| File name: | system_update_5.07.0137.exe |
| Full analysis: | https://app.any.run/tasks/37915af0-e141-4a64-8485-348ba96cbc12 |
| Verdict: | Malicious activity |
| Analysis date: | October 04, 2022, 21:12:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1713404B182B6D805A343E4B69F9FED6 |
| SHA1: | 2E27C18A7F6F651CB592072D1E2086B598ECC238 |
| SHA256: | 7E2AD5283C76B44A3569CDC19DA043F7C7B316C50DC182735395649545B4E474 |
| SSDEEP: | 196608:J0L4TTmH80P95voMHMgdEfzoYuPo8ivBLdpa6cV7aoo:JByH80bldE3Wo8ivnpPco |
MALICIOUS
Drops executable file immediately after starts
- system_update_5.07.0137.exe (PID: 3188)
- system_update_5.07.0137.exe (PID: 4080)
- system_update_5.07.0137.tmp (PID: 1984)
Application was dropped or rewritten from another process
- system_update_5.07.0137.tmp (PID: 1984)
- StartSuService.exe (PID: 2492)
- SUService.exe (PID: 2768)
- susetsched.exe (PID: 3112)
- ConfigScheduledTask.exe (PID: 3724)
- uncsetting.exe (PID: 1320)
- ConfigService.exe (PID: 1948)
- TVSU2DirAllowWriting.exe (PID: 3496)
Loads dropped or rewritten executable
- InstallUtil.exe (PID: 2180)
- SUService.exe (PID: 2768)
Loads the Task Scheduler COM API
- susetsched.exe (PID: 3112)
- schtasks.exe (PID: 292)
- schtasks.exe (PID: 4036)
Uses Task Scheduler to run other applications
- ConfigScheduledTask.exe (PID: 3724)
Changes settings of System certificates
- certutil.exe (PID: 3080)
- certutil.exe (PID: 3460)
SUSPICIOUS
Checks supported languages
- system_update_5.07.0137.exe (PID: 3188)
- system_update_5.07.0137.exe (PID: 4080)
- system_update_5.07.0137.tmp (PID: 3140)
- cmd.exe (PID: 3104)
- cmd.exe (PID: 328)
- InstallUtil.exe (PID: 2180)
- StartSuService.exe (PID: 2492)
- SUService.exe (PID: 2768)
- susetsched.exe (PID: 3112)
- ConfigScheduledTask.exe (PID: 3724)
- uncsetting.exe (PID: 1320)
- ConfigService.exe (PID: 1948)
- system_update_5.07.0137.tmp (PID: 1984)
- cmd.exe (PID: 1584)
- TVSU2DirAllowWriting.exe (PID: 3496)
Executable content was dropped or overwritten
- system_update_5.07.0137.exe (PID: 3188)
- system_update_5.07.0137.exe (PID: 4080)
- system_update_5.07.0137.tmp (PID: 1984)
Drops a file with a compile date too recent
- system_update_5.07.0137.exe (PID: 3188)
- system_update_5.07.0137.exe (PID: 4080)
- system_update_5.07.0137.tmp (PID: 1984)
Reads the Windows organization settings
- system_update_5.07.0137.tmp (PID: 1984)
Removes files from Windows directory
- system_update_5.07.0137.tmp (PID: 1984)
- certutil.exe (PID: 3080)
- certutil.exe (PID: 3460)
- system_update_5.07.0137.exe (PID: 4080)
Reads Windows owner or organization settings
- system_update_5.07.0137.tmp (PID: 1984)
Reads the computer name
- system_update_5.07.0137.tmp (PID: 1984)
- system_update_5.07.0137.tmp (PID: 3140)
- InstallUtil.exe (PID: 2180)
- StartSuService.exe (PID: 2492)
- SUService.exe (PID: 2768)
- uncsetting.exe (PID: 1320)
- susetsched.exe (PID: 3112)
- ConfigScheduledTask.exe (PID: 3724)
- ConfigService.exe (PID: 1948)
Starts application with an unusual extension
- system_update_5.07.0137.exe (PID: 4080)
Creates files in the Windows directory
- system_update_5.07.0137.exe (PID: 4080)
- InstallUtil.exe (PID: 2180)
- system_update_5.07.0137.tmp (PID: 1984)
- certutil.exe (PID: 3080)
- certutil.exe (PID: 3460)
Starts CMD.EXE for commands execution
- system_update_5.07.0137.tmp (PID: 1984)
- cmd.exe (PID: 3104)
Application launched itself
- cmd.exe (PID: 3104)
Creates a directory in Program Files
- system_update_5.07.0137.tmp (PID: 1984)
Creates a software uninstall entry
- system_update_5.07.0137.tmp (PID: 1984)
Changes default file association
- system_update_5.07.0137.tmp (PID: 1984)
Creates files in the program directory
- InstallUtil.exe (PID: 2180)
- StartSuService.exe (PID: 2492)
- SUService.exe (PID: 2768)
- ConfigScheduledTask.exe (PID: 3724)
- system_update_5.07.0137.tmp (PID: 1984)
Creates or modifies windows services
- InstallUtil.exe (PID: 2180)
Executed as Windows Service
- SUService.exe (PID: 2768)
Uses ICACLS.EXE to modify access control list
- SUService.exe (PID: 2768)
Uses NETSH.EXE for network configuration
- uncsetting.exe (PID: 1320)
Reads Environment values
- system_update_5.07.0137.tmp (PID: 1984)
- netsh.exe (PID: 528)
- netsh.exe (PID: 3964)
INFO
Application was dropped or rewritten from another process
- system_update_5.07.0137.tmp (PID: 3140)
Checks supported languages
- findstr.exe (PID: 3452)
- icacls.exe (PID: 3036)
- netsh.exe (PID: 3964)
- schtasks.exe (PID: 292)
- certutil.exe (PID: 3080)
- certutil.exe (PID: 3460)
- netsh.exe (PID: 528)
- schtasks.exe (PID: 4036)
- opera.exe (PID: 1088)
Reads the computer name
- icacls.exe (PID: 3036)
- netsh.exe (PID: 3964)
- certutil.exe (PID: 3080)
- certutil.exe (PID: 3460)
- schtasks.exe (PID: 4036)
- netsh.exe (PID: 528)
- opera.exe (PID: 1088)
- schtasks.exe (PID: 292)
Reads settings of System Certificates
- certutil.exe (PID: 3460)
- certutil.exe (PID: 3080)
Manual execution by user
- opera.exe (PID: 1088)
Check for Java to be installed
- opera.exe (PID: 1088)
Reads the date of Windows installation
- opera.exe (PID: 1088)
Creates files in the user directory
- opera.exe (PID: 1088)
Dropped object may contain Bitcoin addresses
- opera.exe (PID: 1088)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (79.7) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (8.6) |
| .exe | | | Win16/32 Executable Delphi generic (3.9) |
| .exe | | | Generic Win/DOS Executable (3.8) |
| .exe | | | DOS Executable Generic (3.8) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2020-Jan-06 06:31:46 |
| Detected languages: |
|
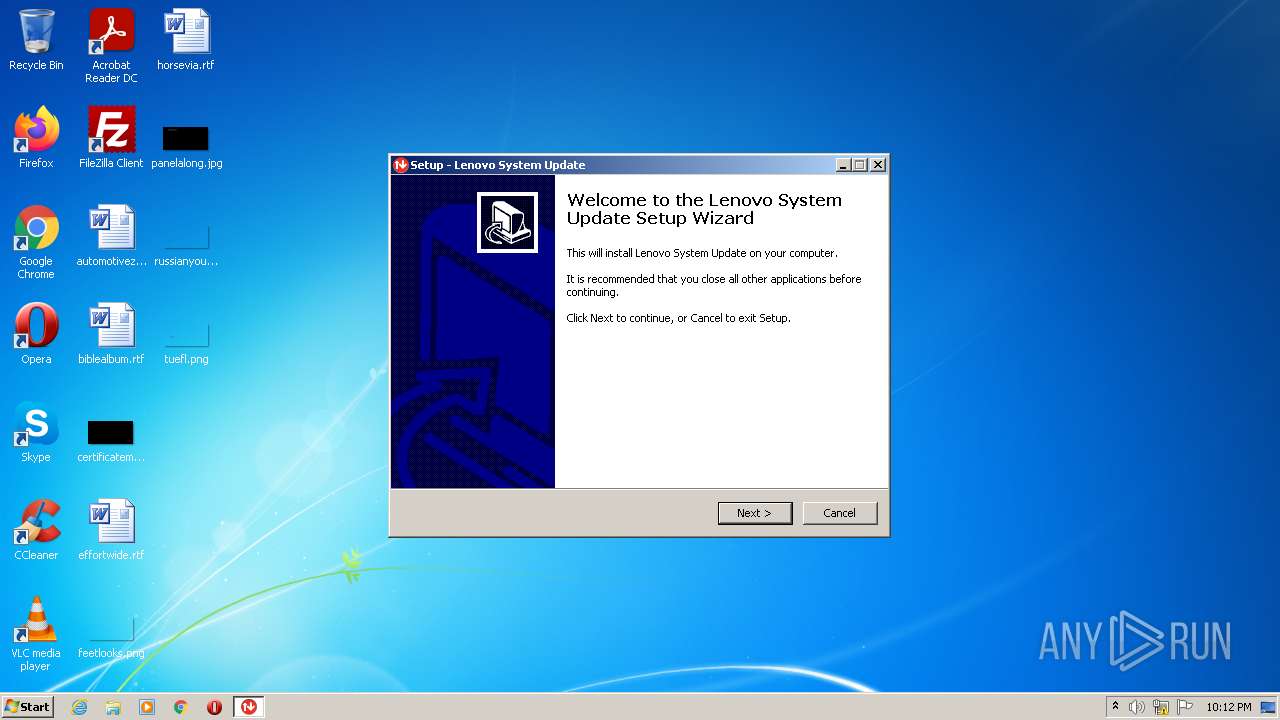
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Lenovo |
| FileDescription: | Lenovo System Update Setup |
| FileVersion: | 5.07.0137 |
| LegalCopyright: | - |
| ProductName: | Lenovo System Update |
| ProductVersion: | 5.07.0137 |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 80 |
| e_cp: | 2 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | 15 |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | 26 |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 256 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 10 |
| TimeDateStamp: | 2020-Jan-06 06:31:46 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 4096 | 146080 | 146432 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.32291 |
.itext | 151552 | 4968 | 5120 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.91348 |
.data | 159744 | 5672 | 6144 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.32921 |
.bss | 167936 | 24920 | 0 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.idata | 196608 | 1608 | 2048 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.08948 |
.didata | 200704 | 3646 | 4096 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.2563 |
.edata | 204800 | 113 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.3265 |
.tls | 208896 | 20 | 0 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.rdata | 212992 | 93 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.37999 |
.rsrc | 217088 | 244204 | 244224 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.02788 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 2.41891 | 816 | Latin 1 / Western European | English - United States | RT_ICON |
2 | 3.30618 | 304 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 2.47581 | 176 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 7.73695 | 4201 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 2.79096 | 1640 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 3.20638 | 744 | Latin 1 / Western European | English - United States | RT_ICON |
7 | 3.31916 | 488 | Latin 1 / Western European | English - United States | RT_ICON |
8 | 3.25564 | 296 | Latin 1 / Western European | English - United States | RT_ICON |
9 | 7.93819 | 11287 | Latin 1 / Western European | English - United States | RT_ICON |
10 | 4.47867 | 3752 | Latin 1 / Western European | English - United States | RT_ICON |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
kernel32.dll (delay-loaded) |
oleaut32.dll |
user32.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
dbkFCallWrapperAddr | 1 | 181644 |
__dbk_fcall_wrapper | 2 | 45716 |
Total processes
70
Monitored processes
24
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | "C:\Windows\system32\schtasks.exe" /Create /TN "TVT\TVSUUpdateTask" /XML "C:\Program Files\Lenovo\System Update\tmpTVSUUpdateTask_Weekly.xml" /F | C:\Windows\system32\schtasks.exe | — | ConfigScheduledTask.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 328 | C:\Windows\system32\cmd.exe /S /D /c" dir /a /b "C:\Program Files\Lenovo\System Update"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 528 | "C:\Windows\system32\netsh.exe" advfirewall firewall add rule name="TvsuUNCServer" dir=out action=allow program="C:\Program Files\Lenovo\System Update\uncserver.exe" enable=yes profile=any protocol=UDP | C:\Windows\system32\netsh.exe | — | uncsetting.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1088 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | Explorer.EXE | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 1320 | "C:\Program Files\Lenovo\System Update\uncsetting.exe" | C:\Program Files\Lenovo\System Update\uncsetting.exe | — | SUService.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: uncsetting Exit code: 0 Version: 5.7.0.137 Modules
| |||||||||||||||
| 1584 | "C:\Windows\system32\cmd.exe" /c call "C:\Program Files\Lenovo\System Update\detectpm.cmd" | C:\Windows\system32\cmd.exe | — | system_update_5.07.0137.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1948 | "C:\Program Files\Lenovo\System Update\ConfigService.exe" settrigger | C:\Program Files\Lenovo\System Update\ConfigService.exe | — | system_update_5.07.0137.tmp | |||||||||||
User: admin Integrity Level: HIGH Description: ConfigService Application Exit code: 0 Version: 5, 7, 0, 137 Modules
| |||||||||||||||
| 1984 | "C:\Windows\TempInst\is-JGILQ.tmp\system_update_5.07.0137.tmp" /SL5="$2013A,7520034,410112,C:\Users\admin\AppData\Local\Temp\system_update_5.07.0137.exe" /SPAWNWND=$20130 /NOTIFYWND=$20138 | C:\Windows\TempInst\is-JGILQ.tmp\system_update_5.07.0137.tmp | system_update_5.07.0137.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2180 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe" "C:\Program Files\Lenovo\System Update\SUService.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe | — | system_update_5.07.0137.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: .NET Framework installation utility Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 2492 | "C:\Program Files\Lenovo\System Update\StartSuService.exe" | C:\Program Files\Lenovo\System Update\StartSuService.exe | — | system_update_5.07.0137.tmp | |||||||||||
User: admin Integrity Level: HIGH Description: StartSUService Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
3 844
Read events
3 529
Write events
310
Delete events
5
Modification events
| (PID) Process: | (1984) system_update_5.07.0137.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: C00700000862FA1136D8D801 | |||
| (PID) Process: | (1984) system_update_5.07.0137.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 0B4EECA5E4D13561AAA9F84442C13B2EB1BA7518C229673852624865513E14A6 | |||
| (PID) Process: | (1984) system_update_5.07.0137.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (1984) system_update_5.07.0137.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 142F7B13C22172F200E9A6ACE829974E9505578E7FB5CF1C1CE16E3DB309FC7A | |||
| (PID) Process: | (1984) system_update_5.07.0137.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\tvsu.exe |
| Operation: | write | Name: | (default) |
Value: C:\Program Files\Lenovo\System Update\tvsu.exe | |||
| (PID) Process: | (1984) system_update_5.07.0137.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\tvsu.exe |
| Operation: | write | Name: | Path |
Value: C:\Program Files\Lenovo\System Update\ | |||
| (PID) Process: | (1984) system_update_5.07.0137.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\tvsu_install.exe |
| Operation: | write | Name: | (default) |
Value: C:\swtools\readyapps\appinstall.exe -tvsu | |||
| (PID) Process: | (1984) system_update_5.07.0137.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\tvsu_install.exe |
| Operation: | write | Name: | Path |
Value: C:\swtools\readyapps\tvsu | |||
| (PID) Process: | (1984) system_update_5.07.0137.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\tvsu_install.exe |
| Operation: | write | Name: | Version |
Value: 5.07 | |||
| (PID) Process: | (1984) system_update_5.07.0137.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\tvsu_install.exe |
| Operation: | write | Name: | W7_CmdInst |
Value: setuptvsu.exe | |||
Executable files
198
Suspicious files
24
Text files
364
Unknown types
39
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1984 | system_update_5.07.0137.tmp | C:\Program Files\Lenovo\System Update\Common.dll | executable | |
MD5:— | SHA256:— | |||
| 3188 | system_update_5.07.0137.exe | C:\Users\admin\AppData\Local\Temp\is-L5N39.tmp\system_update_5.07.0137.tmp | executable | |
MD5:— | SHA256:— | |||
| 1984 | system_update_5.07.0137.tmp | C:\Program Files\Lenovo\System Update\is-Q6RRT.tmp | executable | |
MD5:— | SHA256:— | |||
| 1984 | system_update_5.07.0137.tmp | C:\Program Files\Lenovo\System Update\unins000.exe | executable | |
MD5:— | SHA256:— | |||
| 1984 | system_update_5.07.0137.tmp | C:\Program Files\Lenovo\System Update\is-2R4N7.tmp | executable | |
MD5:— | SHA256:— | |||
| 1984 | system_update_5.07.0137.tmp | C:\Program Files\Lenovo\System Update\ConfigScheduledTask.exe | executable | |
MD5:— | SHA256:— | |||
| 4080 | system_update_5.07.0137.exe | C:\Windows\TempInst\is-JGILQ.tmp\system_update_5.07.0137.tmp | executable | |
MD5:— | SHA256:— | |||
| 1984 | system_update_5.07.0137.tmp | C:\Program Files\Lenovo\System Update\clearsuservice.exe | executable | |
MD5:— | SHA256:— | |||
| 1984 | system_update_5.07.0137.tmp | C:\Program Files\Lenovo\System Update\is-32U39.tmp | executable | |
MD5:— | SHA256:— | |||
| 1984 | system_update_5.07.0137.tmp | C:\Program Files\Lenovo\System Update\is-E190N.tmp | executable | |
MD5:43141E85E7C36E31B52B22AB94D5E574 | SHA256:EA308C76A2F927B160A143D94072B0DCE232E04B751F0C6432A94E05164E716D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1088 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 592 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1088 | opera.exe | 185.26.182.94:443 | certs.opera.com | Opera Software AS | — | whitelisted |
1088 | opera.exe | 93.184.220.29:80 | crl3.digicert.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
certs.opera.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |