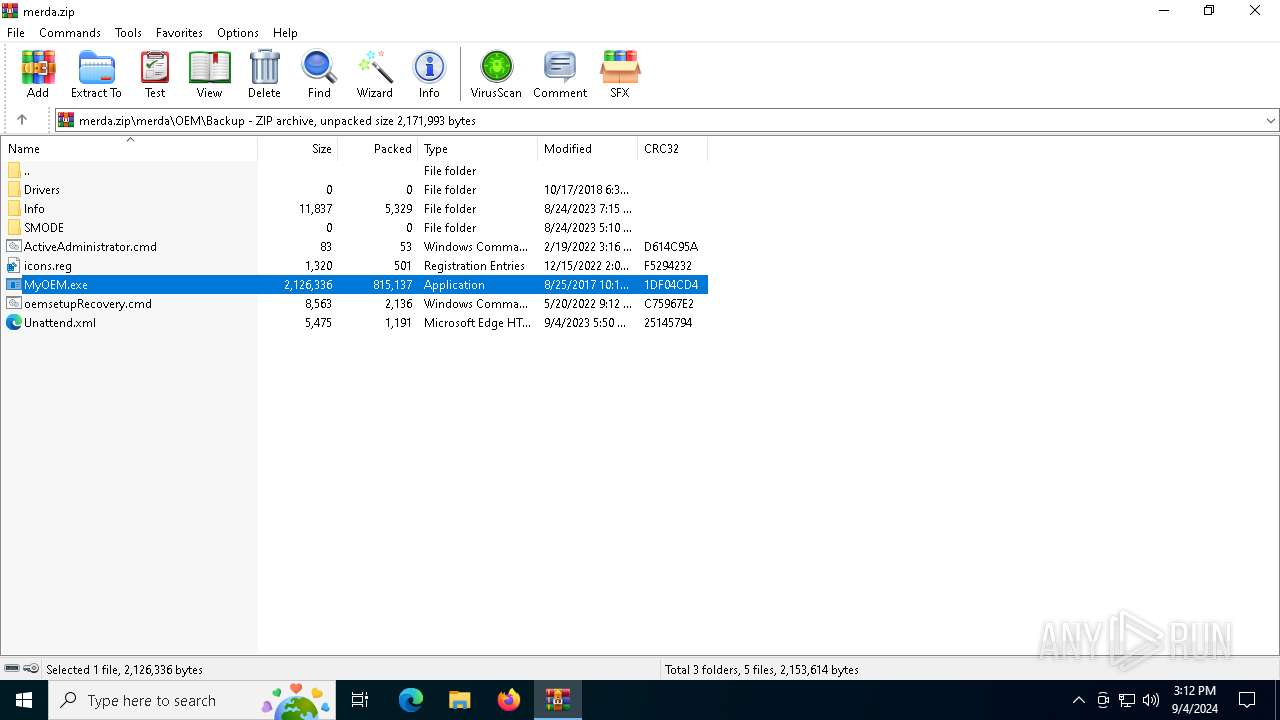
| File name: | merda.zip |
| Full analysis: | https://app.any.run/tasks/111877d6-1bfd-4f93-8305-1437c35c00d6 |
| Verdict: | Malicious activity |
| Analysis date: | September 04, 2024, 15:12:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 5C35BDB46B37348CBD8A2421928A40A4 |
| SHA1: | C7663F39292D919BEA4FB5EE87CC83E22F2FE8E5 |
| SHA256: | 7ED1D5BF09F8DAACC317F3CD8DFF1B155D3052F3457CDD5354A02EECBCD0D641 |
| SSDEEP: | 24576:+c6mCxIOhlaTfFz3iRL9G9rwFlzaqSbl5gPhUWcvdA0WKoBar6riRAsAKifuXMw+:+c6DxIOhlaTfFz3iRL9G9rwFlzaqSbla |
MALICIOUS
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 7152)
- net.exe (PID: 360)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5700)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 5476)
- WinRAR.exe (PID: 5700)
- cmd.exe (PID: 5464)
- cmd.exe (PID: 6364)
Application launched itself
- cmd.exe (PID: 5476)
- cmd.exe (PID: 5464)
- cmd.exe (PID: 6364)
Process checks presence of unattended files
- WinRAR.exe (PID: 5700)
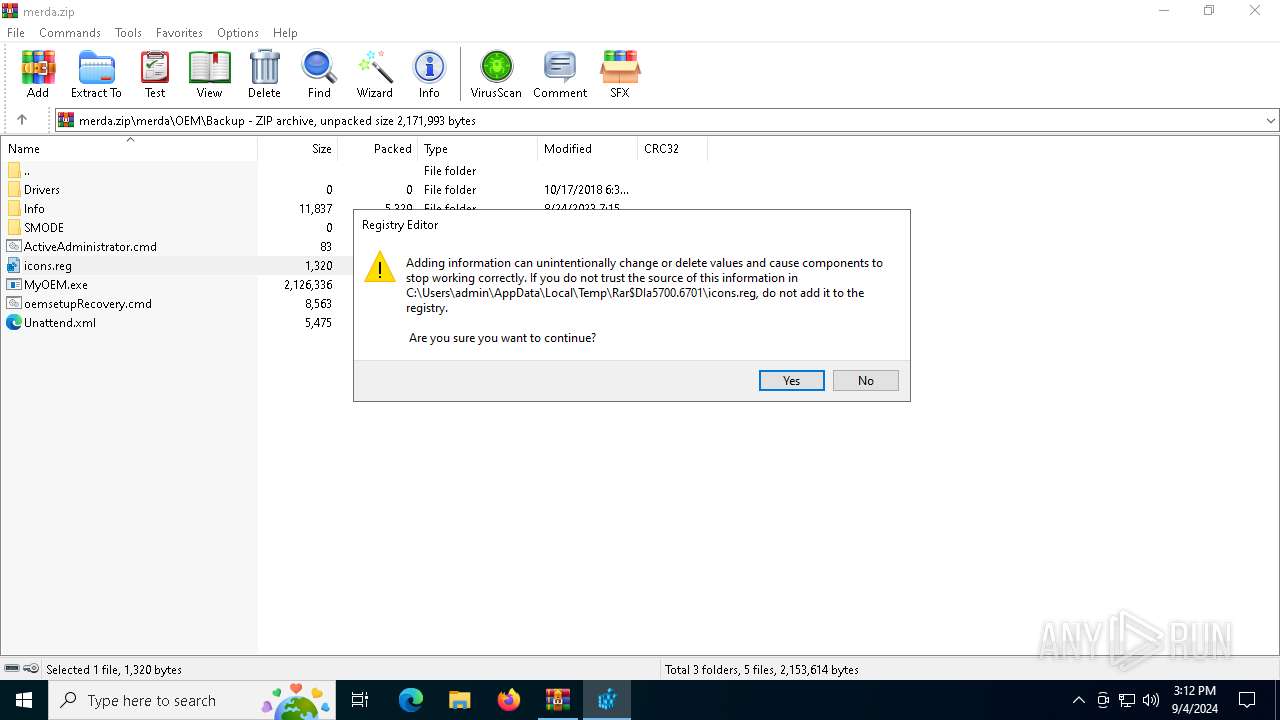
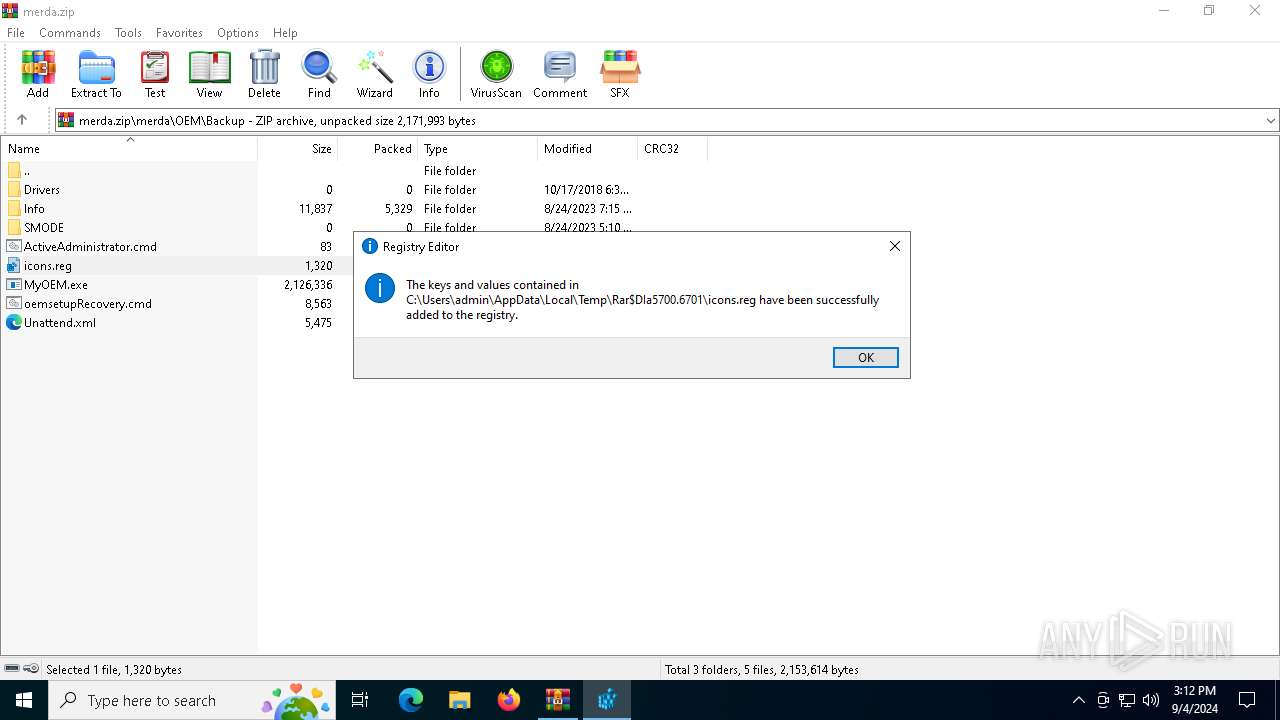
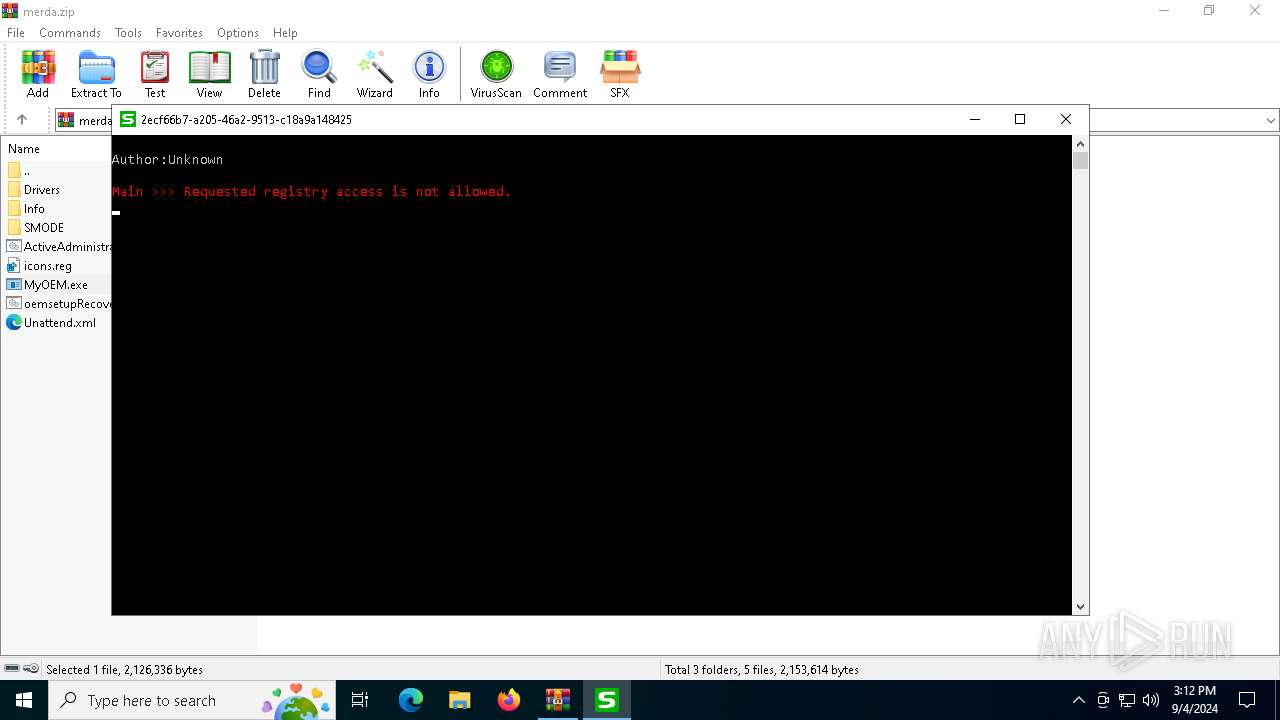
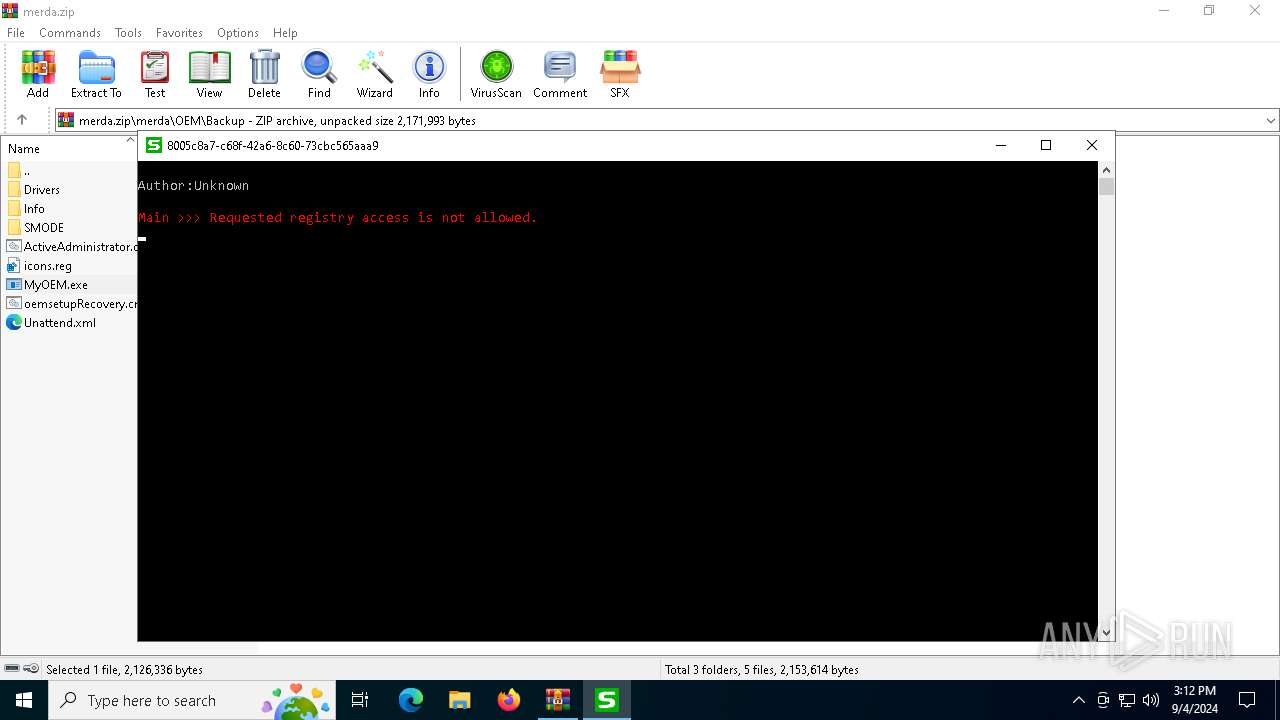
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5476)
Executing commands from ".cmd" file
- WinRAR.exe (PID: 5700)
Uses WMIC.EXE to obtain memory chip information
- cmd.exe (PID: 5464)
- cmd.exe (PID: 6364)
Starts application with an unusual extension
- cmd.exe (PID: 6364)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 5700)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 5700)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5700)
Checks supported languages
- MyOEM.exe (PID: 4732)
- MyOEM.exe (PID: 6312)
- tree.com (PID: 2520)
Reads the computer name
- MyOEM.exe (PID: 4732)
- MyOEM.exe (PID: 6312)
Reads the time zone
- net1.exe (PID: 1780)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 5044)
- WMIC.exe (PID: 1448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:09:04 17:10:06 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | merda/ |
Total processes
168
Monitored processes
45
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 360 | net user admin /active:yes | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1440 | "regedit.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa5700.6701\icons.reg" | C:\Windows\regedit.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1440 | C:\WINDOWS\system32\cmd.exe /c reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\RecoveryEnvironment" /v TargetOS | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1448 | wmic memorychip | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1780 | C:\WINDOWS\system32\net1 user admin /active:yes | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1992 | reg add HKEY_LOCAL_MACHINE\TEMPHIVE\Microsoft\Office\16.0\Common\OEM /v OOBE /t REG_SZ /d {9A9279D2-0358-4258-8D20-02ABD3159EF0} /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2520 | reg add "HKEY_LOCAL_MACHINE\TEMPHIVE\Microsoft\WindowsUpdate\Orchestrator\UScheduler_Oobe\OfficeClickToRun " /f /t REG_SZ /v "startArg" /d "/update SCHEDULEDTASK triggeringUI=AprilForkExpressLane skipMoratorium=true displayLevel=none" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2520 | tree "ECHO is on.\Recovery\OEM\Backup\Drivers" /f | C:\Windows\System32\tree.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Tree Walk Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2572 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | MyOEM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2588 | reg add HKEY_LOCAL_MACHINE\TEMPHIVE\Microsoft\Office\16.0\Common\OEM /v OOBEMode /t REG_SZ /d OEM /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 287
Read events
6 257
Write events
30
Delete events
0
Modification events
| (PID) Process: | (5700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\merda.zip | |||
| (PID) Process: | (5700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.reg\OpenWithProgids |
| Operation: | write | Name: | regfile |
Value: | |||
| (PID) Process: | (1440) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\NewStartPanel |
| Operation: | write | Name: | {031E4825-7B94-4dc3-B131-E946B44C8DD5} |
Value: 1 | |||
| (PID) Process: | (1440) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\NewStartPanel |
| Operation: | write | Name: | {208D2C60-3AEA-1069-A2D7-08002B30309D} |
Value: 1 | |||
| (PID) Process: | (1440) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\NewStartPanel |
| Operation: | write | Name: | {20D04FE0-3AEA-1069-A2D8-08002B30309D} |
Value: 0 | |||
Executable files
2
Suspicious files
7
Text files
47
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5476 | cmd.exe | C:\Users\admin\AppData\Local\Temp\oobe.log | text | |
MD5:76B5A17DFF67A80BFDD3AE66A139E197 | SHA256:854D8A5FEF6B7AE896A1D9BCF13315838871BC05BBEEDC78B1B209837C5D6626 | |||
| 5700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5700.7522\merda\OEM\Backup\oemsetupRecovery.cmd | text | |
MD5:FE725240A4BCE7639B7BE284A342B9B1 | SHA256:1EC3C0691256E8D357559A5DE8172CD36BFE2B213EF6F17911EE0CE3847A7518 | |||
| 5700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa5700.6701\icons.reg | text | |
MD5:E0A6BDDAA6CB63D556804E74CAE81BC6 | SHA256:CB6BBE77921317D8176D36CD297E7841C493C9992FB9646E3777C35687511E27 | |||
| 5700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5700.7522\merda\ReAgentOld.xml | xml | |
MD5:6DEE011EC54B6F3F80601A5D10BAAB7C | SHA256:EB2C3EE9D7B5E8487562E9F14EEEB869797AD3CED79DE047A8B4616C38361216 | |||
| 5700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5700.7522\merda\OEM\Backup\MyOEM.exe | executable | |
MD5:0277574F871917866B61041A1E39A626 | SHA256:A0974FB35140A83A566E5BFC168AE6922FE462C33A99E94C36CB6A4997DE386C | |||
| 5700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5700.7522\merda\OEM\Scripts\BeforeImageApply.cmd | text | |
MD5:228738777A5537FEBC78ACBF45A97F76 | SHA256:4915D2C27FDF13C6D358C98C6C19666B4EB0DABBCB46F4AA3D16BEB652DB312D | |||
| 5700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5700.7522\merda\OEM\Backup\Unattend.xml | xml | |
MD5:2C44B92FB9A6DEA94A1A8A43FA51625A | SHA256:8E63CE0B6DEF3BF5BEB3D9D68B1D38D2C54368F90B34A5702E87E70138412A53 | |||
| 5700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5700.7522\merda\OEM\ResetConfig.xml | xml | |
MD5:CF97373B4A1BA8A05829EF54A1D4F730 | SHA256:61F49E0740FD73E24963332846EDCDD10A9CE7B3CF99DFF22587273519AC5634 | |||
| 5700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5700.7522\merda\OEM\Scripts\BeforeImageApply.log | text | |
MD5:F347119069E0B6A8E408B35EA6EDF755 | SHA256:58711E605007A3CEC4C15D67982D961E9AFD431FCDE2E3B946B3008D26FE7BA3 | |||
| 5700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5700.7522\merda\OEM\Backup\Info\Default\1033\oobe.xml | xml | |
MD5:71C8466BFBE1B4BE0593D708958CA697 | SHA256:C05FF9F56C24069F06681889F3BEA158AB81236954BCFEF0ECF7016D6B3D9651 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
28
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6120 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6460 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6460 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6224 | svchost.exe | 52.183.220.149:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 52.183.220.149:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6120 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |