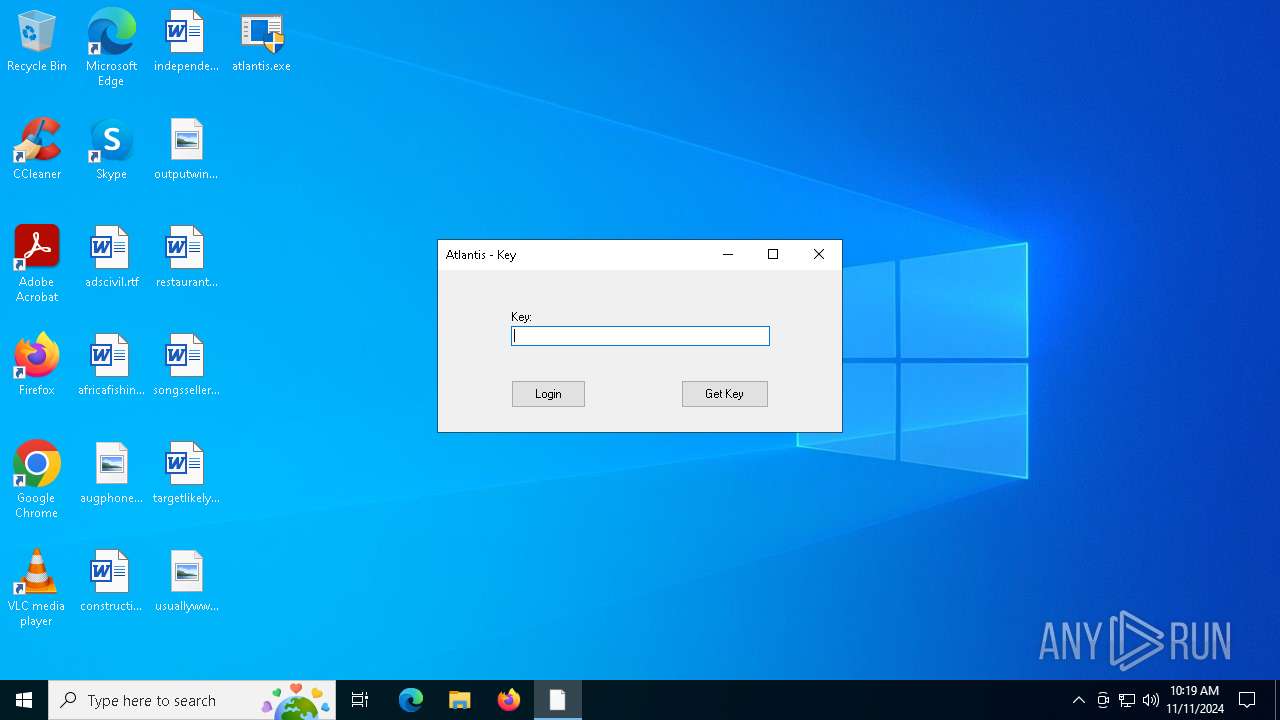
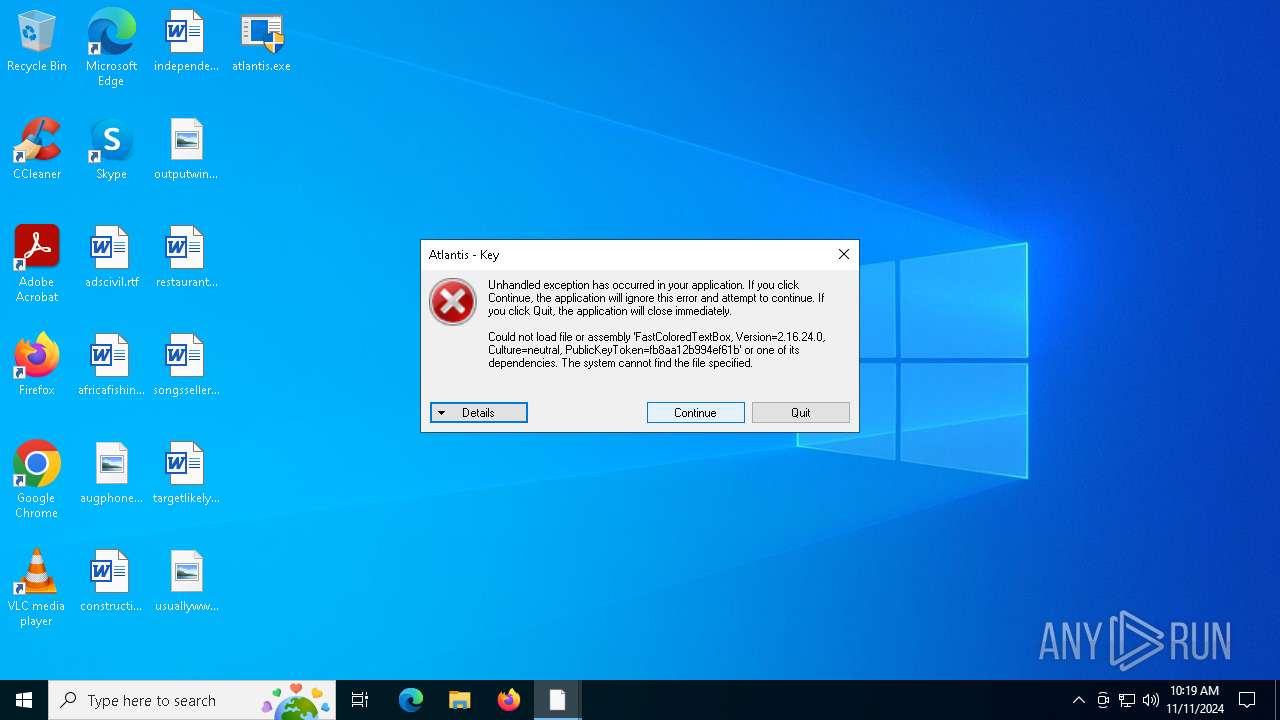
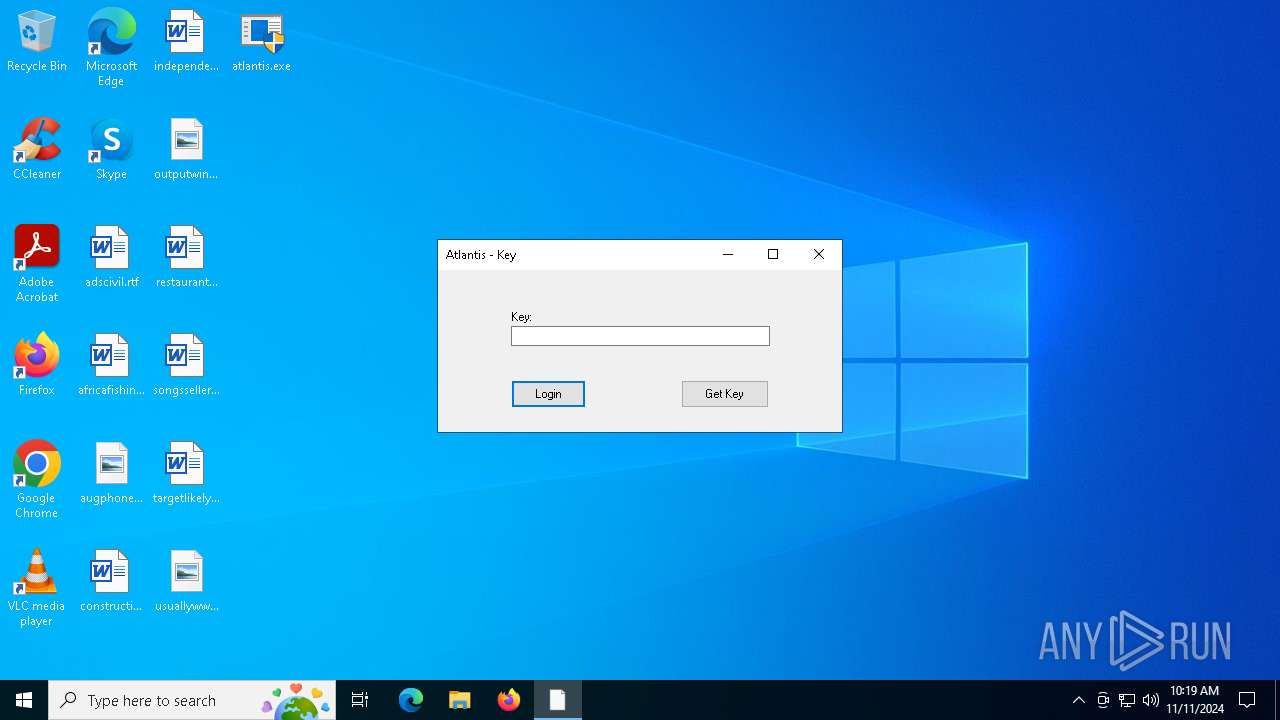
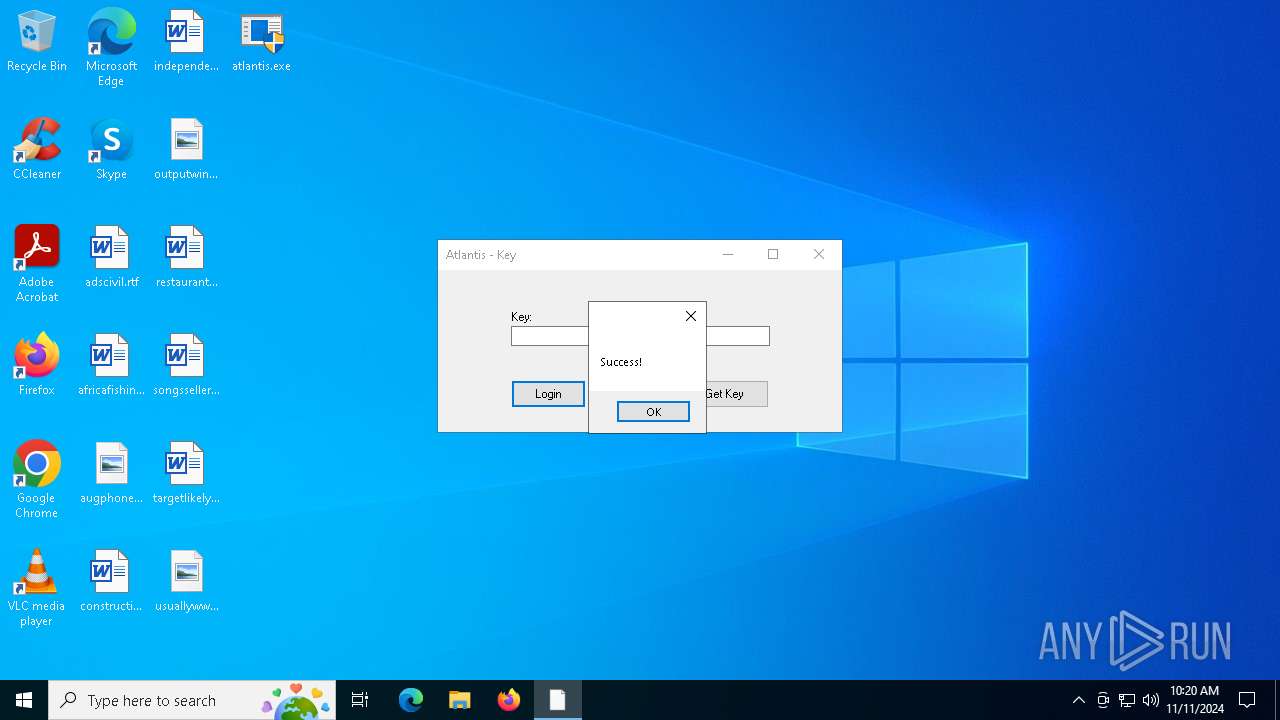
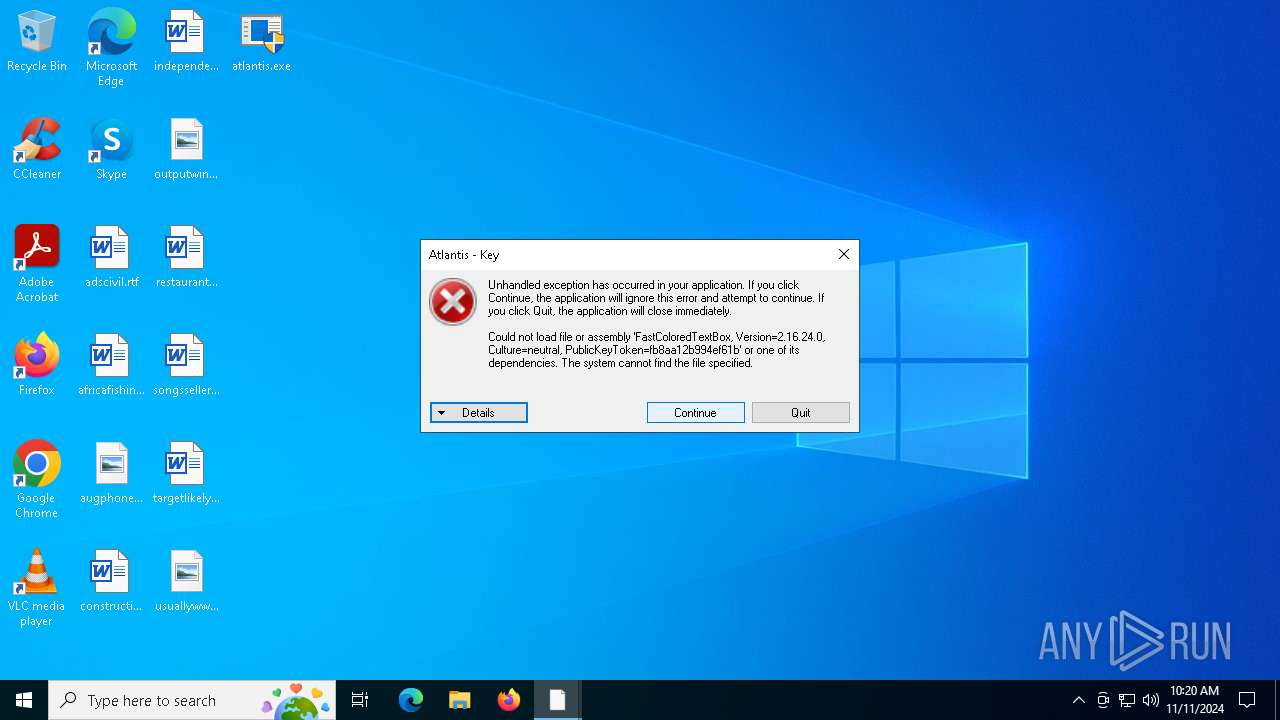
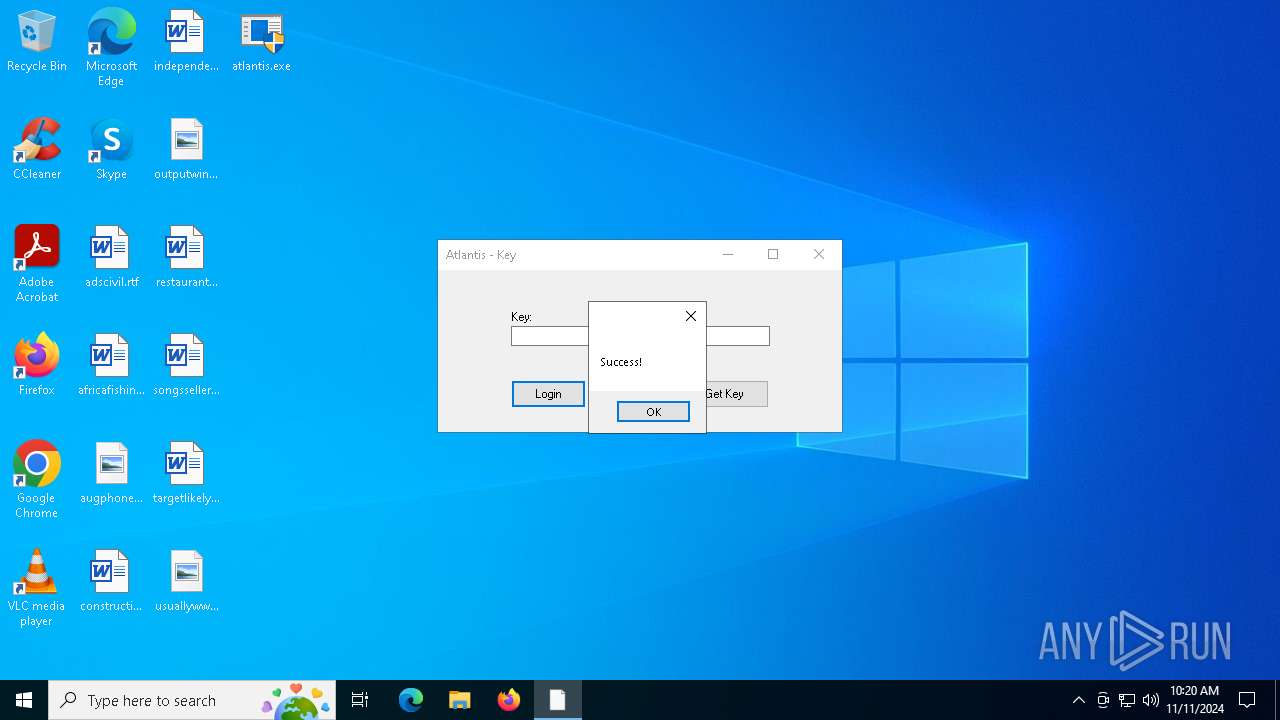
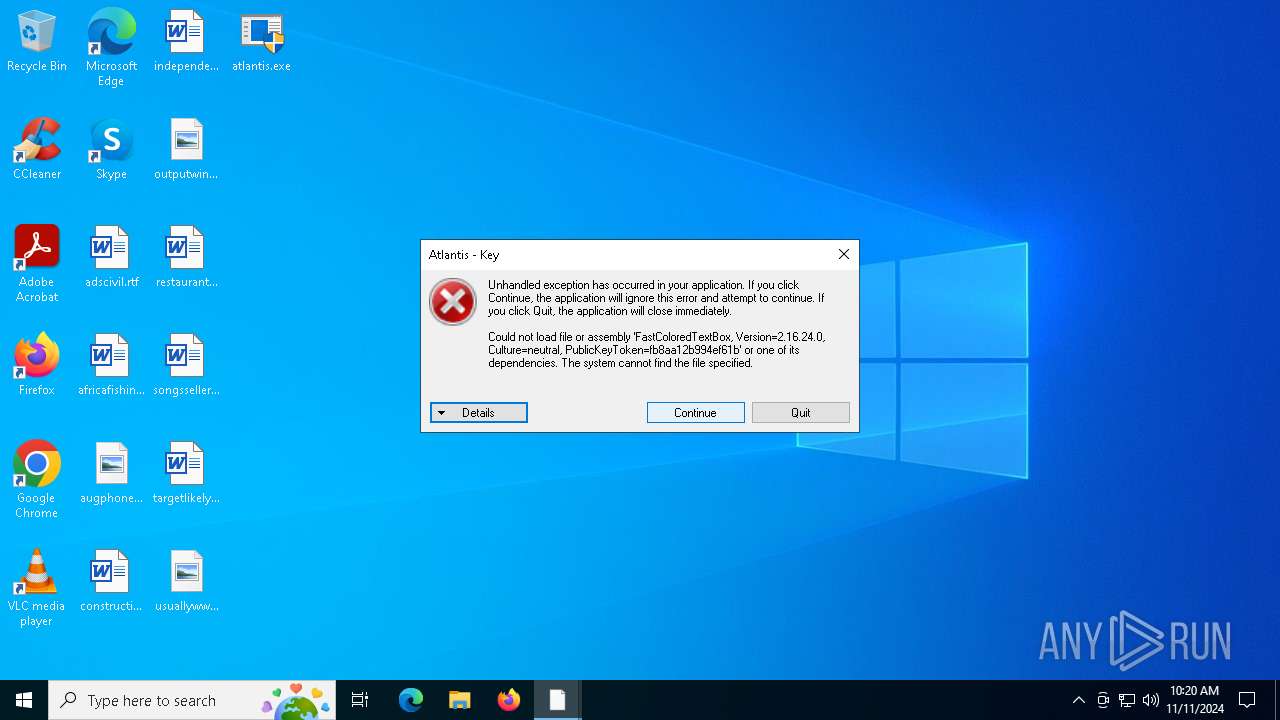
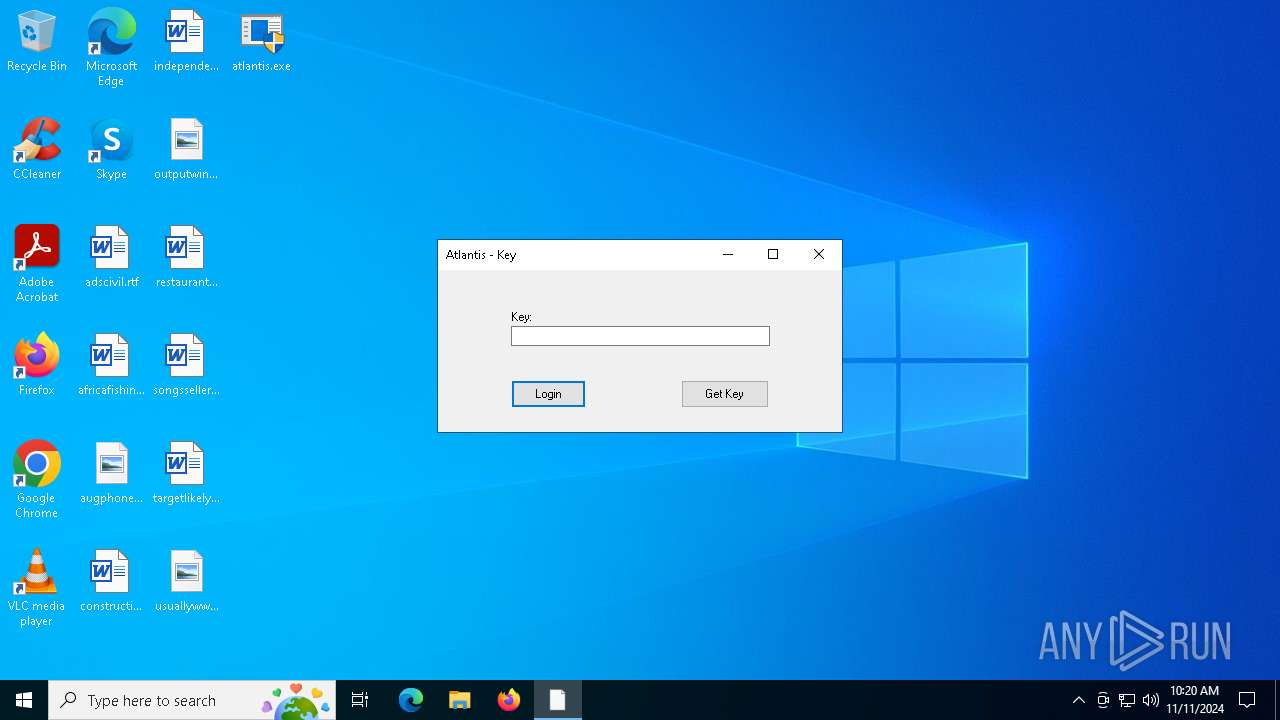
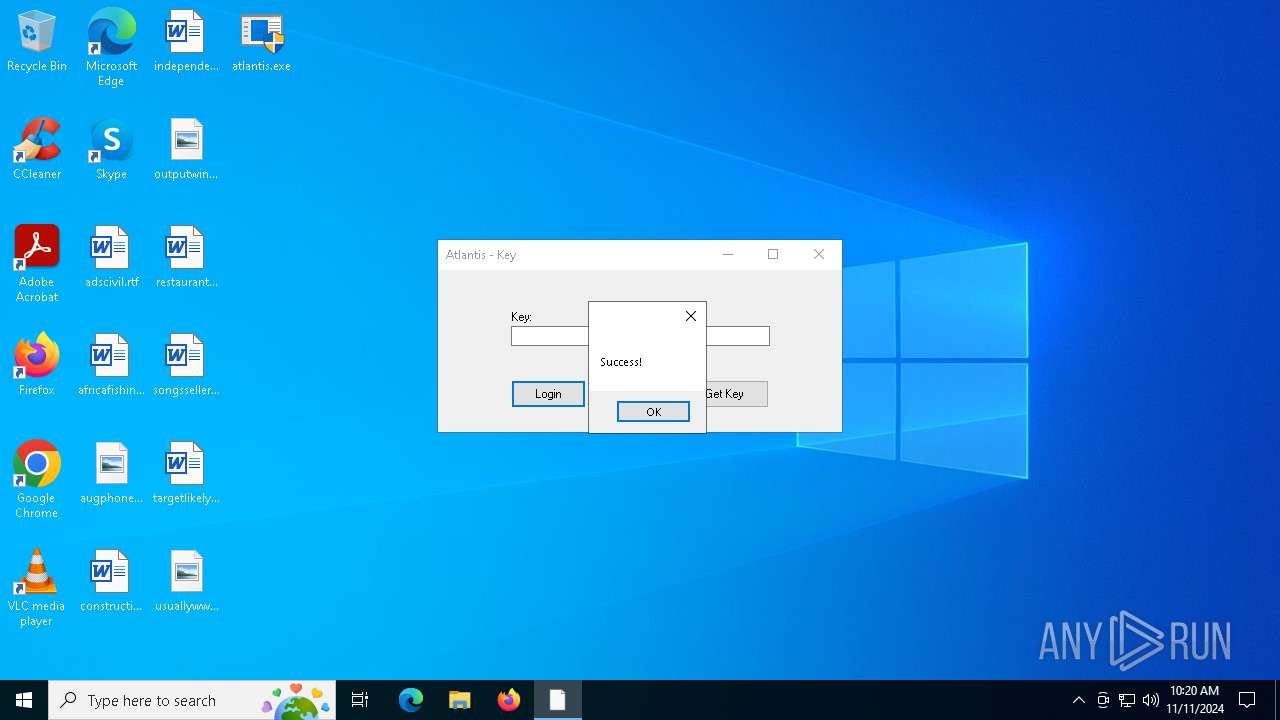
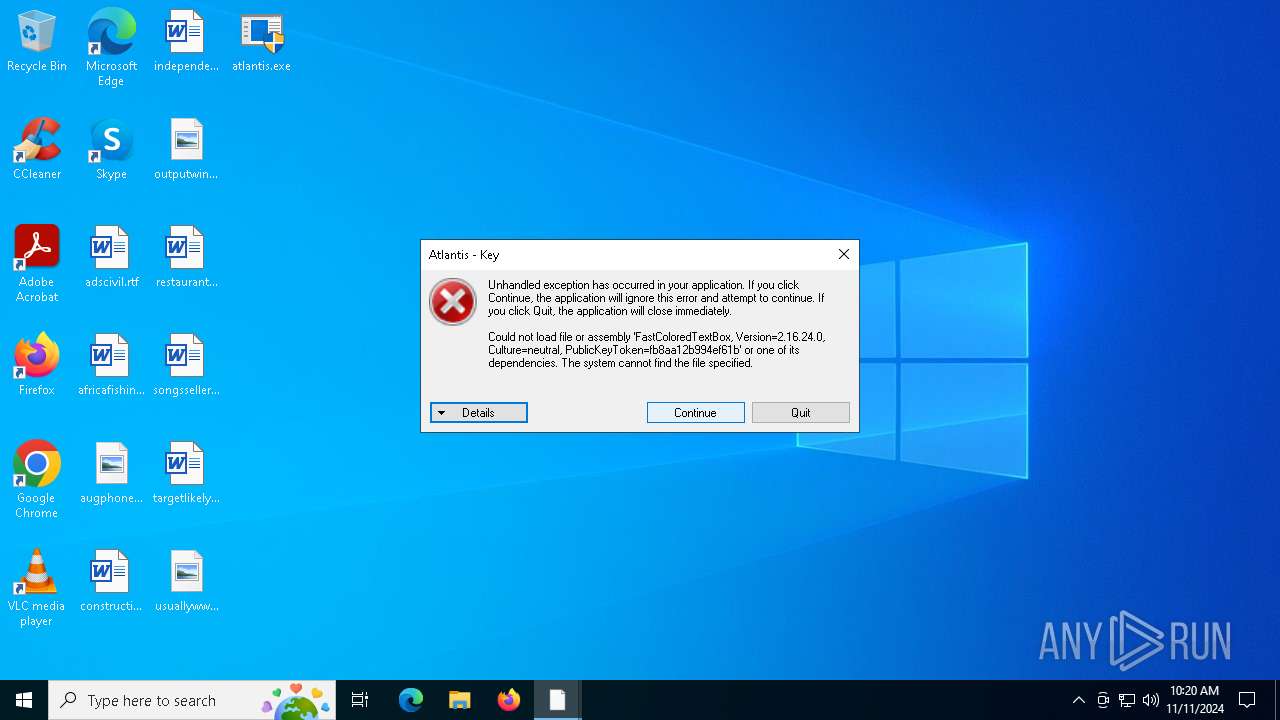
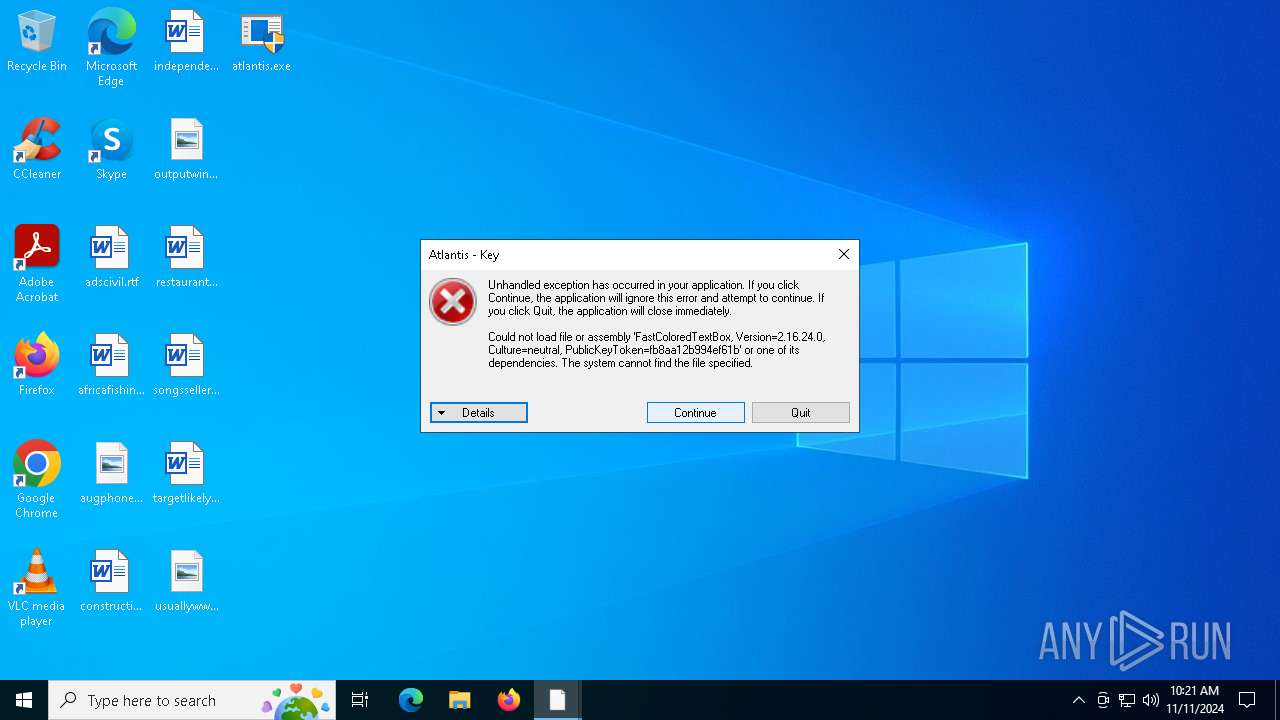
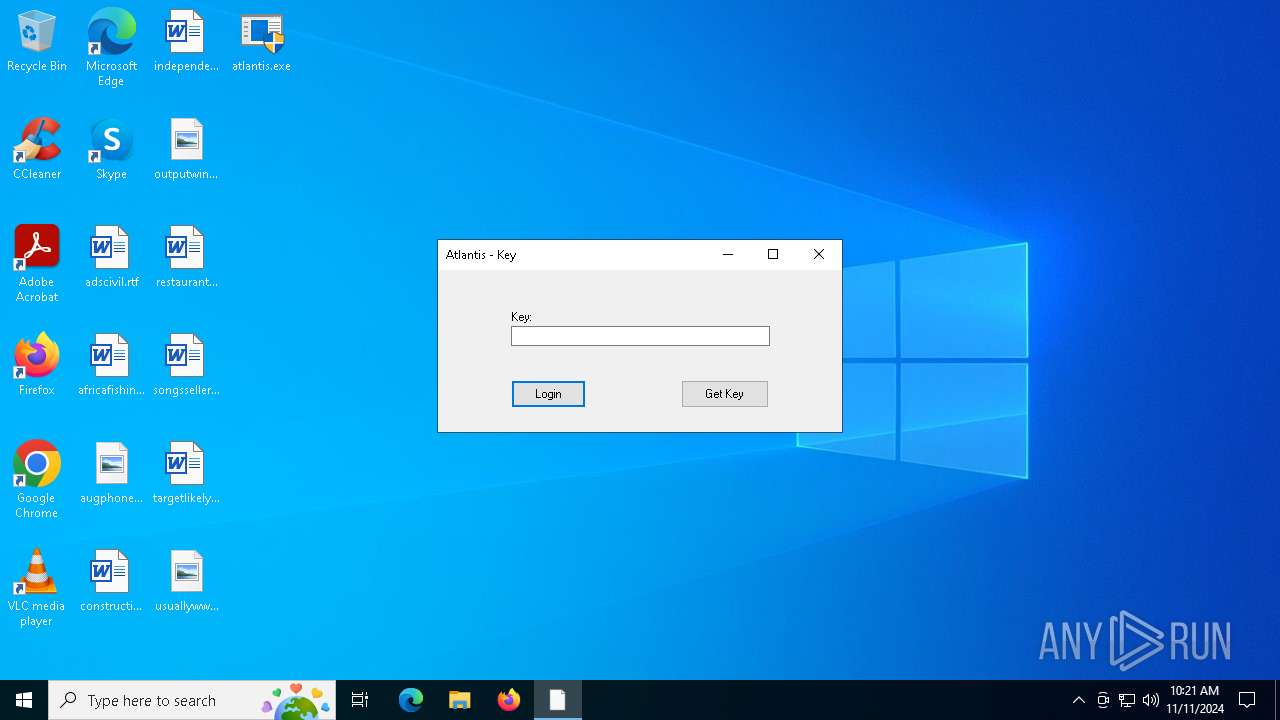
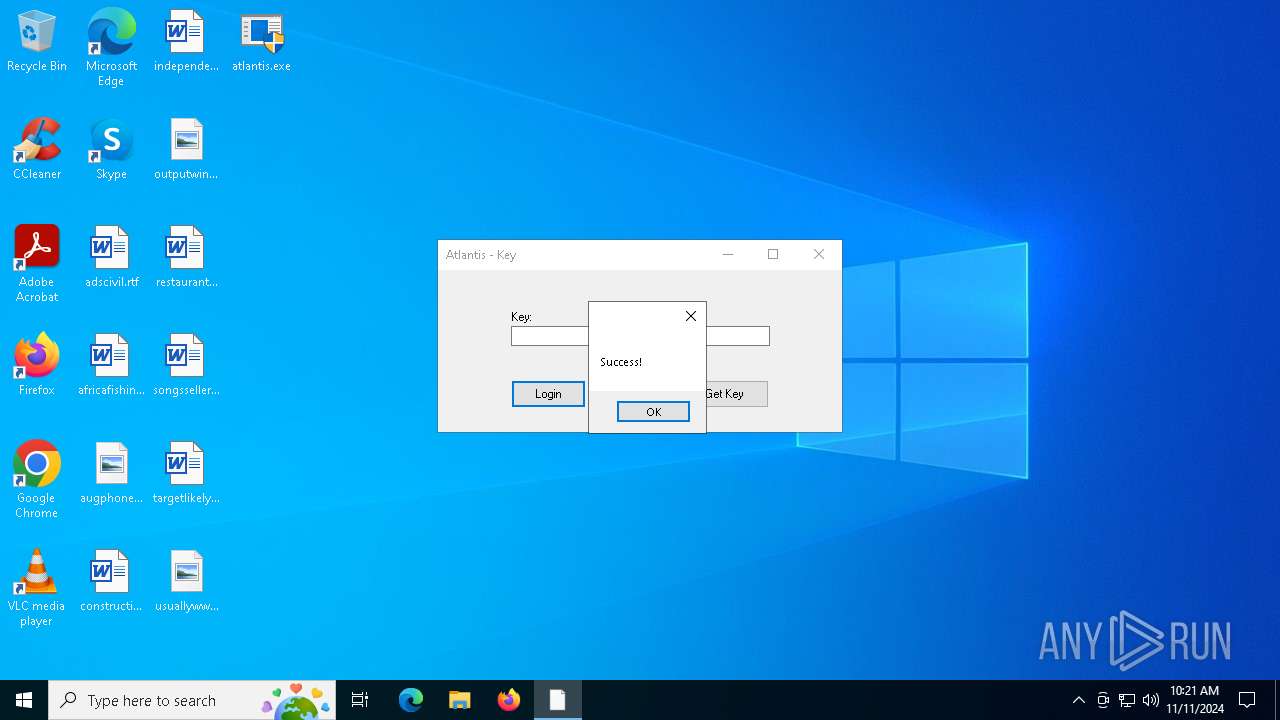
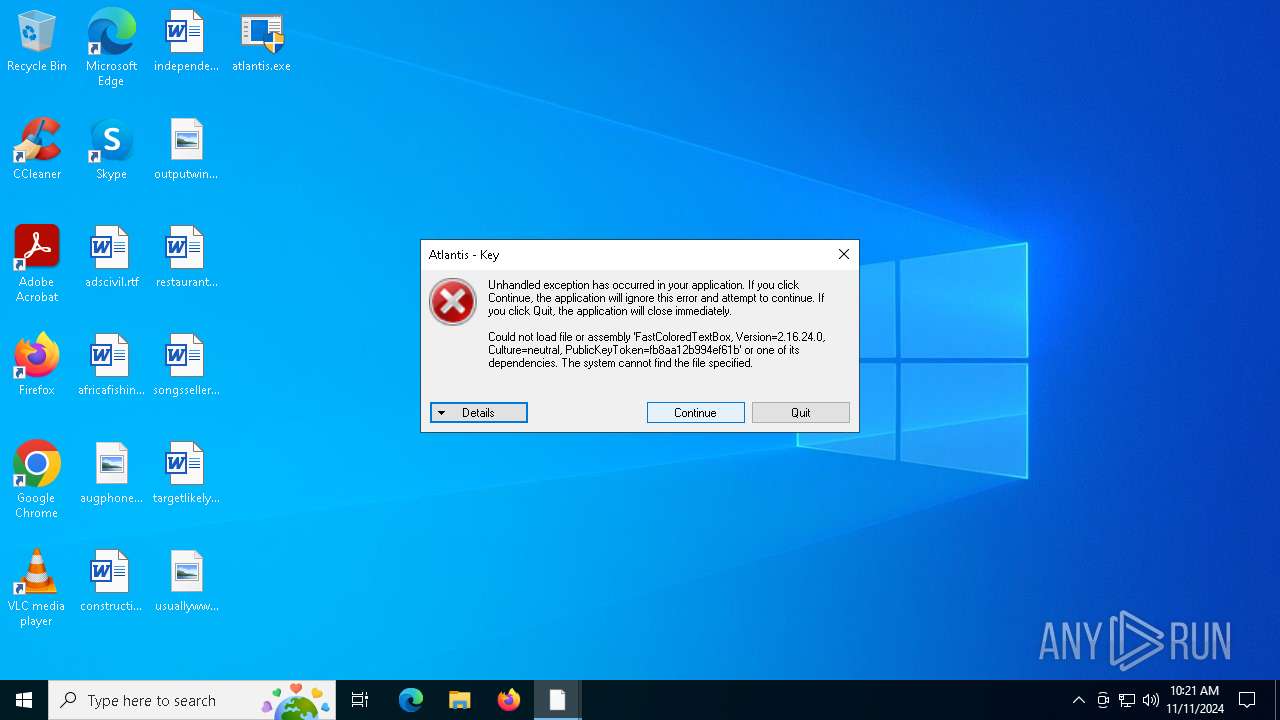
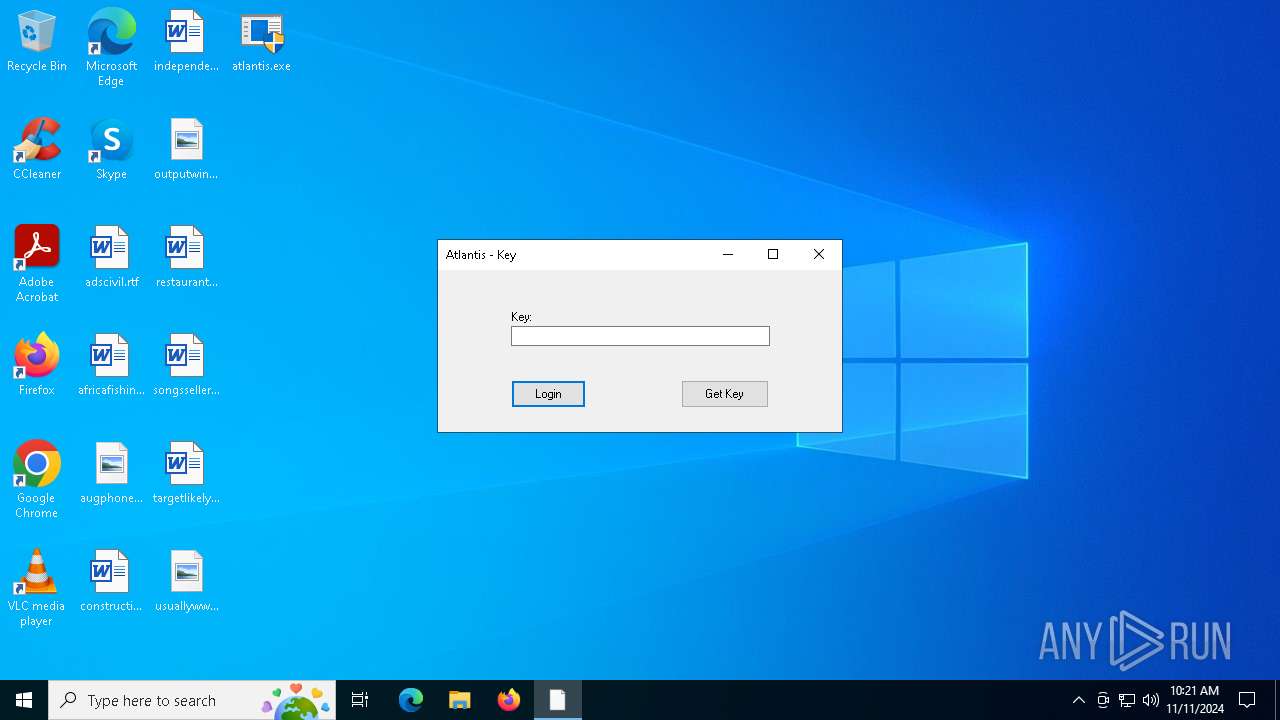
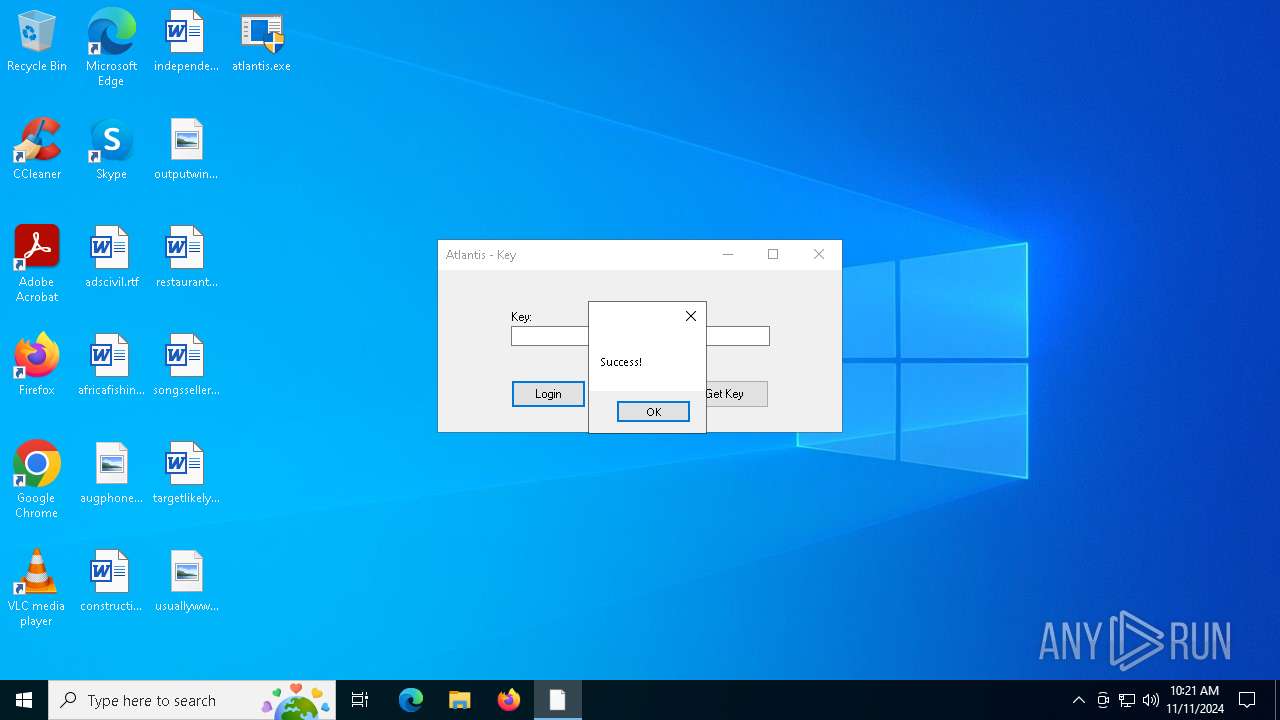
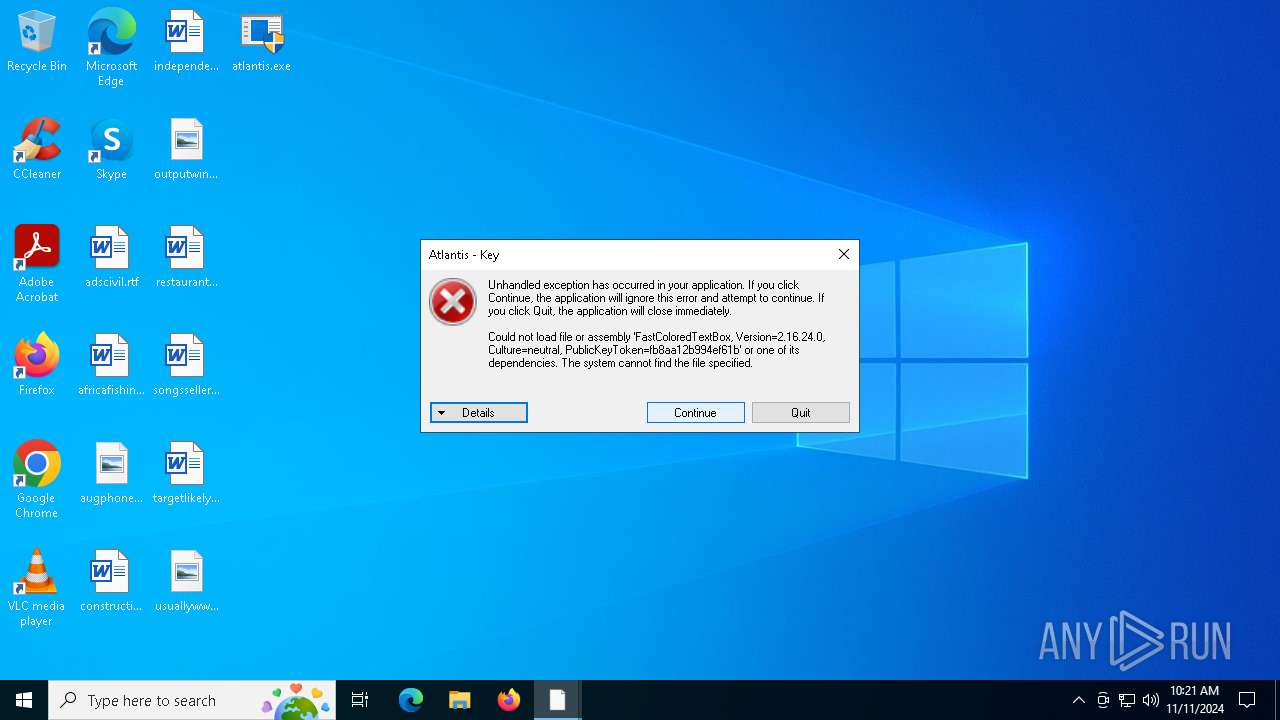
| File name: | atlantis.exe |
| Full analysis: | https://app.any.run/tasks/142d2e29-34ab-4183-af41-580bb7e62e3e |
| Verdict: | Malicious activity |
| Analysis date: | November 11, 2024, 10:19:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 3 sections |
| MD5: | B28FF133BFC6821909596CAEDA6A86A7 |
| SHA1: | 4EF6C00AD77B3C3FA0AEC0D1A8D86E7C12BD54B0 |
| SHA256: | 7E954645CA546EFFCD3F964D3CE0B0B95EB82EE962A3A2D131AC4E6971CCE4CF |
| SSDEEP: | 3072:bqy40/1Thw5w4qjPR8y9bBW3L3sBcmxy1S99I999999UfjyoF9I7rO9a1Y9Oa697:i0/1Thw5w4qjPRrf2VrRZHMrbLcPNW72 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- atlantis.exe (PID: 6692)
- spoolsv.exe (PID: 6964)
- explorer.exe (PID: 6100)
- icsys.icn.exe (PID: 6044)
Starts application with an unusual extension
- atlantis.exe (PID: 6692)
Starts itself from another location
- explorer.exe (PID: 6100)
- atlantis.exe (PID: 6692)
- icsys.icn.exe (PID: 6044)
- svchost.exe (PID: 6236)
- spoolsv.exe (PID: 6964)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:04:01 07:08:22+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 106496 |
| InitializedDataSize: | 12288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x290c |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | Project1 |
| FileVersion: | 1 |
| ProductVersion: | 1 |
| InternalName: | TJprojMain |
| OriginalFileName: | TJprojMain.exe |
Total processes
132
Monitored processes
8
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3916 | c:\windows\resources\spoolsv.exe PR | C:\Windows\Resources\spoolsv.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 5748 | "C:\Users\admin\Desktop\atlantis.exe" | C:\Users\admin\Desktop\atlantis.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
| 6044 | C:\Windows\Resources\Themes\icsys.icn.exe | C:\Windows\Resources\Themes\icsys.icn.exe | atlantis.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 6100 | c:\windows\resources\themes\explorer.exe | C:\Windows\Resources\Themes\explorer.exe | icsys.icn.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.00 Modules
| |||||||||||||||
| 6236 | c:\windows\resources\svchost.exe | C:\Windows\Resources\svchost.exe | — | spoolsv.exe | |||||||||||
User: admin Integrity Level: HIGH Version: 1.00 Modules
| |||||||||||||||
| 6608 | c:\users\admin\desktop\atlantis.exe | C:\Users\admin\Desktop\atlantis.exe | — | atlantis.exe | |||||||||||
User: admin Integrity Level: HIGH Description: atlantis Version: 1.0.0.0 Modules
| |||||||||||||||
| 6692 | "C:\Users\admin\Desktop\atlantis.exe" | C:\Users\admin\Desktop\atlantis.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 6964 | c:\windows\resources\spoolsv.exe SE | C:\Windows\Resources\spoolsv.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
1 036
Read events
1 017
Write events
15
Delete events
4
Modification events
| (PID) Process: | (6692) atlantis.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (6044) icsys.icn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (6100) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (6100) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
| (PID) Process: | (6100) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (6100) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Svchost |
Value: | |||
| (PID) Process: | (6236) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (6236) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
| (PID) Process: | (6236) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (6236) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Svchost |
Value: | |||
Executable files
5
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6100 | explorer.exe | C:\Windows\Resources\spoolsv.exe | executable | |
MD5:6FD99AF4C7FE0036BF7261773EC5AADB | SHA256:EEED189DB2D0849DCE8462F3904BE67214C0480CB5E1DCECE8A0EB0193280C02 | |||
| 6044 | icsys.icn.exe | C:\Windows\Resources\Themes\explorer.exe | executable | |
MD5:C7C450A37F58414BA6EBBCD8E16CB466 | SHA256:F19F7AF98CF4E9BF7F28EC6C26805A31A036ED9890A1F4FA1A67A40DDEB40C1B | |||
| 6692 | atlantis.exe | C:\Users\admin\Desktop\atlantis.exe | executable | |
MD5:0EEBF1934EE9EF1D51A4327C67B9D3BD | SHA256:98C42F0E12CB3BEAA1EF35E62A8EB0F0C7F49C755F47D61E049EB60F686E1718 | |||
| 6964 | spoolsv.exe | C:\Windows\Resources\svchost.exe | executable | |
MD5:721652E70067A73A30C216A9B5F8C81F | SHA256:D5BA8EF24029AAD7B05BF52C3D291AD5043AE1C828C0730DB95A20BFDB3120E6 | |||
| 3916 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DFE356511BB3679DB6.TMP | binary | |
MD5:02353B3CC2B21C2285BCDF3F6C83FE07 | SHA256:0F26CF89459927549C9DB441BA7E90622A74401A19E158ED9B7C701FCC5E5763 | |||
| 6044 | icsys.icn.exe | C:\Users\admin\AppData\Local\Temp\~DFBF907437973B87D7.TMP | binary | |
MD5:3A1BB68E6B1452E3A74680604D784F2E | SHA256:FD9B0194AB2704F1612652CB6B2645E5D9D052B1182A5E33BF67FD4D14EB718C | |||
| 6692 | atlantis.exe | C:\Windows\Resources\Themes\icsys.icn.exe | executable | |
MD5:B26D893F1D8C0CD101CF6EA12059DD9B | SHA256:62835F353B2DB8338161F93DD46C417161717C2F57E30C145AA2D991C458DAAD | |||
| 6964 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DFA9444128A1FBF71F.TMP | binary | |
MD5:DB18D02414DBF405B30A9CC6D2A3CB94 | SHA256:7307A3A63254698F98BC6B1E0418D15BF3733709BB019F74B6289E56A18E1E45 | |||
| 6692 | atlantis.exe | C:\Users\admin\AppData\Local\Temp\~DF88FAC537AFEC5CE6.TMP | binary | |
MD5:E1434A8699AB54456D94B3C75BB90F45 | SHA256:E1A7E378A735AB809B23D8F1BEB91C90031D97F3C91C194FD0ED7449D4D386CA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
23
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1584 | RUXIMICS.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1584 | RUXIMICS.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1584 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.23.209.185:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
1584 | RUXIMICS.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6944 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |