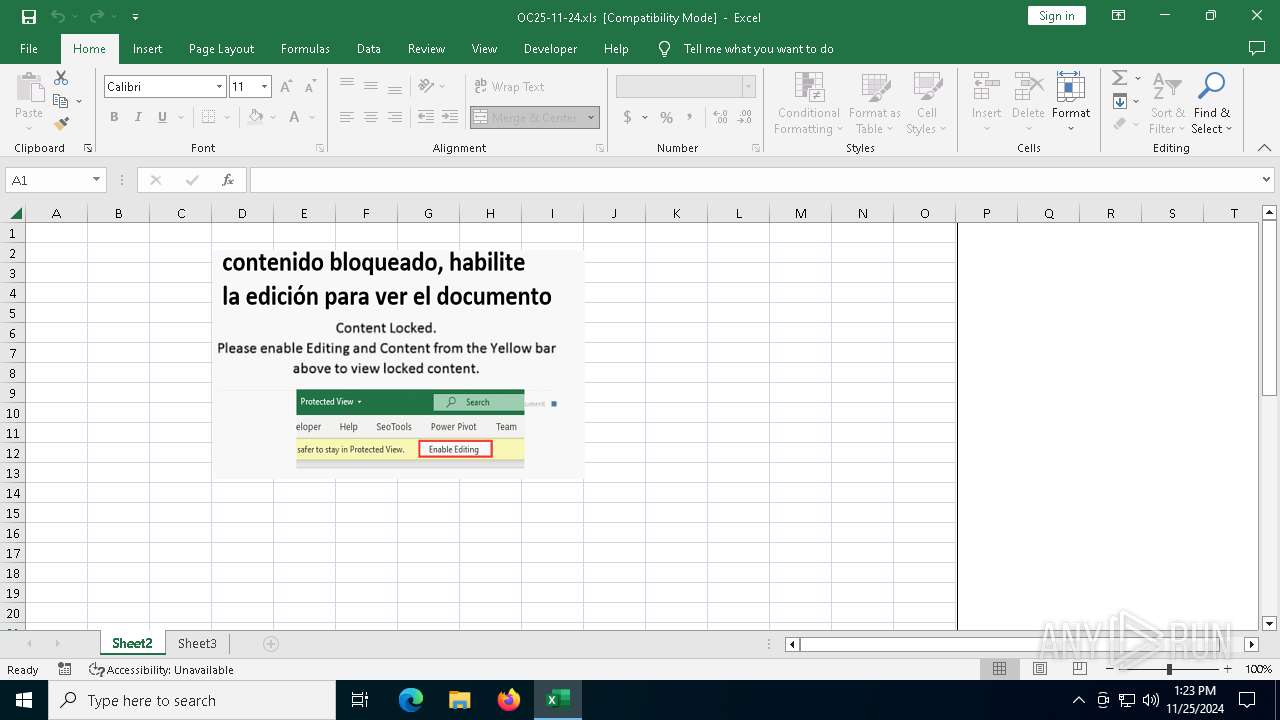
| File name: | OC25-11-24.xls |
| Full analysis: | https://app.any.run/tasks/9c34f629-5fb1-4b0a-9361-767d9ad6bc1f |
| Verdict: | Malicious activity |
| Analysis date: | November 25, 2024, 13:22:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Name of Creating Application: Microsoft Excel, Create Time/Date: Sat Sep 16 00:00:00 2006, Last Saved Time/Date: Mon Nov 25 11:48:53 2024, Security: 1 |
| MD5: | D923DC9F1ABD640E545D1992BEF70FB4 |
| SHA1: | 1C69FD2C258F80163DDE3AA3B6E96AE9B4A42FA1 |
| SHA256: | 7F8C3780744584BC15D10CD35195CAD98506691E51F75714F35A295E7D4ED638 |
| SSDEEP: | 6144:jxUhHcI5z7r6V6ETINU02MECkZlNWT27uwYuD:jxUhHX17r1gx02MmZlN0aHYuD |
MALICIOUS
Drops known malicious image
- EXCEL.EXE (PID: 6296)
SUSPICIOUS
Sets XML DOM element text (SCRIPT)
- splwow64.exe (PID: 6704)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| Author: | - |
|---|---|
| LastModifiedBy: | - |
| Software: | Microsoft Excel |
| CreateDate: | 2006:09:16 00:00:00 |
| ModifyDate: | 2024:11:25 11:48:53 |
| Security: | Password protected |
| CodePage: | Windows Latin 1 (Western European) |
| AppVersion: | 12 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
| CompObjUserTypeLen: | 38 |
| CompObjUserType: | Microsoft Office Excel 2003 Worksheet |
Total processes
135
Monitored processes
2
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6296 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" C:\Users\admin\AppData\Local\Temp\OC25-11-24.xls | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6704 | C:\WINDOWS\splwow64.exe 8192 | C:\Windows\splwow64.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 440
Read events
6 185
Write events
231
Delete events
24
Modification events
| (PID) Process: | (6296) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (6296) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\EXCEL\6296 |
| Operation: | write | Name: | 0 |
Value: 0B0E10FF9007DB1FF7E64FA1DD2ED2512EECB7230046BA9D92B3D2E7CFED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5119831D2120965007800630065006C002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6296) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (6296) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (6296) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (6296) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (6296) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (6296) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (6296) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (6296) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
0
Suspicious files
12
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6296 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:CD901CA7B065557DC8F2F56CD6980F47 | SHA256:AED51E443B0AC7FCE0760CEF8D16603BA4D47A28DC10553B630284E775ECBF87 | |||
| 6296 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:C3F4B1BA303F1EB7771D481E85E269AE | SHA256:10027189FAD77602BCFEB8E6C7D6AA5E2F561C8FC9F0FA28924BD5C9739674B6 | |||
| 6296 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\A134FC08-FFFE-48BC-82D9-F9FBAFB01FBD | xml | |
MD5:40A596F1AE88E21E4BE9E924C6BDB01C | SHA256:220165CE5FCE6E6CC71A7AC031BBBC7143FAC1222E4C6E3D7E05D633C7BBB8D8 | |||
| 6296 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | der | |
MD5:99BA6B7F0F3EC8D66A8B6A80669C7B3D | SHA256:D3B813690DFC256C53B3AF9FC4015F5AA3344ABB4416CE0D79BC2CE6603D299B | |||
| 6296 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\B288DE6D.emf | binary | |
MD5:BB7E0B7055A570167131B2B6861CB461 | SHA256:E9AD1DC6FD3237803D6B2BA631DA5D70593655E5BAD780E9C383F6509D2B1C3F | |||
| 6296 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\excel.exe_Rules.xml | xml | |
MD5:13AF026BB17E87B1A24C00E8295447B0 | SHA256:4695B860F6568E9EDDC220E4C80C848D5B6BE780C9A4A31FAD4D878E098FF8DB | |||
| 6296 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json.tmp | binary | |
MD5:342D573DAD45DBB9F0F3253D39FD0F00 | SHA256:272520269B0689CE0813A1E4D6608230E6CA1D757DCD5B44FAD102795B785C50 | |||
| 6296 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\PreviewFont\flat_officeFontsPreview_4_40.ttf | binary | |
MD5:4296A064B917926682E7EED650D4A745 | SHA256:E04E41C74D6C78213BA1588BACEE64B42C0EDECE85224C474A714F39960D8083 | |||
| 6296 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json | binary | |
MD5:342D573DAD45DBB9F0F3253D39FD0F00 | SHA256:272520269B0689CE0813A1E4D6608230E6CA1D757DCD5B44FAD102795B785C50 | |||
| 6296 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\b8ab77100df80ab2.customDestinations-ms | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
40
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3568 | svchost.exe | GET | 200 | 2.16.164.43:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3568 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4384 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4384 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6492 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6296 | EXCEL.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4804 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3568 | svchost.exe | 2.16.164.43:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.23.209.149:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
3568 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |