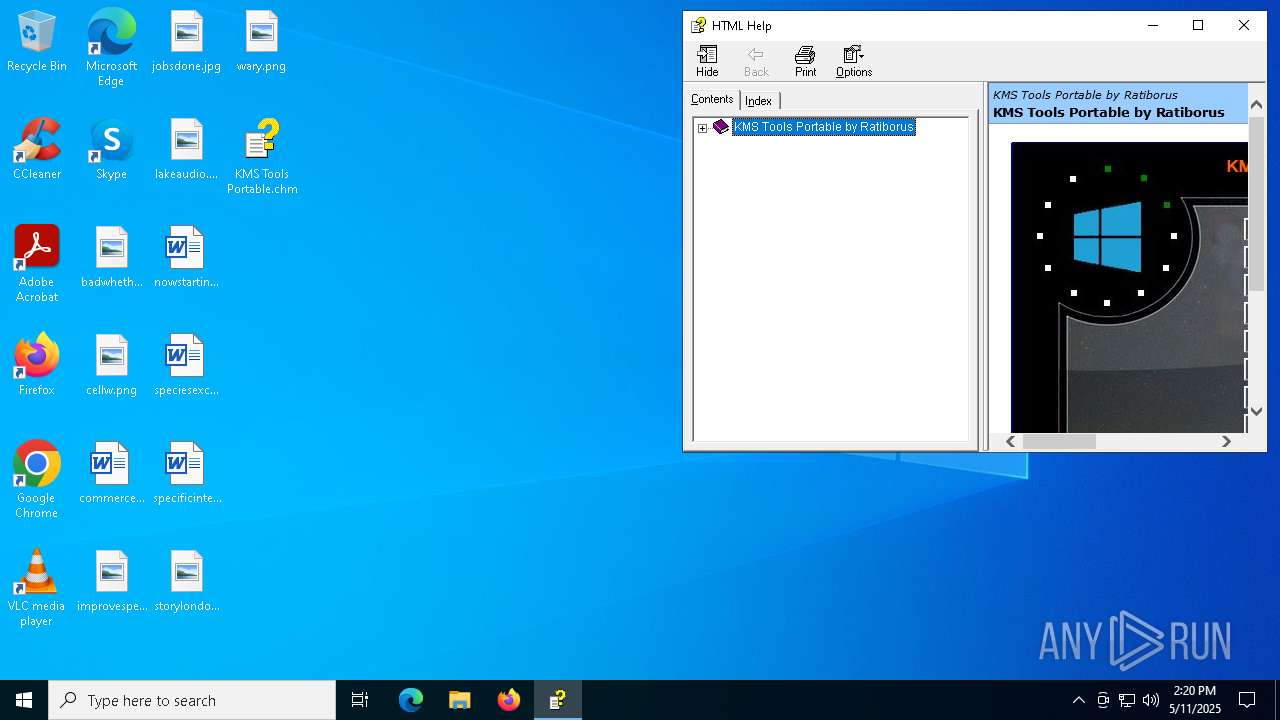
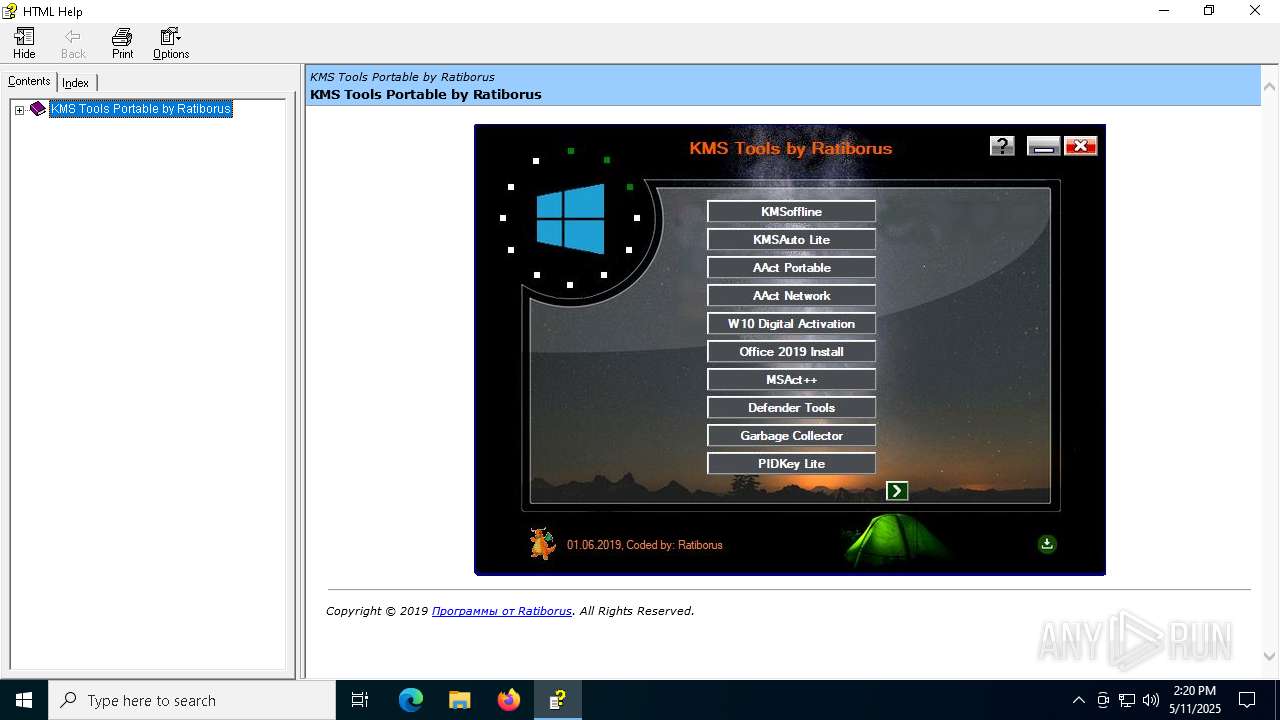
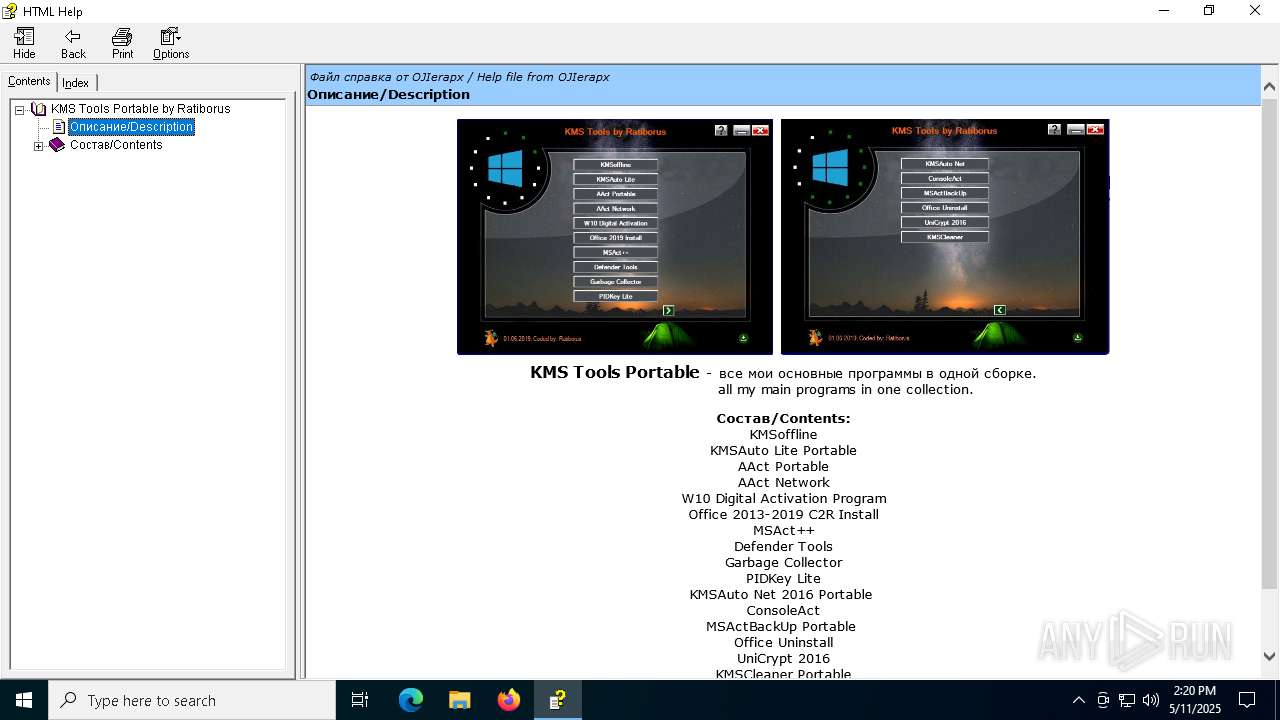
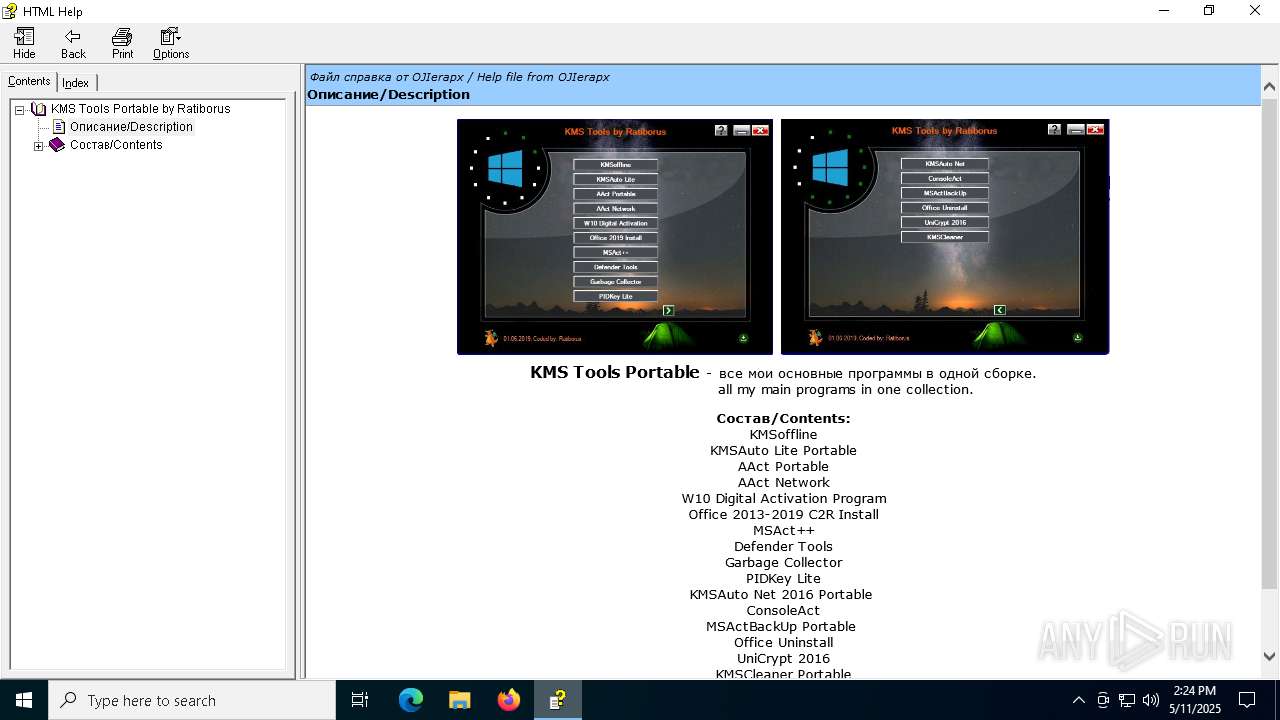
| File name: | KMS Tools Portable.chm |
| Full analysis: | https://app.any.run/tasks/88da36f6-22f1-4cb6-ac06-a6e32b6bcb13 |
| Verdict: | Malicious activity |
| Analysis date: | May 11, 2025, 14:20:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-htmlhelp |
| File info: | MS Windows HtmlHelp Data |
| MD5: | 16498D20922A580AD81241D9CF7DCDF0 |
| SHA1: | DC05B5089E993E85EE8E10B174A15F6BB03E2532 |
| SHA256: | 7FBCBF065CE1626694DF8C443C377D0478CF32601FE74B0FD742FBCFB4F94A3F |
| SSDEEP: | 24576:c93iWDn3DixqqPMJB2ZgUo/2epA9en42Imtb0xhlaZn8R/5KYG31dqK:c93iW7WoqPMJB2ZgUi2eu9en42Imtb08 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Internet Explorer settings
- hh.exe (PID: 7336)
Reads Microsoft Outlook installation path
- hh.exe (PID: 7336)
Reads the BIOS version
- KMS Tools Unpack.exe (PID: 7248)
- KMS Tools Unpack.exe (PID: 4688)
- KMS Tools Unpack.exe (PID: 3240)
- KMS Tools Unpack.exe (PID: 7752)
Starts CMD.EXE for commands execution
- install.exe (PID: 7652)
- GSetup.exe (PID: 7676)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1616)
- cmd.exe (PID: 5384)
There is functionality for taking screenshot (YARA)
- GSetup.exe (PID: 7676)
Executing commands from a ".bat" file
- GSetup.exe (PID: 7676)
- install.exe (PID: 7652)
INFO
The sample compiled with russian language support
- hh.exe (PID: 7336)
Checks proxy server information
- hh.exe (PID: 7336)
- slui.exe (PID: 7272)
Create files in a temporary directory
- hh.exe (PID: 7336)
- install.exe (PID: 7652)
- GSetup.exe (PID: 7676)
Reads security settings of Internet Explorer
- hh.exe (PID: 7336)
Creates files or folders in the user directory
- hh.exe (PID: 7336)
Manual execution by a user
- KMS Tools Unpack.exe (PID: 3332)
- KMS Tools Unpack.exe (PID: 7248)
- KMS Tools Unpack.exe (PID: 3240)
- KMS Tools Unpack.exe (PID: 680)
- KMS Tools Unpack.exe (PID: 4688)
- KMS Tools Unpack.exe (PID: 4988)
- KMS Tools Unpack.exe (PID: 7628)
- KMS Tools Unpack.exe (PID: 7752)
Process checks whether UAC notifications are on
- KMS Tools Unpack.exe (PID: 7248)
- KMS Tools Unpack.exe (PID: 3240)
- KMS Tools Unpack.exe (PID: 4688)
- KMS Tools Unpack.exe (PID: 7752)
Checks supported languages
- KMS Tools Unpack.exe (PID: 7248)
- KMS Tools Unpack.exe (PID: 3240)
- KMS Tools Unpack.exe (PID: 4688)
- KMS Tools Unpack.exe (PID: 7752)
- install.exe (PID: 7652)
- GSetup.exe (PID: 7676)
Reads mouse settings
- KMS Tools Unpack.exe (PID: 7248)
- KMS Tools Unpack.exe (PID: 4688)
- KMS Tools Unpack.exe (PID: 3240)
- KMS Tools Unpack.exe (PID: 7752)
Reads the computer name
- KMS Tools Unpack.exe (PID: 4688)
- KMS Tools Unpack.exe (PID: 7248)
- KMS Tools Unpack.exe (PID: 7752)
- install.exe (PID: 7652)
- GSetup.exe (PID: 7676)
- KMS Tools Unpack.exe (PID: 3240)
Reads the software policy settings
- slui.exe (PID: 7460)
- slui.exe (PID: 7272)
Creates files in the program directory
- KMS Tools Unpack.exe (PID: 7752)
- install.exe (PID: 7652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .chm | | | Windows HELP File (100) |
|---|
EXIF
EXE
| CHMVersion: | 3 |
|---|---|
| LanguageCode: | Russian |
Total processes
449
Monitored processes
314
Malicious processes
3
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | ping -n 1 localhost | C:\Windows\SysWOW64\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 232 | ping -n 1 localhost | C:\Windows\SysWOW64\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | ping -n 1 localhost | C:\Windows\SysWOW64\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | ping -n 1 localhost | C:\Windows\SysWOW64\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | ping -n 1 localhost | C:\Windows\SysWOW64\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | ping -n 1 localhost | C:\Windows\SysWOW64\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | "C:\Users\admin\Desktop\KMS Tools Unpack.exe" | C:\Users\admin\Desktop\KMS Tools Unpack.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 684 | ping -n 1 localhost | C:\Windows\SysWOW64\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | ping -n 1 localhost | C:\Windows\SysWOW64\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
82 515
Read events
82 510
Write events
3
Delete events
2
Modification events
| (PID) Process: | (7336) hh.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7336) hh.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7336) hh.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7336) hh.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (7336) hh.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
Executable files
0
Suspicious files
4
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7752 | KMS Tools Unpack.exe | C:\Users\admin\Desktop\GSetup.exe | — | |
MD5:— | SHA256:— | |||
| 7752 | KMS Tools Unpack.exe | C:\ProgramData\Setup\install.exe | — | |
MD5:— | SHA256:— | |||
| 7676 | GSetup.exe | C:\Users\admin\Desktop\KMSTools.exe | — | |
MD5:— | SHA256:— | |||
| 7652 | install.exe | C:\ProgramData\Setup\KMSTools.exe | — | |
MD5:— | SHA256:— | |||
| 7336 | hh.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\1[1].JPG | image | |
MD5:422898E1706089EFD5A7E6BD055F2B7F | SHA256:07ED228F125AA77F25B3C9D16B8C4F092253BCD48192E652C63F752162F0D639 | |||
| 7336 | hh.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\_template[1].css | text | |
MD5:AB5BE7866083FC6233445F8AC51AB57C | SHA256:C0254BDDB7DAC7B1E7902A9A5313F2BCF9790113EEE8833E2AD01E377C6C79E0 | |||
| 7652 | install.exe | C:\Users\admin\AppData\Local\Temp\SelfDelete.bat | text | |
MD5:F6767EEC9C4A1965F07A9660B171BAA5 | SHA256:968F596E2ABBC88B2D9B0C74E51129B468FC77AD0687F79BC3A3A25E47F9FA75 | |||
| 7336 | hh.exe | C:\Users\admin\AppData\Local\Temp\IMT823E.tmp | binary | |
MD5:37DD1A3FC6A8F6C87C0DEA4894C67293 | SHA256:04BBCBC68D2BD1692A924256596DD3708E19CB9879CB01CC4BBB6BF76FD74374 | |||
| 7336 | hh.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\9[1].JPG | image | |
MD5:E2F19317D305496857C1213EB1E6F7F8 | SHA256:527D2F2FE980D90CB6CA317AA93BC113643D70C3E7C6A426CF7F274A2A8167D3 | |||
| 7676 | GSetup.exe | C:\Users\admin\AppData\Local\Temp\SelfDelete.bat | text | |
MD5:3A129191A1F32C387628A0BAB6F27B1E | SHA256:37A408CB44CF7A2738A87B719E36502EDDF1CED7F4A5C089563DABF1234C1257 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
24
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.193:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8060 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8060 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.193:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |