| File name: | Lesbian Porn.exe |
| Full analysis: | https://app.any.run/tasks/f5413a2d-3b95-487e-b7a4-924fad422de3 |
| Verdict: | Malicious activity |
| Analysis date: | February 02, 2021, 07:17:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9070443026870D41BE58CEA9BBE1E662 |
| SHA1: | 63663DCC2A4DE23C281E1703C92A36597AF930EB |
| SHA256: | 7F3260DC5EB86551359905CE5395D4BD3C87A543090DF8CF6E14BE7745ADF3B2 |
| SSDEEP: | 12288:fhkDgouVA2nxKkoCvdRgQriDwOIjmxiZnYQE7PJcW4amwBzogUn8gX:lRmJkZoQricOISxiZY1sa7zotb |
MALICIOUS
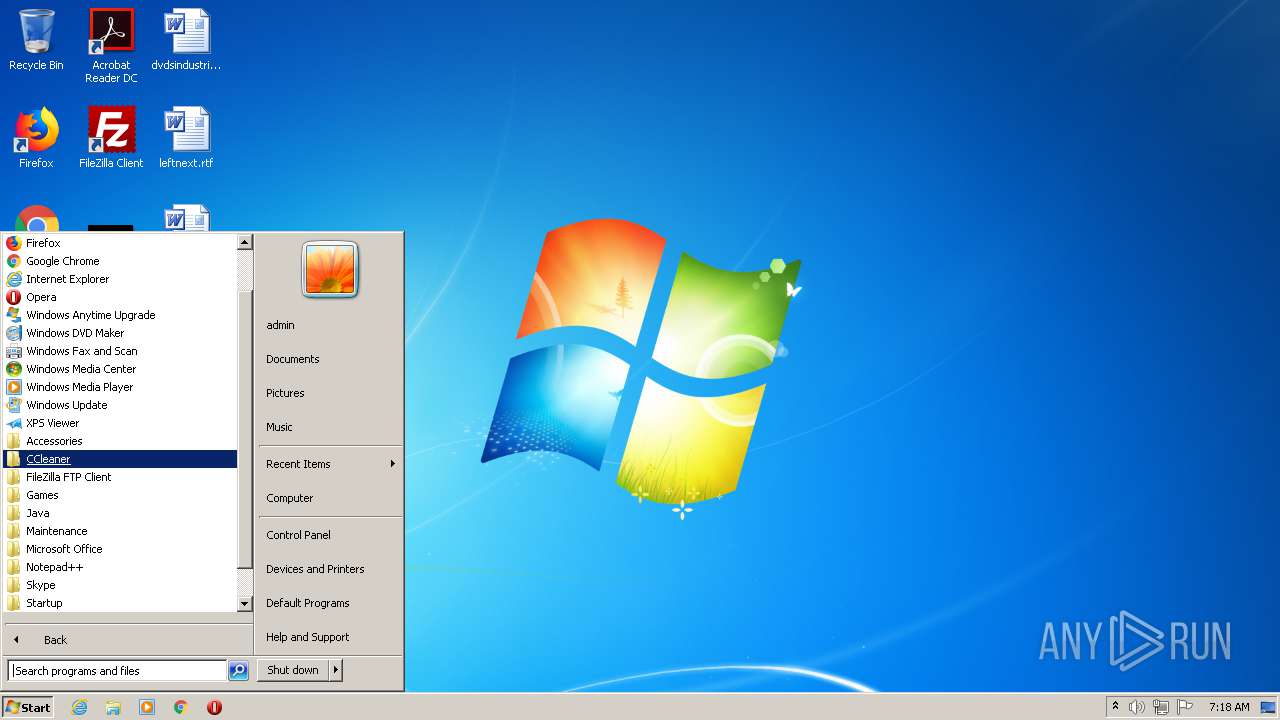
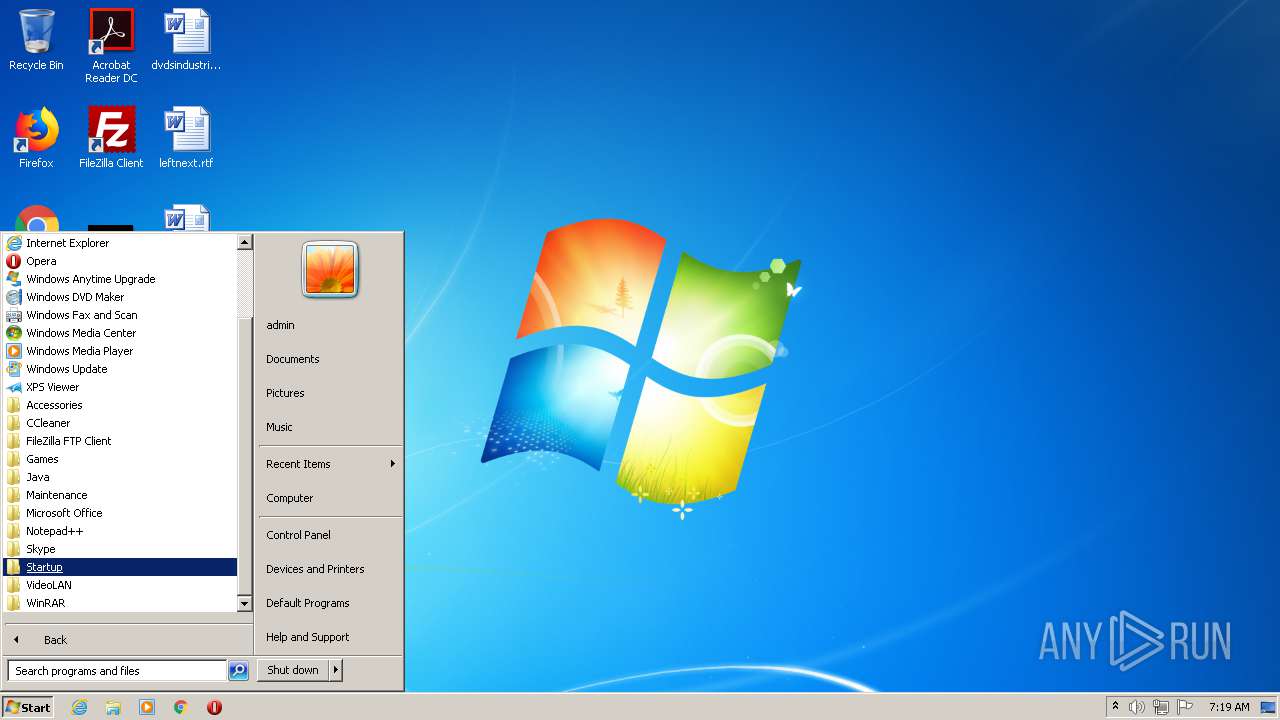
Writes to a start menu file
- Lesbian Porn.exe (PID: 1924)
Connects to CnC server
- Lesbian Porn.exe (PID: 1924)
Changes the autorun value in the registry
- Lesbian Porn.exe (PID: 1924)
SUSPICIOUS
Drops a file with a compile date too recent
- Lesbian Porn.exe (PID: 1924)
Uses NETSH.EXE for network configuration
- Lesbian Porn.exe (PID: 1924)
Creates files in the user directory
- Lesbian Porn.exe (PID: 1924)
Executable content was dropped or overwritten
- Lesbian Porn.exe (PID: 1924)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:01:29 22:32:28+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 526336 |
| InitializedDataSize: | 247296 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x165c1 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.7.3.0 |
| ProductVersionNumber: | 6.7.3.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| CompanyName: | ymjhcnykmmmmmmjhkuy, |
| Comments: | hbmjhvj,v hhjn,jh |
| FileDescription: | j,vhjmcngmyjhcj |
| FileVersion: | 6.7.3 |
| InternalName: | xfgngmhgmhg |
Total processes
38
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1924 | "C:\Users\admin\AppData\Local\Temp\Lesbian Porn.exe" | C:\Users\admin\AppData\Local\Temp\Lesbian Porn.exe | explorer.exe | ||||||||||||
User: admin Company: ymjhcnykmmmmmmjhkuy, Integrity Level: MEDIUM Description: j,vhjmcngmyjhcj Exit code: 0 Version: 6.7.3 Modules
| |||||||||||||||
| 3412 | "C:\Windows\System32\netsh.exe" firewall add allowedprogram "C:\Users\admin\AppData\Local\Temp\Lesbian Porn.exe" "Lesbian Porn.exe" ENABLE | C:\Windows\System32\netsh.exe | — | Lesbian Porn.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
135
Read events
69
Write events
66
Delete events
0
Modification events
| (PID) Process: | (1924) Lesbian Porn.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Lesbian Porn.exe |
Value: "C:\Users\admin\AppData\Local\Temp\Lesbian Porn.exe" | |||
| (PID) Process: | (1924) Lesbian Porn.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Lesbian Porn.exe |
Value: "C:\Users\admin\AppData\Local\Temp\Lesbian Porn.exe" | |||
| (PID) Process: | (3412) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3412) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-100 |
Value: DHCP Quarantine Enforcement Client | |||
| (PID) Process: | (3412) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-101 |
Value: Provides DHCP based enforcement for NAP | |||
| (PID) Process: | (3412) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-103 |
Value: 1.0 | |||
| (PID) Process: | (3412) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-102 |
Value: Microsoft Corporation | |||
| (PID) Process: | (3412) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\napipsec.dll,-1 |
Value: IPsec Relying Party | |||
| (PID) Process: | (3412) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\napipsec.dll,-2 |
Value: Provides IPsec based enforcement for Network Access Protection | |||
| (PID) Process: | (3412) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\napipsec.dll,-4 |
Value: 1.0 | |||
Executable files
1
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1924 | Lesbian Porn.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Lesbian Porn.exe | executable | |
MD5:— | SHA256:— | |||
| 1924 | Lesbian Porn.exe | C:\Users\admin\AppData\Local\Temp\Lesbian Porn.exe.ini | text | |
MD5:301A3E5A5C08C60B2952122A97E1A838 | SHA256:89886E624DB56B7F7E7A0A857FC7E63EBFFFE9EB69B329489B79DD0A3E24F7FA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
3
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1924 | Lesbian Porn.exe | 91.109.180.3:8816 | lolotmo1.no-ip.biz | Lost Oasis SARL | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
lolotmo1.no-ip.biz |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a Suspicious no-ip Domain |
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
1924 | Lesbian Porn.exe | A Network Trojan was detected | ET WORM W32/Njw0rm CnC Beacon |