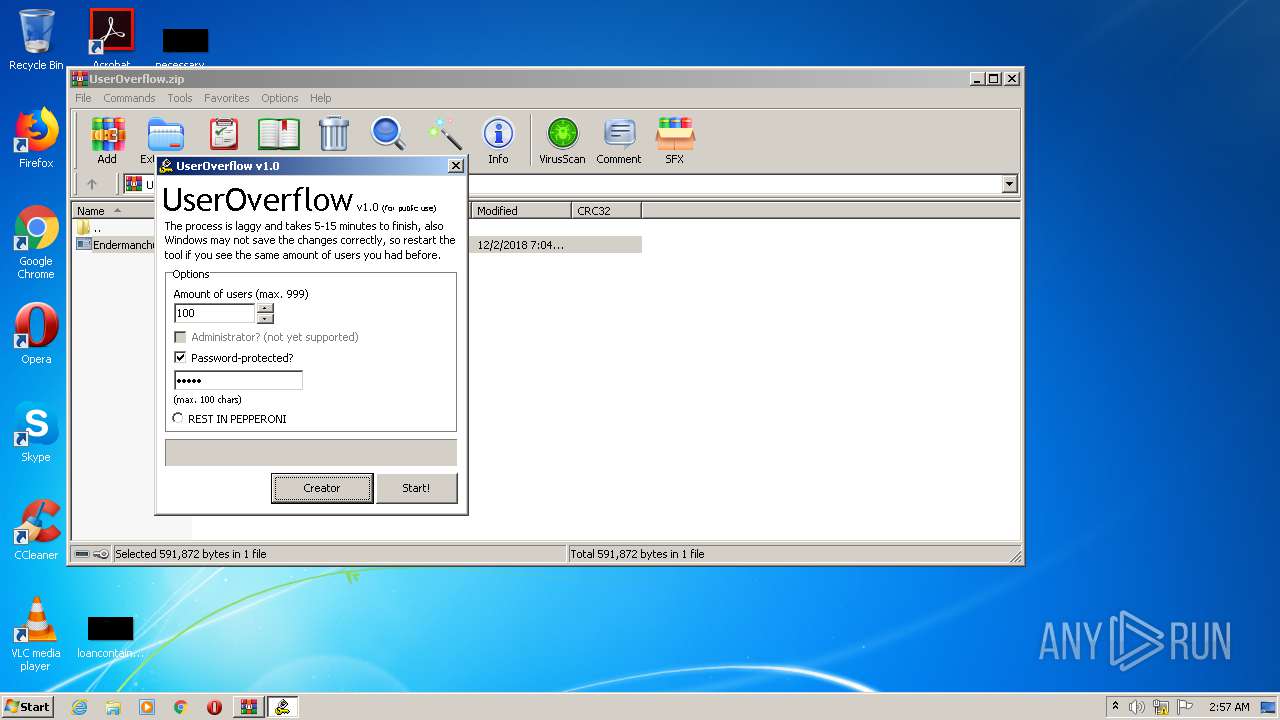
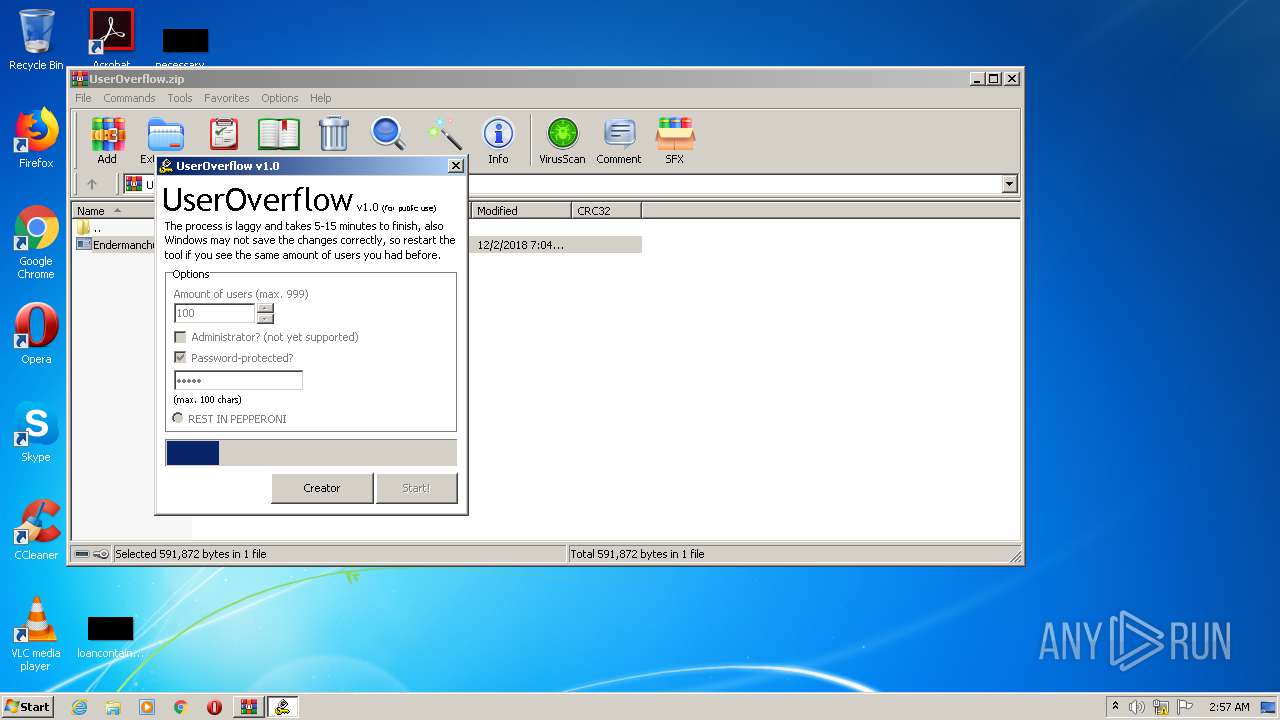
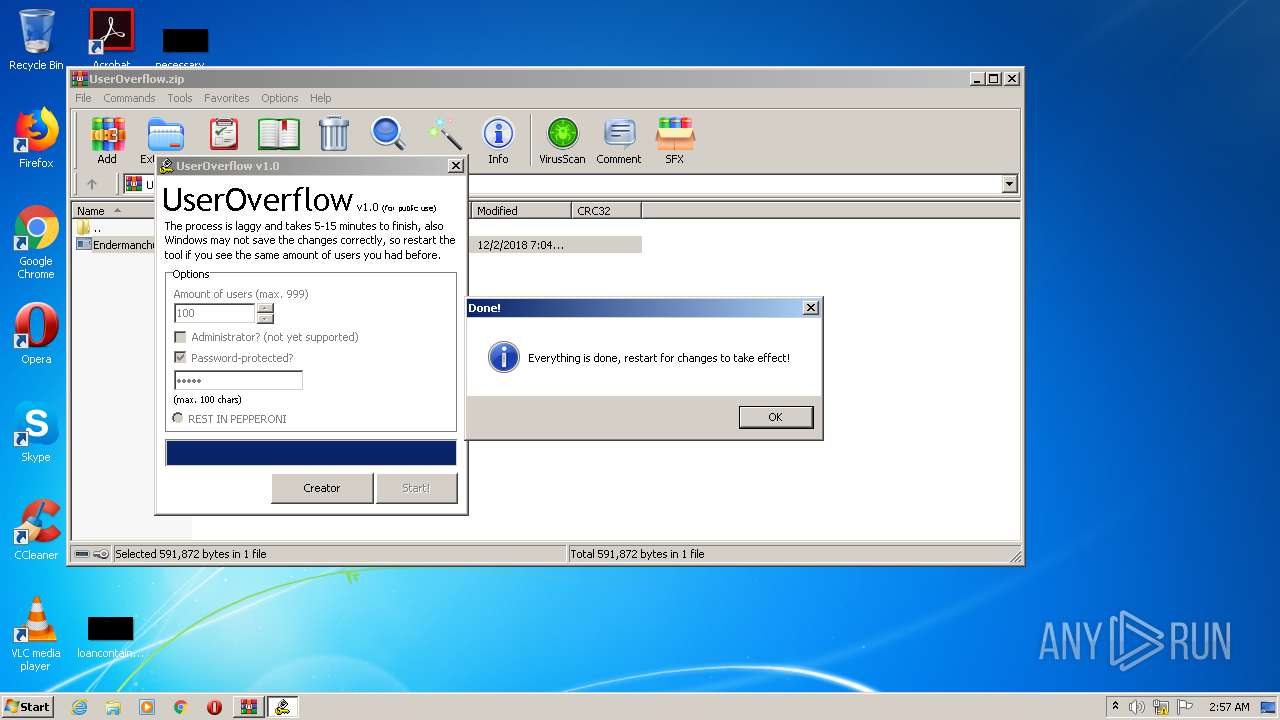
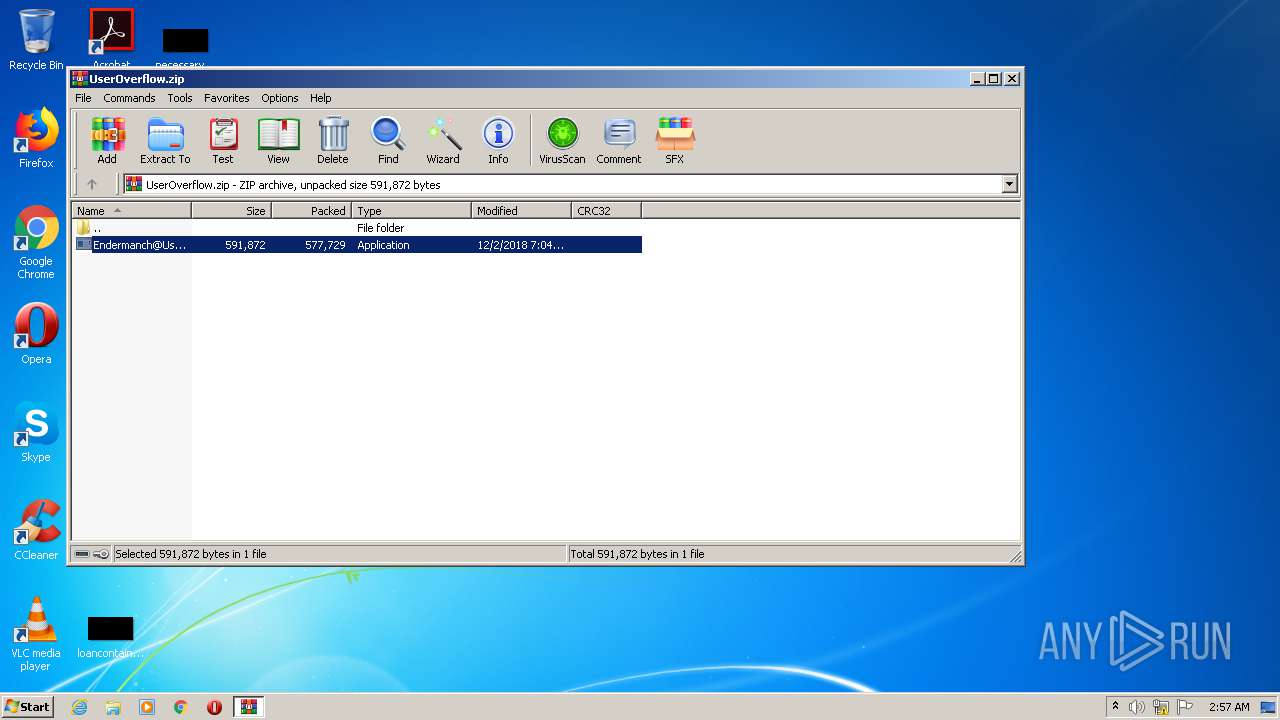
| File name: | UserOverflow.zip |
| Full analysis: | https://app.any.run/tasks/51ac5875-c56e-4ecf-acba-a381cb01e756 |
| Verdict: | Malicious activity |
| Analysis date: | November 30, 2020, 02:55:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
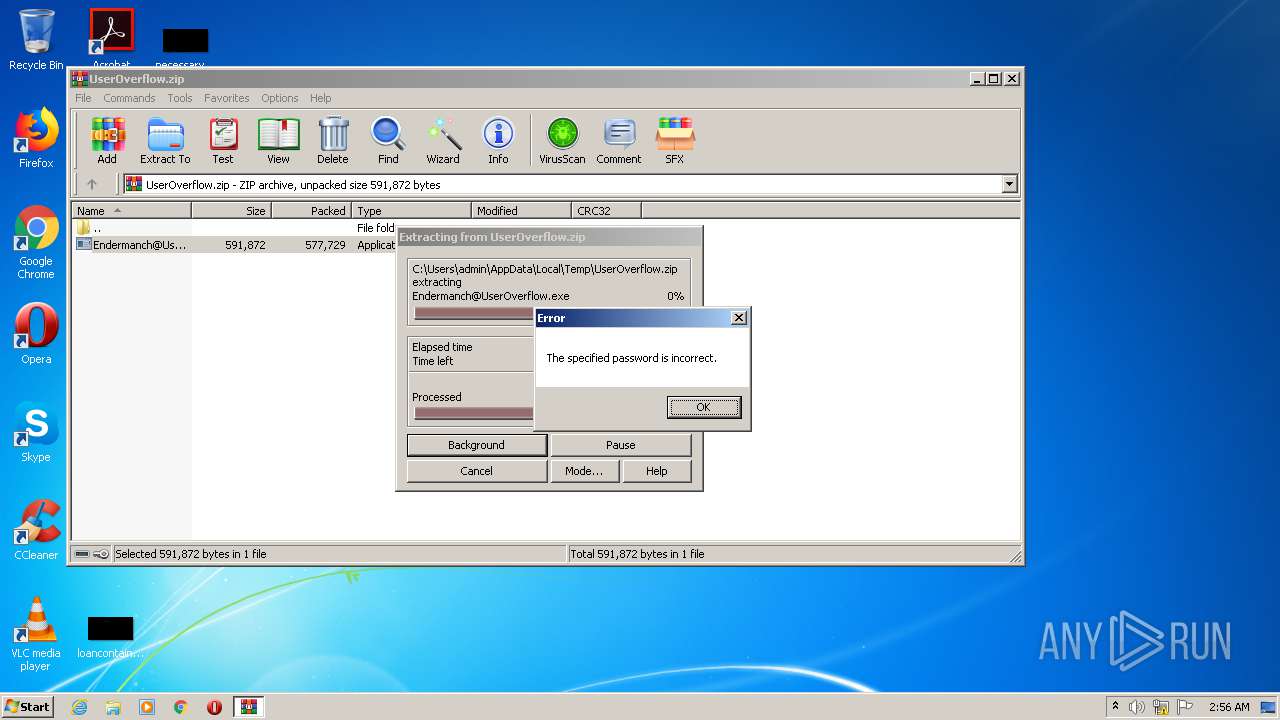
| File info: | Zip archive data, at least v5.1 to extract |
| MD5: | E63EB8701ABEAFC17E18807F996A2C4B |
| SHA1: | E11387F6C188416F43E1A72F4FFDD759F4E43E54 |
| SHA256: | 7EAFD43C18F9613D762567CB5E00D58DF71208D6B94C23D634DAEC42170E0D6C |
| SSDEEP: | 12288:3vKCI7fDejRGO3Aq/GYakzIbNmUywpTMwWEMnPz4:fKCI7mLANFkGtMwlyL4 |
MALICIOUS
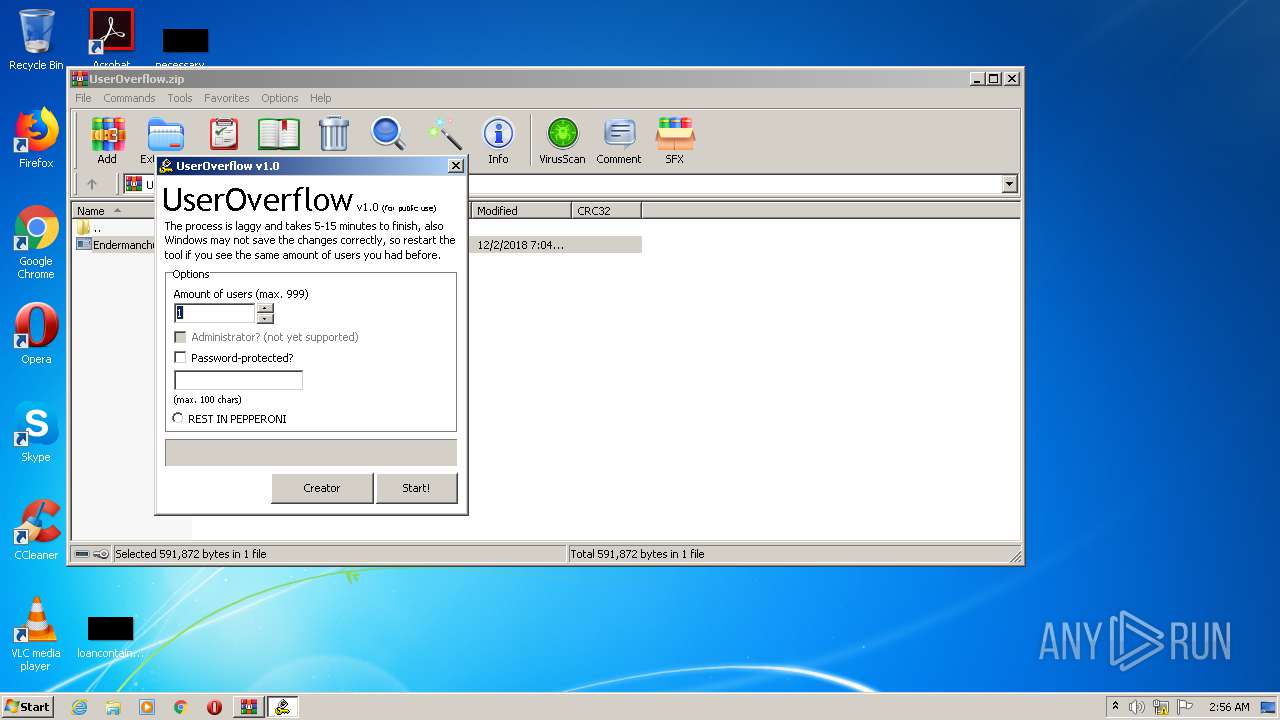
Application was dropped or rewritten from another process
- Endermanch@UserOverflow.exe (PID: 1744)
Starts NET.EXE to view/add/change user profiles
- Endermanch@UserOverflow.exe (PID: 1744)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1724)
Executed via COM
- DllHost.exe (PID: 2064)
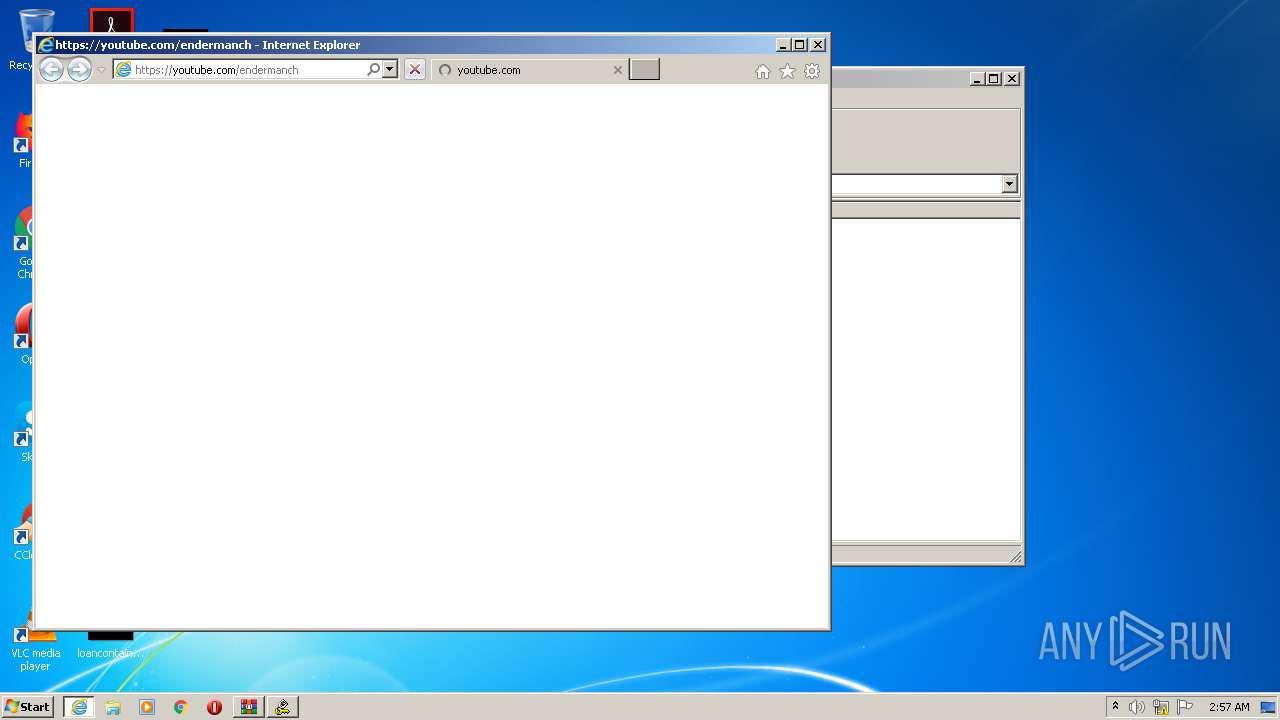
Starts Internet Explorer
- Endermanch@UserOverflow.exe (PID: 1744)
INFO
Application launched itself
- iexplore.exe (PID: 3672)
Changes internet zones settings
- iexplore.exe (PID: 3672)
Reads settings of System Certificates
- iexplore.exe (PID: 2952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2018:12:02 22:04:29 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 577729 |
| ZipUncompressedSize: | 591872 |
| ZipFileName: | Endermanch@UserOverflow.exe |
Total processes
342
Monitored processes
205
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 256 | C:\Windows\system32\net1 user user99 death /add | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 272 | C:\Windows\system32\net1 user user20 death /add | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 276 | C:\Windows\system32\net1 user user74 death /add | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 532 | C:\Windows\system32\net1 user user61 death /add | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 548 | "C:\Windows\System32\net.exe" user user16 death /add | C:\Windows\System32\net.exe | — | Endermanch@UserOverflow.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 564 | "C:\Windows\System32\net.exe" user user94 death /add | C:\Windows\System32\net.exe | — | Endermanch@UserOverflow.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 568 | "C:\Windows\System32\net.exe" user user52 death /add | C:\Windows\System32\net.exe | — | Endermanch@UserOverflow.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 592 | "C:\Windows\System32\net.exe" user user34 death /add | C:\Windows\System32\net.exe | — | Endermanch@UserOverflow.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 684 | "C:\Windows\System32\net.exe" user user6 death /add | C:\Windows\System32\net.exe | — | Endermanch@UserOverflow.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 752 | C:\Windows\system32\net1 user user41 death /add | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
959
Read events
898
Write events
60
Delete events
1
Modification events
| (PID) Process: | (1724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1724) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\UserOverflow.zip | |||
| (PID) Process: | (1724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
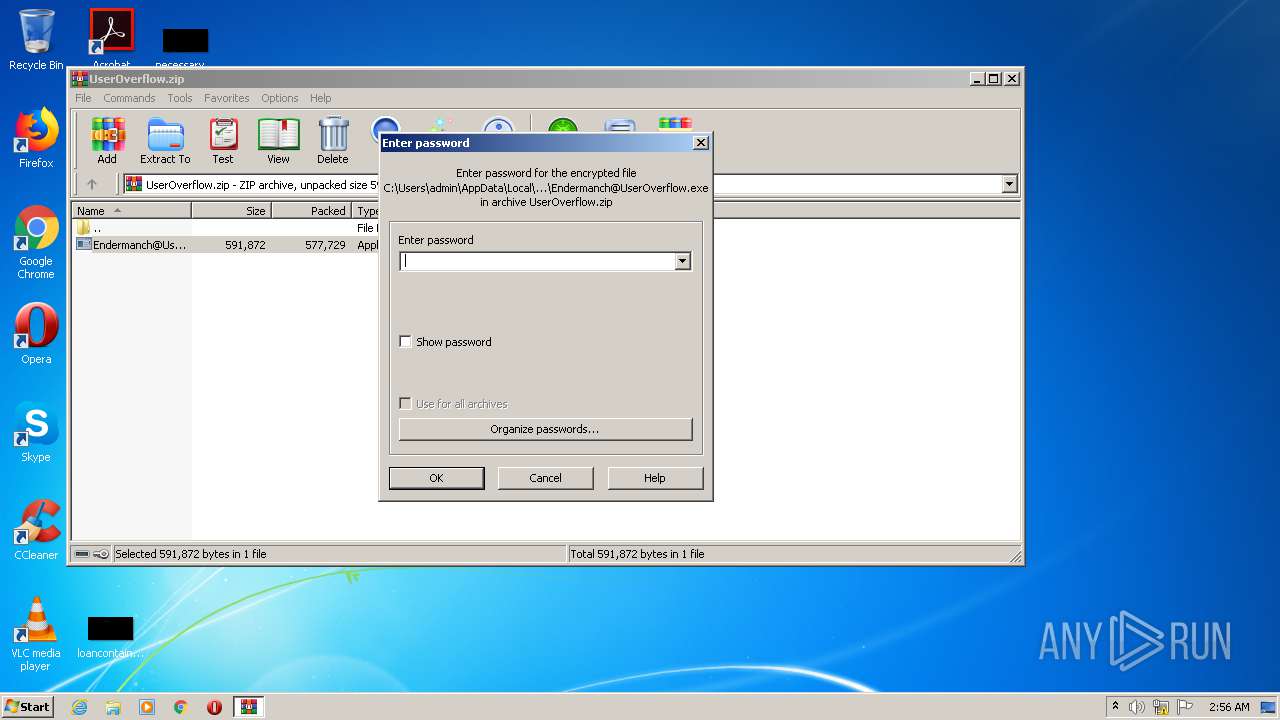
| (PID) Process: | (1724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
Executable files
1
Suspicious files
10
Text files
0
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab2AA3.tmp | — | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar2AA4.tmp | — | |
MD5:— | SHA256:— | |||
| 3672 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFAE7F9DB9AFCC2313.TMP | — | |
MD5:— | SHA256:— | |||
| 3672 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFA9D94A04317A0012.TMP | — | |
MD5:— | SHA256:— | |||
| 3672 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF0895F8333AFB122F.TMP | — | |
MD5:— | SHA256:— | |||
| 3672 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF4BE6593B18847989.TMP | — | |
MD5:— | SHA256:— | |||
| 3672 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{BCFFF6AD-32B7-11EB-8E7A-12A9866C77DE}.dat | — | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CC197601BE0898B7B0FCC91FA15D8A69_7C1C45A209E1552633930171FD75B297 | binary | |
MD5:— | SHA256:— | |||
| 3672 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{BCFFF6AF-32B7-11EB-8E7A-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CC197601BE0898B7B0FCC91FA15D8A69_7C1C45A209E1552633930171FD75B297 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
7
DNS requests
5
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1528 | werfault.exe | GET | — | 13.88.21.125:80 | http://watson.microsoft.com/StageOne/Generic/AppHangB1/dllhost_exe/6_1_7600_16385/4a5bc6b7/2a4b/0.htm?LCID=1033&OS=6.1.7601.2.00010100.1.0.48.17514&SM=DELL&SPN=DELL&BV=DELL&MID=3ADE2C42-4AB9-49B7-B142-BE9AEEA69063 | US | — | — | whitelisted |
2952 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQD76E8xQFZstgIAAAAAgFWS | US | der | 472 b | whitelisted |
2952 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
2952 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQD76E8xQFZstgIAAAAAgFWS | US | der | 472 b | whitelisted |
2952 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2952 | iexplore.exe | 64.233.168.91:443 | youtube.com | Google Inc. | US | unknown |
2952 | iexplore.exe | 172.217.18.99:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2952 | iexplore.exe | 64.233.169.190:443 | www.youtube.com | Google Inc. | US | unknown |
1528 | werfault.exe | 13.88.21.125:80 | watson.microsoft.com | Microsoft Corporation | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
youtube.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.youtube.com |
| whitelisted |
watson.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1528 | werfault.exe | Potential Corporate Privacy Violation | ET POLICY Application Crash Report Sent to Microsoft |
1528 | werfault.exe | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |