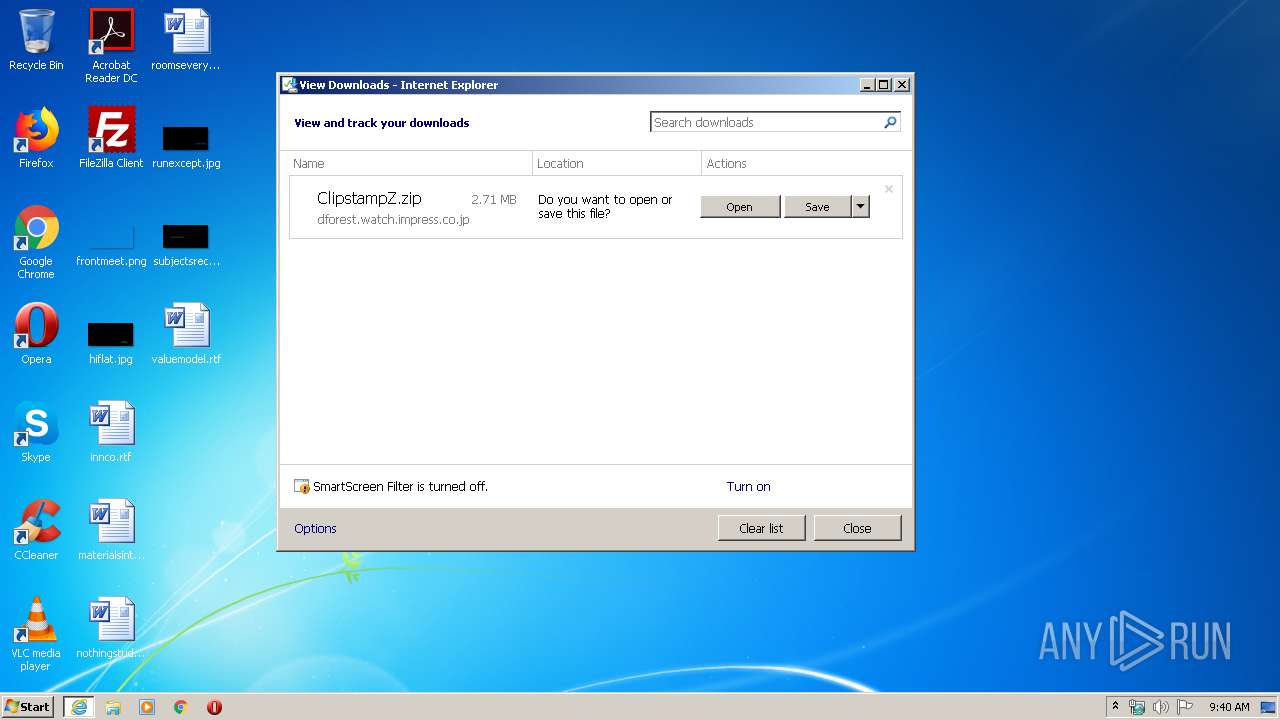
| URL: | https://dforest.watch.impress.co.jp/library/c/clipstamp/10893/ClipstampZ.zip |
| Full analysis: | https://app.any.run/tasks/11b413fb-1a59-4498-aebb-2f4d817316b1 |
| Verdict: | No threats detected |
| Analysis date: | April 09, 2020, 08:40:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 37EC1C4659B0EB6D338CAAD282260971 |
| SHA1: | A89247EA1E3FC4C83DBACFA76F50184903C894EF |
| SHA256: | 7F816D24AB9E744119F74BB48F7E4A611C99A55B30FB25F2738E0DCF6ED8FBF4 |
| SSDEEP: | 3:N8bKXp3gW3cGCGeN+MAEPVn:2e9nCtzAEtn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
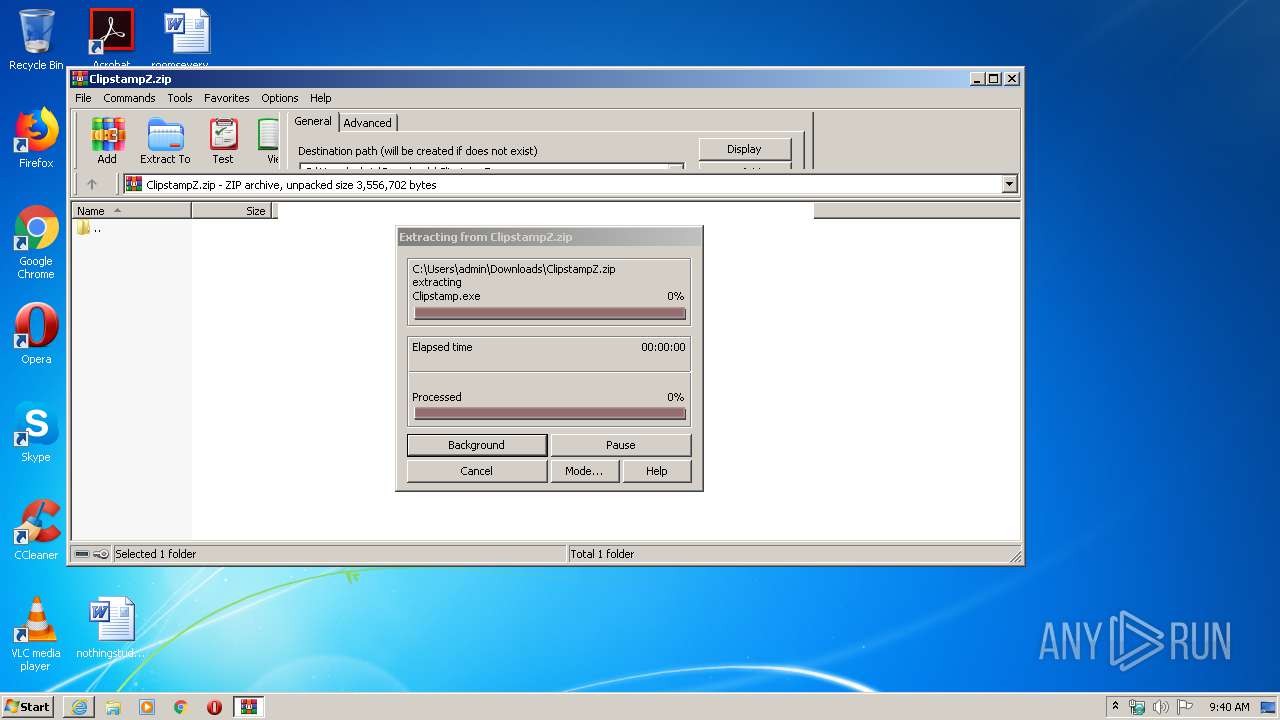
- WinRAR.exe (PID: 3088)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 3640)
- iexplore.exe (PID: 2072)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 440)
- WINWORD.EXE (PID: 2748)
- WINWORD.EXE (PID: 3724)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3640)
Changes internet zones settings
- iexplore.exe (PID: 3640)
Application launched itself
- iexplore.exe (PID: 3640)
Manual execution by user
- WINWORD.EXE (PID: 2748)
- WINWORD.EXE (PID: 440)
- WINWORD.EXE (PID: 3724)
Creates files in the user directory
- WINWORD.EXE (PID: 2748)
- WINWORD.EXE (PID: 3724)
Reads settings of System Certificates
- iexplore.exe (PID: 2072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
42
Monitored processes
6
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\~$omseverything.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2072 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3640 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2748 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\valuemodel.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3088 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\ClipstampZ.zip" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3640 | "C:\Program Files\Internet Explorer\iexplore.exe" https://dforest.watch.impress.co.jp/library/c/clipstamp/10893/ClipstampZ.zip | C:\Program Files\Internet Explorer\iexplore.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3724 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\roomseverything.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
3 836
Read events
3 112
Write events
425
Delete events
299
Modification events
| (PID) Process: | (2072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\LowCache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\LowCache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\LowCache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3640) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 2616316662 | |||
| (PID) Process: | (3640) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30805578 | |||
| (PID) Process: | (3640) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3640) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3640) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3640) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3640) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
Executable files
2
Suspicious files
11
Text files
6
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2072 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab4356.tmp | — | |
MD5:— | SHA256:— | |||
| 2072 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar4357.tmp | — | |
MD5:— | SHA256:— | |||
| 2072 | iexplore.exe | C:\Users\admin\Downloads\ClipstampZ.zip.gb9ay00.partial | — | |
MD5:— | SHA256:— | |||
| 3640 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF295601AB2A169CA6.TMP | — | |
MD5:— | SHA256:— | |||
| 3640 | iexplore.exe | C:\Users\admin\Downloads\ClipstampZ.zip.gb9ay00.partial:Zone.Identifier | — | |
MD5:— | SHA256:— | |||
| 3640 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFA1FD56DC49EC2838.TMP | — | |
MD5:— | SHA256:— | |||
| 3640 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{C7B33269-7A3D-11EA-972D-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 2748 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRC8B2.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2748 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{6C0404D9-EA83-46A9-BDC3-57CDDA2E45D0}.tmp | — | |
MD5:— | SHA256:— | |||
| 2748 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{A2BB5460-5173-4F0E-BAC4-C1DB2E093C3E}.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
6
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2072 | iexplore.exe | GET | 200 | 104.41.179.244:80 | http://ocsp.cybertrust.ne.jp/OcspServer/MFUwUzBRME8wTTAJBgUrDgMCGgUABBR5QrJnas7nAW1uF6lDsi8LMOggpwQUc6gIUym4FfuZgOXFN9j4OXukEwYCFEOYCxQTLsRu6HsuIZ7iRhXJ1uo6 | JP | der | 1.43 Kb | whitelisted |
2072 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAVDQNCixMyBEfqoN31G4G8%3D | US | der | 1.47 Kb | whitelisted |
2072 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAVDQNCixMyBEfqoN31G4G8%3D | US | der | 1.47 Kb | whitelisted |
2072 | iexplore.exe | GET | 200 | 104.41.179.244:80 | http://ocsp.cybertrust.ne.jp/OcspServer/MFUwUzBRME8wTTAJBgUrDgMCGgUABBR5QrJnas7nAW1uF6lDsi8LMOggpwQUc6gIUym4FfuZgOXFN9j4OXukEwYCFEOYCxQTLsRu6HsuIZ7iRhXJ1uo6 | JP | der | 1.43 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2072 | iexplore.exe | 118.238.26.53:443 | dforest.watch.impress.co.jp | So-net Entertainment Corporation | JP | unknown |
2072 | iexplore.exe | 104.41.179.244:80 | ocsp.cybertrust.ne.jp | Microsoft Corporation | JP | unknown |
2072 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dforest.watch.impress.co.jp |
| suspicious |
ocsp.digicert.com |
| whitelisted |
ocsp.cybertrust.ne.jp |
| whitelisted |