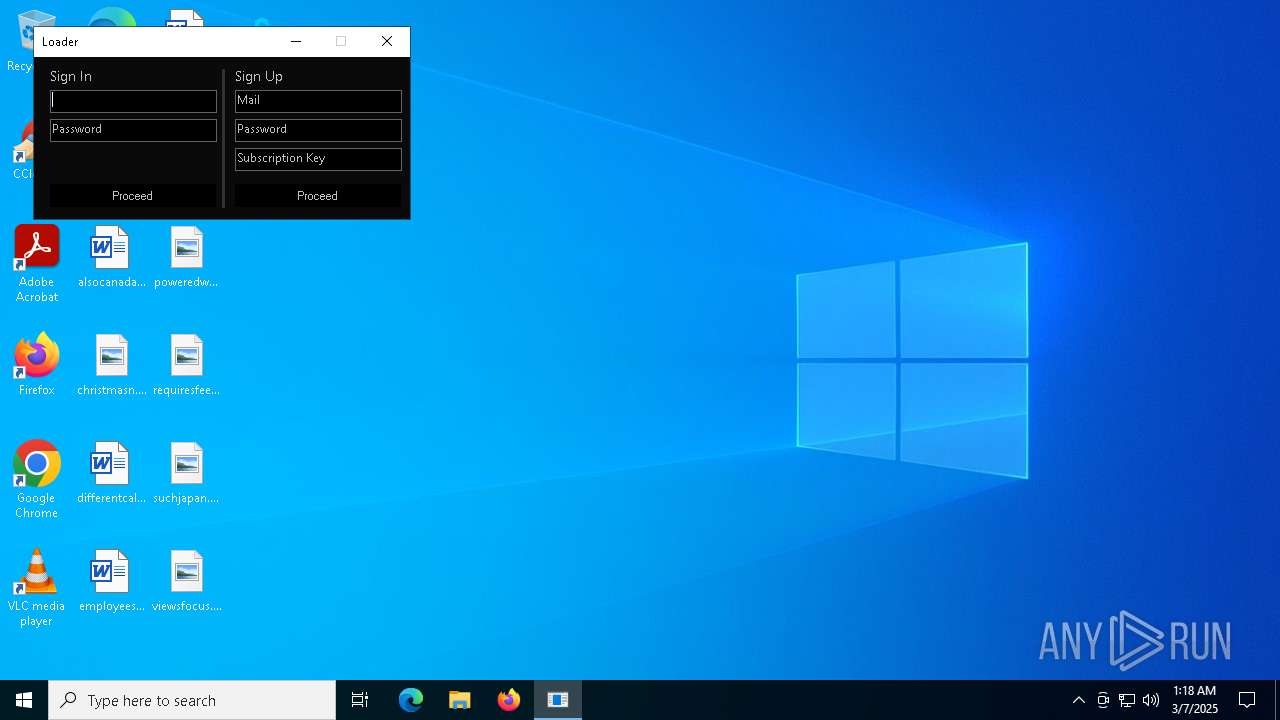
| File name: | Seliware.exe |
| Full analysis: | https://app.any.run/tasks/d4fc7301-4d1f-4a43-baac-0939e1a46cc1 |
| Verdict: | Malicious activity |
| Analysis date: | March 07, 2025, 01:18:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 8 sections |
| MD5: | 2790AF19BEA9B6602D4D1B23C88B0463 |
| SHA1: | 77EF3E0A96F1DF2373B3B71363A596666508782F |
| SHA256: | 7F833702251B3DC148C41FA505B7464183B5451DBFBB736405170A5DAEDA6045 |
| SSDEEP: | 49152:0MECrOQhbmLlYYyIlAmLlYYyIlveUw11lfcAA7b+3wUPcfXOKbkjy7gK3HpjexWS:0MRrqLlaUBLlaUveUu3wHnmeRyyrXpS5 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- Seliware.exe (PID: 6192)
Reads security settings of Internet Explorer
- Seliware.exe (PID: 6192)
Executable content was dropped or overwritten
- Seliware.exe (PID: 6192)
Reads the date of Windows installation
- Seliware.exe (PID: 6192)
INFO
Reads the computer name
- Seliware.exe (PID: 6192)
- SeliwareLoaderRewrite.exe (PID: 5800)
Create files in a temporary directory
- Seliware.exe (PID: 6192)
Checks supported languages
- Seliware.exe (PID: 6192)
- SeliwareLoaderRewrite.exe (PID: 5800)
Process checks computer location settings
- Seliware.exe (PID: 6192)
Reads the machine GUID from the registry
- SeliwareLoaderRewrite.exe (PID: 5800)
Reads Environment values
- SeliwareLoaderRewrite.exe (PID: 5800)
Disables trace logs
- SeliwareLoaderRewrite.exe (PID: 5800)
Checks proxy server information
- SeliwareLoaderRewrite.exe (PID: 5800)
- slui.exe (PID: 1512)
Reads the software policy settings
- SeliwareLoaderRewrite.exe (PID: 5800)
- slui.exe (PID: 1512)
.NET Reactor protector has been detected
- SeliwareLoaderRewrite.exe (PID: 5800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:05:12 10:17:15+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.33 |
| CodeSize: | 236032 |
| InitializedDataSize: | 482304 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x266b0 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
126
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1512 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5800 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\SeliwareLoaderRewrite.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\SeliwareLoaderRewrite.exe | Seliware.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: SeliwareLoaderRewrite Version: 1.0.0.0 Modules
| |||||||||||||||
| 6192 | "C:\Users\admin\Desktop\Seliware.exe" | C:\Users\admin\Desktop\Seliware.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6644 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\SeliwareLoaderRewrite.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\SeliwareLoaderRewrite.exe | — | Seliware.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: SeliwareLoaderRewrite Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
7 435
Read events
7 421
Write events
14
Delete events
0
Modification events
| (PID) Process: | (5800) SeliwareLoaderRewrite.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SeliwareLoaderRewrite_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5800) SeliwareLoaderRewrite.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SeliwareLoaderRewrite_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5800) SeliwareLoaderRewrite.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SeliwareLoaderRewrite_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5800) SeliwareLoaderRewrite.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SeliwareLoaderRewrite_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5800) SeliwareLoaderRewrite.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SeliwareLoaderRewrite_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5800) SeliwareLoaderRewrite.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SeliwareLoaderRewrite_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (5800) SeliwareLoaderRewrite.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SeliwareLoaderRewrite_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (5800) SeliwareLoaderRewrite.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SeliwareLoaderRewrite_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5800) SeliwareLoaderRewrite.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SeliwareLoaderRewrite_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5800) SeliwareLoaderRewrite.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SeliwareLoaderRewrite_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
8
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6192 | Seliware.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\System.Numerics.Vectors.dll | executable | |
MD5:AAA2CBF14E06E9D3586D8A4ED455DB33 | SHA256:1D3EF8698281E7CF7371D1554AFEF5872B39F96C26DA772210A33DA041BA1183 | |||
| 6192 | Seliware.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\System.Memory.dll | executable | |
MD5:6FB95A357A3F7E88ADE5C1629E2801F8 | SHA256:8E76318E8B06692ABF7DAB1169D27D15557F7F0A34D36AF6463EFF0FE21213C7 | |||
| 6192 | Seliware.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\SeliwareLoaderRewrite.exe | executable | |
MD5:C08AE983171F995E60FD8C89CCB3A7E1 | SHA256:D2911F61A56D4F9CF97D5F4D76E7AD03032E63BD38553EEFBC2A4B026B201B04 | |||
| 6192 | Seliware.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Newtonsoft.Json.dll | executable | |
MD5:195FFB7167DB3219B217C4FD439EEDD6 | SHA256:E1E27AF7B07EEEDF5CE71A9255F0422816A6FC5849A483C6714E1B472044FA9D | |||
| 6192 | Seliware.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\System.Runtime.CompilerServices.Unsafe.dll | executable | |
MD5:DA04A75DDC22118ED24E0B53E474805A | SHA256:66409F670315AFE8610F17A4D3A1EE52D72B6A46C544CEC97544E8385F90AD74 | |||
| 6192 | Seliware.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\ICSharpCode.SharpZipLib.dll | executable | |
MD5:9E9E0A210297968AAF2E00D13958C0B4 | SHA256:CB9C05B5A1E1DB26FF43490EE26F2E02ABAE3F321D2DD5DDD43A68DA48EAB83D | |||
| 6192 | Seliware.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\System.Buffers.dll | executable | |
MD5:ECDFE8EDE869D2CCC6BF99981EA96400 | SHA256:ACCCCFBE45D9F08FFEED9916E37B33E98C65BE012CFFF6E7FA7B67210CE1FEFB | |||
| 6192 | Seliware.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\System.Threading.Tasks.Extensions.dll | executable | |
MD5:0F384AFCF671483188B9019D3B7457A7 | SHA256:2C9CAD6410E37E44FA73CCCB576F418184F1AE5A0A257E165A136BDAA941A0C6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
21
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 200 | 188.114.97.3:443 | https://seliware.com/authenticate | unknown | binary | 18 b | unknown |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5800 | SeliwareLoaderRewrite.exe | 188.114.96.3:443 | seliware.com | CLOUDFLARENET | NL | unknown |
1272 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1512 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
seliware.com |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |