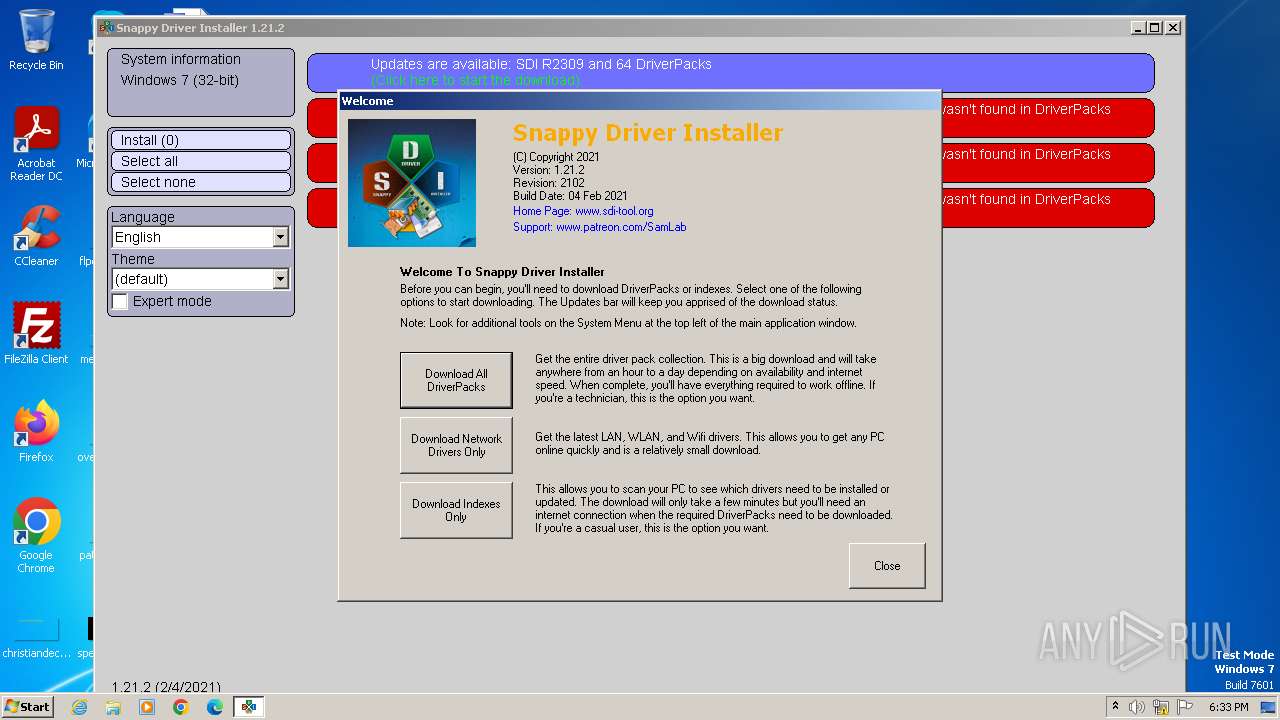
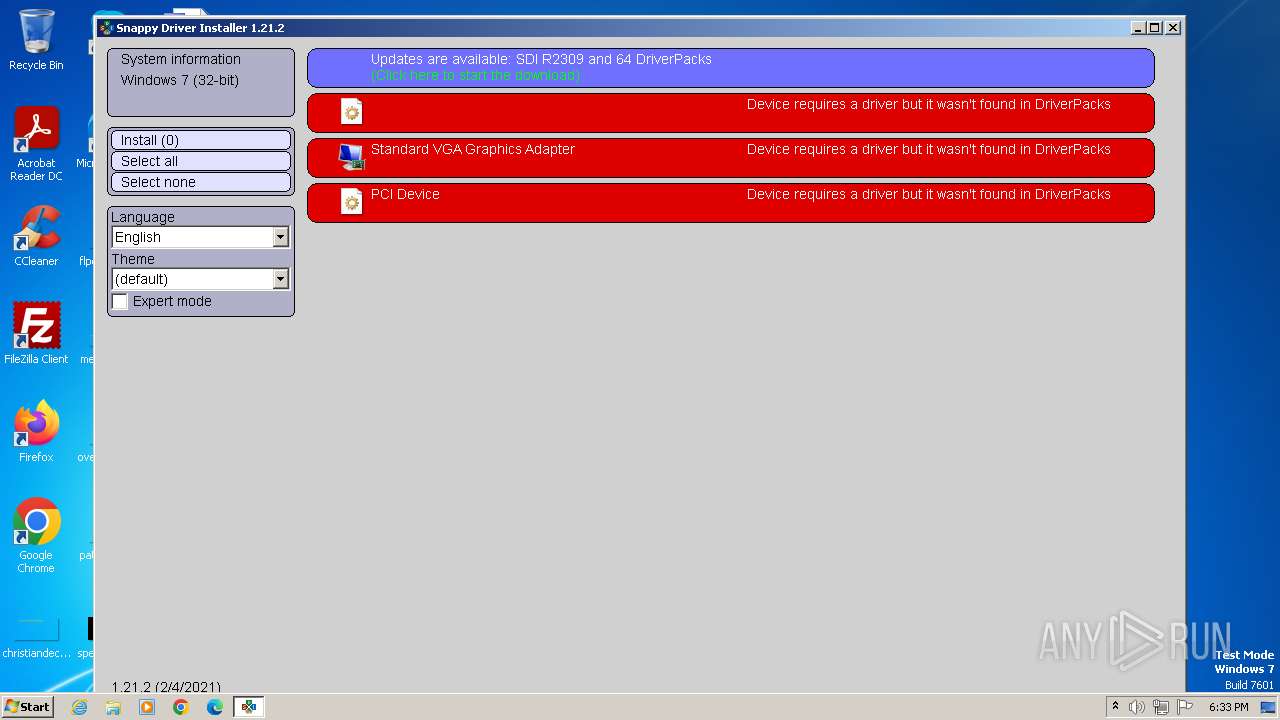
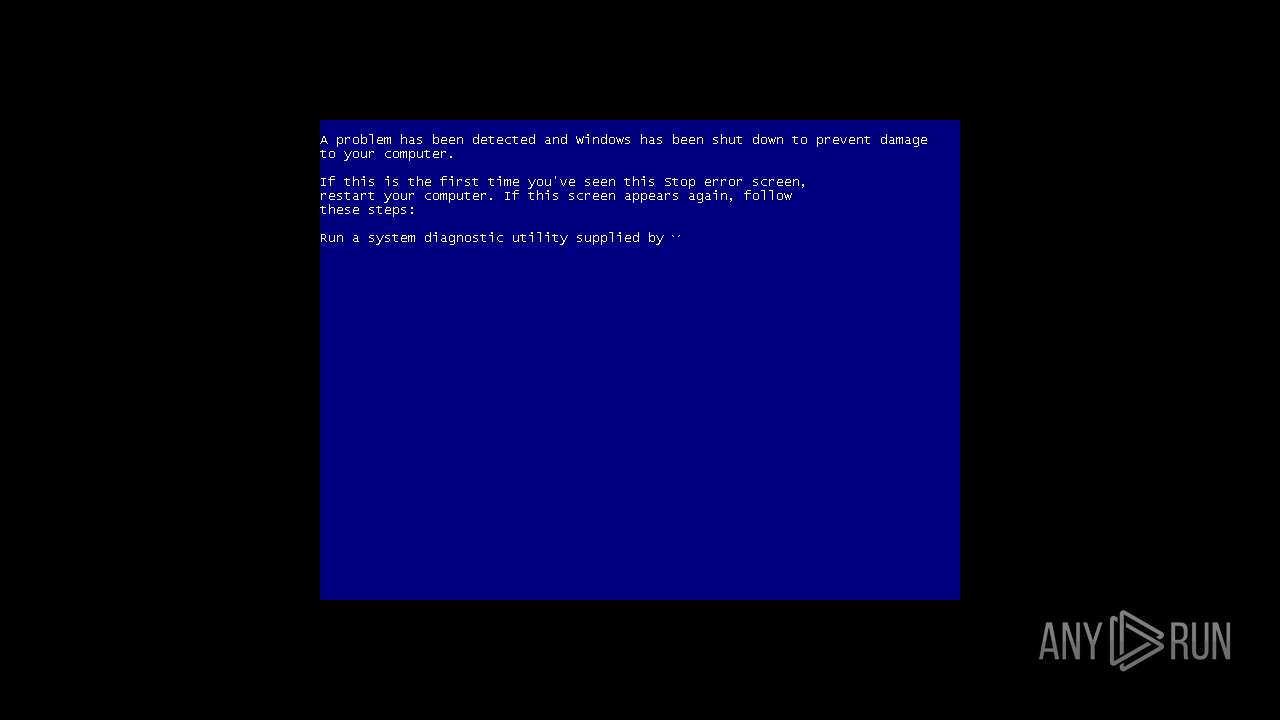
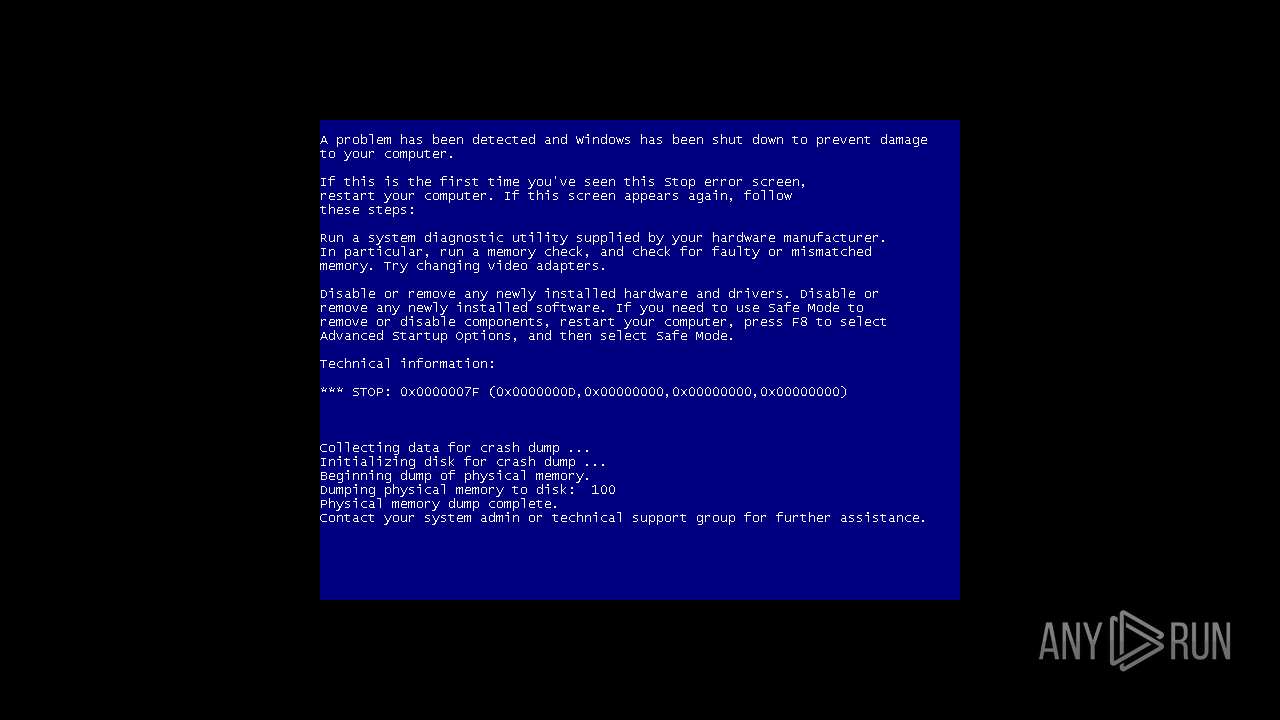
| File name: | SDI_R2102.exe |
| Full analysis: | https://app.any.run/tasks/2b0490cd-6c44-4573-998b-c8f2a8c79783 |
| Verdict: | Malicious activity |
| Analysis date: | May 23, 2024, 17:32:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 (stripped to external PDB), for MS Windows |
| MD5: | F71ED270A20AD7965E61A919B585905F |
| SHA1: | 5AF7BB83DE9471CEE03C18E056E4D12A17753D2B |
| SHA256: | 7FA36B4CDE896CBB9B1A58E746C23BE788E887EDB24E68C388C6A29A8C6393E2 |
| SSDEEP: | 98304:nOPtQ1pAdSDKYeFAfiK+fnVs9RYY/VoBoafw4dX2uxs:M |
MALICIOUS
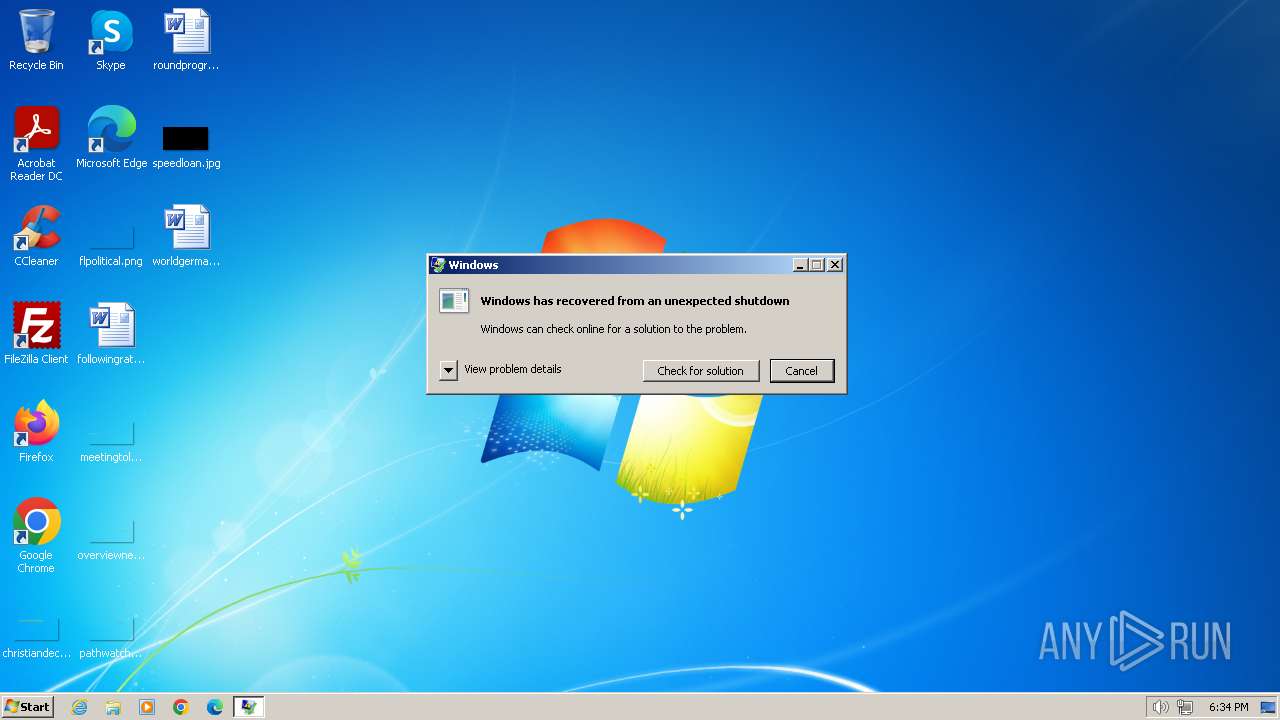
Drops the executable file immediately after the start
- SDI_R2102.exe (PID: 4080)
SUSPICIOUS
Application launched itself
- WerFault.exe (PID: 2128)
Potential Corporate Privacy Violation
- SDI_R2102.exe (PID: 4080)
The process executes via Task Scheduler
- ctfmon.exe (PID: 664)
- sipnotify.exe (PID: 1944)
Connects to unusual port
- SDI_R2102.exe (PID: 4080)
Reads settings of System Certificates
- sipnotify.exe (PID: 1944)
Reads the Internet Settings
- runonce.exe (PID: 2104)
- sipnotify.exe (PID: 1944)
INFO
Create files in a temporary directory
- SDI_R2102.exe (PID: 4080)
- WerFault.exe (PID: 2136)
Checks supported languages
- SDI_R2102.exe (PID: 4080)
- wmpnscfg.exe (PID: 552)
- IMEKLMG.EXE (PID: 2228)
- IMEKLMG.EXE (PID: 2220)
- wmpnscfg.exe (PID: 2512)
- wmpnscfg.exe (PID: 2536)
Reads the machine GUID from the registry
- SDI_R2102.exe (PID: 4080)
Reads the computer name
- SDI_R2102.exe (PID: 4080)
- wmpnscfg.exe (PID: 552)
- IMEKLMG.EXE (PID: 2228)
- IMEKLMG.EXE (PID: 2220)
- wmpnscfg.exe (PID: 2512)
- wmpnscfg.exe (PID: 2536)
Manual execution by a user
- runonce.exe (PID: 2104)
- IMEKLMG.EXE (PID: 2220)
- wmpnscfg.exe (PID: 552)
- IMEKLMG.EXE (PID: 2228)
- wmpnscfg.exe (PID: 2512)
- wmpnscfg.exe (PID: 2536)
Reads security settings of Internet Explorer
- runonce.exe (PID: 2104)
- sipnotify.exe (PID: 1944)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2220)
- IMEKLMG.EXE (PID: 2228)
Reads the software policy settings
- sipnotify.exe (PID: 1944)
Reads the time zone
- runonce.exe (PID: 2104)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.3) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.1) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:02:04 16:02:20+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 3179008 |
| InitializedDataSize: | 4809216 |
| UninitializedDataSize: | 181760 |
| EntryPoint: | 0x14e0 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.21.2.2102 |
| ProductVersionNumber: | 1.21.2.2102 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | www.SamLab.ws |
| FileDescription: | Snappy Driver Installer |
| FileVersion: | 1.21 1.21.2 |
| LegalCopyright: | GNU GPL v3 |
| OriginalFileName: | SDI_1.21.2.exe |
| ProductName: | Snappy Driver Installer |
| ProductVersion: | 1.21.2 |
Total processes
90
Monitored processes
12
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 552 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 664 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1944 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 2104 | runonce.exe /Explorer | C:\Windows\System32\runonce.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2128 | "C:\Windows\System32\WerFault.exe" -k -rq | C:\Windows\System32\WerFault.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2136 | C:\Windows\System32\WerFault.exe -k -q | C:\Windows\System32\WerFault.exe | — | WerFault.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2220 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2228 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2512 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2536 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
7 233
Read events
7 182
Write events
32
Delete events
19
Modification events
| (PID) Process: | (664) ctfmon.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | internat.exe |
Value: | |||
| (PID) Process: | (2104) runonce.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | *WerKernelReporting |
Value: %SYSTEMROOT%\SYSTEM32\WerFault.exe -k -rq | |||
| (PID) Process: | (2104) runonce.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2104) runonce.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2104) runonce.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2104) runonce.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2136) WerFault.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Windows Error Reporting\KernelFaults\Queue |
| Operation: | delete value | Name: | C:\Windows\Minidump\052324-8500-01.dmp |
Value: 踒巵괷ǚ | |||
| (PID) Process: | (2136) WerFault.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Windows Error Reporting\KernelFaults\Queue |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2220) IMEKLMG.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\IMEJP\14.0 |
| Operation: | write | Name: | SetPreload |
Value: 1 | |||
| (PID) Process: | (2228) IMEKLMG.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\IMEKR\14.0 |
| Operation: | write | Name: | SetPreload |
Value: 1 | |||
Executable files
0
Suspicious files
9
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2136 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WER7F73.tmp.cab.tmp | — | |
MD5:— | SHA256:— | |||
| 2136 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\Kernel_0_0_cab_08587fee\Report.wer | — | |
MD5:— | SHA256:— | |||
| 4080 | SDI_R2102.exe | C:\Users\admin\AppData\Local\Temp\logs\2024_05_23__18_33_06__USER-PC_state.snp | binary | |
MD5:971189BF137BF65034AFCB1D001096FF | SHA256:70040E6814E01439491B379A9C768BF4147C6AE4A6ECD0A1DD523AC471340F41 | |||
| 2136 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WER7F72.tmp.cab.tmp | binary | |
MD5:E5AA0ED5F0E7DA78132AE0B18D970274 | SHA256:CD3C82DDA206E5AB07B6DB001F6F30E962FCE5DC6E876708B10DF96A28022F8F | |||
| 2136 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WER7F74.tmp.cab.tmp | binary | |
MD5:EB18567FA1EF4DD683CF1EB2D3597E8A | SHA256:42BDCEDDCDE45144D8EEB5F960F7F852F6F3864843FCEB790B6BD2EF6CC06AF7 | |||
| 1944 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\script.js | text | |
MD5:A2682382967C351F7ED21762F9E5DE9E | SHA256:36B1D26F1EC69685648C0528C2FCE95A3C2DBECF828CDFA4A8B4239A15B644A2 | |||
| 2136 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WER7F76.tmp.cab.tmp | binary | |
MD5:8BA028678E2B812B0A124ADC1BAB3ECE | SHA256:9C43C0DF390C39D64F1E5E8E9E032029A634F0B5CE12B24DE2D20A38BF8A0CEC | |||
| 2136 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WER7F75.tmp.cab.tmp | binary | |
MD5:90252A8086CC23226091E0CBB766562F | SHA256:0B138ABB3D0432C65C53D4462AA46BD8CB3E579DD0489B74DE020DB92121B416 | |||
| 2136 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WER7F71.tmp.cab | compressed | |
MD5:45F81F8B1513072AFA8BFA1F7FE2BD42 | SHA256:EC6C6311A9C96E30E2C5C62C861D9DE18E052A5C9662E813AD2E08F4093C8275 | |||
| 4080 | SDI_R2102.exe | C:\Users\admin\AppData\Local\Temp\logs\2024_05_23__18_33_00__USER-PC_state.snp | binary | |
MD5:5DA9E50DF23F462D2DD6C1A2C82E9351 | SHA256:44B315DB8441F3C8E4FB398638F80444B00FC9CDEECDA78A80D4D9D6D07B351D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
266
DNS requests
6
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4080 | SDI_R2102.exe | GET | 200 | 185.26.122.80:80 | http://driveroff.net/SDI_Update.torrent | unknown | — | — | unknown |
4080 | SDI_R2102.exe | GET | 200 | 192.9.228.30:8080 | http://share.camoe.cn:8080/announce?info_hash=9%c3%b95%91%3e%7bu%b6y%da%ca%a3%b9%f9%cb%b4oH%9c&peer_id=-LT1000-15HPQTgnoafM&port=50171&uploaded=0&downloaded=0&left=44532717023&corrupt=0&key=942CA51&event=started&numwant=200&compact=1&no_peer_id=1&supportcrypto=1&redundant=0 | unknown | — | — | unknown |
1944 | sipnotify.exe | HEAD | 200 | 23.61.141.106:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133609628331400000 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4080 | SDI_R2102.exe | 185.26.122.80:80 | driveroff.net | Hostland LTD | RU | unknown |
4080 | SDI_R2102.exe | 239.192.152.143:6771 | — | — | — | unknown |
4080 | SDI_R2102.exe | 67.215.246.10:6881 | router.bittorrent.com | — | — | unknown |
4080 | SDI_R2102.exe | 49.13.77.253:6881 | router.bitcomet.com | — | — | unknown |
4080 | SDI_R2102.exe | 82.221.103.244:6881 | router.utorrent.com | — | — | unknown |
4080 | SDI_R2102.exe | 192.9.228.30:8080 | share.camoe.cn | ORACLE-BMC-31898 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
router.bittorrent.com |
| shared |
router.utorrent.com |
| whitelisted |
router.bitcomet.com |
| unknown |
driveroff.net |
| unknown |
share.camoe.cn |
| unknown |
query.prod.cms.rt.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4080 | SDI_R2102.exe | Potential Corporate Privacy Violation | ET P2P Possible Torrent Download via HTTP Request |
— | — | Potential Corporate Privacy Violation | ET P2P BitTorrent - Torrent File Downloaded |
4080 | SDI_R2102.exe | Potential Corporate Privacy Violation | ET P2P BitTorrent DHT ping request |
— | — | Potential Corporate Privacy Violation | GPL P2P BitTorrent announce request |