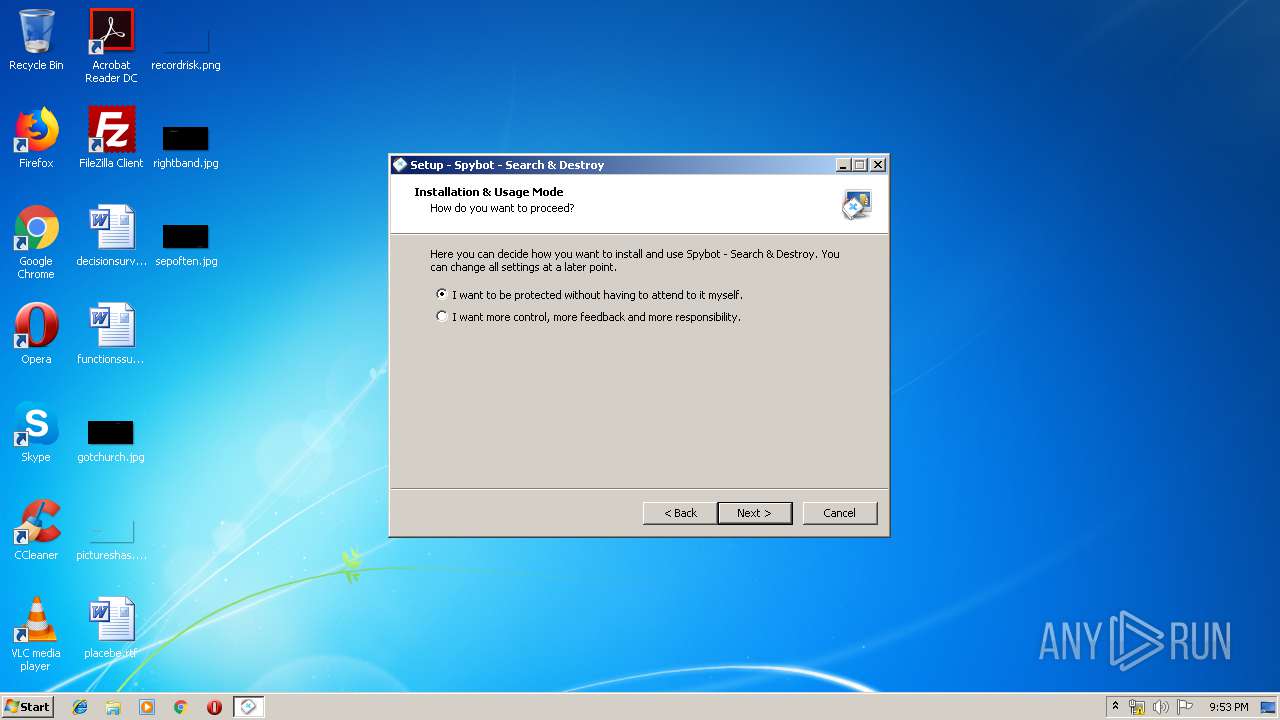
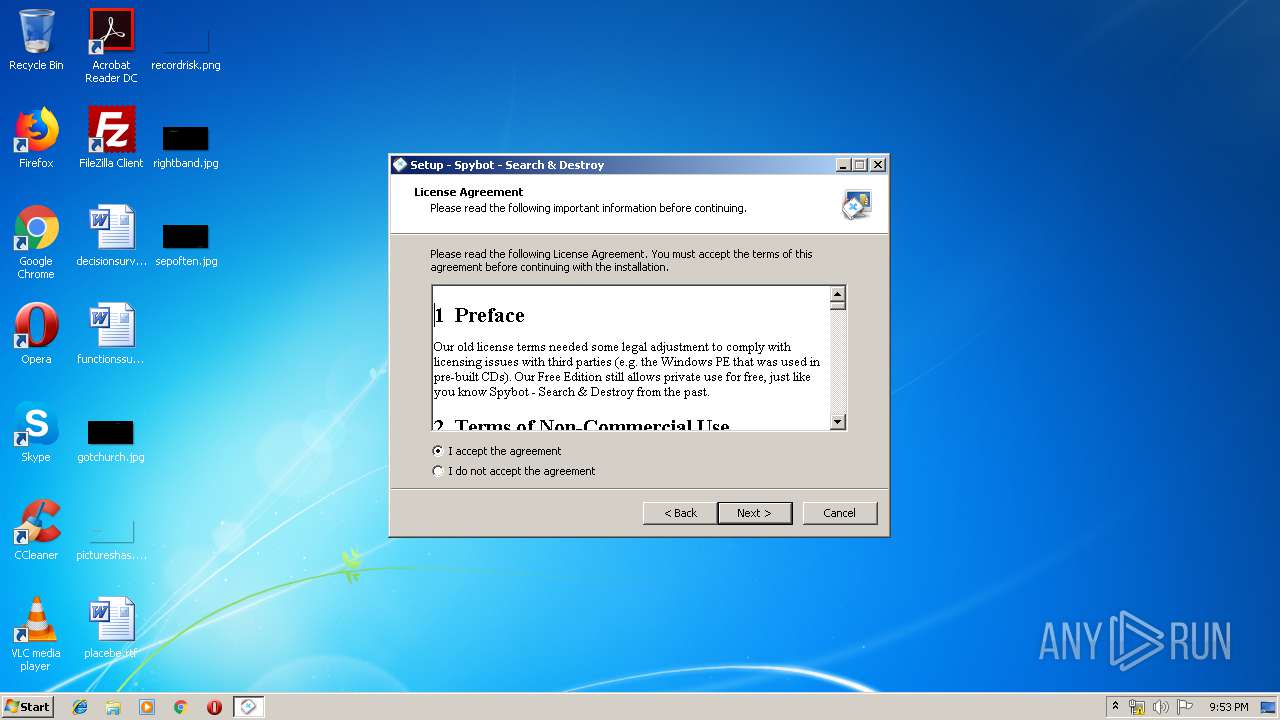
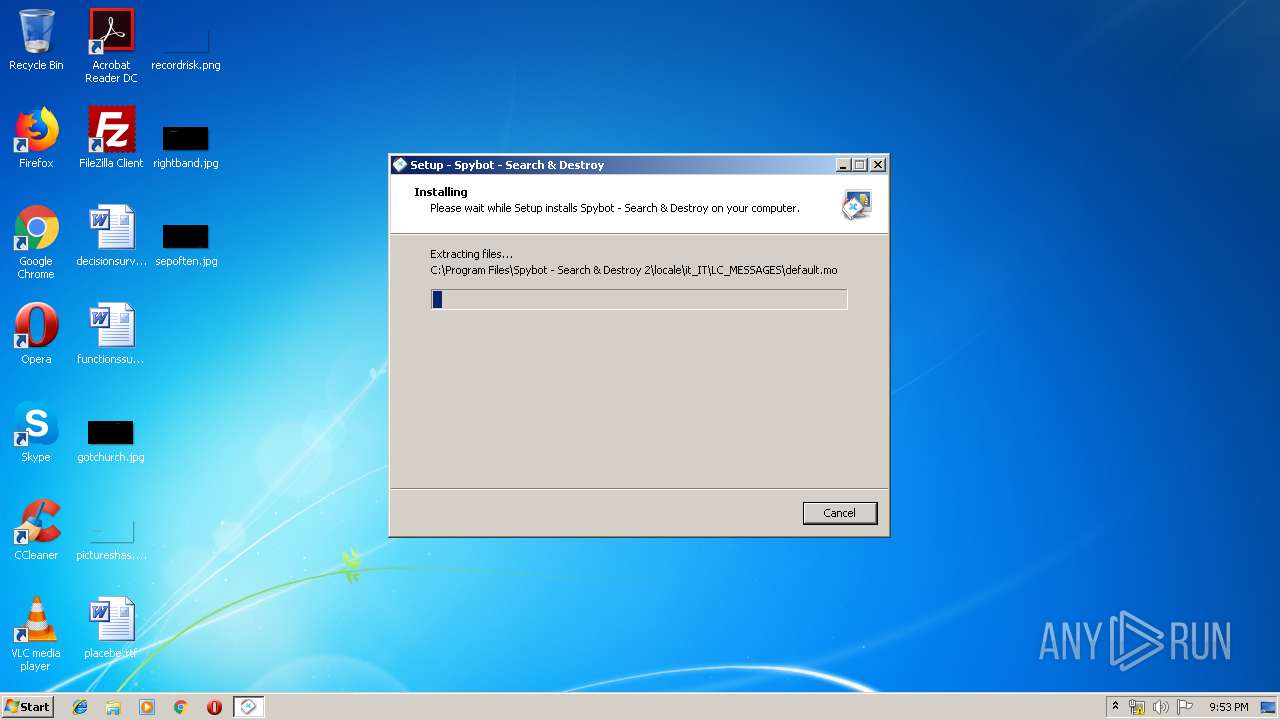
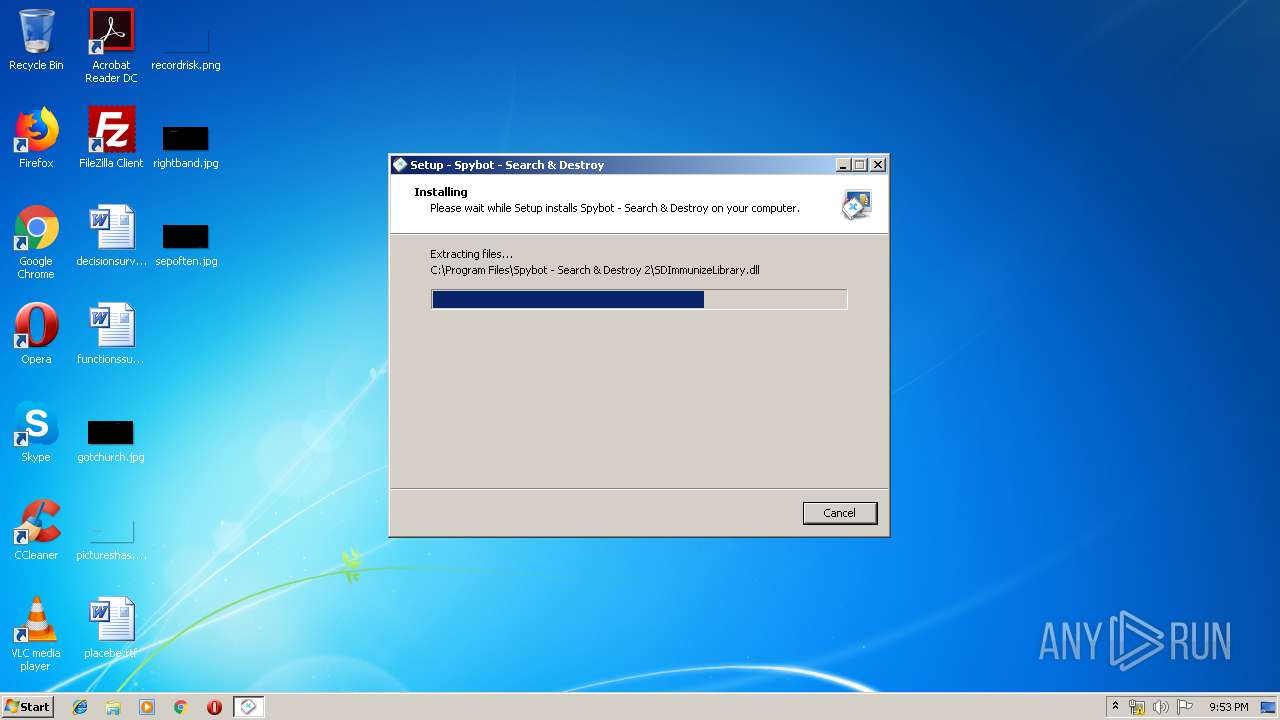
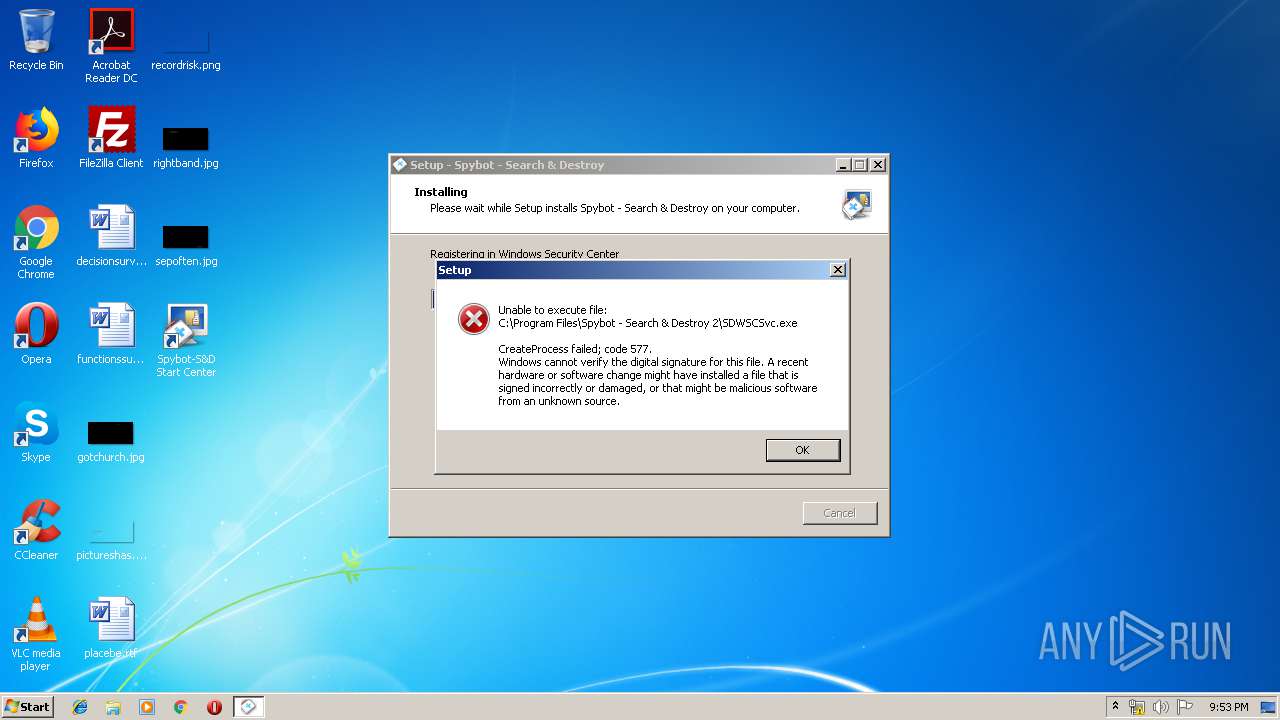
| URL: | https://download.fosshub.com/Protected/expiretime=1579347869;badurl=aHR0cHM6Ly93d3cuZm9zc2h1Yi5jb20vU3B5Ym90LVNlYXJjaC1hbmQtRGVzdHJveS5odG1s/e7c1900fbd40d08906375de5a7db3da72737adacd45ab8aad7f484bde1afdf18/5b7e63bf0c200816f7b798b8/5b7e64120c200816f7b798c4/spybotsd-2.7.64.0.exe |
| Full analysis: | https://app.any.run/tasks/89d29c9f-0366-4398-87f1-6326ef6e9ac2 |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2020, 21:51:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 47BD278F781D15C9BDF3234C658D1413 |
| SHA1: | 268757B3BD13472FB060202D3754D515AB40DA99 |
| SHA256: | 7EEA5F7A20B447A5D1F8E627B9F9C59CAE0445E7C1AD05FEDC1EB216763C55A1 |
| SSDEEP: | 6:2SKFfme4tX+StsV1BXsk71EL0AVf3znn0dA:2xZvG+hnXsbfzn0dA |
MALICIOUS
Application was dropped or rewritten from another process
- spybotsd-2.7.64.0.exe (PID: 2564)
- spybotsd-2.7.64.0.exe (PID: 4068)
- SDTray.exe (PID: 1932)
- SDFSSvc.exe (PID: 3888)
- SDUpdSvc.exe (PID: 2620)
- SDUpdate.exe (PID: 2264)
- SDUpdate.exe (PID: 3432)
- SDWelcome.exe (PID: 1608)
- SDImmunize.exe (PID: 2916)
- SDSettings.exe (PID: 4000)
- SDWelcome.exe (PID: 2068)
- SDImmunize.exe (PID: 2560)
- SDFiles.exe (PID: 4040)
- SDWelcome.exe (PID: 912)
- SDSettings.exe (PID: 3524)
- SDRootAlyzer.exe (PID: 2632)
- SDRootAlyzer.exe (PID: 1024)
- SDTools.exe (PID: 2676)
- SDTools.exe (PID: 2836)
Changes settings of System certificates
- svchost.exe (PID: 1080)
- SDTools.exe (PID: 2836)
Actions looks like stealing of personal data
- SDTray.exe (PID: 1932)
- SDUpdSvc.exe (PID: 2620)
- spybotsd-2.7.64.0.tmp (PID: 1856)
- SDUpdate.exe (PID: 2264)
- SDWelcome.exe (PID: 1608)
- SDUpdate.exe (PID: 3432)
- SDFSSvc.exe (PID: 3888)
- SDWelcome.exe (PID: 2068)
- SDImmunize.exe (PID: 2560)
- SDFiles.exe (PID: 4040)
- SDSettings.exe (PID: 4000)
- SDWelcome.exe (PID: 912)
- SDSettings.exe (PID: 3524)
- SDRootAlyzer.exe (PID: 1024)
- SDTools.exe (PID: 2836)
Changes the autorun value in the registry
- spybotsd-2.7.64.0.tmp (PID: 1856)
Loads dropped or rewritten executable
- SDTray.exe (PID: 1932)
- SDFSSvc.exe (PID: 3888)
- SDUpdSvc.exe (PID: 2620)
- SDUpdate.exe (PID: 2264)
- SDWelcome.exe (PID: 1608)
- SDUpdate.exe (PID: 3432)
- SDSettings.exe (PID: 4000)
- SDImmunize.exe (PID: 2560)
- SDFiles.exe (PID: 4040)
- SDSettings.exe (PID: 3524)
- SDRootAlyzer.exe (PID: 1024)
- SDWelcome.exe (PID: 912)
- SDTools.exe (PID: 2836)
Loads the Task Scheduler DLL interface
- spybotsd-2.7.64.0.tmp (PID: 1856)
Loads the Task Scheduler COM API
- spybotsd-2.7.64.0.tmp (PID: 1856)
Runs injected code in another process
- SDRootAlyzer.exe (PID: 1024)
Application was injected by another process
- smss.exe (PID: 264)
- services.exe (PID: 448)
- csrss.exe (PID: 404)
- lsass.exe (PID: 456)
- wininit.exe (PID: 396)
- lsm.exe (PID: 464)
- winlogon.exe (PID: 552)
- svchost.exe (PID: 608)
- svchost.exe (PID: 692)
- svchost.exe (PID: 796)
- svchost.exe (PID: 1080)
- svchost.exe (PID: 840)
- svchost.exe (PID: 864)
- svchost.exe (PID: 1000)
- csrss.exe (PID: 348)
- svchost.exe (PID: 1232)
- svchost.exe (PID: 1352)
- IMEDICTUPDATE.EXE (PID: 1384)
- qemu-ga.exe (PID: 1460)
- svchost.exe (PID: 1824)
- taskeng.exe (PID: 2032)
- dwm.exe (PID: 280)
- ctfmon.exe (PID: 708)
- SearchIndexer.exe (PID: 1872)
- wmiprvse.exe (PID: 3060)
- taskeng.exe (PID: 3080)
- windanr.exe (PID: 3716)
- spoolsv.exe (PID: 1204)
- explorer.exe (PID: 352)
SUSPICIOUS
Adds / modifies Windows certificates
- svchost.exe (PID: 1080)
- SDTools.exe (PID: 2836)
Starts Internet Explorer
- spybotsd-2.7.64.0.tmp (PID: 1856)
Executable content was dropped or overwritten
- spybotsd-2.7.64.0.exe (PID: 2564)
- spybotsd-2.7.64.0.tmp (PID: 1856)
- spybotsd-2.7.64.0.exe (PID: 4068)
- chrome.exe (PID: 1296)
Reads Windows owner or organization settings
- spybotsd-2.7.64.0.tmp (PID: 1856)
Reads the Windows organization settings
- spybotsd-2.7.64.0.tmp (PID: 1856)
Searches for installed software
- svchost.exe (PID: 840)
- SDTools.exe (PID: 2836)
Creates executable files which already exist in Windows
- spybotsd-2.7.64.0.tmp (PID: 1856)
Creates files in the Windows directory
- spybotsd-2.7.64.0.tmp (PID: 1856)
- svchost.exe (PID: 796)
- SDFSSvc.exe (PID: 3888)
- svchost.exe (PID: 864)
- SDUpdate.exe (PID: 2264)
Modifies the open verb of a shell class
- spybotsd-2.7.64.0.tmp (PID: 1856)
Creates or modifies windows services
- spybotsd-2.7.64.0.tmp (PID: 1856)
- SDTray.exe (PID: 1932)
- services.exe (PID: 448)
- SDFSSvc.exe (PID: 3888)
- SDUpdSvc.exe (PID: 2620)
Creates COM task schedule object
- spybotsd-2.7.64.0.tmp (PID: 1856)
Reads Environment values
- SDTray.exe (PID: 1932)
- SDFSSvc.exe (PID: 3888)
- SDUpdate.exe (PID: 2264)
- SDWelcome.exe (PID: 1608)
- SDUpdate.exe (PID: 3432)
- SDImmunize.exe (PID: 2560)
- SDSettings.exe (PID: 4000)
- SDWelcome.exe (PID: 2068)
- SDFiles.exe (PID: 4040)
- SDWelcome.exe (PID: 912)
- SDSettings.exe (PID: 3524)
- SDRootAlyzer.exe (PID: 1024)
- SDTools.exe (PID: 2836)
Creates files in the program directory
- SDTray.exe (PID: 1932)
- SDFSSvc.exe (PID: 3888)
- SDUpdSvc.exe (PID: 2620)
- SDImmunize.exe (PID: 2560)
- SDSettings.exe (PID: 4000)
- SDFiles.exe (PID: 4040)
- SDRootAlyzer.exe (PID: 1024)
Executed as Windows Service
- SDFSSvc.exe (PID: 3888)
- SDUpdSvc.exe (PID: 2620)
Removes files from Windows directory
- SDFSSvc.exe (PID: 3888)
- SDUpdate.exe (PID: 2264)
Executed via Task Scheduler
- SDUpdate.exe (PID: 2264)
Loads DLL from Mozilla Firefox
- csrss.exe (PID: 404)
Creates files in the user directory
- SDUpdate.exe (PID: 3432)
- SDImmunize.exe (PID: 2560)
- SDSettings.exe (PID: 4000)
- SDWelcome.exe (PID: 1608)
- SDWelcome.exe (PID: 912)
- SDSettings.exe (PID: 3524)
- SDFiles.exe (PID: 4040)
- SDRootAlyzer.exe (PID: 1024)
- SDTools.exe (PID: 2836)
Reads the cookies of Mozilla Firefox
- SDImmunize.exe (PID: 2560)
- SDSettings.exe (PID: 4000)
- SDSettings.exe (PID: 3524)
- SDTools.exe (PID: 2836)
Reads the cookies of Google Chrome
- SDSettings.exe (PID: 4000)
- SDSettings.exe (PID: 3524)
- SDTools.exe (PID: 2836)
INFO
Reads the hosts file
- chrome.exe (PID: 1296)
- chrome.exe (PID: 1324)
- SDFSSvc.exe (PID: 3888)
- SDImmunize.exe (PID: 2560)
- SDTools.exe (PID: 2836)
Application launched itself
- chrome.exe (PID: 1296)
Reads settings of System Certificates
- chrome.exe (PID: 1324)
- SDTools.exe (PID: 2836)
Application was dropped or rewritten from another process
- spybotsd-2.7.64.0.tmp (PID: 3008)
- spybotsd-2.7.64.0.tmp (PID: 1856)
Reads Internet Cache Settings
- chrome.exe (PID: 1296)
Changes internet zones settings
- iexplore.exe (PID: 1756)
Creates files in the user directory
- iexplore.exe (PID: 3224)
Reads internet explorer settings
- iexplore.exe (PID: 3224)
Loads dropped or rewritten executable
- spybotsd-2.7.64.0.tmp (PID: 1856)
Creates a software uninstall entry
- spybotsd-2.7.64.0.tmp (PID: 1856)
Creates files in the program directory
- spybotsd-2.7.64.0.tmp (PID: 1856)
Manual execution by user
- SDWelcome.exe (PID: 912)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
85
Monitored processes
62
Malicious processes
22
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 264 | \SystemRoot\System32\smss.exe | C:\Windows\System32\smss.exe | System | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Session Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=984,2362764329789182552,18086670521994703777,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=4343248990804479983 --mojo-platform-channel-handle=3508 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 280 | "C:\Windows\system32\Dwm.exe" | C:\Windows\System32\dwm.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Desktop Window Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 348 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 352 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 396 | wininit.exe | C:\Windows\System32\wininit.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Start-Up Application Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 404 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 448 | C:\Windows\system32\services.exe | C:\Windows\System32\services.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Services and Controller app Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 456 | C:\Windows\system32\lsass.exe | C:\Windows\System32\lsass.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Security Authority Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 464 | C:\Windows\system32\lsm.exe | C:\Windows\System32\lsm.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Session Manager Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
15 039
Read events
13 059
Write events
1 964
Delete events
16
Modification events
| (PID) Process: | (2608) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 1296-13223771528512750 |
Value: 259 | |||
| (PID) Process: | (1296) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1296) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1296) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1296) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1296) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1296) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1296) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1296) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1512-13197841398593750 |
Value: 0 | |||
| (PID) Process: | (1296) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
87
Suspicious files
122
Text files
739
Unknown types
79
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\9360c5cf-6dab-44cb-b70b-6ec8d0dbb804.tmp | — | |
MD5:— | SHA256:— | |||
| 1296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000020.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF39a63d.TMP | text | |
MD5:— | SHA256:— | |||
| 1296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 864 | svchost.exe | C:\Windows\appcompat\programs\RecentFileCache.bcf | txt | |
MD5:— | SHA256:— | |||
| 1296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF39a65c.TMP | text | |
MD5:— | SHA256:— | |||
| 1296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 1296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF39a68b.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
42
TCP/UDP connections
45
DNS requests
24
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1932 | SDTray.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEAb9%2BQOWA63qAArrPye7uhs%3D | US | der | 471 b | whitelisted |
1932 | SDTray.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAPxtOFfOoLxFJZ4s9fYR1w%3D | US | der | 471 b | whitelisted |
1932 | SDTray.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSFDxAmS5JEAmWxO0Ue9OdQ9z7zPAQUFQASKxOYspkH7R7for5XDStnAs0CEAMBmgI6%2F1ixa9bV6uYX8GY%3D | US | der | 471 b | whitelisted |
1932 | SDTray.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSPwl%2BrBFlJbvzLXU1bGW08VysJ2wQUj%2Bh%2B8G0yagAFI8dwl2o6kP9r6tQCEAs%2F0y45skewnIBAVx1q0vM%3D | US | der | 471 b | whitelisted |
3888 | SDFSSvc.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAPxtOFfOoLxFJZ4s9fYR1w%3D | US | der | 471 b | whitelisted |
3224 | iexplore.exe | GET | 301 | 167.114.117.64:80 | http://www.safer-networking.org/business/technician-edition/ | CA | html | 269 b | whitelisted |
3888 | SDFSSvc.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSFDxAmS5JEAmWxO0Ue9OdQ9z7zPAQUFQASKxOYspkH7R7for5XDStnAs0CEAMBmgI6%2F1ixa9bV6uYX8GY%3D | US | der | 471 b | whitelisted |
3432 | SDUpdate.exe | GET | 200 | 167.114.117.64:80 | http://updates1.safer-networking.org/spybotsd2.uid | CA | binary | 16.3 Kb | whitelisted |
3888 | SDFSSvc.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEAb9%2BQOWA63qAArrPye7uhs%3D | US | der | 471 b | whitelisted |
3888 | SDFSSvc.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSPwl%2BrBFlJbvzLXU1bGW08VysJ2wQUj%2Bh%2B8G0yagAFI8dwl2o6kP9r6tQCEAs%2F0y45skewnIBAVx1q0vM%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1324 | chrome.exe | 172.217.21.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1324 | chrome.exe | 205.234.175.175:443 | download.fosshub.com | CacheNetworks, Inc. | US | suspicious |
1324 | chrome.exe | 216.58.207.45:443 | accounts.google.com | Google Inc. | US | whitelisted |
1324 | chrome.exe | 216.239.36.117:443 | www.google.com | Google Inc. | US | whitelisted |
1324 | chrome.exe | 216.58.206.3:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
1324 | chrome.exe | 172.217.16.206:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
1296 | chrome.exe | 13.107.4.50:80 | www.download.windowsupdate.com | Microsoft Corporation | US | whitelisted |
3224 | iexplore.exe | 167.114.117.64:80 | www.safer-networking.org | OVH SAS | CA | unknown |
1856 | spybotsd-2.7.64.0.tmp | 167.114.117.64:80 | www.safer-networking.org | OVH SAS | CA | unknown |
3224 | iexplore.exe | 167.114.117.64:443 | www.safer-networking.org | OVH SAS | CA | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.fosshub.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
ssl.gstatic.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
www.safer-networking.org |
| whitelisted |
www.bing.com |
| whitelisted |
www.paypalobjects.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1856 | spybotsd-2.7.64.0.tmp | Misc activity | SUSPICIOUS [PTsecurity] HTTP GET method with http_client_body (RFC7231) |
Process | Message |
|---|---|
SDTray.exe | C:\Program Files\Spybot - Search & Destroy 2\SDLicense.dll: GetCodeSignatureIssuerPE: -1 |
SDTray.exe | TMemoryMappedFileBase: Handle created, |
SDTray.exe | TMemoryMappedFileBase: Handle created, |
SDTray.exe | TMemoryMappedFileBase: Handle created, |
SDTray.exe | TMemoryMappedFileBase: Handle created, |
SDFSSvc.exe | C:\Program Files\Spybot - Search & Destroy 2\SDLicense.dll: GetCodeSignatureIssuerPE: -1 |
SDFSSvc.exe | sbsdWebTestLists.AddListFromFile: missing file Includes\GoodBanks.sbs |
SDFSSvc.exe | sbsdWebTestLists.AddListFromFile: missing file Includes\GoodBankScripts.sbs |
SDFSSvc.exe | TSDScannerService.ServiceCreate.1 |
SDFSSvc.exe | TMemoryMappedFileBase: Handle created, |