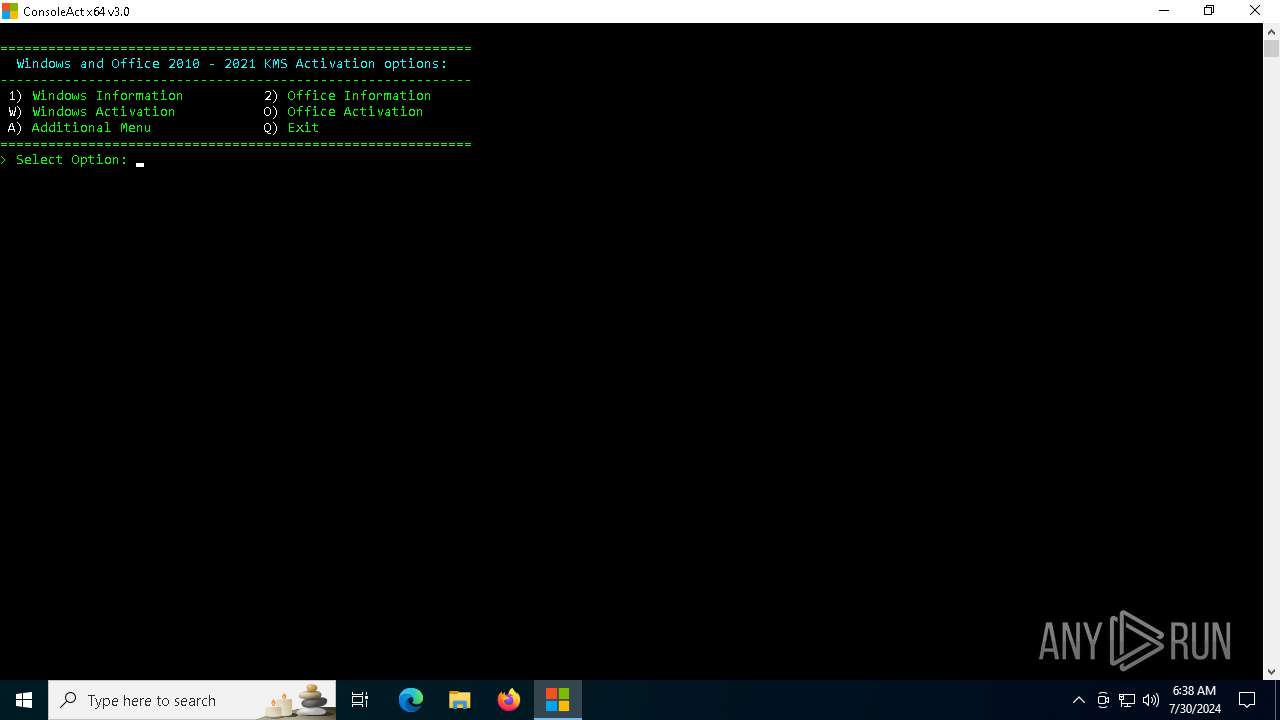
| File name: | ConsoleAct_3.0.exe |
| Full analysis: | https://app.any.run/tasks/c4799fcb-7ef4-4104-9556-67b8622f2020 |
| Verdict: | Malicious activity |
| Analysis date: | July 30, 2024, 06:38:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | BAA4274E11B6EEE268D0F6F80D517CB4 |
| SHA1: | B81EF15BFEFC1D7A823CD0F97BA4BE916F04A31B |
| SHA256: | 7E55D8AEA1ACDD0DADA0E9CA17F8CD9E8399C2E3B95742A4D7DC788F2F684C52 |
| SSDEEP: | 49152:2RSmQfZch2d77ABcM5w9heoxSiVHGSMbW3Y0GoHXFI0uiIfUyMB97wFKE7e+FygA:2RTAd7cBUh5XVHZY0d2hYBZwqWygxiUG |
MALICIOUS
Drops the executable file immediately after the start
- ConsoleAct_3.0.exe (PID: 6776)
Uses WMIC.EXE to add exclusions to the Windows Defender
- cmd.exe (PID: 2188)
- cmd.exe (PID: 4128)
Starts NET.EXE for service management
- cmd.exe (PID: 4276)
- net.exe (PID: 1256)
Accesses name of the domain to which a computer belongs via WMI (SCRIPT)
- cscript.exe (PID: 4632)
- cscript.exe (PID: 6812)
- cscript.exe (PID: 7080)
SUSPICIOUS
Found strings related to reading or modifying Windows Defender settings
- ConsoleAct_3.0.exe (PID: 6776)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5240)
- cmd.exe (PID: 5340)
- cmd.exe (PID: 2348)
- cmd.exe (PID: 3384)
- cmd.exe (PID: 6084)
- cmd.exe (PID: 6708)
- cmd.exe (PID: 5692)
- cmd.exe (PID: 6388)
- cmd.exe (PID: 2116)
- cmd.exe (PID: 3980)
- cmd.exe (PID: 6632)
- ConsoleAct_3.0.exe (PID: 6776)
- cmd.exe (PID: 1136)
- cmd.exe (PID: 6964)
- cmd.exe (PID: 4988)
- cmd.exe (PID: 3656)
- cmd.exe (PID: 6044)
Starts CMD.EXE for commands execution
- ConsoleAct_3.0.exe (PID: 6776)
Starts SC.EXE for service management
- cmd.exe (PID: 6224)
Hides command output
- cmd.exe (PID: 6224)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 6432)
Executable content was dropped or overwritten
- ConsoleAct_3.0.exe (PID: 6776)
The process executes VB scripts
- cmd.exe (PID: 7156)
- cmd.exe (PID: 3588)
- cmd.exe (PID: 4432)
- cmd.exe (PID: 2976)
- cmd.exe (PID: 6044)
- cmd.exe (PID: 1780)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 6224)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 3384)
- cscript.exe (PID: 1388)
- cscript.exe (PID: 4632)
- cscript.exe (PID: 6812)
- cscript.exe (PID: 1712)
- cscript.exe (PID: 7080)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 1388)
- cscript.exe (PID: 3384)
- cscript.exe (PID: 4632)
- cscript.exe (PID: 6812)
- cscript.exe (PID: 1712)
- cscript.exe (PID: 7080)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 1388)
- cscript.exe (PID: 6812)
- cscript.exe (PID: 3384)
- cscript.exe (PID: 4632)
- cscript.exe (PID: 7080)
- cscript.exe (PID: 1712)
The process downloads a VBScript from the remote host
- cmd.exe (PID: 6044)
INFO
Reads product name
- ConsoleAct_3.0.exe (PID: 6776)
Checks supported languages
- ConsoleAct_3.0.exe (PID: 6776)
Reads Environment values
- ConsoleAct_3.0.exe (PID: 6776)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 2368)
- WMIC.exe (PID: 7004)
- cscript.exe (PID: 1388)
- cscript.exe (PID: 3384)
- cscript.exe (PID: 4632)
- cscript.exe (PID: 6812)
- cscript.exe (PID: 7080)
- cscript.exe (PID: 1712)
Checks proxy server information
- slui.exe (PID: 6788)
UPX packer has been detected
- ConsoleAct_3.0.exe (PID: 6776)
Reads Microsoft Office registry keys
- reg.exe (PID: 4580)
- reg.exe (PID: 5084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (87) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.4) |
| .exe | | | DOS Executable Generic (6.4) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2020:12:25 02:25:27+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.5 |
| CodeSize: | 1032192 |
| InitializedDataSize: | 73728 |
| UninitializedDataSize: | 1286144 |
| EntryPoint: | 0x2362d0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.0.0.0 |
| ProductVersionNumber: | 3.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| OriginalFileName: | ConsoleAct_x64.exe |
| LegalCopyright: | MSFree Inc., Ratiborus |
Total processes
209
Monitored processes
69
Malicious processes
7
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1136 | "C:\WINDOWS\System32\cmd.exe" /c reg.exe add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\osppsvc.exe" /f /v "KMS_Emulation" /t REG_DWORD /d 1 2>&1 | C:\Windows\System32\cmd.exe | — | ConsoleAct_3.0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1256 | net.exe stop sppsvc /y | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | reg.exe add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\osppsvc.exe" /f /v "KMS_RenewalInterval" /t REG_DWORD /d 10080 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1388 | cscript.exe C:\WINDOWS\System32\slmgr.vbs //NoLogo /sdns | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1544 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1712 | cscript.exe C:\WINDOWS\System32\slmgr.vbs //NoLogo /ato | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1780 | "C:\WINDOWS\System32\cmd.exe" /c cscript.exe C:\WINDOWS\System32\slmgr.vbs //NoLogo /ato 2>&1 | C:\Windows\System32\cmd.exe | — | ConsoleAct_3.0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1884 | reg.exe add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\osppsvc.exe" /f /v "KMS_ActivationInterval" /t REG_DWORD /d 120 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2116 | "C:\WINDOWS\System32\cmd.exe" /c reg.exe add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe" /f /v "KMS_Emulation" /t REG_DWORD /d 1 2>&1 | C:\Windows\System32\cmd.exe | — | ConsoleAct_3.0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 483
Read events
5 465
Write events
18
Delete events
0
Modification events
| (PID) Process: | (6776) ConsoleAct_3.0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 1 | |||
| (PID) Process: | (6056) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe |
| Operation: | write | Name: | KMS_Emulation |
Value: 1 | |||
| (PID) Process: | (5128) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe |
| Operation: | write | Name: | GlobalFlag |
Value: 256 | |||
| (PID) Process: | (6652) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe |
| Operation: | write | Name: | KMS_ActivationInterval |
Value: 120 | |||
| (PID) Process: | (5272) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe |
| Operation: | write | Name: | KMS_RenewalInterval |
Value: 10080 | |||
| (PID) Process: | (4016) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe |
| Operation: | write | Name: | VerifierDlls |
Value: SppExtComObjHook.dll | |||
| (PID) Process: | (5296) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe |
| Operation: | write | Name: | KMS_HWID |
Value: 7000B60096041C9B | |||
| (PID) Process: | (6716) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\osppsvc.exe |
| Operation: | write | Name: | KMS_Emulation |
Value: 1 | |||
| (PID) Process: | (6704) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\osppsvc.exe |
| Operation: | write | Name: | GlobalFlag |
Value: 256 | |||
| (PID) Process: | (1884) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\osppsvc.exe |
| Operation: | write | Name: | KMS_ActivationInterval |
Value: 120 | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6776 | ConsoleAct_3.0.exe | C:\Windows\System32\SppExtComObjHook.dll | executable | |
MD5:95F143EC661A5DA85C3C8199D9FE06E7 | SHA256:F239C27B50CEF792FEA5B34378FBAC83BCC06B8442D508BD9ADD7DDF8CA5C632 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
44
DNS requests
26
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6700 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
752 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6220 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5368 | SearchApp.exe | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5368 | SearchApp.exe | 2.23.209.167:443 | www.bing.com | Akamai International B.V. | GB | unknown |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1620 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
t-ring-fdv2.msedge.net |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |