| File name: | ipscan-win32-3.7.6.exe |
| Full analysis: | https://app.any.run/tasks/c33ae00e-244f-4d4e-9335-a35d9e2d5595 |
| Verdict: | Malicious activity |
| Analysis date: | March 14, 2025, 15:29:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive, with extra data prepended |
| MD5: | 05AC9DB34D4F167508A1E58F5857F31C |
| SHA1: | 3E90F7BCCC2B6BEBF8E79DB4729F8F39AF46A88D |
| SHA256: | 7E7F92D6FF919FE8CBE63F2DAA348D122339D1A0AAC0883AFCF799FACD214810 |
| SSDEEP: | 98304:HjRsaChNOJExe4w4RSvtvlcMnjbtBGyV4H7ywTXxcj3h7nWms2kUsWYHDZf5xYbq:MCRC3Aej |
MALICIOUS
No malicious indicators.SUSPICIOUS
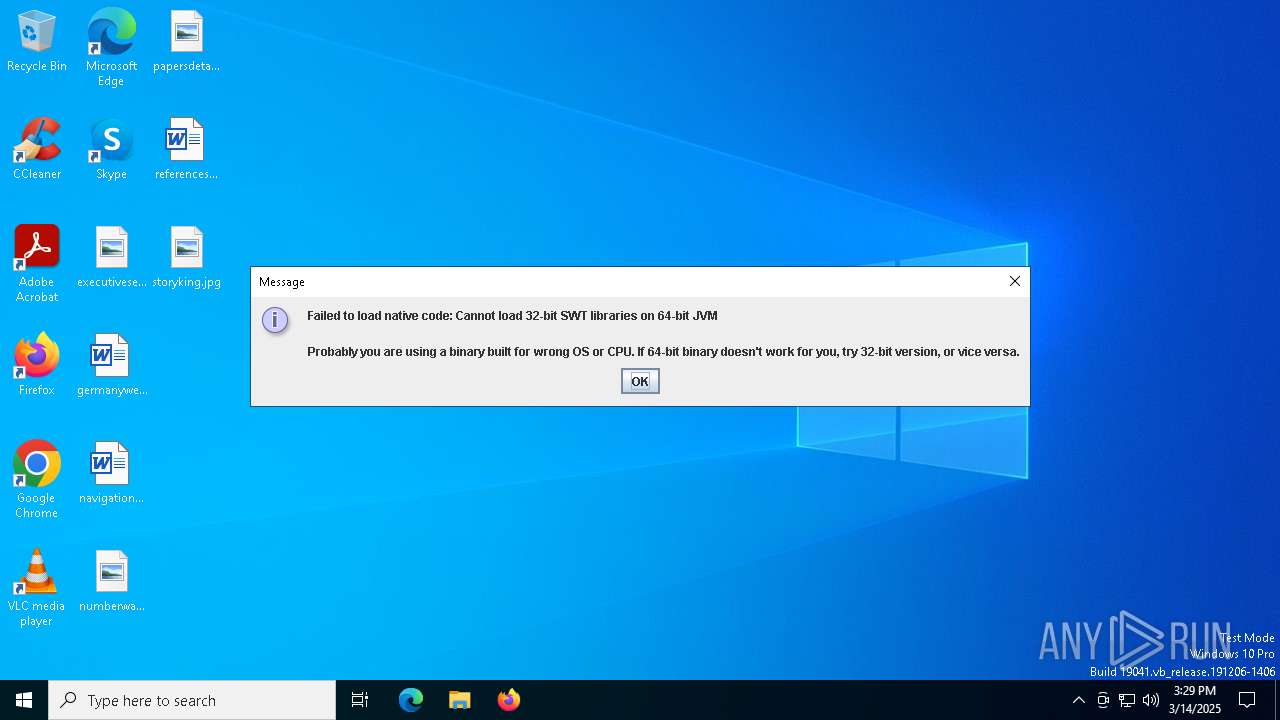
Checks for Java to be installed
- javaw.exe (PID: 3884)
There is functionality for taking screenshot (YARA)
- javaw.exe (PID: 3884)
INFO
Creates files in the program directory
- javaw.exe (PID: 3884)
Checks supported languages
- ipscan-win32-3.7.6.exe (PID: 4880)
- javaw.exe (PID: 3884)
Application based on Java
- javaw.exe (PID: 3884)
Create files in a temporary directory
- javaw.exe (PID: 3884)
The sample compiled with english language support
- ipscan-win32-3.7.6.exe (PID: 4880)
Creates files or folders in the user directory
- javaw.exe (PID: 3884)
Reads the computer name
- javaw.exe (PID: 3884)
Reads the machine GUID from the registry
- javaw.exe (PID: 3884)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.3) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.1) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1973:09:28 06:57:28+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 2.24 |
| CodeSize: | 4608 |
| InitializedDataSize: | 125440 |
| UninitializedDataSize: | 512 |
| EntryPoint: | 0x12a0 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.9.9.9 |
| ProductVersionNumber: | 3.9.9.9 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | angryip.org |
| FileDescription: | Angry IP Scanner - fast and friendly network scanner |
| InternalName: | ipscan |
| LegalCopyright: | Anton Keks |
| OriginalFileName: | ipscan.exe |
| ProductName: | Angry IP Scanner |
| ProductVersion: | 3+ |
Total processes
137
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 720 | C:\WINDOWS\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1764 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3884 | javaw -jar "C:\Users\admin\AppData\Local\Temp\ipscan-win32-3.7.6.exe" | C:\Program Files (x86)\Common Files\Oracle\Java\javapath_target_2989500\javaw.exe | ipscan-win32-3.7.6.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Version: 8.0.2710.9 Modules
| |||||||||||||||
| 4448 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4880 | "C:\Users\admin\AppData\Local\Temp\ipscan-win32-3.7.6.exe" | C:\Users\admin\AppData\Local\Temp\ipscan-win32-3.7.6.exe | — | explorer.exe | |||||||||||
User: admin Company: angryip.org Integrity Level: MEDIUM Description: Angry IP Scanner - fast and friendly network scanner Modules
| |||||||||||||||
| 5504 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
826
Read events
825
Write events
1
Delete events
0
Modification events
| (PID) Process: | (3884) javaw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\JavaSoft\Prefs\ipscan |
| Operation: | write | Name: | uuid |
Value: a4e1ba68-e045-4e5a-a807-994db3b66044 | |||
Executable files
0
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3884 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:A747532EE1315BD3FF950921AB979DC4 | SHA256:C8A474BF46D8181C536D2A6892194865388C28C0171802FA74F15B3DAA322B9A | |||
| 3884 | javaw.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1693682860-607145093-2874071422-1001\83aa4cc77f591dfc2374580bbd95f6ba_bb926e54-e3ca-40fd-ae90-2764341e7792 | binary | |
MD5:C8366AE350E7019AEFC9D1E6E6A498C6 | SHA256:11E6ACA8E682C046C83B721EEB5C72C5EF03CB5936C60DF6F4993511DDC61238 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
25
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.194.200:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 104.81.99.218:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
812 | backgroundTaskHost.exe | GET | 200 | 104.81.99.218:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4228 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4228 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.19.194.200:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.65:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 104.81.99.218:80 | ocsp.digicert.com | AKAMAI-AS | PL | whitelisted |
3884 | javaw.exe | 142.250.181.238:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |