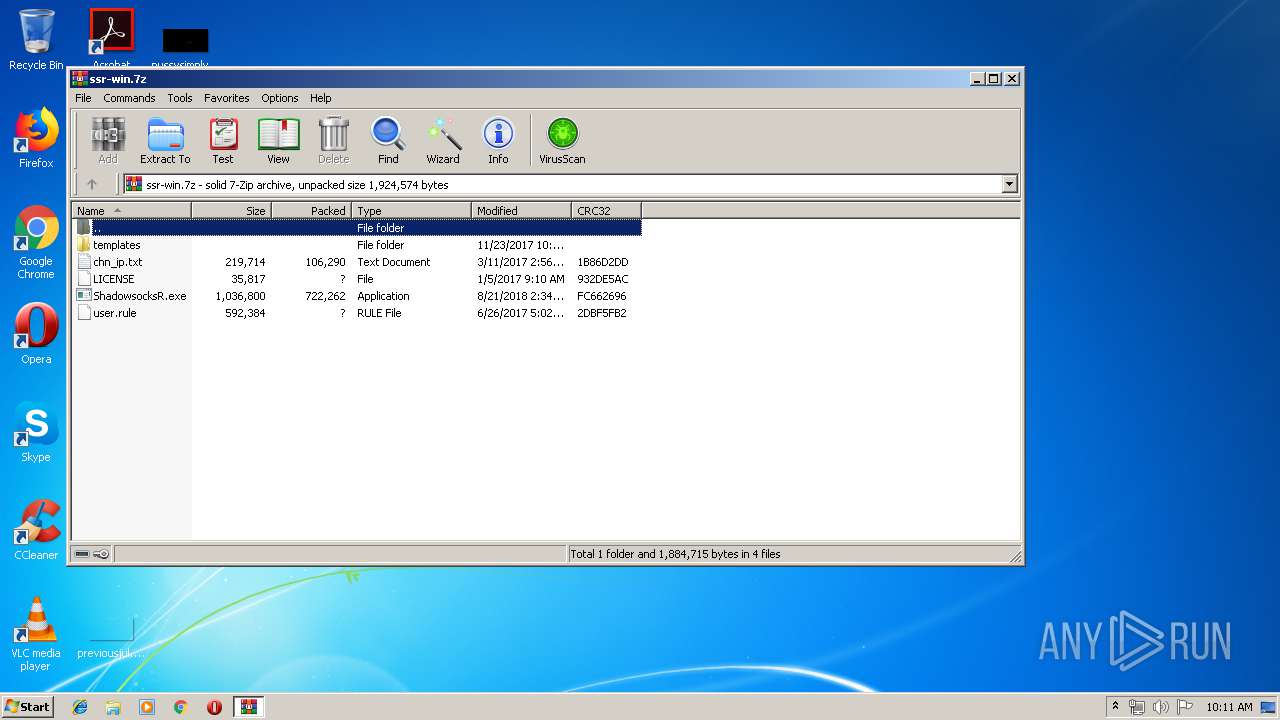
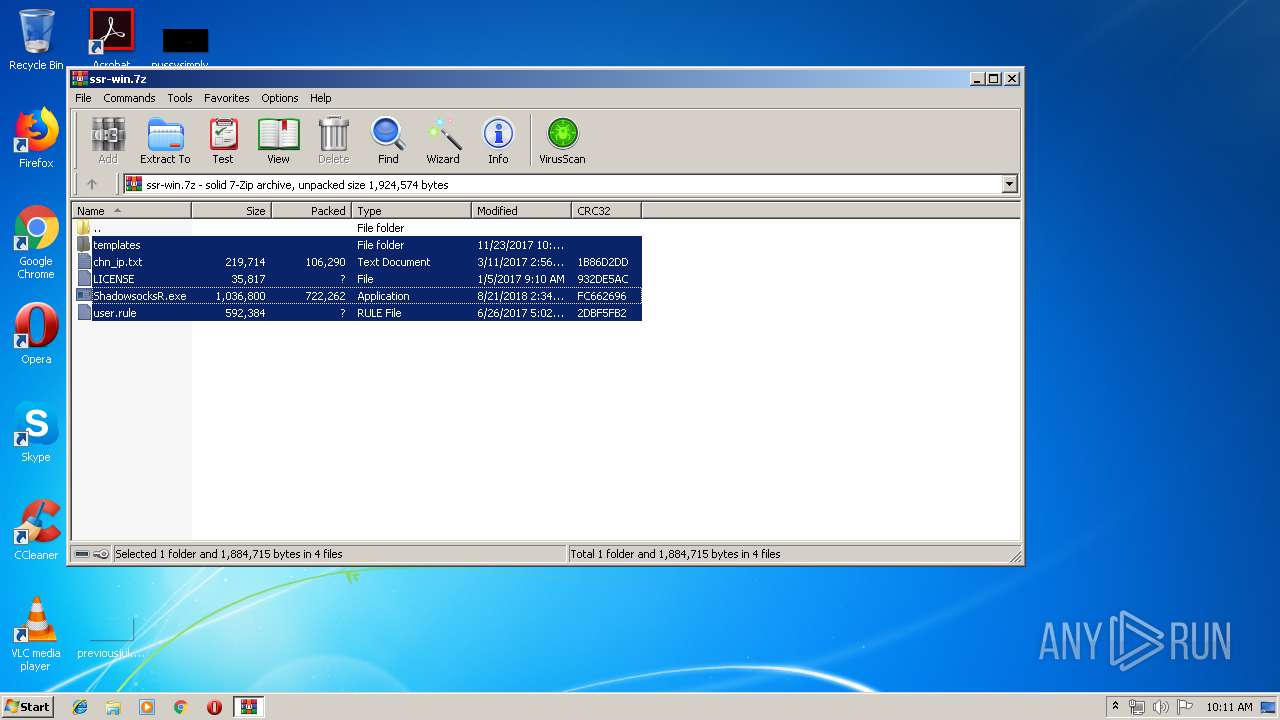
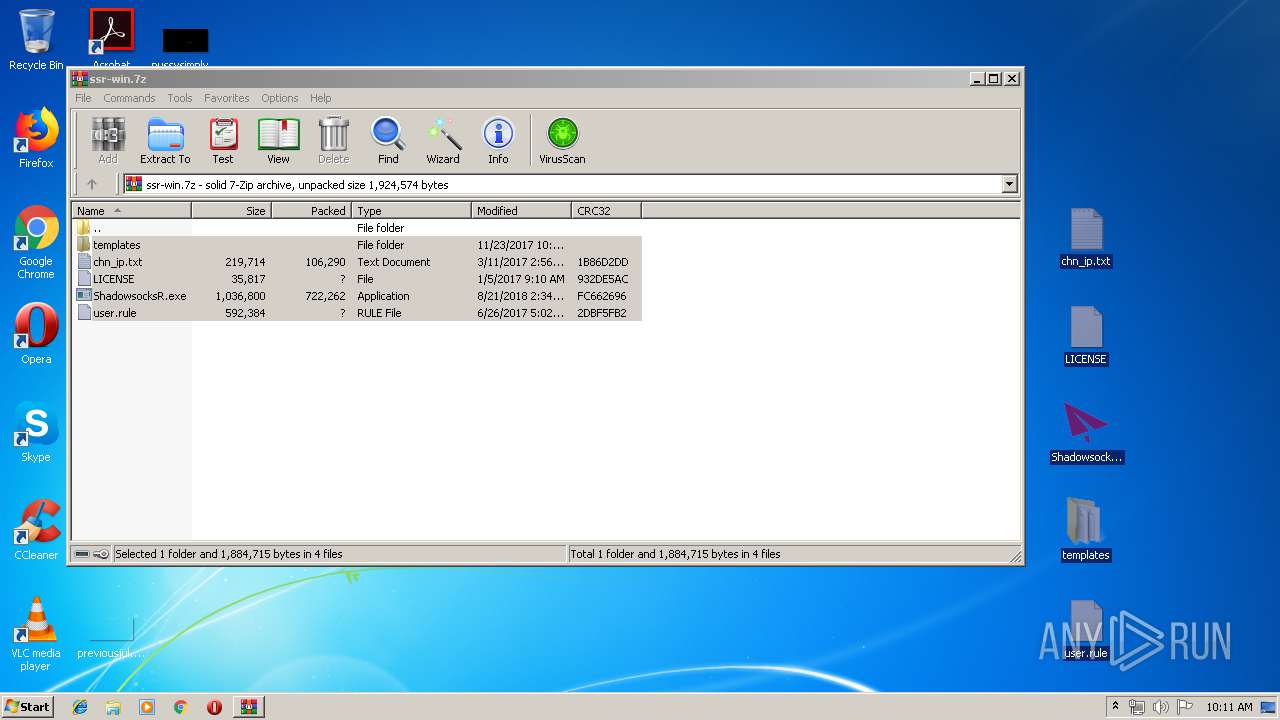
| File name: | ssr-win.7z |
| Full analysis: | https://app.any.run/tasks/7cf705f5-dfd4-4d44-b155-ea0a8c040099 |
| Verdict: | Malicious activity |
| Analysis date: | May 01, 2019, 09:11:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | FFC4C293F7679D4EAE66E1A79BEB7BAF |
| SHA1: | 3D676A8119C9A0576B0A44DEE5311AED457BE00D |
| SHA256: | 7EBC565B6F0E13AE9FCC4A2DC88F4E58C88D42D63067EEB4E69F96846CAB58C9 |
| SSDEEP: | 24576:eZUvfkShaoIWHVJqwjRnBoDjsoBesg0Rbi+7HA:eOnk/eHVr1BmsoIb0dU |
MALICIOUS
Application was dropped or rewritten from another process
- ShadowsocksR.exe (PID: 300)
- ShadowsocksR.exe (PID: 2688)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3180)
- ShadowsocksR.exe (PID: 2688)
SUSPICIOUS
Executable content was dropped or overwritten
- ShadowsocksR.exe (PID: 300)
Uses RUNDLL32.EXE to load library
- ShadowsocksR.exe (PID: 300)
Reads Internet Cache Settings
- rundll32.exe (PID: 1372)
- rundll32.exe (PID: 3372)
Reads Environment values
- ShadowsocksR.exe (PID: 300)
Creates files in the user directory
- rundll32.exe (PID: 1372)
INFO
Application launched itself
- iexplore.exe (PID: 2824)
Reads Internet Cache Settings
- iexplore.exe (PID: 1656)
Reads internet explorer settings
- iexplore.exe (PID: 1656)
Changes internet zones settings
- iexplore.exe (PID: 2824)
Creates files in the user directory
- iexplore.exe (PID: 2824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
43
Monitored processes
9
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Users\admin\Desktop\ShadowsocksR.exe" | C:\Users\admin\Desktop\ShadowsocksR.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: ShadowsocksR Exit code: 0 Version: 5.1.5.0 Modules
| |||||||||||||||
| 1372 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | ShadowsocksR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1656 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2824 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
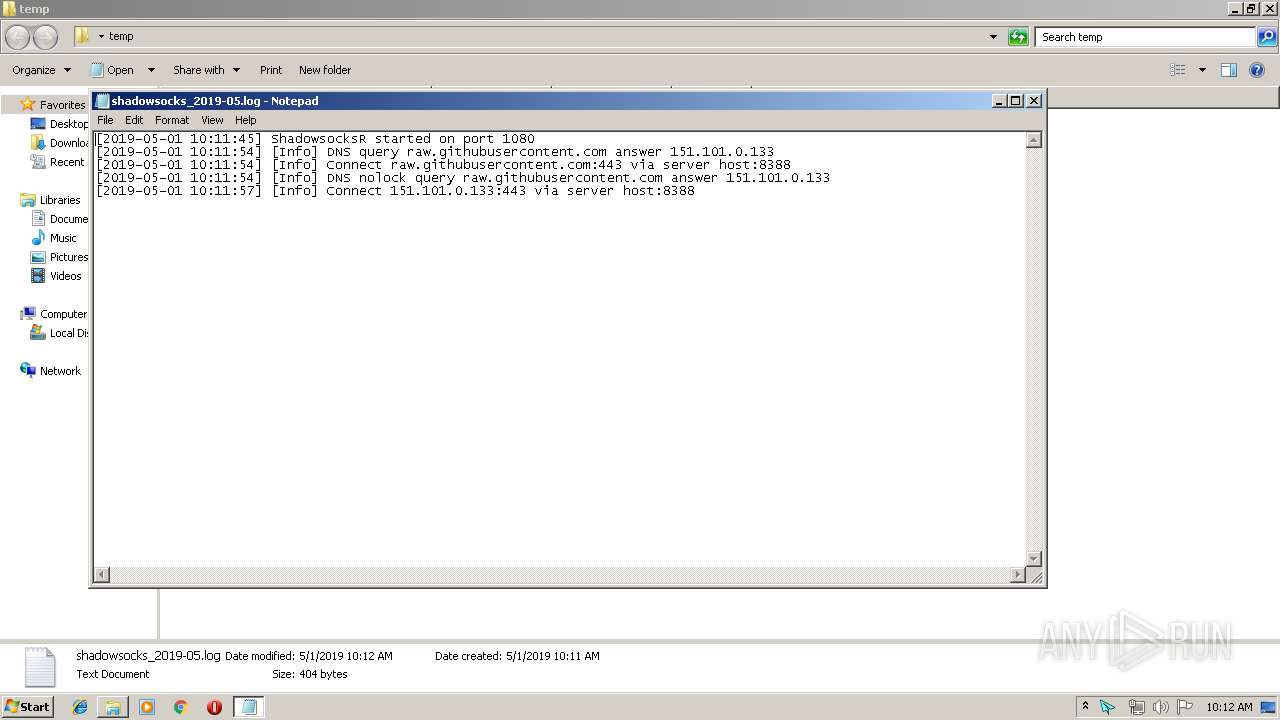
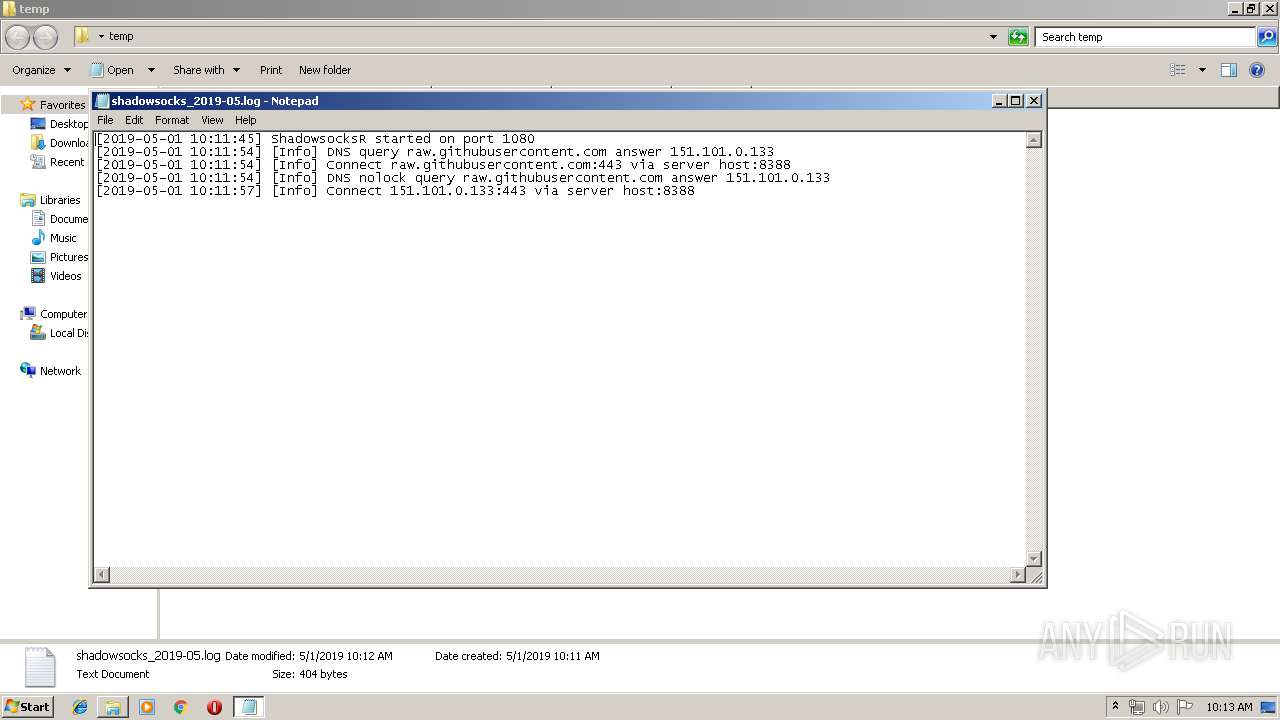
| 1784 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\temp\shadowsocks_2019-05.log | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2688 | "C:\Users\admin\Desktop\temp\ShadowsocksR.exe" "C:\Users\admin\Desktop\temp/privoxy.conf" | C:\Users\admin\Desktop\temp\ShadowsocksR.exe | ShadowsocksR.exe | ||||||||||||
User: admin Company: The Privoxy team - www.privoxy.org Integrity Level: MEDIUM Description: Privoxy Exit code: 0 Version: 3.0.26 Modules
| |||||||||||||||
| 2824 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3180 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3372 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | ShadowsocksR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3844 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\ssr-win.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
1 271
Read events
1 153
Write events
116
Delete events
2
Modification events
| (PID) Process: | (3844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3844) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\ssr-win.7z | |||
| (PID) Process: | (3844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3844) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
| (PID) Process: | (3180) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
2
Suspicious files
3
Text files
34
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3844.40020\ShadowsocksR.exe | — | |
MD5:— | SHA256:— | |||
| 3844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3844.40020\chn_ip.txt | text | |
MD5:BE3DF2201406E988F960135DDD0773A7 | SHA256:BB041B10A21756B980ABB69DD9FB0E850D6408C0D4E3B7272DF88CAFAEEB3686 | |||
| 3844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3844.40020\LICENSE | text | |
MD5:AB2DED24BAB23BD5E8E9C3EDBBC3BF44 | SHA256:B53E45FA09646E762CE929B756B323291551316BB06DFF2B67F3BF88B9EF0691 | |||
| 3844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3844.40020\templates\cgi-error-404 | text | |
MD5:CF20751C946B0E1C173807A599C418A4 | SHA256:7236B6834E383BCD792388454D3E0A244E3D1C4C165529BCBB21A03637C056E2 | |||
| 3844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3844.40020\templates\cgi-error-disabled | text | |
MD5:5CA98CFB63DC760CD51C6DDF77C7A1C7 | SHA256:2DF95BB3FD7747DD0DA8E3549484E27C6A92A0F332BC5CEB899CC83CDF5F5F94 | |||
| 3844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3844.40020\templates\cgi-error-parse | text | |
MD5:C531A638863FBD9150777CDA265685CF | SHA256:5951DDBF32F5108DA5F3B79E2F83F72E68286DAC34B3C8F2679BD3F645E14388 | |||
| 3844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3844.40020\templates\cgi-style.css | text | |
MD5:CB493C5CE7E5372BC8182E3B4819C77A | SHA256:423A735CB550B737E1C7A77294A65AB1A23BFBE2ECF41F7E4C4C906C13B4F71D | |||
| 3844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3844.40020\templates\cgi-error-file | text | |
MD5:F9B572A4705DD539D182AD0C2C3D8A0B | SHA256:EBAD87C26638EA5223E9B730E8E22D274C6B1FD59588FF4605CDE88E4CF7B6D4 | |||
| 3844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3844.40020\templates\edit-actions-add-url-form | text | |
MD5:5D6E45D606C955E0ECBD03A664586C10 | SHA256:12CB7DF9462FD88AC563AFA25F1421BC310DACB492FE32FBEA58909E80EB55E9 | |||
| 3844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3844.40020\templates\cgi-error-bad-param | text | |
MD5:2CEFA54A4C2FA0C8BC3FBA4953F01598 | SHA256:9C0028D654760B242884C661A8D912C886DAD323E5C49AFCC20CCBEFD04249CF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
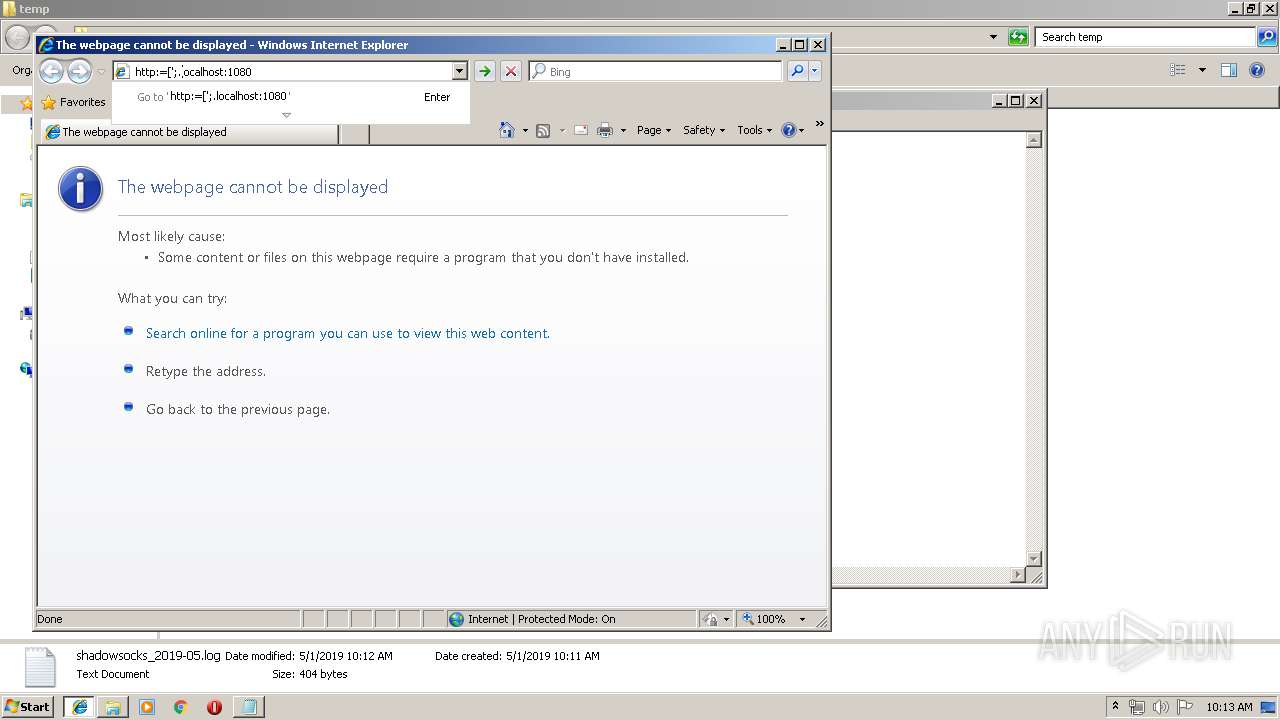
raw.githubusercontent.com |
| shared |
www.bing.com |
| whitelisted |