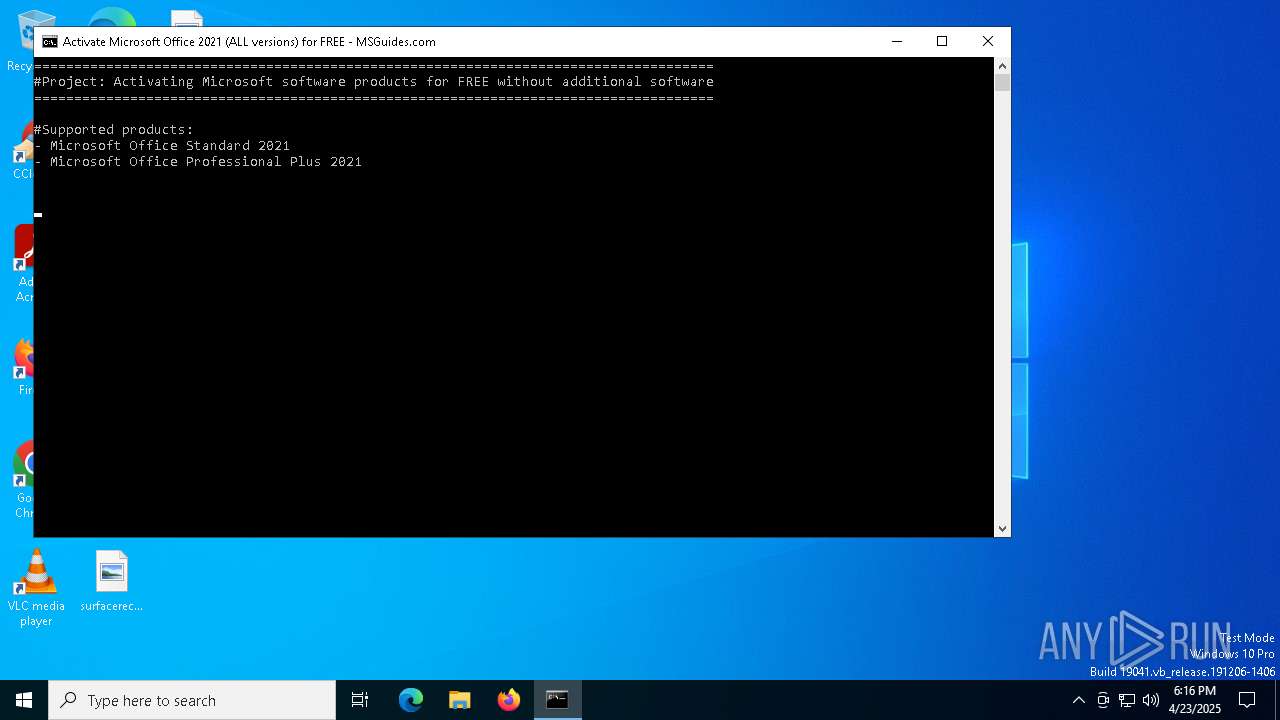
| File name: | office.msguides.bat |
| Full analysis: | https://app.any.run/tasks/4ab1cf50-0f52-4e62-8858-ac5e70ba3ceb |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2025, 18:16:03 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines (1197), with CRLF line terminators |
| MD5: | AABCFB044A85D94A2D0E691893A66BFD |
| SHA1: | 5CD918570D4AC1B52370E326A3926C88CFE70EA0 |
| SHA256: | 7E7A9EF2F02F5D48E0F0F6DB478974921B7CA555A3ABC44CBB25E4415D94129C |
| SSDEEP: | 48:Wimr63WuzcqoXucXuu7hsJBzozcPUwfufmcbZ/T/8ZxGSq3v:jmr633zcqKumuc6+cPUDzZ/A36 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- cmd.exe (PID: 7352)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 7352)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 7452)
- cscript.exe (PID: 8088)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 5680)
- cscript.exe (PID: 7820)
- cscript.exe (PID: 5084)
- cscript.exe (PID: 6184)
- cscript.exe (PID: 904)
Gets a collection of all available drive names (SCRIPT)
- cscript.exe (PID: 7452)
- cscript.exe (PID: 8088)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 5680)
- cscript.exe (PID: 5084)
- cscript.exe (PID: 7820)
- cscript.exe (PID: 904)
- cscript.exe (PID: 6184)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 8088)
- cscript.exe (PID: 7452)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 5084)
- cscript.exe (PID: 5680)
- cscript.exe (PID: 904)
- cscript.exe (PID: 7820)
- cscript.exe (PID: 6184)
Gets the drive type (SCRIPT)
- cscript.exe (PID: 7452)
- cscript.exe (PID: 8088)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 5680)
- cscript.exe (PID: 5084)
- cscript.exe (PID: 7820)
- cscript.exe (PID: 904)
- cscript.exe (PID: 6184)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 7452)
- cscript.exe (PID: 8088)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 5084)
- cscript.exe (PID: 5680)
- cscript.exe (PID: 7820)
- cscript.exe (PID: 904)
- cscript.exe (PID: 6184)
Executes application which crashes
- cscript.exe (PID: 7452)
- cscript.exe (PID: 8088)
- cscript.exe (PID: 6512)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 7452)
- cscript.exe (PID: 8088)
- cscript.exe (PID: 6512)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 7452)
- cscript.exe (PID: 8088)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 5680)
- cscript.exe (PID: 5084)
- cscript.exe (PID: 7820)
- cscript.exe (PID: 904)
- cscript.exe (PID: 6184)
The process executes VB scripts
- cmd.exe (PID: 7352)
The process creates files with name similar to system file names
- WerFault.exe (PID: 8176)
- WerFault.exe (PID: 5228)
Sets XML DOM element text (SCRIPT)
- cscript.exe (PID: 7820)
INFO
Reads the software policy settings
- cscript.exe (PID: 8088)
- cscript.exe (PID: 7452)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 5084)
- cscript.exe (PID: 5680)
- cscript.exe (PID: 904)
- cscript.exe (PID: 7820)
- cscript.exe (PID: 6184)
Reads security settings of Internet Explorer
- cscript.exe (PID: 7452)
- cscript.exe (PID: 8088)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 5084)
- cscript.exe (PID: 5680)
- cscript.exe (PID: 904)
- cscript.exe (PID: 7820)
- cscript.exe (PID: 6184)
Creates files or folders in the user directory
- WerFault.exe (PID: 5228)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
154
Monitored processes
19
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 904 | cscript //nologo ospp.vbs /sethst:kms7.MSGuides.com | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1052 | find /i "successful" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5084 | cscript //nologo ospp.vbs /unpkey:6F7TH | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5228 | C:\WINDOWS\system32\WerFault.exe -u -p 6512 -s 1520 | C:\Windows\System32\WerFault.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5680 | cscript //nologo ospp.vbs /setprt:1688 | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6184 | cscript //nologo ospp.vbs /act | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6512 | cscript ospp.vbs /inslic:"..\root\Licenses16\ProPlus2021VL_KMS_Client_AE-ul.xrm-ms" | C:\Windows\System32\cscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 3221225477 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6668 | choice /n /c YN /m "Would you like to visit my blog [Y,N]?" | C:\Windows\System32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7352 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\office.msguides.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7360 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
31 422
Read events
31 422
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
13
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7944 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_cscript.exe_62b6f5ddb4f9b32f9faaaa562a56d6d8f11b6a_d25c8a3a_a7282696-2603-4cd3-826c-a4e95ef2e6d4\Report.wer | — | |
MD5:— | SHA256:— | |||
| 8176 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_cscript.exe_62b6f5ddb4f9b32f9faaaa562a56d6d8f11b6a_d25c8a3a_13c4f6f4-3028-4a06-8e57-b3fd018a4694\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5228 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_cscript.exe_62b6f5ddb4f9b32f9faaaa562a56d6d8f11b6a_d25c8a3a_d64b6974-4ac1-4ee6-810f-3d9ef1949828\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7452 | cscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\36AC0BE60E1243344AE145F746D881FE | binary | |
MD5:411D4C6D9068F0593E05D0F67B46BF77 | SHA256:743747DD59C21B0ECD5328A93F31A5D89A9765AFC6740C4963EBA797AA383043 | |||
| 7452 | cscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:86BEC7A51419CF6F8277608E79B2B807 | SHA256:1AE99C253A484A9CB6814FB52AFD40E347DFE2CD6273E50B245695B87C1BC6E5 | |||
| 7944 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER1869.tmp.xml | xml | |
MD5:503962A1786DCB7535B37AD9F5025ED4 | SHA256:82B388D5A8B9CD5E3874127031EF988DC9594A5CE9BBE1815767FAA93B0C1ED5 | |||
| 7944 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER180A.tmp.WERInternalMetadata.xml | binary | |
MD5:7CF0FF50C9BD616C276B7D1E23A811D1 | SHA256:AEE1326B11BEAE982CBC152A5A0AB3D7BFC9403BB92C5069F6393BE4EFA36457 | |||
| 8176 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER2363.tmp.dmp | binary | |
MD5:4E2DECDEA9EF8DDAE9303C35444ED05B | SHA256:81A792D3A8091A070F5101E4372059EBE59B65EA0737527B2CB0BE0800CA31ED | |||
| 7452 | cscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\36AC0BE60E1243344AE145F746D881FE | binary | |
MD5:F0E540327DA48B9AAB6D1B434807435A | SHA256:650D83E9933E87D00605B2954E2B8A110B2B228BEEE5E02ED4518FE5E87D434E | |||
| 7944 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\cscript.exe.7452.dmp | binary | |
MD5:1733B8211B46FC6F694D69F4EF849B16 | SHA256:3F0C391B7E1043D8A069A568E806A45A7155DD150F87ED2DE723E3ECC4A2EAE5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
23
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7452 | cscript.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
2568 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7452 | cscript.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_2010-07-06.crl | unknown | — | — | whitelisted |
2568 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
6544 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7452 | cscript.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation.sls.microsoft.com |
| whitelisted |