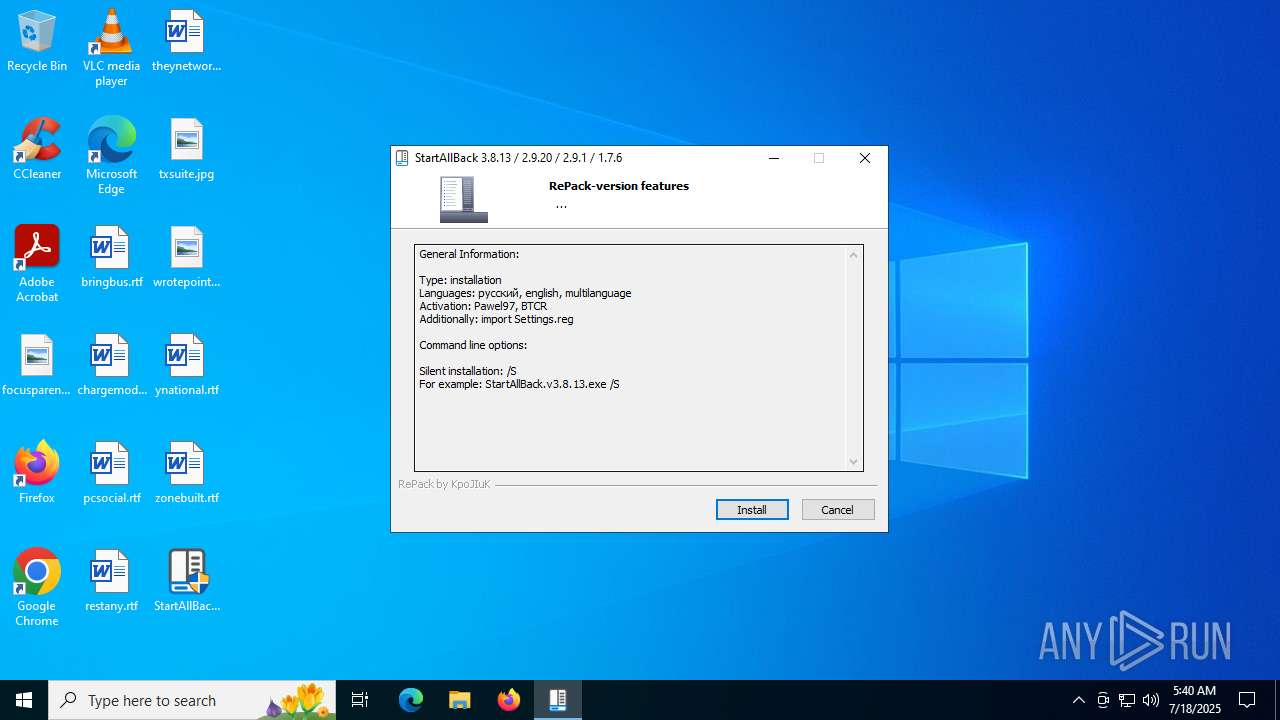
| File name: | StartAllBack.v3.8.13.exe |
| Full analysis: | https://app.any.run/tasks/53cedb84-1c8d-43d8-aed1-d094ff317baf |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2025, 05:40:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 405EB588B0FE23E8BF446ABF89EAF472 |
| SHA1: | 200707C43DEB5F33F52B5DD6CB8F840116CA03DF |
| SHA256: | 7F432F8D4522B489C0770978F5C0494873EE7FD203DCD5595BAB799137D660AB |
| SSDEEP: | 98304:pe11j+msmlHfFSUdb6ddEaCB2mNC5QDbEgNq3s0mqDNigWo759otJePXl6ghJSVq:OUFV9Lb |
MALICIOUS
Executing a file with an untrusted certificate
- StartIsBackCfg.exe (PID: 6948)
Uses Task Scheduler to run other applications
- StartIsBackCfg.exe (PID: 6948)
SUSPICIOUS
The process creates files with name similar to system file names
- StartAllBack.v3.8.13.exe (PID: 4520)
Malware-specific behavior (creating "System.dll" in Temp)
- StartAllBack.v3.8.13.exe (PID: 4520)
Executable content was dropped or overwritten
- StartAllBack.v3.8.13.exe (PID: 4520)
- StartIsBackCfg.exe (PID: 6948)
Process drops legitimate windows executable
- StartAllBack.v3.8.13.exe (PID: 4520)
- StartIsBackCfg.exe (PID: 6948)
Uses TASKKILL.EXE to kill process
- StartIsBackCfg.exe (PID: 6948)
Reads security settings of Internet Explorer
- StartIsBackCfg.exe (PID: 6948)
- StartMenuExperienceHost.exe (PID: 2140)
- StartScreen.exe (PID: 5388)
Changes default file association
- StartIsBackCfg.exe (PID: 6948)
Creates a software uninstall entry
- StartIsBackCfg.exe (PID: 6948)
Creates/Modifies COM task schedule object
- StartIsBackCfg.exe (PID: 6948)
The process executes via Task Scheduler
- explorer.exe (PID: 2096)
Write to the desktop.ini file (may be used to cloak folders)
- StartScreen.exe (PID: 5388)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 2140)
- SearchApp.exe (PID: 3620)
INFO
Checks supported languages
- StartAllBack.v3.8.13.exe (PID: 4520)
- StartIsBackCfg.exe (PID: 6948)
- startscreen.exe (PID: 2096)
- TextInputHost.exe (PID: 5160)
- StartScreen.exe (PID: 5388)
- StartMenuExperienceHost.exe (PID: 2140)
- SearchApp.exe (PID: 3620)
The sample compiled with english language support
- StartAllBack.v3.8.13.exe (PID: 4520)
- StartIsBackCfg.exe (PID: 6948)
Create files in a temporary directory
- StartAllBack.v3.8.13.exe (PID: 4520)
- StartIsBackCfg.exe (PID: 6948)
- StartScreen.exe (PID: 5388)
Reads the computer name
- StartAllBack.v3.8.13.exe (PID: 4520)
- StartIsBackCfg.exe (PID: 6948)
- StartScreen.exe (PID: 5388)
- StartMenuExperienceHost.exe (PID: 2140)
- TextInputHost.exe (PID: 5160)
- SearchApp.exe (PID: 3620)
Reads Environment values
- StartAllBack.v3.8.13.exe (PID: 4520)
- SearchApp.exe (PID: 3620)
The sample compiled with russian language support
- StartAllBack.v3.8.13.exe (PID: 4520)
- StartIsBackCfg.exe (PID: 6948)
Creates files in the program directory
- StartIsBackCfg.exe (PID: 6948)
Reads security settings of Internet Explorer
- explorer.exe (PID: 2096)
Creates files or folders in the user directory
- explorer.exe (PID: 2096)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 2140)
- SearchApp.exe (PID: 3620)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 3620)
Checks proxy server information
- explorer.exe (PID: 2096)
- SearchApp.exe (PID: 3620)
- slui.exe (PID: 3460)
Reads the software policy settings
- SearchApp.exe (PID: 3620)
- slui.exe (PID: 3460)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:30 16:56:02+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 412160 |
| UninitializedDataSize: | 16384 |
| EntryPoint: | 0x3665 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.8.13.0 |
| ProductVersionNumber: | 3.8.13.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | www.startisback.com |
| FileDescription: | StartAllBack v3.8.13 |
| FileVersion: | 3.8.13.0 |
| LegalCopyright: | © www.startisback.com |
| ProductName: | StartAllBack v3.8.13 |
Total processes
168
Monitored processes
29
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 512 | "C:\Users\admin\Desktop\StartAllBack.v3.8.13.exe" | C:\Users\admin\Desktop\StartAllBack.v3.8.13.exe | — | explorer.exe | |||||||||||
User: admin Company: www.startisback.com Integrity Level: MEDIUM Description: StartAllBack v3.8.13 Exit code: 3221226540 Version: 3.8.13.0 Modules
| |||||||||||||||
| 984 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1352 | schtasks.exe /Create /TN "\StartIsBack health check" /XML "C:\Users\admin\AppData\Local\Temp\sibtask.xml" | C:\Windows\SysWOW64\schtasks.exe | — | StartIsBackCfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1740 | taskkill.exe /F /IM explorer* | C:\Windows\SysWOW64\taskkill.exe | — | StartIsBackCfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | startscreen.exe /stop | C:\Users\admin\AppData\Local\Temp\STARTISBACK\startscreen.exe | — | StartIsBackCfg.exe | |||||||||||
User: admin Company: www.startisback.com Integrity Level: HIGH Description: StartIsBack Helper Tool Exit code: 0 Version: 5.9.8 Modules
| |||||||||||||||
| 2096 | "C:\WINDOWS\explorer.exe" /NoUACCheck | C:\Windows\explorer.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2148 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2348 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
33 204
Read events
32 918
Write events
268
Delete events
18
Modification events
| (PID) Process: | (4520) StartAllBack.v3.8.13.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\StartIsBack |
| Operation: | write | Name: | WelcomeShown |
Value: 2 | |||
| (PID) Process: | (4520) StartAllBack.v3.8.13.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\StartIsBack |
| Operation: | write | Name: | AutoUpdates |
Value: 0 | |||
| (PID) Process: | (2096) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\CPC\Volume\{eaf65672-68c3-4f99-8d5c-104b5f4d8fff} |
| Operation: | write | Name: | Data |
Value: D60D00000DF0ADBA01000000080000000000008000000000000000300000000000000000FF06E703FF000000160000009FF23EA01E00000004000000030000000000000000000000000000000000000000005C005C003F005C00530054004F005200410047004500230056006F006C0075006D00650023007B00390030006300660033006400640036002D0030006100660037002D0031003100650063002D0062003400380030002D003800300036006500360066003600650036003900360033007D002300300030003000300030003000330046004100410046003000300030003000300023007B00350033006600350036003300300064002D0062003600620066002D0031003100640030002D0039003400660032002D003000300061003000630039003100650066006200380062007D000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000005C005C003F005C0056006F006C0075006D0065007B00650061006600360035003600370032002D0036003800630033002D0034006600390039002D0038006400350063002D003100300034006200350066003400640038006600660066007D005C0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000004E005400460053000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0000 | |||
| (PID) Process: | (2096) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\CPC\Volume\{eaf65672-68c3-4f99-8d5c-104b5f4d8fff} |
| Operation: | write | Name: | Generation |
Value: 1 | |||
| (PID) Process: | (2096) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\CPC\Volume\{2f5c5e71-85a9-11eb-90a8-9a9b76358421} |
| Operation: | write | Name: | Data |
Value: D60D00000DF0ADBA0100000008000000000000800000000000000030000000000000000006020200FF000000100000000EE13DAC1E00000004000000030000000000000000000000000000000000000000005C005C003F005C00530054004F005200410047004500230056006F006C0075006D00650023007B00390030006300660033006400640036002D0030006100660037002D0031003100650063002D0062003400380030002D003800300036006500360066003600650036003900360033007D002300300030003000300030003000300030003000300031003000300030003000300023007B00350033006600350036003300300064002D0062003600620066002D0031003100640030002D0039003400660032002D003000300061003000630039003100650066006200380062007D000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000005C005C003F005C0056006F006C0075006D0065007B00320066003500630035006500370031002D0038003500610039002D0031003100650062002D0039003000610038002D003900610039006200370036003300350038003400320031007D005C00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000046004100540033003200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0000 | |||
| (PID) Process: | (2096) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\CPC\Volume\{2f5c5e71-85a9-11eb-90a8-9a9b76358421} |
| Operation: | write | Name: | Generation |
Value: 1 | |||
| (PID) Process: | (2096) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | delete value | Name: | UpgradeOrPBRAttempts |
Value: | |||
| (PID) Process: | (2096) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | delete value | Name: | DefaultStartLayout_UseWin7UpgradeBehavior |
Value: | |||
| (PID) Process: | (2096) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | delete value | Name: | DefaultStartLayout_UseWin8UpgradeBehavior |
Value: | |||
| (PID) Process: | (2096) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | delete value | Name: | LogonWork |
Value: | |||
Executable files
27
Suspicious files
26
Text files
107
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4520 | StartAllBack.v3.8.13.exe | C:\Users\admin\AppData\Local\Temp\STARTISBACK\StartIsBack32.dll | executable | |
MD5:E4B19C388CF6D649053E7F018388B9A4 | SHA256:6405B9AD8B1557381DE5A3D51502F408891283BA22AD45166343261E703BEE07 | |||
| 4520 | StartAllBack.v3.8.13.exe | C:\Users\admin\AppData\Local\Temp\nswDCD0.tmp\modern-header.bmp | image | |
MD5:7B52C676D68BED1E688D184CE820A891 | SHA256:BA081C4B86CEAE14E7B0DD520EFC9414EE10D48ACCF172A92E0C3215AD8D75CB | |||
| 4520 | StartAllBack.v3.8.13.exe | C:\Users\admin\AppData\Local\Temp\nswDCD0.tmp\System.dll | executable | |
MD5:192639861E3DC2DC5C08BB8F8C7260D5 | SHA256:23D618A0293C78CE00F7C6E6DD8B8923621DA7DD1F63A070163EF4C0EC3033D6 | |||
| 4520 | StartAllBack.v3.8.13.exe | C:\Users\admin\AppData\Local\Temp\nswDCD0.tmp\LangDLL.dll | executable | |
MD5:549EE11198143574F4D9953198A09FE8 | SHA256:131AA0DF90C08DCE2EECEE46CCE8759E9AFFF04BF15B7B0002C2A53AE5E92C36 | |||
| 4520 | StartAllBack.v3.8.13.exe | C:\Users\admin\AppData\Local\Temp\STARTISBACK\StartIsBack64.dll | executable | |
MD5:7CA847E6522F074352EADC0B62EB3399 | SHA256:584D631FA9F62873409CC51777FBBE8DF673887A8AF0A092D4B0523DA512E577 | |||
| 4520 | StartAllBack.v3.8.13.exe | C:\Users\admin\AppData\Local\Temp\STARTISBACK\UpdateCheck.exe | executable | |
MD5:F9756C261AA978C787302DEBFF8F142A | SHA256:A8D52A2653709D93D0D2C05D653DCF8F0CB06F11422D183EB6871528C95DF319 | |||
| 4520 | StartAllBack.v3.8.13.exe | C:\Users\admin\AppData\Local\Temp\STARTISBACK\Orbs\StartIsBack_Ei8htOrb_v2_by_PainteR.bmp | image | |
MD5:641328C75E6B117545211DB22DAFCAA0 | SHA256:76A72C9AD77843B58223DD588483AC1265A31C15AAEB47EE66D1925DE787644B | |||
| 4520 | StartAllBack.v3.8.13.exe | C:\Users\admin\AppData\Local\Temp\STARTISBACK\Orbs\Windows 7.orb | executable | |
MD5:85328E698E8A74852B4061A683915DC8 | SHA256:E5B74E9E7BD6758A0154B11462AE3328EDD143190865198104D8BD53B9AF7275 | |||
| 4520 | StartAllBack.v3.8.13.exe | C:\Users\admin\AppData\Local\Temp\nswDCD0.tmp\nsDialogs.dll | executable | |
MD5:B7D61F3F56ABF7B7FF0D4E7DA3AD783D | SHA256:89A82C4849C21DFE765052681E1FAD02D2D7B13C8B5075880C52423DCA72A912 | |||
| 4520 | StartAllBack.v3.8.13.exe | C:\Users\admin\AppData\Local\Temp\nswDCCF.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
69
TCP/UDP connections
59
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 72.246.169.155:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.31.128:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 400 | 20.190.159.131:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.31.128:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.159.130:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.31.67:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 200 | 40.126.31.0:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.3:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.128:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.67:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2168 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.55.110.211:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.55.110.211:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 72.246.169.155:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 72.246.169.155:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2168 | RUXIMICS.exe | 72.246.169.155:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
www.bing.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
explorer.exe | Purging StartIsBack cache directory |