| URL: | x.com |
| Full analysis: | https://app.any.run/tasks/435dd001-d05c-4e63-b97f-9d3fbe221813 |
| Verdict: | Malicious activity |
| Analysis date: | February 27, 2024, 14:31:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 9A4323A3426983AB24744F3FDBD15200 |
| SHA1: | 71AC3B64AD14777054A74CA197A7C160E61562D1 |
| SHA256: | 7F7ED12DFE7AF503DB4F7D8CFA1A264A4F9610FD6677B8AE297EB9DFAFAB279D |
| SSDEEP: | 3:4n:4 |
MALICIOUS
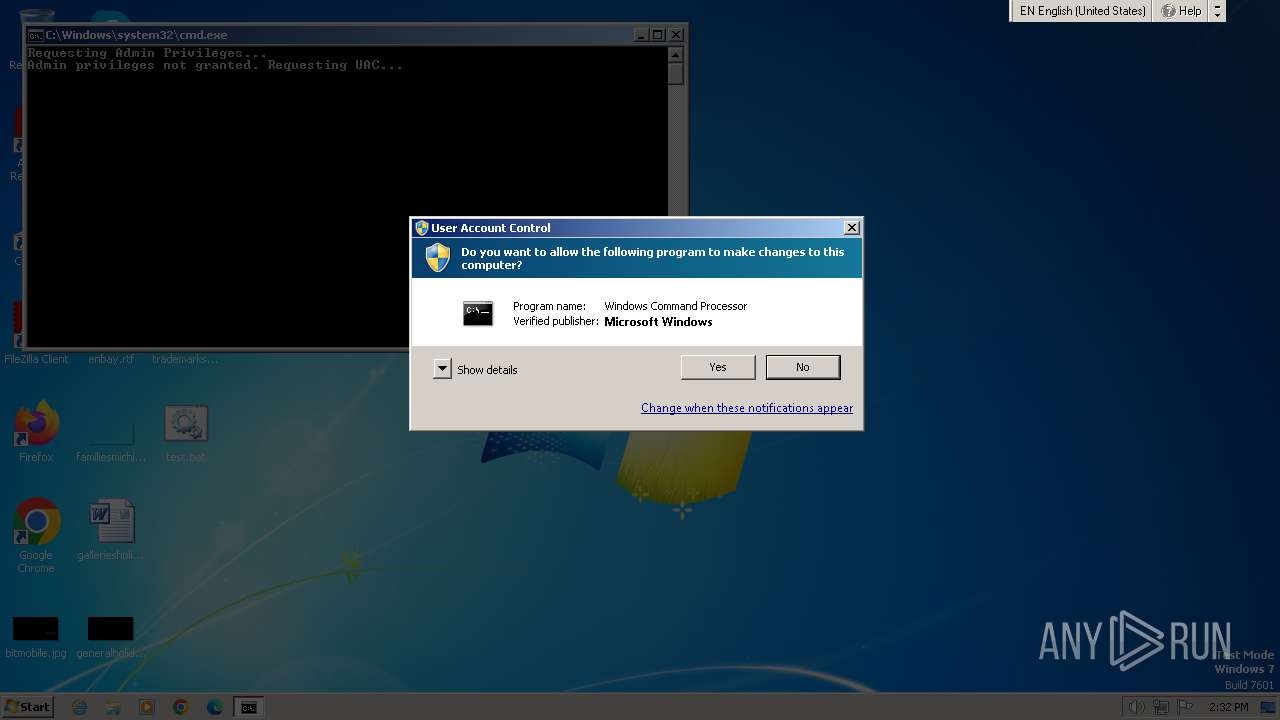
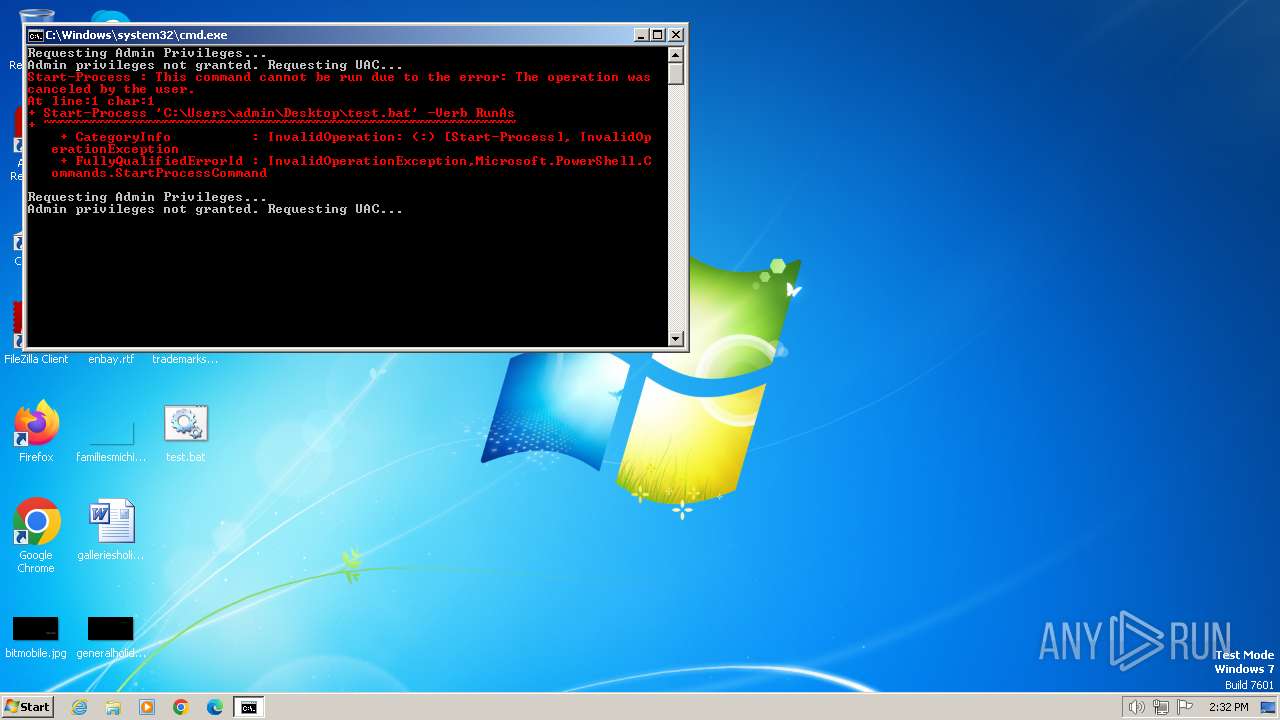
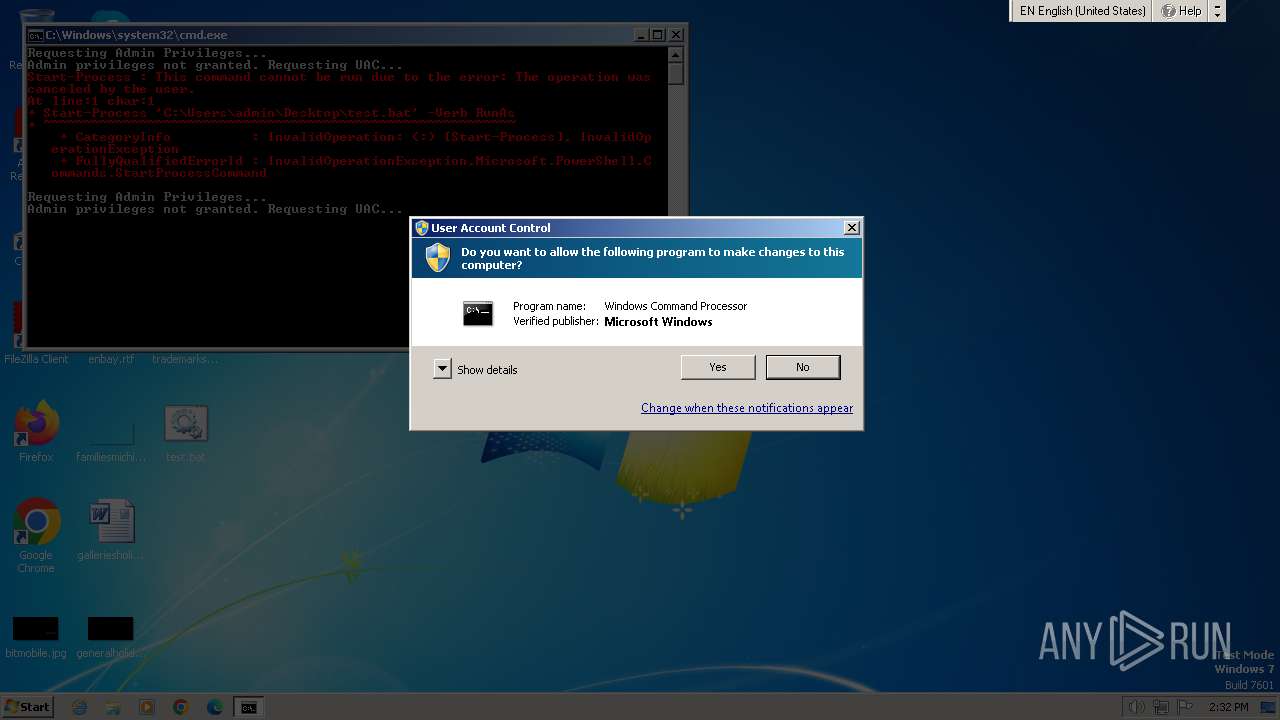
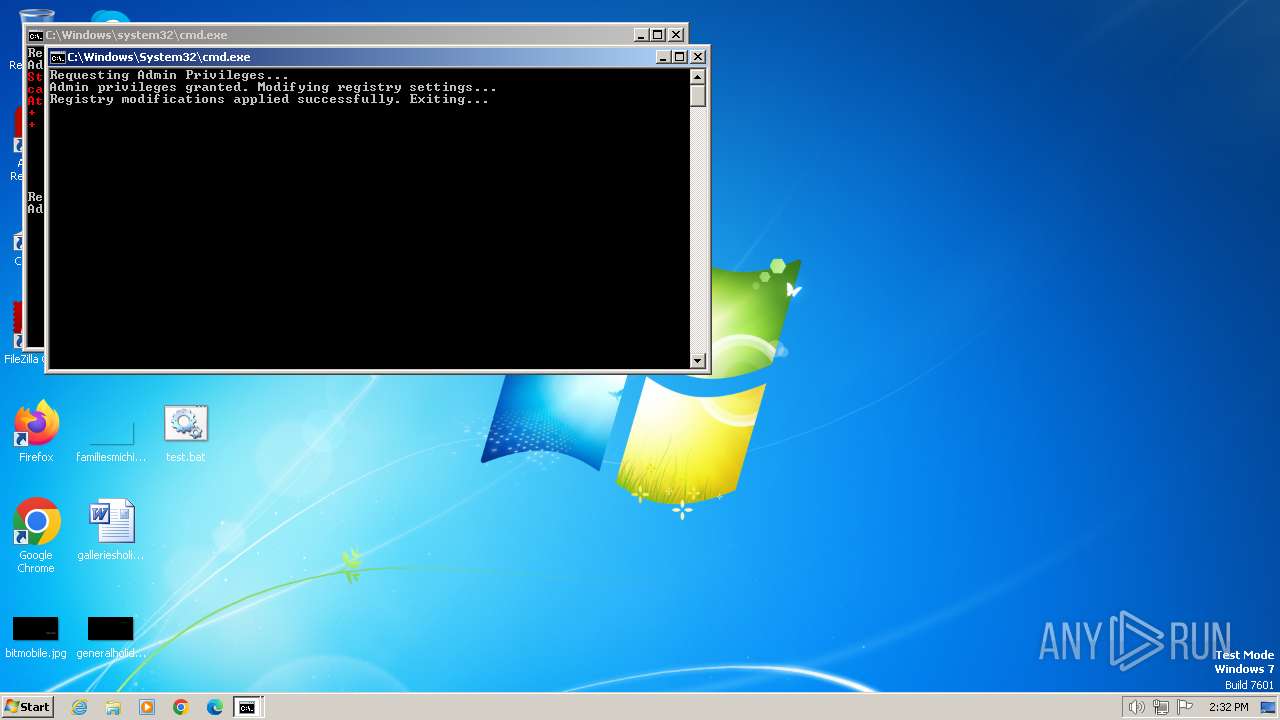
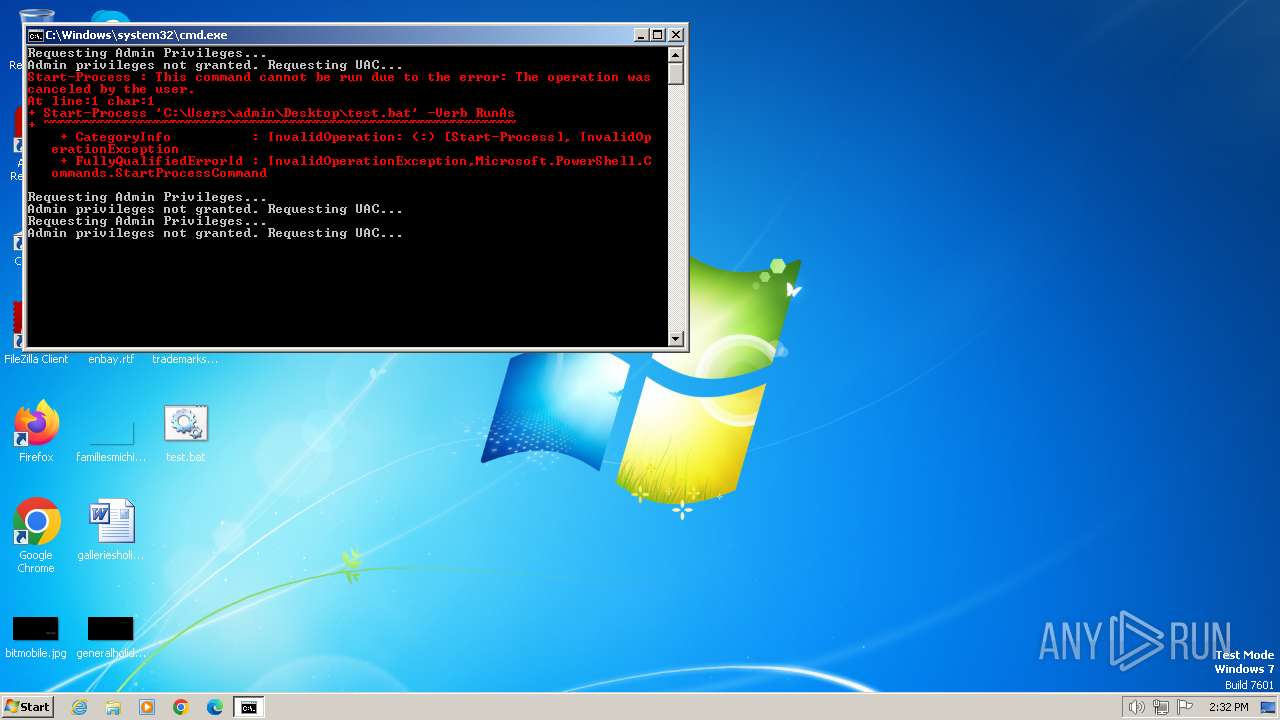
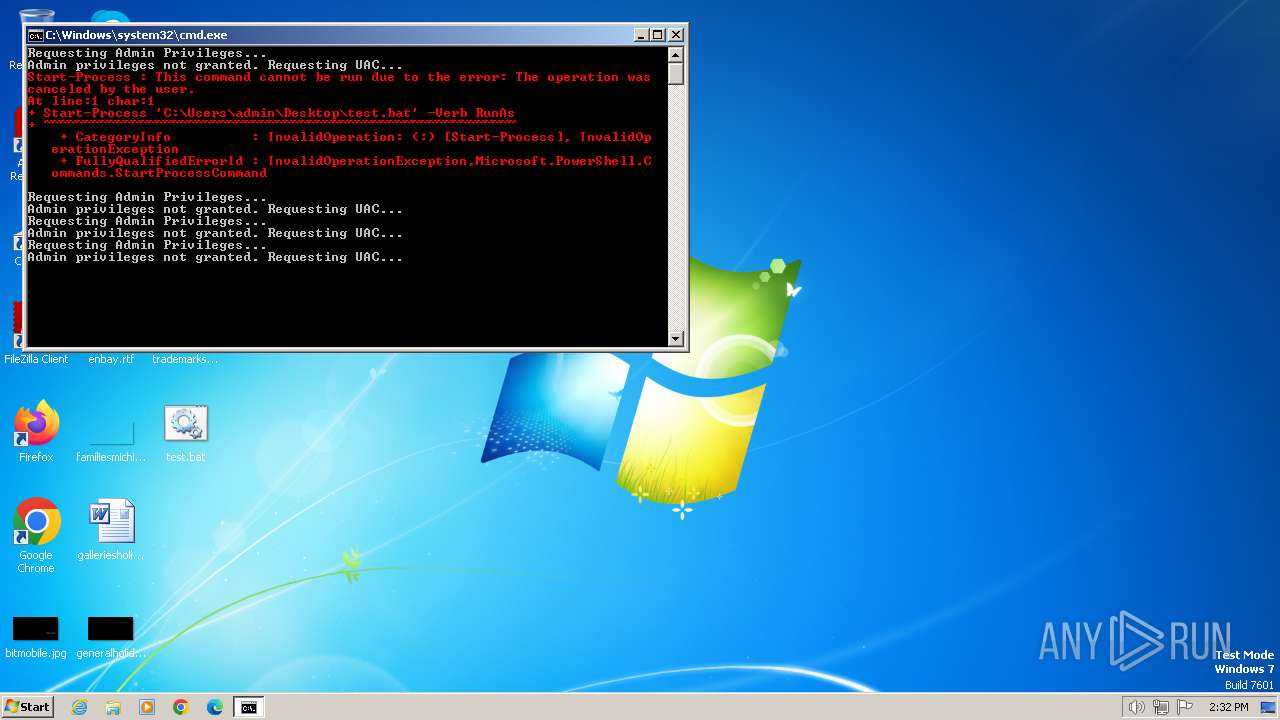
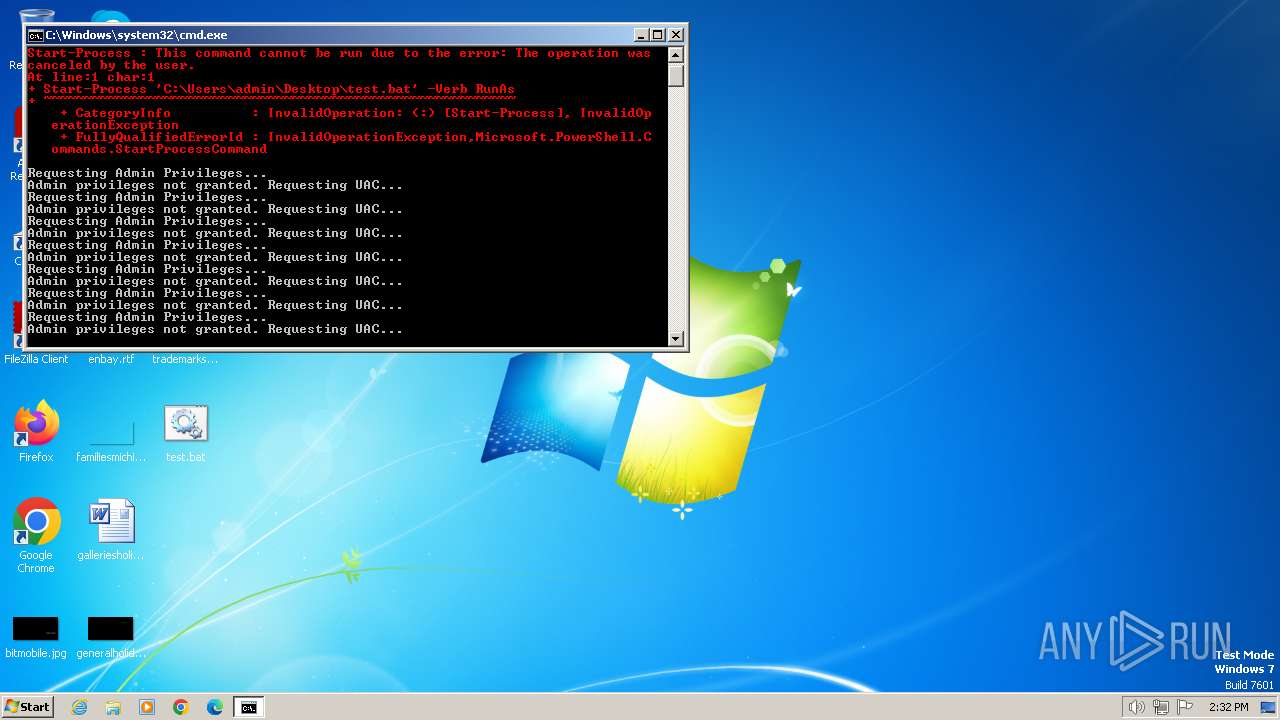
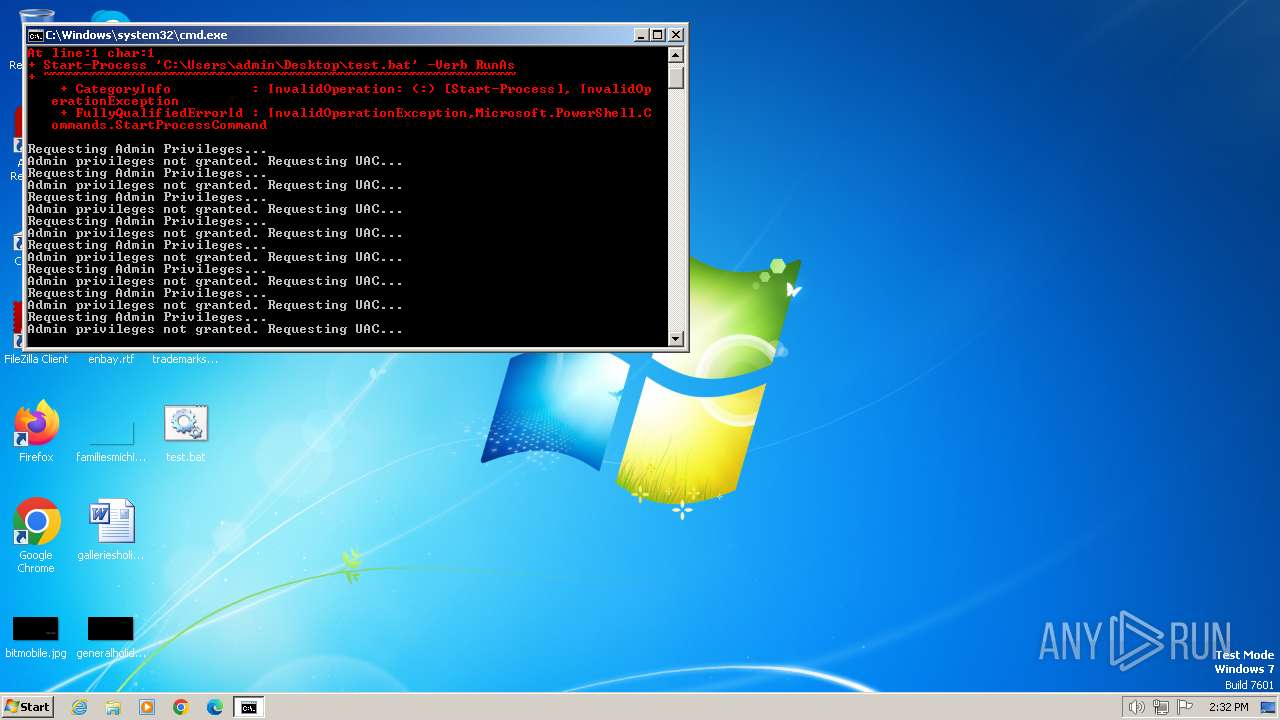
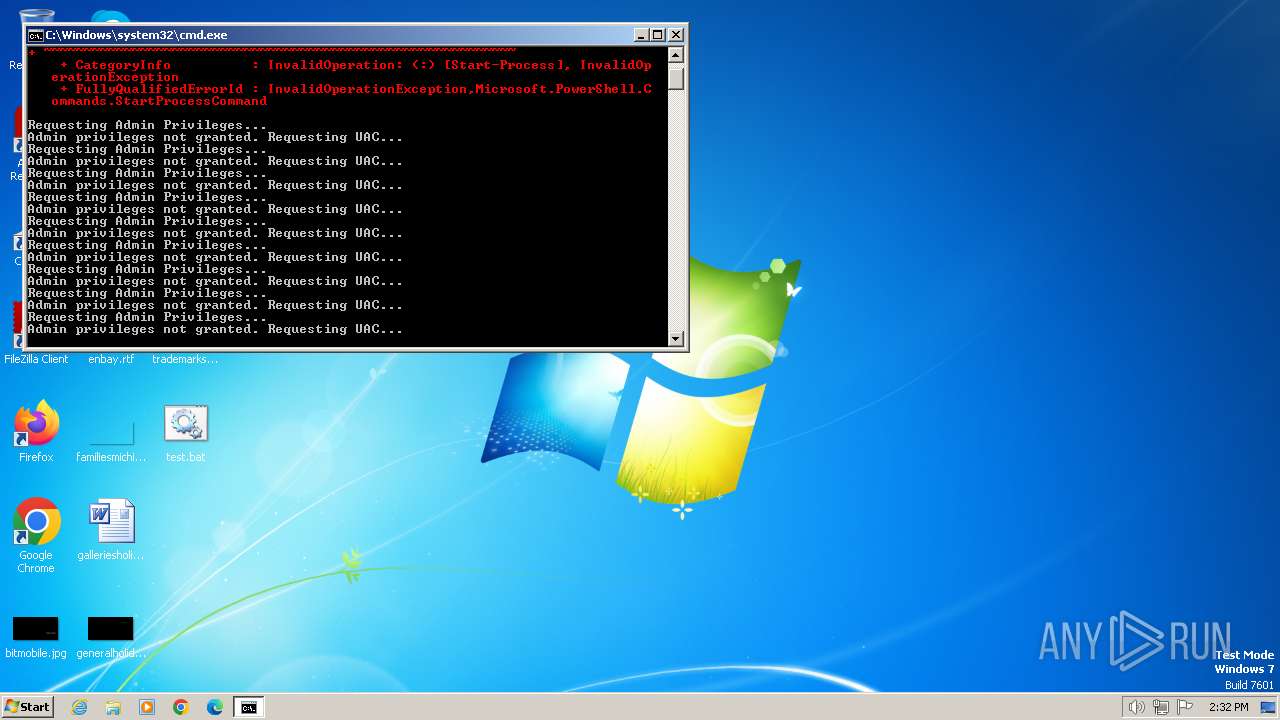
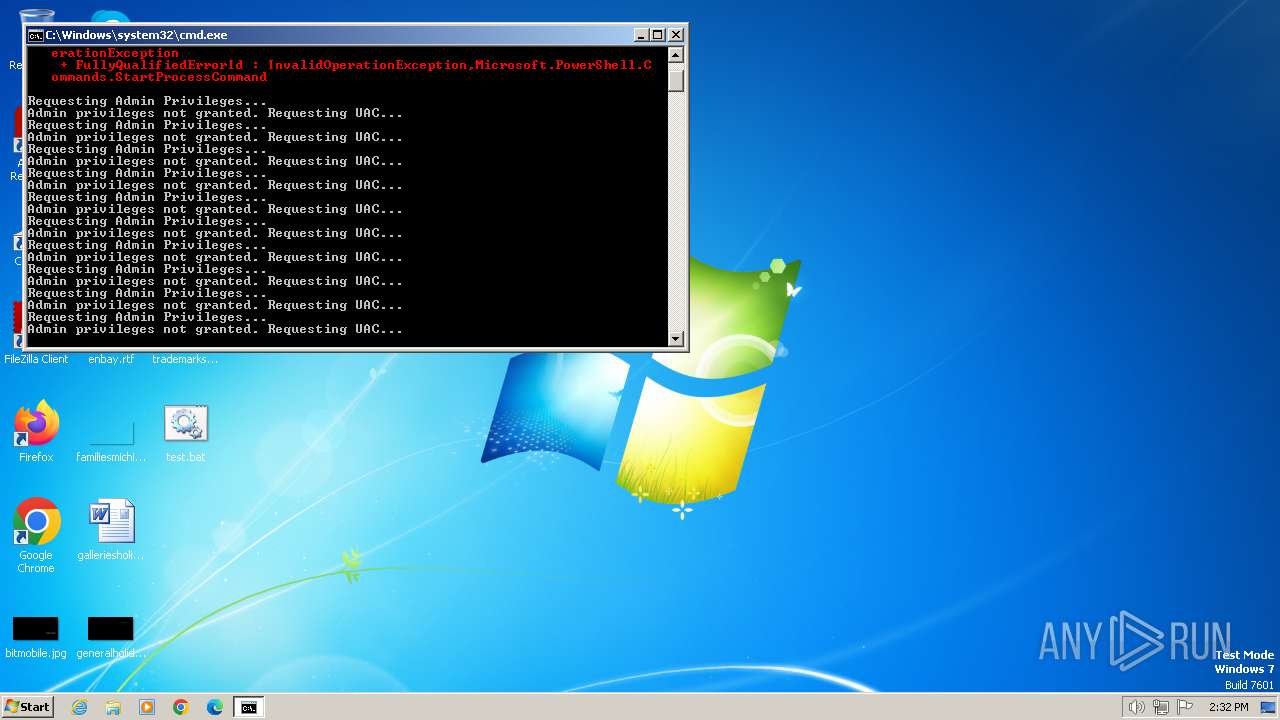
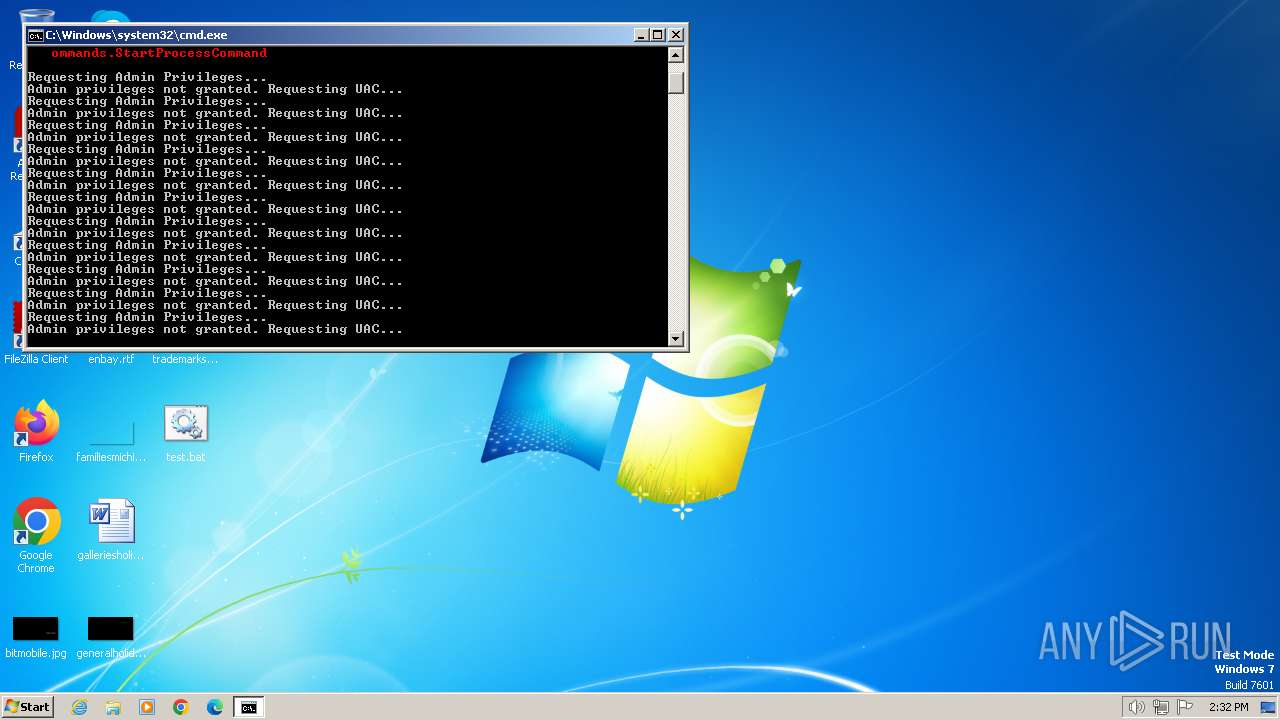
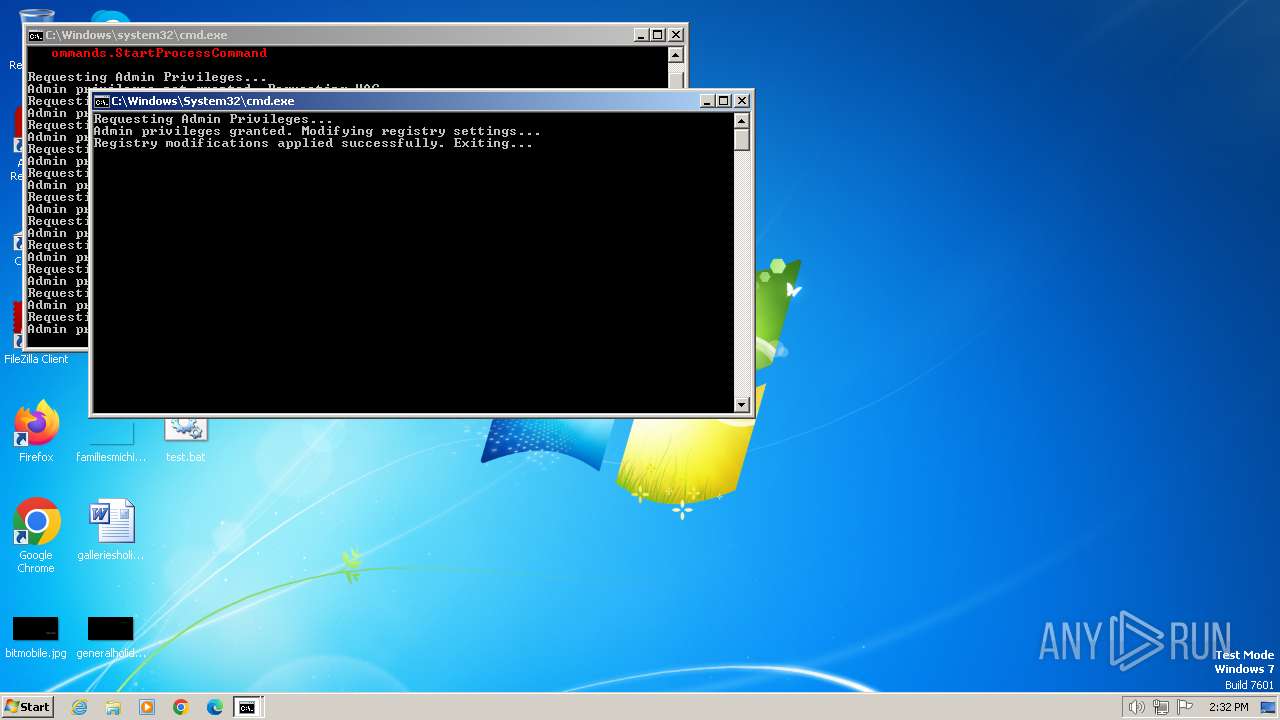
UAC/LUA settings modification
- reg.exe (PID: 3148)
- reg.exe (PID: 568)
- reg.exe (PID: 1928)
- reg.exe (PID: 2112)
- reg.exe (PID: 2308)
- reg.exe (PID: 2448)
- reg.exe (PID: 2156)
- reg.exe (PID: 2316)
- reg.exe (PID: 2576)
- reg.exe (PID: 1768)
- reg.exe (PID: 3312)
- reg.exe (PID: 2944)
- reg.exe (PID: 2068)
SUSPICIOUS
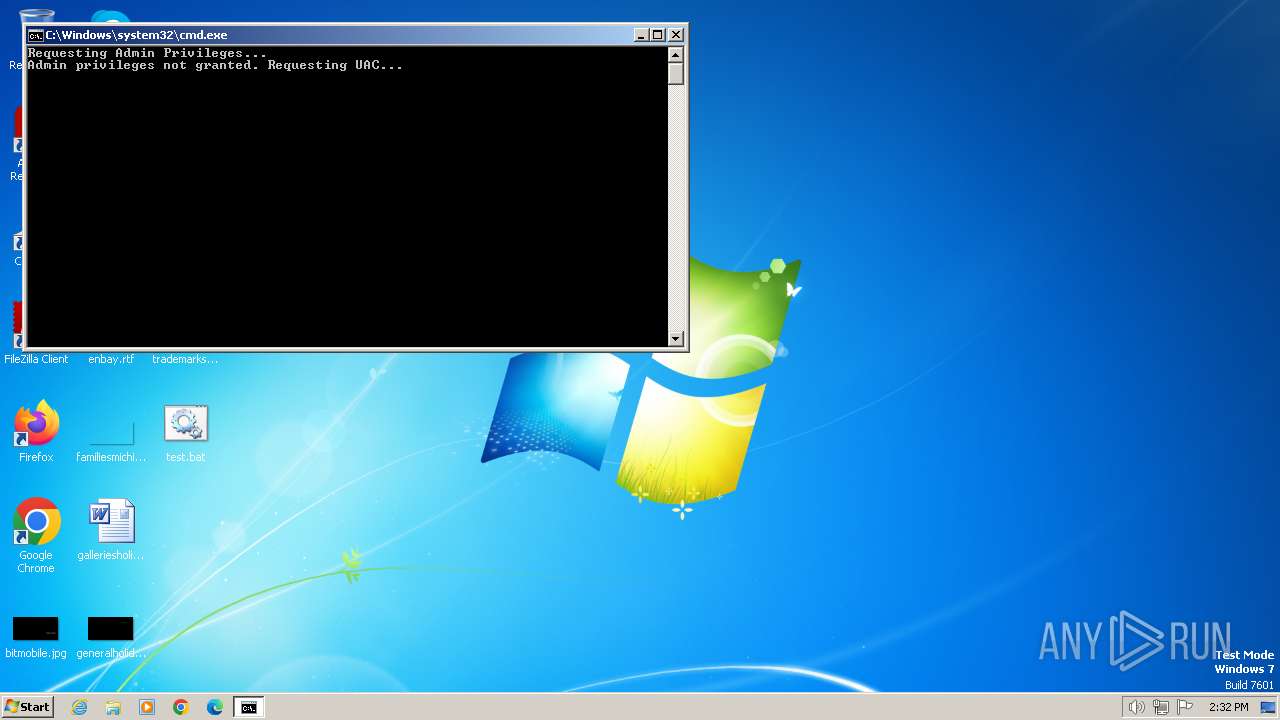
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 984)
Reads the Internet Settings
- powershell.exe (PID: 2448)
- powershell.exe (PID: 2068)
- powershell.exe (PID: 2820)
- powershell.exe (PID: 2668)
- powershell.exe (PID: 3036)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 3568)
- powershell.exe (PID: 2192)
- powershell.exe (PID: 3148)
- powershell.exe (PID: 3404)
- powershell.exe (PID: 848)
- powershell.exe (PID: 2108)
- powershell.exe (PID: 2112)
- powershell.exe (PID: 4092)
Powershell scripting: start process
- cmd.exe (PID: 984)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 984)
- cmd.exe (PID: 2612)
- cmd.exe (PID: 2432)
- cmd.exe (PID: 316)
- cmd.exe (PID: 3964)
- cmd.exe (PID: 1348)
- cmd.exe (PID: 3140)
- cmd.exe (PID: 3632)
- cmd.exe (PID: 1780)
- cmd.exe (PID: 1492)
- cmd.exe (PID: 2964)
- cmd.exe (PID: 1652)
- cmd.exe (PID: 1288)
- cmd.exe (PID: 2648)
Executing commands from a ".bat" file
- powershell.exe (PID: 2448)
- powershell.exe (PID: 2820)
- powershell.exe (PID: 2668)
- powershell.exe (PID: 3036)
- powershell.exe (PID: 2192)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 3568)
- powershell.exe (PID: 3148)
- powershell.exe (PID: 3404)
- powershell.exe (PID: 848)
- powershell.exe (PID: 2112)
- powershell.exe (PID: 2108)
- powershell.exe (PID: 4092)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 2448)
- powershell.exe (PID: 2820)
- powershell.exe (PID: 2668)
- powershell.exe (PID: 3036)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 2192)
- powershell.exe (PID: 3148)
- powershell.exe (PID: 3404)
- powershell.exe (PID: 848)
- powershell.exe (PID: 2112)
- powershell.exe (PID: 2108)
- powershell.exe (PID: 4092)
- powershell.exe (PID: 3568)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2612)
- cmd.exe (PID: 2432)
- cmd.exe (PID: 316)
- cmd.exe (PID: 1348)
- cmd.exe (PID: 3964)
- cmd.exe (PID: 3140)
- cmd.exe (PID: 3632)
- cmd.exe (PID: 2648)
- cmd.exe (PID: 1780)
- cmd.exe (PID: 1492)
- cmd.exe (PID: 2964)
- cmd.exe (PID: 1652)
- cmd.exe (PID: 1288)
INFO
Application launched itself
- msedge.exe (PID: 1384)
Manual execution by a user
- cmd.exe (PID: 984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
234
Monitored processes
168
Malicious processes
1
Suspicious processes
25
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Windows\System32\cmd.exe" /C "C:\Users\admin\Desktop\test.bat" | C:\Windows\System32\cmd.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 448 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3888 --field-trial-handle=1332,i,11719122761088438670,6008917233430165441,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 480 | reg.exe ADD "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v PromptOnSecureDesktop /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 532 | timeout /t 1 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 568 | reg.exe ADD "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v EnableLUA /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 584 | timeout /t 1 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 664 | net session | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | reg.exe ADD "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v PromptOnSecureDesktop /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 680 | reg.exe ADD "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v ConsentPromptBehaviorAdmin /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 748 | reg.exe ADD "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v ConsentPromptBehaviorAdmin /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
31 066
Read events
30 875
Write events
185
Delete events
6
Modification events
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: 7D990A2CF4702F00 | |||
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\FirstNotDefault |
| Operation: | delete value | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: | |||
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
Executable files
1
Suspicious files
127
Text files
66
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF17f54d.TMP | — | |
MD5:— | SHA256:— | |||
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF17f57b.TMP | — | |
MD5:— | SHA256:— | |||
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF17f5ca.TMP | — | |
MD5:— | SHA256:— | |||
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:DF0BCCD68449F07F531D76F53C718178 | SHA256:12025F4DA9E53A8B91892D4F6E6A9B89513F3488BFE9F1EEEC3C05F7EF96BDD8 | |||
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 3672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\CrashpadMetrics.pma | binary | |
MD5:886E82F2CA62ECCCE64601B30592078A | SHA256:E5E13D53601100FF3D6BB71514CBCCC4C73FE9B7EF5E930100E644187B42948E | |||
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Platform Notifications\LOG.old~RF17f6a4.TMP | text | |
MD5:ECA1E6D785935E14007478113E6C81C4 | SHA256:18EDB99F8AD496607DC6B4E0135A9101371465FCF01CE86973E93E6C2C560709 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
33
DNS requests
44
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1492 | msedge.exe | GET | 301 | 104.244.42.129:80 | http://x.com/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1492 | msedge.exe | 104.244.42.129:80 | x.com | TWITTER | US | unknown |
1384 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
1492 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1492 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1492 | msedge.exe | 104.244.42.65:443 | x.com | TWITTER | US | unknown |
1492 | msedge.exe | 104.244.42.194:443 | api.twitter.com | TWITTER | US | unknown |
1492 | msedge.exe | 152.199.21.141:443 | abs.twimg.com | EDGECAST | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
x.com |
| unknown |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
twitter.com |
| whitelisted |
abs.twimg.com |
| whitelisted |
api.twitter.com |
| whitelisted |
api.x.com |
| unknown |
video.twimg.com |
| whitelisted |
t.co |
| shared |
pbs.twimg.com |
| whitelisted |