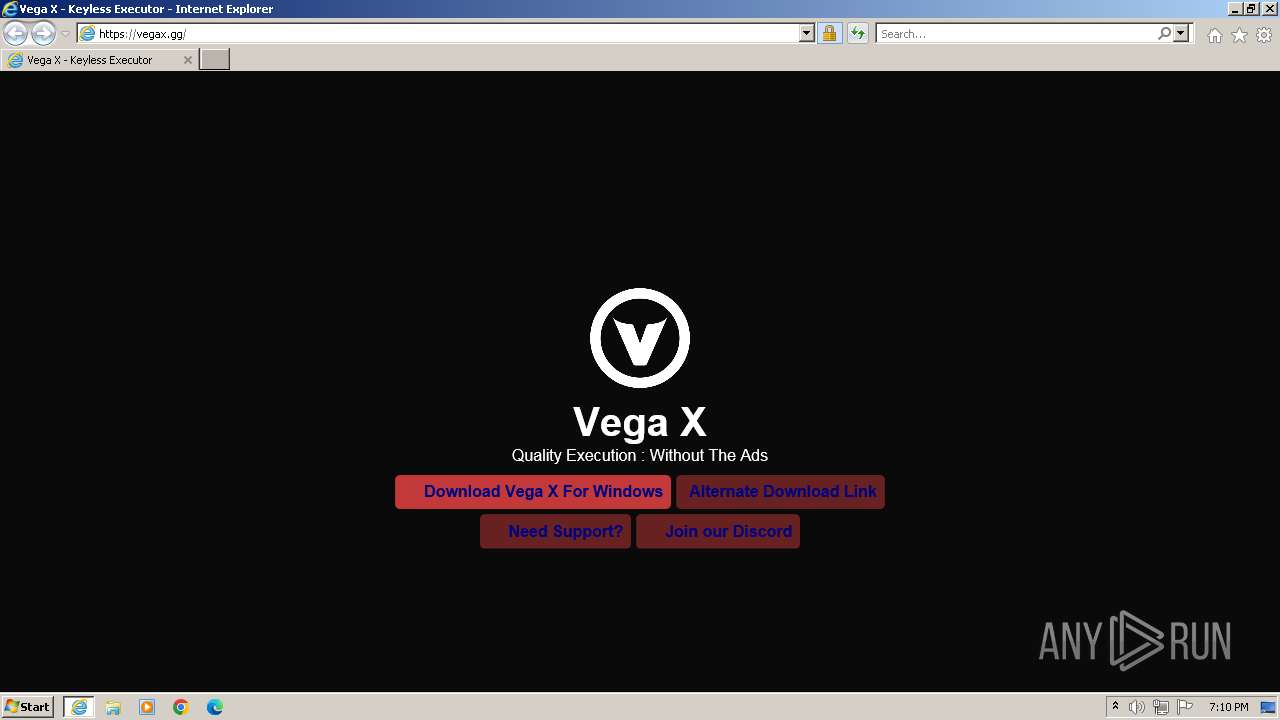
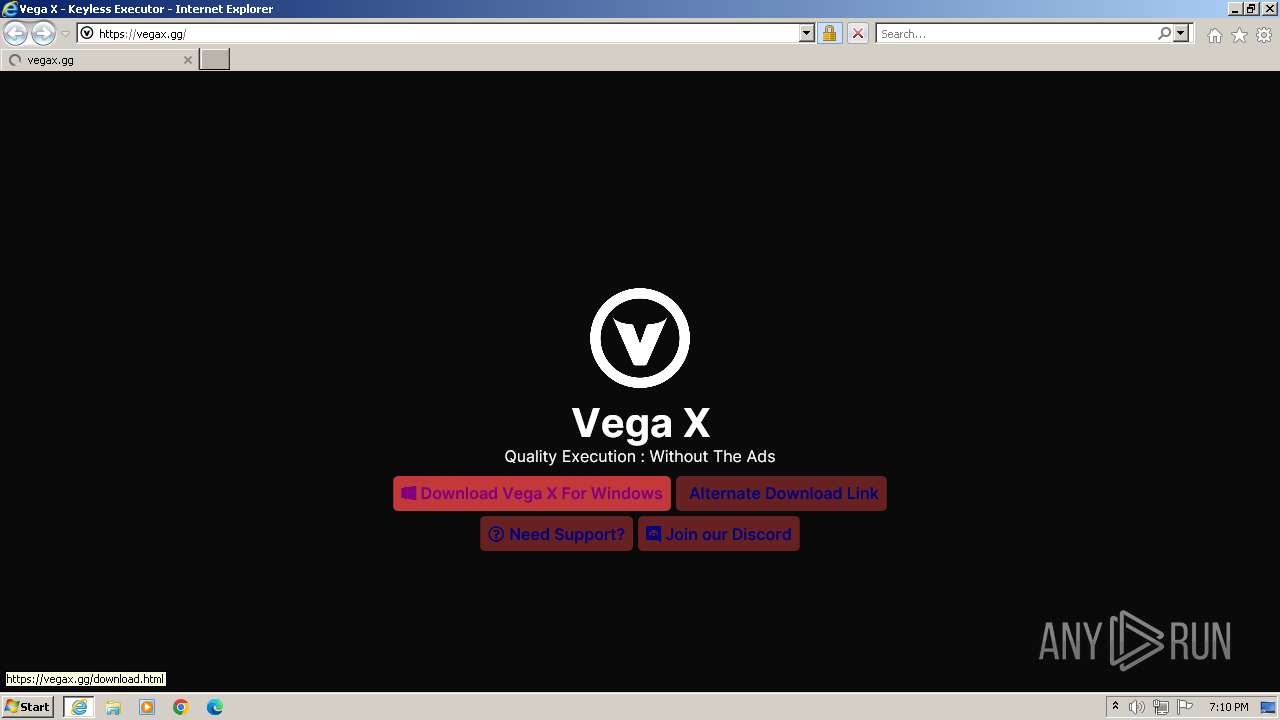
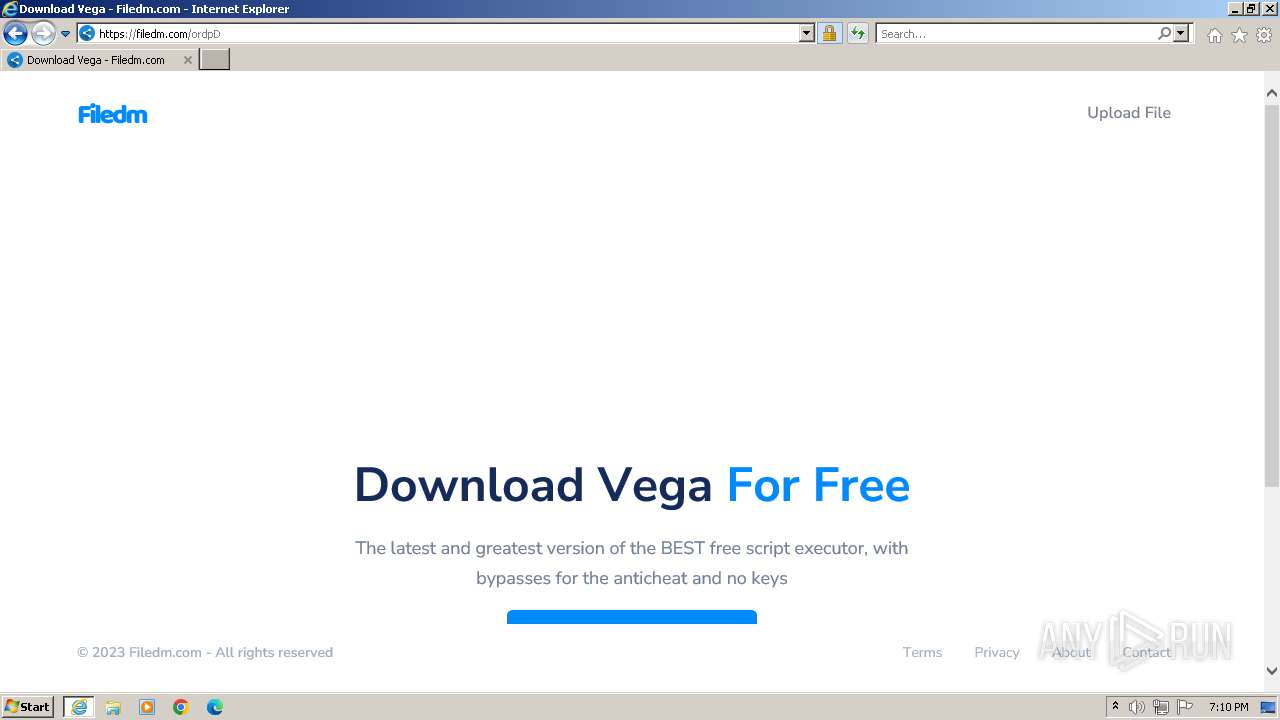
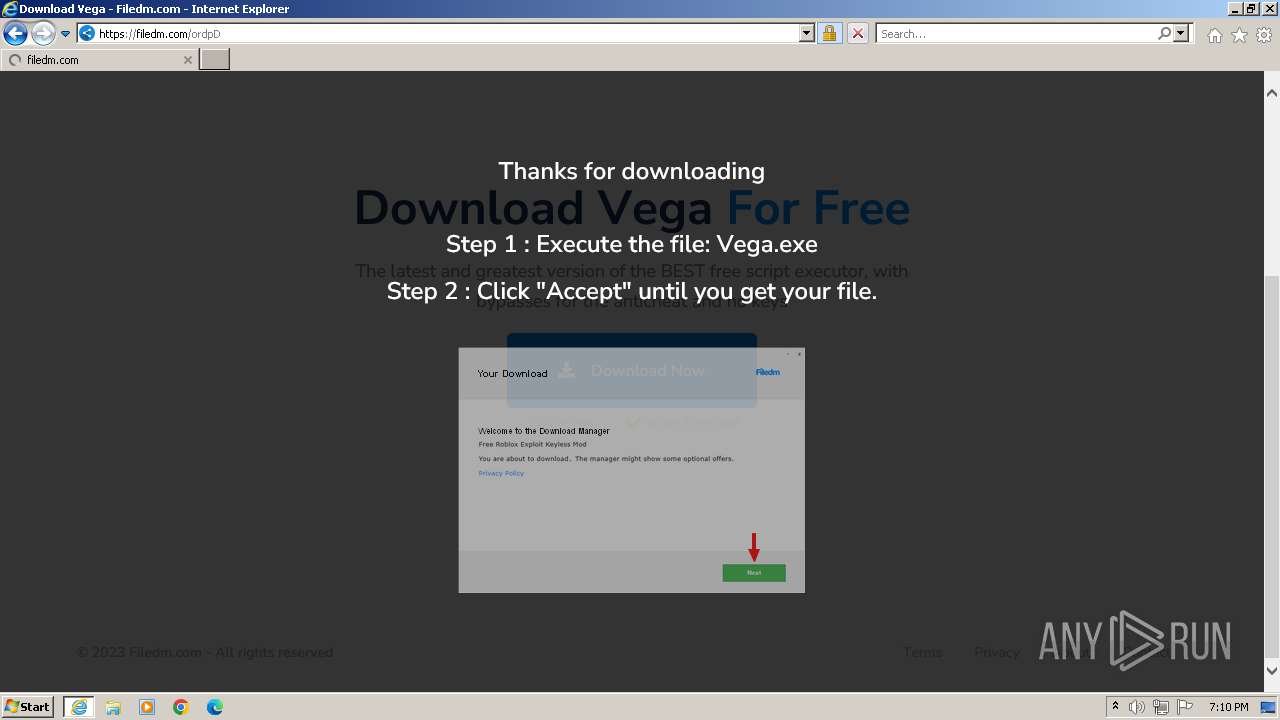
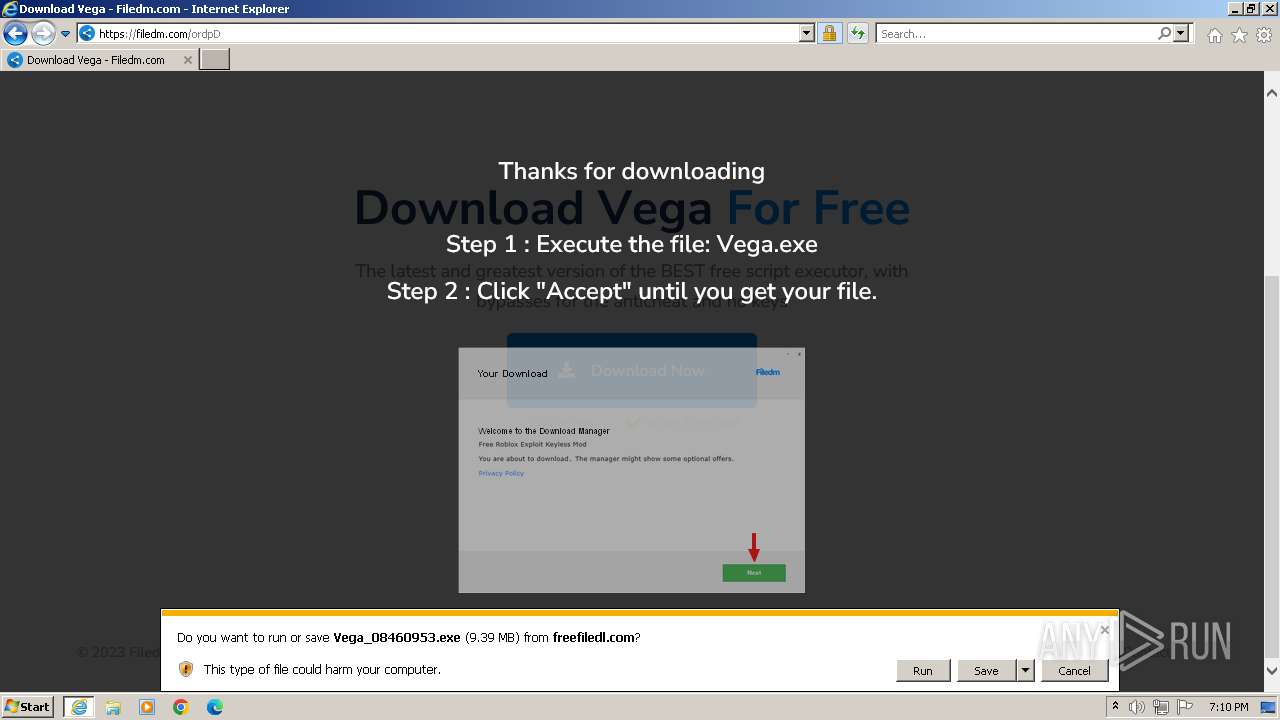
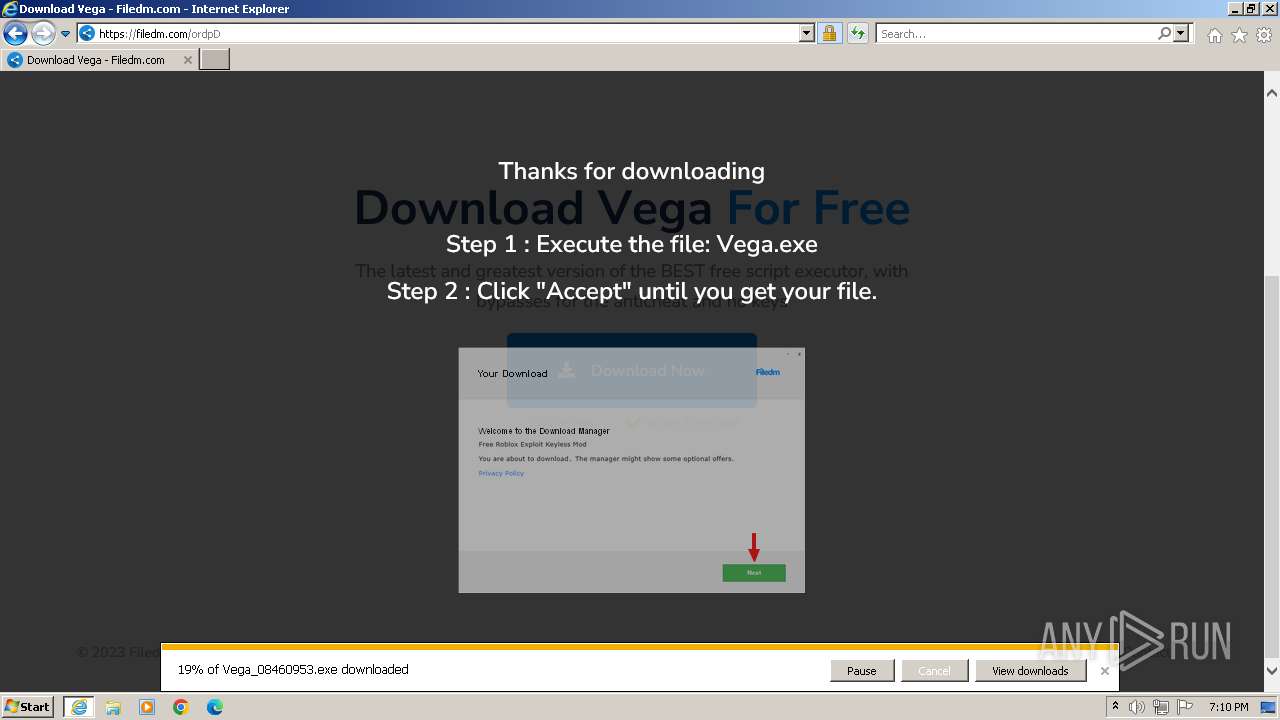
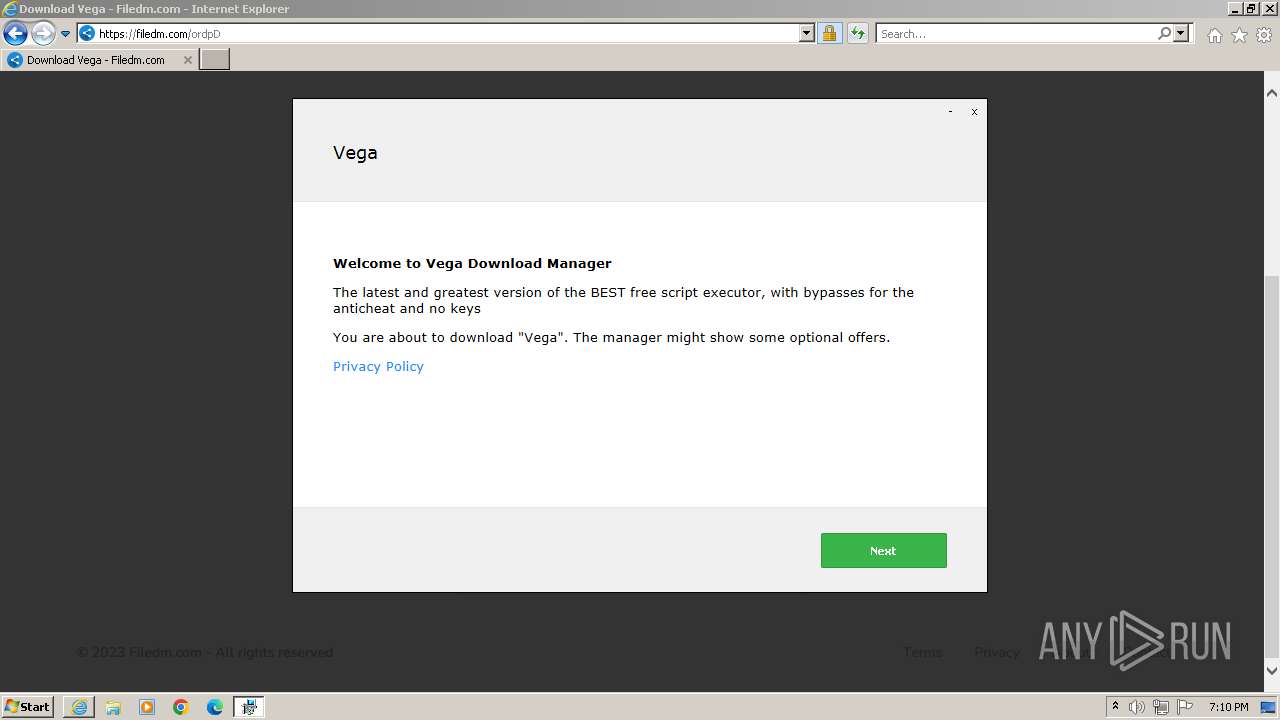
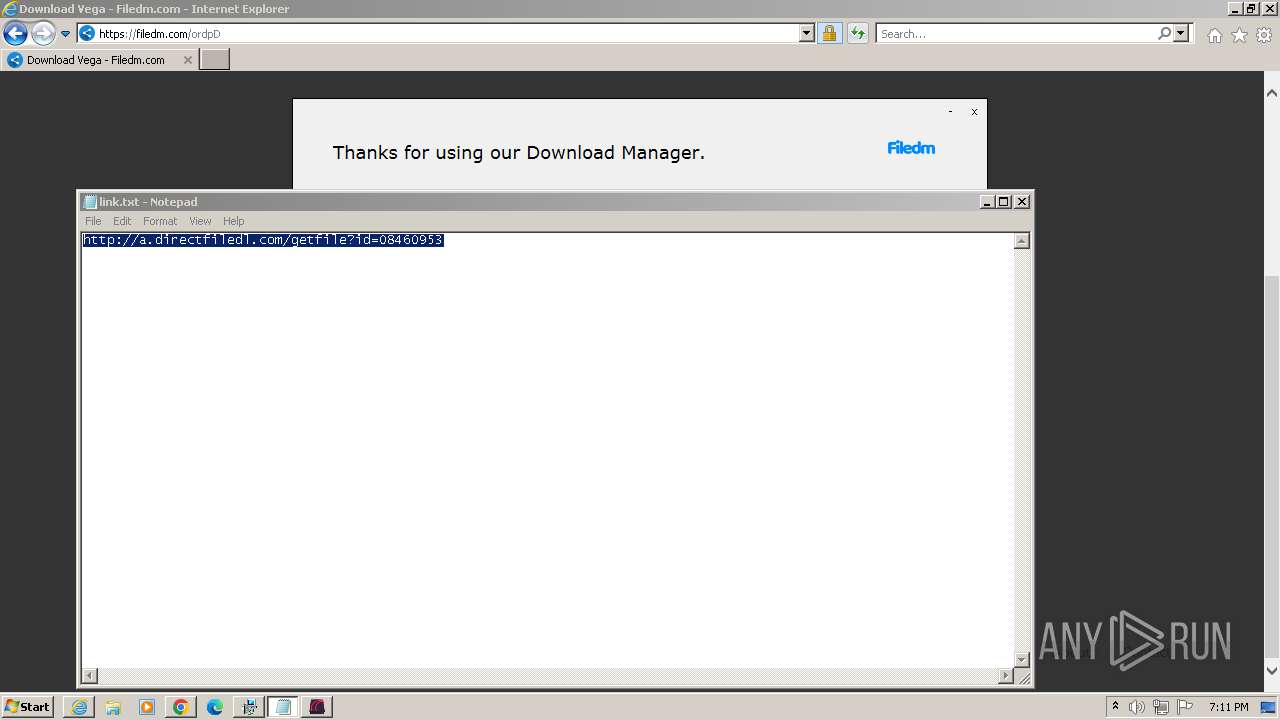
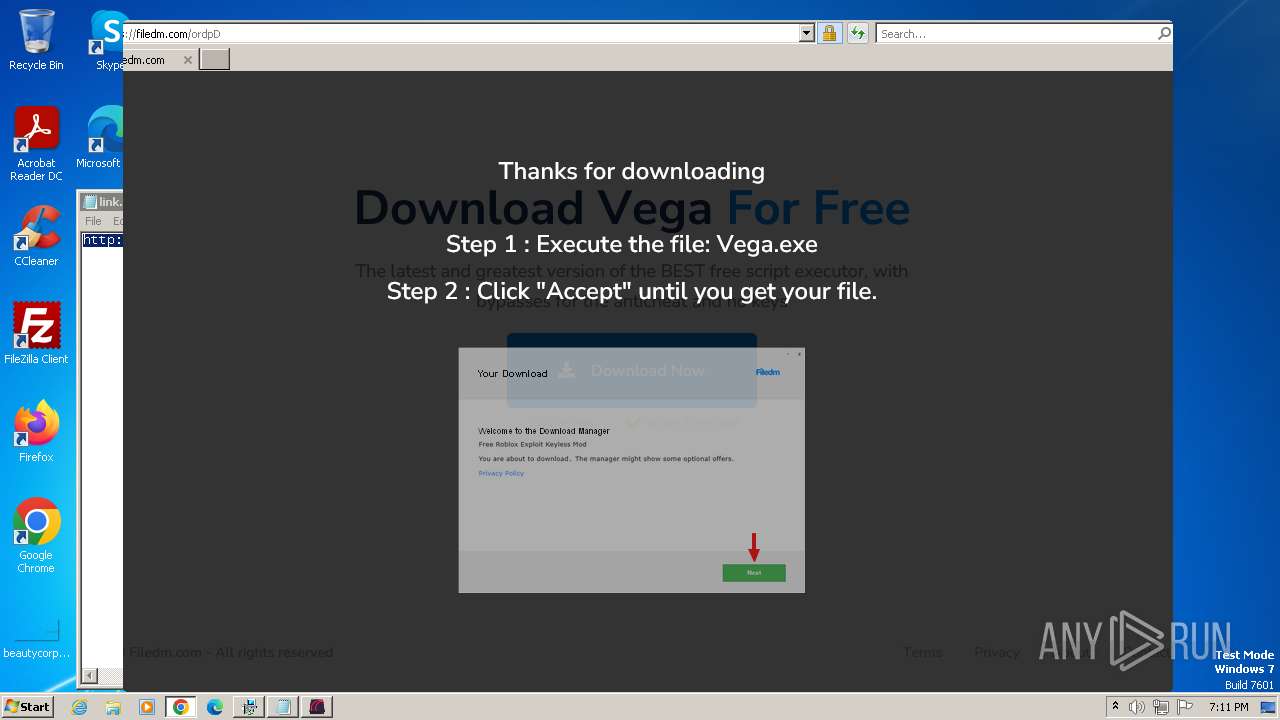
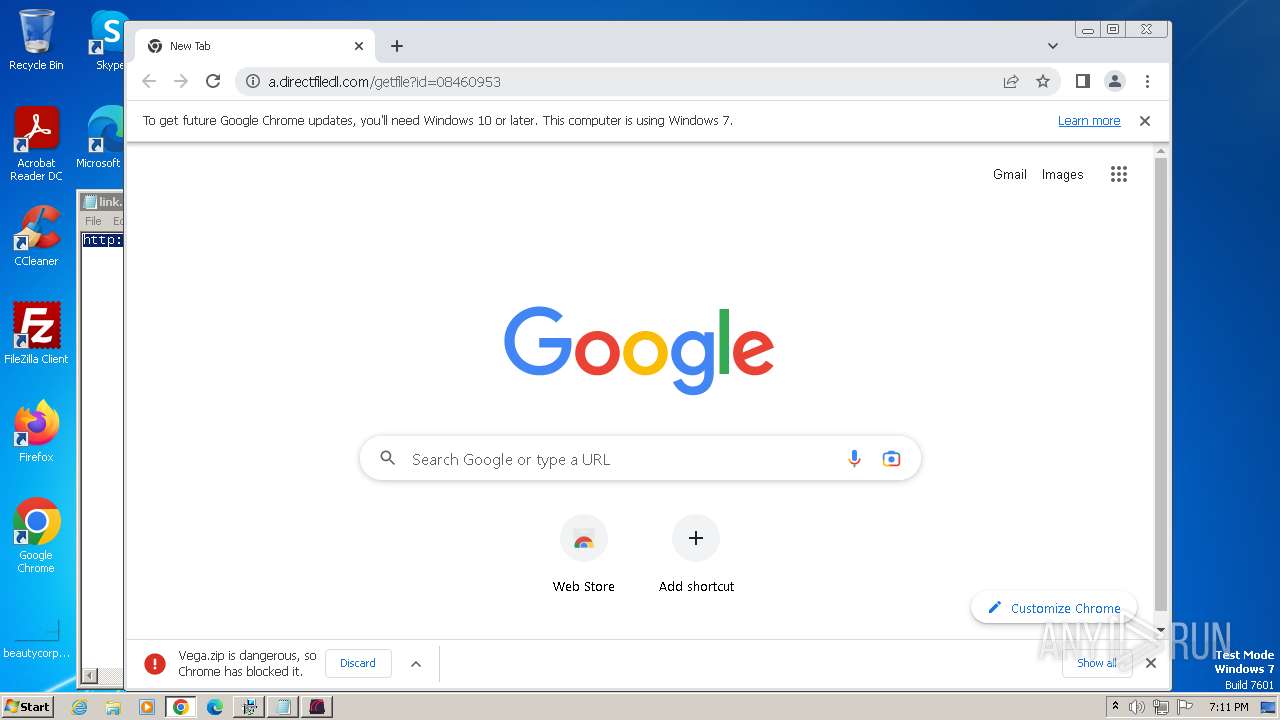
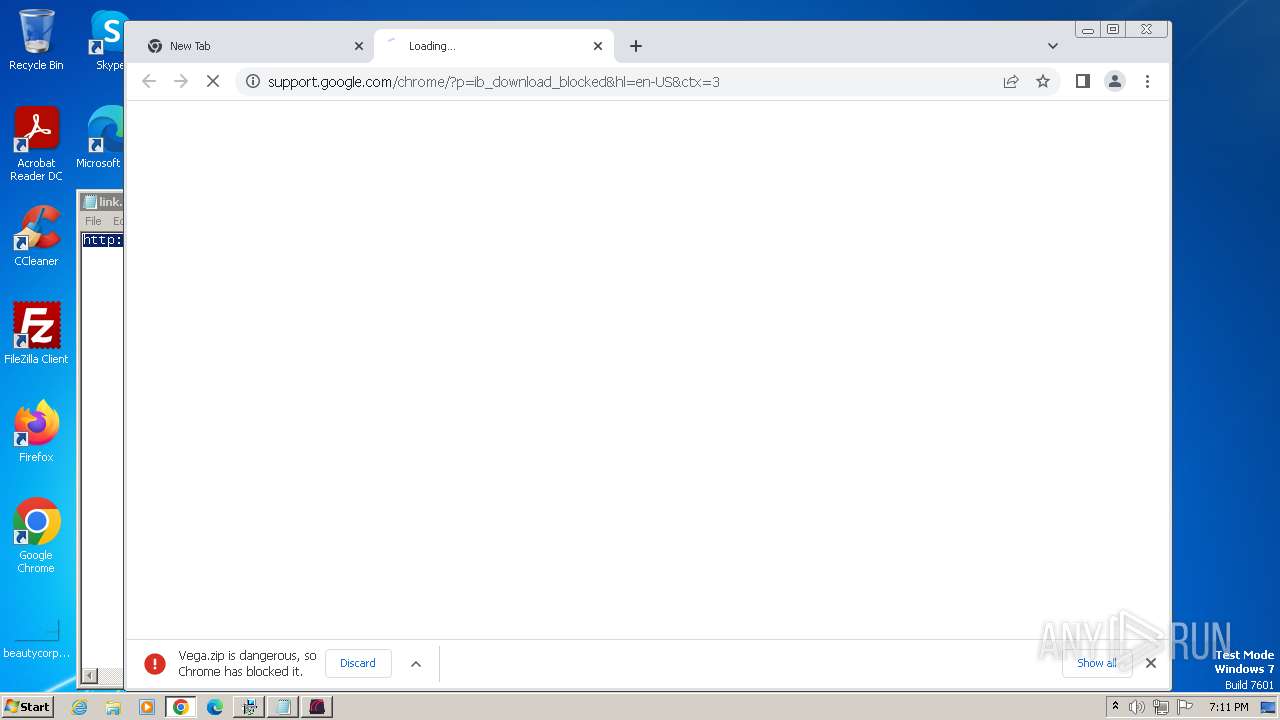
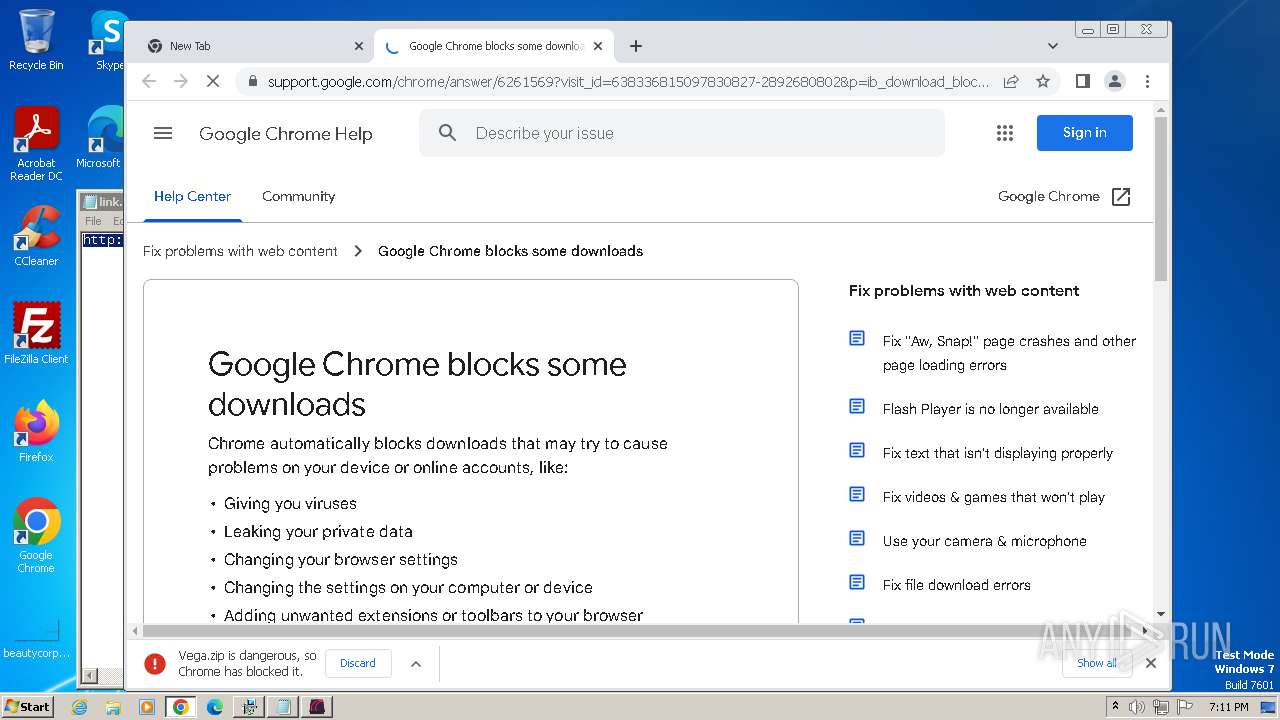
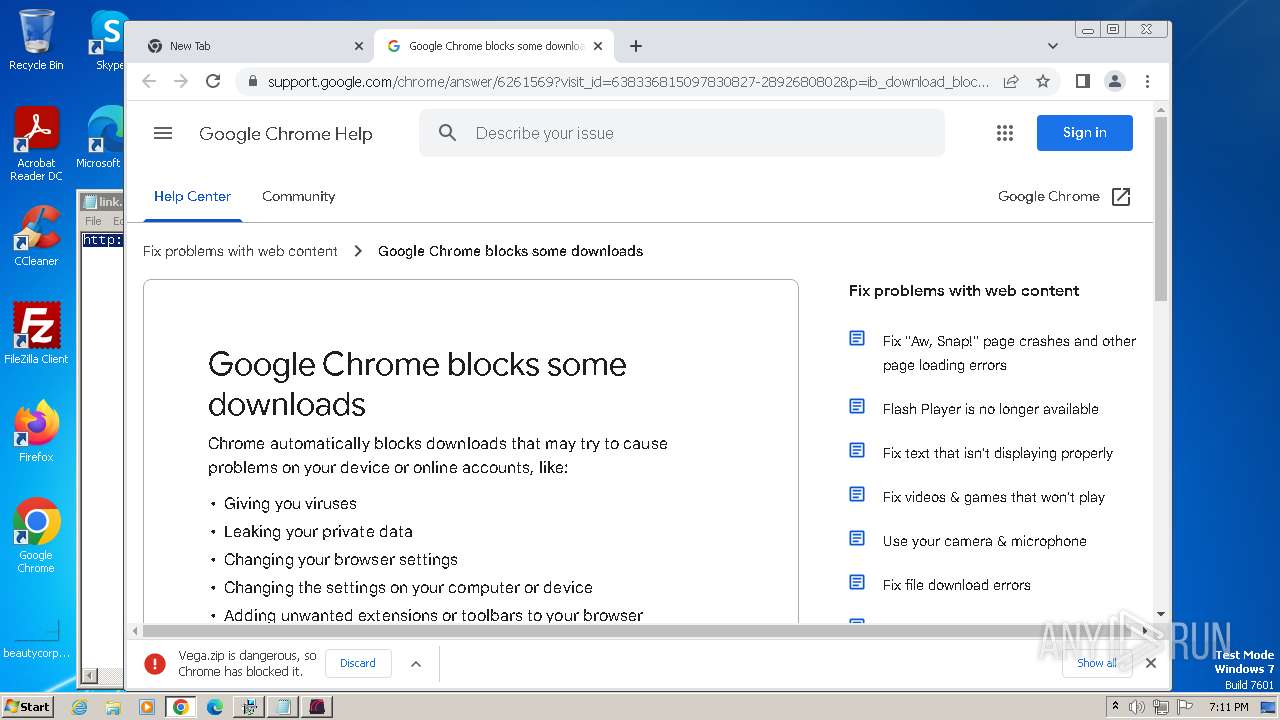
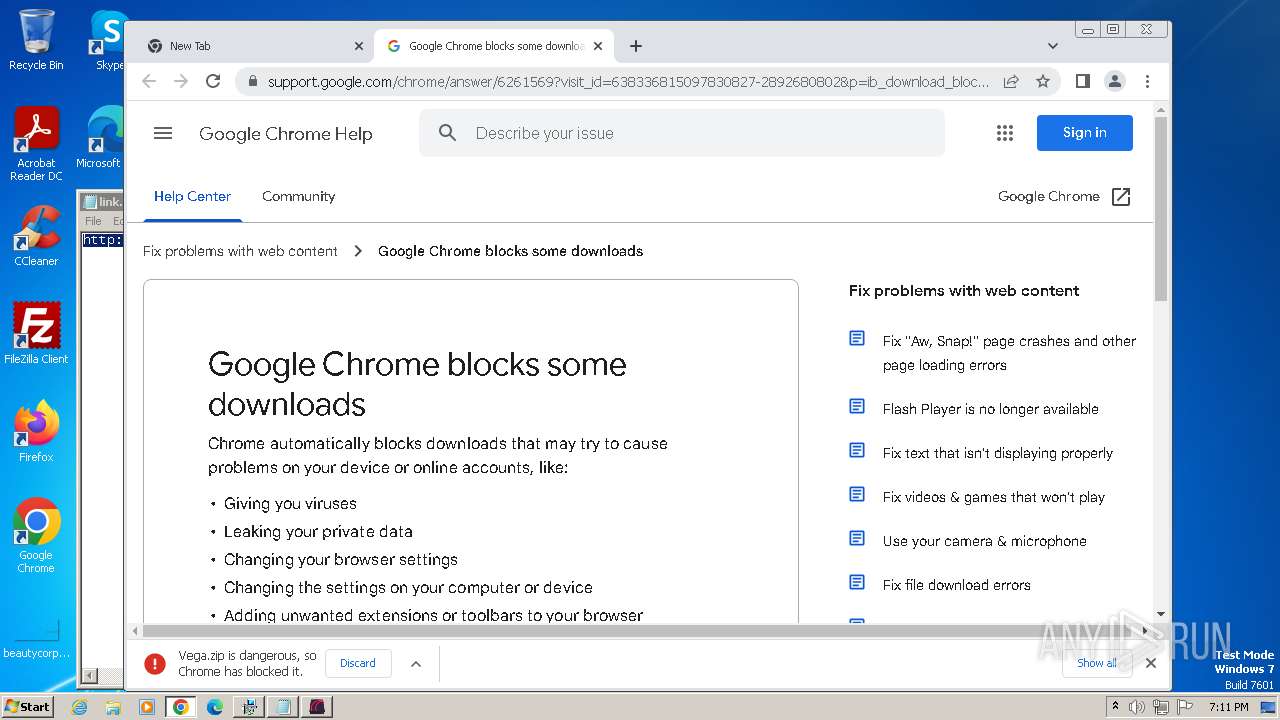
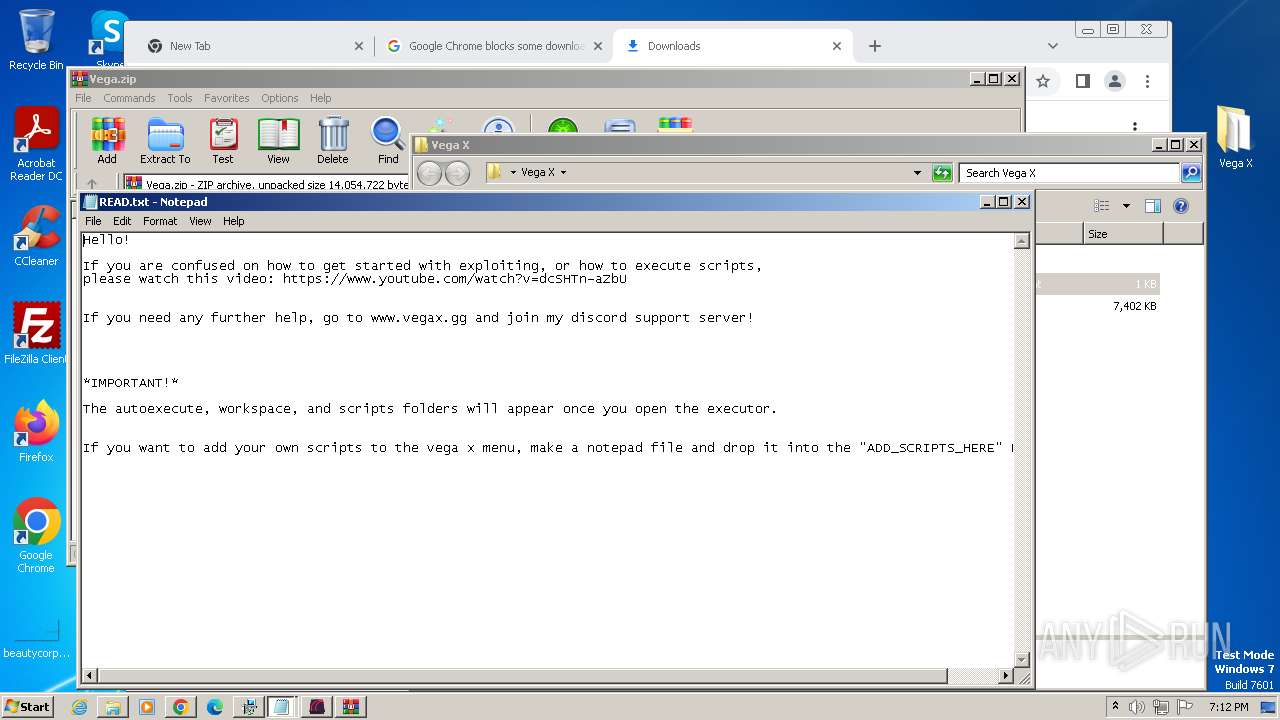
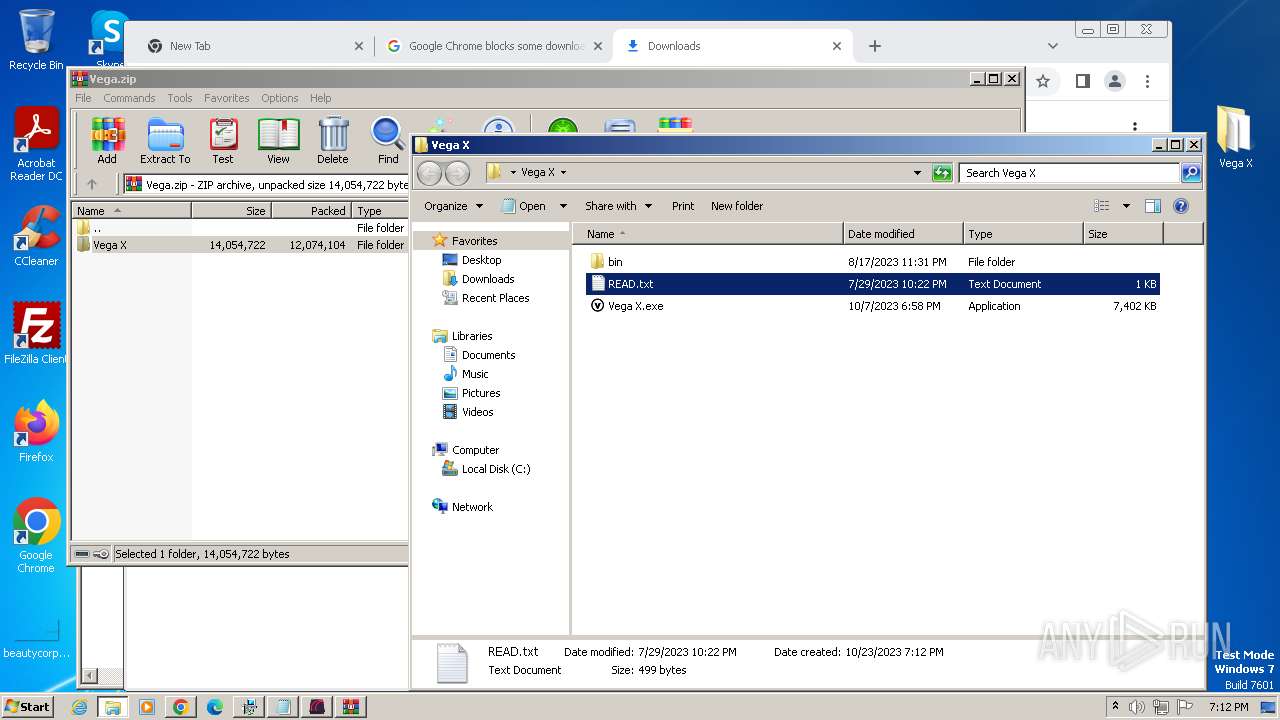
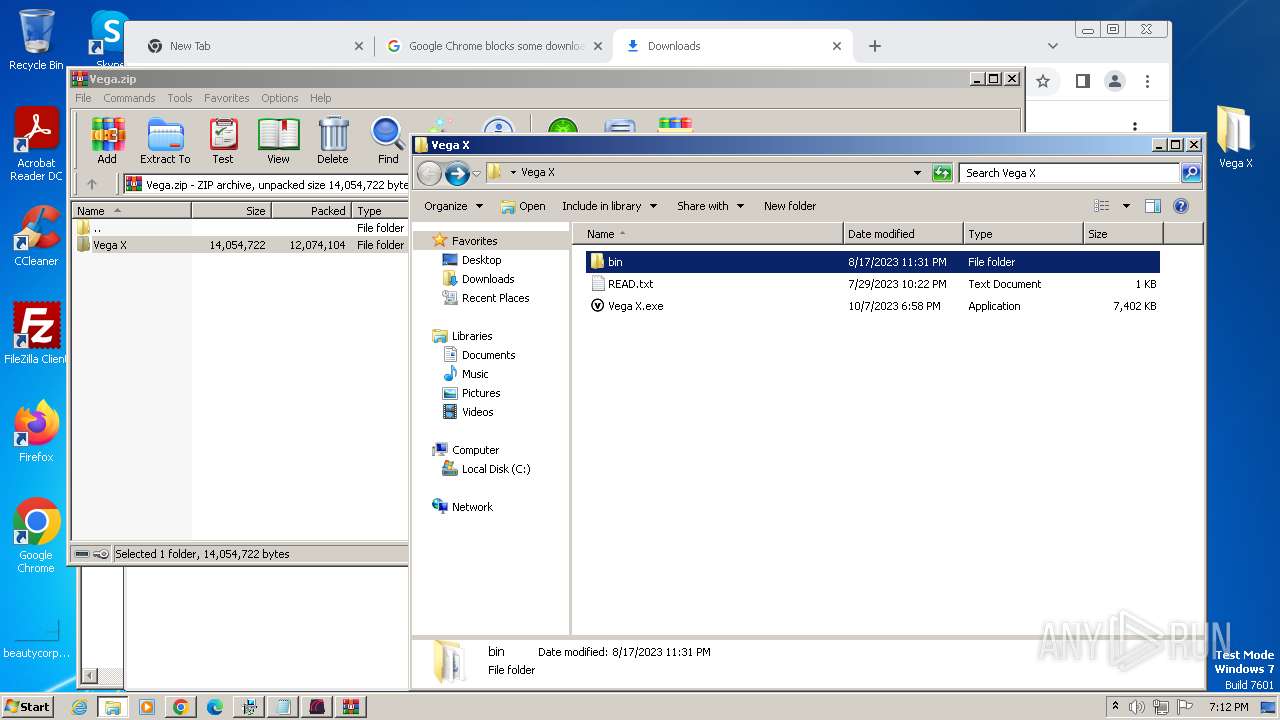
| URL: | https://vegax.gg |
| Full analysis: | https://app.any.run/tasks/1e6e3739-f211-4f17-935c-eb4220db15c2 |
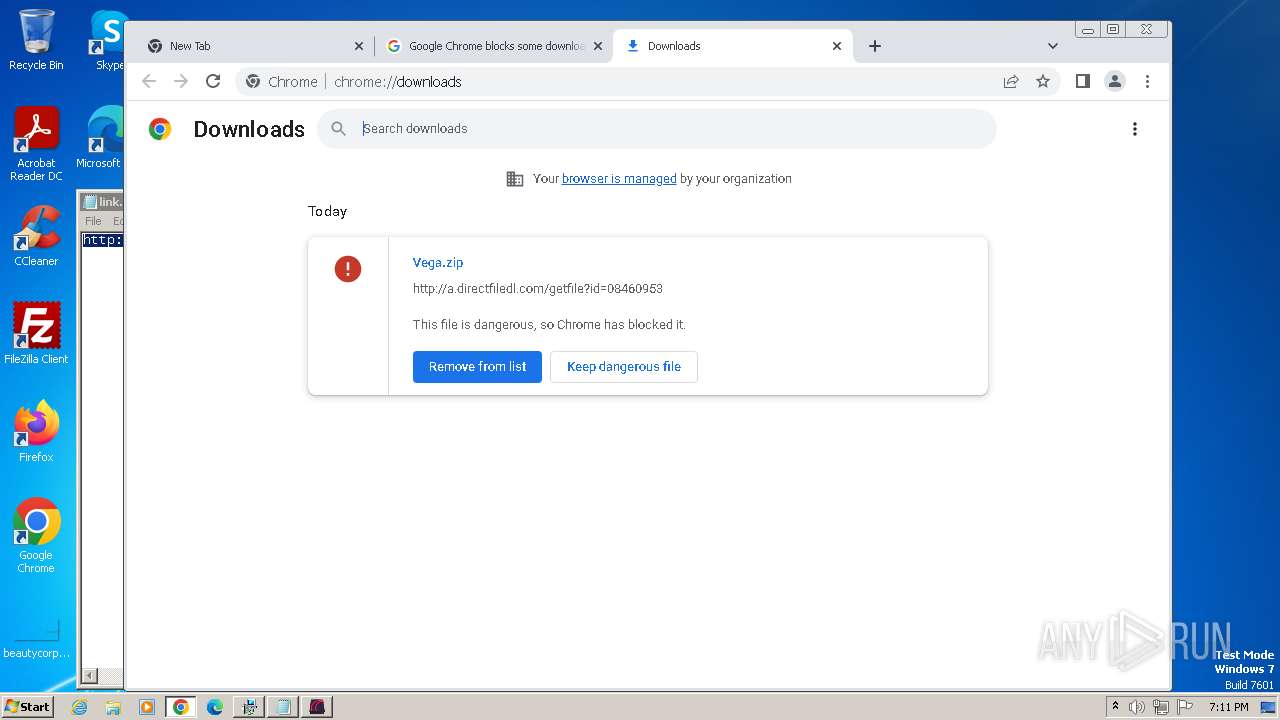
| Verdict: | Malicious activity |
| Analysis date: | October 23, 2023, 18:09:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 29965BD44BACB0DEBC3DAE584AA45488 |
| SHA1: | 42DB82C3C77F4B1974FEAFD7BDF38C897ACEF52F |
| SHA256: | 7E4E9B7D8C69DBE80BCD3D155A1092A8268AA50C2E16B568D948CF00C4032F73 |
| SSDEEP: | 3:N8h0ln:2h0ln |
MALICIOUS
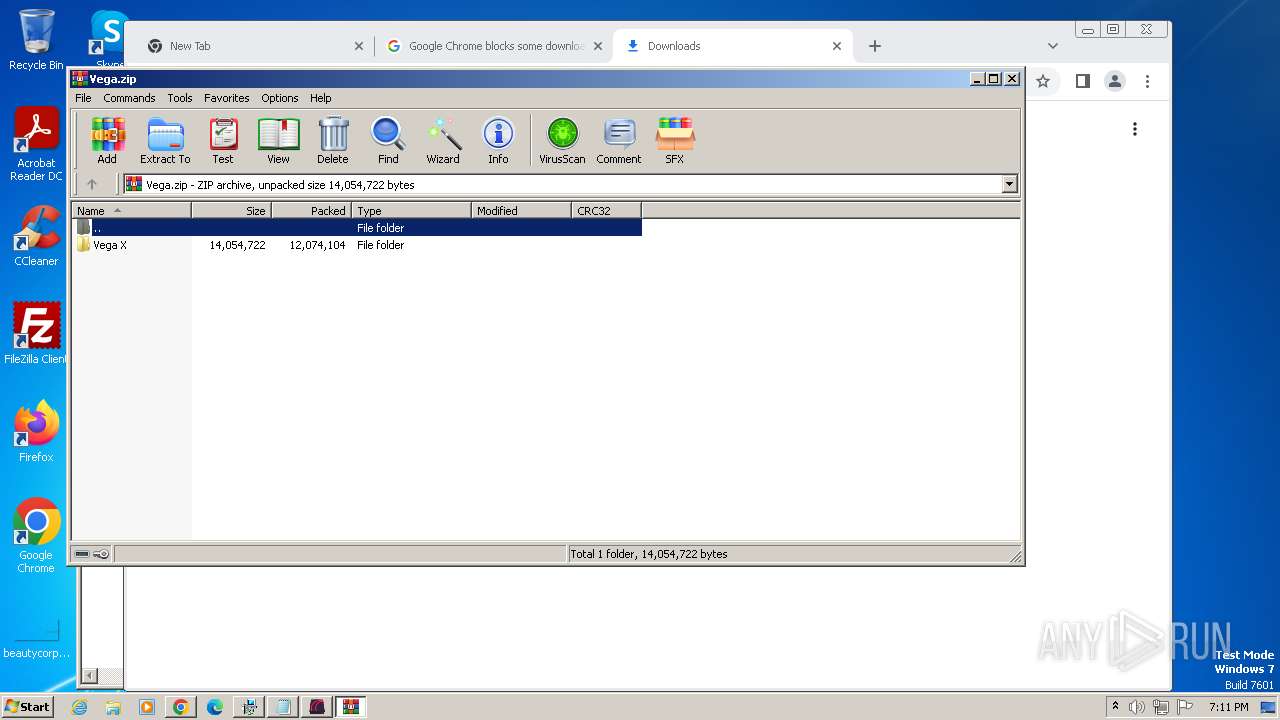
Application was dropped or rewritten from another process
- Vega_08460953.exe (PID: 292)
- Vega_08460953.exe (PID: 2356)
- setup08460953.exe (PID: 3612)
- setup08460953.exe (PID: 3724)
- OperaGX.exe (PID: 2940)
- Vega X.exe (PID: 1880)
- Vega X.exe (PID: 4088)
Drops the executable file immediately after the start
- Vega_08460953.exe (PID: 2356)
- setup08460953.exe (PID: 3612)
- OperaGX.exe (PID: 2940)
Actions looks like stealing of personal data
- setup08460953.exe (PID: 3612)
Loads dropped or rewritten executable
- setup08460953.exe (PID: 3724)
- setup08460953.exe (PID: 3612)
SUSPICIOUS
Reads the Internet Settings
- Vega_08460953.exe (PID: 2356)
- setup08460953.exe (PID: 3612)
- setup08460953.exe (PID: 3724)
Reads settings of System Certificates
- Vega_08460953.exe (PID: 2356)
- setup08460953.exe (PID: 3612)
Reads security settings of Internet Explorer
- Vega_08460953.exe (PID: 2356)
- setup08460953.exe (PID: 3612)
The process drops C-runtime libraries
- setup08460953.exe (PID: 3612)
Checks Windows Trust Settings
- Vega_08460953.exe (PID: 2356)
- setup08460953.exe (PID: 3612)
Process drops legitimate windows executable
- setup08460953.exe (PID: 3612)
Reads the Windows owner or organization settings
- setup08460953.exe (PID: 3612)
Adds/modifies Windows certificates
- Vega_08460953.exe (PID: 2356)
- iexplore.exe (PID: 3820)
Searches for installed software
- setup08460953.exe (PID: 3612)
Starts CMD.EXE for commands execution
- setup08460953.exe (PID: 3612)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1616)
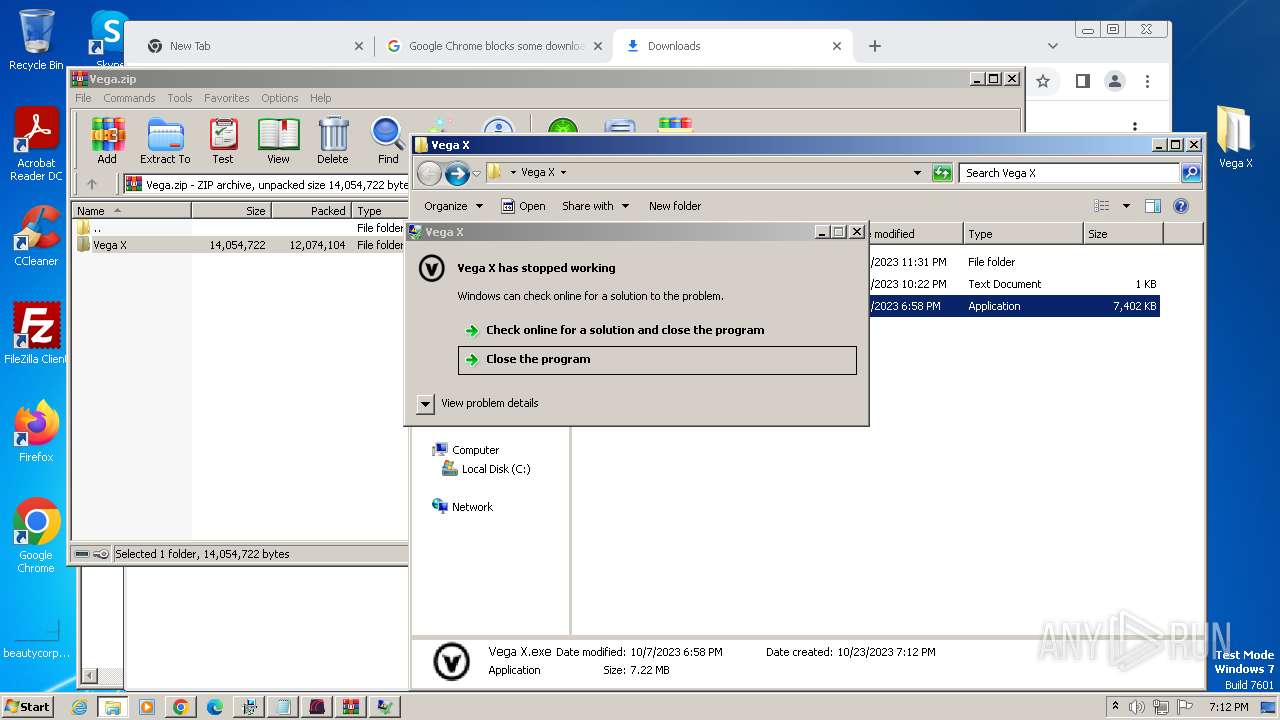
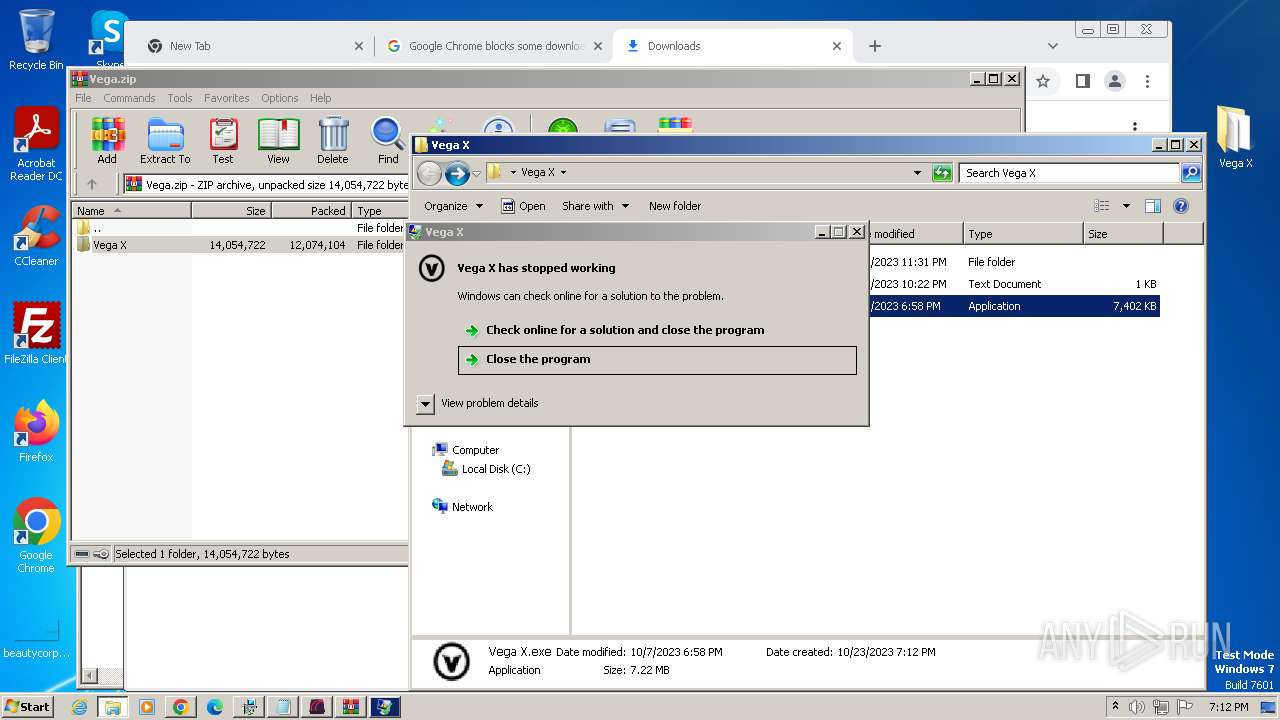
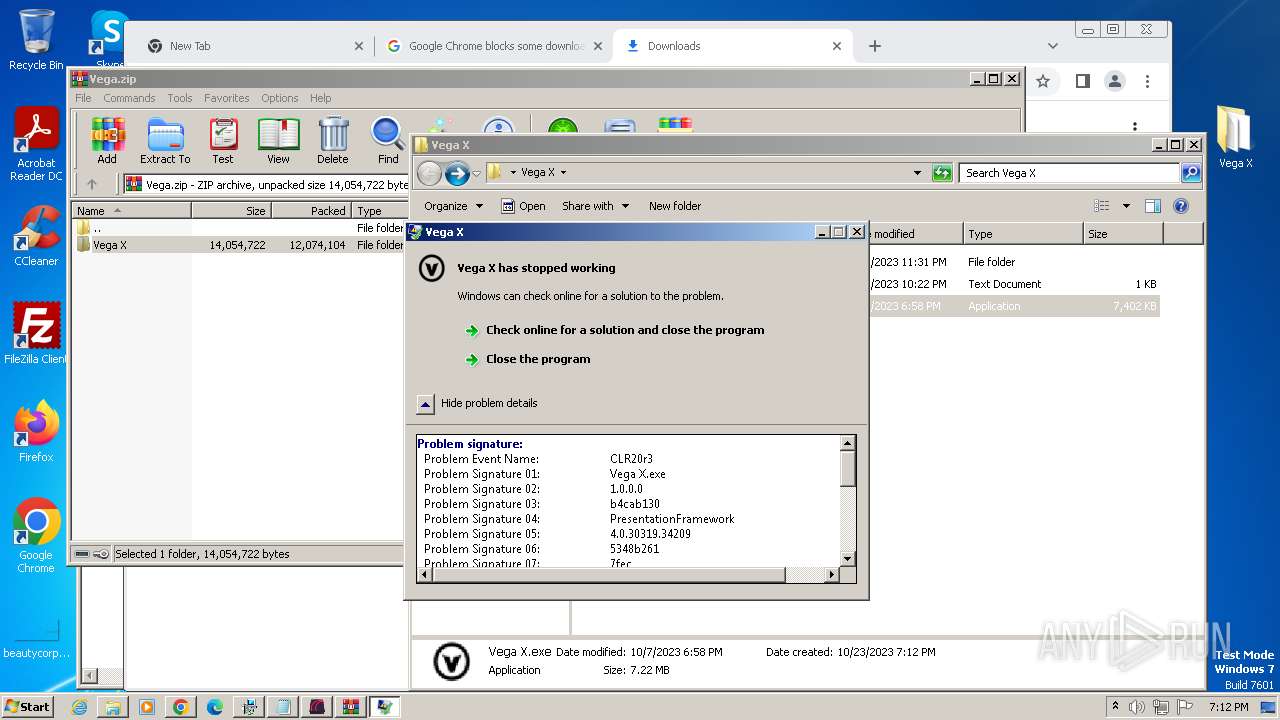
Start notepad (likely ransomware note)
- Vega_08460953.exe (PID: 2356)
Executing commands from a ".bat" file
- setup08460953.exe (PID: 3612)
Get information on the list of running processes
- cmd.exe (PID: 1616)
INFO
The process uses the downloaded file
- iexplore.exe (PID: 3820)
- chrome.exe (PID: 1336)
- chrome.exe (PID: 3760)
- WinRAR.exe (PID: 240)
- chrome.exe (PID: 3324)
- chrome.exe (PID: 3184)
Application launched itself
- iexplore.exe (PID: 3820)
- chrome.exe (PID: 2552)
Checks supported languages
- Vega_08460953.exe (PID: 2356)
- setup08460953.exe (PID: 3612)
- setup08460953.exe (PID: 3724)
- OperaGX.exe (PID: 2940)
- Vega X.exe (PID: 1880)
- Vega X.exe (PID: 4088)
Reads the computer name
- Vega_08460953.exe (PID: 2356)
- setup08460953.exe (PID: 3612)
- setup08460953.exe (PID: 3724)
- Vega X.exe (PID: 4088)
- Vega X.exe (PID: 1880)
Checks proxy server information
- Vega_08460953.exe (PID: 2356)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3820)
- iexplore.exe (PID: 1560)
- WinRAR.exe (PID: 240)
- chrome.exe (PID: 3324)
Reads the machine GUID from the registry
- Vega_08460953.exe (PID: 2356)
- setup08460953.exe (PID: 3612)
- setup08460953.exe (PID: 3724)
- Vega X.exe (PID: 4088)
- Vega X.exe (PID: 1880)
Create files in a temporary directory
- setup08460953.exe (PID: 3612)
- setup08460953.exe (PID: 3724)
- OperaGX.exe (PID: 2940)
Creates files or folders in the user directory
- Vega_08460953.exe (PID: 2356)
- setup08460953.exe (PID: 3612)
- OperaGX.exe (PID: 2940)
Reads Environment values
- setup08460953.exe (PID: 3612)
Reads product name
- setup08460953.exe (PID: 3612)
Manual execution by a user
- notepad.exe (PID: 2888)
- Vega X.exe (PID: 1880)
- chrome.exe (PID: 2552)
- Vega X.exe (PID: 4088)
- notepad.exe (PID: 2224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
99
Monitored processes
49
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Vega.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | chrome.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 292 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\Vega_08460953.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\Vega_08460953.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Download Manager Exit code: 3221226540 Version: 1 Modules
| |||||||||||||||
| 948 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=540 --field-trial-handle=1152,i,13955448648296297026,963670922848943005,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1012 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6acf8b38,0x6acf8b48,0x6acf8b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=20 --mojo-platform-channel-handle=4132 --field-trial-handle=1152,i,13955448648296297026,963670922848943005,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1052 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=21 --mojo-platform-channel-handle=4312 --field-trial-handle=1152,i,13955448648296297026,963670922848943005,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1336 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4196 --field-trial-handle=1152,i,13955448648296297026,963670922848943005,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1396 | timeout 5 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1560 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3820 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1616 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\H2OCleanup.bat"" | C:\Windows\System32\cmd.exe | — | setup08460953.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
40 586
Read events
40 272
Write events
308
Delete events
6
Modification events
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
39
Suspicious files
455
Text files
98
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:10E74C7624DA6D40F31C050EDA3988B9 | SHA256:4217CD62ED5208BA0E544316DD11F75C3EDF441765EB4973FC5A4A692AFC6C6E | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:ECC91BD26FE464752A98AC31642FCFE7 | SHA256:1ECA1A8E470F492DEDEADB5556BD29991FBAA0A4C1DC6289147643EEE33EE002 | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabC15C.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabC13A.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:60FE01DF86BE2E5331B0CDBE86165686 | SHA256:C08CCBC876CD5A7CDFA9670F9637DA57F6A1282198A9BC71FC7D7247A6E5B7A8 | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6688704DF53F38A6D7FEE74E6C9BEEA9 | binary | |
MD5:22544679071D1D1502C5D2F7ACB9983F | SHA256:11694B8335FAF285A631DB1111F1B3CF4EE8799FC4F5191A79F407ADD0A63BAA | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\fontawesome-all.min[1].css | text | |
MD5:E0076D9B1984448E1B530D5B1A419C7A | SHA256:19BC4712BCA32DB280000F294E2D0C1DC178063A9DD4278FC22D30A39C068846 | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:D5A226F4E74FEC74F6F4B632CF85CD1A | SHA256:6CB259F68ECE722EA2D21A600960825F785F35400AB91F1330187D598DA3FC9F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
42
TCP/UDP connections
118
DNS requests
95
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1560 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ab6c62e3d2bbc5b0 | unknown | compressed | 4.66 Kb | unknown |
3820 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1560 | iexplore.exe | GET | 200 | 142.251.141.35:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
1560 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?7147a541e8aecbd1 | unknown | compressed | 61.6 Kb | unknown |
1560 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?060020e49c501eb3 | unknown | compressed | 4.66 Kb | unknown |
1560 | iexplore.exe | GET | 200 | 2.19.198.179:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgTMYVt80scUTq7%2FjMZCNFW%2BRA%3D%3D | unknown | der | 503 b | unknown |
1560 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?5a9de4fb6882b969 | unknown | compressed | 61.6 Kb | unknown |
1560 | iexplore.exe | GET | 200 | 23.212.210.158:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
1560 | iexplore.exe | GET | 200 | 142.251.141.35:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
1560 | iexplore.exe | GET | 200 | 142.251.141.35:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQD50q2MxTvdnxLfPCm8%2F51a | unknown | binary | 472 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1560 | iexplore.exe | 194.233.168.129:443 | — | Linode, LLC | DE | unknown |
1560 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
1560 | iexplore.exe | 23.212.210.158:80 | x1.c.lencr.org | AKAMAI-AS | AU | unknown |
1560 | iexplore.exe | 2.19.198.179:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
1560 | iexplore.exe | 216.58.213.106:443 | fonts.googleapis.com | GOOGLE | US | unknown |
1560 | iexplore.exe | 142.251.141.35:80 | ocsp.pki.goog | GOOGLE | US | unknown |
1560 | iexplore.exe | 172.217.20.67:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
3820 | iexplore.exe | 194.233.168.129:443 | — | Linode, LLC | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
fonts.googleapis.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
filedm.com |
| malicious |
x2.c.lencr.org |
| whitelisted |
Threats
9 ETPRO signatures available at the full report
Process | Message |
|---|---|
setup08460953.exe | |
setup08460953.exe | file:resources/tis/TranslateOfferTemplate.tis(82) : warning :'async' does not contain any 'await'
|
setup08460953.exe | at sciter:init-script.tis
|
setup08460953.exe | Error: File not found - sciterwrapper:console.tis
|
setup08460953.exe | |
setup08460953.exe | |
setup08460953.exe | |
setup08460953.exe | Error: File not found - sciterwrapper:console.tis
|
setup08460953.exe | at sciter:init-script.tis
|
setup08460953.exe | file:resources/tis/TranslateOfferTemplate.tis(82) : warning :'async' does not contain any 'await'
|