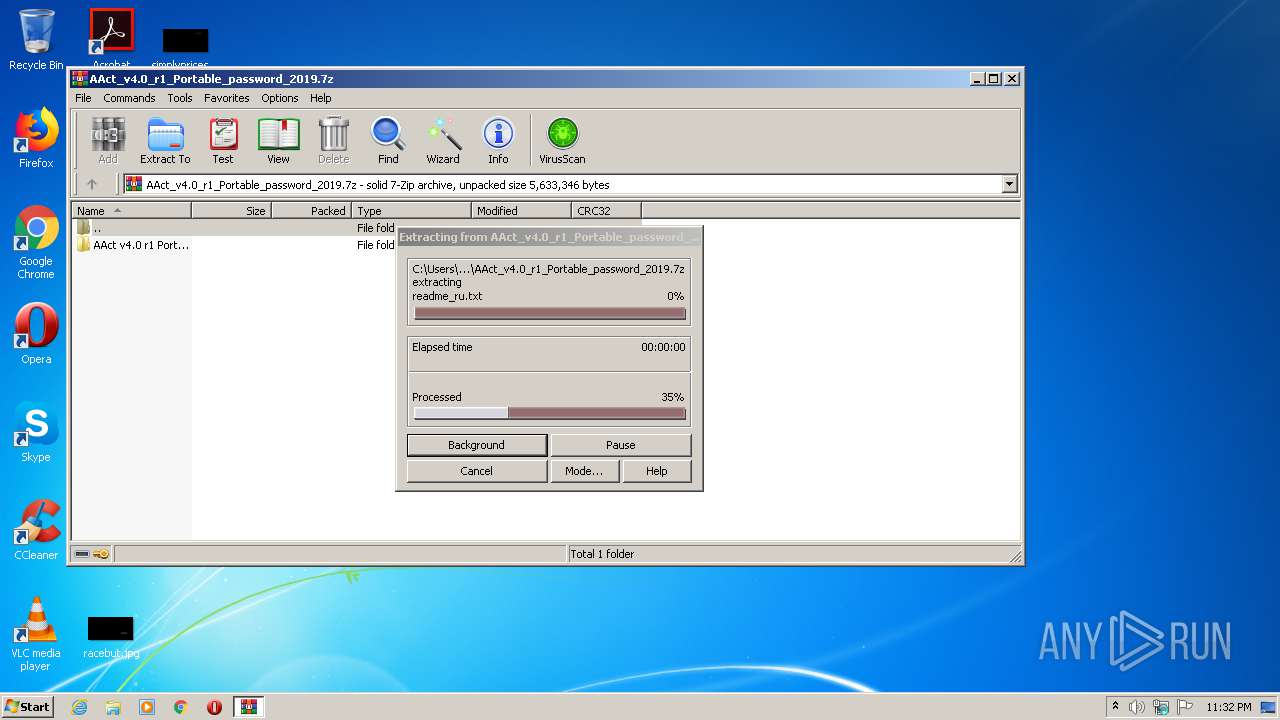
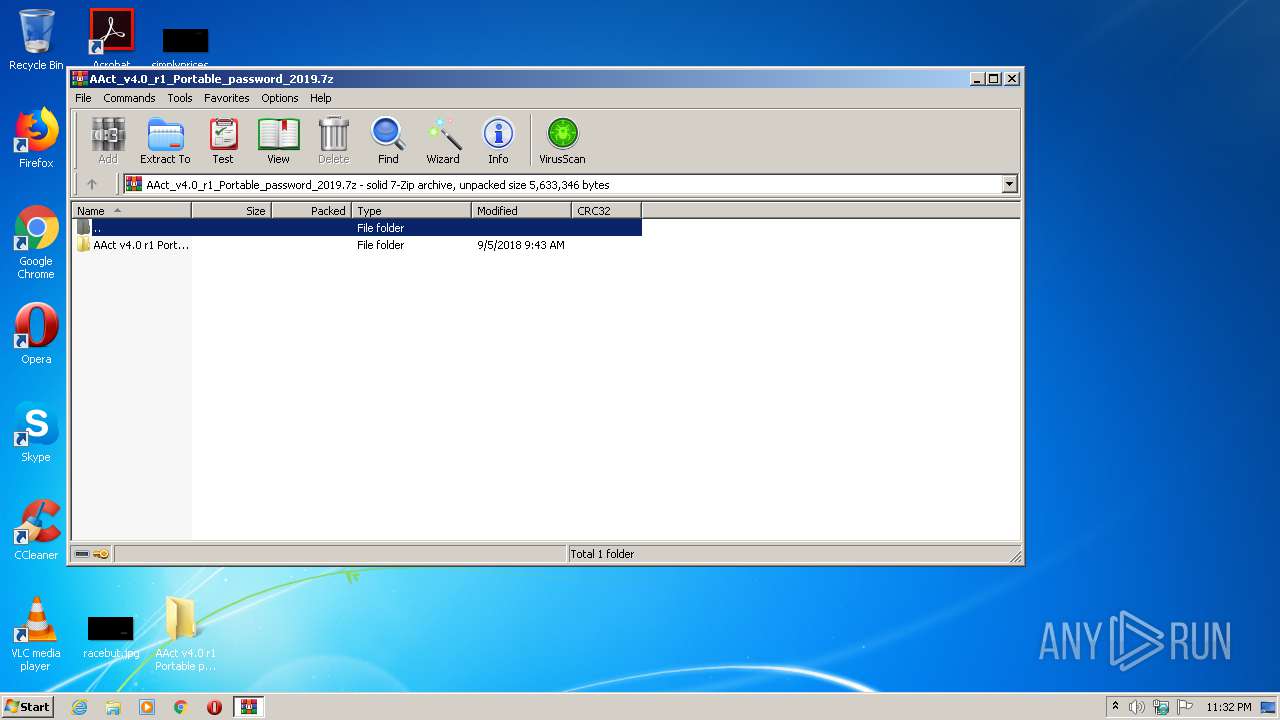
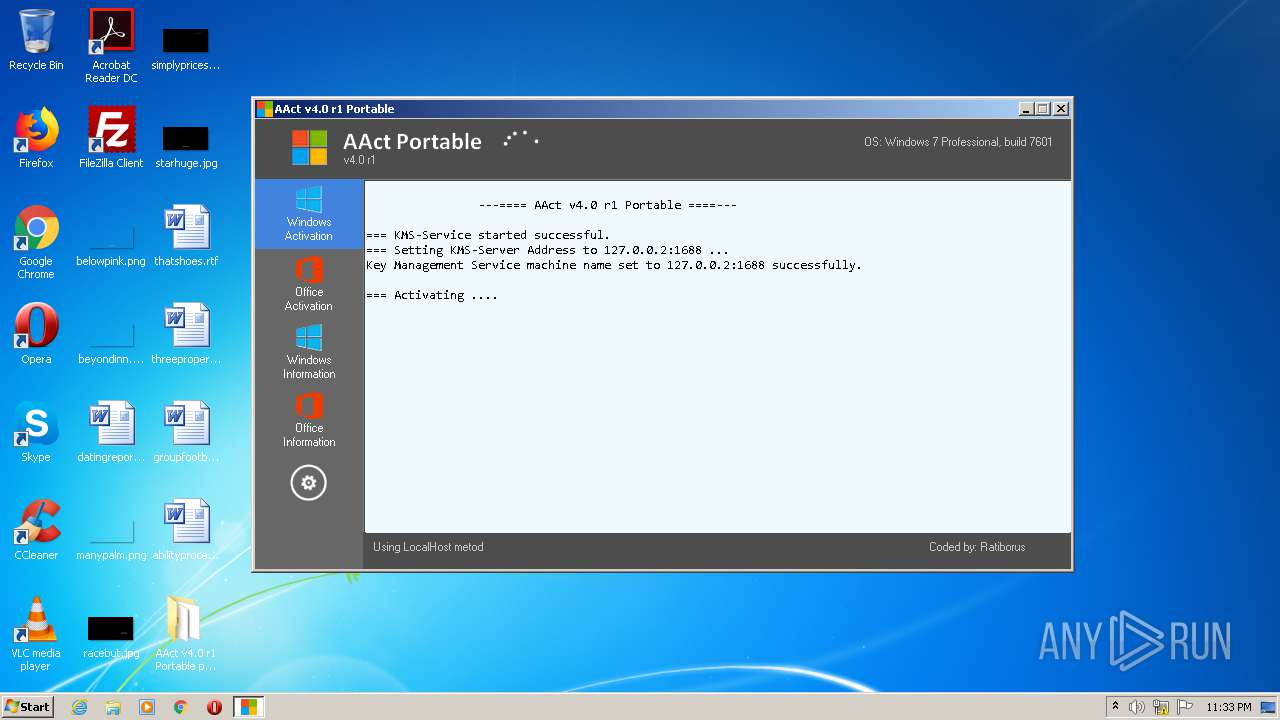
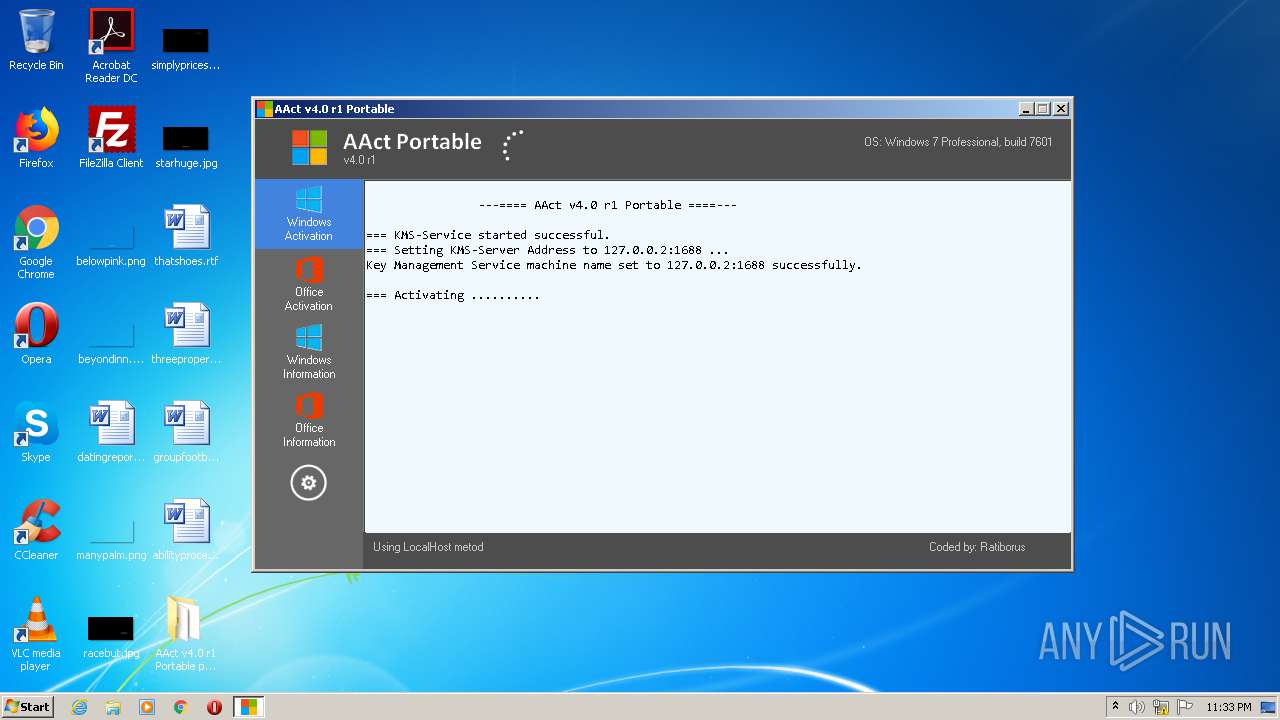
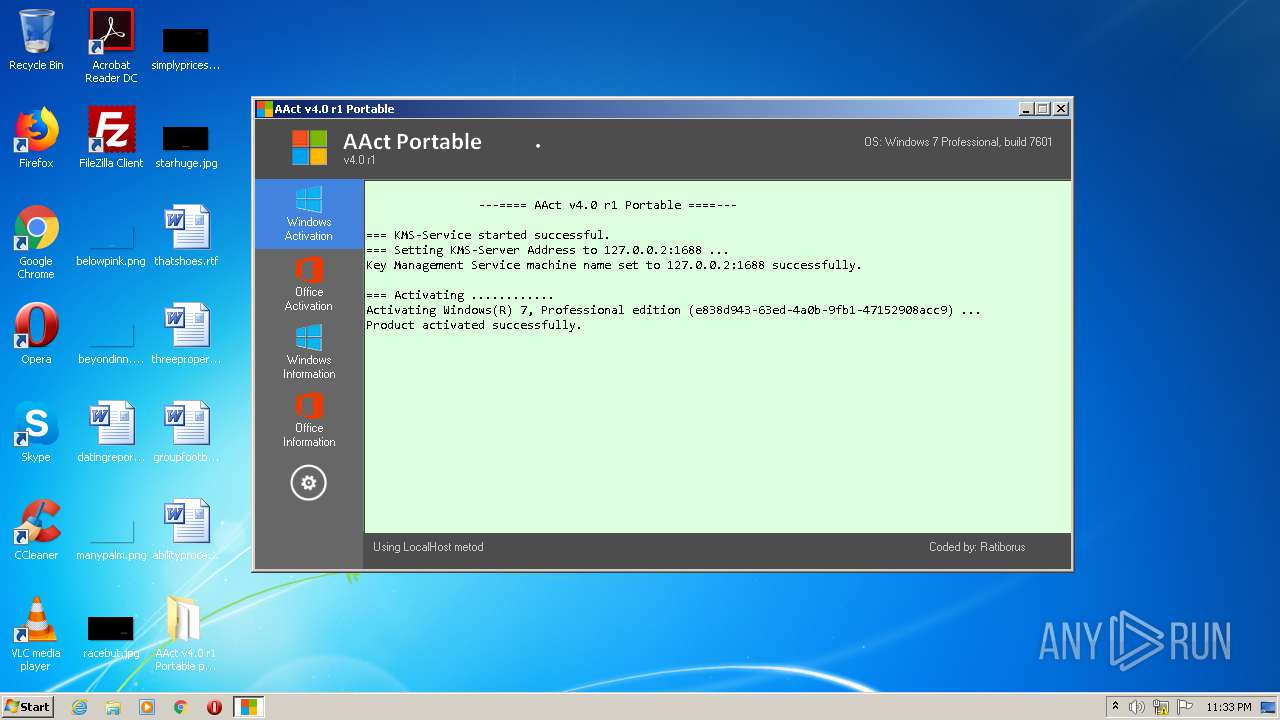
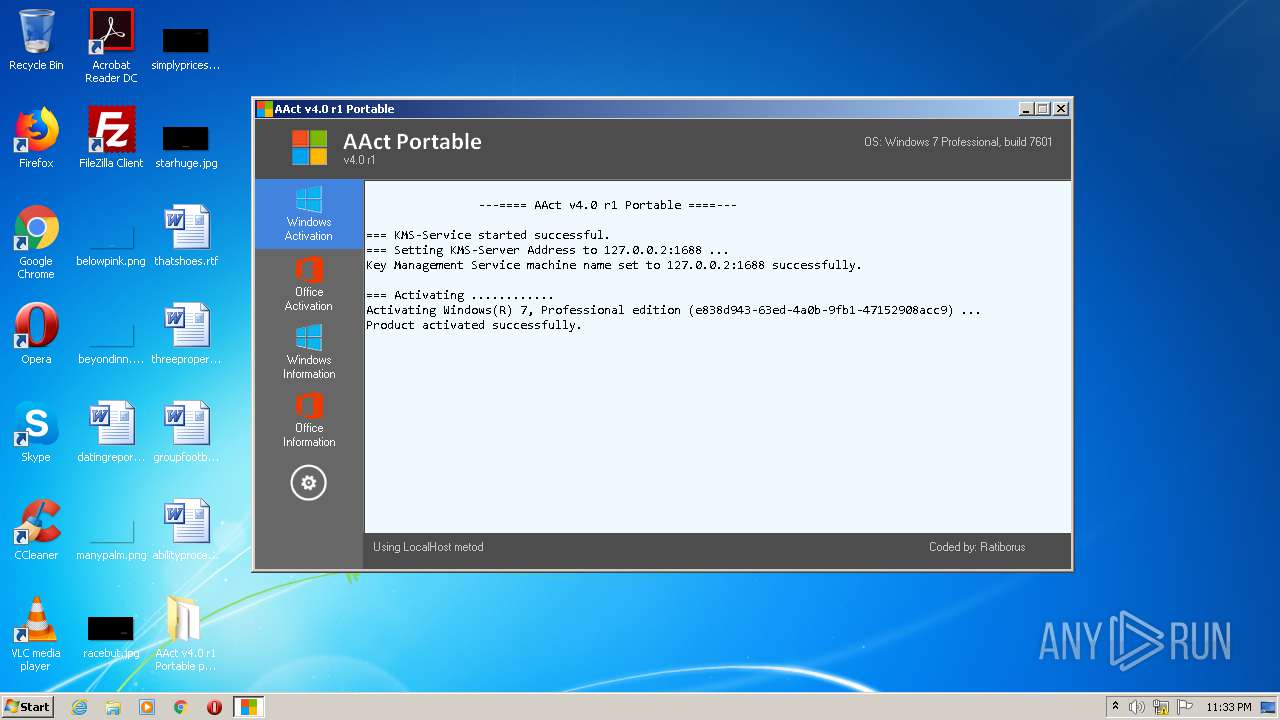
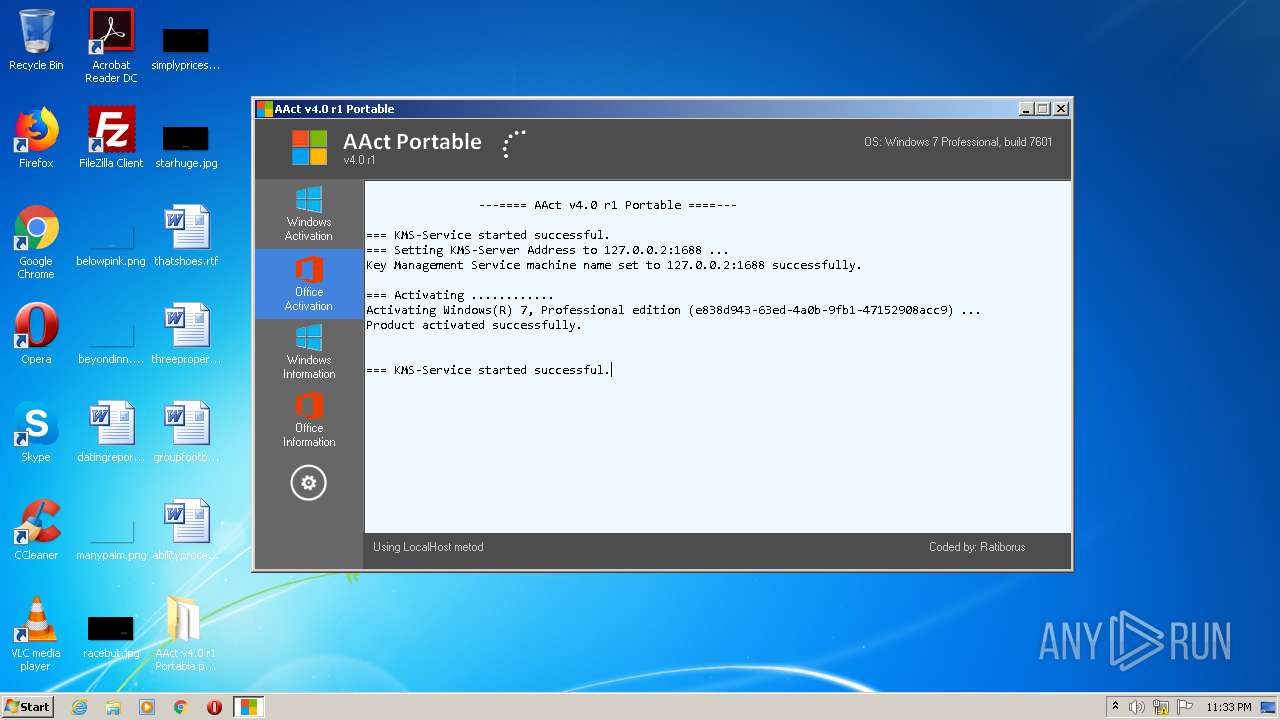
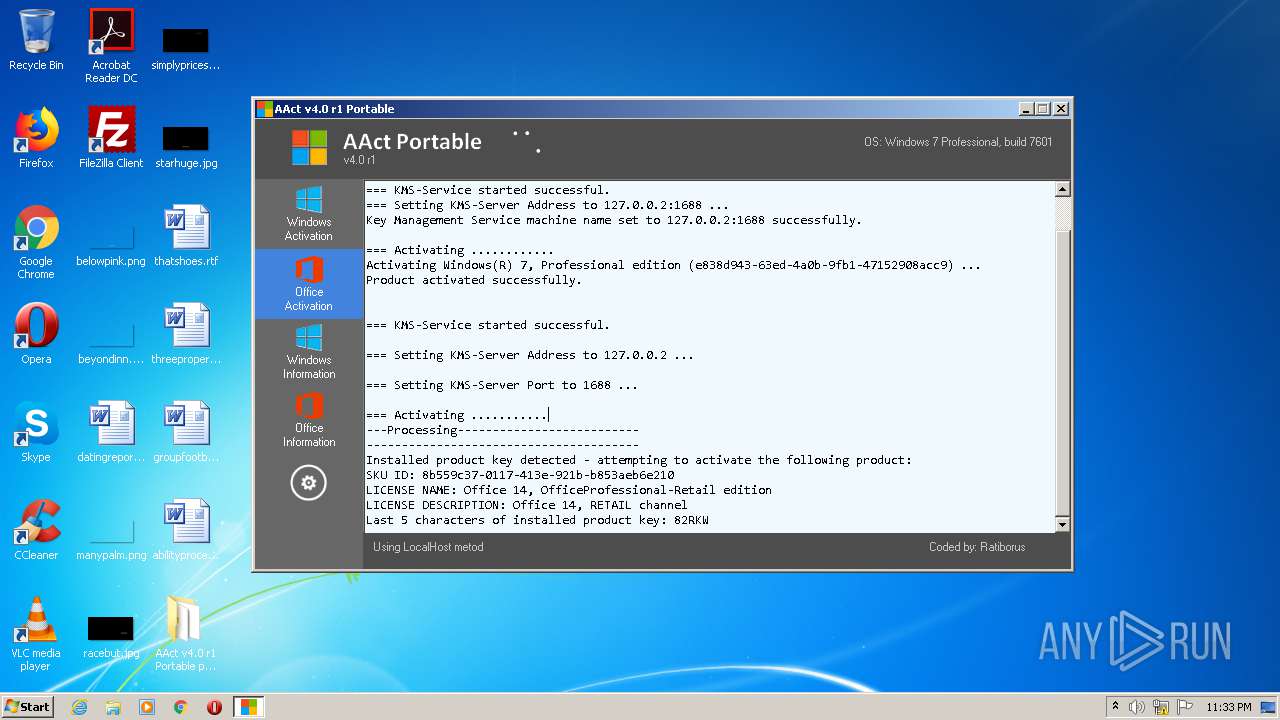
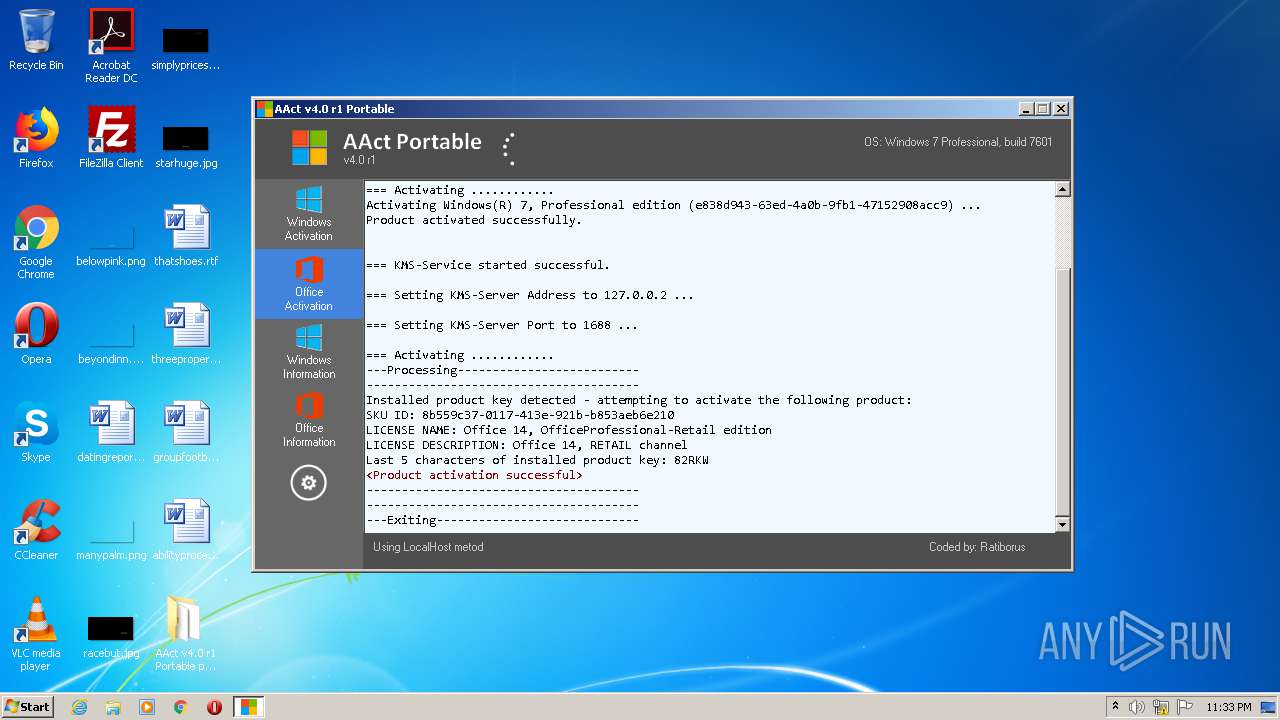
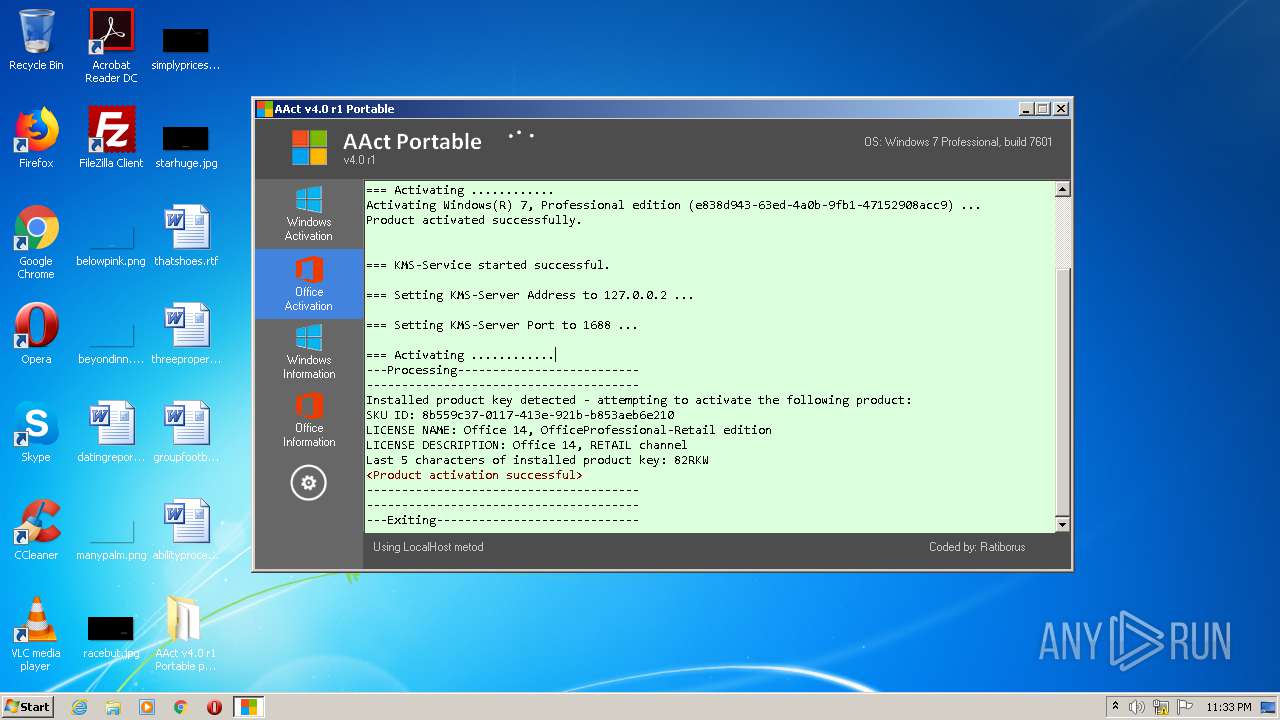
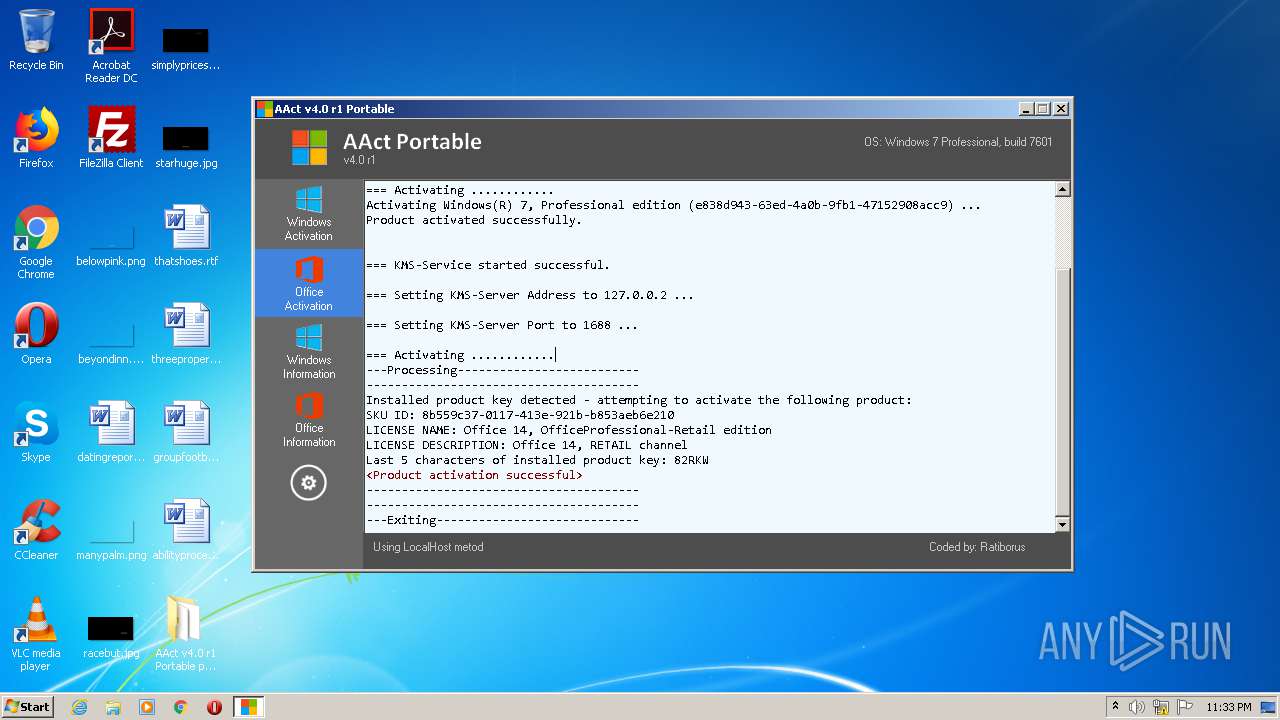
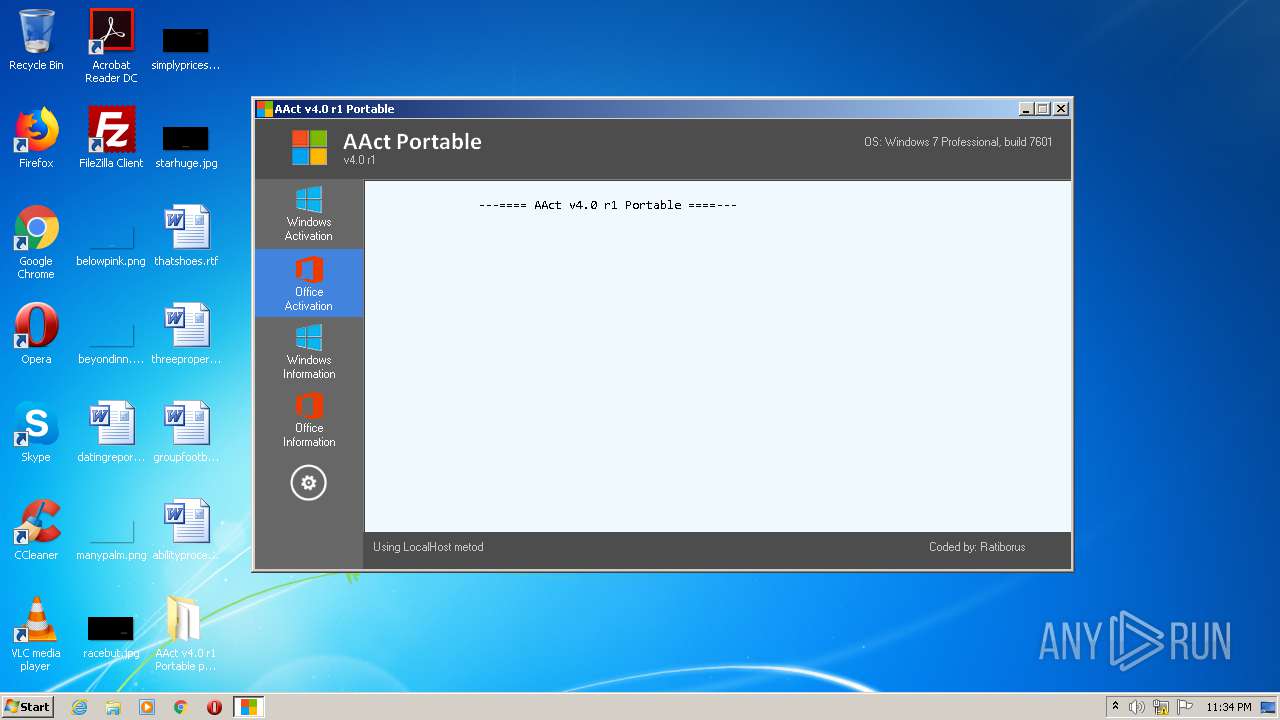
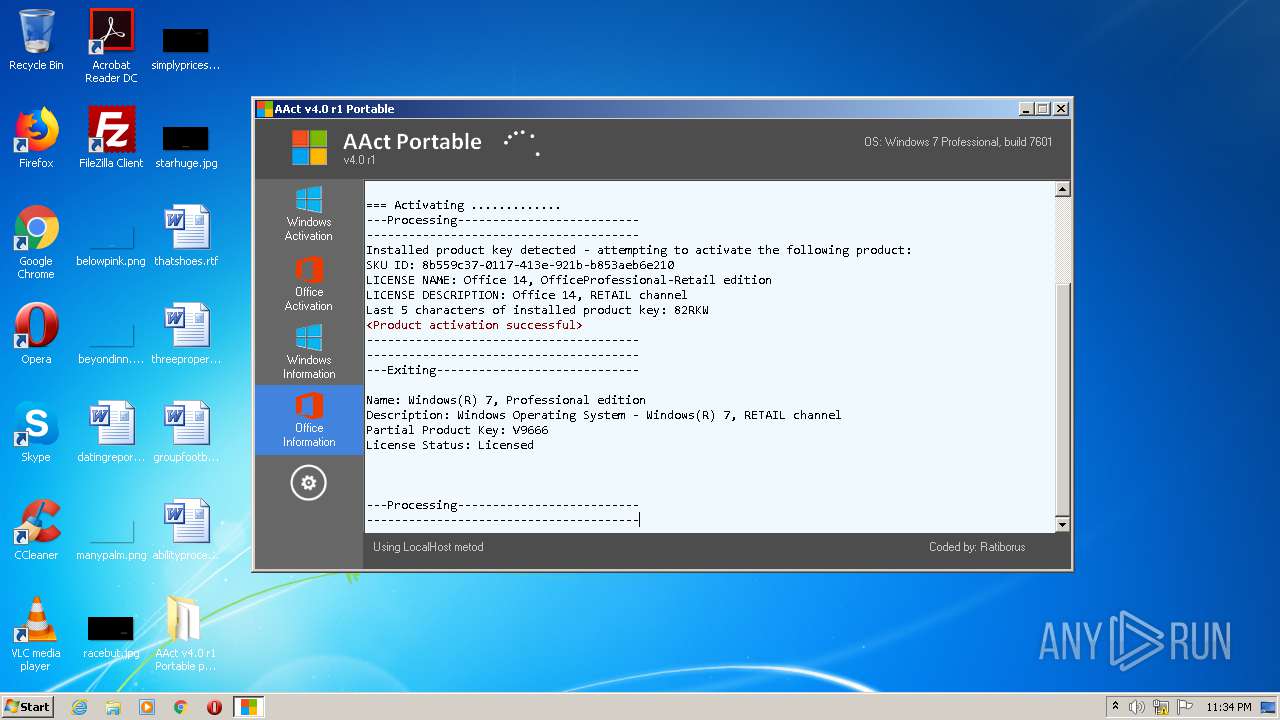
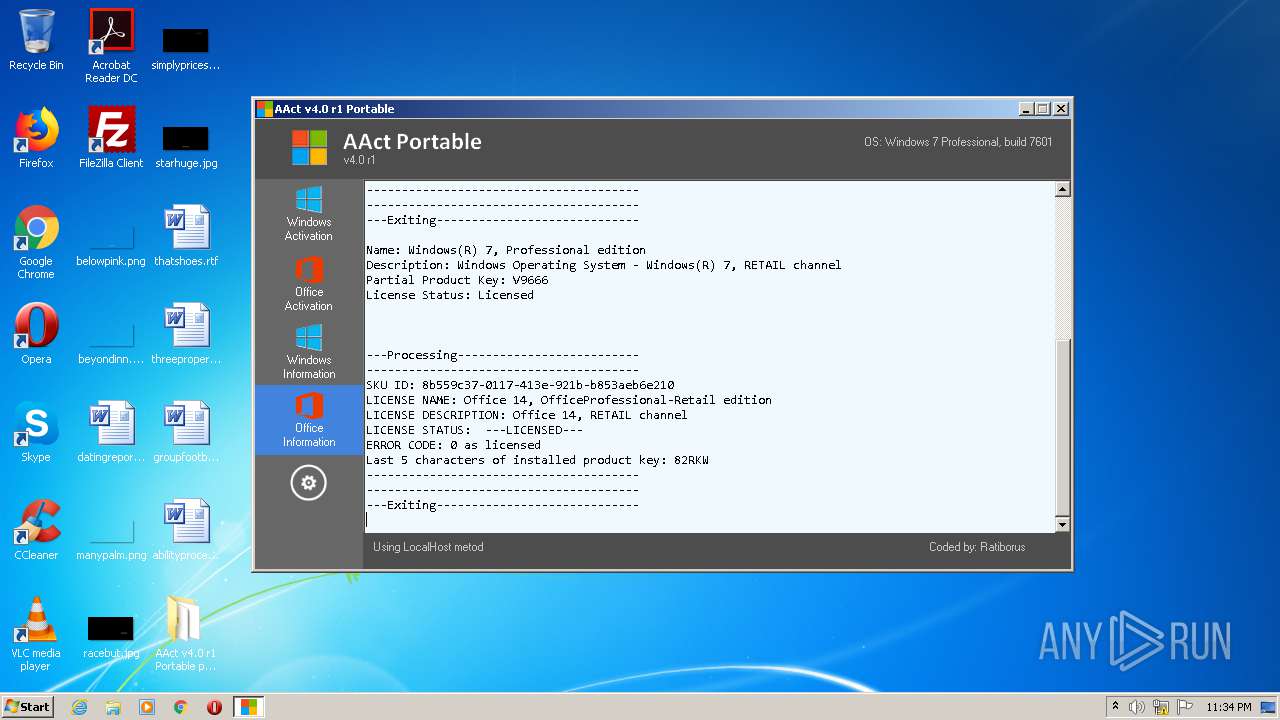
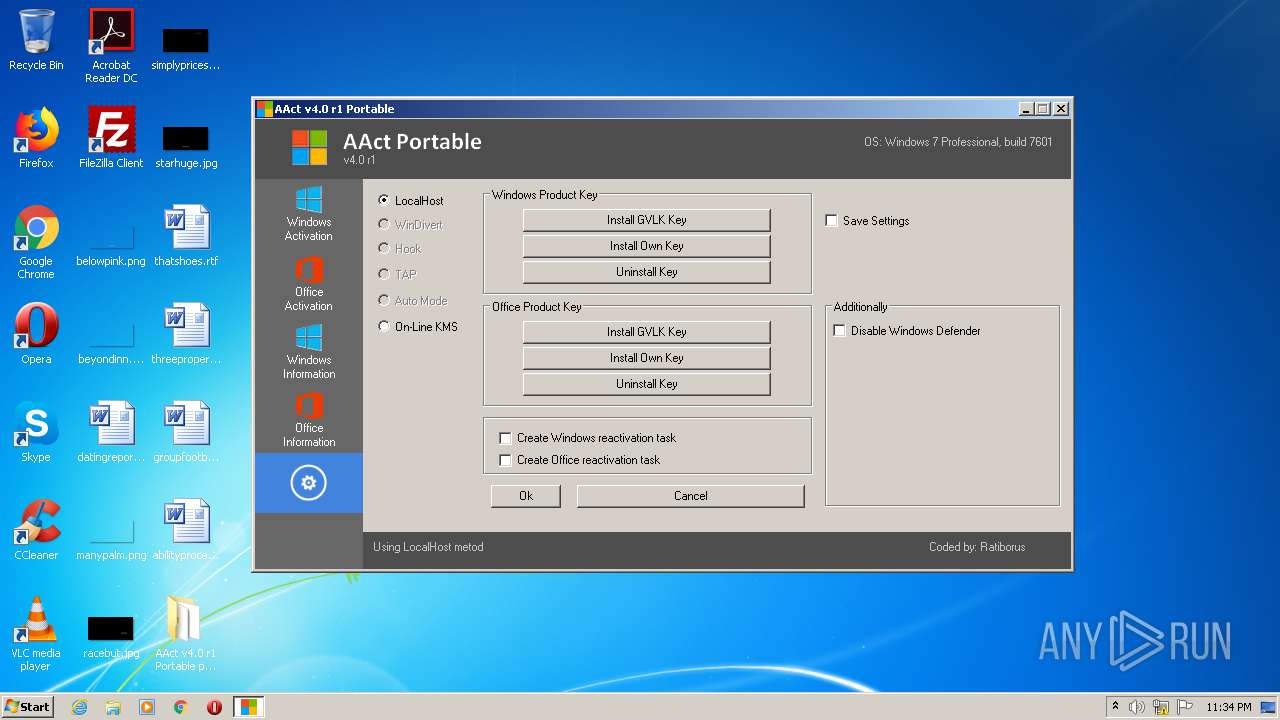
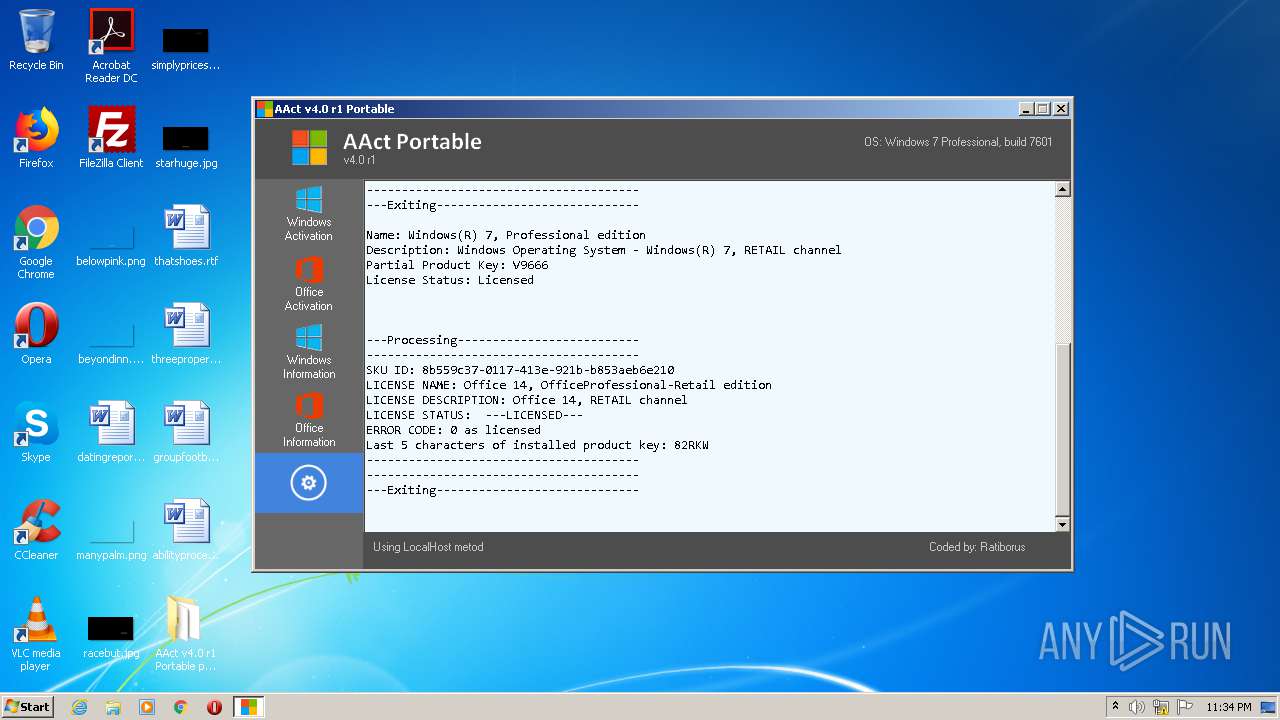
| File name: | AAct_v4.0_r1_Portable_password_2019.7z |
| Full analysis: | https://app.any.run/tasks/fb01e085-1c8d-4bc8-9af2-132775b8465c |
| Verdict: | Malicious activity |
| Analysis date: | July 06, 2020, 22:31:24 |
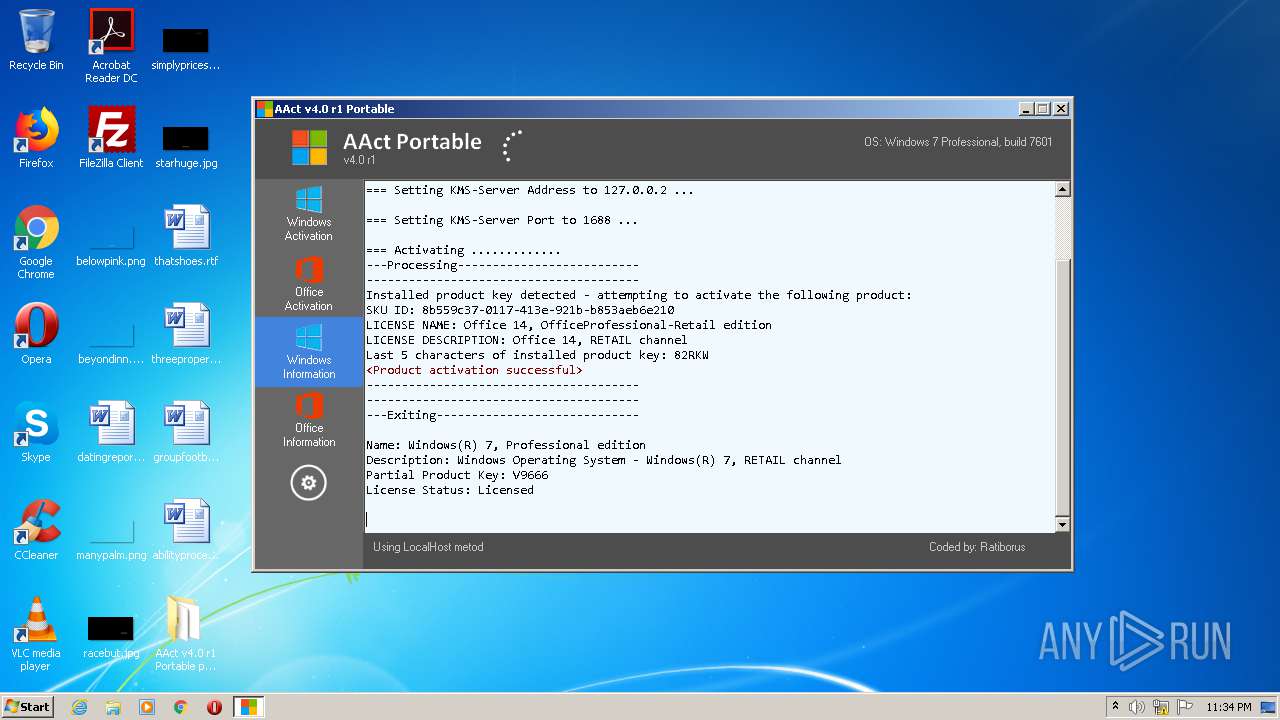
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | D64349D34B392CE8347B72AE2082C004 |
| SHA1: | 249BA8E69660B0F6CBFA44BA211BB78B28E87FD2 |
| SHA256: | 8000FEDD941024CC459C93C3DE1982529D835BF271E094630C0BF980CD96BC9E |
| SSDEEP: | 24576:M03WymVOqZtKc2P2dNlElwwY3THR17c0MUBPePz:M/ymy5AEQ337c0MUIPz |
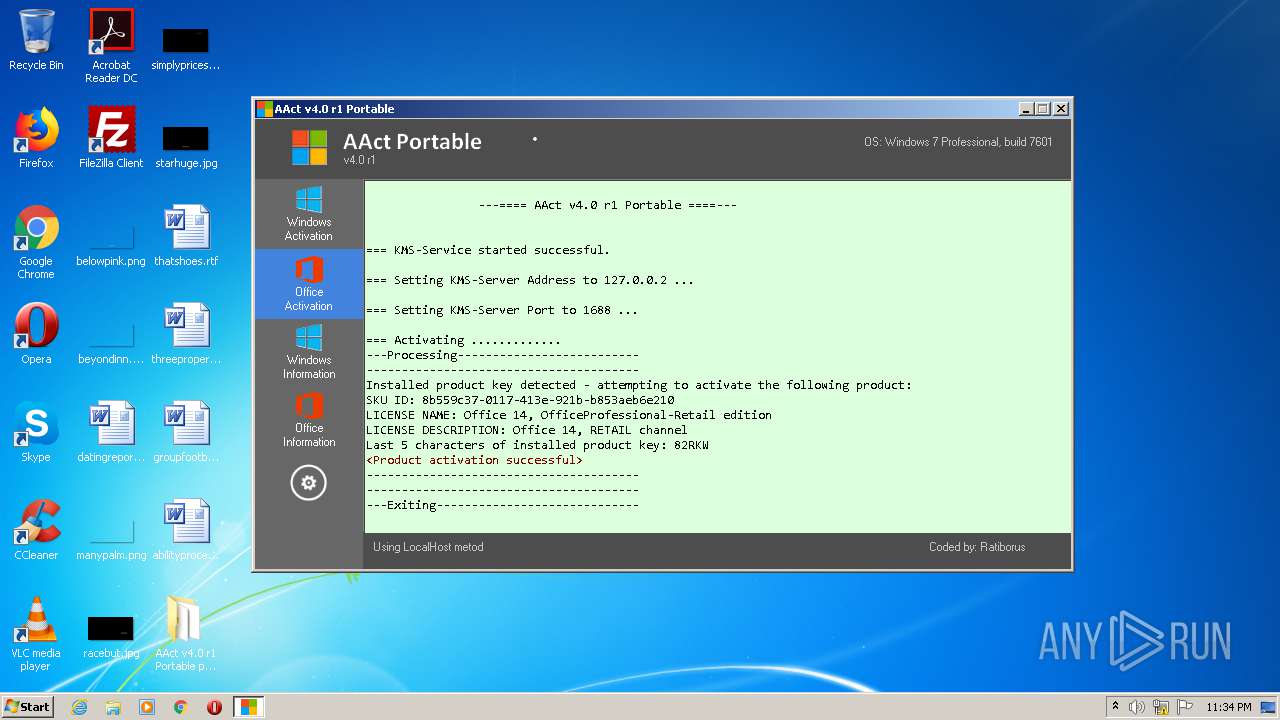
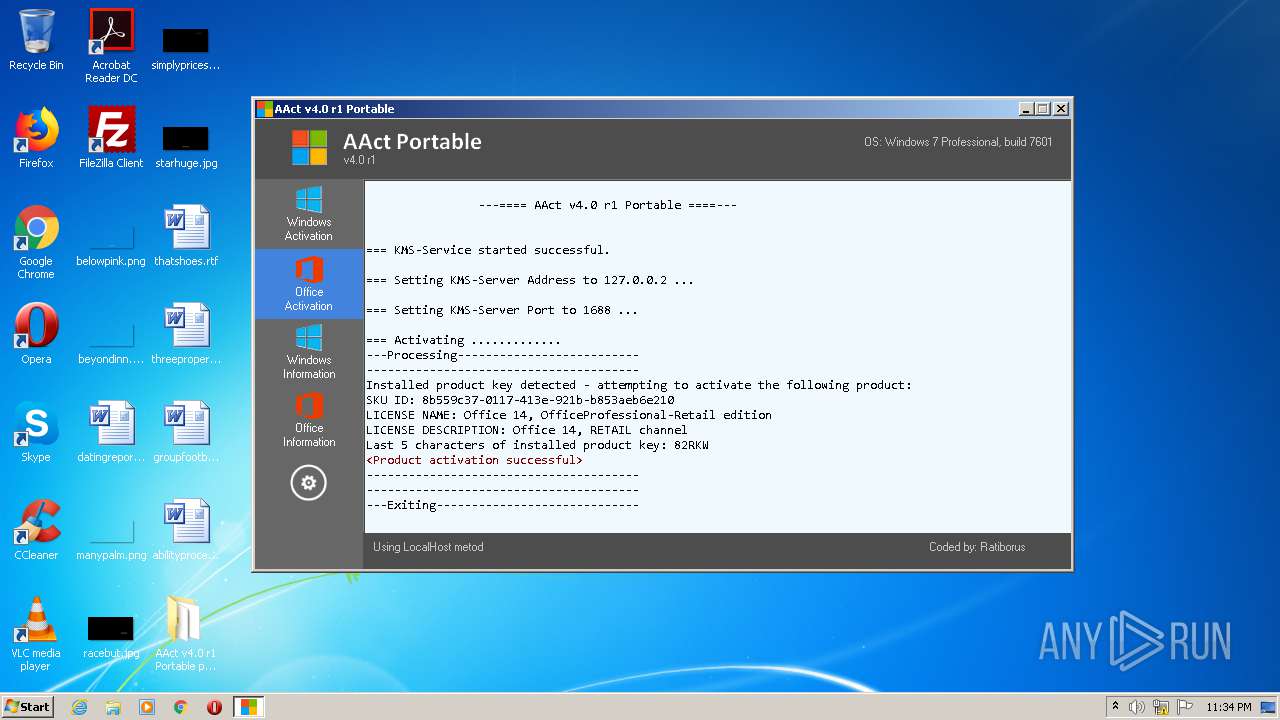
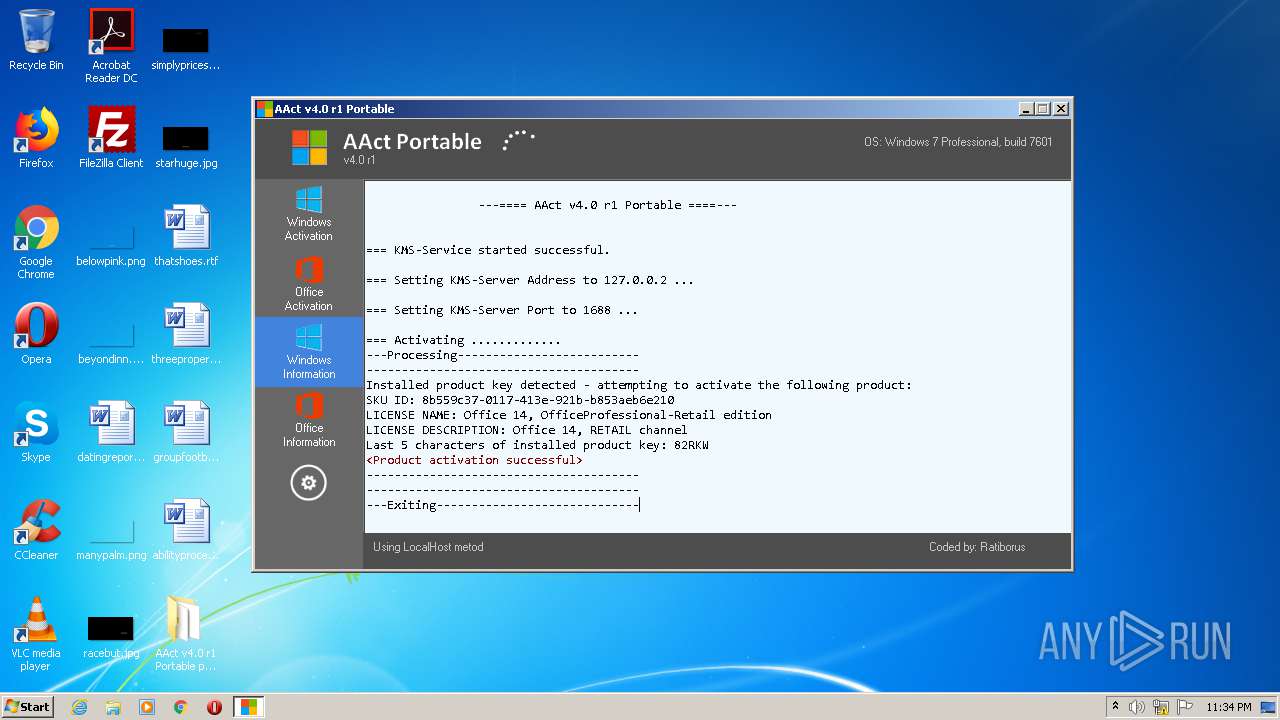
MALICIOUS
Application was dropped or rewritten from another process
- KMSSS.exe (PID: 3164)
- AAct.exe (PID: 1516)
- KMSSS.exe (PID: 1564)
- KMSSS.exe (PID: 2848)
Starts NET.EXE for service management
- cmd.exe (PID: 1788)
- cmd.exe (PID: 1024)
- cmd.exe (PID: 1944)
SUSPICIOUS
Executes scripts
- cmd.exe (PID: 3348)
- cmd.exe (PID: 2920)
- cmd.exe (PID: 3504)
- cmd.exe (PID: 1236)
- cmd.exe (PID: 2644)
- cmd.exe (PID: 608)
- cmd.exe (PID: 3740)
- cmd.exe (PID: 3076)
- cmd.exe (PID: 3928)
- cmd.exe (PID: 1560)
- cmd.exe (PID: 2756)
- cmd.exe (PID: 960)
- cmd.exe (PID: 2188)
- cmd.exe (PID: 2596)
- cmd.exe (PID: 2212)
- cmd.exe (PID: 3368)
- cmd.exe (PID: 2540)
- cmd.exe (PID: 2348)
- cmd.exe (PID: 3440)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 2520)
- cmd.exe (PID: 452)
- cmd.exe (PID: 2532)
- cmd.exe (PID: 2832)
- cmd.exe (PID: 3356)
- cmd.exe (PID: 1376)
- cmd.exe (PID: 1476)
- cmd.exe (PID: 1948)
- cmd.exe (PID: 3896)
Executable content was dropped or overwritten
- AAct.exe (PID: 1516)
- WinRAR.exe (PID: 1232)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2380)
- cmd.exe (PID: 1764)
- cmd.exe (PID: 2116)
- cmd.exe (PID: 2692)
- cmd.exe (PID: 3044)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2664)
- AAct.exe (PID: 1516)
Starts CMD.EXE for commands execution
- AAct.exe (PID: 1516)
Uses IPCONFIG.EXE to discover IP address
- cmd.exe (PID: 788)
- cmd.exe (PID: 2616)
INFO
Manual execution by user
- AAct.exe (PID: 1516)
Reads Microsoft Office registry keys
- reg.exe (PID: 2760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
194
Monitored processes
93
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 452 | "C:\Windows\System32\cmd.exe" /c Netsh.exe Advfirewall Firewall delete rule name=0pen_Port_KMS protocol=TCP | C:\Windows\System32\cmd.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 472 | net.exe start osppsvc | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
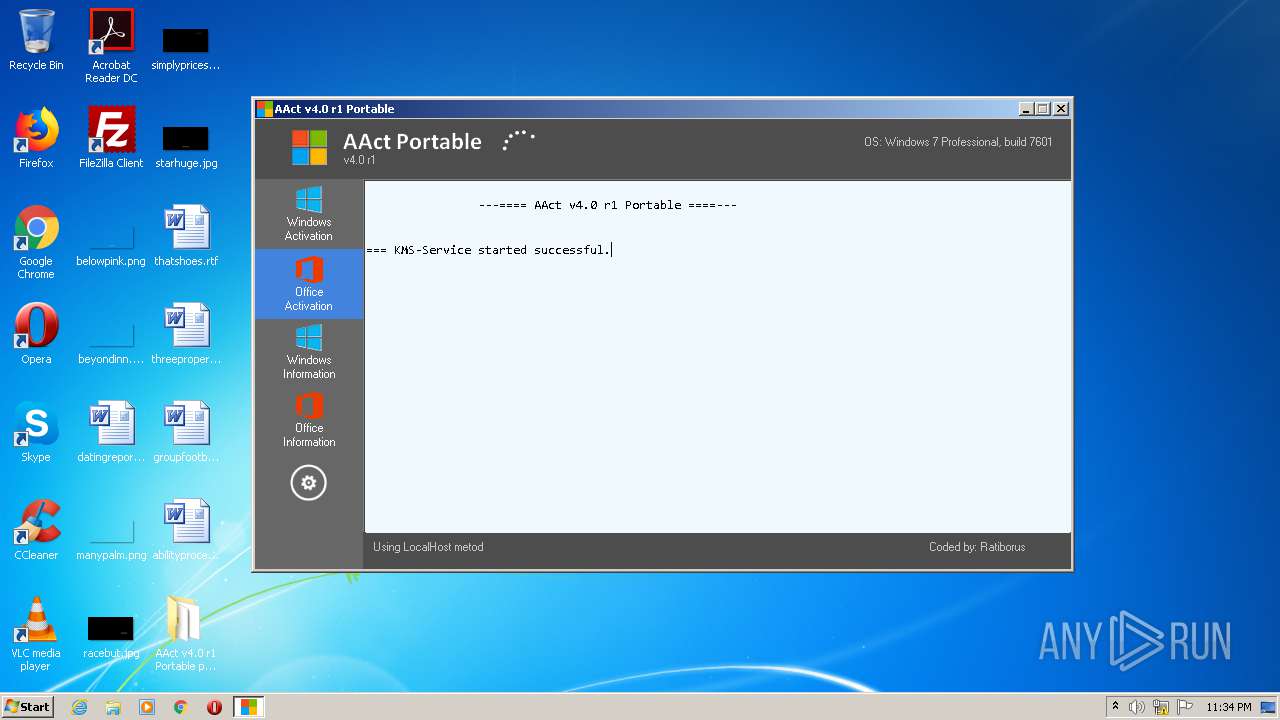
| 608 | "C:\Windows\System32\cmd.exe" /c cscript.exe C:\Windows\System32\slmgr.vbs //NoLogo /sdns | C:\Windows\System32\cmd.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 788 | "C:\Windows\System32\cmd.exe" /c ipconfig.exe /flushdns | C:\Windows\System32\cmd.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
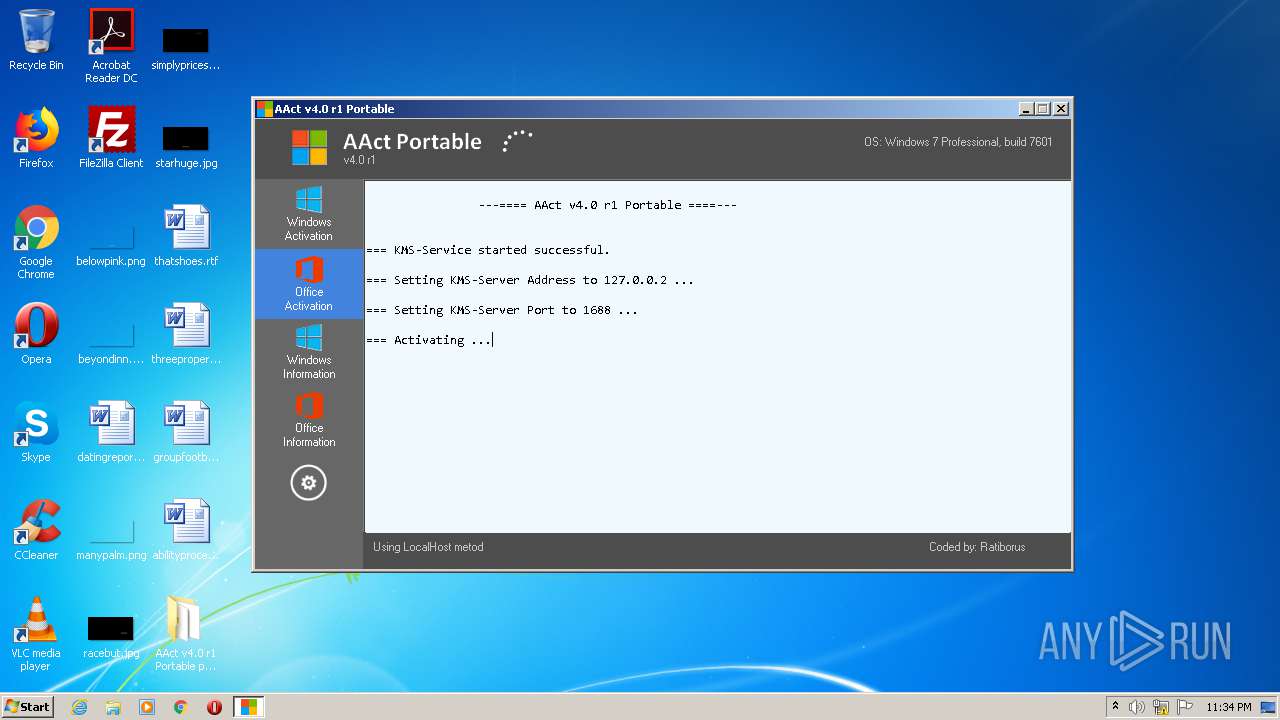
| 920 | Netsh.exe Advfirewall Firewall add rule name=0pen_Port_KMS dir=in action=allow protocol=TCP localport=1688 | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
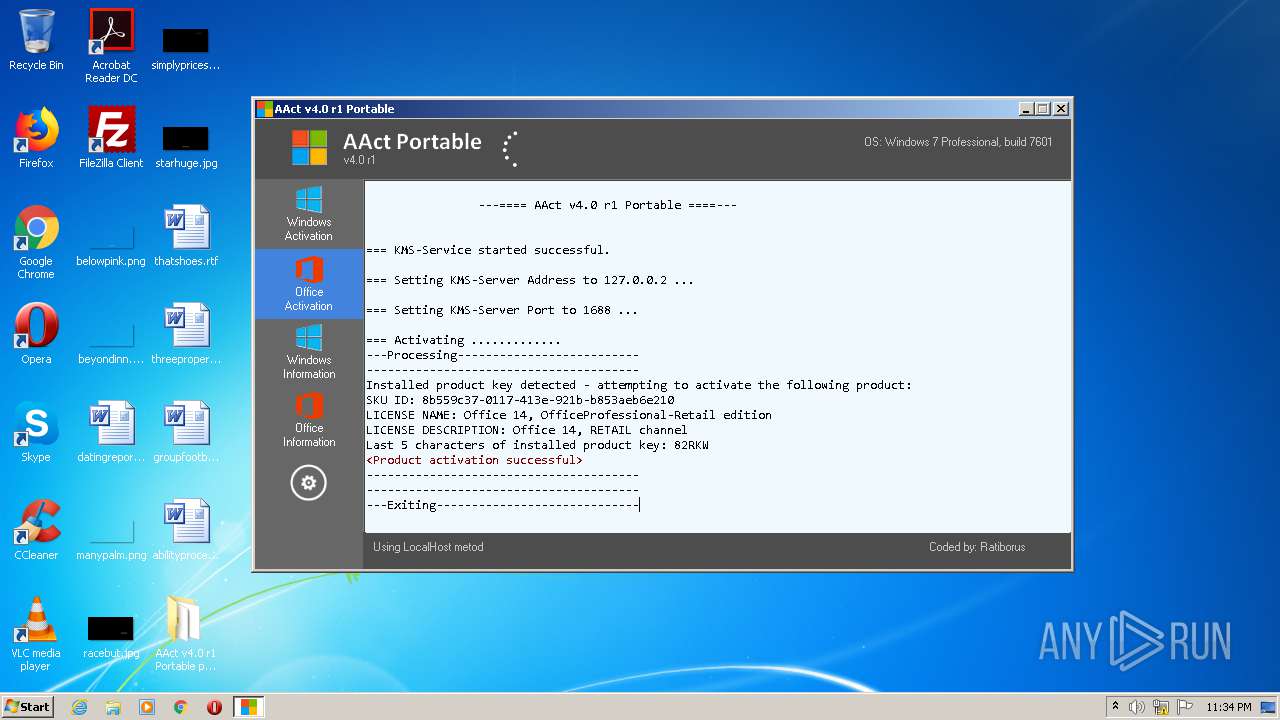
| 960 | "C:\Windows\System32\cmd.exe" /c cscript.exe "C:\Program Files\Microsoft Office\Office14\ospp.vbs" //NoLogo /act | C:\Windows\System32\cmd.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1024 | "C:\Windows\System32\cmd.exe" /c net.exe start osppsvc | C:\Windows\System32\cmd.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1024 | Netsh.exe Advfirewall Firewall delete rule name=0pen_Port_KMS protocol=TCP | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1232 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\AAct_v4.0_r1_Portable_password_2019.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1236 | "C:\Windows\System32\cmd.exe" /c cscript.exe C:\Windows\System32\slmgr.vbs //NoLogo /ato | C:\Windows\System32\cmd.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 654
Read events
1 222
Write events
432
Delete events
0
Modification events
| (PID) Process: | (1232) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1232) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1232) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1232) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (1232) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1232) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\AAct_v4.0_r1_Portable_password_2019.7z | |||
| (PID) Process: | (1232) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1232) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1232) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1232) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
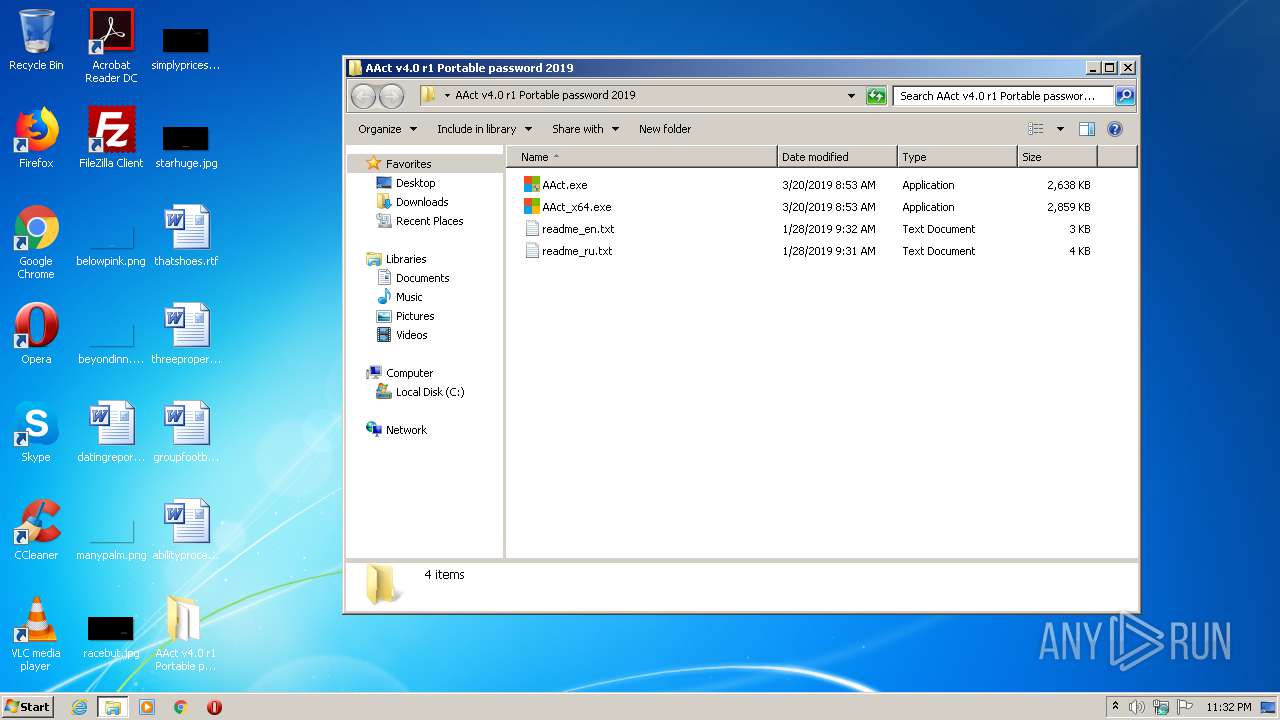
Executable files
3
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1232 | WinRAR.exe | C:\Users\admin\Desktop\AAct v4.0 r1 Portable password 2019\readme_ru.txt | text | |
MD5:97CFC67D7774B3FAC626CF36A1456528 | SHA256:17FF3A22661B442DBE6437FAC5D276A152C7ADFFA65FDCC106BA60B5A3D583C0 | |||
| 1516 | AAct.exe | C:\Users\admin\Desktop\AAct v4.0 r1 Portable password 2019\AAct_files\KMSSS.exe | executable | |
MD5:01A80AAD5DABED1C1580F7E00213CF9D | SHA256:FD7499214ABAA13BF56D006AB7DE78EB8D6ADF17926C24ACE024D067049BC81D | |||
| 1232 | WinRAR.exe | C:\Users\admin\Desktop\AAct v4.0 r1 Portable password 2019\readme_en.txt | text | |
MD5:35DB3ACB89F704147901B83C9BDC0B5B | SHA256:C56E528E8E536B5D71033E190B6E5B4EA735D9E76C6EB46CE3AB5BC0C23EB03E | |||
| 1232 | WinRAR.exe | C:\Users\admin\Desktop\AAct v4.0 r1 Portable password 2019\AAct.exe | executable | |
MD5:A087B2E6EC57B08C0D0750C60F96A74C | SHA256:E12B6641D7E7E4DA97A0FF8E1A0D4840C882569D47B8FAB8FB187AC2B475636C | |||
| 1232 | WinRAR.exe | C:\Users\admin\Desktop\AAct v4.0 r1 Portable password 2019\AAct_x64.exe | executable | |
MD5:7F3DFE3836F04A1A4CAB8377FC572500 | SHA256:F53A0AC49FE1EB88C937F8829B93A24BBB0B332B955BB1374046FBCEAF663E54 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
4
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3464 | wmiprvse.exe | POST | 302 | 184.25.217.162:80 | http://go.microsoft.com/fwlink/?LinkID=88339 | NL | — | — | whitelisted |
3464 | wmiprvse.exe | POST | 302 | 184.25.217.162:80 | http://go.microsoft.com/fwlink/?LinkID=88340 | NL | — | — | whitelisted |
3464 | wmiprvse.exe | POST | 302 | 184.25.217.162:80 | http://go.microsoft.com/fwlink/?LinkID=88341 | NL | — | — | whitelisted |
2092 | wmiprvse.exe | POST | 302 | 184.25.217.162:80 | http://go.microsoft.com/fwlink/?LinkID=120750 | NL | — | — | whitelisted |
2092 | wmiprvse.exe | POST | 302 | 184.25.217.162:80 | http://go.microsoft.com/fwlink/?LinkID=120751 | NL | — | — | whitelisted |
2092 | wmiprvse.exe | POST | 302 | 184.25.217.162:80 | http://go.microsoft.com/fwlink/?LinkID=120750 | NL | — | — | whitelisted |
2092 | wmiprvse.exe | POST | 302 | 184.25.217.162:80 | http://go.microsoft.com/fwlink/?LinkID=120751 | NL | — | — | whitelisted |
2092 | wmiprvse.exe | POST | 302 | 184.25.217.162:80 | http://go.microsoft.com/fwlink/?LinkID=120752 | NL | — | — | whitelisted |
2092 | wmiprvse.exe | POST | 302 | 184.25.217.162:80 | http://go.microsoft.com/fwlink/?LinkID=120752 | NL | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3464 | wmiprvse.exe | 184.25.217.162:80 | go.microsoft.com | Akamai International B.V. | NL | malicious |
3464 | wmiprvse.exe | 40.91.122.234:443 | activation.sls.microsoft.com | Microsoft Corporation | US | unknown |
2092 | wmiprvse.exe | 184.25.217.162:80 | go.microsoft.com | Akamai International B.V. | NL | malicious |
2092 | wmiprvse.exe | 40.91.122.234:443 | activation.sls.microsoft.com | Microsoft Corporation | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
activation.sls.microsoft.com |
| whitelisted |