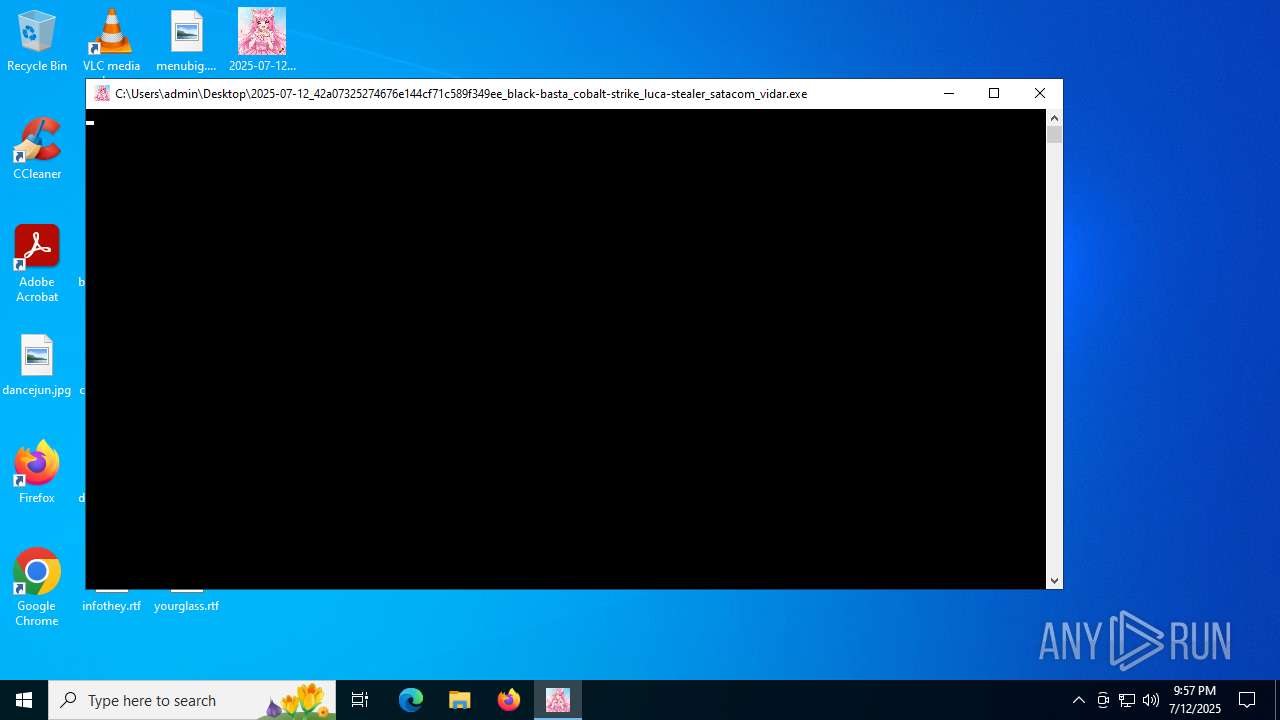
| File name: | 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe |
| Full analysis: | https://app.any.run/tasks/7b816a27-fc66-4da7-a677-e1571c248def |
| Verdict: | Malicious activity |
| Analysis date: | July 12, 2025, 21:56:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | 42A07325274676E144CF71C589F349EE |
| SHA1: | 8A11B87709855C4E8A8632C5BDEF01698727C99E |
| SHA256: | 7FEB9B335EF48C7EBD5C8AFD1E2A140754F52E2B9051D0E3AD75872EFB505825 |
| SSDEEP: | 196608:1X5r4fVjt4f/fY83VwCTA9GaEtazmQkIiEEe4IAstwIs5MxkIK:1X5r4EHfYy3TAHzAIiEbfazMaIK |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 5884)
Process drops python dynamic module
- 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 5884)
Process drops legitimate windows executable
- 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 5884)
Application launched itself
- 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 5884)
Loads Python modules
- 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4844)
The process drops C-runtime libraries
- 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 5884)
INFO
Reads the computer name
- 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 5884)
- 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4844)
The sample compiled with english language support
- 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 5884)
Checks supported languages
- 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 5884)
- 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4844)
Create files in a temporary directory
- 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 5884)
Checks proxy server information
- 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe (PID: 4844)
- slui.exe (PID: 4824)
Reads the software policy settings
- slui.exe (PID: 4824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:07:11 04:53:09+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 179712 |
| InitializedDataSize: | 221696 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc650 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
135
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4824 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4844 | "C:\Users\admin\Desktop\2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe" | C:\Users\admin\Desktop\2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 5884 | "C:\Users\admin\Desktop\2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe" | C:\Users\admin\Desktop\2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 6572 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 814
Read events
3 814
Write events
0
Delete events
0
Modification events
Executable files
100
Suspicious files
1
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5884 | 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI58842\OpenGL\DLLS\freeglut32.vc14.dll | executable | |
MD5:67882F7987F27C8C2E7B4EBAC37BF42C | SHA256:C9C00A4EA9B9FECDCAE81F6FACAF27E349714D56FE7640CE9C37ED38841A0B87 | |||
| 5884 | 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI58842\OpenGL\DLLS\GLE_WIN32_README.txt | text | |
MD5:C02858F933D989EDB257604159557A23 | SHA256:A7DF9B1FCC74D4DDF51CA0774CC94F00DC55146052FBE08614DBA0E9DA68F887 | |||
| 5884 | 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI58842\MSVCR100.dll | executable | |
MD5:366FD6F3A451351B5DF2D7C4ECF4C73A | SHA256:AE3CB6C6AFBA9A4AA5C85F66023C35338CA579B30326DD02918F9D55259503D5 | |||
| 5884 | 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI58842\MSVCP140.dll | executable | |
MD5:BC88B387CAFA556068B5C5D6FF3CCC8F | SHA256:0F885B509A685D2BBFA652FED26B5FB31D88FBDAB0A978C641D1C7B8AA460AA9 | |||
| 5884 | 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI58842\OpenGL\DLLS\gle_COPYING.src | text | |
MD5:6ADED20D3E824C7CBA05E3A445097BD8 | SHA256:17C3504E92FA17B916F2AE09E9C192263A68BD8F1429E18DE8A809BBA46CF82D | |||
| 5884 | 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI58842\OpenGL\DLLS\freeglut64.vc10.dll | executable | |
MD5:3FA883DB6531510AFB85EDCFF0B53E02 | SHA256:01354ABB19F7126EF9461CED319FA9FA0AF213CF741699A4A7F1813DC43918E9 | |||
| 5884 | 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI58842\OpenGL\DLLS\gle32.vc14.dll | executable | |
MD5:88A3205111462AE2ACBBEFB1F1739F99 | SHA256:D14BF244F41FC2ECF2DFABA5A73A389ADED8690282943666EB9880BAB3FFA36D | |||
| 5884 | 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI58842\OpenGL\DLLS\gle64.vc9.dll | executable | |
MD5:AE552D58FEB38120998F915BAC18C783 | SHA256:B427510AF633A6298481E738942F3268DAEDF44D6C01AF74620579034BEDE9CE | |||
| 5884 | 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI58842\OpenGL\DLLS\gle64.vc14.dll | executable | |
MD5:E46AA74667E91A7BB003C4243EA7F0E5 | SHA256:7FFE63498DE7A3A12D10D54C185824C7DB8EAD55418109A1E897D28DFEF55199 | |||
| 5884 | 2025-07-12_42a07325274676e144cf71c589f349ee_black-basta_cobalt-strike_luca-stealer_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\_MEI58842\OpenGL\DLLS\freeglut_README.txt | text | |
MD5:7FF3463A0B9F82966D040B5CA7519508 | SHA256:F02832D18D064A938357A3EA4E0B3C43E1C86E9EBE58A96095C53197573CAA53 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
22
DNS requests
9
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5104 | RUXIMICS.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5104 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5104 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5104 | RUXIMICS.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5104 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
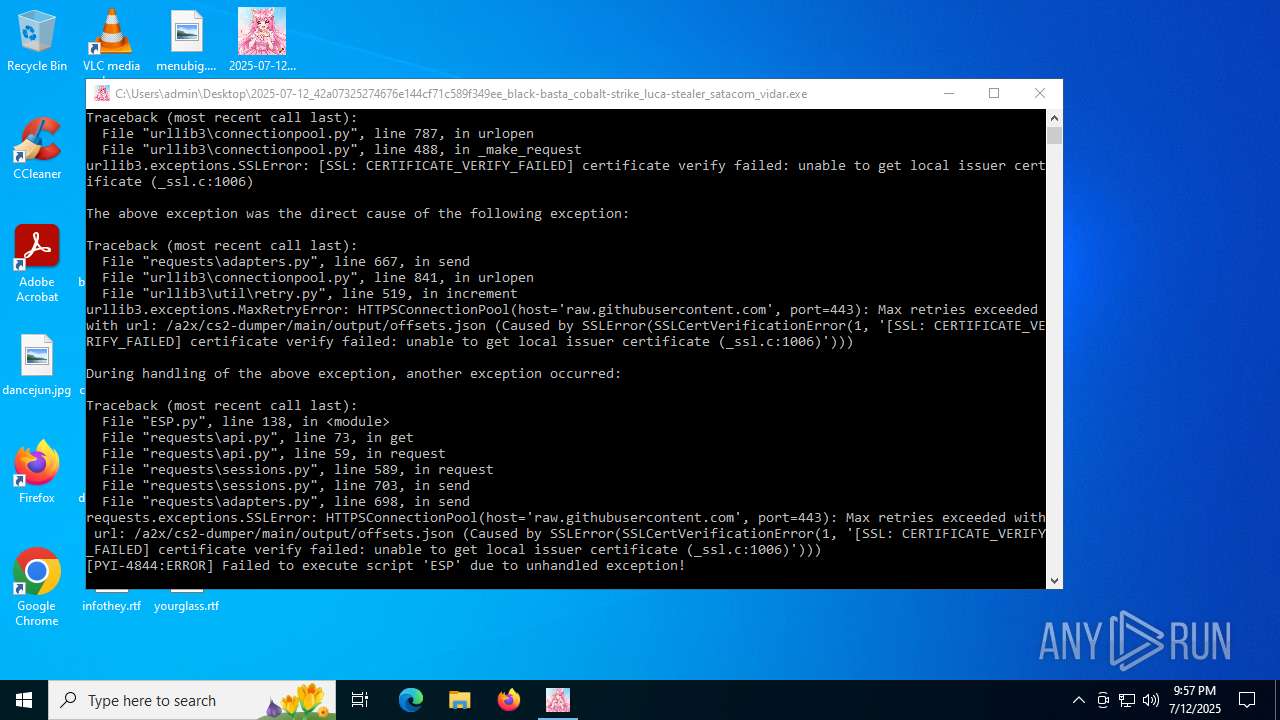
raw.githubusercontent.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |