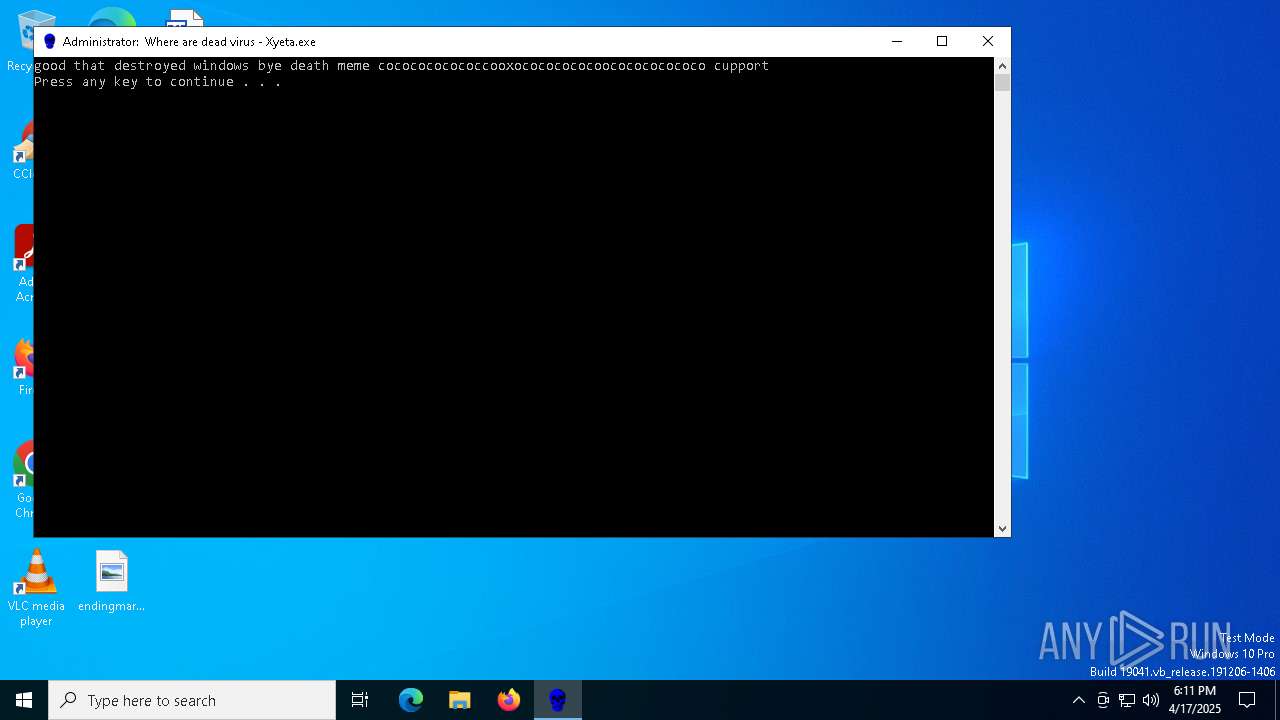
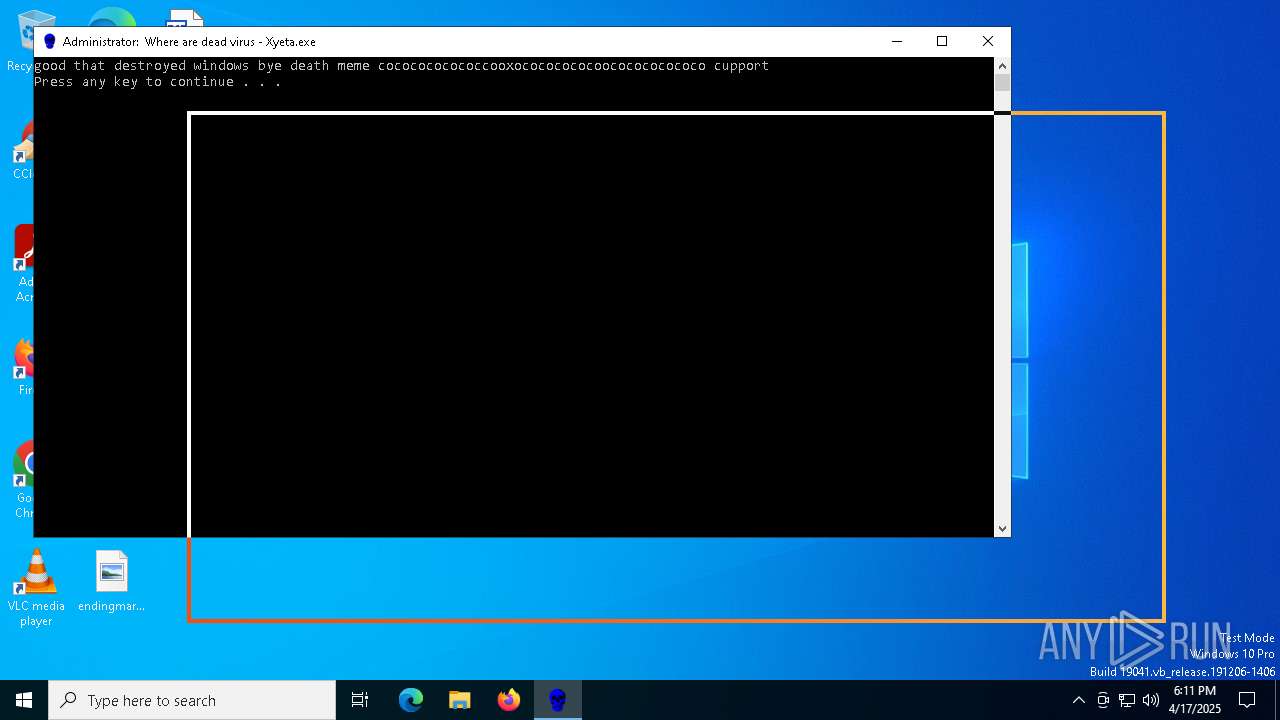
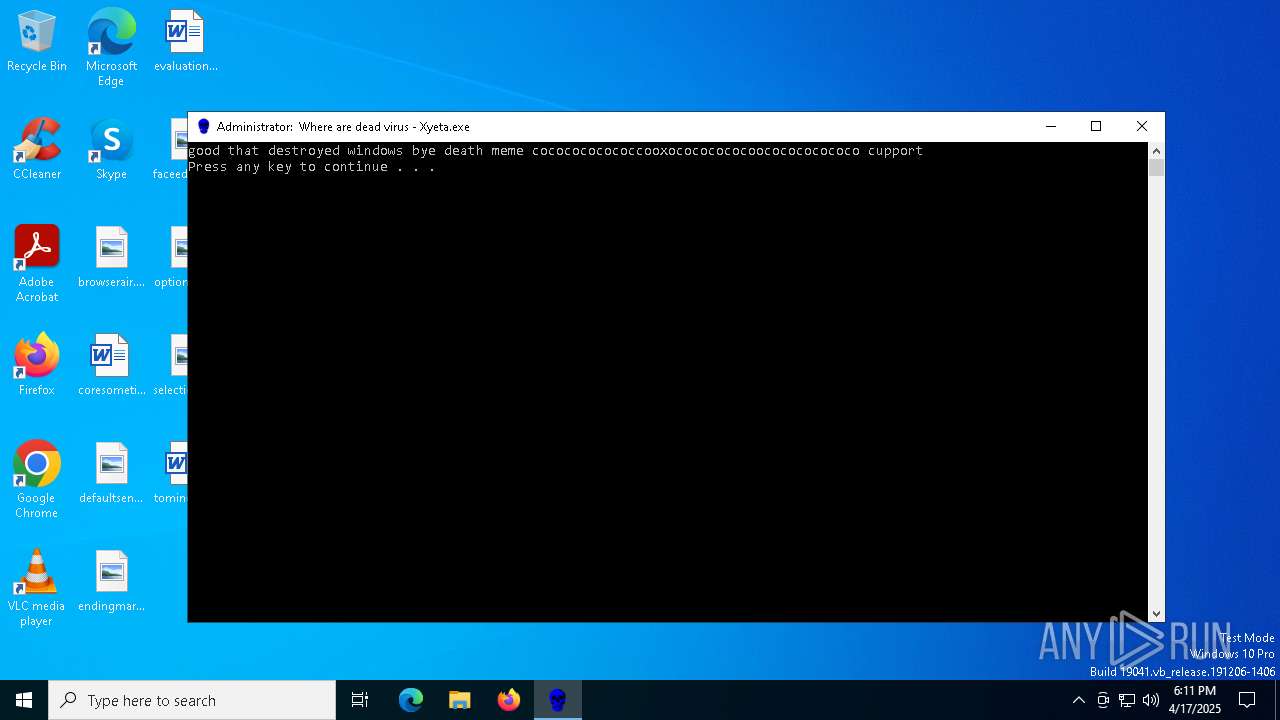
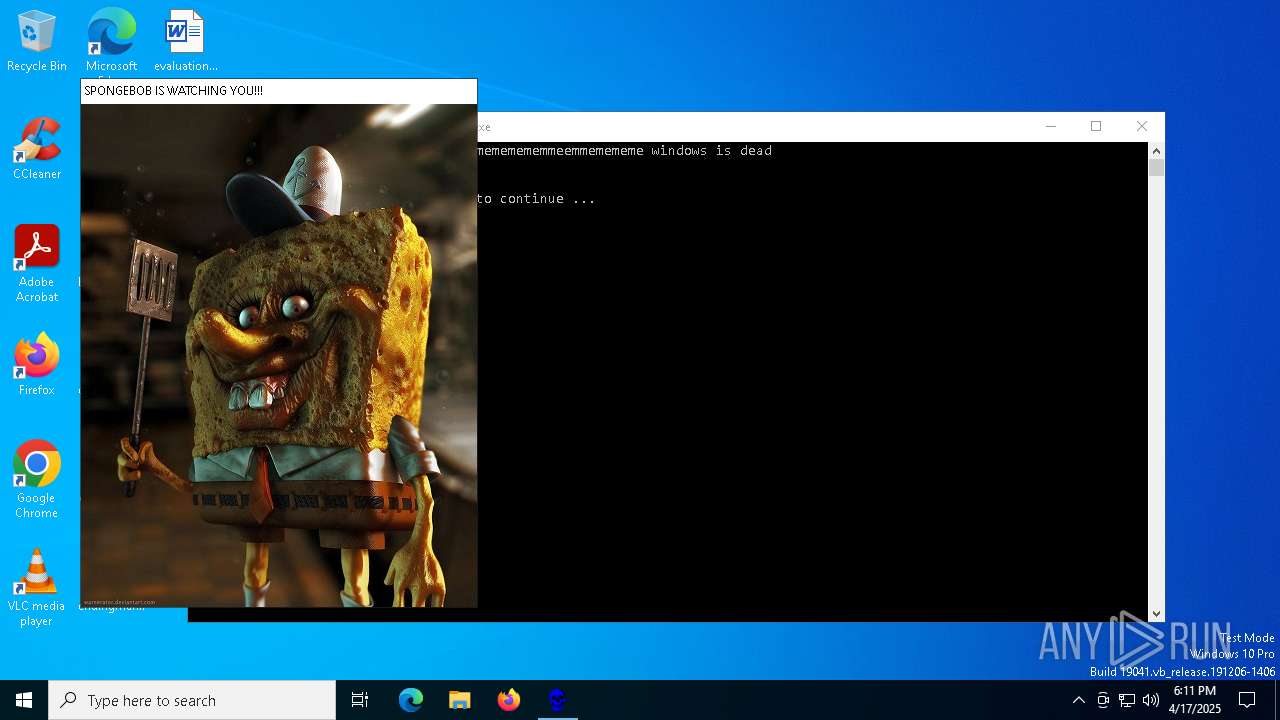
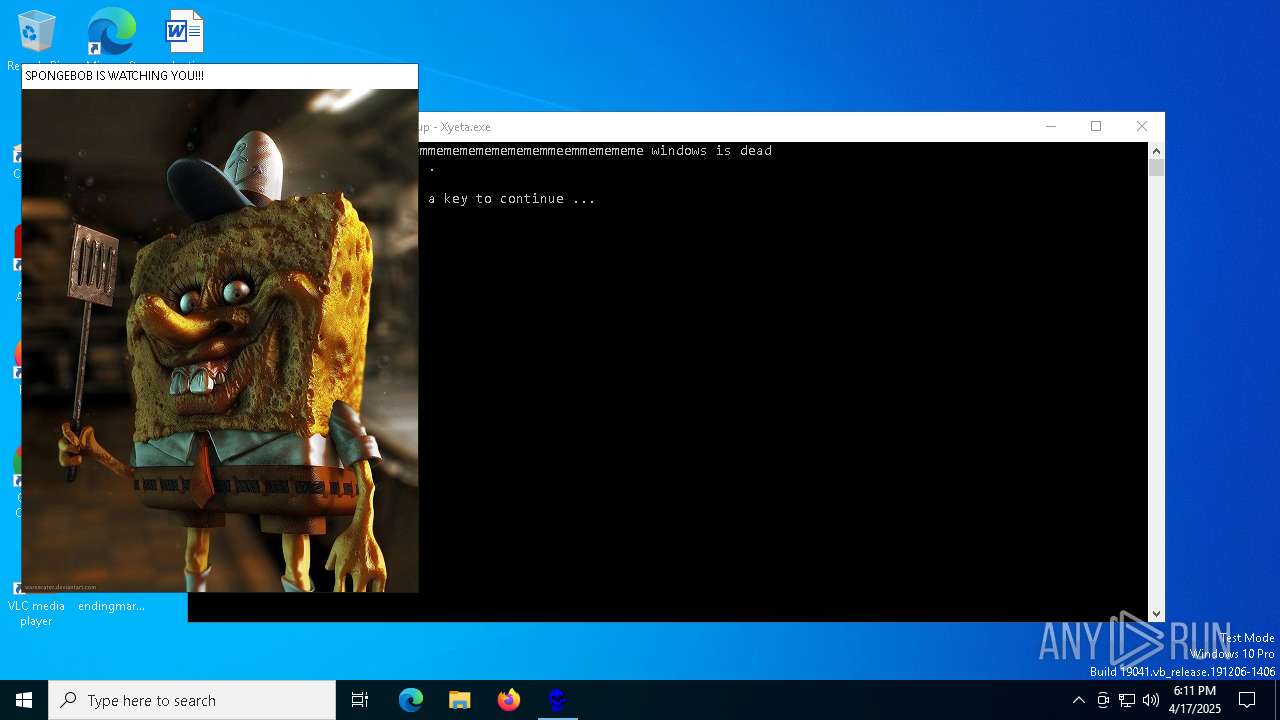
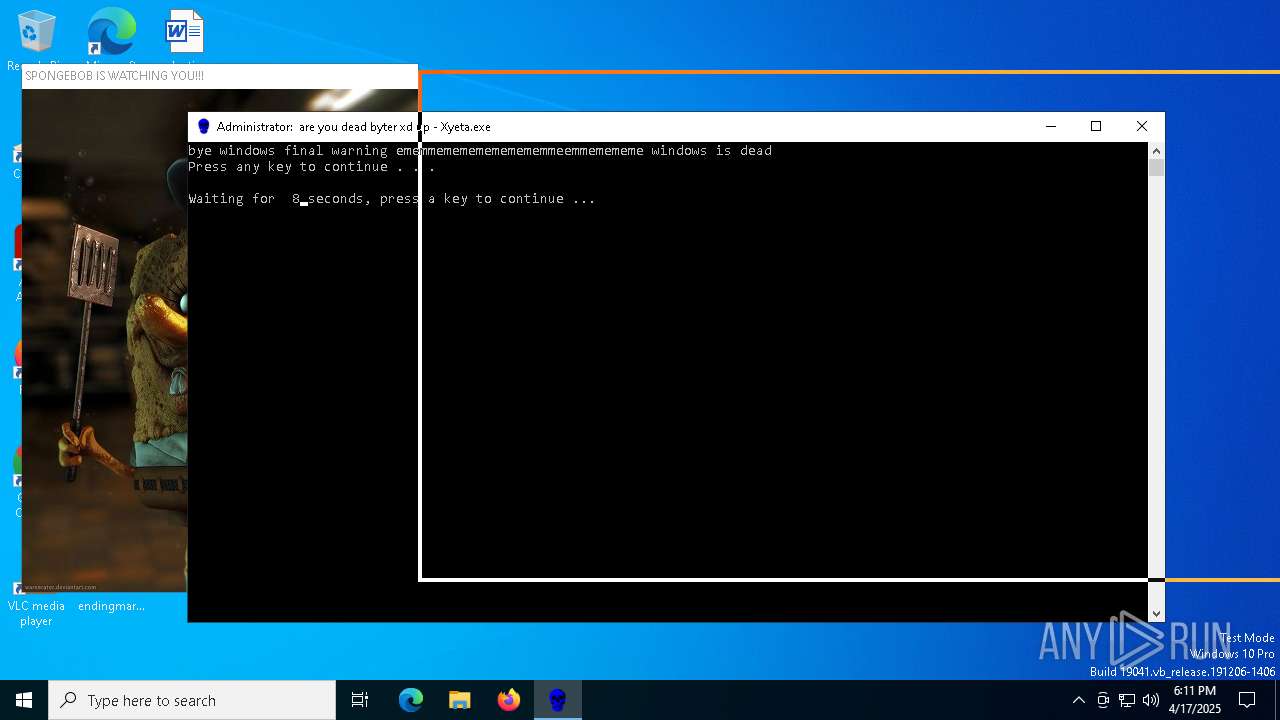
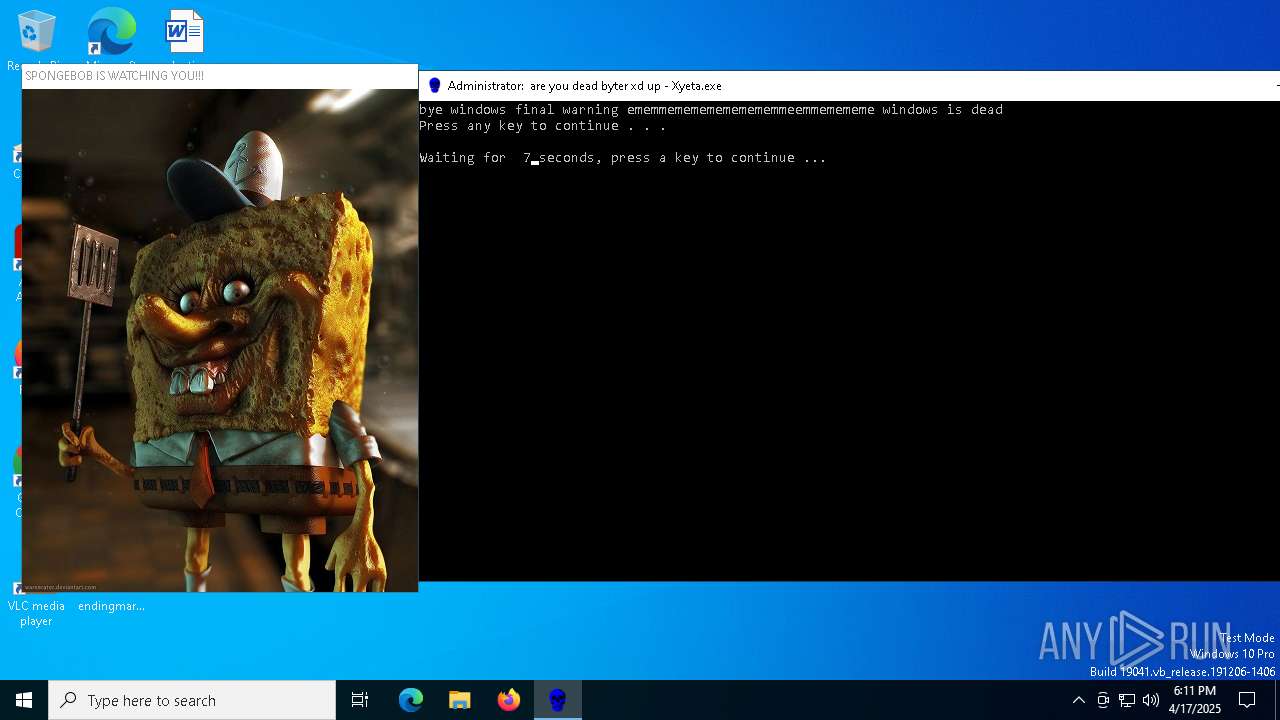
| File name: | Xyeta.exe |
| Full analysis: | https://app.any.run/tasks/68967ddc-11d0-4a1f-825e-72b159e537fc |
| Verdict: | Malicious activity |
| Analysis date: | April 17, 2025, 18:11:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 5 sections |
| MD5: | 8D5AC3A5FA3E8550947012B551B87E15 |
| SHA1: | 1696AE03E51510091E856FFCC1785E2838913D98 |
| SHA256: | 7F1B9C45A25E7EF1A8388965A45047AFAE0926E19C0E00A41CC4CBD75BACA0D2 |
| SSDEEP: | 98304:k9lssslGGGWEEEliiijjjjCLLLLLLLLLLLLLLLNiiiaooosVVVVUUUG000eXXXm7:m+ |
MALICIOUS
GENERIC has been found (auto)
- Xyeta.exe (PID: 7216)
Uses Task Scheduler to run other applications
- MBR.exe (PID: 7752)
Changes the autorun value in the registry
- MBR.exe (PID: 7752)
SUSPICIOUS
Executing commands from a ".bat" file
- Xyeta.exe (PID: 7216)
Starts CMD.EXE for commands execution
- Xyeta.exe (PID: 7216)
Executable content was dropped or overwritten
- Xyeta.exe (PID: 7216)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7284)
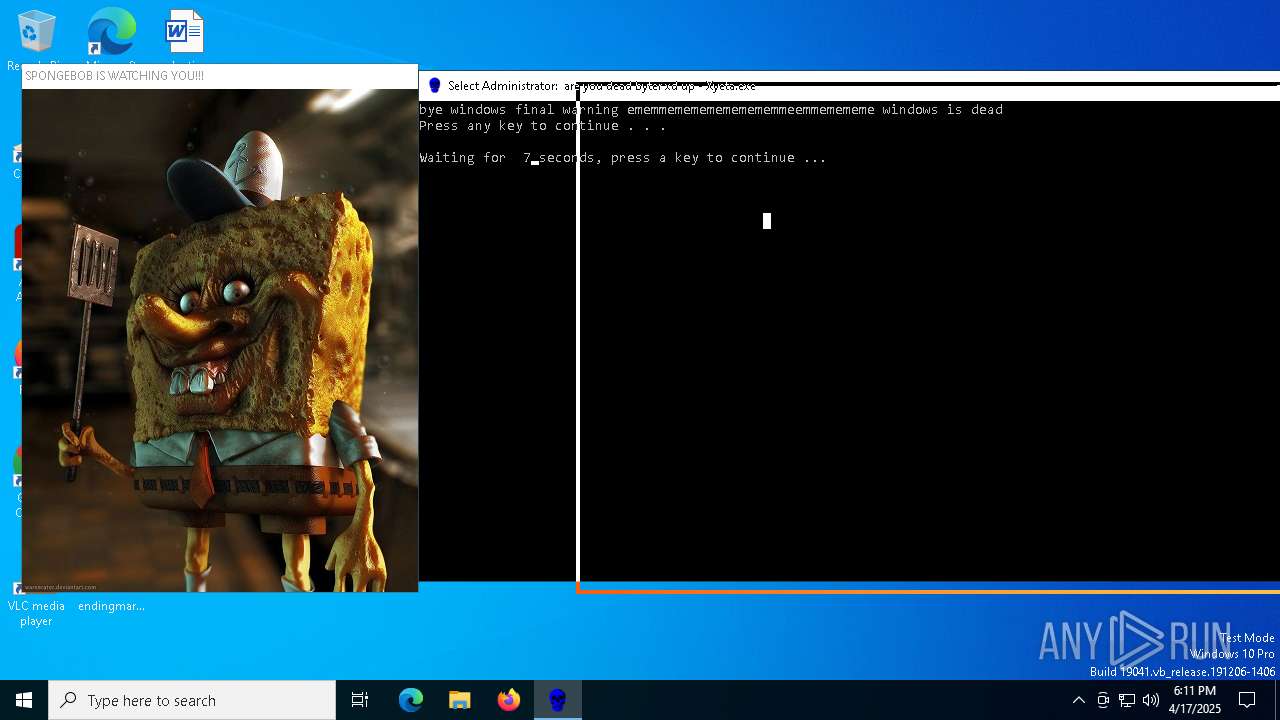
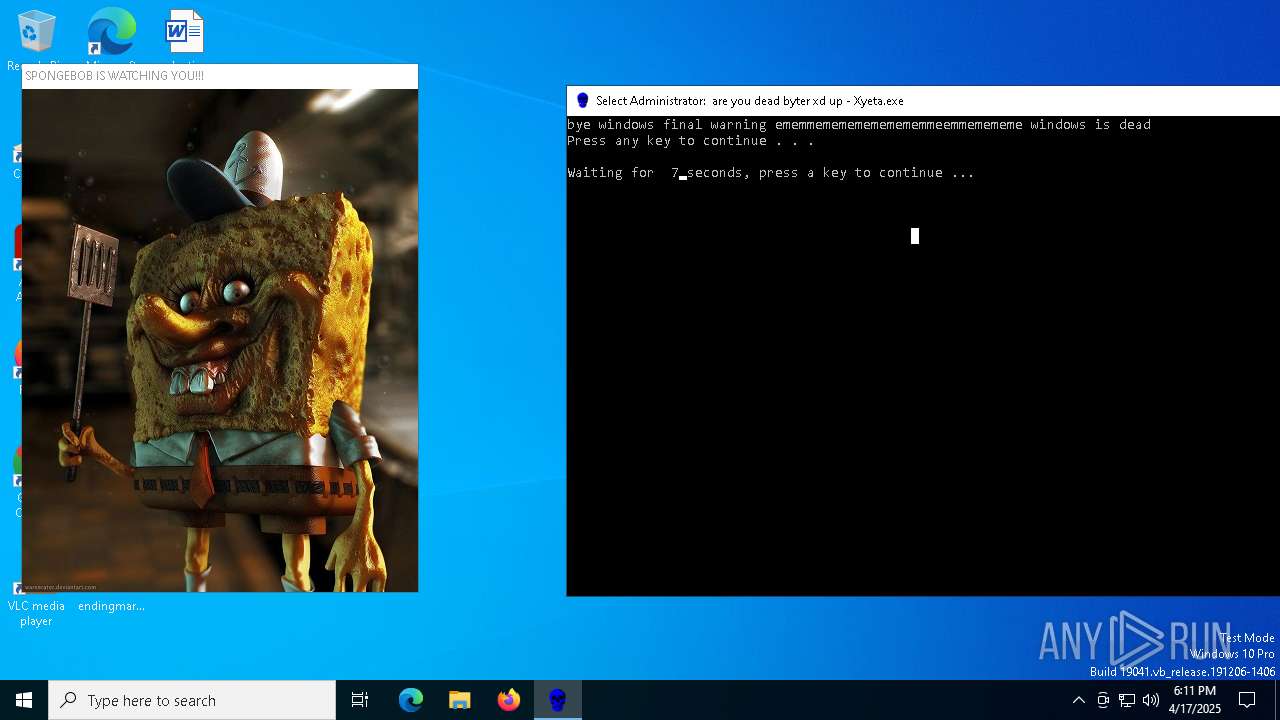
Probably fake Windows Update
- schtasks.exe (PID: 7808)
There is functionality for taking screenshot (YARA)
- Xyeta.exe (PID: 7216)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7284)
INFO
Checks supported languages
- MBR.exe (PID: 7752)
- Xyeta.exe (PID: 7216)
- snd1.exe (PID: 7760)
- ScaryBob.exe (PID: 7772)
- noise.exe (PID: 8088)
- PatBlt3.exe (PID: 8096)
- sqmove.exe (PID: 8112)
The sample compiled with english language support
- Xyeta.exe (PID: 7216)
Create files in a temporary directory
- Xyeta.exe (PID: 7216)
Reads the computer name
- snd1.exe (PID: 7760)
- ScaryBob.exe (PID: 7772)
- noise.exe (PID: 8088)
Reads the software policy settings
- slui.exe (PID: 7352)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Microsoft Visual Basic 6 (47.9) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (18.2) |
| .exe | | | Win64 Executable (generic) (16.1) |
| .scr | | | Windows screen saver (7.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:10:17 13:02:05+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 60416 |
| InitializedDataSize: | 3231744 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
Total processes
147
Monitored processes
17
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4776 | "C:\Users\admin\AppData\Local\Temp\Xyeta.exe" | C:\Users\admin\AppData\Local\Temp\Xyeta.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6816 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7216 | "C:\Users\admin\AppData\Local\Temp\Xyeta.exe" | C:\Users\admin\AppData\Local\Temp\Xyeta.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 7228 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Xyeta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7284 | "C:\WINDOWS\sysnative\cmd" /c "C:\Users\admin\AppData\Local\Temp\B652.tmp\B653.bat C:\Users\admin\AppData\Local\Temp\Xyeta.exe" | C:\Windows\System32\cmd.exe | — | Xyeta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7320 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7352 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7752 | MBR.exe | C:\Users\admin\AppData\Local\Temp\B652.tmp\MBR.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 7760 | snd1.exe | C:\Users\admin\AppData\Local\Temp\B652.tmp\snd1.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 7772 | ScaryBob.exe | C:\Users\admin\AppData\Local\Temp\B652.tmp\ScaryBob.exe | — | cmd.exe | |||||||||||
User: admin Company: HorrorTrojans Integrity Level: HIGH Version: 6.06.0006 Modules
| |||||||||||||||
Total events
1 346
Read events
1 299
Write events
45
Delete events
2
Modification events
| (PID) Process: | (7760) snd1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\AudioCompressionManager\DriverCache\msacm.msg711 |
| Operation: | write | Name: | fdwSupport |
Value: 1 | |||
| (PID) Process: | (7760) snd1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\AudioCompressionManager\DriverCache\msacm.msg711 |
| Operation: | write | Name: | cFormatTags |
Value: 3 | |||
| (PID) Process: | (7760) snd1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\AudioCompressionManager\DriverCache\msacm.msg711 |
| Operation: | write | Name: | aFormatTagCache |
Value: 010000001000000006000000120000000700000012000000 | |||
| (PID) Process: | (7760) snd1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\AudioCompressionManager\DriverCache\msacm.msg711 |
| Operation: | write | Name: | cFilterTags |
Value: 0 | |||
| (PID) Process: | (7760) snd1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\AudioCompressionManager\DriverCache\msacm.msgsm610 |
| Operation: | write | Name: | fdwSupport |
Value: 1 | |||
| (PID) Process: | (7760) snd1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\AudioCompressionManager\DriverCache\msacm.msgsm610 |
| Operation: | write | Name: | cFormatTags |
Value: 2 | |||
| (PID) Process: | (7760) snd1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\AudioCompressionManager\DriverCache\msacm.msgsm610 |
| Operation: | write | Name: | aFormatTagCache |
Value: 01000000100000003100000014000000 | |||
| (PID) Process: | (7760) snd1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\AudioCompressionManager\DriverCache\msacm.msgsm610 |
| Operation: | write | Name: | cFilterTags |
Value: 0 | |||
| (PID) Process: | (7760) snd1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\AudioCompressionManager\DriverCache\msacm.l3acm |
| Operation: | write | Name: | fdwSupport |
Value: 1 | |||
| (PID) Process: | (7760) snd1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\AudioCompressionManager\DriverCache\msacm.l3acm |
| Operation: | write | Name: | cFormatTags |
Value: 2 | |||
Executable files
6
Suspicious files
2
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7752 | MBR.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 7216 | Xyeta.exe | C:\Users\admin\AppData\Local\Temp\B652.tmp\B653.bat | text | |
MD5:E0E08D707F7F23265B342395801D6025 | SHA256:FD6F446C397D227E7D931E7FD098D7C9A33975C40989218FC9E82B5F2A457746 | |||
| 7216 | Xyeta.exe | C:\Users\admin\AppData\Local\Temp\B652.tmp\noise.wav | binary | |
MD5:5633E3AC07AC396635C72F38956295BA | SHA256:E4E02350B261D25F37C52EA06079C0CCF759EC4ABADD12B8A826B9D6361A21C4 | |||
| 7216 | Xyeta.exe | C:\Users\admin\AppData\Local\Temp\B652.tmp\sqmove.exe | executable | |
MD5:8AD1DA4C2B678FFBC0F5D95ADFEB5C9B | SHA256:6CAAD2810E0D398EF80F5AA63F8F9ED09DBC5B6BB169E43B7319FE9A1EEA85F2 | |||
| 7216 | Xyeta.exe | C:\Users\admin\AppData\Local\Temp\B652.tmp\ScaryBob.exe | executable | |
MD5:DA6EA8C9E8072DD9B07CF18EACA5BF1F | SHA256:7989C7E5C2D6277718AC7D529334B0547F428D2E8BBBF0E71EF6EA5161B26320 | |||
| 7216 | Xyeta.exe | C:\Users\admin\AppData\Local\Temp\B652.tmp\MBR.exe | executable | |
MD5:4D56B50156494C20372908A20DAD3B34 | SHA256:AAF6029FF69D4EDDF3442855DFFA507F52CFBB73D5B22D9B06CAC0915E41FC9C | |||
| 7216 | Xyeta.exe | C:\Users\admin\AppData\Local\Temp\B652.tmp\snd1.wav | binary | |
MD5:18BF859250C6EE6A2C48ABC244B805CA | SHA256:EF96EBBC8BA14D21D091341D1FBEFE4A2D6956826F183BE6E4191EDA5F541F5C | |||
| 7216 | Xyeta.exe | C:\Users\admin\AppData\Local\Temp\B652.tmp\PatBlt3.exe | executable | |
MD5:08E74E5F077F0337D0C0D15DDE94F8BE | SHA256:B41D36F67E147133F8C3AA054B52275F68D7E2735A65EB3ABCDCD08BEDE1100B | |||
| 7216 | Xyeta.exe | C:\Users\admin\AppData\Local\Temp\B652.tmp\noise.exe | executable | |
MD5:3C285EEC317672F7EB27EC27244CBE59 | SHA256:81CBB8C54D2DFDDA281E37AFF08F9F98AFAB3F415FBE3C7B5242C1B85495E715 | |||
| 7216 | Xyeta.exe | C:\Users\admin\AppData\Local\Temp\B652.tmp\snd1.exe | executable | |
MD5:C59DBF876BF5AB5F7073E38B382F2686 | SHA256:85C6416337E28D1CA1C5DAC316CDB36B967E6ABF18F4D19CC85B1471FF382C28 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
18
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5048 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5048 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
2656 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.25:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5048 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |