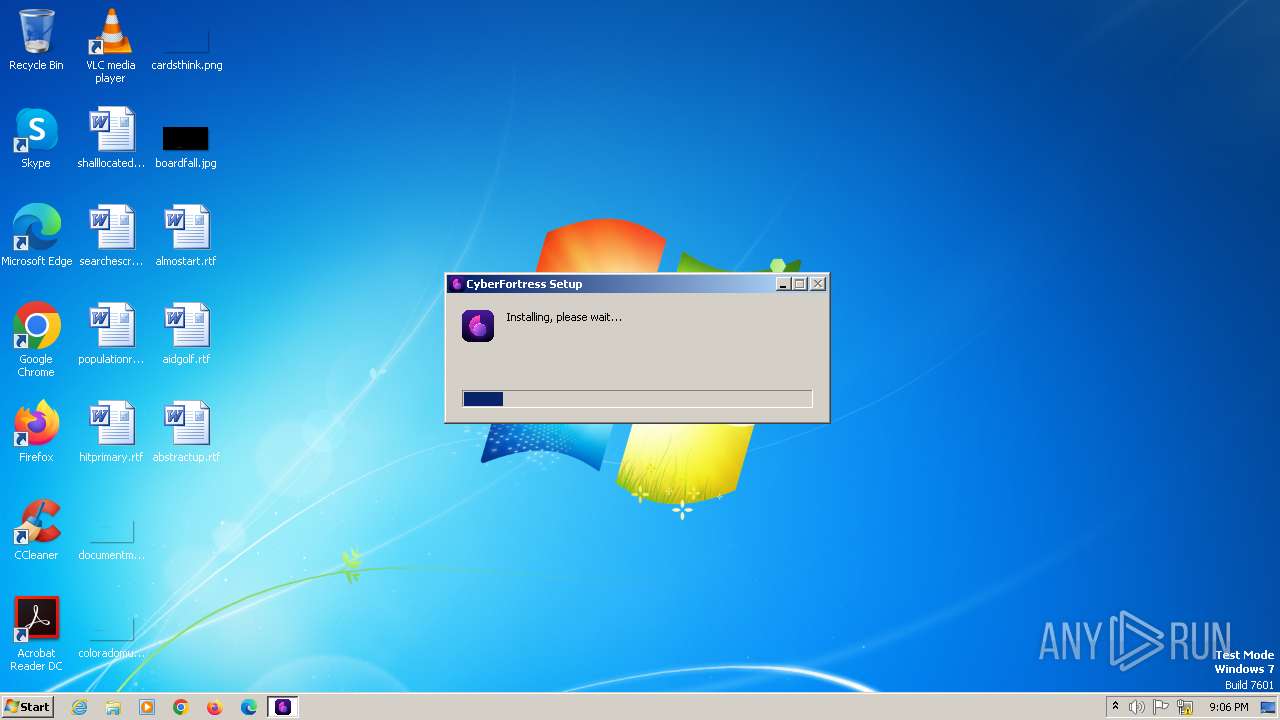
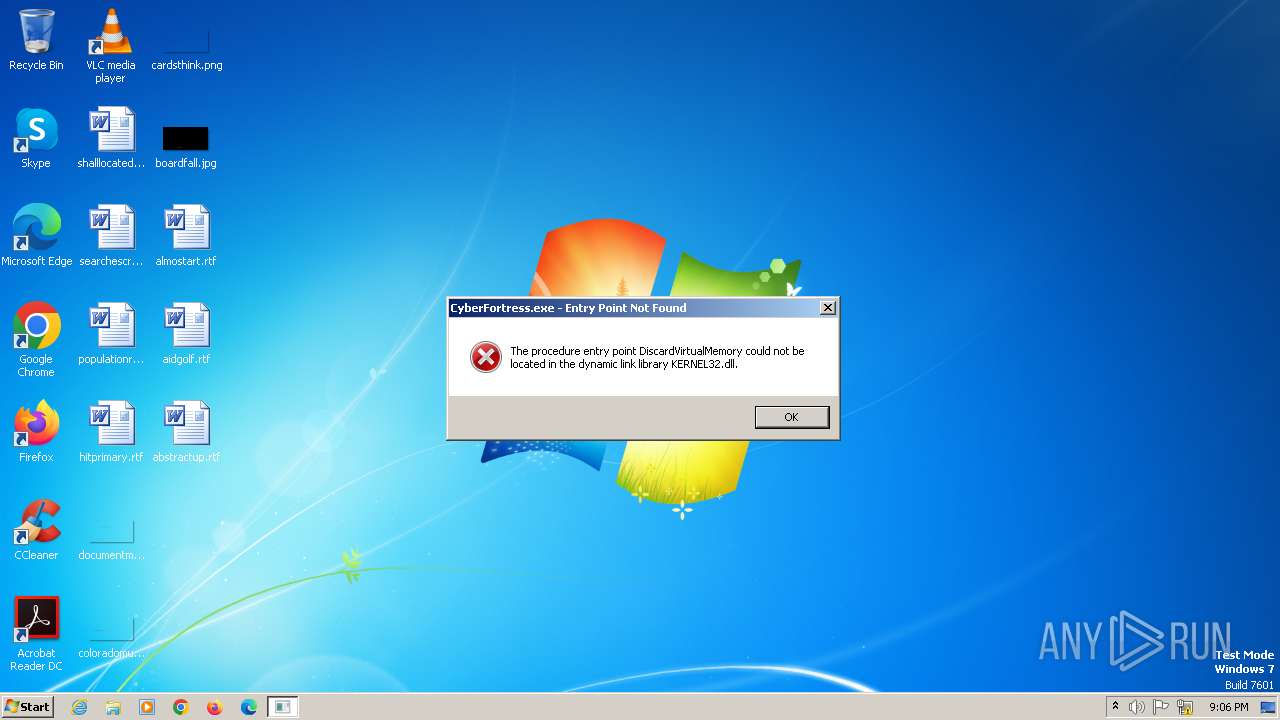
| File name: | CyberFortress.exe |
| Full analysis: | https://app.any.run/tasks/4afa8741-4f1a-495f-85ed-7b94a74e2116 |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2023, 21:05:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 94937A227802E1002F098C4263C84C2C |
| SHA1: | A7BFDE36EA5A1445C9D1237D9D426E33F5D0C843 |
| SHA256: | 7EA7B1AA5E1C6C951FABD35CF26F221399C9AEB36FF557B278D070957A559AFA |
| SSDEEP: | 786432:h/t93a1oyQENY6StCBQ2JbyX/ruD+Q52dFx:h193auyQkY6SQWmbyX/ruD++2Tx |
MALICIOUS
Drops the executable file immediately after the start
- CyberFortress.exe (PID: 1940)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- CyberFortress.exe (PID: 1940)
The process creates files with name similar to system file names
- CyberFortress.exe (PID: 1940)
Drops 7-zip archiver for unpacking
- CyberFortress.exe (PID: 1940)
Process drops legitimate windows executable
- CyberFortress.exe (PID: 1940)
INFO
Checks supported languages
- CyberFortress.exe (PID: 1940)
Reads the computer name
- CyberFortress.exe (PID: 1940)
Create files in a temporary directory
- CyberFortress.exe (PID: 1940)
Creates files or folders in the user directory
- CyberFortress.exe (PID: 1940)
Reads the machine GUID from the registry
- CyberFortress.exe (PID: 1940)
Manual execution by a user
- CyberFortress.exe (PID: 3028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:15 23:26:14+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 473088 |
| UninitializedDataSize: | 16384 |
| EntryPoint: | 0x338f |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.12.0 |
| ProductVersionNumber: | 1.0.12.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileDescription: | Stay safe with cyberfortr |
| FileVersion: | 1.0.12 |
| LegalCopyright: | CyberFortress © 2023 |
| ProductName: | CyberFortress |
| ProductVersion: | 1.0.12 |
Total processes
33
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1940 | "C:\Users\admin\AppData\Local\Temp\CyberFortress.exe" | C:\Users\admin\AppData\Local\Temp\CyberFortress.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Stay safe with cyberfortr Exit code: 0 Version: 1.0.12 Modules
| |||||||||||||||
| 3028 | "C:\Users\admin\AppData\Local\Programs\CyberFortress\CyberFortress.exe" | C:\Users\admin\AppData\Local\Programs\CyberFortress\CyberFortress.exe | — | explorer.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: MEDIUM Description: CyberFortress Exit code: 0 Version: 1.0.12 Modules
| |||||||||||||||
Total events
718
Read events
718
Write events
0
Delete events
0
Modification events
Executable files
19
Suspicious files
120
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1940 | CyberFortress.exe | C:\Users\admin\AppData\Local\Temp\nsw7C01.tmp\app-64.7z | — | |
MD5:— | SHA256:— | |||
| 1940 | CyberFortress.exe | C:\Users\admin\AppData\Local\Temp\nsw7C01.tmp\7z-out\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 1940 | CyberFortress.exe | C:\Users\admin\AppData\Local\Temp\nsw7C01.tmp\7z-out\LICENSES.chromium.html | — | |
MD5:— | SHA256:— | |||
| 1940 | CyberFortress.exe | C:\Users\admin\AppData\Local\Temp\nsw7C01.tmp\StdUtils.dll | executable | |
MD5:C6A6E03F77C313B267498515488C5740 | SHA256:B72E9013A6204E9F01076DC38DABBF30870D44DFC66962ADBF73619D4331601E | |||
| 1940 | CyberFortress.exe | C:\Users\admin\AppData\Local\Temp\nsw7C01.tmp\7z-out\locales\af.pak | binary | |
MD5:B293CC5EA7DB02649BD7D386B8FA0624 | SHA256:7BB75ADEF02D28819F1BD3B42FA46ED56D6DFBEAE072341997B09B8C1F52D8DC | |||
| 1940 | CyberFortress.exe | C:\Users\admin\AppData\Local\Temp\nsw7C01.tmp\installerHeaderico.ico | image | |
MD5:452D4A7F047DA341DADE3165E38EE9A1 | SHA256:0EB6E56EA5686D964D1B085B43E08EE8CE1C38A62CB7F830C45A8F888763B24C | |||
| 1940 | CyberFortress.exe | C:\Users\admin\AppData\Local\Temp\nsw7C01.tmp\7z-out\chrome_100_percent.pak | binary | |
MD5:443C58245EEB233D319ABF7150B99C31 | SHA256:99CA6947D97DF212E45782BBD5D97BFB42112872E1C42BAB4209CEEDF66DC760 | |||
| 1940 | CyberFortress.exe | C:\Users\admin\AppData\Local\Temp\nsw7C01.tmp\7z-out\chrome_200_percent.pak | binary | |
MD5:81B5B74FE16C7C81870F539D5C263397 | SHA256:CB4FD141A5C4D188A3ECB203E9D41A3AFCA648724160E212289ADCAC666FBFF4 | |||
| 1940 | CyberFortress.exe | C:\Users\admin\AppData\Local\Temp\nsw7C01.tmp\System.dll | executable | |
MD5:0D7AD4F45DC6F5AA87F606D0331C6901 | SHA256:3EB38AE99653A7DBC724132EE240F6E5C4AF4BFE7C01D31D23FAF373F9F2EACA | |||
| 1940 | CyberFortress.exe | C:\Users\admin\AppData\Local\Temp\nsw7C01.tmp\7z-out\locales\el.pak | binary | |
MD5:7F92F844B9D8BEF68DADBDB85A084BD6 | SHA256:87F0A26D73FEA2EBB5017A95E937E08D7C347BAECBE93514C1B866C1E28DEA32 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1956 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
324 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |