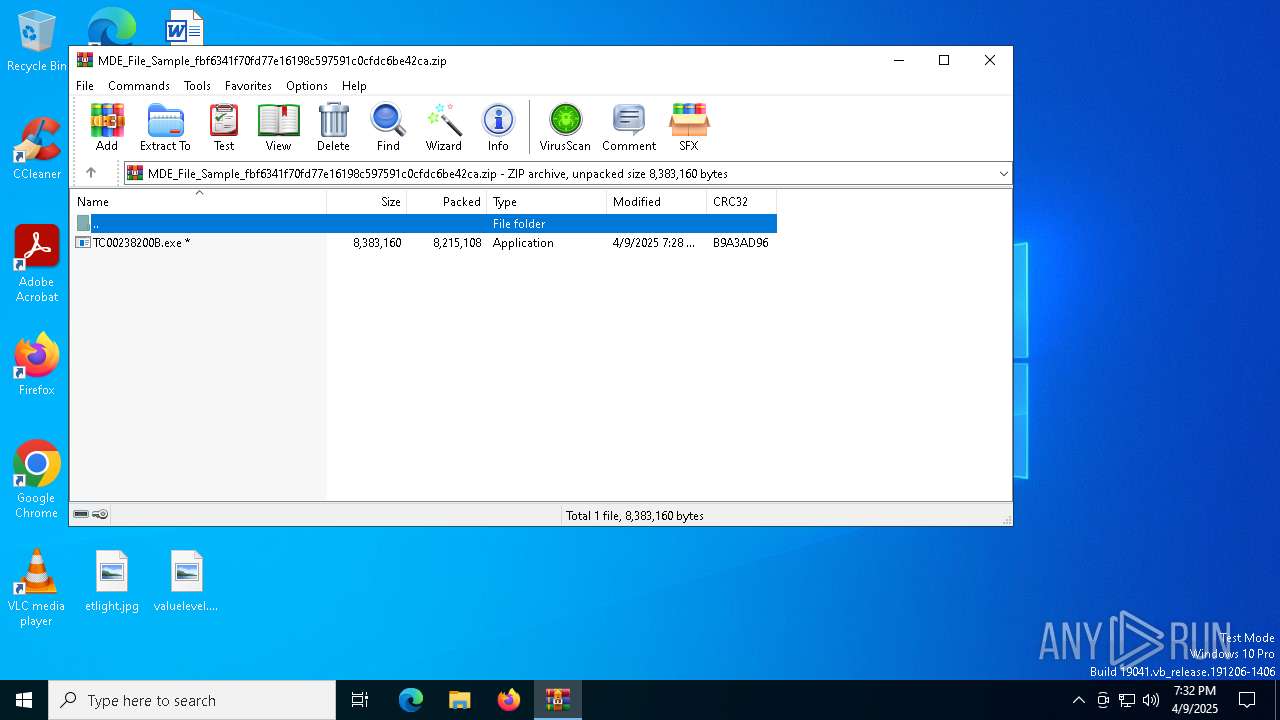
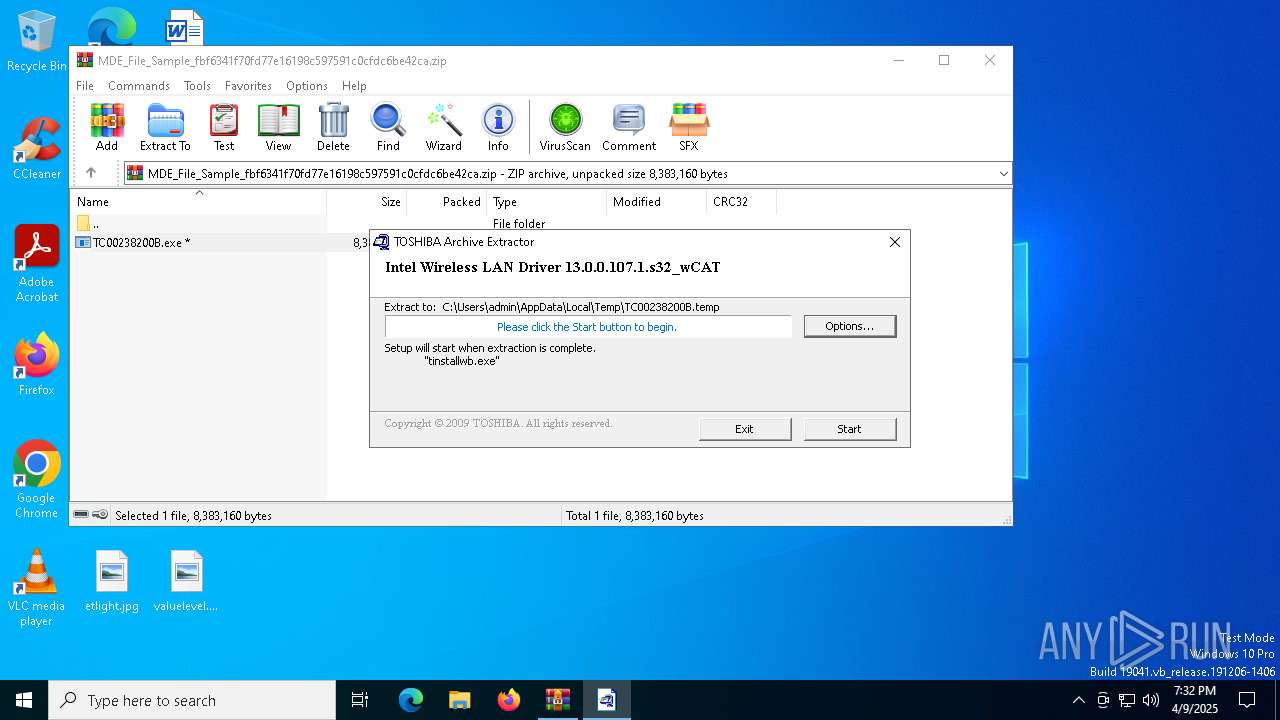
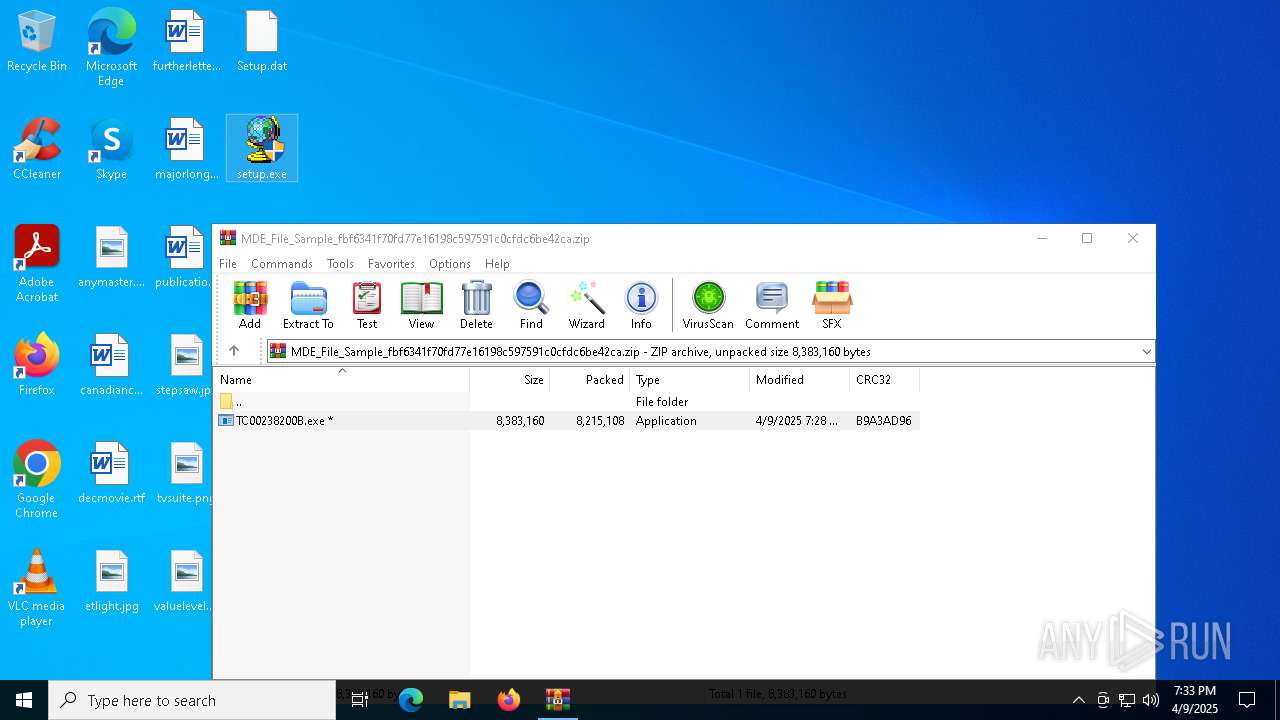
| File name: | MDE_File_Sample_fbf6341f70fd77e16198c597591c0cfdc6be42ca.zip |
| Full analysis: | https://app.any.run/tasks/fa989b12-4f83-4093-b9ae-572c882092ff |
| Verdict: | Malicious activity |
| Analysis date: | April 09, 2025, 19:32:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C71D3081D00ECC06DD3636162F158306 |
| SHA1: | 6128C0D023AB6A75F6724C2B9ACB1248103405EE |
| SHA256: | 7F135949A5F86340C5CE3FC28E80A69B91E309229F0007EFA5D6BE9701BC4CA1 |
| SSDEEP: | 98304:APLbHD0T8xJI66hyPqZu0TICIMHtfREWw4Y9z8govTgB5KDpDC6Zzjd504BNK0Ju:0GNNOUTKl4abIA |
MALICIOUS
Executing a file with an untrusted certificate
- TC00238200B.exe (PID: 7496)
- tinstallwb.exe (PID: 7808)
- tinstallwb.exe (PID: 7856)
- setup.exe (PID: 7988)
- setup.exe (PID: 8036)
- setup.exe (PID: 7896)
- setup.exe (PID: 8128)
- setup.exe (PID: 8176)
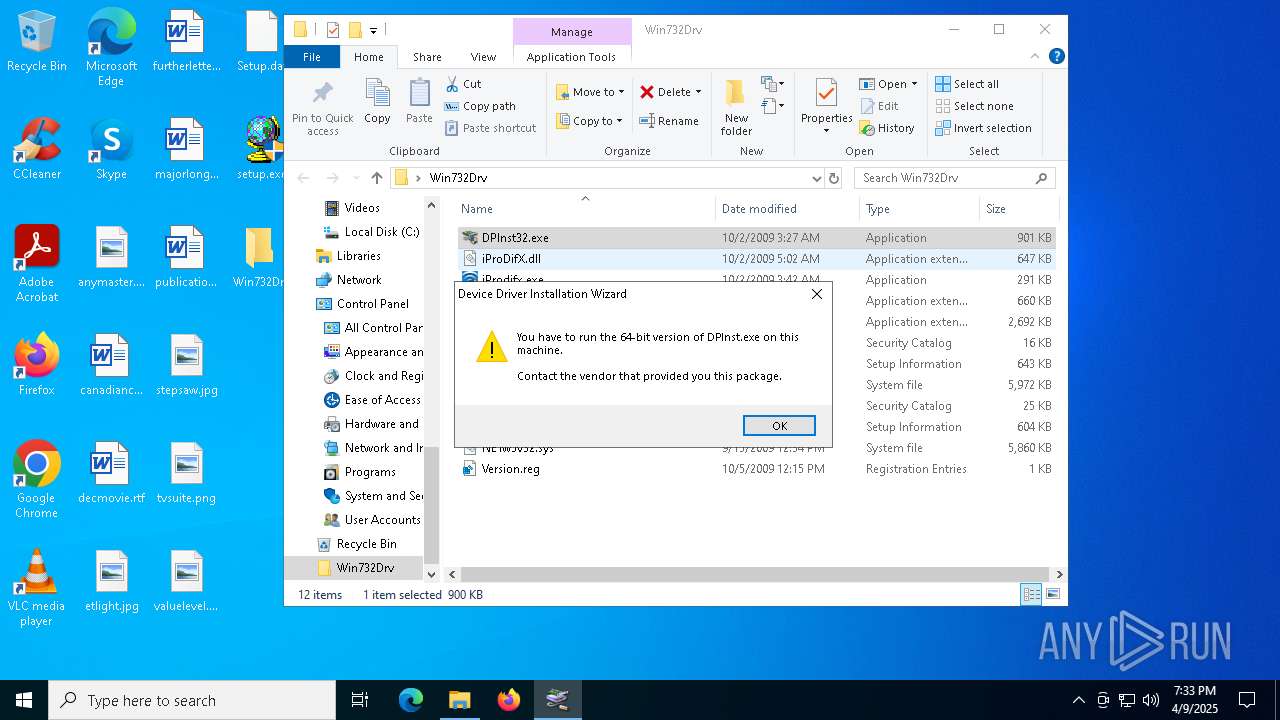
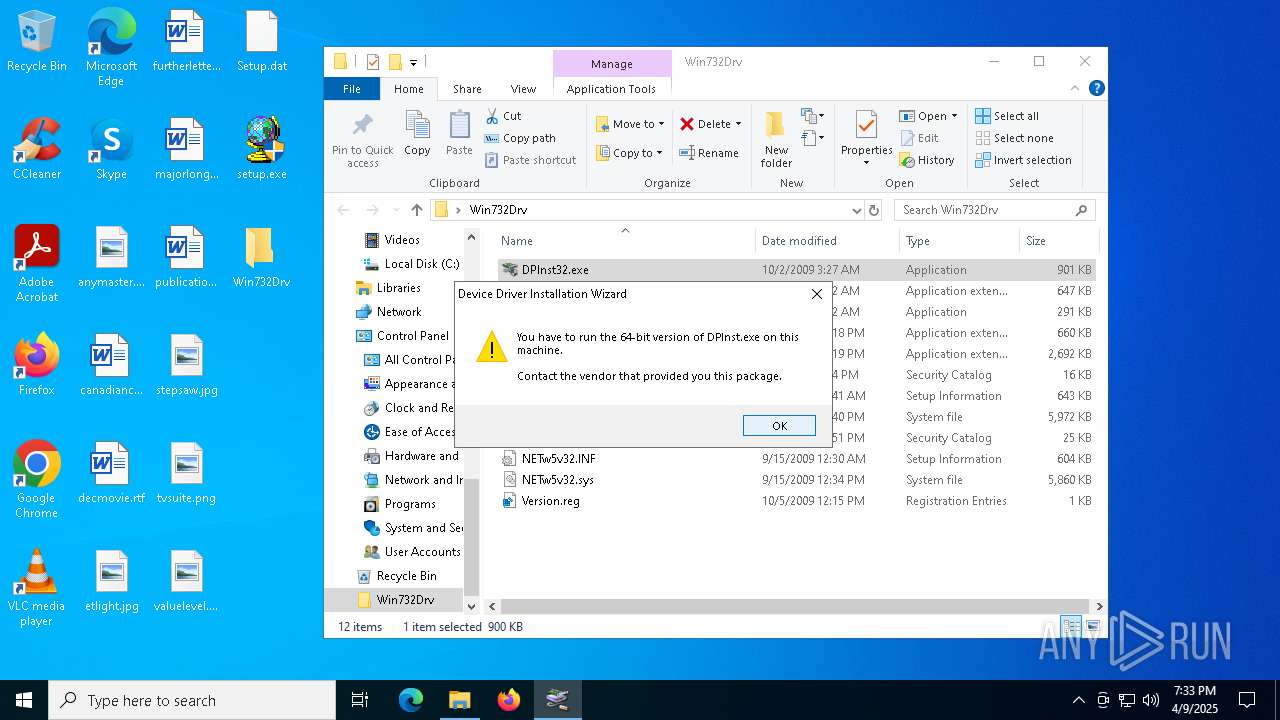
- DPInst32.exe (PID: 3332)
- DPInst32.exe (PID: 1660)
- DPInst32.exe (PID: 5800)
- DPInst32.exe (PID: 1052)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 664)
- TC00238200B.exe (PID: 7496)
Process drops legitimate windows executable
- TC00238200B.exe (PID: 7496)
Drops a system driver (possible attempt to evade defenses)
- TC00238200B.exe (PID: 7496)
Executable content was dropped or overwritten
- TC00238200B.exe (PID: 7496)
Uses REG/REGEDIT.EXE to modify registry
- setup.exe (PID: 7896)
- setup.exe (PID: 8176)
- setup.exe (PID: 8036)
Creates file in the systems drive root
- tinstallwb.exe (PID: 7856)
The process checks if it is being run in the virtual environment
- tinstallwb.exe (PID: 7856)
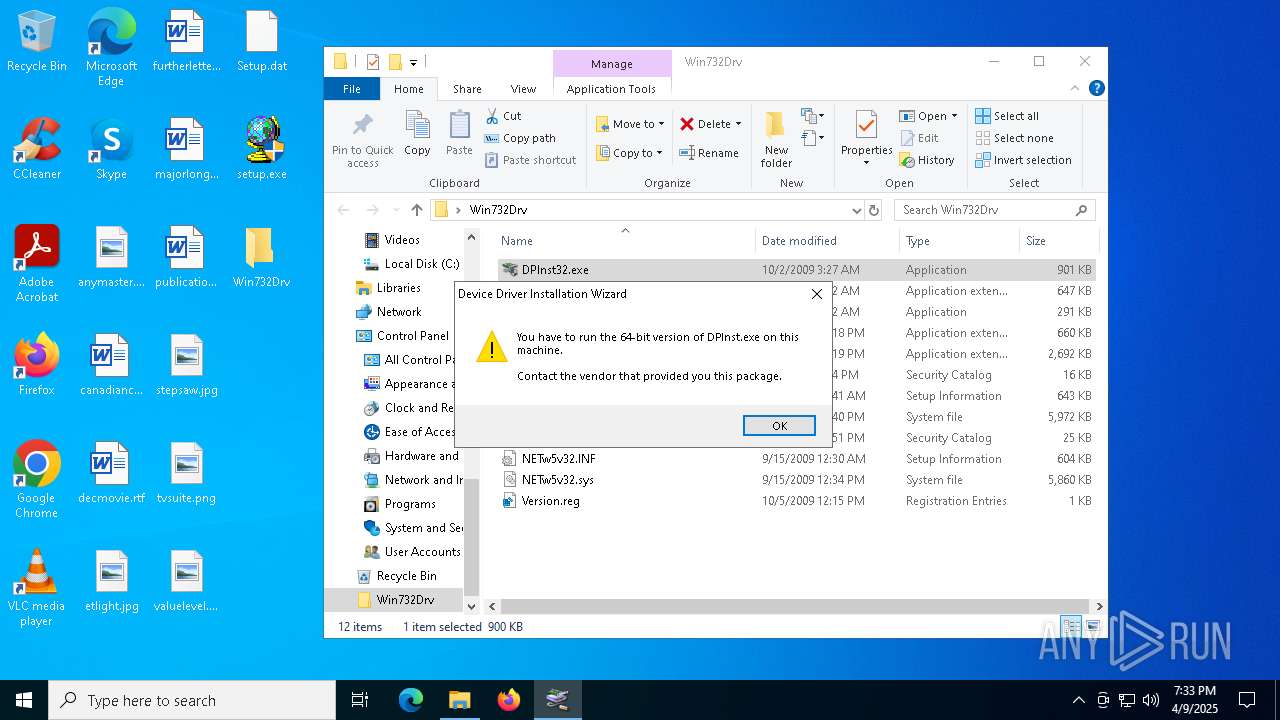
Starts a Microsoft application from unusual location
- DPInst32.exe (PID: 3332)
- DPInst32.exe (PID: 1660)
- DPInst32.exe (PID: 5800)
- DPInst32.exe (PID: 1052)
INFO
The sample compiled with arabic language support
- TC00238200B.exe (PID: 7496)
The sample compiled with japanese language support
- TC00238200B.exe (PID: 7496)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 664)
Reads the computer name
- TC00238200B.exe (PID: 7496)
- setup.exe (PID: 7896)
- tinstallwb.exe (PID: 7856)
- DPInst32.exe (PID: 1660)
- DPInst32.exe (PID: 1052)
Checks supported languages
- TC00238200B.exe (PID: 7496)
- setup.exe (PID: 7896)
- setup.exe (PID: 8036)
- tinstallwb.exe (PID: 7856)
- setup.exe (PID: 8176)
- DPInst32.exe (PID: 1660)
- DPInst32.exe (PID: 1052)
The sample compiled with english language support
- TC00238200B.exe (PID: 7496)
Process checks computer location settings
- TC00238200B.exe (PID: 7496)
- setup.exe (PID: 7896)
- setup.exe (PID: 8036)
- setup.exe (PID: 8176)
Reads the machine GUID from the registry
- setup.exe (PID: 7896)
- setup.exe (PID: 8176)
- setup.exe (PID: 8036)
Create files in a temporary directory
- setup.exe (PID: 7896)
- setup.exe (PID: 8176)
- setup.exe (PID: 8036)
Creates files or folders in the user directory
- setup.exe (PID: 7896)
Manual execution by a user
- setup.exe (PID: 8036)
- setup.exe (PID: 7988)
- setup.exe (PID: 8176)
- DPInst32.exe (PID: 3332)
- DPInst32.exe (PID: 1660)
- setup.exe (PID: 8128)
- DPInst32.exe (PID: 5800)
- DPInst32.exe (PID: 1052)
Reads the software policy settings
- slui.exe (PID: 7276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:09 19:28:38 |
| ZipCRC: | 0xb9a3ad96 |
| ZipCompressedSize: | 8215108 |
| ZipUncompressedSize: | 8383160 |
| ZipFileName: | TC00238200B.exe |
Total processes
154
Monitored processes
23
Malicious processes
6
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\MDE_File_Sample_fbf6341f70fd77e16198c597591c0cfdc6be42ca.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1052 | "C:\Users\admin\Desktop\Win732Drv\DPInst32.exe" | C:\Users\admin\Desktop\Win732Drv\DPInst32.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 2147483648 Version: 2.1 Modules
| |||||||||||||||
| 1324 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | "C:\Users\admin\Desktop\Win732Drv\DPInst32.exe" | C:\Users\admin\Desktop\Win732Drv\DPInst32.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 2147483648 Version: 2.1 Modules
| |||||||||||||||
| 2432 | C:\WINDOWS\regedit /s "C:\Users\admin\Desktop\HWDev.reg" | C:\Windows\regedit.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3268 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3332 | "C:\Users\admin\Desktop\Win732Drv\DPInst32.exe" | C:\Users\admin\Desktop\Win732Drv\DPInst32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Driver Package Installer Exit code: 3221226540 Version: 2.1 Modules
| |||||||||||||||
| 5800 | "C:\Users\admin\Desktop\Win732Drv\DPInst32.exe" | C:\Users\admin\Desktop\Win732Drv\DPInst32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Driver Package Installer Exit code: 3221226540 Version: 2.1 Modules
| |||||||||||||||
| 7228 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7260 | C:\WINDOWS\regedit /s "C:\Users\admin\Desktop\HWDev.reg" | C:\Windows\SysWOW64\regedit.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 532
Read events
5 223
Write events
4 297
Delete events
12
Modification events
| (PID) Process: | (664) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (664) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (664) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (664) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\MDE_File_Sample_fbf6341f70fd77e16198c597591c0cfdc6be42ca.zip | |||
| (PID) Process: | (664) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (664) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (664) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (664) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (664) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7920) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\TOSHIBA\ConfigFree |
| Operation: | write | Name: | InternalDevice74 |
Value: PCI\VEN_168C&DEV_002A&SUBSYS_7141144F | |||
Executable files
13
Suspicious files
6
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7496 | TC00238200B.exe | C:\Users\admin\Desktop\setup.exe | executable | |
MD5:E368D9EB6C388F336E2591A6AE6B96CD | SHA256:55F6F380E137C170DED4B710668689FBE8B99BDFEAF21B8063FF5C5093F6557B | |||
| 7496 | TC00238200B.exe | C:\Users\admin\Desktop\Version.txt | text | |
MD5:57593CD97DA7C1F31F9686853D233F8D | SHA256:8EED0D666EA4E3F4AF7D8F38204B053E58B36B46BE822981CEBEC3E4434FD495 | |||
| 7496 | TC00238200B.exe | C:\Users\admin\Desktop\Setup.dat | binary | |
MD5:B4F77A0B0734895EA2D64F429F939A6F | SHA256:0B1B560891029F7BFB430467F1E95C0F676342443E57D87AE31B9B51C348FC78 | |||
| 7496 | TC00238200B.exe | C:\Users\admin\Desktop\Win732Drv\iProDifX.dll | executable | |
MD5:38BB87E94AD55DF15E1E41BFB43EEF09 | SHA256:5ABB66806D2F50BA1DDC60488715C78EED4A74E12DA9C87ED70C4F4F75B17F46 | |||
| 7496 | TC00238200B.exe | C:\Users\admin\Desktop\Win732Drv\iProdifx.exe | executable | |
MD5:81EAEE348AF31E97CBFCDAE2CA66332E | SHA256:365D0A201C1F4D8B210EA2A7055AFAEF58FE3CCF6884800CAD6A6945CCF3A8B0 | |||
| 7496 | TC00238200B.exe | C:\Users\admin\Desktop\Win732Drv\NETw5c32.dll | executable | |
MD5:8902A26DE72BDFFEBDEF83B16A2D4AEF | SHA256:736A00ACFB30CBD2A8A361D3FAD4A1A5C0B9DA46EDC30315BE627F828075D593 | |||
| 7496 | TC00238200B.exe | C:\Users\admin\Desktop\Win732Drv\NETw5s32.cat | binary | |
MD5:41D07FEF83694263D6C3F889FA88B70A | SHA256:DCBF243CA48044AF7D0D1299E48C8B8DED652449935AB6CF988875E729CDA38B | |||
| 664 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb664.46050\TC00238200B.exe | executable | |
MD5:F094D944065D1B03D93285CF59473010 | SHA256:1E99ADC792926A1BB2993F1F6E2A5AAE7C69FBB98CA18BAB8925270BA4AD85F3 | |||
| 7496 | TC00238200B.exe | C:\Users\admin\Desktop\Win732Drv\DPInst32.exe | executable | |
MD5:E6213CEC602F332BF8E868B7B8BF2BB1 | SHA256:4478F6FCFD2FC9BE012668592BFBF6838A115D983F9D30171669B20CAFE529B9 | |||
| 7496 | TC00238200B.exe | C:\Users\admin\Desktop\tinstallwb.exe | executable | |
MD5:A3C1616D23A11AAC55740CBB53DBFC7F | SHA256:92854B88554B1B0497C0CA2CD81AF816D0171AEDE92DAFF16A282714B6284682 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
18
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7656 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7656 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7656 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7656 | SIHClient.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |