| URL: | https://www.kakaocorp.com/service/KakaoTalk |
| Full analysis: | https://app.any.run/tasks/82204c2e-2ded-4d73-ae4d-f467f342dea0 |
| Verdict: | Malicious activity |
| Analysis date: | May 11, 2021, 05:44:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 33F95C04A5A98C60F6A73EB9EC912EA9 |
| SHA1: | 2A140010D2DB479654328CBB3F13B40E880FE81F |
| SHA256: | 7FC2B93EC4448D0B0383AAB96870C26C5CDF4FEA730F7E5297E863DCE30970E9 |
| SSDEEP: | 3:N8DSLVMgSXAGXqgO:2OLSvAG6gO |
MALICIOUS
Application was dropped or rewritten from another process
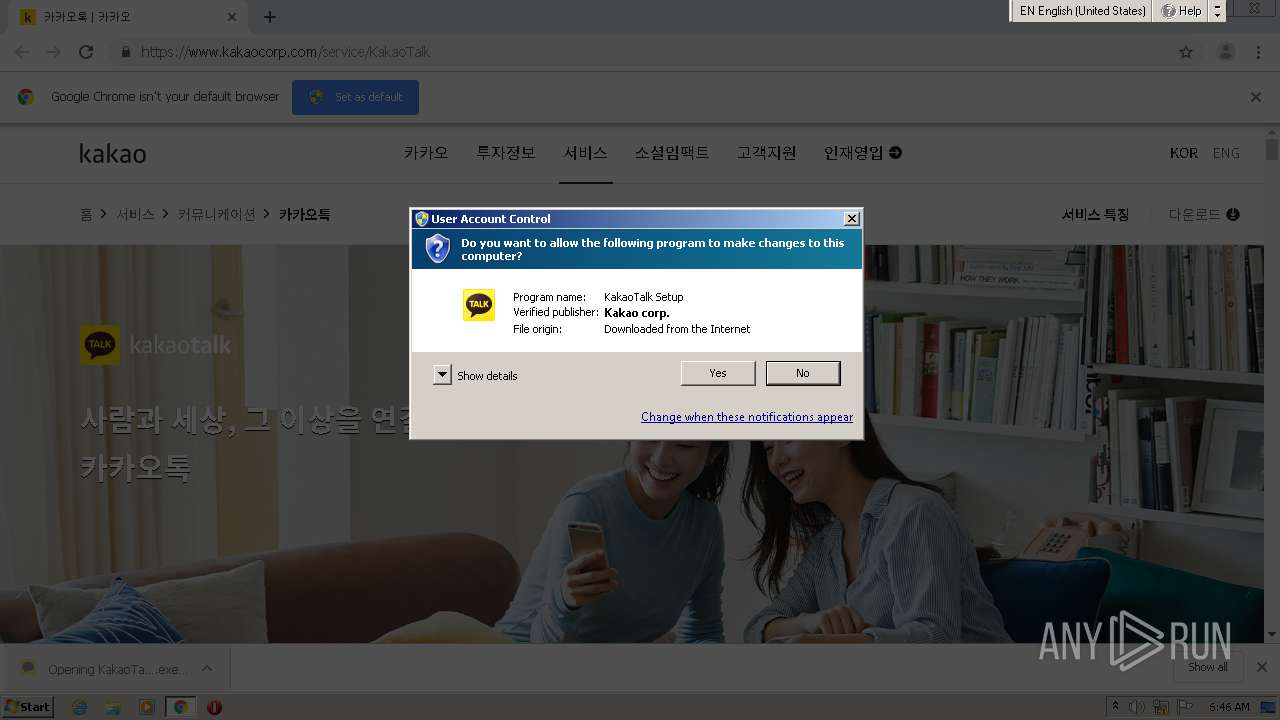
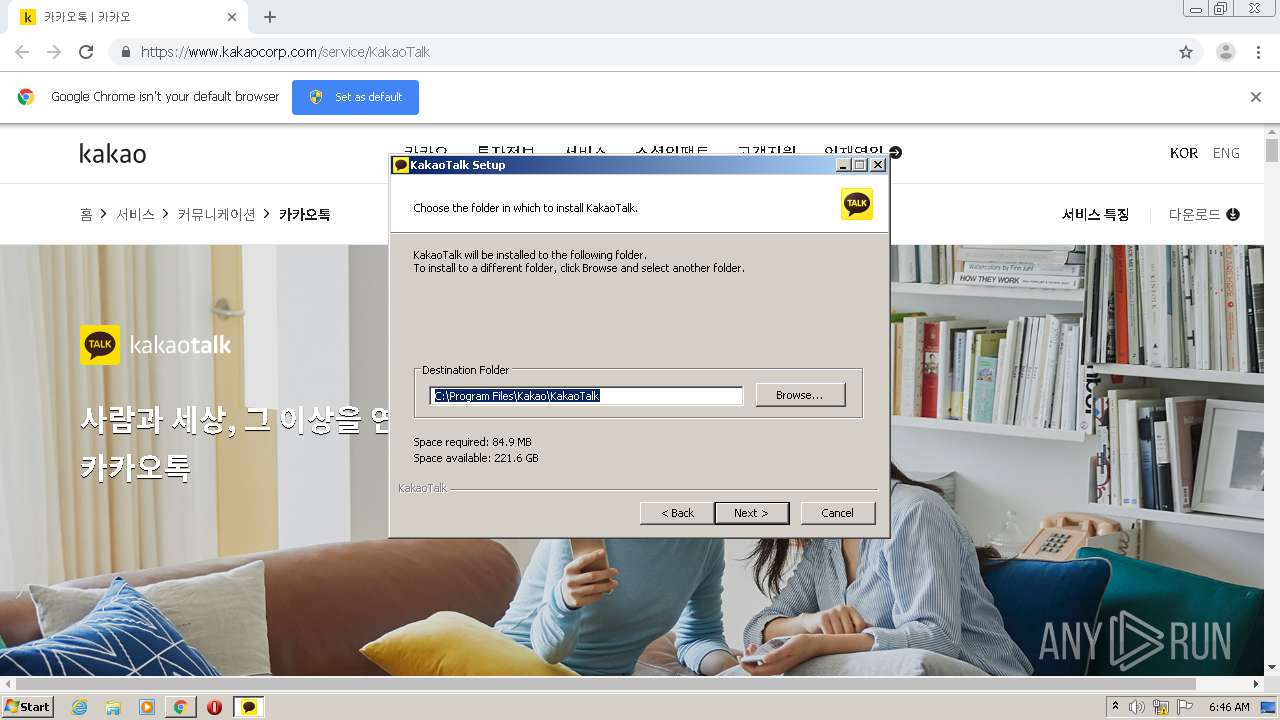
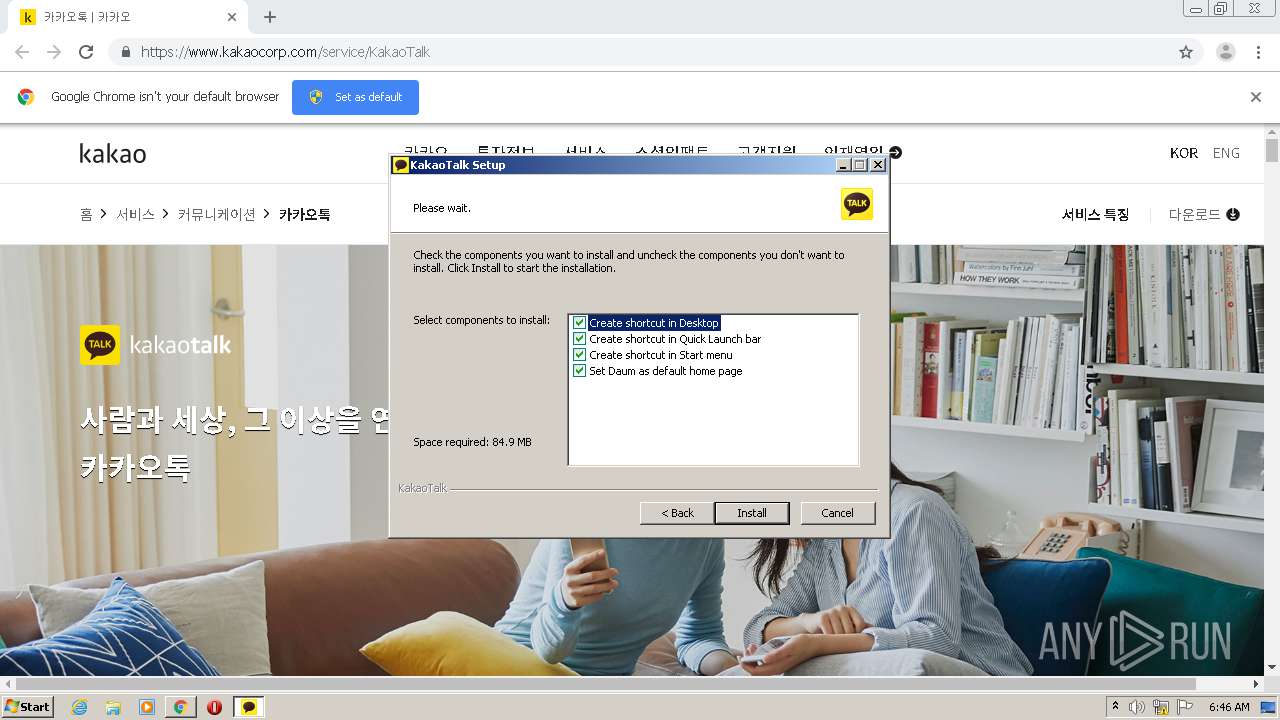
- KakaoTalk_Setup.exe (PID: 1032)
- KakaoTalk_Setup.exe (PID: 2896)
- KakaoTalk.exe (PID: 3936)
- KakaoTalk.exe (PID: 1704)
Changes the autorun value in the registry
- KakaoTalk_Setup.exe (PID: 1032)
- KakaoTalk.exe (PID: 1704)
Loads dropped or rewritten executable
- KakaoTalk.exe (PID: 3936)
- KakaoTalk_Setup.exe (PID: 1032)
SUSPICIOUS
Drops a file with too old compile date
- KakaoTalk_Setup.exe (PID: 1032)
Creates a software uninstall entry
- KakaoTalk_Setup.exe (PID: 1032)
Drops a file with a compile date too recent
- KakaoTalk_Setup.exe (PID: 1032)
Changes the started page of IE
- KakaoTalk_Setup.exe (PID: 1032)
Changes default file association
- KakaoTalk_Setup.exe (PID: 1032)
Creates files in the user directory
- KakaoTalk_Setup.exe (PID: 1032)
Executable content was dropped or overwritten
- chrome.exe (PID: 1720)
- KakaoTalk_Setup.exe (PID: 1032)
Application launched itself
- KakaoTalk.exe (PID: 3936)
Drops a file that was compiled in debug mode
- KakaoTalk_Setup.exe (PID: 1032)
Creates a directory in Program Files
- KakaoTalk_Setup.exe (PID: 1032)
Creates files in the program directory
- KakaoTalk_Setup.exe (PID: 1032)
INFO
Reads settings of System Certificates
- chrome.exe (PID: 1720)
Application launched itself
- chrome.exe (PID: 1720)
Reads the hosts file
- chrome.exe (PID: 3136)
- chrome.exe (PID: 1720)
Dropped object may contain Bitcoin addresses
- KakaoTalk_Setup.exe (PID: 1032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
57
Monitored processes
15
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1032 | "C:\Users\admin\Downloads\KakaoTalk_Setup.exe" | C:\Users\admin\Downloads\KakaoTalk_Setup.exe | chrome.exe | ||||||||||||
User: admin Company: Kakao Corp. Integrity Level: HIGH Description: KakaoTalk Setup Exit code: 0 Version: 3.2.6.2748 Modules
| |||||||||||||||
| 1228 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,15920962969759892034,12650038701552680529,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17850760862379752608 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2096 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1704 | "C:\Program Files\Kakao\KakaoTalk\KakaoTalk.exe" RelayBYSETUP | C:\Program Files\Kakao\KakaoTalk\KakaoTalk.exe | KakaoTalk.exe | ||||||||||||
User: admin Company: Kakao Corp. Integrity Level: MEDIUM Description: KakaoTalk Exit code: 0 Version: 3.2.6.2748 Modules
| |||||||||||||||
| 1720 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking "https://www.kakaocorp.com/service/KakaoTalk" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1772 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,15920962969759892034,12650038701552680529,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=4748090625933903040 --mojo-platform-channel-handle=1032 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2372 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6eb8a9d0,0x6eb8a9e0,0x6eb8a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2516 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,15920962969759892034,12650038701552680529,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12125114694710454792 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2424 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2632 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1044,15920962969759892034,12650038701552680529,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=731419326454321619 --mojo-platform-channel-handle=968 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2896 | "C:\Users\admin\Downloads\KakaoTalk_Setup.exe" | C:\Users\admin\Downloads\KakaoTalk_Setup.exe | — | chrome.exe | |||||||||||
User: admin Company: Kakao Corp. Integrity Level: MEDIUM Description: KakaoTalk Setup Exit code: 3221226540 Version: 3.2.6.2748 Modules
| |||||||||||||||
| 3136 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,15920962969759892034,12650038701552680529,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=1858615551119766045 --mojo-platform-channel-handle=1564 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 346
Read events
1 241
Write events
102
Delete events
3
Modification events
| (PID) Process: | (1720) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1720) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1720) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1720) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1720) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4020) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 1720-13265185489656000 |
Value: 259 | |||
| (PID) Process: | (1720) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1720) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1720) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (1720) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1720-13265185489656000 |
Value: 259 | |||
Executable files
13
Suspicious files
695
Text files
6 160
Unknown types
51
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-609A19D2-6B8.pma | — | |
MD5:— | SHA256:— | |||
| 1720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\2a52e3a4-2864-474c-83ec-e2d19db3a3f6.tmp | — | |
MD5:— | SHA256:— | |||
| 1720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF1de9d6.TMP | text | |
MD5:— | SHA256:— | |||
| 1720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF1debe9.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
21
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1704 | KakaoTalk.exe | GET | 200 | 203.238.180.28:80 | http://app.pc.kakao.com/talk/win32/patch/patch.txt | KR | text | 623 b | malicious |
1032 | KakaoTalk_Setup.exe | GET | 200 | 211.231.108.75:80 | http://start.www.daum.net/startpage/?hcode=D_KAKAOTALK | KR | html | 32 b | whitelisted |
1032 | KakaoTalk_Setup.exe | GET | 302 | 211.231.108.75:80 | http://start.tiara.daum.net/startpage/index.html?hcode=D_KAKAOTALK | KR | image | 35 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3136 | chrome.exe | 211.249.221.27:443 | www.kakaocorp.com | DREAMLINE CO. | KR | unknown |
3136 | chrome.exe | 172.217.18.109:443 | accounts.google.com | Google Inc. | US | suspicious |
3136 | chrome.exe | 121.53.216.28:443 | tv.kakao.com | DREAMLINE CO. | KR | unknown |
3136 | chrome.exe | 211.249.221.246:443 | developers.kakao.com | DREAMLINE CO. | KR | suspicious |
3136 | chrome.exe | 2.17.120.104:443 | t1.kakaocdn.net | Akamai International B.V. | — | unknown |
3136 | chrome.exe | 211.249.220.83:443 | stat.tiara.kakaocorp.com | DREAMLINE CO. | KR | unknown |
3136 | chrome.exe | 113.29.189.143:443 | app-pc.kakaocdn.net | Kakao Corp | KR | suspicious |
3136 | chrome.exe | 142.250.185.142:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
1032 | KakaoTalk_Setup.exe | 211.231.108.75:80 | start.tiara.daum.net | Kakao Corp | KR | unknown |
— | — | 142.250.184.227:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.kakaocorp.com |
| unknown |
accounts.google.com |
| shared |
tv.kakao.com |
| unknown |
developers.kakao.com |
| suspicious |
t1.daumcdn.net |
| whitelisted |
t1.kakaocdn.net |
| whitelisted |
stat.tiara.kakaocorp.com |
| unknown |
cdnjs.cloudflare.com |
| whitelisted |
webid.ad.daum.net |
| whitelisted |
ssl.gstatic.com |
| whitelisted |