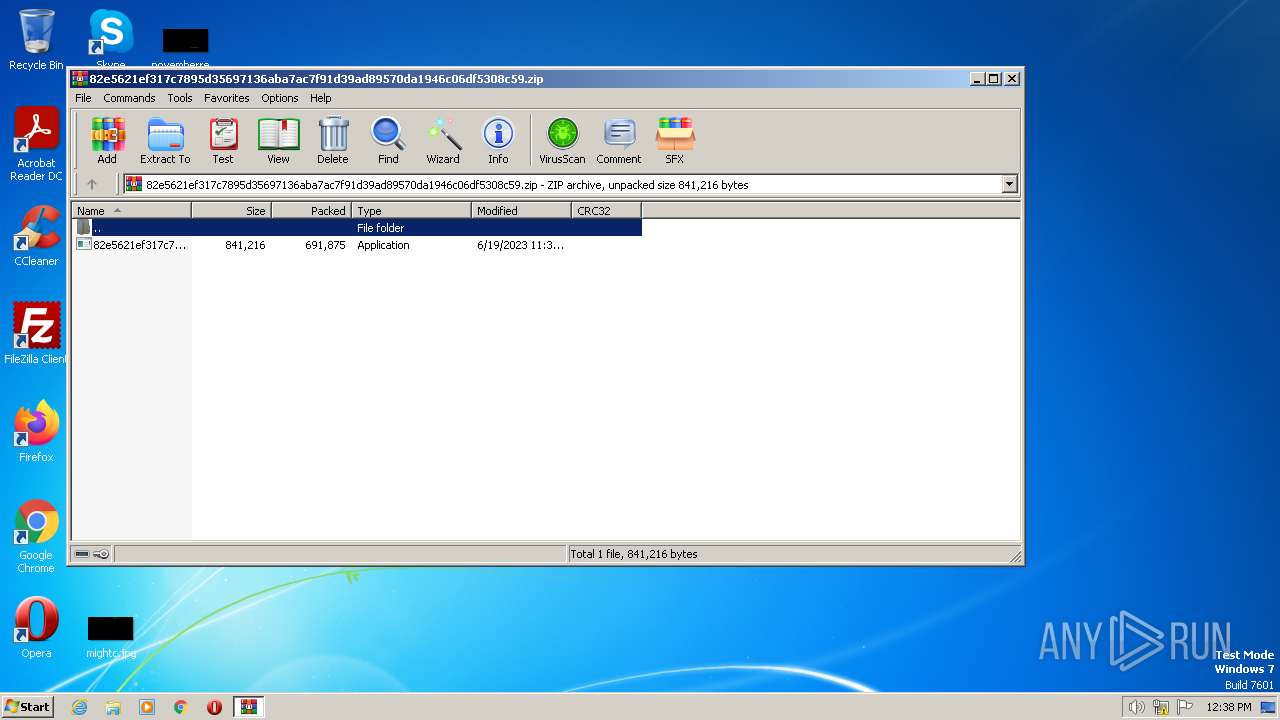
| File name: | 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.zip |
| Full analysis: | https://app.any.run/tasks/80894995-3f6e-409f-99cb-9f3177e23ff4 |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2023, 11:38:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract |
| MD5: | E40B3AC059BCFB3A37B72E1565E3151F |
| SHA1: | CC0F72EE77BAF34D0D277841F5DBC14D3A45A1C3 |
| SHA256: | 7F6A2D7D6382DFD0897BB2E50180526E0FEB7F339C0E564F67BCF1A553BEADD9 |
| SSDEEP: | 12288:W6DEptN5cwwEdIZYi6UvzAU53qFN2jQLMFnHVYOsEgu3QUopdJooslVTC:W2e5F5dIZYNUn5a2kOC7EgugUopdJrs2 |
MALICIOUS
Application was dropped or rewritten from another process
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 3336)
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 1060)
Uses Task Scheduler to run other applications
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 3336)
SNAKE detected by memory dumps
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 1060)
BLACKGUARD detected by memory dumps
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 1060)
SUSPICIOUS
Reads the Internet Settings
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 3336)
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 1060)
Executable content was dropped or overwritten
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 3336)
Application launched itself
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 3336)
INFO
Reads the computer name
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 3336)
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 1060)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1116)
Checks supported languages
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 3336)
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 1060)
The process checks LSA protection
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 3336)
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 1060)
Creates files or folders in the user directory
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 3336)
Manual execution by a user
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 3336)
Create files in a temporary directory
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 3336)
Reads the machine GUID from the registry
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 3336)
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 1060)
Reads Environment values
- 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe (PID: 1060)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
SnakeKeylogger
(PID) Process(1060) 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe
Keys
DES6fc98cd6
Options
SMTP Useradministracion@riogrande.es
SMTP Passwordu1T8hf3?
SMTP Hostriogrande.es
SMTP SendTocounty@valleycountysar.org
SMTP Port25
BlackGuard
(PID) Process(1060) 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe
C2 (2)http://checkip.dyndns.org
https://api.telegram.org
Strings (427)WinForms_RecursiveFormCreate
WinForms_SeeInnerException
lfwhUWZlmFnGhDYPudAJ.Resources
Software\
Win32_OperatingSystem
Version
.txt
$%SMTPDV$
$#TheHashHere%&
False
$ProtectPass%
ProtectFalse
BsrOkyiChvpfhAkipZAxnnChkMGkLnAiZhGMyrnJfULiDGkfTkrTELinhfkLkJrkDExMvkEUCxUkUGr
Country Name:
CountryCode:
Region Name:
Region Code:
City:
TimeZone:
Latitude:
Longitude:
ZzHN95aDFK10Ltdoj2UXp2Fl5yji01m9Gx7jCwN15ko=
GMo4BV2mUThjHvh0nRM/cw==
IACNaOg/bwCNrANaQjv16Q==
7L5bYii2xdYv2u9GWSJcvcG/ESep3BBpToL0V6baP08=
O+dvBLjH3Ow=
Yx74dJ0TP3M=
ZyiAEnXWZP
chrome
firefox
zlclient
egui
bdagent
npfmsg
olydbg
anubis
wireshark
avastui
_Avp32
vsmon
mbam
keyscrambler
_Avpcc
_Avpm
Ackwin32
Outpost
Anti-Trojan
ANTIVIR
Apvxdwin
ATRACK
Autodown
Avconsol
Ave32
Avgctrl
Avkserv
Avnt
Avp32
Avpcc
Avpdos32
Avpm
Avptc32
Avpupd
Avsched32
AVSYNMGR
Avwin95
Avwupd32
Blackd
Blackice
Cfiadmin
Cfiaudit
Cfinet
Cfinet32
Claw95
Claw95cf
Cleaner
Cleaner3
Defwatch
Dvp95
Dvp95_0
Ecengine
Esafe
Espwatch
F-Agnt95
Findviru
Fprot
F-Prot
F-Prot95
Fp-Win
F-Stopw
Iamapp
Iamserv
Ibmasn
Ibmavsp
Icload95
Icloadnt
Icmon
Icsupp95
Icsuppnt
Iface
Iomon98
Jedi
Lockdown2000
Lookout
Luall
MCAFEE
Moolive
Mpftray
N32scanw
NAVAPW32
NAVLU32
Navnt
NAVRUNR
Navw32
Navwnt
NeoWatch
NISSERV
Nisum
Nmain
Normist
NORTON
Nupgrade
Nvc95
Padmin
Pavcl
Pavsched
Pavw
PCCIOMON
PCCMAIN
Pccwin98
Pcfwallicon
Persfw
POP3TRAP
PVIEW95
Rav7
Rav7win
Rescue
Safeweb
Scan32
Scan95
Scanpm
Scrscan
Serv95
SMCSERVICE
Snort
Sphinx
Sweep95
SYMPROXYSVC
Tbscan
Tds2-98
Tds2-Nt
TermiNET
Vet95
Vettray
Vscan40
Vsecomr
Vshwin32
Vsstat
Webscanx
WEBTRAP
Wfindv32
Zonealarm
LOCKDOWN2000
RESCUE32
LUCOMSERVER
avgcc
avgamsvr
avgupsvc
avgw
avgcc32
avgserv
avgserv9
avgserv9schedapp
avgemc
ashwebsv
ashdisp
ashmaisv
ashserv
aswUpdSv
symwsc
norton
Norton Auto-Protect
norton_av
nortonav
ccsetmgr
ccevtmgr
avadmin
avcenter
avgnt
avguard
avnotify
avscan
guardgui
nod32krn
nod32kui
clamscan
clamTray
clamWin
freshclam
oladdin
sigtool
w9xpopen
Wclose
cmgrdian
alogserv
mcshield
vshwin32
avconsol
vsstat
avsynmgr
avcmd
avconfig
licmgr
sched
preupd
MsMpEng
MSASCui
Avira.Systray
/C choice /C Y /N /D Y /T 3 & Del "
cmd.exe
software\microsoft\windows\currentversion\run
------------------------
Content-Type
multipart/form-data; boundary=
POST
/sendMessage?chat_id=
&text=
utf-8
{0:f2} GB
user-agent
Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.2; .NET CLR1.0.3705;)
<html><head><title>Current IP Check</title></head><body>
</body></html>
Current IP Address:
{Null}
Clipboard |
http
<http>
%FTPDV$
Create
- Clipboard Logs ID -
STOR
Pc Name:
| Snake Tracker
Clipboard
text/plain
True
$%TelegramDv$
/sendDocument?chat_id=
&caption=
application/x-ms-dos-executable
Screenshot
.png
\SnakeKeylogger
\SnakeKeylogger\
- Screenshot Logs ID -
Screenshot |
KP |
- keystroke Logs ID -
Keystrokes
Keylogger |
SnakeKeylogger
PW |
- Passwords ID -
Passwords
Rǫ
SnakePW
.ldb
oken
ProtectTrue
300000
[ENTR]
[TAP]
ObjectLength
ChainingModeGCM
AuthTagLength
ChainingMode
KeyDataBlob
Microsoft Primitive Provider
BCrypt.BCryptDecrypt() (get size) failed with status code: {0}
BCrypt.BCryptDecrypt(): authentication tag mismatch
BCrypt.BCryptDecrypt() failed with status code:{0}
BCrypt.BCryptOpenAlgorithmProvider() failed with status code:{0}
BCrypt.BCryptSetAlgorithmProperty(BCrypt.BCRYPT_CHAINING_MODE, BCrypt.BCRYPT_CHAIN_MODE_GCM) failed with status code:{0}
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
IMAP Password
POP3 Password
HTTP Password
SMTP Password
Software\Microsoft\Office\15.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676
Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676
Software\Microsoft\Windows Messaging Subsystem\Profiles\9375CFF0413111d3B88A00104B2A6676
Software\Microsoft\Office\16.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676
Email
GetBytes
SMTP Server
Nothing
Outlook
Foxmail
SOFTWARE\Classes\Foxmail.url.mailto\Shell\open\command
Foxmail.exe
Storage\
\Accounts\Account.rec0
Account
POP3Account
Password
POP3Password
E-Mail: {0}
PSWD: {0}
\Local State
"encrypted_key":"(.*?)"
\Kinza\User Data\Default\Login Data
logins
origin_url
username_value
password_value
\Sputnik\Sputnik\User Data\Default\Login Data
\SalamWeb\User Data\Default\Login Data
\MapleStudio\ChromePlus\User Data\Default\Login Data
\QIP Surf\User Data\Default\Login Data
\BlackHawk\User Data\Default\Login Data
\7Star\7Star\User Data\Default\Login Data
APPDATA
\Fenrir Inc\Sleipnir5\setting\modules\ChromiumViewer\Default\Login Data
\CatalinaGroup\Citrio\User Data\Default\Login Data
\Google\Chrome SxS\User Data\Default\Login Data
\Google\Chrome\User Data\Default\Login Data
\Coowon\Coowon\User Data\Default\Login Data
\CocCoc\Browser\User Data\Default\Login Data
\uCozMedia\Uran\User Data\Default\Login Data
\Tencent\QQBrowser\User Data\Default\Login Data
\Orbitum\User Data\Default\Login Data
\Slimjet\User Data\Default\Login Data
\Iridium\User Data\Default\Login Data
\Vivaldi\User Data\Default\Login Data
\Chromium\User Data\Default\Login Data
\GhostBrowser\User Data\Default\Login Data
\CentBrowser\User Data\Default\Login Data
\Xvast\User Data\Default\Login Data
\Chedot\User Data\Default\Login Data
\SuperBird\User Data\Default\Login Data
\360Browser\Browser\User Data\Default\Login Data
\360Chrome\Chrome\User Data\Default\Login Data
\Comodo\Dragon\User Data\Default\Login Data
\BraveSoftware\Brave-Browser\User Data\Default\Login Data
\Torch\User Data\Default\Login Data
\UCBrowser\User Data_i18n\Default\UC Login Data.18
wow_logins
\Blisk\User Data\Default\Login Data
\Epic Privacy Browser\User Data\Default\Login Data
\Yandex\YandexBrowser\User Data\Default\Ya Login Data
\Nichrome\User Data\Default\Login Data
\Amigo\User Data\Default\Login Data
\Kometa\User Data\Default\Login Data
\Xpom\User Data\Default\Login Data
\Elements Browser\User Data\Default\Login Data
\Microsoft\Edge\User Data\Default\Login Data
ataD nigoL\elbatS arepO\erawtfoS arepO\
tad.dnaw\eliforp\arepO\arepO\
ReadTable
snigol
GetRowCount
GetValue
lru_nigiro
eulav_emanresu
eulav_drowssap
abcdefghijklmnopqrstuvwxyz1234567890_-.~!@#$%^&*()[{]}\|';:,<>/?+=
\FileZilla\recentservers.xml
Host
Pass
Port
Host:
AppData
\.purple\accounts.xml
protocol
name
password
\Liebao7\User Data\Default\EncryptedStorage
entries
str3
str2
blob0
\AVAST Software\Browser\User Data\Default\Login Data
Software\Microsoft\Windows NT\CurrentVersion
DigitalProductID
BCDFGHJKMPQRTVWXY2346789
All User Profile * : (?<after>.*)
after
{0}{1}{2}{3}{4}
WiFi Name:
wlan show profile name="
" key=clear
netsh
wlan show profile
Key Content * : (?<after>.*)
Open Network
\discord\Local Storage\leveldb\
.log
UNIQUE
table
Mozilla\Firefox\Profiles
logins.json
Waterfox\Profiles
Thunderbird\Profiles\
Mozilla\SeaMonkey\Profiles
Comodo\IceDragon\Profiles
8pecxstudios\Cyberfox\Profiles
FlashPeak\SlimBrowser\Profiles
Mozilla\icecat\Profiles
PostboxApp\Profiles
Moonchild Productions\Pale Moon\Profiles
NSS_Shutdown
PROGRAMFILES
\Mozilla Thunderbird\
\Mozilla Firefox\
\SeaMonkey\
\Comodo\IceDragon\
\Cyberfox\
\Pale Moon\
\Waterfox Current\
\SlimBrowser\
\Postbox\
\mozglue.dll
\nss3.dll
NSS_Init
PK11SDR_Decrypt
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe |
|---|---|
| ZipUncompressedSize: | 841216 |
| ZipCompressedSize: | 691875 |
| ZipCRC: | 0x050ae997 |
| ZipModifyDate: | 2023:06:19 11:36:34 |
| ZipCompression: | Unknown (99) |
| ZipBitFlag: | 0x0003 |
| ZipRequiredVersion: | 51 |
Total processes
43
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1060 | "C:\Users\admin\Desktop\82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe" | C:\Users\admin\Desktop\82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe | 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe | ||||||||||||
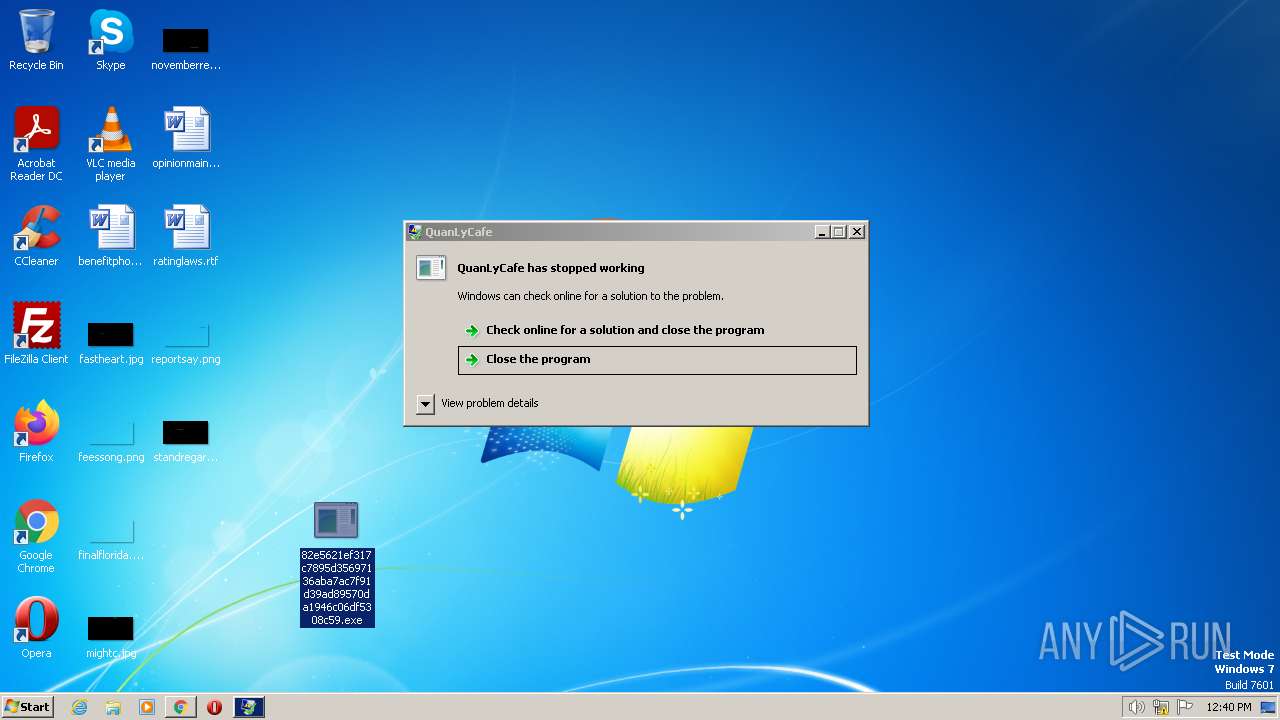
User: admin Integrity Level: MEDIUM Description: QuanLyCafe Exit code: 0 Version: 1.0.0.0 Modules
SnakeKeylogger(PID) Process(1060) 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe Keys DES6fc98cd6 Options SMTP Useradministracion@riogrande.es SMTP Passwordu1T8hf3? SMTP Hostriogrande.es SMTP SendTocounty@valleycountysar.org SMTP Port25 BlackGuard(PID) Process(1060) 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe C2 (2)http://checkip.dyndns.org https://api.telegram.org Strings (427)WinForms_RecursiveFormCreate WinForms_SeeInnerException lfwhUWZlmFnGhDYPudAJ.Resources Software\ Win32_OperatingSystem Version .txt $%SMTPDV$ $#TheHashHere%& False $ProtectPass% ProtectFalse BsrOkyiChvpfhAkipZAxnnChkMGkLnAiZhGMyrnJfULiDGkfTkrTELinhfkLkJrkDExMvkEUCxUkUGr Country Name: CountryCode: Region Name: Region Code: City: TimeZone: Latitude: Longitude: ZzHN95aDFK10Ltdoj2UXp2Fl5yji01m9Gx7jCwN15ko= GMo4BV2mUThjHvh0nRM/cw== IACNaOg/bwCNrANaQjv16Q== 7L5bYii2xdYv2u9GWSJcvcG/ESep3BBpToL0V6baP08= O+dvBLjH3Ow= Yx74dJ0TP3M= ZyiAEnXWZP chrome firefox zlclient egui bdagent npfmsg olydbg anubis wireshark avastui _Avp32 vsmon mbam keyscrambler _Avpcc _Avpm Ackwin32 Outpost Anti-Trojan ANTIVIR Apvxdwin ATRACK Autodown Avconsol Ave32 Avgctrl Avkserv Avnt Avp32 Avpcc Avpdos32 Avpm Avptc32 Avpupd Avsched32 AVSYNMGR Avwin95 Avwupd32 Blackd Blackice Cfiadmin Cfiaudit Cfinet Cfinet32 Claw95 Claw95cf Cleaner Cleaner3 Defwatch Dvp95 Dvp95_0 Ecengine Esafe Espwatch F-Agnt95 Findviru Fprot F-Prot F-Prot95 Fp-Win F-Stopw Iamapp Iamserv Ibmasn Ibmavsp Icload95 Icloadnt Icmon Icsupp95 Icsuppnt Iface Iomon98 Jedi Lockdown2000 Lookout Luall MCAFEE Moolive Mpftray N32scanw NAVAPW32 NAVLU32 Navnt NAVRUNR Navw32 Navwnt NeoWatch NISSERV Nisum Nmain Normist NORTON Nupgrade Nvc95 Padmin Pavcl Pavsched Pavw PCCIOMON PCCMAIN Pccwin98 Pcfwallicon Persfw POP3TRAP PVIEW95 Rav7 Rav7win Rescue Safeweb Scan32 Scan95 Scanpm Scrscan Serv95 SMCSERVICE Snort Sphinx Sweep95 SYMPROXYSVC Tbscan Tds2-98 Tds2-Nt TermiNET Vet95 Vettray Vscan40 Vsecomr Vshwin32 Vsstat Webscanx WEBTRAP Wfindv32 Zonealarm LOCKDOWN2000 RESCUE32 LUCOMSERVER avgcc avgamsvr avgupsvc avgw avgcc32 avgserv avgserv9 avgserv9schedapp avgemc ashwebsv ashdisp ashmaisv ashserv aswUpdSv symwsc norton Norton Auto-Protect norton_av nortonav ccsetmgr ccevtmgr avadmin avcenter avgnt avguard avnotify avscan guardgui nod32krn nod32kui clamscan clamTray clamWin freshclam oladdin sigtool w9xpopen Wclose cmgrdian alogserv mcshield vshwin32 avconsol vsstat avsynmgr avcmd avconfig licmgr sched preupd MsMpEng MSASCui Avira.Systray /C choice /C Y /N /D Y /T 3 & Del " cmd.exe software\microsoft\windows\currentversion\run ------------------------ Content-Type multipart/form-data; boundary= POST /sendMessage?chat_id= &text= utf-8 {0:f2} GB user-agent Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.2; .NET CLR1.0.3705;) <html><head><title>Current IP Check</title></head><body> </body></html> Current IP Address: {Null} Clipboard | http <http> %FTPDV$ Create - Clipboard Logs ID - STOR Pc Name: | Snake Tracker Clipboard text/plain True $%TelegramDv$ /sendDocument?chat_id= &caption= application/x-ms-dos-executable Screenshot .png \SnakeKeylogger \SnakeKeylogger\ - Screenshot Logs ID - Screenshot | KP | - keystroke Logs ID - Keystrokes Keylogger | SnakeKeylogger PW | - Passwords ID - Passwords Rǫ SnakePW .ldb oken ProtectTrue 300000 [ENTR] [TAP] ObjectLength ChainingModeGCM AuthTagLength ChainingMode KeyDataBlob Microsoft Primitive Provider BCrypt.BCryptDecrypt() (get size) failed with status code: {0} BCrypt.BCryptDecrypt(): authentication tag mismatch BCrypt.BCryptDecrypt() failed with status code:{0} BCrypt.BCryptOpenAlgorithmProvider() failed with status code:{0} BCrypt.BCryptSetAlgorithmProperty(BCrypt.BCRYPT_CHAINING_MODE, BCrypt.BCRYPT_CHAIN_MODE_GCM) failed with status code:{0} BCrypt.BCryptImportKey() failed with status code:{0} BCrypt.BCryptGetProperty() (get size) failed with status code:{0} BCrypt.BCryptGetProperty() failed with status code:{0} IMAP Password POP3 Password HTTP Password SMTP Password Software\Microsoft\Office\15.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676 Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676 Software\Microsoft\Windows Messaging Subsystem\Profiles\9375CFF0413111d3B88A00104B2A6676 Software\Microsoft\Office\16.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676 Email GetBytes SMTP Server Nothing Outlook Foxmail SOFTWARE\Classes\Foxmail.url.mailto\Shell\open\command Foxmail.exe Storage\ \Accounts\Account.rec0 Account POP3Account Password POP3Password E-Mail: {0} PSWD: {0} \Local State "encrypted_key":"(.*?)" \Kinza\User Data\Default\Login Data logins origin_url username_value password_value \Sputnik\Sputnik\User Data\Default\Login Data \SalamWeb\User Data\Default\Login Data \MapleStudio\ChromePlus\User Data\Default\Login Data \QIP Surf\User Data\Default\Login Data \BlackHawk\User Data\Default\Login Data \7Star\7Star\User Data\Default\Login Data APPDATA \Fenrir Inc\Sleipnir5\setting\modules\ChromiumViewer\Default\Login Data \CatalinaGroup\Citrio\User Data\Default\Login Data \Google\Chrome SxS\User Data\Default\Login Data \Google\Chrome\User Data\Default\Login Data \Coowon\Coowon\User Data\Default\Login Data \CocCoc\Browser\User Data\Default\Login Data \uCozMedia\Uran\User Data\Default\Login Data \Tencent\QQBrowser\User Data\Default\Login Data \Orbitum\User Data\Default\Login Data \Slimjet\User Data\Default\Login Data \Iridium\User Data\Default\Login Data \Vivaldi\User Data\Default\Login Data \Chromium\User Data\Default\Login Data \GhostBrowser\User Data\Default\Login Data \CentBrowser\User Data\Default\Login Data \Xvast\User Data\Default\Login Data \Chedot\User Data\Default\Login Data \SuperBird\User Data\Default\Login Data \360Browser\Browser\User Data\Default\Login Data \360Chrome\Chrome\User Data\Default\Login Data \Comodo\Dragon\User Data\Default\Login Data \BraveSoftware\Brave-Browser\User Data\Default\Login Data \Torch\User Data\Default\Login Data \UCBrowser\User Data_i18n\Default\UC Login Data.18 wow_logins \Blisk\User Data\Default\Login Data \Epic Privacy Browser\User Data\Default\Login Data \Yandex\YandexBrowser\User Data\Default\Ya Login Data \Nichrome\User Data\Default\Login Data \Amigo\User Data\Default\Login Data \Kometa\User Data\Default\Login Data \Xpom\User Data\Default\Login Data \Elements Browser\User Data\Default\Login Data \Microsoft\Edge\User Data\Default\Login Data ataD nigoL\elbatS arepO\erawtfoS arepO\ tad.dnaw\eliforp\arepO\arepO\ ReadTable snigol GetRowCount GetValue lru_nigiro eulav_emanresu eulav_drowssap abcdefghijklmnopqrstuvwxyz1234567890_-.~!@#$%^&*()[{]}\|';:,<>/?+= \FileZilla\recentservers.xml Host Pass Port Host: AppData \.purple\accounts.xml protocol name password \Liebao7\User Data\Default\EncryptedStorage entries str3 str2 blob0 \AVAST Software\Browser\User Data\Default\Login Data Software\Microsoft\Windows NT\CurrentVersion DigitalProductID BCDFGHJKMPQRTVWXY2346789 All User Profile * : (?<after>.*) after {0}{1}{2}{3}{4} WiFi Name: wlan show profile name=" " key=clear netsh wlan show profile Key Content * : (?<after>.*) Open Network \discord\Local Storage\leveldb\ .log UNIQUE table Mozilla\Firefox\Profiles logins.json Waterfox\Profiles Thunderbird\Profiles\ Mozilla\SeaMonkey\Profiles Comodo\IceDragon\Profiles 8pecxstudios\Cyberfox\Profiles FlashPeak\SlimBrowser\Profiles Mozilla\icecat\Profiles PostboxApp\Profiles Moonchild Productions\Pale Moon\Profiles NSS_Shutdown PROGRAMFILES \Mozilla Thunderbird\ \Mozilla Firefox\ \SeaMonkey\ \Comodo\IceDragon\ \Cyberfox\ \Pale Moon\ \Waterfox Current\ \SlimBrowser\ \Postbox\ \mozglue.dll \nss3.dll NSS_Init PK11SDR_Decrypt | |||||||||||||||
| 1116 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3336 | "C:\Users\admin\Desktop\82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe" | C:\Users\admin\Desktop\82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: QuanLyCafe Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3792 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\IghAgYEPrw" /XML "C:\Users\admin\AppData\Local\Temp\tmp1DD1.tmp" | C:\Windows\System32\schtasks.exe | — | 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 481
Read events
1 454
Write events
27
Delete events
0
Modification events
| (PID) Process: | (1116) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (1116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
2
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1116.19004\82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe | executable | |
MD5:AE6CE9E081EBCAD0F1A822C8BF9E8811 | SHA256:82E5621EF317C7895D35697136ABA7AC7F91D39AD89570DA1946C06DF5308C59 | |||
| 3336 | 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe | C:\Users\admin\AppData\Roaming\IghAgYEPrw.exe | executable | |
MD5:AE6CE9E081EBCAD0F1A822C8BF9E8811 | SHA256:82E5621EF317C7895D35697136ABA7AC7F91D39AD89570DA1946C06DF5308C59 | |||
| 3336 | 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe | C:\Users\admin\AppData\Local\Temp\tmp1DD1.tmp | xml | |
MD5:8D59A93894DCAB07B86C6309956944EC | SHA256:06CF721FBA44FE07C5880BB66081B714BC58A0709E385488AF3C364A83C6DD59 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
10
DNS requests
4
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4004 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1060 | 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe | 193.122.6.168:80 | checkip.dyndns.org | ORACLE-BMC-31898 | DE | malicious |
1060 | 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe | 132.226.8.169:80 | checkip.dyndns.org | ORACLE-BMC-31898 | JP | malicious |
1060 | 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe | 193.122.130.0:80 | checkip.dyndns.org | ORACLE-BMC-31898 | US | malicious |
1060 | 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe | 132.226.247.73:80 | checkip.dyndns.org | ORACLE-BMC-31898 | BR | malicious |
1060 | 82e5621ef317c7895d35697136aba7ac7f91d39ad89570da1946c06df5308c59.exe | 158.101.44.242:80 | checkip.dyndns.org | ORACLE-BMC-31898 | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
checkip.dyndns.org |
| shared |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1076 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Query (checkip .dyndns .org) |
1076 | svchost.exe | Misc activity | AV INFO Query to checkip.dyndns. Domain |